A Comparative Performance Analysis of Routing Protocols in MANET using NS3 Simulator
Автор: Rakesh Kumar Jha, Pooja Kharga
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 4 vol.7, 2015 года.
Бесплатный доступ
Due to frequent topology changes and routing overhead, selection of routing protocol in Mobile Ad-hoc Network (MANET) is a great challenge. A design issue for an efficient and effective routing protocol is to achieve optimum values of performance parameters under network scenarios. There are various routing protocols available for MANET. This paper involves study of four routing protocols (Ad-hoc On Demand Distance Vector Routing, Optimized Link State Routing, Dynamic Source Routing and Distance Sequenced Distance Vector), and performance comparisons between these routing protocols on the basis of performance metrics (throughput, packet delivery ratio, Packet dropped, jitter and end to end delay measured after simulation of network) with the help of NS3 Simulator.
AODV, OLSR, DSDV, Throughput, Packet delivery ratio, End to end delay, Jitter, Packet dropped
Короткий адрес: https://sciup.org/15011405
IDR: 15011405
Текст научной статьи A Comparative Performance Analysis of Routing Protocols in MANET using NS3 Simulator
Published Online March 2015 in MECS DOI: 10.5815/ijcnis.2015.04.08
-
I. Introduction
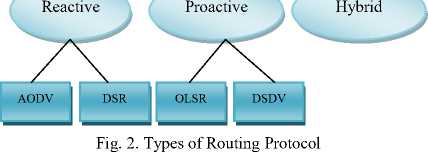
Mobile ad hoc network (MANET) [1] [15] has been popular research topic with the growth of Laptop and WiFi wireless networking since mid-1990s. A MANET [3] [4] is a self-configuring infrastructure less network of mobile devices connected by wireless [16] in which each device is free to move independently in any direction. It having dynamic topologies, Bandwidth constrained, variable capacity links, Energy constrained operation and limited physical security. Routing protocol plays an important role in any network [7]. It specifies how routes communicate with each other, disseminating information to select routes between any two nodes on a network. There is various kind of routing protocol present for ad hoc network and these can be categorized in three schemes: Flat and Hierarchical architecture, Proactive and Reactive routing protocol, Hybrid protocols. Here Proactive and Reactive routing protocol have been discussed for ad hoc network.
Fig. 1. Mobile Ad hoc Network
Above Fig. shows the Mobile Ad hoc Network.
Table 1.Comparision between protocols
|
Features |
Reactive |
Proactive |
Hybrid |
|
Routing Structure |
Flat |
Flat/Hierarchi cal |
Hierarchical |
|
Route Acquisiti on |
On demand |
Table driven |
Combination of both |
|
Routing Overhead |
Low |
High |
Medium |
|
Latency |
High due to flooding |
Low due to routing tables |
Inside zone Low outside similar to reactive protocols |
|
Scalabilit y |
Not suitable for large networks |
Low |
Designed for large networks |
|
Routing informati on |
Available when required |
Always available |
Combination of both |
|
Periodic Updates |
Not needed |
Yes whenever the topology of the network changes |
Yes |
|
Mobility |
Route Maintenance |
Periodic updates |
Combination of both |
Fig. 2 represents the types of routing protocol.
Routing Protocols
Above table represents the features of three protocols.
The rest of the paper is organized as follows: Section II introduces the Routing Protocols. Section III, IV, V and VI discuss the Overview of OLSR, AODV, DSDV and DSR Routing Protocols. Section VII presents the simulation results. Section VIII describes the performance metrics and section IX involves the performance analysis on the basis of metrics mentioned in above section. Finally section X concludes the paper.
-
II. Routing Protocols
In MANET [5] [18] routing protocol should be capable to handle a very large number of nodes with limited resources. The main issue associate with the routing protocol involves being appeared and disappeared of nodes in various locations. It is necessary to reduce routing message overhead despite the increasing number of nodes. Another important issue is to keeping the routing table small, reason being increasing the routing table affects the control packets sent in the network and in turn affects large link overheads.
Routing protocol [6] needs to have following qualities to be effective: distributed operation, loop freedom, demand based operation, proactive operation, security and unidirectional link support. Distributed operation means that any node can enter or leave whenever they want. Loop-freedom is to prevent overhead created during sending information uselessly. Demand based operation is to decrease traffic and use bandwidth resources more efficiently. Proactive operation is used when they require enough bandwidth and energy resources. Security is the most important factor for any communication.
Routing protocol [8][9] is categorized on the basis of how and when route are discovered, but both select the shortest path to the destination.
-
A. Proactive Routing Protocols
Proactive routing protocols [11] are also known as Table-driven routing protocol uses link-state routing algorithms which floods link information about its neighbors frequently. This type of protocol keeps and maintains up-to-date routing information between every pair of nodes by sending control message periodically in network. One of the main advantages of this protocol is that routes are ready to use when needed. The major drawback of proactive routing protocols includes the overhead of flooding route. There are various proactive routing protocols present for MANET [2] like DSDV, OLSR, and WRP etc.
-
B. Reactive Routing Protocols
Reactive or on-demand routing protocols [11] were designed to reduce overheads present in proactive protocols by maintaining information. It uses distancevector routing algorithm and establishes the route to given destination only when a node request it by initiating route discovery process. This protocols work on route discovery and route maintenance mechanism. Reactive routing protocols have drawback of delay in finding routes to new destination. There are number of reactive routing protocols available in MANET [14] like DSR, AODV, TORA and LMR etc.
-
III. Optimized Link State Routing Protocol (OLSR)
Optimized Link State Routing Protocol [3] [17] is based on link state algorithm. Being a proactive routing protocol, it has an advantage of having the route immediately available within the standard routing table when needed. Due to optimization nature minimum flooding duplication occurs in highly connected network. Each node in the network selects a set of neighboring nodes to retransmit the packets and this set of nodes is called multipoint relays of that node. Instead of pure flooding the OLSR protocol employs Multipoint Relay (MPR) in network to reduce the possible overhead, flooding of broadcast and time interval for control message transmission. Only MPRs forward the control packets in such a way that information should reach entire network and these MPRs are responsible for declaring LS information. Each node periodically broadcasts a list of its one hop neighbors to select the MPRs with the help of hello message. Route calculations are done by MPR from source to destination node. OLSR supports three mechanisms: neighbor sensing, efficient flooding of control traffic and sufficient topology information.
OLSR uses two types of control message: Hello and Topology Control (TC). Hello messages are used to find the information about the link status and node’s neighbors while TC messages are used for broadcasting information about own advertised neighbors includes at least the MPR selector list.
-
IV. Ad-hoc On Demand Distance Vector Routing (AODV)
The AODV routing protocol [10] is a reactive protocol that means routes are established whenever needed. It is based on On-demand mechanism of route discovery and route maintenance, plus the use of hop-by-hop routing and sequence number. Routing table consists of the information about the next hop to the destination and a sequence number received from the destination. This protocol supports two phase: route discovery, route maintenance; and data forwarding. Route discovery is done by broadcasting the RREQ message to its neighbors with the requested destination sequence number, which prevents looping problem. Neighbors reply with the RREP packets while having corresponding route otherwise forward RREQ packets to their neighbors. While noticed the breakage of the route the node sends RERR message to the neighbors. It uses the HELLO message periodically to inform the neighbor that link to the host is alive. While receiving the HELLO message node updates the lifetime of the node information in the routing table. Being a flat routing protocol, AODV protocol does not need any central administrative system to handle the routing process. It also reduces the control traffic message overhead at the cost of increased latency in finding new routes.
One carry all the available routing information is called full dump and other types i.e. incremental dump carries information that has changed since the last full dump. A full dump requires multiple Network Protocol Data Units (NPDU) while the incremental dump requires only one to fit in all information. While receiving the information packet from another node, node compares the sequence number with the available sequence number for the entry, and updates the entry with the new sequence number if the sequence number is larger or smaller. If the information arrives with the same sequence number, metric entry will be required.
In this protocol the updates lead to high control overhead during high mobility due to broken links. Another drawback is that node has to wait for a table update message initiated by the same destination node in order to obtain information about a particular destination node.
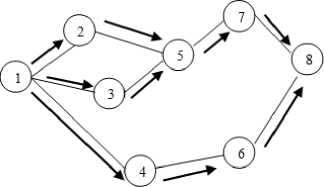
Fig.3. Propagation of RREQ
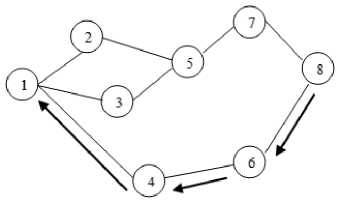
Fig. 4. Path taken by RREP
A source node broadcasts a RREQ packet to its neighbors, which then forwards the request to their neighbors and so on until they reach its destination as shown in Fig 3. When RREQ reaches the destination node, it responds by RREP packet as shown in Fig 4.
-
V. Distance Sequenced Distance Vector (DSDV)
The DSDV routing protocol [3] is a proactive routing protocol based on the Bellman-Ford routing algorithm that provides solution for shortest path between two nodes. In addition it introduces new feature i.e. sequence number for each routing table entry of entire network to avoid the formation of routing loops. Routing table is updated periodically throughout the network to maintain consistency in the table. To maintain the up-to-date view of the network, the tables are exchanged at regular interval of time. In order to reduce the amount of information carried during the broadcasting the routing information packets, two types of message are defined.
-
VI. Dynamic Source Routing (DSR)
DSR is a reactive protocol based on source routing concept that requires each packet to carry the full address (every hop in the route) from source to destination. It is based on On-demand mechanism of route discovery and route maintenance. An advantage of DSR protocol is that nodes can store multiple routes in their route cache. Source node can check its route cache for a valid route before initiating route discovery, and if a valid route is found there is no need for route discovery. On the other hand, if a node does not have such a route, it initiates route discovery by broadcasting a RREQ packet. The RREQ packet contains the address of the destination along with address of source, a route record field and a unique identification number. Once the RREQ reaches either the destination or a node that knows a route to destination, it responds with a RREP along with the reverse of the route collected by the RREQ. A failed link is detected by either actively monitoring acknowledgements or passively running in promiscuous mode, overhearing that packet is forwarded by neighboring node. The failed link is notified to the source node with RERR packet. The source node can use other known route to destination node or the process of route discovery is initiated again to find new route to destination. Another thing is to be noted that it does not require hello message exchanges, therefore nodes can enter sleep node to conserve their power. Also saves a considerable amount of bandwidth in the network.
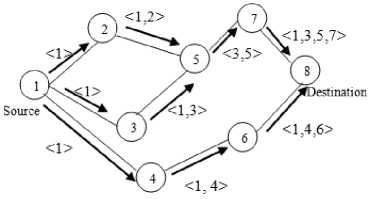
Fig. 5. Route discovery
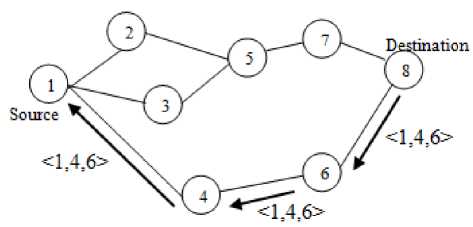
Fig. 6. Route reply
For route discovery a source node broadcasts a route request packet to its neighboring nodes as shown in Fig 5. In Fig. 6 a route reply message is sent back if the request packet reaches either destination nodes or intermediate nodes having active route to the destination nodes.
Table 2: Summary of protocols
|
Feature |
OLSR |
AODV |
DSDV |
DSR |
|
Protocol Type |
Link State |
Table driven and Source routing |
Distance vector |
Source routing |
|
Route maintained in |
Routing Table |
Routing Table |
Routing Table |
Route cache |
|
Route discovery |
Via control message link sensing |
On demand |
Via control message |
On demand |
|
Multiple route discovery |
Yes |
No |
No |
Yes |
|
Multicast |
Yes |
Yes |
Yes |
No |
|
Broadcast |
Limited by MPR set |
Yes |
Full |
Yes |
|
Reuse of routing informatio n |
Yes |
No |
Yes |
No |
|
Route reconfigur ation |
Link state Mechanis m/ Routing Message Transmissi on in advance |
Erase route then source notification or local route repair |
Sequence number adopted |
Erase route the source notificat ion |
|
Limited overhead |
Concepts of MPRs |
No |
Concept of Sequence numbers |
Concept of route cache |
|
Advantage s |
Minimize the overhead, improve the transmissi on quality |
Adaptable to highly dynamic topologies, reduced control overhead |
Avoid extra traffic, reduce the amount of space in the routing table |
Multiple routes, reduced bandwid th overhea d |
|
Disadvant ages |
Require more processing power and bandwidth |
Scalability problems, large delay caused by the route discovery process |
High control overhead, wastage of bandwidth |
Scalabil ity problem s due to source routing and flooding , large delay |
-
VII. Simulation tool
NS3 is open source discrete-event network simulator and improves simulation credibility. NS3 is not backward compatible with NS2, built from the scratch to replace NS2. NS2 and NS3 are both written with the help of C++ but NS3 does not support NS2 APIs. Some models have been ported from NS2 to NS3. NS3 is written in C++, with optional python bindings. NetAnim is GUI based network simulator used for NS3. It is stand-alone program that uses XML trace files to display the simulation graphically. It is based on Qt4 GUI toolkit.
-
VIII. Simulation Results
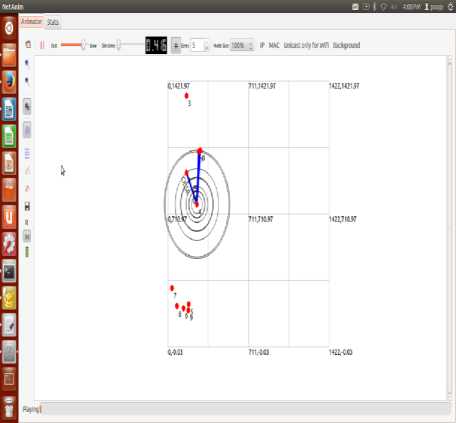
Fig. 7. Running Network with OLSR protocol
Fig. 7 showing running network with OLSR protocol using GUI based network simulator.
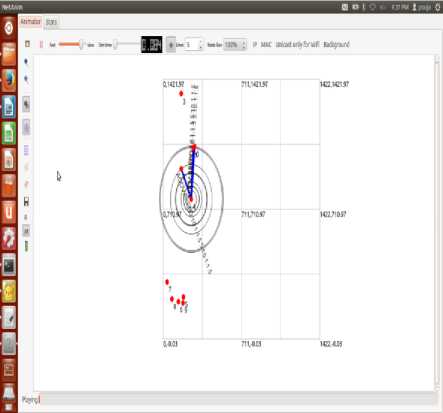
Fig. 8. Running Network with AODV protocol
Fig. 8 represents that network with AODV protocol is running with the help of GUI based network simulator.
Fig. 9. Running Network with DSDV protocol
The number of data packets that is not successfully delivered to the destination during transmission.
E. Jitter
It describes standard deviation of packet delay between all nodes.
-
IX. Performance Comparison Analysis
After Studying of three protocols (OLSR, AODV, and DSDV) we show performance comparisons of these protocols on the basis of performance metrics mentioned above. During the performance analysis we have realized that DSR is under development process. So Simulation is performed with varying nodes using rest of the three protocols.
In first scenarios we discuss about Packet delivery ratio for three protocols.
As we can see in Fig. 9, network with DSDV protocol is simulating on the GUI based network simulator named NetAnim [12][13].
-
VIII. Performance Metrics
There are various performance matrices to evaluate the routing protocols for MANET simulation but here we discuss the following metrics.
-
A. Throughput
It measures how well the network can constantly provide data to the destination.
( Re ceivedbytes Throughput = I
I* 8
Packet deliver y ratio (%)
OLSR
DSDV
AODV
Simulation time *
1024*1024
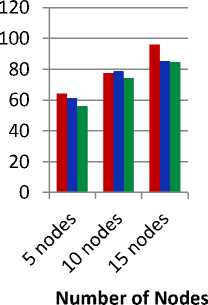
Fig. 10. Packet delivery ratio v/s number of nodes
It is derived in Mbps. For achieving better performance it should be high.
-
B. Packet Delivery Ratio
The ratio of the number of data packets delivered to the destination nodes and the number of data packets sent by source nodes.
Packetdeliveryratio = ( Re ceivedpacket I Sentpacket ) * 100%
The performance would be better when it is high.
-
C. End to end delay
The average time interval between the generation of packets in a source node and successfully delivery of it in a destination node.
Endtoendde lay = Delays um I Re ceivedpackets (3)
The performance would be better when it is low.
-
D. Number of Packets dropped
Fig. 10 shows the variation of PDR by varying the number of nodes. Here we can see that as the number of nodes is increased packet delivery ratio also increased in each case. In many cases it has been analyzed that packet delivery ratio is better for OLSR protocol and least for AODV.
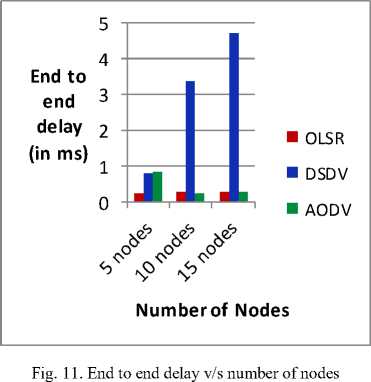
Fig. 11 shows the end to end delay with varying the number of nodes. As mentioned above end to end delay should be low for better performance. End to end delay for OLSR is almost same while changing the number of nodes, and it is least compared to other protocols.
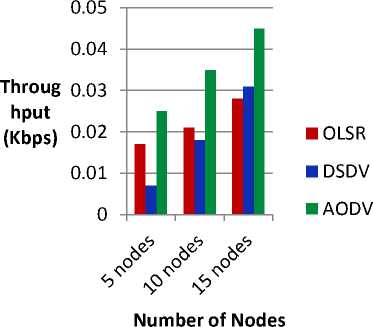
Fig. 12. Throughput v/s number of nodes
Fig. 12 represents the performance comparison of three protocols with respect to the metric throughput with varying the number of nodes. Throughput for AODV protocol is better while comparing it with OLSR and DSDV protocols as shown in figure.
Number of Nodes
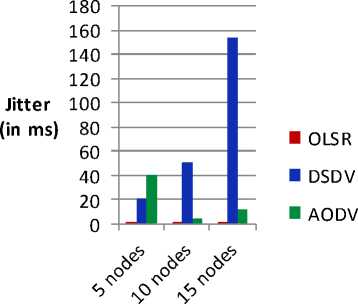
Fig. 14. Jitter v/s number of nodes
Above Fig. represents the performance analysis of protocols in terms of jitter by varying number of nodes. OLSR protocol shows the least jitter than DSDV and AODV protocols in each case.
While comparing OLSR with AODV and DSDV protocols we observed that OLSR protocol gives best result on the basis of Packet delivery ratio, packet dropped, jitter and end to end delay. As far as throughput is considered, the performance of AODV protocol is better for the network with varying number of nodes.
■ OLSR
■ DSDV
■ AODV
Number of Nodes
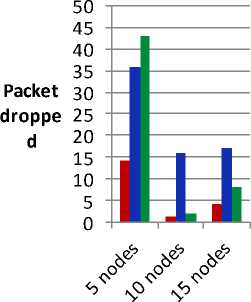
Fig. 13. Packet dropped v/s number of nodes
Fig. 13 showing the comparisons of routing protocols in terms of packet dropped with respect to number of nodes. As we can see that OLSR protocol provides less packet dropped compared to other protocols.
X. Conclusions
This paper includes the study and performance comparisons of three protocols with respect to the metrics packet delivery ratio, end to end delay, packet dropped, jitter and throughput. The result of simulation indicates that performance of AODV is certainly superior to the other protocols in terms of throughput for network having varying number of nodes. We observed that OLSR protocol gives better result than other two protocols while having considered the packet delivery ratio, Packet dropped, jitter and end to end delay.
Список литературы A Comparative Performance Analysis of Routing Protocols in MANET using NS3 Simulator
- Rakesh Kumar Jha, SV Limkar, DU Dalal, "A Performance Comparisons of Routing Protocols (DSR and TORA) for Security Issue in MANET (Mobile Ad Hoc Networks)," in IJCA Special Issue on MANETs (2), 2010, pp. 78-83.
- Charles E. Perkins, Elizabeth M. Royer, Samir R. Das and MLahesh K. Marina, Performance Comparison of Two On-Demand Routing Protocols for Ad Hoc Networks, IEEE Personal Communications, February 2001.
- Dilpreet Kaur, Naresh Kumar, "Comparative Analysis of AODV, OLSR, TORA, DSR and DSDV Routing Protocols in Mobile Ad-Hoc Networks," in International Journal of Computer Network and Information Security(IJCNIS), vol. 5, no.3, pp.39, 2013.
- Awadhesh Kumar, Prabhat Singh, Vinay Kumar, Neeraj Tyagi "Performance Analysis of AODV, CBRP, DSDV and DSR MANET Routing Protocol Using NS2 Simulation" in IJCNIS, vol.5, no.9, pp.45-50,2013. DOI: 10.5815/ijcnis.2013.09.06.
- H.Vignesh Ramamoorthy,D.Suganya Devi,"A New Proposal for Route Finding in Mobile AdHoc Networks", IJCNIS, vol.5, no.7, pp.1-8,2013. DOI: 10.5815/ijcnis.2013.07.01.
- Anil Kumar Verma, Dr. Harsh Sadawarti, Performance analysis of AODV, DSR and TORA routing protocols, IACSIT,Vol. 2, No. 2, ISSN :1793-8236, pp. 226-231, April 2010.
- Z. Hao, X. Yun and H. Zhang, " An Efficient Routing Mechanism in Network Simulation," In Proceedings of the 20th Workshop on Principles of Advanced and Distributed Simulation, Singapore, 2006:150-157.
- P. Johansson et al., "Routing Protocols for Mobile Ad-hoc Networks – A Comparative Performance Analysis," Proc. IEEE/ACM MOBICOM '99, Aug.1999, pp. 195-206.
- H. Ehsan and Z.A. Uzmi (2004), "Performance Comparison of Ad Hoc Wireless Network Routing Protocols," IEEE 8th international Multitopic Conference, Proceedings of INMIC, Dec 2004, pp. 457-465.
- Anuj K.Gupta, Dr. Harsh Sadawatri and Dr. Anil K. Verma, "Performance analysis of AODV, DSR & TORA Routing Protocols," IACSIT International Journal of Engineering and Technology, Vol.2 (2), April 2010.
- C.M barushimana, A. Shahrabi, "Comparative Study of Reactive and Proactive Routing Protocols Performance in Mobile Ad-Hoc Networks," Workshop on Advanced Information Networking and Application, Vol. 2, May 2003, pp. 679-684.
- NetAnim. [Online]. Available at: http://www.nsnam.org/wiki/NetAnim_1.0
- Ns-3 tutorial. [Online]. Available: http://www.nsnam.org/docs/release/3.14/tutorial/ singlehtml/index.html
- Boukerche A., "Performance comparison and analysis of ad hoc routing algorithms," IEEE international conference on performance, computing, and communications, 2001, pp. 171-178.
- Mohit kumar and Rashmi Mishra, "An Overview of MANET: History, Challenges and Applications," Indian Journal of Computer Science and Engineering (IJCSE), Vol. 3 (1), March 2012.
- YP Kosta, Upena D Dalal, Rakesh Kumar Jha " Security Comparison of Wired and Wireless Network with Firewall and Virtual Private Network (VPN)" in Recent Trends in information, Telecommunication and Computing (ITC), 2010 International Conference on IEEE, pp. 281-283.
- T. Clausen and P. Jaqcquet, "Optimized Link State Routing (OLSR) Protocol", RFC 3626, IETF Networking Group, October 2003.
- Subir Kumar Sarkar, T. G. Basavaraju and C. Puttamadappa, "Ad hoc Mobile Wireless Networks: Principles, Protocols and Applications. 1st ed. Auerbach Publications, 2008.


