A Novel Routing Scheme for Mobile Ad Hoc Network
Автор: Prem Chand, M.K.Soni
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 4 vol.5, 2013 года.
Бесплатный доступ
Mobile Ad hoc Network (MANET) is a collection of mobile users without any support of fixed infrastructure. The nodes in these networks have several constraints such as transmission power, bandwidth and processing capability. In addition to it an important parameter of interest is the residual battery power of the nodes. Conventional routing schemes do not take this aspect into consideration. Therefore this paper proposes a routing strategy that takes this aspect into consideration by modifying the Route Request (RREQ) packet of the Ad hoc On demand Distance Vector (AODV) routing protocol. The protocol chooses a threshold below which a node is not allowed to relay data/control packets. The results show a remarkable improvement in the value of Packet Delivery Ratio (PDR), throughput and at the same time the network lifetime is not affected.
Mobile ad hoc network, routing protocol, AODV, Residual battery power, performance study, packet delivery ratio, average end-to-end delay
Короткий адрес: https://sciup.org/15011179
IDR: 15011179
Текст научной статьи A Novel Routing Scheme for Mobile Ad Hoc Network
Published Online April 2013 in MECS
Mobile Ad hoc Network (MANET) [1-2] is a flexible network that can be setup anytime anywhere without any support of prerequisite infrastructure. Due to its quick deployment and infrastructure less nature these networks have applications in areas such as defense and disaster areas. A routing protocol is used to have multi-hop communication in these networks. The primary goal [3-6] of such a protocol is to deliver the information between a pair of nodes in a timely manner. The routing protocol has several constraints such as dynamic and constantly changing topology, transmission power, bandwidth and processing capability of the nodes.
In addition to above parameters one important aspect that should be taken into consideration is the residual battery [7] powers of the nodes, which may be defined as the remaining power of a node at any particular time. More is the residual battery power more are the chances that the path so chosen is reliable and higher will be the network lifetime. Conventional routing [8-9] protocols do not take this aspect into consideration.
To cope up with this issue we propose a routing strategy that modifies the Route Request (RREQ) packet of the conventional Ad hoc On demand Distance Vector (AODV) [3] protocol. We defined a threshold battery power value and priority of the application which is used as a metric for path selection. A node having low battery power is used as an intermediate node if and only if the priority of the RREQ packet is one (high) else it drops the RREQ packet. In this way the nodes with lesser battery power are avoided from path selection mechanism used in AODV. The rest of the paper is ordered as follows. Section 2 gives the basic working of standard AODV protocol. Section 3 describes the working of the proposed protocol. Section 4 gives the detail of simulation setup. Results of the proposed strategy are being discussed in section 5 followed by concluding remarks in section 6 and at last but not least various references are mentioned.
-
II. Basic working of standard AODV Protocol
This section discusses the conventional AODV [10-12] protocol that is used as our base protocol. The working of the protocol is divided into three below mentioned phases.
-
A. Route Request phase (RREQ)
AODV protocol uses on demand approach for finding routes; consequently a route is established only on its requirement by a source node. The source node broadcasts the route request (RREQ) packet in the network when a route is not present for required destination. The route request packet carries a few network information, some of them are source identifier, broadcast identifier, destination sequence number and time to live (TTL).
-
B. Route Reply phase (RREP)
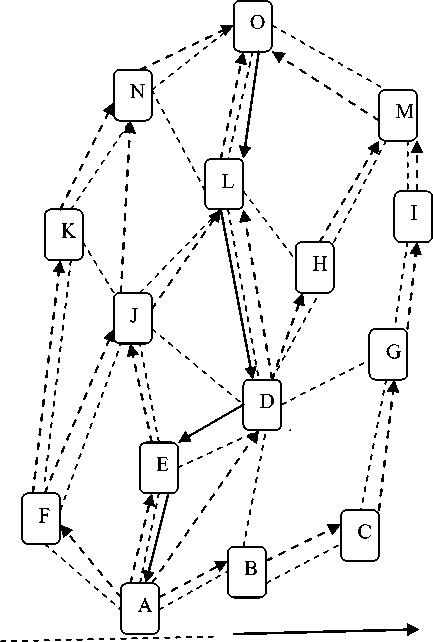
When an intermediate [13-15] node receives a route request, it either forwards it or prepares a route reply, if it has valid route to destination. Figure 1 shows the movement of RREQ and RREP packet from source to destination and destination to source respectively. In this figure source node A starts route finding process by broadcasting RREQ packet in the network for destination node O. If the route request (RREQ) packet reaches the destination node O, through one or other route, the destination O also sends a route reply (RREP) to the source, consequently source may get multiple route reply messages which later on filtered on the basis of their freshness. To conclude, it is the characteristic of AODV protocol that out of various route reply messages received by the source node from destination side, the last message which is fresh enough is being selected for further route to be followed.
-
C. Maintenance phase
AODV protocol does not repair a broken route locally, the route error (RERR) message is sent whenever a link breaks which is determined by the periodically link level acknowledgements observed by source and destination nodes. When a source node came to know about the path breaks, it again reestablishes the route by broadcasting the RREQ packet
Network Link RREP
RREQ
-
Figure 1: Route founding in AODV
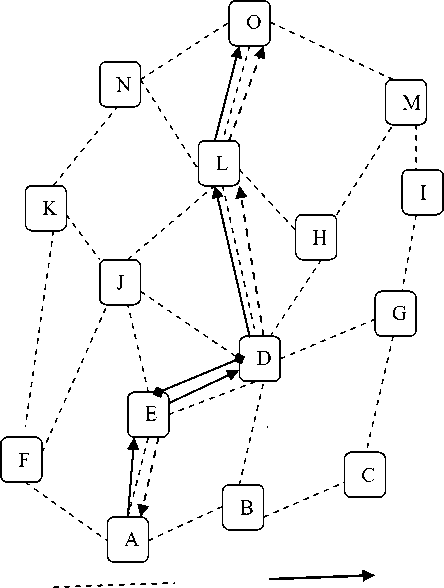
Consider the example shown in figure 2, here as the path breaks between D an E, both the nodes initiates the route error (RERR) message to inform their end nodes about the path break. After getting the RERR message end nodes of both sides delete the related information from their tables (buffer memory). The source node restart the route finding job with new broadcast ID and prior destination sequence number.
-
iii. The Proposal
Before discussing our proposal we would like to give an introduction of the RREQ format [15-20] of the conventional AODV protocol that will help in better understanding of our proposed routing scheme.
-
A. Modification in the RREQ
Figure 3(a) shows the RREQ format of the base protocol. Various fields related to the RREQ format are as follows:
Type : 1 (It give the packet format type).
J : Join flag; reserved for multicast.
R : Repair flag; reserved for multicast.
-
G : Gratuitous RREP flag; indicates whether a
gratuitous RREP should be unicast to the node specified in the Destination IP Address field.
-
D : Destination only flag; indicates only the destination may respond to this RREQ.
U : Unknown sequence number; indicates the destination sequence number is Unknown.
Reserved : Sent as 0; ignored on reception.
Hop Count : The number of hops from the Originator IP Address to the node handling the request.
Network Link Route for A to O
Route Error Broken Link
Figure 2: Route maintenance in AODV
|
Type (8 Bit) |
J |
R |
G |
D |
U |
Reserved (11 Bit) |
Hop Count (8 Bit) |
|
RREQ ID |
|||||||
|
Destination IP Address |
|||||||
|
Destination Sequence Number |
|||||||
|
Originator IP Address |
|||||||
|
Originator Sequence Number |
|||||||
Figure 3 (a) Conventionnel RREQ message format
The format contains eleven unreserved bits as shown in the original format that can be used. Figure 3 (b) shows the modified RREQ format. We have added two extra fields as follows:
P = Instantaneous power level
Pr = Priority
|
Type (8 Bit) |
J |
R |
G |
D |
U |
P |
Pr |
Reserved (9 Bit) |
Hop Count (8 Bit) |
|
RREQ ID |
|||||||||
|
Destination IP Address |
|||||||||
|
Destination Sequence Number |
|||||||||
|
Originator IP Address |
|||||||||
|
Originator Sequence Number |
|||||||||
Figure 3 (b): Modified (Proposed) RREQ format
The instantaneous power (P) is of one bit and is used for representing low/high residual battery power of the node. Each node before Broadcasting a RREQ packet must check its residual battery power (defined as threshold value of battery) status for taking further action as either it is low or high, if low no broadcast else broadcast.
Another field of parity (Pr) in the form of 0/1 for representing low/high is also being added to next reserved bit of RREQ, which shows that the RREQ should not be dropped if its energy is low and priority is high. The proposed strategy will work as per the specifications mentioned in Table 1.
Table 1. Basic functionality of modified reserved bits
|
P |
Pr |
Operation to be performed |
|
0 |
0 |
The node should not broadcast RREQ |
|
0 |
1 |
The node should broadcast RREQ |
|
1 |
0 |
The node should broadcast RREQ |
|
1 |
1 |
The node should broadcast RREQ |
The next section discusses about the simulation set up parameters used for evaluating the efficacy of the proposed protocol.
-
iv. Simulation Setup
This section illustrates the tool used for the proposed routing scheme, various setup parameters, and snapshot that shows the working of modified routing strategy.
-
A. Tool Used
To evaluate the efficacy of the proposed routing scheme the simulation tool used is QualNet 5.2 (evaluation version), with GUI tools for performance comparison of new routing strategy with other conventional routing protocols. The simulator contains standard API for composition of protocols across different layers. QualNet support a wider range of networks and their analysis, some of them are MANET, QoS, Wired Networks, Satellite and cellular.
-
B. Setup Parameters
Table 2 shows the simulation set up parameters used in our proposal.
Table 2. Setup Parameters used
|
Parameter |
Value |
|
Number of Nodes |
40,50,60,70 |
|
Transmission Range |
300-450 |
|
Mobility Model Used |
Random Way Point (RWP) |
|
Placement of Nodes |
Random |
|
Routing Protocol |
AODV,AODV1,DSR,DYMO |
|
Energy Model |
Mica-Motes |
|
Battery Model |
Linear Model |
|
Size of simulation region |
2250000 Sq. Units |
|
Application Layer |
CBR Traffic |
|
Battery Threshold |
2 (mah) |
|
Priority |
0/1 |
|
Simulation Time |
1500 Seconds |
|
Shape of Simulation Region |
Square |
-
C. Snapshots
Figure 4 as shown here is the real print of simulation process.
Figure 4: Snapshot of simulation process
-
v. RESULTS AND ANALYSIS
-
A. Impact and analysis of number of Bytes received
The performance of all routing protocols decreases significantly as the number of selfish nodes increases (as shown in figures (6 to 9)). In the same time the performance of our propose strategy (AODV1_0) in case of AODV1 with priority 0 is nearly same as of DSR till up to 20% concentration of selfish nodes. The performance of AODV1_0 is Comparative higher than
AODV and AODV1_1 (AODV1 with priority 1) since it takes into account the residual battery power of the nodes.
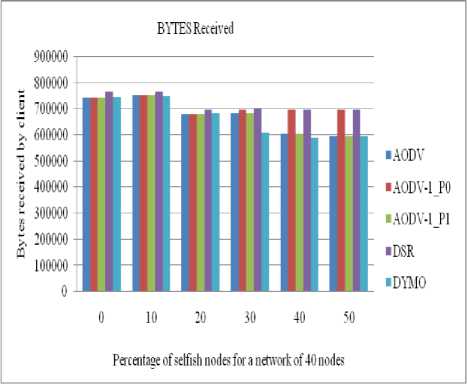
Figure 6: Number of bytes received by a client in a network of 40 nodes
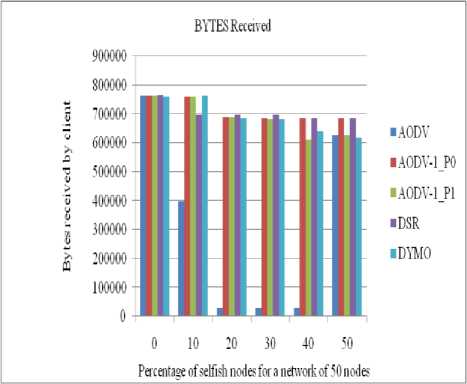
Figure 7: Number of bytes received by a client in a network of 50 nodes
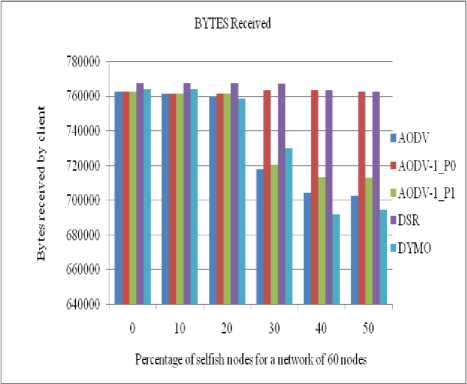
Figure 8: Number of bytes received by a client in a network of 60 nodes
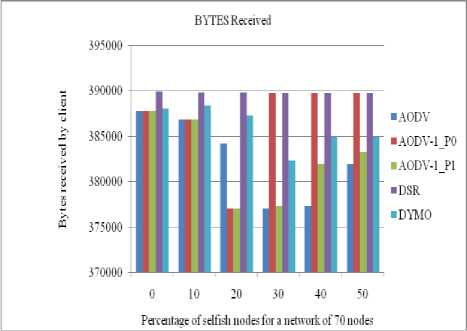
Figure 9: Number of bytes received by a client in a network of 70 nodes
-
B. End to End Delay
Since our protocol takes into account the residual battery power of the intermediate nodes hence the shortest path may or may not be selected therefore end to end delay is higher than its counterpart. Figures 10 to 13 show the comparative end to end delay between nodes for 0 to 50% (with 10% of interval) of selfish nodes for different networks having 40/50/60/70 nodes.
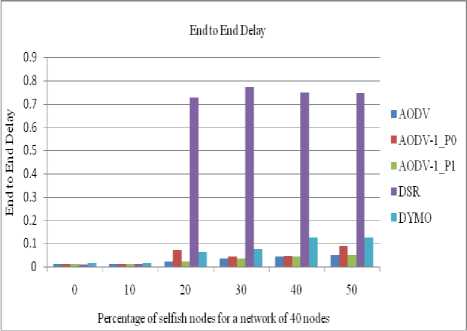
Figure 10: End to End Delay between the nodes in a network of 40 nodes
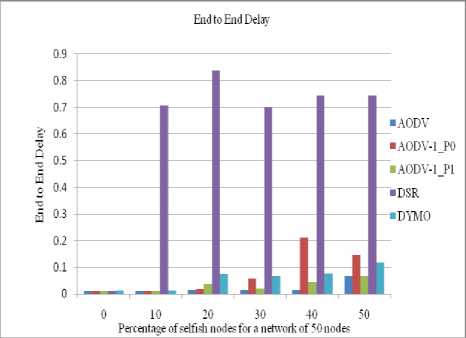
Figure 11: End to End Delay between the nodes in a network of 50 nodes
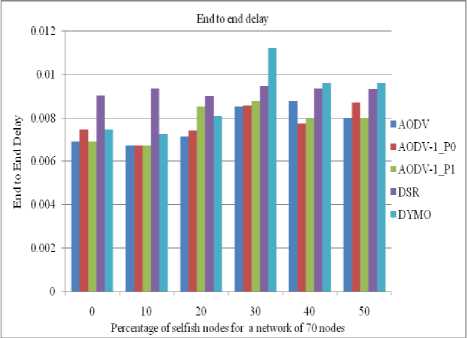
Figure 13: End to End Delay between the nodes in a network of 70 nodes
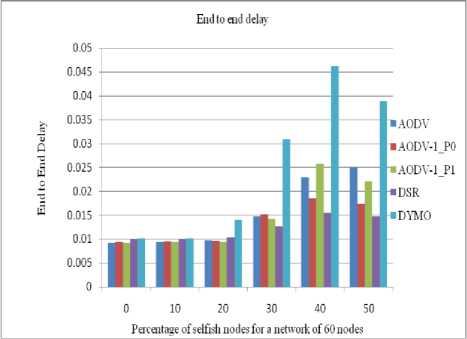
Figure 12: End to End Delay between the nodes in a network of 60 nodes
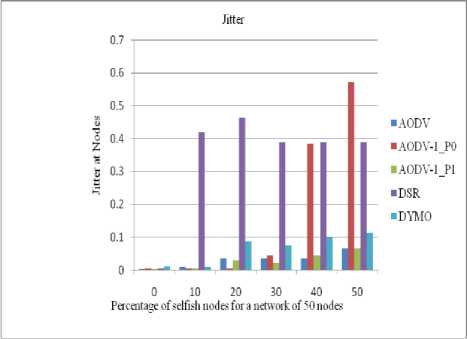
Figure 15: Jitter at the client in a network of 50 nodes
-
C. Jitter
In MANET the value of jitter is much diversified. As there is no regular pattern of jitter, we can’t fix any defined rule for it. Below discussed figures (14 to 17) shows various results of jitter value for different taken scenarios.
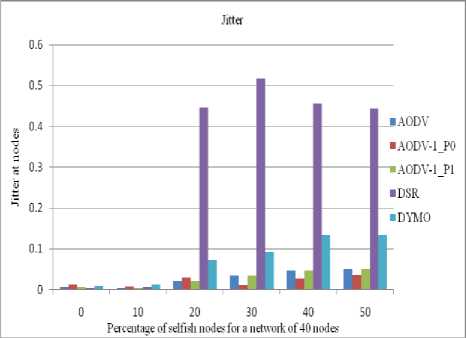
Figure 14: Jitter at the client in a network of 40 nodes
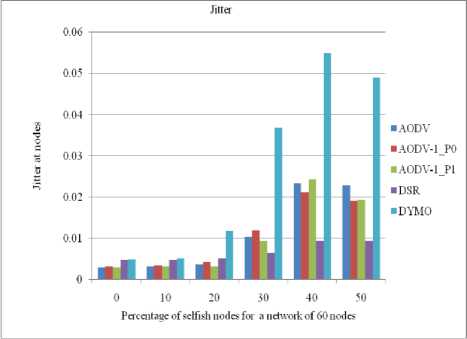
Figure 16: Jitter at the client in a network of 60 nodes
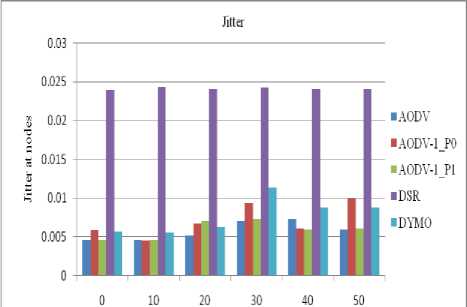
Percentage of selfish nodes f« a network of 70 nodes
Figure 17: Jitter at the client in a network of 70 nodes
-
D. Impact and analysis of number of Packets received
The performance of all routing protocols decreases significantly as the number of selfish nodes increases (as shown in figures 18 to 21). The performance of AODV1_0 (AODV1 in case of priority 0) is nearly same as of DSR till up to 20% concentration of selfish nodes. The performance of AODV1_0 is comparative higher than AODV and AODV1_1 since it takes into account the residual battery power of the nodes.
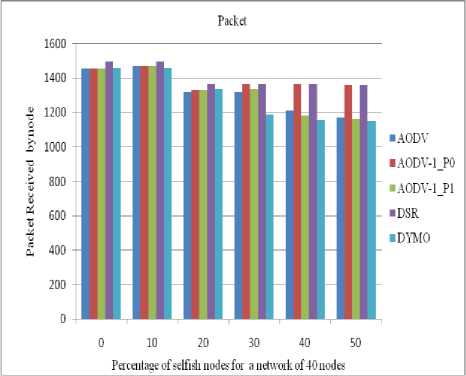
Figure 18: Number of packets received by a client in a network of 40 nodes
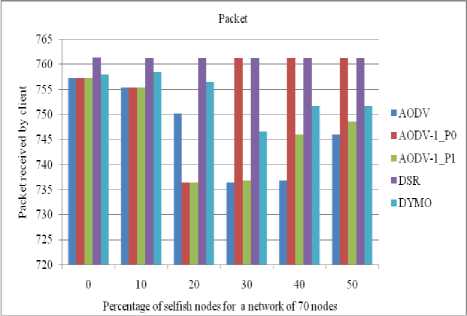
Figure 21: Number of packets received by a client in a network of 70 nodes
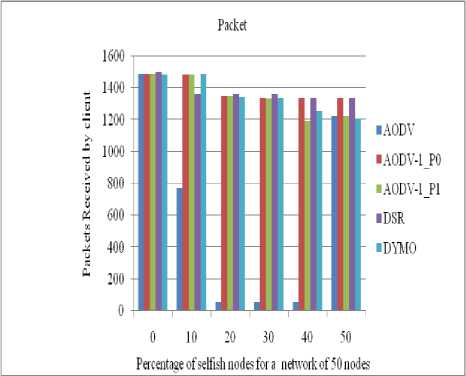
Figure 19: Number of packets received by a client in a network of 50 nodes
-
E. Impact and analysis of Throughput received
The performance of all routing protocols decreases significantly as the number of selfish nodes increases (as shown in figures 22 to 25).The performance of AODV1 in case of priority 0 is nearly same as of DSR till up to 20% concentration of selfish nodes .The performance of AODV1_0 is Comparative higher than AODV and AODV1_1 since it takes into account the residual battery power of the nodes.
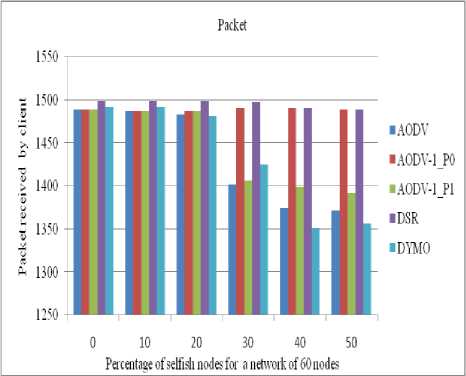
Figure 20: Number of packets received by a client in a network of 60 nodes
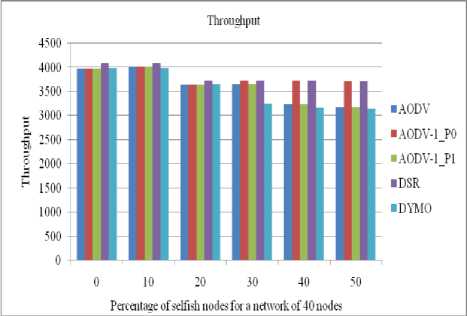
Figure 22: Throughput received by a client in a network of 40 nodes
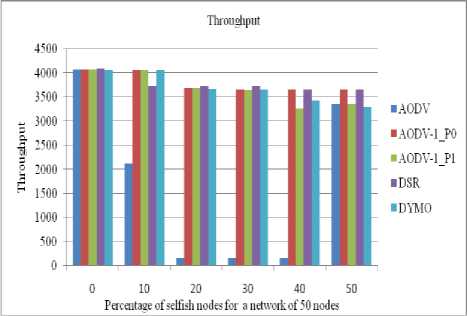
Figure 23: Throughput received by a client in a network of 50 nodes
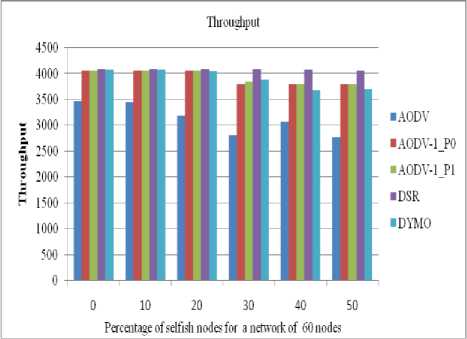
Figure 24: Throughput received by a client in a network of 60 nodes.
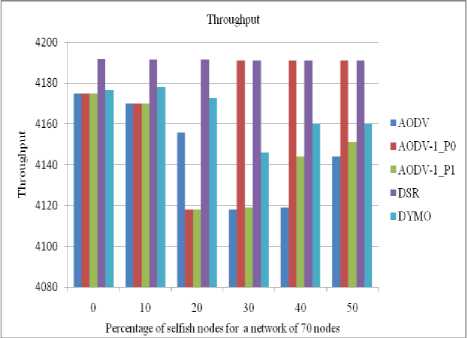
Figure 25: Throughput received by a client in a network of 70 nodes
-
F. Network life time
It is the time in which 10% of the nodes get dead (As in our experiment we have taken ‘k value for network lifetime calculation’ = 0.1)
In our findings the network life time for all routing protocols is same since it mainly depends upon the hello request and reply packets.
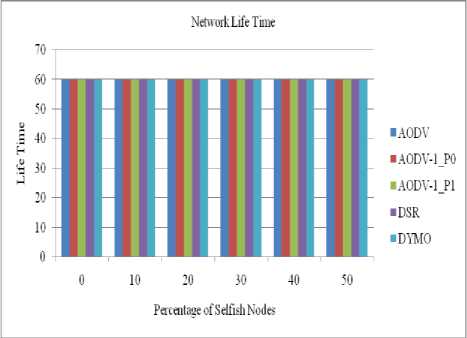
Figure 26: Network life time for a network of 40/50/60/70 nodes
-
VI. Conclusion
The proposed routing scheme simply modifies the RREQ of the conventional AODV protocol. It was seen from the above results that by simply adding two extra fields i.e. p and Pr the performance can certainly be improved. The following points can be inferred from the above results.
-
• The value of PDR, throughput was almost same up till 25% concentration of power deficient nodes of the total nodes. It was also observed that the performance of our routing scheme significantly improves after 25% concentration of power deficient nodes of the total nodes.
-
• The value of network lifetime is same as of AODV and our proposed routing protocol.
-
• The value of end to end delay increases for our protocol in comparison to the standard AODV protocol since our protocol checks the residual battery power at every intermediate node.
These results can be very fruitful for researchers working in the area of ad hoc network.
Список литературы A Novel Routing Scheme for Mobile Ad Hoc Network
- Chen, L., Heinzelman, W.B., 2005, "QoS-aware Routing based on Bandwidth Estimation for Mobile Ad-hoc Networks" IEEE Journal on Selected Areas in Communications, Volume 23, Issue 3, March, 561-572.
- Romdhani, L., Bonnet, C., 2005, "A Cross-layer On-demand Routing Protocol for Delay-Sensitive Applications", IEEE 16th International Symposium on Personal, Indoor and Mobile Radio Communications, Volume 2, 11-14 September, 994-998.
- C. E. Perkins, S.R. Das, and E. Royer, "Ad-hoc on Demand DistanceVector (AODV)". March 2000, http://www.ietf.org/internal-drafts/draft-ietf-manet-aodv-05.txt
- R.S. Sisodia, B. S. Manoj, and C. Siva Ram Murthy(2002): "A Preferred Link-Based Routing Protocol for Ad-hoc Wireless Networks". Journal of Communications and Networks, vol. 4, no. 1, pp. 14-21
- Y. C. Hu and D. Johnson (2000), "Caching Strategies in On-demand Routing Protocols for Wireless Ad-hoc Networks," Proc. IEEE/ACM MOBICOM '00, pp. 231–42.
- Hanzo,II, L., Tafazolli, R., 2006, "Quality of Service Routing and Admission Control for Mobile Ad-hoc networks with a contention-based MAC Layer", IEEE International Conference on Mobile Adhoc and Sensor Systems, 9-12 October, 501-504.
- L. Chen and W.B. Heinzelman, "QoS-Aware Routing Based on Bandwidth Estimation for Mobile Ad Hoc Networks," IEEE J. Selected Areas in Comm., vol. 23, no. 3, pp. 561-572, Mar. 2005.
- Mayhew, G.L., 2007, "Quality of Service in Mission Orientated Ad-hoc Networks", IEEE Aerospace Conference, 3-10 March, 1-9.
- Abdullah, J., Parish, D., 2007, "Impact of QoS Routing Metrics for MANETs in the Pervasive Computing Environment"; International Conference on Wireless and Optical Communications Networks 2007, 2-4 July, 1-5.
- S. Ramanathan and M. E. Steenstrup. 1996. A survey of routing techniques for mobile communications networks. MobileNetworks and Applications 1:98-104.
- J.Y. Teo, Y. Ha, C.K. Tham, "Interference-Minimized Multipath Routing with Congestion Control in Wireless Sensor Network for High-Rate Streaming", IEEETransactions on Mobile Computing, vol. 7, no. 9, pp.1124-1137, September 2008.
- Kone, V., Nandi, S., 2006, "QoS Constrained Adaptive Routing Protocol for Mobile Adhoc Networks", 9th International Conference on Information Technology, 18-21 December, 40-45.
- Charles E. Perkins, (2000) "Mobile Ad-Hoc Networks," Addison-Wesley.
- Jayashree S., Manoj B.S. and Siva Ram Murthy C., (2003), "Energy Management in Adhoc Wireless Networks: A Survey of Issues and Solutions". Technical Report, Department of Computer Science and Engineering, Indian Institute of Technology, Madras, India.
- Sunil Tanejaa, Ashwani Kushb, Amandeep Makkarc, and Bharat Bhushand, (2011) "Power Management in Mobile Adhoc Network" International Transaction Journal of Engineering, Management, & Applied Sciences & Technologies, Vol. 2, No. 2.
- Hussein ElAttar, Hussein Abdelaty, Salwa H.ElRamly, Mohamed Aboul-Dahab, (2010) " Improving the Lifetime of Wireless Ad Hoc Networks Using Power Aware Routing" 18th Telecommunications forum TELFOR 2010.
- V. Rodoplu and T.H. Meng, (1999) "Minimum Energy Mobile Wireless Networks," IEEE J. Selected Areas in Comm., vol. 17, No. 8, pp. 1333- 1344.
- Perkins, D., Hughes, H., Owens, C., 2002, "Factors effecting the Performance of Ad hoc Networks," IEEE International Conference on Communications, IEEE Press, 2048-2052.
- Z. Haas,"A New Routing Protocol for Reconfigurable Wireless Networks",In Proceedings of the IEEE International Conference on Universal Personal Communications (ICUPC), pages 562–565, October 1997.
- X. Hong, M. Gerla, G. Pei, and C.-C. Chiang,"A Group Mobility Model for Ad hoc Wireless Networks", In Proceedings of the ACM/IEEE MSWIM'99, Seattle, WA, August 1999.


