A comparative study of recent steganography techniques for multiple image formats
Автор: Arshiya Sajid Ansari, Mohammad Sajid Mohammadi, Mohammad Tanvir Parvez
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 1 vol.11, 2019 года.
Бесплатный доступ
Steganography is the technique for exchanging concealed secret information in a way to avoid suspicion. The aim of Steganography is to transfer secrete message to another party by hiding the data in a cover object, so that the imposter who monitors the traffic should not distinguish between genuine secret message and the cover object. This paper presents the comparative study and performance analysis of different image Steganography methods using various types of cover media ((like BMP/JPEG/PNG etc.) with the discussion of their file formats. We also discuss the embedding domains along with a discussion on salient technical properties, applications, limitations, and Steganalysis.
Image Steganography, Steganography Embedding Domain, Steganography File Format
Короткий адрес: https://sciup.org/15015657
IDR: 15015657 | DOI: 10.5815/ijcnis.2019.01.02
Текст научной статьи A comparative study of recent steganography techniques for multiple image formats
Published Online January 2019 in MECS
image is a combination of cover image plus hidden data.
This paper presents a survey of Steganography algorithms based on various image formats. The paper is organized as follows. Section I includes the introduction and technical properties of Steganography, applications, limitations, methods, and Steganalysis. Section II presents Steganography cover image formats, their methods/techniques and color model information of each image format. Section III describes the literature review of recent Steganography techniques. Section IV is devoted to comparative analysis. Finally, we wrap up the discussion in Section V.
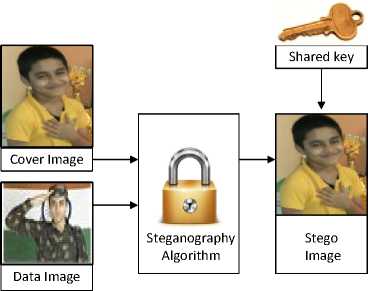
Fig.1. An Example of Image Steganography.
-
A. Applications and Limitations
Steganography is very effective for hiding information and can be used for a number of applications like social, scientific and governmental applications. However, as always, every technology may also have some downsides. Steganography can also be misused for unlawful activities; some constraints are also encountered in using Steganography. Following Table 1 shows some applications, while Table 2 shows some limitations of Steganography.
Table 1. Applications of Steganography Techniques.
|
a. |
Steganography is useful to transfer the secret message from source place to destination place. |
|
b. |
Steganography is also used to store and to transfer the information of secret location. |
|
c. |
Steganography can be used for secure online voting. |
|
d. |
It can be used for private banking. |
|
e. |
It can be used for the military purpose. |
Table 2. Limitations of Steganography Methods.
|
a. |
Terrorist for criminal activities can misuse it. To stop such illegal activities some governments have taken some corrective actions to restrict Steganography and the similar technologies. All these kind of technologies are under high surveillance. |
|
b. |
It can be misused by attackers to harm privacy concern for example in Film Industry (to plagiarise films), social media (to steal the personal information and pictures from WhatsApp Facebook Instagram etc.) Alternatively, software industry (for making pirated software). |
-
B. Steganalysis
Steganalysis is an art of breaking Steganography method to expose the existence of secreted information. Fig. 2. shows the example of Steganalysis process. Steganalysis has two approaches, one is ‘specific Steganalysis' (specific for spatial domain or specific for JPEG) and the second one is ‘universal Steganalysis’ (for all types of image format). It will not go through the specific Steganalysis category over the Internet, because one cannot judge which type of format is being used by the transmitter. In specific Steganalysis approach, the embedding method is already known; whereas universal Steganalysis approach is not aware of any prior knowledge about the embedding method [32]. Steganalysis can also be used to measure the robustness of Steganography method. [30]. Several Steganalysis approaches are presented by researchers in [33 – 38, 42].
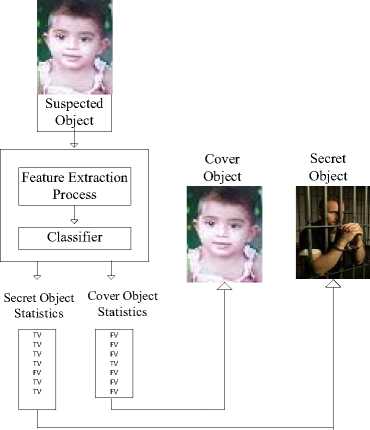
Fig.2. Illustration of the process of Steganalysis.
Steganalysis process is generally consists of six basic steps as shown in Fig. 3. Steganalysis senses suspected object over the Internet to break the Steganography method. The pre-processing step may apply image processing on the set of data images, for example, converting an image from color to greyscale or transformation or cropping or compression.
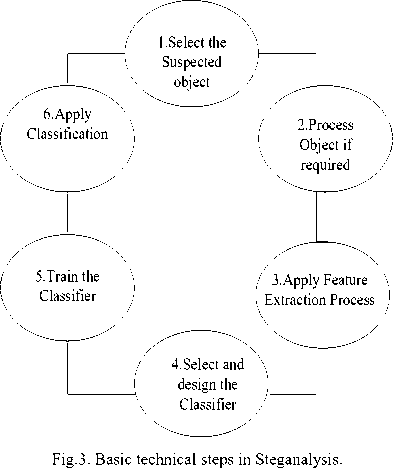
Steganalysis process also reduces dimensions of an image if required. The features should be rather different from the image without hidden message and for the stego-image. The larger the difference, the better the features are. The features should be as general as possible, i.e. they are effective to all different types of images and different data hiding schemes. Feature extraction, classifier design is another key issue for Steganalysis and the performance of a Steganalysis system. Combination of feature extraction and classifier design is evaluated by its classification success or error rate. [50]. Selection and design of the classifier are performed, based on extracted features. Steganalysis train the classifier according to the format required. In Steganalysis, classification is used to classify the set of the data object into the original data object and stego object. Some open source Steganalysis tools available are StegSecret, OpenPuff, StegDetect, StegBreak, StegSpy, Hiderman, Jsteg-shell, Jsteg-shell, JPhide and Seek, Camouflage, F5, Steganography Analyzer Real-Time, JPHide, JPegX, StegExpose.
-
II. Steganography Cover Image Formats
This section presents the discussion on various Steganography image file formats, their color models and different steganography methods / techniques used for various formats.
All the image formats consists of dissimilar characteristics, all contain different header information. The core difference between them is the amount of compression. For example, 24 bit RGB color image needs 9.6 megabytes storage if no compression is used. However, it requires much lesser space with compression. Finer details of image necessitates less compression, while more ratio of compression sacrifices the finer details. JPEG uses lossy compression, while Bitmap, PNG and TIFF images have lossless compression property.
-
A. JPEG (Joint Photographic Experts Group)
JPEG is one of the most commonly used image file formats. It is most widely used in digital cameras, memory cards, web pages, and image processing because JPEG format can compresses the image data into smaller file size and has low risk of attacks. JPEG uses lossy compression, which is a strong downside of it also. The error level is restricted to be below the perception threshold of human observer level. It does not allow editing and restoring images repeatedly, because more quality is lost every time you save an image in JPEG format. The signal delivered to the encoder is normally additive colours red, green and blue which are transformed into YCbCr components. JPEG uses the Huffman coder to encode the AC coefficients and differential encoding for the DC coefficients. It does not allow editing and restoring images repeatedly, because more quality is lost every time an image is saved in JPEG format.
which forms the part of the lossy level; and the second level is the Huffman coding that is a lossless data compression technique. JPEG image data embedding methods store secret data between these two phases [4]. DCT transformed cosine values cannot be back-calculated exactly and repeated calculation using limited precision number produces a rounding error hence, it is called lossy compression.
-
B. BMP (Bitmap)/RGB
BMP format offers compressed and uncompressed images file format in greyscale as well as in color mode. It also supports optional transparency. 8 bit Bitmap has a maximum of 256 colors per pixel. RGB is also available in 16 bits, 24 bits, 36 bits as well as 48 bits format. Here, 48 bits format images are considered as more color depth images as each channel uses 16 bits. In 24 bits format, each of the R, G and B channels use 8 bits and brightness intensity lies between 0 and 256. For 16 bits format, every pixel is two bytes and each color uses a precise number of bits. The syntax of Bitmap-File Structures [57] is as follows and details are as shown in Table 4.
BITMAPFILEHEADER
BITMAPINFOHEADER
RGBQUAD
BYTE bmfh;
bmih;
aColors[];
aBitmapBits[];
Table 3. Header Fields in JPEG File Structure [59].
|
JPEG header fields |
Size |
|
image_width |
512 |
|
image_height |
512 |
|
image_components |
3 |
|
image_color_space |
2 |
|
jpeg_components |
3 |
|
jpeg_color_space |
3 |
|
Comments |
{} |
|
coef_arrays |
{1x3 cell} |
|
quant_tables |
{[8x8 double] [8x8 double]} |
|
ac_huff_tables |
[1x2 struct] |
|
dc_huff_tables |
[1x2 struct |
|
optimize_coding |
0 |
|
comp_info |
[1x3 struct] |
|
progressive_mode |
0 |
A JPEG image consists of some coefficient matrices along with header information. A typical example of a JPEG image file structure has shown in Table 3 [59]. In the JPEG file structure, ‘Coef_arrays’ is one of the components in JPEG image file header. This component is a cell array of size 1 × 3 cell. We can divide each cell array into 8 × 8 blocks for easy and fast mathematical operations (less than 8 × 8 block does not contain enough information and greater than 8 × 8 blocks may not be supported by hardware or may take longer time too). Most of the information about the image lies in the DC coefficient which is the left top corner coefficient of DCT matrix. Other coefficients are known as AC coefficients. The JPEG coefficient values range from –1024 to +1023. Most of the AC coefficients have values of zero. JPEG compression has two levels: first DCT quantization,
Table 4. Bitmap File Structure.
|
Bitmap Structure Fields / Description |
Contained Information |
|
BITMAPFILEHEADER bmfh; [Bitmap file header] |
It contains information about the field type, field size, and layout of a device. It is independent bitmap file. |
|
BITMAPINFOHEADER bmih; [Bitmap information header.] |
It specifies the dimensions, compression type, and color format for the bitmap. |
|
RGBQUAD aColors [ ]; [Color table, and an array of bytes that defines the bitmap bits.] |
The color table, defined as an array of RGBQUAD structures, contains all the basic color elements in bitmap. The number of bytes representing a scan line stored in the bitmap. The first byte in the array represents the pixels in the lower-left side corner of the bitmap and the last byte represents the pixels in the upper-right corner. |
|
BYTE aBitmapBits[ ]; [The bitmap bits, consist of an array of BYTE values representing consecutive rows, or "scan lines," of the bitmap] |
8-bit Bitmap contains the maximum number of 256 colors. Each pixel in the bitmap is denoted by a 1-byte index into the color table. 24-bit Bitmap has a maximum of 2^24 colors. The bitmap bmiColors member is NULL, and each 3-byte sequence in the bitmap array represents the relative intensities of red, green, and blue, respectively, for a pixel. |
-
C. PNG (Portable Network Graphics)
PNG is used when we need a small file that maintains its original quality. It was designed especially for transferring images over the Internet. It supports a number of colors plus a varying degree of transparency. Transparency in the image allows an image to be moved or copied onto any other background image. PNG supports indexed color, grayscale and RGB. It supports palette-based images of 24-bit RGB or 32-bit RGBA colors, grayscale images, and full-colour non-palette-based RGB images. PNG is a lossless data compression. This means that all the data on the image is stored when the image is compressed, means there is no change in resolution. The PNG file always has first 8-byte signature values as shown Table 5 and four parts of chunks as shown in Table 6.
Table 5. PNG file with 8-byte Signature.
|
Field Values |
Purpose Of Hexadecimal values |
|
Hexadecimal 89 |
It has the high bit set to identify transmission systems, it do not support 8-bit data and to reduce the chance that a text file incorrectly interpreted as a PNG, or vice versa. |
|
Hexadecimal 50- 4E - 47 |
It permitting an individual to identify the format without difficulty if it will viewed in a text editor. |
|
Hexadecimal 0D - 0A |
A DOS- style line ending to detect DOS Unix line ending conversion of the data. |
|
Hexadecimal 1A |
A byte that halts display of the file in DOS when the command type used the end-of-file character. |
|
Hexadecimal 0A |
A Unix-style line ending (LF) to detect Unix-DOS line ending conversion. |
Table 6. Chunks within PNG.
|
Value Length |
Chunk type |
Chunk Data |
CRC length |
|
Four bytes |
Four bytes |
Length bytes |
Four bytes |
-
D. TIFF (Tagged Image File Format.)
TIFF format was developed in 1986 by an industry committee chaired by the Aldus Corporation. TIFF file extension is “.tiff" or ".TIFF". TIFF can handle a number of images within a single file. It is lossless format means it is an uncompressed file format when the image is compressed, there is no change in resolution. TIFF permit editing and resaving of the images without compression loss. TIFF offered options to use tags, layers, and transparency, and are compatible with photo manipulation programs like Photoshop. TIFF is the best choice if you need to edit the digital image. TIFF supports bi-level, grayscale, palette-color, and RGB full-color images.
-
E. Colour Models for Image Formats
A color model is a system for creating a whole range of colors from the basic colors. RGB and CMYK are the two common models used for image processing in Steganography. Overview of some more color models are given below.
-
• CMYK model
CMYK model (cyan- magenta- yellow -black). CMYK model uses the printing ink and here colors are the result of reflected light.
-
• RGB model
The RGB model uses light to display color. RGB color model consists of three basic colors red, green and blue. Light is added together in various combinations to reproduce a wide number of colors. The main purpose of the RGB color model is in the display of images on computer or TV. RGB model is an additive color model. Bitmap images used RGB model.
-
• HSV model
Hue means tint or tone, which is produced by "lightning", in terms of their shades of saturation and their brightness values. It is used in color editing software, but not in image analysis. Hue (h) color type ranges from zero to 360 degree, saturation color ranges from 0 to 100 % and value of brightness (v) ranges from 0 to 100 %. HSV and HSB model is same.
-
• HSL model
HSL, like HSV, is a 3-D representation of color. HSL stands also stands for hue, saturation, and lightness. The difference between the HSL and HSV model is: in HSL model the saturation and lightness components span the entire range of values.
-
• NCS model
The Natural Color System (NCS) is based on six colors that cannot be used to describe one another: white, black, red, yellow, green and blue; unlike RGB or CMYK model.
-
• Indexed colour
The color of each pixel is represented by a number. Each number called index corresponds to a color in the color table (the palette).
-
• Steganography Methods /Techniques
Some Steganography methods and techniques used for various image formats are described below.
-
• DCT (Discrete Cosine Transform) /
DWT (Discrete Wavelet Transform) Methods
DCT separates the image into 8*8 pixels blocks and embeds the secret bits by modifying the high or middle frequency. DWT divides the image pixel block into 4 sub-bands (LL, HL, LH, and HH), scan pixel from left to right horizontal manner and top to bottom vertical manner and then perform some addition and subtraction operations on pixels until the whole image get processed.
-
• Distortion Method
This method is used mostly on JPEG images. The secret bit is embedded using the distortion of the image and by calculating an error between original and stego image at the decoding stage in order to restore the hidden bits. The technique uses distortion functions and some error coding functions for Steganography.
-
• Spread Spectrum Method
Spread Spectrum radio transmission transmit messages below the noise level for any frequency level. This technique embeds secret bits in the noise and spreads secret data throughout the cover image. This technique can be merged with the error correction coding to ensure robust Steganography.
-
• Statistical Method
This method modifies the statistical property of an image for embedding. The cover image is divided into sub-images and one secret message bit is transmitted with a corresponding sub-image, transmitted in a way that the changes in statistical characteristics should not be visible.
-
• Adaptive Method
This method works for both spatial and transform domains. By using global statistical characteristics of the image, the method decides what changes can be done in the cover image, before processing the coefficients or pixels.
-
• LSB (Least Significant Bit Substitution) Method
Most common and popular method, in which LSB of a pixel is replaced by the secret message bit. Many modifications to the basic LSB substitution have been proposed, like the indicator method in [1].
-
III. Literature Review based on Different Image
Список литературы A comparative study of recent steganography techniques for multiple image formats
- Parvez, Mohammad Tanvir and Adnan Abdul-Aziz Gutub, (2011), "Vibrant color image Steganography using channel differences and secret data distribution”, Kuwait J Sci Eng 38, no. 1B 127-142.
- Amirtharajan, Rengarajan, Sandeep Kumar Behera, Motamarri Abhilash Swarup, and John Bosco Balaguru Rayappan.. (2010), "Colour guided colour image Steganography”. arXiv preprint arXiv: 1010.4007.pp 1-23.
- Singh, Rama Kant, and Brejesh Lall..(2013)."Saliency map based image Steganography". In Image and Vision Computing New Zealand (IVCNZ), 28th IEEE International Conference of, pp. 430-435.
- Muhammad, K., Ahmad, J., Farman, H. and Zubair, M.(2015)," A novel image steganographic approach for hiding text in color images using HSI color model". arXiv preprint arXiv:1503.00388.,pp 1-11.
- Reddy, V. Lokeswara.,(2015),"Novel Chaos Based Steganography for Images Using Matrix Encoding and Cat mapping Techniques”. Information Security and Computer Fraud 3, pp. 1: 8-14.
- Srinivasan, Avinash, Jie Wu, and Justin Shi.(2015),"Android-Stego: a novel service provider imperceptible MMS Steganography technique robust to message loss". In Proceedings of the 8th International Conference on Mobile Multimedia Communications, ICST, Institute for Computer Sciences, Social-Informatics and Telecommunications Engineering. pp. 205-212.
- Zhang, Yi, Xiangyang Luo, Chunfang Yang, Dengpan Ye, and Fenlin Liu, (2015),"A JPEG comparison Resistant Adaptive Steganography based on the Relative relationship between DCT coefficients.10th international conference on availability and security. 978-1-4673-6590-1/14IEEE DOI.10.1109/ARES2015.53.
- Yang, Ching-Nung, Cheonshik Kim, and Yen-Hung Lo. (2016),"Adaptive real-time reversible data hiding for JPEG images." Journal of Real-Time Image Processing, pp 1-11. Springer.
- Hiney, Jason, Tejas Dakve, Krzysztof Szczypiorski, and Kris Gaj,(2015),"Using Facebook for Image Steganography". In Availability, Reliability, and Security (ARES)", 10th International Conference on, pp. 442-447. IEEE.
- Amirtharajan, Rengarajan, Sandeep Kumar Behera, Motamarri Abhilash Swarup, and John Bosco Balaguru Rayappan. (2010), "Colour guided color image Steganography". arXiv preprint arXiv:1010.4007.
- Fridrich.J, (1999), April.” A new steganographic method for palette-based images”. In PICS pp. 285-289.
- Sujitha, P., and G. Murali, (2013),"Authentication of Gray Scale Document Images via the Use of PNG Image with Data Repairing". International Journal of Science and Research (IJSR) ISSN (Online): 2319-7064 Volume2, Issue 11.
- Zin, Wai. "Message Embedding In PNG File Using LSB Steganographic Technique. November (2013)". International Journal of Science and Research (IJSR) Volume 2.
- Chen, Yung-Fu, Show-Wei Chien, and Hsuan-Hung Lin. (2009),"True color image Steganography using palette and minimum spanning tree". WSEAS International Conference. Proceedings. Mathematics and Computers in Science and Engineering. Ed. Lifent Xi. No. 3. World Scientific and Engineering Academy and Society.
- Shahida, T, & Sobin, C. (2014). “An Efficient Method for Improving Hiding Capacity for JPEG2000 Images”. In Proceedings of International Conference on Internet Computing and Information Communications pp. 159-168 Springer India.
- Wang, C. and Ni, J, (2012), March. “An efficient JPEG steganographic scheme based on the block entropy of DCT coefficients”. In Acoustics, Speech and Signal Processing (ICASSP), 2012 IEEE International Conference on pp. 1785-1788. IEEE.
- Ramaiya M. K., Hemrajani N., and Saxena A. K.,(2013), "Security Improvisation in image Steganography using DES”. in Advance Computing Conference (IACC), IEEE 3rd International, pp. 1094-1099.
- Grover N. and Mohapatra A., (2013),"Digital Image Authentication Model Based on Edge Adaptive Steganography". in Advanced Computing, Networking and Security (ADCONS), 2nd International Conference on, pp. 238-242.
- Hemalatha, S., U. Dinesh Acharya, A. Renuka, and Priya R. Kamath, (February 2013),"A secure and high capacity image Steganography technique". Signal & Image Processing An international journal (SIPIJ)), Vol No 4: 83.
- Pooja Rai; Sandeep Gurung; M K hose, (March 2015),"Analysis of Image Steganography Techniques". International Journal of Computer Applications, ISSN 0975-8887, Volume 114, Issue 1, pp. 11 – 17.
- Huang, Fangjun, Jiwu Huang, and Yun-Qing Shi. (2012) "New channel selection rule for JPEG Steganography". Information Forensics and Security, IEEE Transactions on 7.4: 1181-1191.
- Holub, V., Fridrich, J., & Denemark, T. (2014). “Universal distortion functions for Steganography in an arbitrary domain”. EURASIP Journal on Information Security, 2014(1), 1-13.
- Al-Nofaie, Safia, Manal Fattani, and Adnan Gutub, (2016),"Capacity Improved Arabic Text Steganography Technique Utilizing ‘Kashida’ with Whitespaces". The 3rd International Conference on Mathematical Sciences and Computer Engineering (ICMSCE2016).
- Arshiya Tazeen and Abdul Rahim, (January-2017),”Encrypting Images by Patch-Level Sparse Representation for High Capacity Reversible Data Hiding”. ISSN 2348–2370 Vol.09, Issue.01, Pages: 0001-0008.
- Jiang, N., Zhao, N., & Wang, L. (2016).”LSB based quantum image Steganography algorithm”. International Journal of Theoretical Physics, 55(1), 107-123.
- Bas, Patrick. (2016), "Natural Steganography: cover-source switching for better Steganography". arXiv preprint arXiv:1607.07824.
- Nancy Garg, 2 Kamalinder Kaur, (Nov-Dec 2016),” Data Storage Security Using Steganography Techniques”. International Journal of Technical Research and Applications e-ISSN: 2320-8163, www.ijtra.com Volume 4, Issue 6, PP.93-98.
- Desai, M. B., & Patel, S. V. (2014).” Survey on Universal Image Steganalysis”. International Journal of Computer Science and Information Technologies, 5(3), 4752-4759.
- Mishra, R., Mishra, D., Ranjan, A., and Gupta, H. (2015). "A Survey on Secure Image Steganography based on F5 Algorithm". IJEIR, 4(2), pp.344-347.
- Ghasemzadeh, H., & Kayvanrad, M. H. (2017).” A Comprehensive Review of Audio Steganalysis Methods”. arXiv preprint arXiv:1701.05611.
- Kaur, M. and Kaur, G. (2014).” Review of Various Steganalysis Techniques”. (IJCSIT) International Journal of Computer Science and Information Technologies, 5(2).
- Suryawanshi, G.R., and Mali, S.N.(2015). "Study of Effect of DCT Domain Steganography Techniques in Spatial Domain for JPEG Images Steganalysis". International Journal of Computer Applications, 127(6), pp.16-20.
- Priya, R. L., Eswaran, P., & Kamakshi, S. P. (2013May). "Blind Steganalysis With Modified Markov Features And RBFNN". In International Journal of Engineering Research and Technology, Vol. 2, No. ESRSA Publications.
- Zhan, S. H., & Zhang, H. B. (2007, August).” Blind Steganalysis using wavelet statistics and ANOVA”. In Machine Learning and Cybernetics, 2007 International Conference on Vol. 5, pp. 2515-2519. IEEE.
- Ng, W.W., He, Z.M., Chan, P.P. and Yeung, D.S.(2011 July). “Blind Steganalysis with high generalization capability for different image databases using L-GEM”. In Machine Learning and Cybernetics (ICMLC), 2011 International Conference on Vol. 4, pp. 1690-1695. IEEE.
- Yan, Y., Li, L., & Zhang, Q. (2013).” Universal Steganalysis method based on multi-domain features. Jornal of Information & Computational Science”. 10(7), 2177-2185.
- Wu, S., Zhong, S. and Liu, Y.(2017). "Deep residual learning for image Steganalysis". Multimedia Tools and Applications, Springer, pp.1-17.
- Yamini, B. and Sabitha, R. (2016 Jan),"Universal Steganalysis Defend Against Adaptive Steganography Attack using MX Quadtree Neighbor Finding Mechanism". Indian Journal of Computer Science and Engineering (IJCSE) ISSN: 0976-5166 Vol. 6.
- Badr, S. M., Ismaial, G., & Khalil, A. H. (2014).” A Review on Steganalysis Techniques From Image Format Point of View”. International Journal of Computer Applications, Volume 102– No.4.
- Couchot, J. F., Salomon, M., & Couturier, R. (2016). “Improving Blind Steganalysis in Spatial Domain using a Criterion to Choose the Appropriate Steganalyzer between CNN and SRM+ EC”. arXiv preprint arXiv:1612.08882.
- Zhou, H., Chen, K., Zhang, W., & Yu, N. (2017). “Comments on Steganography Using Reversible Texture Synthesis”. IEEE Transactions on Image Processing, 26(4), 1623-1625.
- Albahar, M. A., Olawumi, O., Haataja, K., & Toivanen, P. (2017)." A Novel Method for Bluetooth pairing using Steganography", International Journal on Information Technology and Security, 9(1), 53-66.
- Li, F., Zhang, X., Chen, B., & Feng, G. (2013). “JPEG Steganalysis with high-dimensional features and Bayesian ensemble classifier”. IEEE Signal Processing Letters, 20(3), 233-236.
- Pan, Y., Ni, J., & Su, W. (2016, July). “Improved Uniform Embedding for Efficient JPEG Steganography”. In International Conference on Cloud Computing and Security pp. 125-133. Springer International Publishing.
- Pelosi, Michael J.; Kessler, Gary; and Brown, Michael Scott S., (2016). "One-Time Pad Encryption Steganography System", Annual Conference on Digital Forensics, Security and Law. 4.CDFSL Proceedings 2016.
- Pandey, Sarita, and Vimal Parganiha. (1 January 2017),"Hiding Secret Image In Video." International Journal of Research In Science & Engineering e-ISSN: 2394-8299 Volume: 3 Issue: p-ISSN: 2394-8280.
- Richa Khare, Rachana Mishra, Indrabhan Arya,(2014). "Video-Steganography By LSB Technique using Neural Network". IEEE 2014 sixth international conference on computational intelligence and communication networks.
- Debnath, B., Das, J.C. and De, D.,(2017). "Reversible logic-based image Steganography using quantum-dot cellular automata for secure Nano communication". IET Circuits, Devices & Systems, 11(1), pp.58-67.
- Moradi, M. (2017). “Combining and Steganography of 3d face textures”. arXiv preprint arXiv:1702.01325.
- Research on Steganalysis, (dated 13/02/2017) https://web.njit.edu/~shi/Steganalysis/steg.htm
- Steganalysis Tools, (23/04/2017). http://stegsecret.sourceforge.net
- Free Software Information (23/04/2017) http://listoffreeware.com/list-of-best-free-Steganography-software-for-windows
- Steganography tools, https://en.wikipedia.org/wiki/Steganography_tools (20/03/2017)
- Noman Koren, (22/09/2016) http://www.normankoren.com/pixels_images.html
- Harris Geospatial Solutions, (10/09/2016) https://www.harrisgeospatial.com/docs/READ_TIFF.html
- PNG Information, (27/04/2017), https://www.lifewire.com/png-file-2622803
- BMP Information (27/04/2017), http://www.digicamsoft.com/bmp/bmp.html
- Information, (27/04/2017), http://www.ssuitesoft.com/ssuitepicselsecurity.htm
- Arshiya Sajid Ansari, Mohammad Sajid Mohammadi, Mohammad Tanvir Parvez, (2017), "JPEG Image Steganography based on Coefficients Selection and Partition". International Journal of Image, Graphics and Signal Processing (IJIGSP), Vol.9, No.6, pp.14-22, 2017.DOI: 10.5815/ijigsp.2017.06.02.
- Pradhan, A., Sekhar, K. R., & Swain, G. (2017). “Adaptive PVD steganography using horizontal, vertical, and diagonal edges in six-pixel blocks”. Security and Communication Networks”, 2017.
- Rojali, Salman, A. G., & George. (2017, August). "Website-based PNG image steganography using the modified Vigenere Cipher, least significant bit, and dictionary-based compression methods". In AIP Conference Proceedings (Vol. 1867, No. 1, p. 020059). AIP Publishing.
- Ramaiya, M. K., Goyal, D., & Hemrajani, N. (2017). "Data Hiding in Image using Cryptography and Steganography, an Investigation". International Journal, 8(7).
- Sharifzadeh, M., Agarwal, C., Salarian, M., & Schonfeld, D. (2017). “A New Parallel Message-distribution Technique for Cost-based Steganography”. arXiv preprint arXiv:1705.08616.
- Denemark, T., & Fridrich, J. (2017). “Steganography with Multiple JPEG Images of the Same Scene”. IEEE Transactions on Information Forensics and Security.
- Wang, Z., Yin, Z., & Zhang, X. (2017).“Distortion Function for JPEG Steganography Based on Image Texture and Correlation in DCT Domain”. IETE Technical Review,1-8.
- Liu, C. L., & Liao, S. R. (2008). “High-performance JPEG steganography using complementary embedding strategy”. Pattern Recognition, 41(9), 2945-2955.
- Akhtar, N., Khan, S. and Johri, P., (2014), February. An improved inverted LSB image steganography. In Issues and Challenges in Intelligent Computing Techniques (ICICT), 2014 International Conference on pp. 749-755. IEEE.
- Umbarkar, A. J., Kamble, P. R., & Thakre, A. V. (2016). Comparative Study Of Edge-Based LSB Matching Steganography For Color Images". ICTACT Journal on Image & Video Processing, 6(3).
- Oktavianto, B., Purboyo, T. W., & Saputra, R. E. (2017).” A Proposed Method for Secure Steganography on PNG Image Using Spread Spectrum Method and Modified Encryption”. International Journal of Applied Engineering Research, 12(21), 10570-10576.
- Sharma, Aditi, Monika Poriye, and Vinod Kumar. (June 2017)."A Secure Steganography Technique Using MSB”, International Journal of Emerging Research in Management &Technology ISSN: 2278-9359 Volume-6, Issue-6.
- Kumar, Dr. Sushil, (2017). "A TQWT Based Approach for Image Steganography", Mathematical Sciences International Research Journal Vol 6 Issue 1 ISSN 2278 – 8697.
- Tarun Kumar, Shikha Chauhan,(2018)."Image Cryptography with Matrix Array Symmetric Key using Chaos based Approach", International Journal of Computer Network and Information Security (IJCNIS), Vol.10, No.3, pp.60-66, DOI: 10.5815/ijcnis.2018.03.07.
- Sengul Dogan, 2018."A New Approach for Data Hiding based on Pixel Pairs and Chaotic Map", International Journal of Computer Network and Information Security(IJCNIS), Vol.10, No.1, pp.1-9,.DOI: 10.5815/ijcnis.2018.01.01.
- Ahmed A. Abu Aziz, Hasan N.Qunoo, Aiman A. Abu Samra, 2018. "Using Homomorphic Cryptographic Solutions on E-voting Systems", International Journal of Computer Network and Information Security (IJCNIS), Vol.10, No.1, pp.44-59,.DOI: 10.5815/ijcnis.2018.01.06.


