A Robust Color Image Watermarking Scheme Using Discrete Wavelet Transformation
Автор: Kaiser J. Giri, Mushtaq Ahmad Peer, P. Nagabhushan
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 1 vol.7, 2014 года.
Бесплатный доступ
Information hiding in digital media such as audio, video and or images in order to establish the owner rights and to protect the copyrights commonly known as digital watermarking has received considerable attention of researchers over last few decades and lot of work has been done accordingly. A number of schemes and algorithms have been proposed and implemented using different techniques. The effectiveness of the technique depends on the host data values chosen for information hiding and the way watermark is being embedded in them. However, in view of the threats posed by the online pirates, the robustness and the security of the underlying watermarking techniques have always been a major concern of the researchers. This paper presents a secure and robust watermarking technique for color images using Discrete Wavelet Transformation. The results obtained have shown that the technique is robust against various common image processing attacks.
Watermarking, Transformation, Copyright, Payload, Robustness, Accuracy Rate, Discrete Wavelet Transform
Короткий адрес: https://sciup.org/15013468
IDR: 15013468
Текст научной статьи A Robust Color Image Watermarking Scheme Using Discrete Wavelet Transformation
Published Online December 2014 in MECS
-
1. Section II presents the overview of the Digital Watermarking.
-
2. Section III provides a brief about Discrete Wavelet Transformation and its relevance in the context of watermarking
-
3. Section IV provides a review of recent techniques used in Digital Watermarking for color images using wavelets.
-
4. Section V discusses the proposed watermarking algorithm.
-
5. Section VI presents the experimental results.
-
6. Finally the conclusion is presented in section VII.
-
II. Digital Watermarking
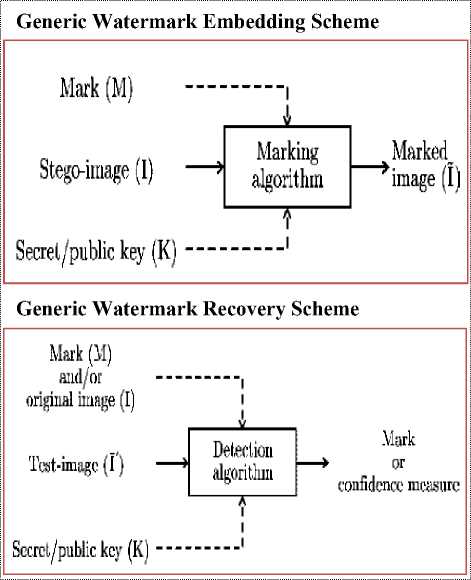
Fig 1. A Generic Watermarking Model
-
A. Watermarking Types
Keeping in view the diverse application requirements and media types, the watermarking can be classified on various parameters into following types [9].
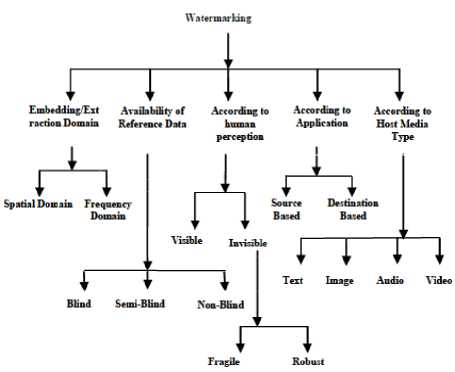
Fig 2. Watermarking types
Embedding/Extraction Domain: The domain being used for watermarking. There are mainly two types of watermarking in this category:
-
1. Spatial Domain: The watermarking is carried out by directly modifying the host data pixels according to the watermark pixels.
-
2. Frequency Domain: The watermarking is carried out by making necessary changes to the transform domain coefficients after subjecting the host data to some reversible transformation. The inverse transform is later applied to obtain the watermarked data.
Availability of Reference Data: Whether original unmarked data is required at the time of extraction of watermark. There are there types of watermarking in this category:
-
1. Blind: The original unwater marked data is required for extraction of watermark.
-
2. Non-Blind: The original unwater marked data is not required for extraction of watermark.
-
3. Semi-Blind: Some features derived from original unwatermarked data are required for extraction of watermark.
According to Human Perception: Whether the embedded watermarking is visible or not. There are two types of watermarking in this category:
-
1. Visible: The embedded watermark inlaid in the host data is transparent.
-
2. Invisible: The embedded watermark inlaid in the host data is hidden and can be extracted only by an authorized user
-
1.1 Fragile: The embedded watermark is destroyable by any kind of modification to the host data
-
1.2 Robust: The embedded watermark is resilient to image processing attacks.
According to Application: The basic Purpose of embedding the watermark, such as copyright protection and or temper detection. There are two types of watermarking in this category:
-
1. Source based: To detect the host data tempering
-
2. Destination based: To embed the watermark for copyright protection
According to host Media Type: The media under consideration for carrying out watermarking. These are four types of watermarking in this category:
-
1. Text: When the host data is text.
-
2. Image: When the host data is an image
-
3. Audio: When the host data is audio
-
4. Video: When the host data is video
-
B. Watermark Requirments
Some general requirements, not necessarily met by all the watermarking schemes are as:
-
1. Perceptual Transparency: The watermark
-
2. Data Payload: The total quantity of information stored as watermark within the host image, this depends on the application under consideration.
-
3. Robustness: The embedded watermark must confirm to different attacks such as compression, scaling, rotation, cropping and noise etc.
-
4. Security: Watermark embedded must be resistant to attempts by attackers to destroy or remove without modifying the cover data itself.
-
5. Effectiveness: The extraction process of embedded watermark must be fast and simple.
embedded must not affect the quality of underlying host image so that the user cannot distinguish the original image from the watermarked one. The watermarked image must replace the original one for all practical purposes
-
C. Watermarking Applications
Image watermarking has diverse applications for variety of purposes, some of the prominent application areas include:
-
1. Protection of Copyrights: To establish the ownership rights on newly produced work, additional copyright information can be inserted as a watermark. This additional information can serve as evidence in case of any ownership dispute.
-
2. Broadcast Monitoring: Watermarking can also be used to verify the content delivery from a broadcasting station and in turn can help to monitor unauthorized broadcast station.
-
3. Tamper Detection: Unlike robust watermarks used for copyright protection, fragile watermarks are used for tamper detection. The destruction or degradation of the watermark indicates it tampering and hence digital content cannot be trusted.
-
4. Authentication and Integrity Verification: Content authentication is mainly used detect any possible change in digital content. This can be achieved through the use of fragile or semi-fragile watermark which has low robustness to modification in an image.
-
5. Content Description: The embedded watermark can contain some detailed information of the host image such as labeling and captioning. For this kind of application, capacity of watermark should be relatively large and there is no strict requirement of robustness.
-
6. Covert Communication: It includes exchange of messages secretly embedded within images. In this case, the main requirement is that hidden data should not raise any suspicion that a secret message is being communicated.
-
III. Discrete Wavelet Transformation
Discrete Wavelet transformation (DWT) a mathematical tool for hierarchically decomposing an image is a promising transformation for carrying out watermarking in the frequency domain [10]. Wavelet transform is more suitable for processing of non- stationary signals. The wavelet transform is based on small waves, called wavelets, of limited duration and multi-resolution analysis [11]. Wavelet transform provides frequency as well as spatial description of an image and retains the temporal information unlike that of the conventional Fourier transformation. The DWT splits the signal into high and low frequency parts. The high frequency part contains information about the edge components, while the low frequency part is split again into high and low frequency parts. The high frequency components being less sensitive to Human Visual System (HVS) eyes are usually used for watermarking Watermark data embedded into low frequencies is more robust to image distortions that have low pass characteristics like filtering, lossy compression, and geometric manipulations but less robust to changes of the histogram such as contrast/brightness adjustment, gamma correction, and cropping. On the other hand, watermark data inserted into middle and high frequencies is typically less robust to low-pass filtering, lossy compression, and small geometric deformations of the image. The proposed method is based on wavelet domain and the watermark is applied to HL sub band in the blue channel being less sensitive to the HVS. In two dimensional applications, for each level of decomposition, we first perform the DWT in the vertical direction, followed by the DWT in the horizontal direction. After the first level of decomposition, are 4 sub-bands: LL1, LH1, HL1, and HH1. For each successive level of decomposition, the LL sub-band of the previous there level is used as the input. To perform second level decomposition, the DWT is applied to LL1 band which decomposes the LL1 band into the four sub- bands LL2, LH2, HL2, and HH2. To perform third level decomposition, the DWT is applied to LL2 band which decompose this band into the four subbands – LL3, LH3, HL3, HH3. This results in 10 subbands per component. LH1, HL1, and HH1 contain the highest frequency bands present in the image tile, while LL3 contains the lowest frequency band. The three-level DWT decomposition is shown in Fig.3.
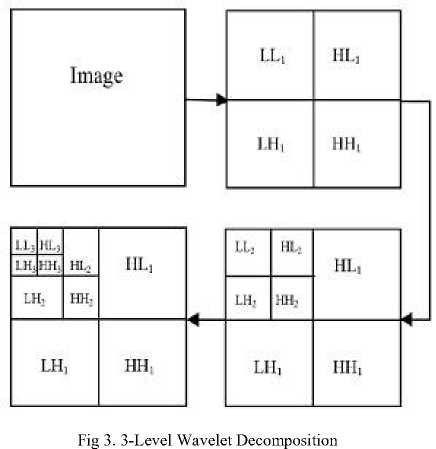
-
IV. Literature Review
Discrete wavelet transformation has many applications in the signal processing. Since an image is also a two dimensional signal, discrete wavelet domain based watermarking has become an area of interest of many researchers over the last few decades as it gives the multiresolution description of the image and is very similar in nature to the theoretical model of human visual system. An image is repeatedly passed through a series of low pass and high pass filters to identify the most significant portion of the image to be taken into account for the consideration of watermark embedding keeping in view the perceptual transparency and robustness properties. Number of techniques has been devised for color watermarking in DWT domain. A DWT based non-blind colour image watermarking scheme has been designed by [12] where in RGB components in both host as well as watermark images are uncorrelated using principal component analysis. The singular values of the corresponding channels of the host image are then used for embedding the watermark after being subjected to DWT. The scheme is resilient against different attacks like cropping, affine transformation, histogram equalization, Y-shearing, X-shearing, Gaussian noise, also satisfies robustness and imperceptibility. A new scheme for watermarking and compression for color images has been proposed by [13]. The watermark size is one fourth as that of the color image. Within each color image components, three images are hidden. DWT is used to decompose each color component into four sub components in which three images are later on hidden. Initially DCT of the watermark is obtained and the result thus obtained is added to a component out of the three components which result from the DWT decomposition after being multiplied by a factor. The R, G and B components are reconstructed by applying Inverse DWT (IWT). Lastly, the main components are used to reconstruct the result. A robust spread spectrum based watermarking scheme in the wavelet domain has been designed by [14]. The scheme has a state of art performance so as the robustness and imperceptibility property are concerned. For secured transmission of data, a unique combination of DWT, Discrete Fourier Transform (DFT) and Singular Value Decomposition (SVD) based watermarking algorithm is presented in [15]. The RGB channels are separated from the original image and one of them is chosen for watermark embedding and subjected to level 1 2D-DWT using HAAR transformation resulting into four frequency sub-bands. For decomposition into U S V matrices, it uses 2D-DFT, SVD in these sub-bands. It then applies 2D-IDFT and 2D-IDWT. A wavelet based watermarking scheme for color images based on bio-inspired optimization principles has been proposed by [16] , the watermark being embedded is a logo watermark and is embedded in the host image after being decomposed using wavelet transformation. The coefficients in the host image and logo watermark are divided into some non-overlapping sub areas and a weighting factor is calculated for each sub-area, usually a visual mask based on HVS characteristics is used in the calculation of the weighting factor. A more robust color image watermarking algorithm using a hybrid of DCT and DWT features has been devised. The image is first converting into YCbCr color space, than the luminance component is selected for embedding watermark because of its sensitivity to human eyes. Before embedding watermark, the luminance component is divided according to the number of bits in the original watermark into two non-overlapping bocks of pixels, and DCT is transformation is performed on each block. In addition to the above, it also uses DWT. The algorithm is resilient to various attacks such as noise addition, JPEG compression, cropping, and filtering [17].
-
V. Proposed Method
An image is a two dimensional signal containing a multitude of frequencies both high and low and is also represented as a two dimensional matrix. Since low frequency components contain maximum energy, modification to these components can degrade the quality of image drastically, even though watermark embedding in these coefficients can increase the robustness. Therefore the most appropriate portion to be taken into account for watermark embedding consists of high frequency components. So in order to identify the significant portion of the image data for consideration of watermark, the image I of size MXN is subjected to level 1 DWT thereby decomposed into four non overlapping multi-resolution sub-bands viz. LL (Approximation subband), HL (Horizontal sub-band), LH (vertical sub-band) and HH (diagonal sub-band), out of which LL is the low frequency component and rest are high frequency (detail) components. As HH sub-band contains edges and texture of the image is also excluded. Since HVS is more sensitive towards horizontal therefore HL is considered in the blue channel being less sensitive to HVS [18-20] out of the remaining two i.e. HL and LH sub-bands. For embedding, the watermark which is gray scale image with a pixel depth of 8 having intensity values in the range of 0 to 255 is rearranged by dividing each intensity value into three digits by using modulus operator. These digits are than embedded into three different streams in an ordered manner using the additive procedure i.e. in one stream 1st digit of every intensity value is embedded, in another second digit and so on. Later on during the extraction phase, reverse process is used to extract these digits and reassembled into a watermark. The watermark embedding and extraction procedures are as follows:
Watermark Embedding:
-
1. Read the color image I of size 512X512 and apply level one DWT on it
-
2. Take the HL (horizontal sub-band) coefficients into consideration for the watermark embedding.
-
3. Rearrange the watermark which a greyscale image of size 32X32 by splitting each intensity value into three digits using the modulus operator resulting three different digit streams having values in the
-
4. Embed these digit streams into three coefficient
-
5. Perform the inverse DWT to obtain the
range of 0 to 9 except for the first digit whose value can be in the range of 0 to 2.
steams of the host image correspondingly.
watermarked image M.
Watermark extraction:
-
1. Read both original (I) as well as watermarked (M) images respectively.
-
2. Perform level one DWT on both the image and consider HL sub-bands in each case and perform the subtraction correspondingly to obtain the watermark W
-
3. Reconstruct the watermark W.
-
VI. Expermental Results
To measure the effectiveness of the proposed technique on the basis of perceptual transparency and robustness, two different experiments were performed, first one to check the PSNR between the original and the watermarked image and another one to check the accuracy rate (AR) of the extracted watermark. The experiment was conducted on four different images and a PSNR value 50 was obtained, which clearly indicates the goodness of the technique in terms of the perceptual transparency property [21-23]. These images were later attacked with different types of noises and the AR of extracted watermarks was computed. It was found that the extracted watermark has an AR of 78.48 in the worst case. Which clearly indicates that the technique is robust one? The results obtained are shown below in Table1 and Table 2.
Table1: Experimental Results Of PSNR Between Original (I) And Watermarked Image(S) And The AR Of The Extracted Watermarks.
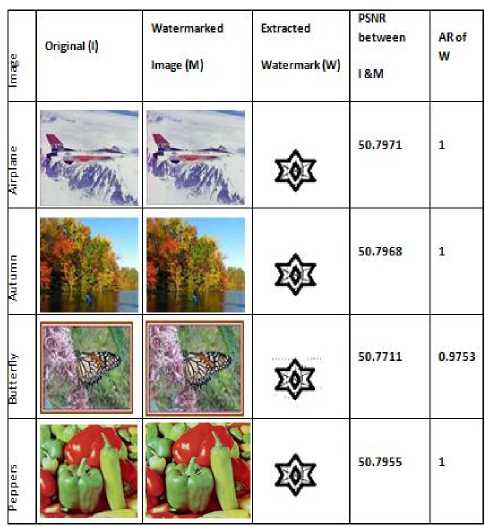
Table2: Experimental Results of the Accuracy Rate of the Extracted Watermark from five images.
|
jfype of Attack |
AR of Extracted Watermark |
|||||
|
Airplane |
Autumn |
Butterfly |
Peppers |
|||
|
Median Filter (Window size) |
3X3 |
0.8675 |
0.8391 |
0.8731 |
0.7893 |
|
|
Gaussian Moise (Variance) |
0.001 |
0.8207 |
0.8053 |
0.8611 |
0.8063 |
|
|
0.002 |
0.8124 |
0.8006 |
0.8538 |
0.8041 |
||
|
0.003 |
0.8085 |
0.7862 |
0.85Б9 |
0.8797 |
||
|
JPEG Compression (Quality Factor) |
90 |
0.7902 |
0.8070 |
0.8250 |
0.7923 |
|
|
80 |
0.7933 |
0.7848 |
0.8301 |
0.8772 |
||
|
70 |
0.7902 |
0.8728 |
0.8147 |
0.7880 |
||
|
Salt & Pepper (Density) |
0.001 |
0.9754 |
0.9700 |
0.9053 |
0.9760 |
|
|
0.002 |
0.9743 |
0.9208 |
0.9005 |
0.9732 |
||
|
0.003 |
0.9715 |
0.8910 |
0.9011 |
0.9695 |
||
-
VII. Conclusion
This paper presents a novel watermarking technique, in which discrete wavelet transformation is used as a tool to analyze the image data by decomposing the image into various coefficients having different resolution. The main impetus behind using the wavelet transformation is to get a detailed description of the image data, so as to identify the more appropriate portion of the image for consideration of watermark embedding. After words the appropriate portion is taken into consideration keeping in view the transparency and robustness property. The results obtained have shown that is technique is robust against common image processing attacks to a good extent even though the payload is slightly higher. The proposed technique also stands good so far as the perceptual transparency and security properties are concerned.
Список литературы A Robust Color Image Watermarking Scheme Using Discrete Wavelet Transformation
- Singh P., Agarwal S., Pandey, "A.A hybrid DWT-SVD based robust watermarking scheme for color images and its comparative performance in YIQ and YUV Color Spaces ", 3rd IEEE International Advance Computing Conference (IACC), 2013.
- Ying Zhang, Jiqin Wang, Xuebo Chen, "Watermarking technique based on wavelet transform for color images", 24th IEEE Chinese Control and Decision Conference (CCDC), 2012.
- Dang H.V., Kinsner Witold, "An intelligent digital colour image watermarking approach based on wavelets and general regression neural networks", 11th IEEE International Conference on Cognitive Informatics & Cognitive Computing (ICCICC), 2012.
- Pramoun T., Amornraksa T., "Improved image watermarking scheme based on DWT coefficients modification in LL sub-band", 9th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), 2012.
- Ruisong Ye and Wenping Yu,"An Image Hiding Scheme Using 3D Sawtooth Map and Discrete Wavelet Transform ", I.J. Image, Graphics and Signal Processing, 2012, 6, 52-60.
- Nader H. H. Aldeeb, Ibrahim S. I. Abuhaiba, "An Improved Watermarking Scheme for Tiny Tamper Detection of Color Images", I.J. Image, Graphics and Signal Processing, 2013, 5, 1-14.
- A.F.ElGamal, N.A.Mosa, W.K.ElSaid, "Block-based Watermarking for Color Images using DCT and DWT" International Journal of Computer Applications (0975 – 8887) Volume 66– No.15, March 2013.
- Sequeira, A., & Kundur, D, "Communications and information theory in watermarking: A survey", In. Proceedings of SPIE Multimedia Systems and Application IV, 4518, 216–227, 2001.
- Kaiser J. Giri, Mushtaq Ahmed Peer & P. nagabhushan, "Copyrirght Protection of Color Images using novel Wavelet based Watermarking Algorithm", In Press: 2nd IEEE Intl. Conf. on Image Information Processing", JUIT, Shimla, India, (2013).
- Nikita Kashyap, G. R. SINHA, "Image Watermarking Using 3-Level Discrete Wavelet Transform (DWT)", International Journal of Modern Education and Computer Science, 2012, volume 3, pages(50-56).
- N. Mohananthini, G. Yamuna, "A Robust Image Watermarking Scheme Based Multiresolution Analysis", I.J. Image, Graphics and Signal Processing, 2012, 11, 9-15.
- Muhammad Imran, Abdul Ghafoor, "A PCA-DWT-SVD based Color Image Watermarking", IEEE International Conference on Systems, Man, and Cybernetics October 14-17, 2012, COEX, Seoul, Korea.
- S.G.Eltaweel, "Compression and Watermarking For Color Images", IEEE, 2012.
- A. K. Verma, Nishant Goyal and C. Patvardhan, "Wavelet based Robust Video Watermarking using Spread Spectrum Technique", Fourth International Conference on Computational Intelligence and Communication Networks, 2012.
- Rahim Ansari, Mrutyunjaya M Devanalamath, K. Manikantan, S. Ramachandran, "Robust Digital Image Watermarking Algorithm in DWT-DFT-SVD Domain for Color Images", International Conference on Communication, Information & Computing Technology (ICCICT), Oct. 19-20, Mumbai, India, 2012.
- Ehsan Vahedi, Reza Aghaeizadeh oroofi and Mohsen Shiva, "Towards a new wavelet based watermarking approach for color images using bio-inspired optimization principles", Digital Signal Processing 22(2012) 153-162.
- A. F. ElGamal, N.A. Mosa and W. K. ElSaid, "Block-based nWatermarking for Color Images using DCT and DWT", International Journal of Computer Applications (0975 – 8887) Volume 66– No.15, March 2013.
- Sangeeta D. Jadhav, Anjali S. Bhalchandra, "Blind Source Separation Based Robust Digital Image Watermarking Using Wavelet Domain Embedding", IEEE Conference on Cybernetics and Intelligent Systems,2010.
- Mingwei Zhao and Yanzhong Dang, "Color Image Copyright Protection Digital Watermarking Algorithm Based on DWT & DCT", IEEE, 2008.
- Nagaraj V.D harwadkar, B. B. Amberker & Avijeet Gorai, "Non-blind Watermarking scheme for color images in RGB space using DWT-SVD", IEEE, 2011.
- Mingwei Zhao and Yanzhong Dang, "Color Image Copyright Protection Digital Watermarking Algorithm Based on DWT & DCT", IEEE, 2008.
- Ming-Shing Hsieh and Din-Chang Tseng , "Wavelet- based Color Image Watermarking using Adaptive Entropy Casting", IEEE International Conference on Multimedia and Expo (ICME), 2006.
- Anfeng Hu, Ning Chen, "A Blind Watermarking Algorithm for Color Image Based on Wavelet Transform and Fourier Transform", The 9th International Conference for Young Computer Scientists, 2008.


