A Robust Image Watermarking Scheme Based Multiresolution Analysis
Автор: N. Mohananthini, G. Yamuna
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 11 vol.4, 2012 года.
Бесплатный доступ
Digital watermarking has been widely applied to solve copyright protection problems of digital media relating to illegal use of distributions. In digital watermarking, a watermark is embedded into a cover image in such way that the resulting watermarked signal is robust to certain distortion. This paper presents a digital image watermarking based on Discrete Wavelet Transform (DWT). In the proposed method, the watermark as well as the cover image seldom looses the quality in both embedding and extraction process. The embedding process is carried out by tetra-furcating the watermark and embedded into the sub-bands of cover image. Signal to Noise Ratio (SNR) and Peak Signal to Noise Ratio (PSNR) are computed to measure image quality for the DWT transform. We present traces of host and watermarked images. From the traces we observe that, we get good SNR and PSNR with DWT. Experiment evaluation demonstrates that the proposed scheme is able to withstand a variety of attacks. This scheme shows good performance on different types of cover images in terms of imperceptibility and resist to jpeg compression.
Wavelet decomposition, Robustness, Digital image Watermarking, Image processing, Peak signal to noise ratio, Multiresolution analysis
Короткий адрес: https://sciup.org/15012454
IDR: 15012454
Текст научной статьи A Robust Image Watermarking Scheme Based Multiresolution Analysis
Digital watermarking is an important and useful technology for protecting the copyright of content and for preventing misuse of multimedia that increases with the rapid development of the internet. This technology embeds a watermark which identifies specific information of a copyrighter or owner in content itself without any distortion in the quality. This content may be an audio, text and video, but most of the time watermarking is applied to still images. The watermarking applications are finger printing, authentication, broadcast monitoring, integrity verification, copy protection and copyright protection.
The image watermarking algorithms can be classified into two categories: spatial-domain techniques and frequency-domain techniques. The spatial-domain techniques directly modify the intensity values of some selected pixels while the frequency-domain techniques modify the values of some transformed coefficients. The watermarking scheme based on the frequency domains can be further classified into the Discrete Fourier Transform (DFT), Discrete Cosine Transform (DCT) and Discrete Wavelet Transform (DWT) domain methods. The watermark is embedded in transformed coefficients of the image such that the watermark is invisible and more robust for some image processing operations [1].
A detailed survey on wavelet based watermarking techniques can be found in [2]. To take the advantage of localization and multiresolution property of the wavelet transform and wavelet tree based watermarking algorithm are proposed in [3, 4]. Their method shows good robustness to geometric attacks like cropping and rotation but it is sensitive to common signal processing attacks like low pass filtering and sharpening. A method proposed in [5] is to discover spatial patterns that are dominant or unique in each spectral band of a hyper spectral image. Their approach relies on the multiresolution image fusion framework as well as on exploratory visual data analysis. It is shown that the proportion of dominant details obtained from multiresolution decomposition, and their reconstructed spatial signature, provides valuable clues for image interpretation.
A watermarking model using biorthogonal wavelets based on embedding a watermark in detail wavelet coefficients of the cover image are suggested in [6]. The result shows that the model was robust against numerous signal distortions, but required the presence of the watermark at the detection and extraction phases. Two visual watermarks are embedded in the DWT domain through modification of both low and high frequency coefficients are explained in [7].
An optimal wavelet based watermarking algorithm that embed a binary logo in all the four sub-bands of wavelet transform. Watermarks are embedded with variable scaling factor in different sub-bands. The scaling factor is high for the LL sub-band and scaling factor is low for other three sub-bands [8].
In paper [9] applied the chaotic characteristics of the standard map to image encryption and image watermarking. Their method uses the shuffling schemes are based on the continuous standard map instead of the discredited one is proposed. Experimental results demonstrate that the host images embedded watermark is robust against various attacks. A new non-blind luminance-based color image watermarking technique is proposed in [10]. The approach is tested against variety of attacks and filters: such as, high pass, low pass, Gaussian, median, salt and peppers, and JPEG compression. The proposed approach shows a great ability to preserve the watermark against these attacks.
Digital watermarking using biorthogonal wavelet transform are presented in [11]. Their method is robust against several attacks. The watermark embedded into the original image in spatial-domain by dividing the original image into different block size and adjusting brightness of a block according to the watermark are presented in [12]. Their method shows robust against some common image processing operations, such as median filter, scaling and rotation. New wavelet based logowatermarking scheme for copyright protection of digital image are presented in [13]. A scheme is developed for reliable extraction of watermark from distorted images. Their method is robust to wide variety of attacks.
In this paper we proposed a digital image watermarking scheme based on wavelet domain. The watermark is divided into four parts then during the embedding process; the divided watermark is embedded into cover image of LL 2 , HL 2 , LH 2 and HH 2 . The extraction processes recover the watermark from the watermarked image. The experimental results have shown this scheme has preferable performance of imperceptibility and robustness.
This paper is organized as follows; The Proposed algorithms for watermark embedding and extraction are explained in section II. The experimental results are presented in section III. Finally, concluding remarks are given in section IV.
II. Proposed watermarking scheme
The proposed method embeds watermark by decomposing the cover image. The watermark used for embedding is a binary logo image, which is very small compared with the size of the cover image. Thus the watermark can be recovered exactly from the watermarked image.
-
A. Discrete Wavelet Transform
The wavelet transform is based on small waves of the multiresolution analysis. In two-dimensional DWT, each level of decomposition produces four bands of data, one corresponding to the low pass band (LL), and three other corresponding to horizontal (HL), vertical (LH), and diagonal (HH) high pass bands. The decomposed image shows an approximation image in the lowest resolution low pass band, and three detail images in higher bands. The low pass band can further be decomposed to obtain another level of decomposition. Fig. 1 shows two levels of decomposition.
|
LL2 |
HL2 |
HL1 |
|
LH2 |
HH2 |
|
|
LH 1 |
HH 1 |
|
Fig. 1. DWT Decomposition with Two Levels
Watermark data is embedded into low frequencies is more robust to image distortions that have low pass characteristics like filtering, lossy compression, and geometric manipulations but less robust to changes of the histogram such as contrast/brightness adjustment, gamma correction, and cropping. On the other hand, watermark data inserted into middle and high frequencies is typically less robust to low-pass filtering, lossy compression, and small geometric deformations of the image.
The proposed method based on wavelet domain and the watermark is applied to all frequency bands LL 2 , HL 2 , LH 2 and HH 2 .
-
B. Watermarking Embedding Process
The block diagram of watermark embedding process is shown in Fig. 2. The steps for watermark embedding are briefly listed as follows,
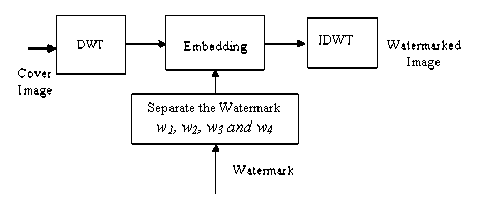
Fig. 2. Watermark Embedding Process
-
(1) The cover image is decomposed by 2-levels using Discrete Wavelet Transform.
-
(2) A Mathematical formula is used to separate the watermark w into w 1 , w 2 , w 3 and w 4 are represented as
W k = T ( k ) X 5 ; k = {1,2,3,4} (1)
Where, w = watermark, T = constant and S = pixel value of original watermark.
-
(3) The watermark w 1 , w 2 , w 3 and w 4 are applied to the gray scale cover image in sub-bands LL 2 , HL 2 , LH 2 and HH 2 respectively.
-
(4) The watermarked image can be obtained by the following equation
WI ( i , j ) = I ( i , j ) + a x w ( i , j )
Where, WI = watermarked image, w=watermark and I = cover Image.
a = scaling factor which determine the strength of watermark.
-
(5) The inverse wavelet transform is performed to get the watermarked image.
-
C. Watermarking Extraction Process
The watermark extraction processes are the inverse process of watermark embedding, shown in Fig. 3. The steps for watermark extraction are briefly listed as follows,
-
(1) The watermarked image and the cover image is decomposed by 2-levels, using Discrete wavelet transform
-
(2) The watermark w 1 , w 2 , w 3 and w 4 can be extracted from the watermarked image sub-bands LL 2 , HL 2 , LH 2 and HH 2 respectively. Then it is divided by the watermark strength factor a . This is summarized as follows,
- '( i , j ) = (WI ( i , j ) - 1 ( i , j )) / a
-
(3) The watermark w can be extracted by using the Mathematical equation
wk ' = T ( — k ) x 5
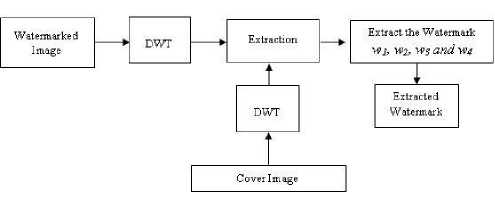
Fig. 3. Watermark Extraction Process
III. Experimental results and Discussion
In this paper, a robust watermarking technique is proposed based on wavelet domain for gray scale images. In our experiments, we use the 512×512 Lena, Barbara and Baboon as the cover images and a 48×48 size gray scale logo is used as watermark image. Fig. 4 shows the set of cover and watermark images.

(a)

(b)
AU

(c)
Fig. 4. Cover Images (a) Lena (b) Barbara (c) Baboon (d) Original Watermark
(d)
-
A. Performance Evaluation
In order to evaluate the performance of watermarking technique, the Peak Signal to Noise Ratio (PSNR) and the Normalized Correlation (NC) are two common quantitative indices are used. Normalized Cross Correlation is used to measure the quality of watermark after recovery. The NC between the embedded watermark W (i, j) and the extracted watermark W’ (i, j) is defined as
HL
EE W ( i , j ) x W '( i , j )
NC = 1 = 1 j =1 . ----------------- (5)
HL
EE [W ( i , j )] 2
i = 1 j = 1
Peak Signal to Noise Ratio (PSNR) is used to measure quality of watermarked image, it is given by
PSNR ( dB ) = lOlog io^^^ (6)
The Mean Square Error (MSE) between a watermarked image and cover image.
N
M5E = T, E ( I - — । ) 2 <7>
N j = 0
Where I w is watermarked image and I is cover image.
-
B. Imperceptibility Evaluation
Fig. 5 shows the watermarked images of Lena, Barbara and Baboon and it is extracted watermark image. Table 1 lists the NC values of extracted watermarks and image quality (PSNR).

(a)
ли

(a) (b)
Fig. 6. (a) Watermarked image with 20% salt and pepper noise (b) Extracted watermark
(b)

(c)

(d)

(e)
Fig. 5. (a), (c) and (e) are watermarked images on Lena, Barbara and Baboon images. (b) Extracted Watermark from Lena, (d) Extracted Watermark from Barbara and (f) Extracted Watermark from Baboon
ли
(f)
T able 1. NC values of extracted watermarks and image quality (PSNR).
|
Watermarked Images |
SNR |
MSE |
PSNR in db |
NC |
|
Lena |
41.0475 |
0.9906 |
47.9649 |
1 |
|
Barbara |
41.8522 |
0.9913 |
47.6783 |
1 |
|
Baboon |
42.6150 |
0.9922 |
47.4552 |
1 |
C. Robustness Evaluation
Robustness of the proposed method is evaluated for various types of image distortions are discussed below.
1) Non-Geometric Attacks: Watermarked Lena Image is tested for non-geometric attacks such as additive noise, median filtering and JPEG compression
Salt & Pepper Noise: The watermarked image is corrupted with salt and pepper noise at the density ranging from 0.02 to 0.1. Fig. 6 shows the noise corrupted watermarked image of Lena and it is extracted watermark. Table 2 lists the PSNR and NC value for different noise densities. The extracted watermark is noisy, but it is recognizable.
T able 2. NC values of extracted watermarks and image quality (PSNR).
|
S.No |
Density of noise |
SNR |
MSE |
PSNR in db |
NC |
|
1. |
0.02 |
15.0353 |
395.4849 |
21.9527 |
0.9365 |
|
2. |
0.04 |
12.0004 |
795.4472 |
18.9179 |
0.8651 |
|
3. |
0.06 |
10.2144 |
1200.1 |
17.1318 |
0.7976 |
|
4. |
0.08 |
9.0360 |
1574.2 |
15.9534 |
0.7619 |
|
5. |
0.10 |
8.0770 |
1963.2 |
14.9944 |
0.7024 |
Gaussian noise: The watermarked image is added with Gaussian noise of variance ranging from 0.02 to 0.1. Fig. 7 shows the noise added watermarked image of Lena and it is extracted watermark. Table 3 lists the PSNR and NC value for different noise intensities.

(a)
Fig. 7. (a) Watermarked image with 20% Gaussian noise (b) Extracted watermark

(b)
T able 3. NC values of extracted watermarks and image quality (PSNR).
|
S.No |
Variance of noise |
SNR |
MSE |
PSNR in db |
NC |
|
1. |
0.02 |
10.2556 |
1188.8 |
17.1730 |
0.6190 |
|
2. |
0.04 |
7.5702 |
2206.2 |
14.4876 |
0.6032 |
|
3. |
0.06 |
6.0684 |
3117.5 |
12.9859 |
0.5437 |
|
4. |
0.08 |
5.1004 |
3896.0 |
12.0178 |
0.5079 |
|
5. |
0.10 |
4.4027 |
4574.9 |
11.3201 |
0.5595 |
Median Filtering: Median filtering is a nonlinear operation used in image processing to reduce noise in an image. Fig. 8 shows the watermarked image of Lena and it is extracted watermark for 3 x 3 filter size. Table 4 lists the PSNR and NC value for different size of mask.

(a) (b)
Fig. 8. (a) Watermarked image with 3 x 3 median filtering (b) Extracted watermark

(a) (b)
Fig. 10. (a) Watermarked image with histogram equalization (b) Extracted watermark
T able 4. NC values of extracted watermarks and image quality (PSNR).
|
S.No |
Filter size |
SNR |
MSE |
PSNR in db |
NC |
|
1. |
3 x 3 |
26.0647 |
31.2019 |
32.9822 |
0.8968 |
|
2. |
5 x 5 |
22.5151 |
70.6557 |
29.4325 |
0.8095 |
|
3. |
7 x 7 |
20.4893 |
112.6497 |
27.4067 |
0.7778 |
|
4. |
9 x 9 |
19.2504 |
149.8354 |
26.1678 |
0.7817 |
JPEG compression: Table 5 lists extracted watermark and image quality of watermarked image after attacking by JPEG compression with different compression ratio. Fig. 9 shows the watermarked image of Lena and it is extracted watermark. It shows the embedded watermark fully extracted from JPEG compressed image.


(a) (b)
Fig. 9. (a) Watermarked image with JPEG compression Q=90 (b) Extracted watermark
T able 6. NC values of extracted watermarks and image quality (PSNR).
|
SNR |
MSE |
PSNR in db |
NC |
|
9.6431 |
1368.3 |
16.5606 |
0.8532 |
Rotation: Fig. 11 shows the rotation of watermarked image and it is extracted watermark. Table 7 list the PSNR and NC value for rotation. The watermarked image rotated by 45 degrees to the right and then rotated back to its original position.

(a) (b)
Fig. 11. (a) Watermarked image with rotation of 45 degrees (b) Extracted watermark
T able 7. NC values of extracted watermarks and image quality (PSNR).
|
SNR |
MSE |
PSNR in db |
NC |
|
3.4447 |
5704.1 |
10.3621 |
0.8016 |
T able 5. NC values of extracted watermarks and image quality (PSNR).
|
S.No |
%Q |
SNR |
MSE |
PSNR in db |
NC |
|
1. |
10 |
22.3297 |
73.7373 |
29.2471 |
0.7976 |
|
2. |
40 |
26.4180 |
28.7647 |
33.3354 |
0.8294 |
|
3. |
60 |
27.5873 |
21.9747 |
34.5047 |
0.8849 |
|
4. |
80 |
29.4243 |
14.3956 |
36.3417 |
0.9325 |
|
5. |
90 |
31.5632 |
8.7971 |
38.4806 |
0.9643 |
-
3) Common image processing Attacks: A watermarked Lena image is tested for common image processing attacks such as sharpening and smoothing.
Sharpening: Sharpening operations are used to enhance the subjective quality. Fig. 12 shows sharpening of watermarked image of Lena and it is extracted watermark. Table 8 list the PSNR and NC value for sharpening.
2) Geometric Attacks: A watermarked Lena image is tested for geometric attacks such as rotation and histogram equalization.
Histogram equalization: Fig. 10 shows the histogram equalization of watermarked image of Lena and it is extracted watermark. Table 6 list the PSNR and NC value for histogram equalization.

(a) (b)
Fig. 12. (a) Watermarked image with sharpening (b) Extracted watermark
T able 8. NC values of extracted watermarks and image quality (PSNR).
|
SNR |
MSE |
PSNR in db |
NC |
|
15.1402 |
386.0459 |
22.0576 |
0.7024 |
Smoothing: Fig. 13 shows smoothing of watermarked image of Lena and it is extracted watermark. Table 9 list the PSNR and NC value of smoothing.

(a) (b)
Fig. 13. (a) Watermarked image with smoothing (b) Extracted watermark
T able 9. NC values of extracted watermarks and image quality (PSNR).
|
SNR |
MSE |
PSNR in db |
NC |
|
32.7194 |
6.7408 |
39.6369 |
0.9960 |
The results presented here give a good indication of the capabilities of the proposed method for different types of attacks. The advantage of our proposed method has preferable performance of imperceptibility and robustness to common image processing operations.
IV. Conclusion
In this paper, we proposed a robust watermarking scheme on DWT. In the embedding process, the watermark is separated and then embedded to cover image. In the extracting process, the original watermark is retrieved from the watermarked image. The Experimental result shows that the proposed method has good imperceptibility on the watermarked image and superior in terms of Peak Signal to Noise Ratio (PSNR). The proposed method has high robustness to geometric (histogram equalization and rotation), non geometric (filtering, lossy compression and noise adding) and common image processing attacks (sharpening and smoothing). After applying these attacks the extracted watermark is recognizable. As a future initiative, we will address the extension of the technique to blind watermarking schemes.
Список литературы A Robust Image Watermarking Scheme Based Multiresolution Analysis
- P. Ramana Reddy, DR. Munaga, V.N.K. Prasad and DR D. Sreenivasarao, Robust Digital Watermarking of Images using Wavelets, International Journal of Computer and Electrical Engineering, 2009,Vol. 1, No. 2, 1793-8163.
- G.C. Langelaar, I. Setyawan and R.I. Lagendijk, Watermarking digital image and video data, IEEE Signal Process. Magazine, 2000, 20 – 46.
- X.D. Zhang, J. Feng and K.T. Lo, Image watermarking using tree-based spatial-frequency feature of wavelet transform, J. Visual Comm. Image Representation, 2003, 474 – 491.
- S.H. Wang and Y.P. Lin, Wavelet tree quantization for copyright protection watermarking, IEEE Trans. Image Process, 2004, 13, 154 – 165.
- Mario Beauchemin, Spatial pattern discovery for hyperspectral images based on multiresolution analysis, International journal of image and data fusion, Taylor & Francis 2012, vol. 3, Issue 1, 93-110.
- D. Kundur and D. Hatzinakos, Digital watermarking using multiresolution wavelet decomposition, Tech. Rep., Dept. of Electrical and Computer Engineering, University of Toronto, 1998.
- R. Mehul and R. Priti, Discrete Wavelet Transform Based Multiple Watermarking Scheme. Proceedings of IEEE Region 10 Technical Conference on Convergent Technologies for the Asia-Pacific, 14 – 17 October 2003, Bangalore, India.
- P. Tao and A.M. Eskicioglu, A robust multiple watermarking scheme in the discrete wavelet transform domain, Quality of Service and Control of Next-Generation Communication Networks II, Proceedings of the SPIE, 2004, Vol. 5601, pp. 133-144.
- Ruisong Ye and Huiqing Huang, Application of the Chaotic Ergodicity of Standard Map in Image Encryption and Watermarking, I.J. Image, Graphics and Signal Processing, 2010, 1, 19-29.
- Jamal Ali Hussein, Luminance-based Embedding Approach for Color Image Watermarking, I.J. Image, Graphics and Signal Processing, 2012, 3, 49-55.
- Suhad Hajjara, Moussa Abdallah and Amjad Hudaib, Digital Image Watermarking using Localized Biorthogonal Wavelets, European Journal of Scientific Research, 2009, Vol. 26, No.4, pp. 594 – 608.
- S. Kimpan, A. Lasakul and S. Chitwong, Variable block size based adaptive watermarking in spatial domain, IEEE international Symposium on Communications and Information Technology, 2004. vol. 1, pp.374-377.
- A. Adhipathi Reddy and B.N. Chatterji, A new wavelet based logo-watermarking scheme, Elsevier, 2005, pp. 1019 – 1027.


