A Novel Image Encryption Scheme Based on Multi-orbit Hybrid of Discrete Dynamical System
Автор: Ruisong Ye, Huiqing Huang, Xiangbo Tan
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 10 vol.6, 2014 года.
Бесплатный доступ
A multi-orbit hybrid image encryption scheme based on discrete chaotic dynamical systems is proposed. One generalized Arnold map is adopted to generate three orbits for three initial conditions. Another chaotic dynamical system, tent map, is applied to generate one pseudo-random sequence to determine the hybrid orbit points from which one of the three orbits of generalized Arnold map. The hybrid orbit sequence is then utilized to shuffle the pixels' positions of plain-image so as to get one permuted image. To enhance the encryption security, two rounds of pixel gray values' diffusion is employed as well. The proposed encryption scheme is simple and easy to manipulate. The security and performance of the proposed image encryption have been analyzed, including histograms, correlation coefficients, information entropy, key sensitivity analysis, key space analysis, differential analysis, etc. All the experimental results suggest that the proposed image encryption scheme is robust and secure and can be used for secure image and video communication applications.
Chaotic dynamical system, generalized Arnold map, tent map, shuffling, diffusion
Короткий адрес: https://sciup.org/15014695
IDR: 15014695
Текст научной статьи A Novel Image Encryption Scheme Based on Multi-orbit Hybrid of Discrete Dynamical System
Published Online October 2014 in MECS DOI: 10.5815/ijmecs.2014.10.05
Chaos refers to a kind of pseudo-random irregular movement occurring in a certain dynamical system. Chaotic phenomenon was found by Lorenz, an American meteorologist, in the study of weather problems. Lorenz found the so-called butterfly effect, i.e., the properties of sensitivity to initial conditions in the study of weather forecast through numerical experiments over a long period of time. Loren is now called father of chaos thanks to his contribution to the study of chaotic motion in the deterministic system. Chaotic system is a complex nonlinear dynamic system, which has some fantastic characteristics, such as orbit inscrutability, sensitivity to initial conditions and control parameters, pseudorandomness, topological transitivity, etc. Chaotic system has been widely applied in many disciplines, such as mathematics, physics, biology, computer, finance and even arts. Especially chaotic system has become a very important tool in the field of information security. It has been successfully introduced to modern cryptography thanks to its fantastic chaotic features meeting the fundamental requirements such as mixing and diffusion in the sense of cryptography. Meanwhile, digital multimedia data is being stored on different media, increasingly shared and communicated over the Internet and wireless networks nowadays. Protection of digital information against illegal usage becomes extremely necessary and urgent. It is well known that digital images possess some intrinsic features, such as bulk data capacity, high correlation among adjacent pixels, and human visual properties. As a result, traditional encryption algorithms, such as DES, RSA [1], are thereby not suitable for practical digital image encryption due to the weakness of low-level efficiency while encrypting images. All these factors make chaotic system a potential candidate for constructing cryptosystems, and thereby many chaosbased image cryptosystems have been proposed [2-15].
In this paper, we propose an image encryption scheme based on hybrid orbit of discrete dynamical chaotic system. The adopting of hybrid orbit of chaotic system can enlarge the key space greatly and therefore enhance the security compared with the conventional image encryption based on single orbit of dynamical system. Given three initial states, the generalized Arnold map is used to generate three orbits. Tent map is applied to generate one pseudo-random sequence to determine the hybrid orbit points from which one of the three yielded orbits. Based on the hybrid sequences derived by the hybrid orbit, we design an image encryption scheme with plain-image dependent key stream. The proposed scheme applies different key streams when encrypting different plain-images (even with the same hybrid chaotic sequences). To make the proposed scheme resist differential analysis attack, we perform one diffusion process with two rounds of diffusion operation which depends on both the cipher keys and the plain-image. The diffusion process can modify the pixel values and break the correlations between adjacent pixels of an image simultaneously. The security and performance analysis of the proposed image encryption are carried out using the histograms, correlation coefficients, information entropy, key sensitivity analysis, differential analysis, key space analysis, etc. All the experimental results show that the proposed image encryption scheme is highly secure and excellent performance, which makes it suitable for practical application.
The rest of the paper is organized as follows. In Section II, we briefly introduce the generalized Arnold map and tent map and discuss their chaotic natures. The hybrid sequence derived from multiple orbits of generalized Arnold map is outlined as well. Section III devotes to designing the image encryption scheme. One shuffling stage and one diffusion stage are presented to encrypt images. In Section IV, we present the results of security and performance analysis of the proposed image encryption scheme using the histograms, correlation coefficients, information entropy, key sensitivity analysis, differential analysis, key space analysis, encryption rate analysis, etc. Section V concludes the paper.
-
II. Chaotic Dynamical Systems
Skew Tent map is defined by
| zn / a, n+1 1(1 - zn ) / (1 - a ),
0 ^ z n ^ a;
a < z n ^ 1;
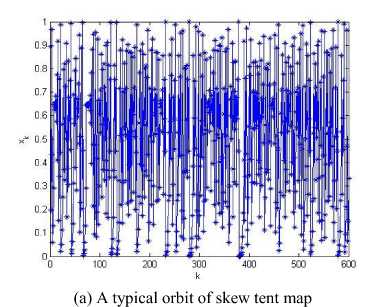
where a e (0,1) is the control parameter, zn , zn+ j e [0,1] are the states. It is a noninvertible transformation of the unit interval onto itself. The transformation is continuous and piecewise linear. Note that the slope of the left branch is 1 / a > 1 and the slope of the right branch is - 1 / (1 - a ) <- 1. A typical orbit of x0 = 0.49 derived from the dynamical system is { xk = Tk ( x 0) , k = 0 , 1,- •} , which is shown in Fig. 1(a), for a = 0 . 45. Its waveform is quite irregular and indicates that the system is chaotic. For any a e (0 , 1), the piecewise linear map (1) has a Lyapunov exponent - a ln a - (1 - a )ln(1 - a ) , which is larger than 0, also implying that the map is chaotic. So the control parameter a and the initial condition x can be regarded as cipher keys. There exist some good dynamical features in the skew tent map. It has been verified that the density p(x ) of the skew tent map is the same as the regular tent map [16],
( 1 , if x e (0 , 1) , p ( x ) = <
-
1 0 , otherwise .
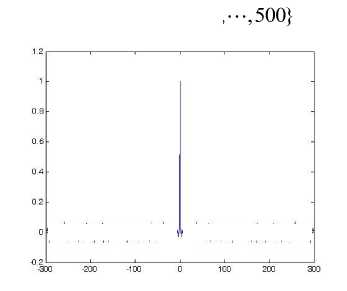
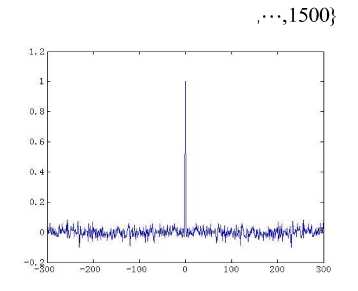
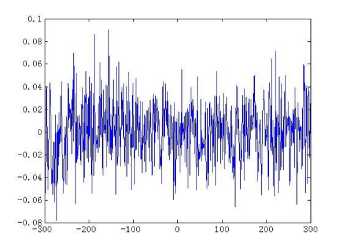
The distribution of the points {xk : k = 0,1,-••, 6000} of a typical orbit of length 6000 is represented by the histogram of Fig. 1(b). It can be seen that the points of the orbit spread more or less evenly over the unit interval in the course of time. Skew tent map also possesses desirable auto-correlation and cross-correlation features, i.e., the auto-correlation function has the characteristics of 5 function and the cross-correlation owns the nature of zero function. The iterated trajectories are used to calculate the correlation coefficients, which are shown in Figs. 1(c)-(d) respectively.
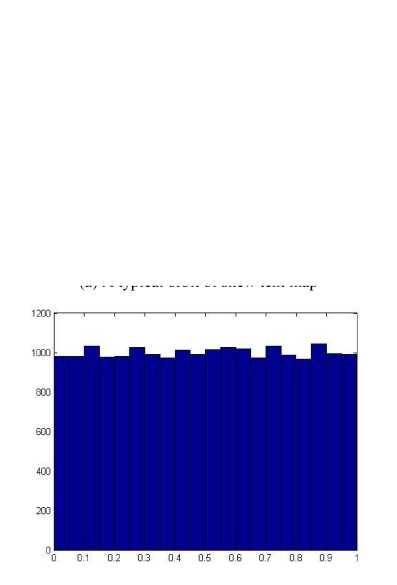
(b) Histogram of a typical orbit of length 6000
100 200 300
-300 -200 -100
(c) Auto-correlation
(d) Cross-correlation
Fig. 1. The chaotic nature of skew tent map
The pseudo-random sequence derived by the skew tent map is processed to generate another pseudo-random integer sequence composed of 1, 2, 3, which will be applied to randomly select orbits of generalized Arnold map. The quantized sequence is calculated by tn = floor(zn x 3) +1, tn e {1,2,3} (2)
l?":*i*;vy^
Arnold map is a two-dimensional invertible chaotic map introduced by Arnold and Avez [17]. It is described by
^<«
1 1 If ^ )
1 2 Л У п J
mod 1
where “ x mod 1 ” means the fractional part of a real number x by adding or subtracting an appropriate integer. Therefore ( xn , yn ) is confined in the unit square [0,1) 2 . The classical Arnold map (3) can be generalized to the following form by introducing two positive real control parameters p >0 and q >0,
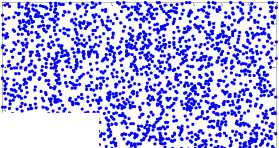
(a) The orbit of (0.5231, 0.7412)
0.9 1
x n + i )f 1 p Y x n ) mod 1. .У п + 1 J I q 1 + pq JI У п J
The generalized Arnold map (4) has one Lyapunov characteristic exponent 1+pq+ p 2 q 2+4 pq , so the map is
^ 2
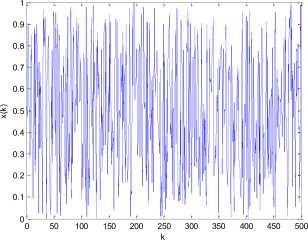
always chaotic for p >0 , q > 0 . The extension of p , q from positive integer numbers to positive real numbers is an essential generalization of the control parameters in conventional generalized Arnold maps, which enlarges the key space significantly. Fig. 2(a) shows an orbit of ( x 0, y0 ) = ( 0.5231,0.7412 ) with length 1500 derived by the generalized Arnold map (2) with p =5.324, q =18.2 , the x-coordinate and the y-coordinate sequences of the orbit are plotted in Fig. 2 (b) and Fig. 2(c) respectively. Some other good dynamical features in the generalized Arnold map, such as desirable auto-correlation and crosscorrelation features are demonstrated in Figs. 2(d)-(f). The good chaotic nature makes it can provide excellent random sequence, which is suitable for designing cryptosystem.
To get one hybrid orbit, we define the following generalized Arnold map with three initial states
(b) Sequence { xk , k = 0, • • •, 500}
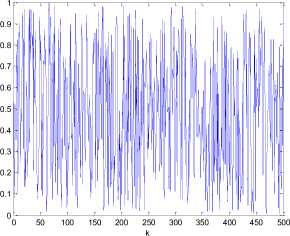
(c) Sequence { yk, k = 0,
M^*w^
*№f*^
'n + 1 || 1 p || x n I
| = | | x| | mod 1, i = 1,2,3 ,
/ 1 I q 1 + pq I у1 ) n + 1 y n J
where ( x\ , y i ) e [0,1), p , q are positive real numbers. Choose three initial state values ( x i , y i ), i = 1,2,3 and apply system (5) to generate three orbits, ( xi , yi ) stands for n th point on the i th orbit. Control parameters p , q and initial values ( x^ , y i ), i = 1,2,3 can be regarded as cipher keys. Therefore the key space enlarges greatly compared with the single orbit case.
(d) Auto-correlation of { xk , k = 0,
(e) Auto-correlation of { yk , k = 0, • • - ,1500}
(f) Cross-correlation of x and y sequences
Fig. 2. Chaotic natures of the generalized Arnold map with p = 5.324, q = 18.2
-
III. The Proposed Image Encryption Scheme
The orbit of generalized Arnold map will be ergodic over the unit square [0,1)2 and therefore we can apply it to design shuffling process of cryptosystem. The pseudorandom sequence generated by generalized Arnold map should be quantized to yield integer coordinates (px, py): px = floor (xn X M) +1, py = floor (yn X N) +1, where (Xn, Уп) is one of (хП, уП )(i = 1,2,3), floor (x) returns the largest integer not larger than x , which makes px,py belong to [1,2,...,M] and [1,2,...,N] respectively. The pseudo-random sequence {t } is used to select the t th orbit point and to form one hybrid orbit {(xn,yn),n = 0,1,-•} . The hybrid orbit possesses better chaotic natures and will enhance the cryptosystem security.
Suppose the plain-image I is a gray image with 256 gray scale levels and with size M x N . We firstly describe some notations for the variables and their values. The control parameter and initial value for skew tent map are a = 0.37, z0 = 0.49 respectively. The parameter and initial values for generalized Arnold map are p = 13.1, q = 33.7 ,
X = ( x ^ , x 0 2 , x 3 ) = [0.31,0.57,0.86], Y = ( У 0 , У 2 , У 3 ) = [0.61,0.32,0.47].
The transient iterated point number is L and the total ergodic orbit point number is N . The corresponding ergodic point number belonging to the i th orbit is denoted by T (i ), i = 1,2,3 with initial values
T (1) = T (2) = T (3) = 0. T ( i ) is increased by 1 if the i th orbit is iterated once. The total N ergodic points on the hybrid orbit distribute over the three orbits, therefore
No = T (1) + T (2) + T (3) at last. Two vectors xend, yend with length 3 are used to record the x -coordinate and y -coordinate of the three current orbit points, they are temporary variables. k is used to record the point number of the hybrid orbit. Matrix index sized M x N and initialized to be zero matrix is one index matrix, whose element values are 0 or 1; index (px, py) = 1 if the pixel at position (px, py) is ergodic, and otherwise index (px, py) = 0 . Variable total denotes the number of unrepeated ergoic points. Vector IC with length L is employed to place the gray values of shuffled image. Another vector C of length L is used to put the gray values of cipher-image.
-
A. The Shuffling Process
Step 1. Read the plain-image I . Set the values for a , z0 p , q , X , Y , No L^ . Iterate (1) to get one vector { zn : n = 0,1, •••, N o + L o} , discard the first L o transient points and get { zn : n = L o + 1,• • •, N o + L o} . For the sake of convenience, we still denote it as { zn : n = 1,--*, N o} . Then apply (2) to quantize it to obtain one integer sequence {f : n = 1,- • •, N o}. The generalized Arnold map (5) is utilized to iterate L times for the three orbit and discard these L transient points to get rid of the harmful transient effect of chaotic system. The values of ( x1^ , y1^ )( i = 1,2,3) are then set to be the initial values of the three orbit to yield the hybrid orbit and set xend ( i ) = x i o, yend ( i ) = y io , k = 1 .
Step 2. Calculate the next point of the t th orbit of the system (5). That is, iterate ( x‘k) + t ( t k ) , y^ + t ( tk ) ) = ( xend (t k ), yend(t k )) to get (^ + t ( t k ) + 1 , y^ + t ( t k ) + 1 ) . Set ( xk , yk ) = ( x L 0 + T ( tk ) + 1 , y L + T ( tk ) + 1 ) , T(t k ) = T(t k ) + 1, k = k + 1 , ( xend(tk ), yend(tk )) = ( xk , yk ) ,
( px , py ) = ( floor ( xend ( tk ) x M ) + 1, floor ( yend ( f ) x N ) + 1) .
If index ( px , py ) =1, then repeat Step 2, otherwise go to Step 3.
Step 3. Excute total = total +1, index (px, py) = 1, IC (total) = mod(I(px, py) + px x py, 256) .
Return to Step 2, until k = N o.
Step 4. Check the remainder pixels which are not ergodic and perform the following code.
If index(i, j) = 0,i = 1,---,M; j = 1,---,N , then set total = total +1, index ( px, py) = 1,
IC ( total ) = mod( I (i , j ) + i x j , 256).
-
B. The Diffusion Process
Step 5. Quantize the pseudo-random sequence { zn : n = 1<--,L } to get one pseudo-random gray value sequence { m(i ) : i = 1,-• •, L } , m ( i ) = floor ( z . x 256) .
Step 6. Set i = 1 and encrypt the first pixel of shuffled image by
C(i) = IC(i)©(mod(C0 + m(i),256)©m(i)) , where C0 is a constant and can be regarded as cipher key. In the experiment, we set C0 = 139. Operation “ © ” stands for the bitwise XOR Operation. Function mod(x, y) represents modular operation.
Step 7. Set i = i + 1 and calculate the gray value of the i th pixel by
C (i ) = IC ( i ) © (mod( C (i - 1) + m(i ), 256) © m(i - 1))
until i = L .
Step 8. To get more efficient diffusion effect, we perform the second round of diffusion. Set i = 1 and execute
C(i ) = C ( i ) © (mod( C ( L ) + m(i ), 256) © m(i )) .
Step 9. Set i = i + 1 and calculate
C(i) = C(i) © (mod(C(i -1) + m(i), 256) © m(i -1)) , until i = L .
Step 10. Convert the vector C to one 2D matrix I 1 with sized M x N ; 1 1 is the cipher-image.
We note that the encryption process is invertible and so the decryption process is just the reverse of the encryption process.
-
IV. Performance and Security Analysis
An ideal encryption cryptosystem requires sensitivity to cipher keys, i.e., the cipher-text should have high correlation with cipher keys [1]. Furthermore, an ideal encryption scheme should have a large key space to make brute-force attack infeasible; it should also well resist various kinds of attacks like statistical attack, differential attack, etc. Some security analysis will be performed on the proposed image encryption scheme, including the most important ones like key sensitivity test, key space analysis, statistical analysis, and differential attack analysis. All the analysis shows that the proposed image encryption scheme is highly secure thanks to its high sensitivity of the control parameters and initial conditions of the considered chaotic systems, large key space, and satisfactory diffusion mechanism. Experimental results suggest that the proposed image encryption technique is robust and secure and can be used for the secure image and video communication applications.
-
A. Key Sensitivity Analysis and Key Space Analysis
The key space of an encryption scheme is composed of the total number of different cipher keys that can be used in the encryption procedure. The high sensitivity of the cipher-image to initial conditions and control parameters is inherent to any chaotic system. A good image encryption scheme needs to contain sufficiently large key space for compensating the degradation dynamics in PC. It should be sensitive to cipher keys as well, and thus can effectively prevent invaders decrypting original data even after they invest large amounts of time and resources. The analysis results regarding the sensitivity and the key space are summarized as follows. Since the permutation process is irrelevant to the diffusion process, the key space consists of the cipher keys in both the circular shift scrambling process and the diffusion process.
The cipher keys consist of those keys p , q , x 1 , x 2 , x 3 , y 1 , y 2 , y 3 in the generalized Arnold map and a, z 0 in the tent map. The sensitivity tests with respect to all cipher keys have been carried out. To verify the sensitivity of cipher key K , the original plain-image I = ( I(i . j))MxN is encrypted with K = p , K = p - A K and K = p + A K respectively while keeping the other key parameters unchanged. Here A K is the perturbing value. The corresponding encrypted images are denoted by I , I 2, I3 respectively. The sensitivity coefficient to the cipher key K is then denoted by the following formula
P s ( K ) = o 2 Tv £ [ N s ( 1 1 ( i , j ) , 1 2 ( i , j ))
-
2 x H x W
+ N s ( 1 1 ( i , j ) , I з ( i , j ))] x 100 % ,
N s ( x , y )
I 1 ’ to.
P ( K ) implies the sensitivity to the perturbation of parameter K . Larger P ( K ) implies more sensitive for cipher key K . Table 1 shows the results of the sensitivity tests. The variation A K is set to be 10 - 14 for p , q , 10 - 15 for x j , x 2 , x 3 and 10 - 16 for y 1 , y 2 , y 3 , a , z0 . We apply the proposed image encryption scheme one round with only perturbing one cipher key K with the corresponding variation value while fixing other parameters. The results in Table 1 imply that the control parameters and the initial values are all strongly sensitive. It also implies from the results that the key space is more than (1014)2 x (1015)3 x (1016)5 = 10153 , which is large enough to make brute-force attack infeasible.
The sensitivity tests can also be demonstrated visually from two aspects. One is to show that the cipher-image is strongly sensitive to the cipher key. If the cipher-key is replaced with a minor change, the cipher-image will become almost completely different visually. The other one can be shown by the decrypted image. Minor perturbation for cipher key will result in tremendous change in the decrypted image and one can’t find any hints for the plain-image.
-
(i) Influence of minor change for cipher keys over encryption. We perform three simulations. The plainimage Lena is encrypted by the cipher keys
a = 0.37, z0 = 0.49, p = 13.1, q = 33.7,
( x 0 , x 2 , x 03) = (0.31,0.57,0.86),
( y 0 , y 2 , y 3 ) = (0.61,0.32,0.47).
The plain-image and cipher-image are shown in Figs. 3(a)-(b) respectively. Replace z =0.49 , q =33.7 , y 2 =0.32
by z0 = 0.49 + 10-16 , q = 33.7+10-14 , y 0:=0.30+10-16 respectively, and keep the other cipher keys unchanged, the cipherimages are shown in Figs. 3(c)-(e) respectively. The difference images are Figs. 3(f)-(h).
-
(ii) Influence of minor change for cipher keys over decryption. Replace p = 13.1 by p =13.1+10-14 and keep the other cipher keys unchanged, the decrypted image is shown in Fig. 4(a), which has a difference 99.22% from the plain-image Lena. Replace a = 0.37 by a =0.37+10 -16 and keep the other cipher keys unchanged, the decrypted image is shown in Fig. 4(b), which has a difference 99.59% from Lena. If x = 0.31 is changed to be x 1 =0.31+10-15 , the decrypted image is shown in Fig. 4(c) with a difference 97.84% from Lena.
Table 1. results regarding the sensitivity to cipher keys
|
Key |
p |
q |
1 x 0 |
2 x 0 |
3 x 0 |
|
P s ( K ) |
0.9962 |
0.9958 |
0.9963 |
0.9958 |
0.9961 |
|
Key |
a |
z 0 |
y 10 |
y 02 |
y 03 |
|
P s ( K ) |
0.9962 |
0.9962 |
0.9962 |
0.9959 |
0.9960 |

(a) Plain-image Lena (b) Cipher-image

(c) Cipher-image by z o = 0.49 + 10 16

(d)Cipher-image by q = 33.7+10-14

(e)Cipher-image by y 2 =0.32+10-16
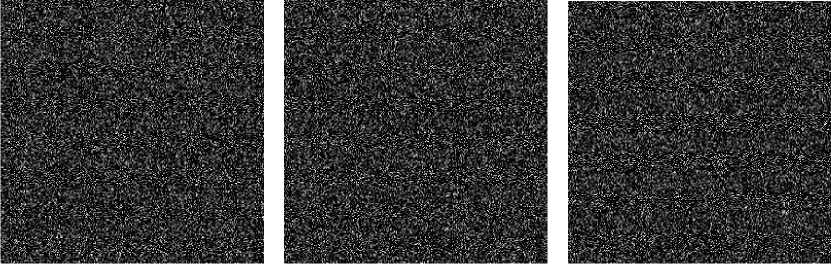
(f) Difference image between (b) and (c) (g) Difference image between (b) and (d) (h) Difference image between (b) and (e)

Fig. 3. Key sensitivity tests I.


( c ) Decrypted image by x 1 =0.31+10-15
(a) Decrypted image by p =13.1+10 1 (b) Decrypted image by a =0.37+10 16
Fig. 4. Key sensitivity test II.
-
B. Statistical Analysis
Shannon pointed out the possibility to solve many kinds of ciphers by statistical analysis in his masterpiece [18]. Therefore, passing the statistical analysis on cipherimage is of crucial importance for a cryptosystem. Indeed, an ideal cryptosystem should be robust against any statistical attack. In order to prove the security of the proposed encryption scheme, the following statistical tests are performed.
-
(i) Histogram. Encrypt the plain-image Lena one round, and then plot the histograms of plain-image and cipherimage as shown in Figs. 5(a)-(b), respectively. Fig. 5(b) shows that the histogram of the cipher-image is fairly uniform and significantly different from the histogram of the original plain-image and hence it does not provide any useful information for the opponents to perform any statistical analysis attack on the encrypted image.
-
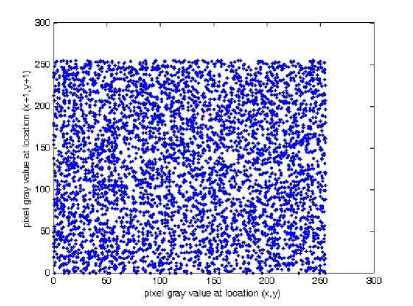
(ii) Correlation of adjacent pixels. To test the correlation between two adjacent pixels, the following performances are carried out. First, we select 3000 pairs of two adjacent pixels randomly from coefficient of the selected pairs using the following formulae:
Cr= cov ( x , y )
VD (x) D (y),
1T cov (x, y )= E( x- E (x))(y - E (y)),
T I = 1
TT
E (x )= E x, D (x ) = E( x- E (x)) ,
T 1=1 T i=i where x, yare the gray-scale values of two adjacent pixels in the image and T is the total pairs of pixels randomly selected from the image. The correlations of two adjacent pixels in the plain-image and in the cipherimage are shown in Table II. The correlation distribution of two adjacent pixels in the plain-image and that in the cipher-image are shown in Fig. 6.
-
(iii) Information entropy analysis. The entropy is the most outstanding feature of randomness. Therefore, it is generally used to measure the strength of the cryptosystem. The entropy H ( m ) of a message source can be measured by
L - 1
H (m) = -E p (mi) log ( p (m-)) i=0
where L is the total number of symbols m , p ( m ) represents the probability of occurrence of symbol m and log denotes the base 2 logarithm so that the entropy is expressed in bits. Considering a random source with 256 outcomes, sharing equal probability, its entropy is equal to 8. Under the proposed cryptosystem, the entropy of encrypted image of Lena is 7.9971 bits while the entropy of plain-image Lena is 7.3507. According to this result, the cipher-image is close to a random source and the proposed algorithm is secure against the entropy attack.
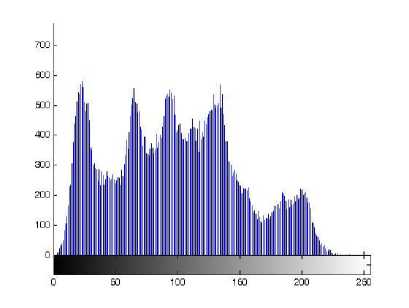
(a) Histogram of plain-image Lena
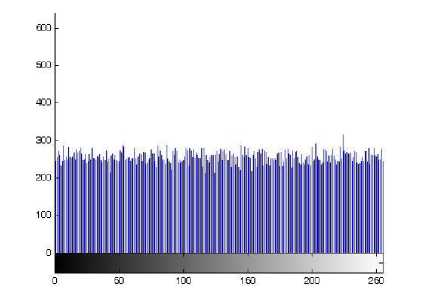
(b) Histogram of cipher-image
Fig. 5. The histograms of plain-image and cipher-image
Table 2. Correlation coefficients of plain-image and cipher-image.
|
Horizontal |
Vertical |
diagonal |
|
|
Plain-image lena |
0.9395 |
0.9689 |
0.9184 |
|
Cipher-image |
0.0052 |
-0.0042 |
0.0141 |
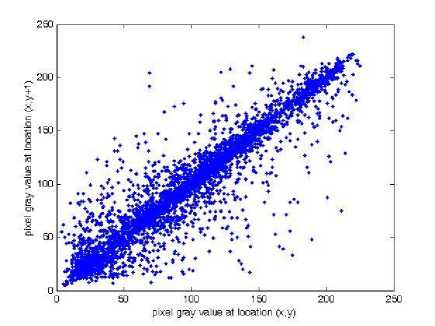
(a)
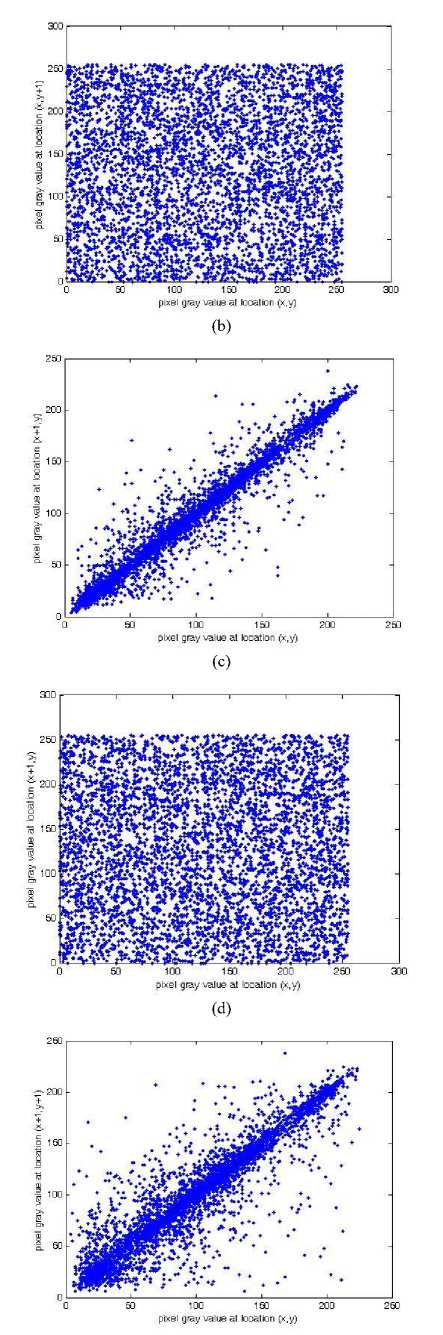
(e)
(f)
Fig. 6. Correlations of two adjacent pixels in the plain-image and in the cipher-image: (a), (c), (e) are for the plain-image; (b),(d),(f) are for the cipher-image
and cipher-image can be found in such analysis, which may further facilitate the opponents to determine the cipher key. If one minor change in the plain-image will cause significant, random and unpredictable changes in the cipher-image, then the encryption scheme will resist differential attack efficiently. To test the influence of only one-pixel changed in the plain-image over the whole cipher-image, two common measures, namely number of pixels change rate (NPCR) and unified average changing intensity (UACI), are evaluated by
NPCR = —1— У D ( i , j ) x 100%,
M x Ny
UA CI =-----1-----УI C ( i , j ) - C ( i , j )| x 100%
M x N x 255 t"j 1 2
-
C. Peak Signal-to-noise Ratio Analysis
Another parameter to describe the encryption quality is the peak signal-to-noise ratio (PSNR). This term is described based on that the mean squared error (MSE) is calculated. This criterion provides the error between input image and output image. The MSE value is
Г 1 MN ,1 1/2
MSE = -- У УГ IqV , j - IeV , j Л ,
I m x n £ tTL O ( ) E ( ,A I where Io (i, j) is the pixel value of plain-image, IE (i, j) is the pixel value of cipher-image. Thus the PSNR is described by where C and C are the two cipher-images corresponding to two plain-images with only one pixel difference, and D(i, j) is defined by
Г 1, c 1 ( i , j ) * c 2 ( i , j ),
D ( i , J ) =I
[ 0, otherwise.
NPCR measures the percentage of different pixels numbers between the two cipher-images whose plainimages only have one-pixel difference; UACI measures the average intensity of differences between the two cipher-images. They indicate the sensitivity of the cipherimages to the minor change of plain-image.
The NPCR for two random images, which is an expected estimate for an ideal image cryptosystem, is given by
PSNR = 20log
I max
MSE
where I is the maximum of pixel value of the image. The PSNR should be a low value, which corresponds to great difference between the original image and the encrypted image. To determine the encryption quality, the PSNR for the encryption of Lena is 8.5508. The calculated PSNR value is very low. Therefore, the encryption quality is good in sense of PSNR test.
D. Differential Analysis
The differential cryptanalysis of a block cipher is the study of how differences in a plaintext can affect the resultant differences in the ciphertext with the same cipher key. It is usually done by implementing the chosen plaintext attack but now there are extensions which use known plaintext as well as ciphertext attacks also. As for image cryptosystems, attackers may generally make a slight change (e.g., modify only one pixel) of the plainimage, and compare the two cipher-images (obtained by applying the same cipher key on two plain-images having one pixel difference only) to find out some meaningful relationships between the plain-image and the cipherimage. If a meaningful relationship between plain-image
NPCRExpected = (1 - 2-L ) x100%, where L is the number of bits used to represent all the gray values of the considered image. For a 8-bit gray scale image L , hence NPGR^cted = 99.6094% . The UACI for two random images, which is an expected estimate for an ideal image cryptosystem, is given by
UACI
Expected
22 L
z 2 L ;1 i ( i + 1)
2 L - 1
x 100%.
For a 8-bit gray image, UAGI Expect ed = 33.4635% .
To resist difference attacks, the values of NPCR and UACI should be close to the expected values. We randomly select 100 pixels and change the gray values with a difference of 1. The numerical results are shown in Fig. 7. The mean values of 100 NPCR and UACI values are 99.6015% and 33.4978% respectively. They are almost the same as the corresponding expected values. We can observe from Fig. 7 that the two measure values are exceptionally good undergoing only one round of encryption.
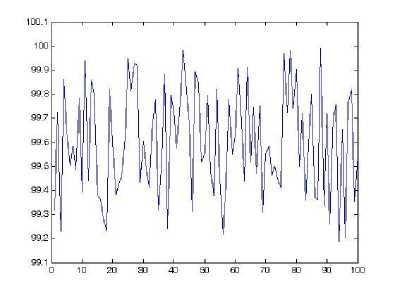
(a) NPCR values
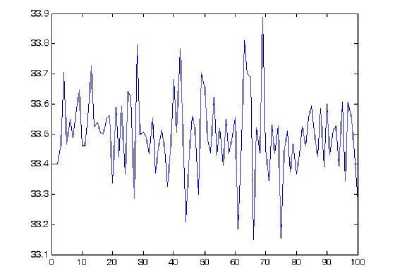
(b) UACI values
Fig. 7. The differential analysis results.
-
V. Conclusions
A novel image encryption scheme based on multi-orbit hybrid of chaotic system is proposed in the paper. The proposed encryption scheme enhances the security compared with conventional image encryption schemes based on singe orbit in the sense that multi-orbit hybrid can enlarge the cipher key space greatly. The proposed image encryption scheme consists of one shuffling stage and one diffusion stage. The shuffling process utilizes the ergodicity of chaotic system and gets good shuffling effect. The diffusion process adopts two rounds of diffusion operation to achieve efficient diffusion effect. Security analyses including key sensitivity analysis, key space analysis, statistical analysis, differential analysis and information entropy analysis are performed. All the experimental results demonstrate that the proposed image encryption scheme possesses large key space to frustrate brute-force attack efficiently and can resist statistical attack, differential attack, etc.
Huiqing Huang was born in 1981 and received the Master degree in Applied Mathematics in 2009 from Shantou University, Shantou, Guangdong, China. He is now a lecturer, at School of Mathematics, Jiaying University, Meizhou,
Guangdong, 514015, China. His research field is fractal, chaos and their applications in information security.
Xiangbo Tan: graduate student at department of mathematics in Shantou University, His research field is chaotic dynamical system and its application in information security.
Список литературы A Novel Image Encryption Scheme Based on Multi-orbit Hybrid of Discrete Dynamical System
- B. Schiener. Applied Cryptography: Protocols, Algorithms and Source Code in C[M], John Wiley and sons, New York, 1996.
- J. Fridrich, Symmetric ciphers based on two-dimension chaotic map [J]. International Journal of Bifurcation and chaos, 1998,8(6):1259-1284.
- F. Huang, Z.-H. Guan, A modified method of a class of recently presented cryptosystems, Chaos, Solitons and Fractals, 23(2005), 1893–1899.
- R. Ye, A novel chaos-based image encryption scheme with an efficient permutation-diffusion mechanism, Optics Communications, 284(2011), 5290–5298.
- N. K. Pareek, V. Patidar, K. K. Sud, Image encryption using chaotic logistic map, Image and Vision Computing, 24(2006), 926-934.
- N. Masuda, K. Aihara, Cryptosystems with discretized chaotic maps, IEEE Trans. Circuits Syst. I, 49(2002), 28–40.
- H. Liu, X. Wang, Color image encryption using spatial bit-level permutation and high-dimension chaotic system, Optics Communications, 284(2011), 3895–3903.
- S. Behnia, A. Akhshani, S. Ahadpour, H. Mahmodi, A. Akhavan, A fast chaotic encryption scheme based on piecewise nonlinear chaotic maps, Phys. Lett. A, 366(2007), 391–396.
- S. Lian, J. Sun, Z. Wang, A block cipher based on a suitable use of the chaotic standard map, Chaos, Solitons and Fractals, 26 (2005), 117–129.
- V. Patidar, N. K. Pareek, K. K. Sud, A new substitution–diffusion based image cipher using chaotic standard and logistic maps, Communications in Nonlinear Science and Numerical Simulation, 14 (2009), 3056–3075.
- N. Masuda, K. Aihara, Cryptosystems with discretized chaotic maps, IEEE Trans. Circuits Syst. I, 49(2002), 28–40.
- S. Behnia, A. Akhshani, S. Ahadpour, H. Mahmodi, A. Akhavan, A fast chaotic encryption scheme based on piecewise nonlinear chaotic maps, Phys. Lett. A, 366(2007), 391–396.
- S. Lian, J. Sun, Z. Wang, A block cipher based on a suitable use of the chaotic standard map, Chaos, Solitons and Fractals, 26 (2005), 117–129.
- L. Kocarev, Chaos-based cryptography: a brief overview, IEEE Circuits and Systems Magazine, 1(2001), 6–21.
- C. Zhu, A novel image encryption scheme based on improved hyperchaotic sequences [J]. Opt. Commun., 2012, 285:29-37.
- M. Hasler and Y. L. Maistrenko, An introduction to the synchronization of chaotic systems: Coupled skew tent map [J], IEEE Transactions on Circuits and Systems, 1997, 44: 856-866.
- V. Arnold, A. Avez, Ergodic problems in classical mechanics [M], Benjamin, New York, 1968.
- C. E. Shannon, Communication theory of secrecy system [J]. Bell Syst. Tech. J, 1949, 28: 656-715.


