A novel approach of kurtosis based watermarking by using wavelet transformation
Автор: Khaza Mizbahuddin Quadry, A. Govardhan, Mohammed Misbahuddin
Журнал: International Journal of Image, Graphics and Signal Processing @ijigsp
Статья в выпуске: 7 vol.10, 2018 года.
Бесплатный доступ
The authentication is used to ensure the authentication of the owner of the data. Currently, the data is available in multimedia format viz., audio, video, image and text. The present paper focuses on the image authentication. The watermarking methods are used for the image authentication. The present paper proposes a novel method of Kurtosis based Watermarking by using Wavelet Transformation (KWWT). The proposed method uses wavelet transformation. Further, the bands or the coefficients are divided into various non overlapped windows. For each of the approximation band windows, the kurtosis value will be estimated. Then the windows in all bands will be selected based on their kurtosis value. Then, the watermark image will be embedded into the selected windows of the bands. Finally, inverse wavelet transformation will be applied to get the resultant watermarked image. The proposed KWWT method is evaluated with 14 input images and 3 watermark images. Various performance measures are estimated and the results show the efficacy of the proposed method.
Band, window, watermark and performance measure
Короткий адрес: https://sciup.org/15015979
IDR: 15015979 | DOI: 10.5815/ijigsp.2018.07.05
Текст научной статьи A novel approach of kurtosis based watermarking by using wavelet transformation
Published Online July 2018 in MECS DOI: 10.5815/ijigsp.2018.07.05
During the recent advancements in the internet technology, the security aspects of data have gained much attention. Among various aspects, the researchers focus more on the authentication. Among various formats of the data, image form of data is used by major researcher’s community. The watermarking method allows embedding of authentication in the input image data. In general, the authentication data consists of watermark of the owner. It is also called as copy right information of the owner. With the watermarking method, the difference between the original and the resultant images cannot be detected by the human eye. Various applications of digital watermarking methods [1] are monitoring of broadcast, control of copy and authentication of content broadcasted etc.
The transformations allow analyzing the input image into various scales. Among various transformations, the wavelet transformation along with the cosine transformation is widely used for the watermarking procedure. The cosine transformation is used to suppress the correlation between various bands of the wavelet transformation [2]. This is used to design the blind watermark. The cosine transformation is also used for the color images. It is observed that the YCbCr model of the color image along with the cosine transformation is suitable for the watermarking algorithm [3]. This method consists of genetic algorithm for selection of the components in Y.
-
II. Related Worrk
The watermarking method with singular value decomposition is used for enhancing the robustness [4]. This method applies the singular value decomposition on the wavelet coefficients of the input image and then fuzzy logic is used for the embedding procedure. The cosine transformation based watermarking method is used for the color images in RGB model [5]. In this process, robustness is increased with the normalization process. The watermarking algorithm can be applicable for the halftone images. In this, the patterns of the watermark can be embedded into two different halftone images [6]. During this process, patterns can be embedded into first image. On the first image, the second image can be overlaid. The modulation based watermarking [7] is found to be efficient for watermarking process. For this, the quantization index based modulation is used. This modulation technique is applied to the dominant parts of the transformation coefficients. The coefficients are further coupled with multiple scales. The watermarking method can be designed based on the optimality measure of the shares [8]. Three different shares will be used for the design of visual watermarking method. The watermarking method can combine the features of spatial and frequency domains [9]. With this, the quantification of the algorithm can be increased and further improves the robustness. The watermarking method can be designed based on the random key generation [10]. The random key can be a pseudorandom number. This number can be used for the selection of the region of the input image. The blind embedding procedure is adopted during the watermarking method. The watermarking method based on the edge information [11] is found to be efficient. This can differentiate the regions of the input image based on the high and low peak values of the edges. The wavelet packet based watermarking [12] is found to be efficient. In this, the energy measure is used for the selection of the sub band of the transformation. The arithmetic progression based watermarking [13] can be implemented with the wavelet transformation. In this, the subbands of the transformation can be selected based on the mean arithmetic progression value. The spread transform dither modulation [14] can be used for the design of the efficient watermarking [15, 16, 17] method. This method also uses the wavelet transformation for resolving the input image at multiple scales.
-
III. Methodology
In the information security research area, various security features should be provided for the input information. The present paper is focusing on providing the security for the images. For images, both the authentication and confidentiality features play a vital role for providing security. The authentication service should ensure the owner of the image and the confidentiality service should ensure the confidentiality of the information in the image. So, to provide these two features, the present paper is proposing a novel invisible watermarking method.
The proposed method is using the wavelet transformation. The wavelet transformation is used to analyze the input image at multiple scales. At each scale, four bands images will be extracted. The first band is called as the approximation band. The approximation band is used to represent the scaled image of the input image. The second band is used to represent the horizontal directional patterns of the input image. The third band is used to represent the vertical directional patterns of the input image. The fourth band is used to represent the diagonal directional patterns of the input image. The Fig. 1 represents the original and the first level wavelet transformation image. The four bands of the input image are shown in Fig. 1. The Fig. 2 shows frequency distribution of patterns in the wavelet coefficients. The Fig. 2(a) shows the distribution of approximation band, the Fig. 2(b) shows the distribution of horizontal band, the Fig. 2(c) shows the distribution of vertical band and Fig. 2(d) shows the distribution of diagonal band.
Among various statistical measures of an image, kurtosis is found to be prominent. The “tailedness” of the image is estimated with the kurtosis measure. It considers the input image as a random variable and applies the normal distribution. The Kurtosis equation is given in (1).
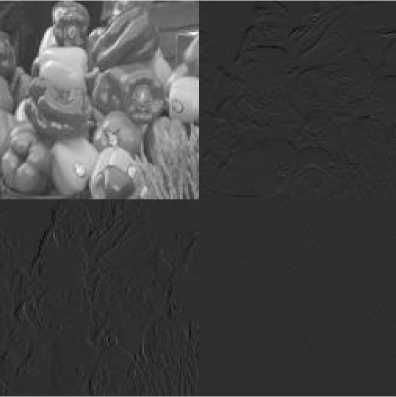
Fig.1. First level coefficient of wavelet transformation.
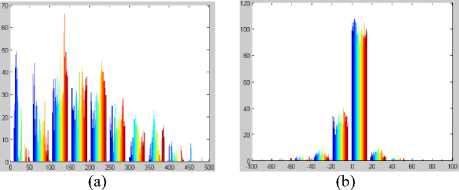
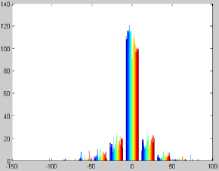
Fig.2. Frequency Distribution of patterns in (a) approximation band (b) horizontal band (c) vertical band (d) diagonal band.
(d)
K =
JN Г I ( i , j ) - m ^ 4
j l 1 ^ )
M X N
- 3
where,
I represent the input image, m represent the mean, σ represent the variance, M and N represents the size of the image.
Based on the Kurtosis measure, the present paper proposes a novel method of Kurtosis based Watermarking by using Wavelet Transformation (KWWT). In the
KWWT, the wavelet transformation is applied on the input image. Each band of the wavelet coefficients are further divided into 4×4 non overlapped windows. The kurtosis value is estimated for each none overlapped window of the approximation band. Then windows that are having highest kurtosis value will be identified and the corresponding windows in the horizontal, vertical and diagonal bands will be selected. The input watermark will be embedded into the corresponding bands of the wavelet coefficients. The methodology of the proposed KWWT method is shown in Fig. 3.
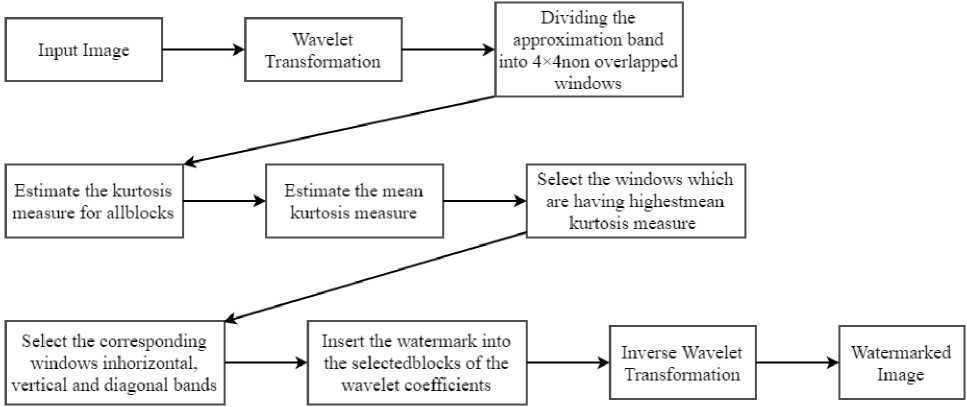
Fig.3. Methodolgoy of the proposed KWWT method.
-
IV. Results and Discussions
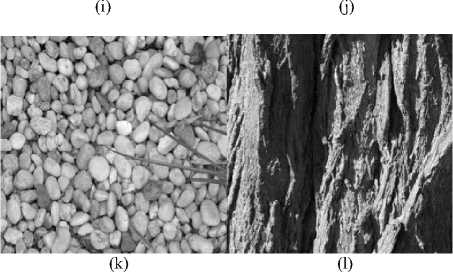
The watermarking methods are widely used in information security for providing the image authentication. The present paper proposes a novel method of Kurtosis based Watermarking by using Wavelet Transformation (KWWT). The proposed method is evaluated with 14 images [18]. The images considered are categorized into seven groups viz., human, animal, flower, fruit, landscape, texture and winter. In each group, two different images are considered for the evaluation of the proposed method. The original 14 images are shown in Fig. 4.
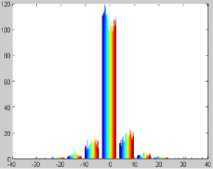
In the proposed KWWT method, the wavelet trnasformation is applied on the input image. Then, the non overlapped windows are estimated for the approximation band. For each non overlapped window, the kurtosis measure is estimated. The Fig. 5 and Fig. 6 represents the kurtosis measure of the Flower Image1 and Landscape Image2. In the approximation band, the non overlapped windows with highest kurtosis measure will be identified. The watermark image will be embedded into the corresponding other bands of the wavelet coefficients. The present paper uses three different watermarks as shown in Fig. 7.
The proposed KWWT method is applied on the 14 input images as shown in Fig. 4 and the three watermark images as shown in Fig. 7. The results of the KWWT method with WM Image1 is shown in Fig. 8. The results of the KWWT method with WM Image2 is shown in Fig. 9. The results of the KWWT method with WM Image3 is shown in Fig. 10. From these results, it is clear that the proposed KWWT method is efficient and robust.

(a) (b)

(c) (d)

(e) (f)
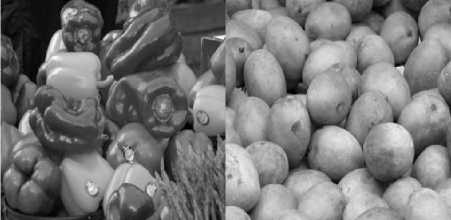
(h)
(g)


(m)
(n)
Fig.4. Original Images (a) Human Image1 (b) Human Image2 (c)
Animal Image1 (d) Animal Image2 (e) Flower Image1 (f) Flower
Image2 (g) Fruit Image 1 (h) Fruit Image2 (i)Landscape Image1 (j) Landscape Image2 (k) Texture Image1 (l) Texture Image2 (m) Winter Image1 (n)Winter Image2.
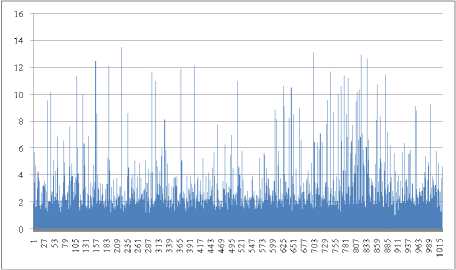
Fig.5. Kurtosis Measure of the Flower Image1.
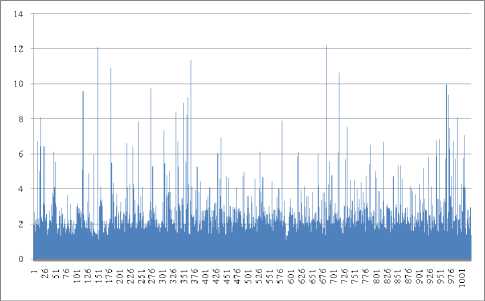
Fig.6. Kurtosis Measure of the Landscape Image2.

(a) (b)
(c)
Fig.7. Watermark Images (a) WM Image1 (b) WM Image2 (c) WM Image3.

(a)
(b)

(c) (d)

(e) (f)

(g) (h)
The performance of the proposed KWWT method is evaluate with various measures viz., Mean Absolute Error (MAE), Mean Square Error(MSE), Root Mean Square Error (RMSE), Peak Signal to Noise Ratio, Signal to Noise Ratio (SNR) and Root Signal to Noise Ratio (RSNR). The performance measures are estimated for all the 14 input images with three different watermark images. The results with WM Image1 are shown in Table 1, results with WM Image2 are shown in Table 2 and the results with WM Image3 are shown in Table 3. From these results, it is observed that the proposed method is found to be efficient.

(i)
(j)

(k)
(l)

(m)
(n)
Fig.8. Watermarked Results with WM Image1 (a) Human Image1 (b) Human Image2 (c) Animal Image1 (d) Animal Image2 (e) Flower Image1 (f) Flower Image2 (g) Fruit Image 1 (h) Fruit Image2 (i)Landscape Image1 (j) Landscape Image2 (k) Texture Image1 (l) Texture Image2 (m) Winter Image1 (n)Winter Image2.

(a) (b)

(c) (d)

(e) (f)

(g) (h)

(i)
(j)

(e) (f)

(k)
(l)

(g) (h)

(m)
(n)

(i) (j)
Fig.9. Watermarked Results with WM Image2 (a) Human Image1 (b) Human Image2 (c) Animal Image1 (d) Animal Image2 (e) Flower Image1 (f) Flower Image2 (g) Fruit Image 1 (h) Fruit Image2 (i)Landscape Image1 (j) Landscape Image2 (k) Texture Image1 (l) Texture Image2 (m) Winter Image1 (n)Winter Image2.

(a) (b)

(k)
(l)

(c) (d)

(m) (n)
Fig.10. Watermarked Results with WM Image3 (a) Human Image1 (b) Human Image2 (c) Animal Image1 (d) Animal Image2 (e) Flower Image1 (f) Flower Image2 (g) Fruit Image 1 (h) Fruit Image2 (i)Landscape Image1 (j) Landscape Image2 (k) Texture Image1 (l) Texture Image2 (m) Winter Image1 (n)Winter Image2.
Table 1. Estimated Performance Measures with WM Image1.
|
S.No. |
Image |
MAE |
MSE |
RMSE |
PSNR |
SNR |
RSNR |
|
1 |
Human1 |
0.0081 |
0.0064 |
0.0800 |
92.0161 |
19402.53222 |
139.2929726 |
|
2 |
Human2 |
0.0530 |
0.0419 |
0.2047 |
75.6865 |
2669.904535 |
51.67111896 |
|
3 |
Animal1 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
131876.4081 |
363.1479149 |
|
4 |
Animal2 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
97705.04296 |
312.578059 |
|
5 |
Flower1 |
0.0000 |
0.0000 |
0.0000 |
589.1390 |
7.97675E+28 |
2.82431E+14 |
|
6 |
Flower2 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
98937.63723 |
314.5435379 |
|
7 |
Fruit1 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
96406.78043 |
310.4944129 |
|
8 |
Fruit2 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
136826.9356 |
369.9012511 |
|
9 |
Landscape1 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
127029.5131 |
356.4119991 |
|
10 |
Landscape2 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
150909.3508 |
388.4705276 |
|
11 |
Texture1 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
126489.5967 |
355.6537595 |
|
12 |
Texture2 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
95622.60859 |
309.2290552 |
|
13 |
Winter1 |
0.0012 |
0.0009 |
0.0308 |
108.6022 |
167557.7613 |
409.3381992 |
|
14 |
Winter2 |
0.0000 |
0.0000 |
0.0000 |
583.3261 |
7.44673E+28 |
2.72887E+14 |
Table 2. Estimated Performance Measures with WM Image2.
|
S.No. |
Image |
MAE |
MSE |
RMSE |
PSNR |
SNR |
RSNR |
|
1 |
Human1 |
0.0064 |
0.0057 |
0.0753 |
93.0495 |
21853.92742 |
147.8307391 |
|
2 |
Human2 |
0.0419 |
0.0372 |
0.1929 |
76.7199 |
3007.231183 |
54.83822739 |
|
3 |
Animal1 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
148538.2124 |
385.4065546 |
|
4 |
Animal2 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
110049.4973 |
331.7370906 |
|
5 |
Flower1 |
0.0000 |
0.0000 |
0.0000 |
589.1390 |
7.97675E+28 |
2.82431E+14 |
|
6 |
Flower2 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
111437.8226 |
333.8230408 |
|
7 |
Fruit1 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
108587.207 |
329.5257304 |
|
8 |
Fruit2 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
154114.2097 |
392.573827 |
|
9 |
Landscape1 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
143078.9409 |
378.2577704 |
|
10 |
Landscape2 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
169975.8548 |
412.2812812 |
|
11 |
Texture1 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
142470.8091 |
377.4530555 |
|
12 |
Texture2 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
107703.9597 |
328.1828144 |
|
13 |
Winter1 |
0.0009 |
0.0008 |
0.0290 |
109.6356 |
188727.6935 |
434.4280073 |
|
14 |
Winter2 |
0.0000 |
0.0000 |
0.0000 |
583.3261 |
7.44673E+28 |
2.72887E+14 |
Table 3. Estimated Performance Measures with WM Image3.
|
S.No. |
Image |
MAE |
MSE |
RMSE |
PSNR |
SNR |
RSNR |
|
1 |
Human1 |
0.0065 |
0.0052 |
0.0725 |
93.7292 |
23632.73547 |
153.7294229 |
|
2 |
Human2 |
0.0427 |
0.0344 |
0.1855 |
77.3996 |
3252.005814 |
57.02636069 |
|
3 |
Animal1 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
160628.532 |
400.7848949 |
|
4 |
Animal2 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
119007.0145 |
344.9739331 |
|
5 |
Flower1 |
0.0000 |
0.0000 |
0.0000 |
589.1390 |
7.97675E+28 |
2.82431E+14 |
|
6 |
Flower2 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
120508.343 |
347.1431161 |
|
7 |
Fruit1 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
117425.7006 |
342.674336 |
|
8 |
Fruit2 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
166658.3895 |
408.238153 |
|
9 |
Landscape1 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
154724.9012 |
393.3508627 |
|
10 |
Landscape2 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
183811.0988 |
428.7319662 |
|
11 |
Texture1 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
154067.2703 |
392.5140384 |
|
12 |
Texture2 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
116470.561 |
341.2778356 |
|
13 |
Winter1 |
0.0010 |
0.0008 |
0.0279 |
110.3153 |
204089.25 |
451.7623822 |
|
14 |
Winter2 |
0.0000 |
0.0000 |
0.0000 |
583.3261 |
7.44673E+28 |
2.72887E+14 |
-
V. Conclusions
The present paper proposes a novel method of Kurtosis based Watermarking by using Wavelet Transformation (KWWT). In the proposed method, the wavelet coefficients are further analyzed in detail for the watermark embedding process. The proposed KWWT is found to be efficient and the robust with the wavelet transformation.
Список литературы A novel approach of kurtosis based watermarking by using wavelet transformation
- Mohammad Abdullatif ; Akram M. Zeki, Jalel Chebil, Teddy Surya Gunawan, “Properties of digital image watermarking,” IEEE 9th International Colloquium on Signal Processing and its Applications (CSPA), 8-10 March 2013.
- Zhi-Yong Meng,Ping-Ping Yu, Guo-Qing Yu, “Copyright protection for digital image based on joint DWT-DCT transformation,” International Conference on Wavelet Analysis and Pattern Recognition (ICWAPR), 15-17 July 2012.
- Mohammad Moosazadeh, Azam Andalib, “A new robust color digital image watermarking algorithm in DCT domain using genetic algorithm and coefficients exchange approach,” Second International Conference on Web Research (ICWR), 27-28 April 2016.
- Anita, Archana Parmar, “Image security using watermarking based on DWT-SVD and Fuzzy Logic,” 4th International Conference on Reliability, Infocom Technologies and Optimization (ICRITO) (Trends and Future Directions), 2-4 Sept. 2015.
- Ahmed Al-Gindy, Amaia Mendez Zorrilla, Bassam Beyrouti, “DCT Watermarking Technique Using Image Normalization” International Conference on Developments of E-Systems Engineering (DeSE), 13-14 Dec. 2015.
- Hsin-Lung Wu, Jen-Chun Chang, Te-Chih Chou, Wei-Ming Lai, “A New Scheme for Data Hiding on Halftone Images,” Fifth International Conference on Genetic and Evolutionary Computing (ICGEC), 29th Aug.-1 Sept. 2011.
- M.El Hajji, H. Douzi, D. Mammass, R. Harba, “A robust wavelet-based watermarking algorithm using mixed scales,” International Conference on Multimedia Computing and Systems (ICMCS), 7-9 April 2011.
- Jitendra Saturwar, D.N. Chaudhari, “Secure visual secret sharing scheme for color images using visual cryptography and digital watermarking,” Second International Conference on Electrical, Computer and Communication Technologies (ICECCT), 22-24 Feb. 2017.
- Amir Anees, Adil Masood Siddiqui, “A technique for digital watermarking in combined spatial and transform domains using chaotic maps,” 2nd National Conference on Information Assurance (NCIA), 11-12 Dec. 2013.
- Saurabh Maheshwari, Reena Gunjan, Vijay Laxmi, Manoj S. Gaur, “Robust multi-modal watermarking using visually encrypted watermark,” 19th International Conference on Systems, Signals and Image Processing (IWSSIP), 11-13 April 2012.
- Kazuki Yamato, Madoka Hasegawa, Yuichi Tanaka, Shigeo Kato, “Digital image watermarking method using between-class variance,” 19th IEEE International Conference on Image Processing (ICIP), 30 Sept.-3 Oct. 2012.
- R. Mothi, M. Karthikeyan, “A wavelet packet and fuzzy based digital image watermarking,” IEEE International Conference on Computational Intelligence and Computing Research (ICCIC), 26-28 Dec. 2013.
- Meeta Malonia, Surendra Kumar Agarwal, “Digital Image Watermarking using Discrete Wavelet Transform and Arithmetic Progression technique,” IEEE Students' Conference on Electrical, Electronics and Computer Science (SCEECS), 5-6 March 2016.
- Yanxia Zhao, Zenghui Zhou, “Multipurpose Blind Watermarking Algorithm for Color Image Based on DWT and DCT,” 8th International Conference on Wireless Communications, Networking and Mobile Computing (WiCOM), 21-23 Sept. 2012.
- Rohit M. Thanki, Komal R. Borisagar, “Compressive Sensing Based Multiple Watermarking Technique for Biometric Template Protection,” IJIGSP Vol.7, No.1, Dec. 2014a, 53-60.
- Ruisong Ye,Leyi Zhuang, “Baker Map's Itinerary Based Image Scrambling Method and Its Watermarking Application in DWT Domain,” IJIGSP Vol.4, No.1, Feb. 2012, 12-20.
- Shubhendu Banerjee, Sayan Chakraborty, Nilanjan Dey, Arijit Kumar Pal, Ruben Ray, “High Payload Watermarking using Residue Number System ,” IJIGSP Vol.7, No.3, Feb. 2015, 1-8.
- http://tabby.vision.mcgill.ca/html/browsedownload.html


