A Secure and Efficient Cryptography System Based on Chaotic Maps for Securing Data Image in Fog Computing
Автор: Samaa Y. Tarabay, Abeer Twakol, Ahmed S. Samrah, Ibrahim Yasser
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 1 vol.15, 2023 года.
Бесплатный доступ
The huge availability and prosperity of net technology results in raised on-line media sharing over the cloud platform which has become one of the important resources and tools for development in our societies. So, in the epoch of enormous data great amount of sensitive information and transmission of different media transmitted over the net for communication. And recently, fog computing has captured the world's attention due to their inherent features relevant compared to the cloud domain, But this push to head for many issues related to data security and privacy in fog computing which it's still under studied in their initial juncture. Therefore, in this paper, we will review a security system that relies on encryption as a kind of effective solution to secure image data. We use an approach of using chaotic map plus space curve techniques moreover the confusion and diffusion strategies are carried out utilizing Hilbert curvature and chaotic map such as two-dimensional Henon map (2D-HM) to assert image confusion with pixel level permutation .Also we relied in our system the way of shuffling the image with blocks and use a key for each block, which is chooses randomly to have a high degree of security. The efficiency of the proposed technique has been tested utilizing different investigations like analysis of entropy [7.9993], NPCR [99.6908%] and finally UACI [33.6247%]. Analysis of results revealed that the proposed system of image encryption technique has favorable effects, and can achieve a good results moreover it fights different attacks and by comparing with another techniques denote that our proposed fulfills high security level with high quality.
Cryptography, Chaotic System, Securing Data, Fog Computing, Image Security
Короткий адрес: https://sciup.org/15018565
IDR: 15018565 | DOI: 10.5815/ijcnis.2023.01.06
Текст научной статьи A Secure and Efficient Cryptography System Based on Chaotic Maps for Securing Data Image in Fog Computing
The expansion of the Internet of Things (IOT) has led to mass production Data, with massive computing resources, storage space and communication bandwidth. The IOT realizes the interconnection of mature technology equipment from home to vehicle and workplace [1]. So, the term fog computing has emerged as horizontal intermediate layer between a cloud data centers and IOT devices that distributes storage, computing and data processing nearer to the end users [2]. Fog computing was first introduced by cisco and by pooling available computing, storage, and network resources at the edge of the network, service delivery is closer to the end user [1, 3]. It is a decentralized computing infrastructure, using one or more IOT collaborative execution on devices or edge devices close to the user a lot of communication, control, storage and management. Through the fog node and equipment, fog computing can reduce processing burden Resource-constrained equipment meets latency requirements delay sensitive applications and overcome bandwidth constraints of centralized services [4].In addition to it, fog computing also provides; (1) support for high mobility, (2) high responsiveness computation resources, (3) different communication protocols, (4) multiple data sources and devices can be integrated and moreover heterogeneity of interface within infrastructure, and (5) interoperability which must be able to interoperate and cooperate with different providers with wide range of services and effortlessly support certain services [5].
However, fog computing has not overcome the threats and security weaknesses that it is still exposed to in its system, which may have a significant impact on the system behavior and its exposure to breach and data exposure to repeated risks due to the lack of permanent stability against security issues, and therefore it is necessary to provide the most Effective solutions that resist these security issues, reduce risks to devices, and provide a strong and secure medium for data [1]. “Fig. 1,” shows fog computing architecture.
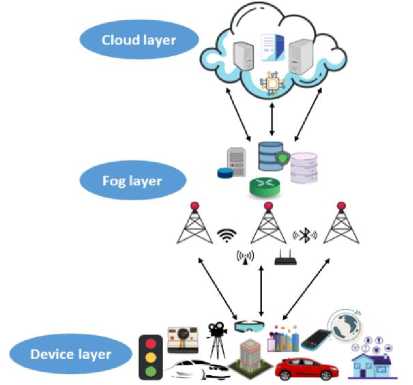
Fig.1. Fog Computing Structure Graph.
Digital image measures utilized in many applications as medical image, and image knowledge base of this digital image have to be compelled to be defend from unauthorized. A significant amount of this data image is private and should remain confidential between the exchanging parties, therefore, most of the ISP's reliance is on encryption and decryption techniques [6]. However, as a result of unlawful wiretapping, revision, or interception, there's a visible lack of security for communication images over the network, significantly [7-9]. Moreover, there're numerous means and tracks in which to emphasize the transference of secured data that compared to other strategies to ensure the safety of images as in medical field as one of the important areas against unauthorized access [7, 9].
Chaos- based secret techniques are thought of to be the foremost necessary because the wonderful features of chaotic system which can pledge the speed and high security [10]. Chaos-depended techniques have lately turn into appealing for shielding image content. Chaotic systems are sensitive, non-liner, deterministic and easy to reconstruct after filling in the image. Use their topmost characteristics like management control parameter, sensitivity to the initial condition, and non-convergence during a chaotic system (or map). Several schemes of image encryption have been proposed using Chaos and their worthiness has been partially demonstrated [11]. The overview of the related work revealed that chaotic systems have been exploited for efficient for multimedia data encryption. In cryptography, having a secure routing is needful to cross data through a secure lines and networks. Chaotic cryptosystem is one of the methods are thought of to be to be one of the essential element necessary because the effective properties of chaotic system which is sensitive, non-liner, deterministic and easy to reconstruct after filling in the image [9].Image encryption process can be categorized as i) position permutation, ii) value transformation. In the first technique it happens permutation for the image position with no changing in the pixel value of the image, and in second technique pixel value is substituted by another with no changing in the image position [12].
2. Related Works
Lately a lot of research represent many schemes of image encryption which is used the cryptosystem of chaotic theory to obtain the strength and the preferable image encryption techniques, here, we will explain and mention some of the research that was presented and received interest in this part. Arwa et al. [13], proposed a technique which based on pixel shuffling starting by converting the pixel value from a three-dimensional value (R, G, B) to 1D, then generate a row vector from image pixel and make a random permutation of row vector. XOR operation is obtained and finally 3D chaotic map is performed, it is limited by losing some data in the decryption process because of using 3D value of image in encryption steps and restored with 1D value in decryption stage. Yasser et al. [10] suggested hybrid method which the chaotic maps are combined, the author based on the technique of Discrete Wavelet Transform (DWT) and disband the image it to sub-bands. Both confusion and diffusion have procedured in the system. Assorts of chaotic maps types could be related to the image to enhance the encryption process. In recent period a lot of authors are turning to the field of using DNA technique, Shuqin et al. [14] characterized an algorithm that is depend on 5D continuous and chaotic system hybrid type, which adopts DNA dynamic coding mechanism and scrambling process with two rounds of diffusion encryption structure to enhance the security, the weakness point that the ability of cipher text to resist noise, cut and compress attacks is weak , also the more dimensional process used the more complexity and heavy cost will be. Many research has been proposed algorithms depend on scan patterns techniques. Mura Mural, P et al [15] designed a scheme based on Space Filling Curve that make the image scrambled using the mechanism of square wave to obtain confusion with many orders and diffused as well using saw-tooth technique with some various orders. The author doesn't use any chaotic equation or system in his proposed system to achieve confusion and diffusion. Another scheme for image encryption, Zhang, Xuncai, et al [16] this algorithm used a scheme of cryptography that depend on hybrid of Hilbert curve and H-fractal to realize the techniques of confusion and diffusion that achieved scrambling and value exchanging operations. In this work the sequence generator is based on both the piece-wise linear chaotic map (PWLCM) and Rossler chaotic. Shahna, K. U.et. al [17] proposes an encryption technique using Logistic map and Z-order curve, pixel scrambling is performed using Z-order curve and random matrix is generated using Logistic map and the results show us that the system does not have a high quality of security and vulnerable. Fu, C.et. al [7] suggested a technique which is bit permutation to overcome the drawbacks of conventional permutation-only type image cipher a significant diffusion effect in permutation procedure through a two-stage bit-level shuffling, scheme has a comparable security level and a much lower computational complexity.
3. Problem Statement
As it was mentioned previously, the encryption of data images is one of the most important issues that must be highlighted and worked to improve and develop in a superior manner, so we are trying to develop a solution to establish a secure and effective encryption system. The major purpose of our project is providing an effective and powerful mechanism to secure image data through an encryption system based on chaotic maps that has results of high sensitivity and quality level, moreover the used of scan patterns properties as the results based on this work showed the effectiveness of the system and its impact on encryption and the difficulty of being exposed to the attacks.
Usually, the cryptography processes which depend on chaotic techniques consists of two main ways includes confusion and diffusion, scrambling is the core meaning of confusion stage, the one that handle with pixels position, while diffusion technology is a technique for pixel value changing and diffuse pixels that has impact of changing the values of another pixel. And here in our proposed algorithm we use a hybrid between both confusion and diffusion in order to enhance and have a high quality of security system. To realize the scrambling operation, we use the Hilbert curve, as considered as popular and it's widely used in many applications because of its continuity as a continuously mapping, scalability and stability as the level increases, the distance of each point on the graph will become smaller and smaller, and as the level increases, the graphics will become more and more the larger, the point movement becomes no longer important. So, it can be regarded as no movement. Besides that, it's worth for mention that Henon map is a good chaotic map that its trajectory of it is simple and have something determined, thus the maps can be easily predicted with super quality plus it has superior features in generating perfect random sequence with regularly and constant allocation. The proposed system ensures high quality of resistance with better security cryptosystem due to both confusion and diffusion technology through two times of scrambling, once for pixel permutation, and another for value permutation using cyclic bit shifting technique. Now we can define the main and effective contributions of this paper in an understandable and summary form:
- The proposed system in our work uses bit permutation for realizing diffusion and the confusion can be actioned through applying pixel permutation mechanism.
- In this scheme, the Henon chaotic map is 2D which is more efficient and used for the generation of permutation sequences for realizing diffusion.
- The Hilbert curve is used for the generation of masking sequences for realizing confusion.
- The approached work proved that cipher image with high keys sensitivity with any changes in the original image.
- The outcome of the proposed algorithm is compared with existing results and validated by different cryptanalysis through many performance evaluation metrics that are usually used to evaluate the efficiency of image encryption approaches.
4. Block Diagram of the Proposed System
4.1. Hilbert Scrambling (Space Filling Curve)
There are some experiments, tests and comparisons that are presented to prove the performance of the proposed system algorithm.
The residuum of this paper is orderly as follows: Section 4 shows flowchart of the proposed system and the proposed approach fully explained below in “Fig. 2,” Section 5 and section 6 discusses the results and the analysis of our results. Conclusion and future works are given in Section 7.
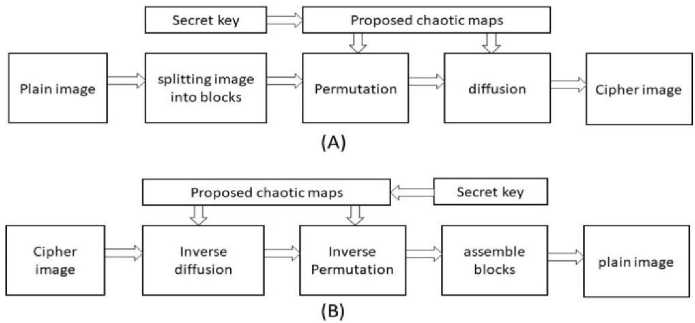
Fig.2. Proposed System Flowchart.
The Hilbert curve is a continuous fractal space-filling curve first described by the German mathematician David Hilbert in 1891 [16]. Hilbert curve is used to make a shuffling process of the pixels position of the original image to get a new scrambled image. According to the characteristics of its own space filling curve, the Hilbert curve can linearly traverse each discrete unit in two dimensions or higher dimensions, and only traverse once, and linearly sort and code each discrete unit, which is the only one of the unit Logo. Since the Hilbert code does not have a large step jump, the aggregation performance of the Hilbert space arrangement is better, that is, the adjacent points on the Hilbert curve must be adjacent in the original space. The Hilbert curve is an FASS curve, that is, space-filling, self-avoiding, selfsimilar, and simple one. These curves are situated in a Euclidean space and have a dimension higher than 1 and have non-hollow internal in the space [16].
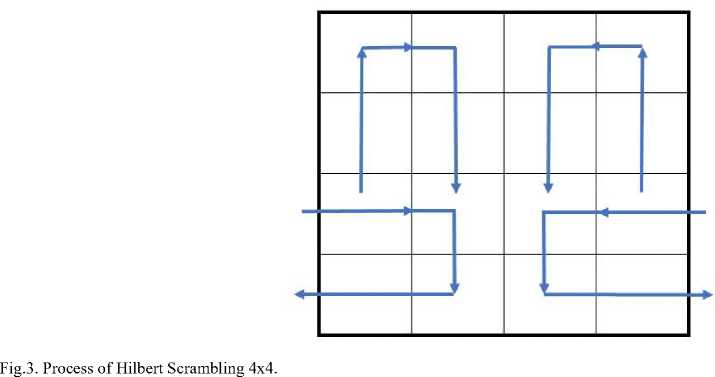
Now we will discuss the first iteration / order of Hilbert curve: the main square is splatted into four parts each part is as mini square starting the curve from the square's center in the southwest then to the square's center in the northwest corner heading to the square's center in northeast ending to the square's center of southeast, here we finished the main cycle, The places of the beginning stage and the ending point of the Hilbert curve refer to the direction of it [16], “Fig. 3,”refer to the description of Hilbert curve process.
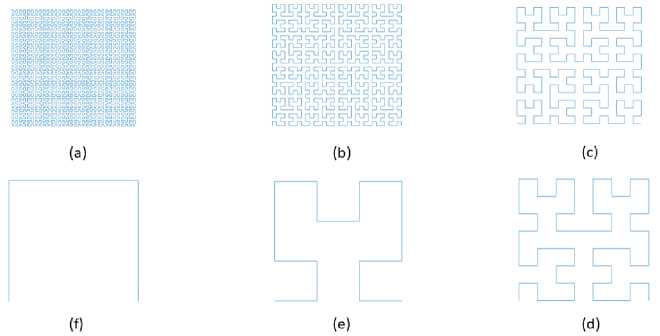
Fig.4. Hilbert Curve Shapes where Fig (a) Refer to Order 6, Fig(b) Refer to Order 5, Fig (c) Refer to Order 4, Fig (d) Refer to Order 3, Fig (e) Refer to Order 2, Fig (f) Refer to Order 1.
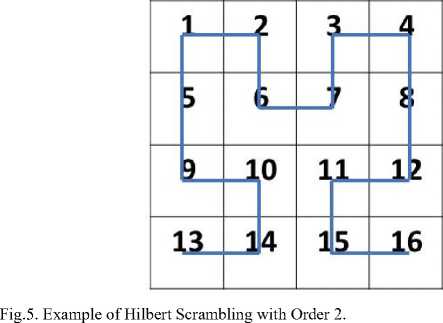
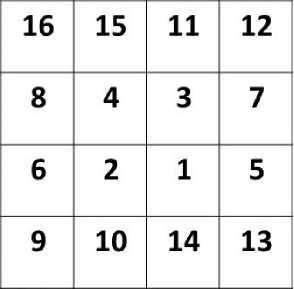
-
4.2. Henon Map
It is a discrete-time dynamical system. It is one of the most studied examples of dynamical systems that exhibit chaotic behavior [21]. The Henon map takes a point (xn,yn) in the plane and maps it to a new point. The map was introduced by Michel Hénon as a simplified model of the Poincaré section of the Lorenz model, using the following equations: - xn+1 = 1 - «xn 2 + Уп
У п + 1 = ^x n
There're two main parameters the Henon map is based on, for the standard Henon map have values of α = 1.4 and β = 0.3. For these classical values the Henon map considered as chaotic, the graph of this map is obtained in “Fig. 6,” Also the simulation of Henon bifurcation map of a chaotic diagram is shown in “Fig. 8& 9,”. Bifurcation diagram plots output sequences of a chaotic map along with the change of its system parameter(s) [22]. From the bifurcation diagram in “Fig. 8&9,” it is clear that Henon map is chaotic for the range of parameter (a) 1 ∈ [1.06, 1.22] ∪ [1.27, 1.29] ∪ [1.31, 1.4] [22]. Moreover, Chaotic motion is very sensitive to initial conditions and lyapunov gives a set of values called ( X ) where one of the values of it must be positive and this means that the system is chaos and has a chaotic movement as we see in “Fig. 7,” when the chaotic system is extremely very small in two different differential its motion path progressively generates indicator separation.
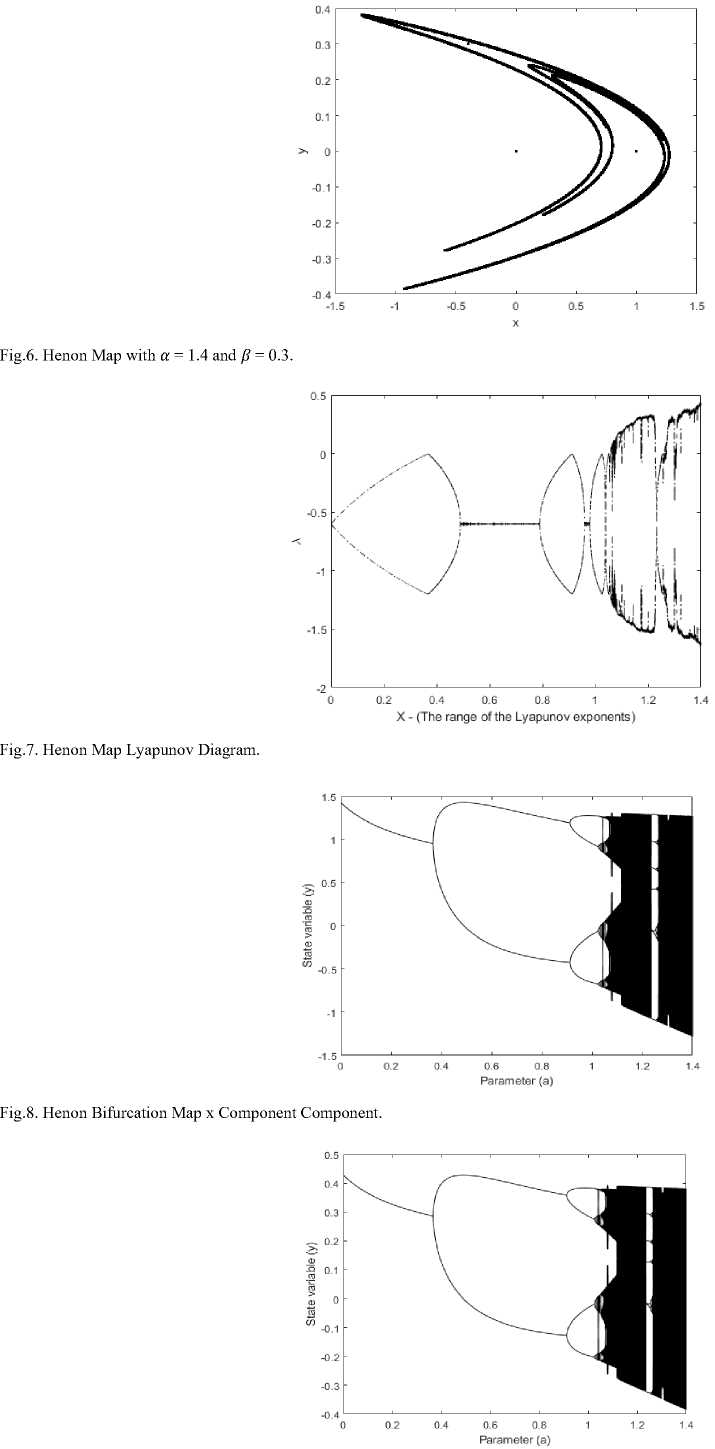
Fig.9. Henon Bifurcation Map y Component.
-
4.3. Encryption Algorithm Steps
The proposed cryptosystem starts with dividing the plain image into blocks then shuffling the pixels of this blocks indices with Hilbert maps key generation, then these shuffles blocks goes through two further encryption steps to strengthen algorithm, the first step is scrambling the images in a confusion process using the key generation of Hilbert scan then the diffusion step which takes the output of the confusion step and performs pixel value alterations based on the Henon map, the Henon maps follows the Henon formulas for generation of the keys the diffusion performs the encryption by altering the current pixel value based on the previous pixel to create a more robust encryption. The decryption process is done by a process of reversing all the previous steps in the encryption process to get the original image again and perform all the steps in order to get the original version of the data as we see below in details:
Our Proposed Algorithm Procedure:
1-Read the plain image (PI) with the size (W × H) where W and H respectively, are width and height of the plain image pixels.
2-Splitting the plain image (PI) into blocks.
3-Shuffling the blocks by Hilbert key generation.
-
4- Generating “Henon key” for each block separately as in the following: -
Г a1 = 0.00000012547
Initial values of Henon map
I bl = 0.00006122 I
Popularize parameters with introducing their initial values: - ai = 0.000001235544789, b = 0.003578891472566, u = 73834772913855, p = 71277967533485
Now upgrading values by these following equations:
u = u + floor(e2П *105)(3)
Here we get:
51 = ^*256 - e2n
v p = p + floor ([S1]*105)(5)
Here we get:
52 = ((X1 *107) - floor(X1 *107))(6)
which;
a = a 1 + ((51 - floor(S1)) *10-5)(7)
b = b1 +
-
- The new values of a1& b1 is presented for repetition henon map (t=500).
-
- Now, two chaotic sequences is obtained x , y.
-
- Through the upgrading of a1& b1 , process the chaotic sequence to get sequences of C1 & C2 by the equations below:
C1 = [ C 1, round (mod(( x 2) - floor ( x 2 ) u *109,255) + 1)] (9)
C 2 = [ C 2, round (mod((y2) - floor (y2 )p*109,255) + 1)] (10)
|
x = 1 - a x2 + y (11) y = в * У (12) |
|
|
- Then we get the two Henon keys: |
Key1 = (C1(t + 1end),[M,N]) (13) Key 2 = (C2(t + 1end),[M,N]) (14) |
Which [M, N] is considered as key size.
5-Then the scrambling step:
-
1) First according to the Hilbert curve mechanism set up the Hilbert pattern due to the description that mentioned above, “Fig. 4,” shows the different orders of Hilbert scrambling curve. ii) second iterate every pixel in the shuffled image from the step 3 in order to get the whole bits and represented in a matrix form (Matrix A), iii) third as the same way of second step, recur the values of the key1 in “(13),” and represented in a matrix form as the size of the key1 (Matrix B).
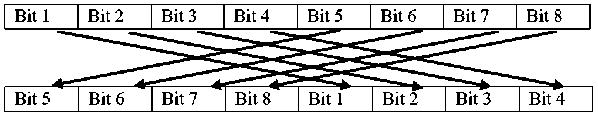
Fig.10. Example of Shifting Bits Process Mechanism.
6-here we get the confusion form of the encrypted image using Key1 and represented a new matrix after completing several procedures on the image to obtain an opaque version that does not have any clear features, let's named it by (IMG).
7-The key2 which is generated in “(14),” is used in this step which is called diffusion step.
|
G 1 = [mod IMG + U + V , 255] XORKey 2(1)] |
(15) |
|
G1i+! = {mod G1 + IMGi+ , + V ,255] XORKey 2/+1] |
(16) |
Where: i=1,2,…
8- Now, after the final encryption process, the decryption on the other hand reverses all of these steps backwards, it starts by inverting the diffusion step using the same key used for encryption, then it reverses to the encryption step and restores the pixels indices caused by confusion using the same Hilbert maps as in the encryption step and finally assembling the blocks to return to the plain version of the data.
5. Performance Metrics5.1. Histogram Analysis
5.2. Correlation Analysis
IMG = mod[ XORG1(1),Key (1) - r - v )255]
IMGi+ j = mod[ XORG1i+1 , Key2i+ j - G 1(1) - r , 255]
There are some performance measures that we use to get to know the impact of the proposed system and its effectiveness in achieving the best expected results from its performance, through some several parameters which cover the statistical, differential and efficiencies metrics.
This histogram is a graph that describes the graphical representation of the image and it is showing the number of pixels in an image at each different intensity value found in that image [20].
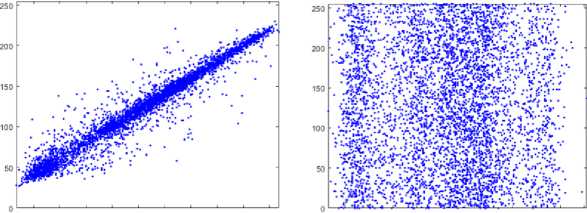
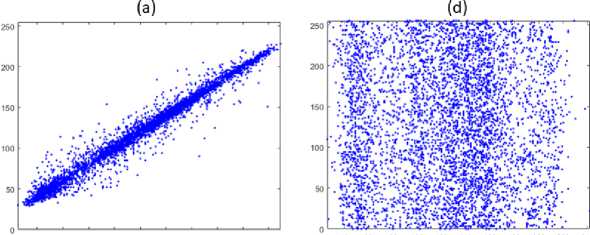
Correlation measures the degree of matching between two adjacent pixels of an image [23]. For the image in naturally, there is usually a high degree of correlation in most cases Due to pixel continuity, adjacent pixel pairs [24]. The following equation used for correlation calculation coefficient, the correlation of the original and encrypted images of our proposed system:
r= E i N^ x i - x )(y i - y )
V E Z/x - - x )2(y . - y ) 2
r = Correlation coefficient, X / = values of the x-variable in a sample, x =mean of the values of the x-variable, y =values of variable in a sample, y =mean of the values of the y-variable.
-
5.3. Information Entropy Analysis
-
5.4. Mean Square Error
It is a statistical merit for gauging the randomness's degree [25], and it describes the confusion properties of the original and the cipher image.
The ideal value is always equal to 8 for which the pixel values of the image always fall in the range of 0-255 [26]. The entropy value may fluctuate for the various pixel values of the image falls. Hence the suggested cryptosystem has 256 states so the maximum information entropy will be approached to 8 [7]. The following equation Used to calculate the information entropy:
2 l - 1
H ( m ) = -Ei = 0 P ( m i )log 2 ( P ( m i )) (20)
Where L indication to the total number of pixels values, p(m / ) is refers to the probability to m / .
As we can see, the above statistical parameters have a strong influence in judging the robustness and resistance of the proposed system towards any screening, in order to ensure that it enjoys a robust encryption level.
It measures the variation of two images. When its result is low that's indication to the less of the variation between both original and encrypted image [10].
MSE =
1 mxnxf
fmn
EEE ( P(i,j ) - c(i,j ))2 k = 1 i = 1 j = 1
Where p(i,j) is mentioned for original image, c(i,f) is mentioned for encrypted image, m, n is mentioned for total number of rows and columns.
-
5.5. Peak Signal-to-Noise Ratio
-
5.6. Number of Pixels Change Rate
PSNR is measuring the ratio and the conformity between original and encrypted image [27].
PSNR = 10log10( Max 01- ) dB
10 MSE
Where Max01 refer to the max conceivable pixel value of the original image.
NPCR is used to measure the change rate of pixel's number of encrypted image when adjusting a pixel in the original image [10].
NPCR =
MxN
E i,j D ( i , j ) X 100%
Where J 0,D1(i,j) = D2(i,j) | [ 1,D1(i,j) * D2(i,j) J
-
5.7. Unified Average Changing Intensity
UACI is for the average change intensity of differences between both original and ciphered images [28].
UACI = £
I D1( i , j ) - D 2( i , j )|"
J——-- X 100%
MNx 255
Where N, M is referred to the columns and rows respectively, D2 is decrypted image, and D1 is the original image. In this part, we will make a comparison between our proposed system and the other different algorithms through the results of NPCR and UACI that ensure our proposed system accomplished a better result compared to the others.
When analyzing the influence on the system in terms of its sensitivity and flexibility towards the attacker changing some features of the original image to obtain a difference in the content of the encrypted image, the need for the availability of differential parameters (the above mentioned) to maintain such attacks will protect the system from activating or forming any changes by any stranger. So, these differential aggressions will not be of any use.
Therefore, performance measures dominate very much in influencing the strength of the system and the extent of the impact of each parameter separately, and therefore the rigidity of the system is subject to such parameters to know the difference between the effect of routine methods and the proposed system. In Table 1 it's shown the various parameters that illustrate the analysis of the effectiveness of performance measures in our system, with a mention of the speed of performance in terms of time, as it is one of the most important parameter that reflect efficiency, especially with regard to real-time applications.
40 60 80 100 120 140 160 180 200 220 40 60 80 100 120 140 160 180 200 220 240
40 60 80 100 120 140 160 180 200 220 40 60 80 100 120 140 160 180 200 220 240
(b) (e)
Table 1. The factors of the Encryption Goodness for Some Various Image Tested.
|
Images |
Entropy |
PSNR |
T(sec) |
MSE |
|
cameraman |
7.9992 |
8.4061 |
0.219399 |
9385.717 |
|
Baboon |
7.9993 |
9.8148 |
0.14299 |
6785.7811 |
|
Peppers |
7.9993 |
8.256 |
0.18481 |
9715.8455 |
|
Lena |
7.9993 |
9.2376 |
0.17867 |
7750.3625 |
|
Mean |
7.999275 |
8.928625 |
0.18147225 |
8409.426525 |
Table 2. Refers to the Parameters of NPCR (%) and UACI (%) of our Proposed System.
|
Images Parameters |
Cameraman |
Baboon |
Peppers |
Lena |
|
NPCR (%) |
99.6779 |
99.6908 |
99.5376 |
99.6908 |
|
UACI (%) |
33.6204 |
33.6247 |
33.5736 |
33.6247 |
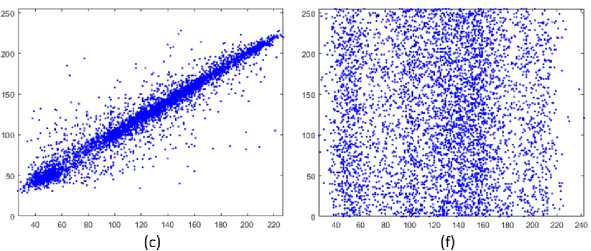
Table 3. Correlation Coefficient of the Original Images and their Encrypted Images.
|
Images |
Directions |
Horizontal |
Vertical |
Diagonal |
|
cameraman |
Plain image cipher image |
0.98448 -0.016364 |
0.99074 0.0048909 |
0.97558 -0.0082512 |
|
Baboon |
Plain image cipher image |
0.98075 0.0094014 |
0.97453 -0.030857 |
0.95822 0.0058893 |
|
Peppers |
Plain image cipher image |
0.97767 -0.018014 |
0.97125 -0.00072265 |
0.97886 -0.020445 |
|
Lena |
Plain image cipher image |
0.97576 -0.0025414 |
0.98412 0.00091759 |
0.96208 -0.0019035 |
For an image there's adjacent pixels have some degrees of correlation in horizontal, vertical and diagonal directions, so it can be seemed that in the original image the correlation is very vigorous regarding to the linearity linkage in all directions and it has a high correlation while the ciphered image has a very low one with random shape. In order to obtain an excellent cryptography algorithm to conserve the data from attackers whom manage statistical onslaught by exploiting correlation values of the original image, therefore it supposed to breakdown this linkage in the encrypted image. from Table 3, it's clear that the correlation value of plain image is close to value 1 and that's refer to the strength of its adjacent pixel correlation, and the opposite for the correlation value of encrypted image is close to value 0 which means the adjacent pixel correlation is extremely weak, and for the negative values it's confirming that there's no rapport between the original and the encrypted image. “Fig. 11,” refer to the simulation of correlation in our proposed algorithm.
Table 4. The Parameters of NPCR (%) and UACI (%) of our Proposed System Compared to another References.
Список литературы A Secure and Efficient Cryptography System Based on Chaotic Maps for Securing Data Image in Fog Computing
- Ni, J., Zhang, K., Lin, X., & Shen, X. (2017). Securing fog computing for internet of things applications: Challenges and solutions. IEEE Communications Surveys & Tutorials, 20(1), 601-628.
- Yousefpour, A., Fung, C., Nguyen, T., Kadiyala, K., Jalali, F., Niakanlahiji, A., & Jue, J. P. (2019). All one needs to know about fog computing and related edge computing paradigms: A complete survey. Journal of Systems Architecture, 98, 289-330.
- Guan, Y., Shao, J., Wei, G., & Xie, M. (2018). Data security and privacy in fog computing. IEEE Network, 32(5), 106-111.
- Ashi, Z., Al-Fawa’reh, M., & Al-Fayoumi, M. (2020). Fog computing: security challenges and countermeasures. Int J Comput Appl, 975, 8887.
- Khan, S., Parkinson, S., & Qin, Y. (2017). Fog computing security: a review of current applications and security solutions. Journal of Cloud Computing, 6(1), 1-22.
- M. N. Alenezi, H. Alabdulrazzaq, “Performance Evaluation of Cryptographic Algorithms: DES, 3DES, Blowfish, Twofish, and Threefish,” International Journal of Communication Networks and Information Security, Vol. 14, No. 1, 2022
- Masood, F., Driss, M., Boulila, W., Ahmad, J., Rehman, S. U., Jan, S. U., & Buchanan, W. J. (2021). A lightweight chaos-based medical image encryption scheme using random shuffling and XOR operations. Wireless Personal Communications, 1-28.
- Mohammad, O. F., Rahim, M. S. M., Zeebaree, S. R. M., & Ahmed, F. Y. (2017). A survey and analysis of the image encryption methods. International Journal of Applied Engineering Research, 12(23), 13265-13280.
- Masood, F., Ahmad, J., Shah, S. A., Jamal, S. S., & Hussain, I. (2020). A novel hybrid secure image encryption based on julia set of fractals and 3D Lorenz chaotic map. Entropy, 22(3), 274.
- Yasser, I., Khalifa, F., Mohamed, M. A., & Samrah, A. S. (2020). A new image encryption scheme based on hybrid chaotic maps. Complexity.
- Albahrani, E. A., & Alshekly, T. K. (2017). New chaotic substation and permutation method for image encryption. International Journal of Applied Information Systems, 12(4), 34-39.
- Teng, L., Wang, X., & Meng, J. (2018). A chaotic color image encryption using integrated bit-level permutation. Multimedia Tools and Applications, 77(6), 6883-6896.
- Benlashram, Arwa, et al. "A novel approach of image encryption using pixel shuffling and 3D chaotic map." Journal of Physics: Conference Series. Vol. 1447. No. 1. IOP Publishing, 2020.
- Zhu, S., & Zhu, C. (2020). Secure image encryption algorithm based on hyper chaos and dynamic DNA coding. Entropy, 22(7), 772.
- Murali, P., & Sankaradass, V. (2019). An efficient space filling curve based image encryption. Multimedia Tools and Applications, 78(2), 2135-2156.
- Zhang, X., Wang, L., Zhou, Z., & Niu, Y. (2019). A chaos-based image encryption technique utilizing hilbert curves and H-fractals. IEEE Access, 7, 74734-74746.
- Shahna, K. U., & Mohamed, A. (2018, July). An image encryption technique using logistic map and Z-order curve. In 2018 International Conference on Emerging Trends and Innovations In Engineering And Technological Research IEEE (ICETIETR) (pp. 1-6).
- Raza, S. F., & Satpute, V. (2019). A novel bit permutation-based image encryption algorithm. Nonlinear Dynamics, 95(2), 859-873.
- Kari, A. P., Navin, A. H., Bidgoli, A. M., & Mirnia, M. (2021). A new image encryption scheme based on hybrid chaotic maps. Multimedia Tools and Applications, 80(2), 2753-2772.
- Farah, M. A., Farah, A., & Farah, T. (2020). An image encryption scheme based on a new hybrid chaotic map and optimized substitution box. Nonlinear Dynamics, 99(4), 3041-3064.
- Wu, J., Liao, X., & Yang, B. (2018). Image encryption using 2D Hénon-Sine map and DNA approach. Signal Processing, 153, 11-23.
- Sheela, S. J., Suresh, K. V., & Tandur, D. (2017). A novel audio cryptosystem using chaotic maps and DNA encoding. Journal of Computer Networks and Communications.
- Yousif, S. F. (2018, January). Grayscale image confusion and diffusion based on multiple chaotic maps. In 2018 1st International scientific conference of engineering sciences-3rd scientific conference of engineering science (ISCES) (pp. 114-119).
- Patro, K. A. K., Soni, A., Netam, P. K., & Acharya, B. (2020). Multiple grayscale image encryption using cross-coupled chaotic maps. Journal of Information Security and Applications, 52, 102470.
- Lu, Q., Zhu, C., & Deng, X. (2020). An efficient image encryption scheme based on the LSS chaotic map and single S-box. IEEE Access, 8, 25664-25678.
- Belazi, A., Abd El-Latif, A. A., & Belghith, S. (2016). A novel image encryption scheme based on substitution-permutation network and chaos. Signal Processing, 128, 155-170.
- Diab, H. (2018). An efficient chaotic image cryptosystem based on simultaneous permutation and diffusion operations. IEEE access, 6, 42227-42244.
- Benlashram, A., Al-Ghamdi, M., AlTalhi, R., & Laabidi, P. K. (2020). A novel approach of image encryption using pixel shuffling and 3D chaotic map. In Journal of Physics: Conference Series (Vol. 1447, No. 1, p. 012009). IOP Publishing.
- Girdhar, A., Kapur, H., & Kumar, V. (2021). A novel grayscale image encryption approach based on chaotic maps and image blocks. Applied Physics B, 127(3), 1-12.
- Abdelfatah, R. I., Nasr, M. E., & Alsharqawy, M. A. (2020). Encryption for multimedia based on chaotic map: Several scenarios. Multimedia Tools and Applications, 79(27), 19717-19738.
- Idrees, B., Zafar, S., Rashid, T., & Gao, W. (2020). Image encryption algorithm using S-box and dynamic Hénon bit level permutation. Multimedia Tools and Applications, 79(9), 6135-6162.
- Arab, A., Rostami, M. J., & Ghavami, B. (2019). An image encryption method based on chaos system and AES algorithm. The Journal of Supercomputing, 75(10), 6663-6682.
- Zhu, S., Zhu, C., Fu, Y., Zhang, W., & Wu, X. (2020). A secure image encryption scheme with compression-confusion-diffusion structure. Multimedia Tools and Applications, 79(43), 31957-31980.
- Cheng, G., Wang, C., & Chen, H. (2019). A novel color image encryption algorithm based on hyperchaotic system and permutation-diffusion architecture. International Journal of Bifurcation and Chaos, 29(09), 1950115.
- Hosny, K. M. (Ed.). (2020). Multimedia security using chaotic maps: principles and methodologies (Vol. 884). Springer Nature.
- Nkandeu, Y. P. K., & Tiedeu, A. (2019). An image encryption algorithm based on substitution technique and chaos mixing. Multimedia Tools and Applications, 78(8), 10013-10034.
- Zhang, X., Zhou, Z., & Niu, Y. (2018). An image encryption method based on the feistel network and dynamic DNA encoding. IEEE Photonics Journal, 10(4), 1-14.
- Guesmi, R., Farah, M. A. B., Kachouri, A., & Samet, M. (2016). A novel chaos-based image encryption using DNA sequence operation and Secure Hash Algorithm SHA-2. Nonlinear Dynamics, 83(3), 1123-1136.
- Slimane, N. B., Bouallegue, K., & Machhout, M. (2017). Designing a multi-scroll chaotic system by operating Logistic map with fractal process. Nonlinear Dynamics, 88(3), 1655-1675.
- Li, C., Luo, G., & Li, C. (2019). An Image Encryption Scheme Based on the Three-dimensional Chaotic Logistic Map. Int. J. Netw. Secur., 21(1), 22-29.


