A Hybrid Cryptographic Model for Data Storage in Mobile Cloud Computing
Автор: Oladeji P. Akomolafe, Matthew O. Abodunrin
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 6 vol.9, 2017 года.
Бесплатный доступ
Mobile Cloud Computing (MCC) is a paradigm that integrates Cloud Computing and Mobile Computing to deliver a better Quality of Experience (QoE) and Quality of Service (QoS) to mobile users and cloud subscribers. Mobile Cloud Computing (MCC) inherited resource limitation from Mobile Computing which was solved with Cloud Computing. Meanwhile, Cloud Computing has inherent problems such as privacy of user's data stored on cloud, intrusion detection, platform reliability, and security threats caused by multiple virtual machines. Thus, hindering the growth and the full acceptance of Mobile Cloud Computing (MCC) by subscribers. However, using a signature based hybrid cryptography ensures confidentiality, integrity, authentication and non-repudiation on resource-poverty devices used in Mobile Cloud Computing. This paper presents a data protection scheme where data is encrypted using a hybrid cryptographic algorithm which is composed of Advanced Encryption Standard (AES), Blake2b and Schnorr signature before being stored in the cloud storage (Amazon Simple Storage Server). Thus, data confidentiality, integrity, authentication and non-repudiation are ensured.
Mobile Cloud Computing (MCC), Amazon S3, Advanced Encryption Standard (AES), Blake2b, Schnorr signature, Cryptography
Короткий адрес: https://sciup.org/15011858
IDR: 15011858
Текст научной статьи A Hybrid Cryptographic Model for Data Storage in Mobile Cloud Computing
Published Online June 2017 in MECS
The ubiquity and increasing capacity of mobile devices have ignited many new computing paradigms such as Mobile Computing, Mobile Cloud Computing, Mobile Sensing, Pervasive Computing, Collaborative Computing and so on. Mobile Cloud Computing (MCC) as one of the paradigms which amalgamated Cloud Computing with Mobile Computing was defined by [2] as “the combination of cloud computing, mobile computing and wireless networks to bring rich computational resources to network operators, mobile users and cloud computing providers”.
MCC inherited different problems from the comprising paradigms. It inherited resource-poverty from Mobile Computing which was solved with Cloud computing.
Meanwhile, Cloud Computing has inherent problems such as security and privacy of user’s data that is stored on cloud, intrusion detection, platform reliability, and security threats caused by multiple virtual machines [12].
In order to mitigate the security and privacy challenges, cryptography has been employed over the years to provide privacy, confidentiality and integrity. Cryptography as one of the major approaches to solving data security issues is defined as the process of encrypting and decrypting data to ensure privacy, confidentiality and integrity. The major feature goals of cryptography are: confidentiality, data integrity, authentication and non-repudiation. These are achieved by using the following cryptography schemes: Encryption, Hash Functions, Message Authentication Codes (MAC) and Digital Signatures. There are three types of Cryptography: Symmetry, Asymmetry and Hybrid [22].
This paper presents a hybrid cryptographic model called ABS comprising Advanced Encryption Standard (AES) Blake2b and Schnorr Signature Scheme which is resource-efficient for better data security in Mobile Cloud Computing (MCC).
-
A. Mobile Cloud Computing
MCC is an integration of Mobile Computing and Cloud Computing. Mobile Cloud Computing integrates the basic functional architectures of mobile communication using either wireless access point or radio tower (Wi-Fi, 3G, 4G or 5G technologies) to access cloud resources (Servers and Virtual Machines) [7] due to resource limitations of the mobile devices as shown in the Fig. 1 below
-
B. MCC Model
MCC model consists of three components mainly as shown in Fig.1. These components include [23]:
-
• Mobile Terminal : This refers to the portable and movable devices such as smart phones, PDA and tablets.
-
• Cloud: It contains servers providing services like Infrastructure-as-a-Service (IaaS), Platform-as-a-
- Service (PaaS) and Software-as-a-Service (SaaS).
-
• Mobile Network: It makes services available to mobile devices. So whenever we talk about the security in MCC, we should consider the security and privacy issues in all these three aspects.
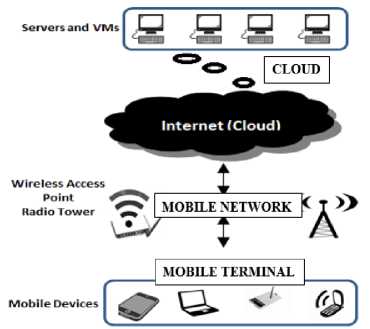
Fig.1. Overview of Mobile Cloud Computing [17]
-
C. MCC Issues
In Mobile Cloud Computing, the data storage and processing are done in the cloud [15]. The security and privacy of user’s data that is stored on cloud is one of the major issues needed to be resolved in MCC [12] because MCC users may store all confidential data in the cloud for either a short or long term usage with little or no control over it while a malicious mind in disguise of a cloud staff may access the confidential data, steal and pass it on to user’s competitors [19]. Therefore, the security of the data in the cloud becomes a real issue. Moreover, the user data needs to be protected not only from the outside attackers but also make it inaccessible to the cloud service providers.
-
D. Cryptography
Список литературы A Hybrid Cryptographic Model for Data Storage in Mobile Cloud Computing
- N. M. AbdElnapi, F. A .Omara, and N. F. Omran, "A hybrid hashing security algorithm for data storage on cloud Computing", International Journal of Computer Science and Information Security, vol. 14, no. 4, pp. 175, 2016.
- S. Abolfazli, Z. Sanaei, E. Ahmed, A. Gani, and R. Buyya, "Cloud-based augmentation for mobile devices: motivation, taxonomies, and open challenges", IEEE Communications Surveys & Tutorials, vol. 16, no. 1, pp.337-368, 2014.
- Y. Alkady, M. I. Habib and R. Y. Rizk, "A new security protocol using hybrid cryptography algorithms", In Computer Engineering Conference (ICENCO), 2013 9th International, pp. 109-115, IEEE, December, 2013.
- J. P. Aumasson, L. Henzen, W. Meier and R.C.W. Phan, "Sha-3 proposal blake", Submission to NIST, 2008.
- J.P. Aumasson, W. Meier and R. C. W. Phan, "The hash function family LAKE", In International Workshop on Fast Software Encryption, pp. 36-53, Springer Berlin Heidelberg, February 2008.
- A. Bhardwaja, G. V. B. Subrahmanyam, V. Avasthi and H. Sastry, "Security algorithms for cloud computing", Procedia Computer Science, vol. 85, pp. 535-542, 2016.
- D. De, "Mobile Cloud Computing: Architectures, Algorithms and Applications", CRC Press, 2016.
- O. Dunkelman and E. Biham, "A framework for iterative hash functions: HAIFA" In 2nd NIST Cryptographic Hash Workshop, vol. 22, August 2006.
- H. M. A Kader, M. M. Hadhoud, S. M. El-Sayed and D. S. AbdElminaam (2014). Performance evaluation of new hybrid encryption algorithms to be used for mobile cloud computing. International Journal of Technology Enhancements and Emerging Engineering Research, 2(4).
- V. Kapoor and R. A. Yadav, "Hybrid cryptography technique to support cyber security infrastructure", International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), vol. 4, no. 11, pp. 3995-4005, November 2015.
- A. Kaur, "An age of cloud in Mobile Computing (Mobile Cloud Computing", International Journal of Advanced Research in Computer and Communication Engineering, vol. 4, no. 11, 2015.
- A. N. Khan, M. M. Kiah, S. U. Khan and S. A. Madani, "Towards secure mobile cloud computing: A survey", Future Generation Computer Systems, vol. 29, no. 5, pp. 1278-1299, 2013.
- P. Kumar and S. B. Rana, "Development of modified AES algorithm for data security", Optik-International Journal for Light and Electron Optics, vol. 127, no. 4, pp. 2341-2345, 2016.
- V. Palanisamy and A. Jeneba Mary, "Hybrid cryptography by the implementation of RSA and AES", International Journal of Current Research, vol. 33, no. 4, pp. 241-244, 2011.
- M. N. Rajkumar, J. Muhamed Sabir, V Venkatesa Kumar and S. P. Bharathi, "A comparative analysis of different encryption techniques used in Mobile Cloud Computing", International Journal of Research in Advent Technology, vol. 2, no. 11, November 2014.
- P. Patel, R. Patel and N. Patel, "Integrated ECC and Blowfish for Smartphone Security", Procedia Computer Science, vol. 78, pp. 210-216, 2016.
- H. Qi, and A. Gani, "Research on mobile cloud computing: Review, trend and perspectives", In Digital Information and Communication Technology and it's Applications (DICTAP), 2012 Second International Conference on (pp. 195-202). IEEE, 2012.
- Ryan Toukatly. Rochester Institute of Technology SHA-3: The BLAKE Hash Function.
- A. Sachdev and M. Bhansali, "Enhancing cloud computing security using AES algorithm", International Journal of Computer Applications, vol. 67, no. 9, 2013.
- C. P. Schnorr, "Efficient identification and signatures for smart cards", In Conference on the Theory and Application of Cryptology (pp. 239-252). Springer New York, August 1989.
- W. Stallings, Cryptography and Network Security: Principles and Practice, 6th ed., Pearson Education, 2014.
- M. Sujithra, G. Padmavathi and S. Narayanan, "Mobile device data security: A cryptographic approach by outsourcing mobile data to cloud", Procedia Computer Science, vol. 47, pp. 480-485, 2015.
- H. Suo, Z. Liu, J. Wan and K. Zhou, "Security and privacy in mobile cloud computing", In 2013 9th International Wireless Communications and Mobile Computing Conference (IWCMC) (pp. 655-659), IEEE, July 2013.
- S. Vanishreeprasad and K N Pushpalatha, "Design and implementation of hybrid cryptosystem using AES and Hash Function. IOSR Journal of Electronics and Communication Engineering, vol. 10, no. 3, pp. 18-24, doi: 10.9790/2834-10321824.
- N. Nagar and U. Suman, "A secure mobile cloud storage environment using encryption algorithm", International Journal of Computer Applications, vol. 140, no. 8, pp. 0975 – 8887, April 2016.
- Seyyed Yasser hashemi, Parisa Sheykhi Hesarlo,"Security, Privacy and Trust Challenges in Cloud Computing and Solutions", IJCNIS, vol.6, no.8, pp.34-40, 2014. DOI: 10.5815/ijcnis.2014.08.05


