A Semi-Blind Watermarking of Color Images Using Slant Transform, DWT and SVD
Автор: Roshan Koju, Shashidhar Ram Joshi
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 3 vol.9, 2017 года.
Бесплатный доступ
This paper presents a robust watermarking for still digital images based on a Slant transform, discrete wavelet transforms and Singular Value Decomposition (SVD). The cover image is transformed using discrete wavelet transform and singular value decomposition while watermark image is transformed using slant transform. It is watermarked by replacing singular values of the high-frequency and low-frequency component of an original image by that of slant transformed watermarks. Experimental results show that our method guarantees the robust resistance against no attack and the robustness against common image processing attacks such as JPEG compression, cropping, histogram equalization, sharpening etc.
Slant transform, double watermarking, copyright protection, JPEG compression, geometric attacks
Короткий адрес: https://sciup.org/15014174
IDR: 15014174
Текст научной статьи A Semi-Blind Watermarking of Color Images Using Slant Transform, DWT and SVD
Published Online March 2017 in MECS
Application and popularization of multimedia technologies and computer networks have made duplication and distribution much easier for multimedia contents. The digital media (such as video, image, audio, and text) can be modified easily by attackers who can claim their ownership. Then copyright protection of intellectual properties has become an important and challenging task. One way for copyright protection is digital watermarking. It is a pattern of bits inserted into a digital image, audio, video or text file that identifies the file's copyright information [1]. Watermarking is done either in spatial domain or frequency domain. Spatial domain methods have less complexity because we do not use any transform, but these are not robust in nature against attacks. Transform domain techniques of watermarking are highly robust than spatial domain watermarking techniques. This happens because the watermarked image is inversely transformed and watermark is irregularly over the image and it becomes difficult for the attacker to read or modify the image[2].
Robustness, transparency (invisibility), payload size and security are four essential factors to determine the quality of watermarking scheme[3]. Robustness means that the embedded watermarks cannot be removed by intentional or unintentional attacks. Although robustness can be obtained based on significant modifications to the host data, such modifications are noticeable and thus do not satisfy the requirement of transparency. Thus, there is a trade-off between robustness and transparency. On increasing robustness, transparency decreases and vice versa [3]. So, the new algorithm to embed the watermark in digital data is to be developed which provide strong robustness and at the same time good transparency.
In this paper, the fusion of Slant transform, discrete wavelet transform (DWT) and Singular value decomposition (SVD) approaches is proposed. This paper is organized as follows: Section II discusses a brief review of some of the works available. Section III presents the proposed method. Section IV throws light on the experimental results and comparison of results with works whereas the summary of results and the conclusion is presented in Section V.
-
II. Related works
Very few works have been done with slant transform. First work was carried out by Xunzhan Zhu, Anthony T.S. Ho [4]. They transformed watermark image using slant transform. Such transformed image was used to replace the middle band frequencies of the cover image. This method was found to be robust against various geometric attacks. Similarly, Anthony T.S. Ho, Xunzhan Zhu and Jun Shen [5] also used slant transform to embed the watermark. They also transformed watermark image through slant transform then the resultant image was used to replace the middle frequencies of the cover image. This method was found robust against various geometric attacks. Alimohammad Latif [6] also used slant transform to watermark cover image. The author first converted the cover image into blocks. These blocks were passed through slant transform. Watermark was inserted into middle band frequencies using correlation. This method was found to transparent up to 33.956 dB. The method survived various geometric attacks. Amy Tun and Yadana Thein [7] used hybrid transform. They used discrete cosine transform in addition with LWT. They embedded the watermark using pseudo-random noise (PN) sequence.
The method was blind and spread spectrum based. Their watermarked image had transparency (Peak Signal to noise ratio (PSNR) value) up to 47.3425 dB.
-
C. N. Sujatha and P. Satyanarayana [8] applied DCT, DWT and SVD for color image watermarking. They embedded watermark image in singular values of DCT and DWT transformed RGB image. Their method was nonblind and needs watermark and cover image during extraction as well. Prescribed method had poor robustness though had good imperceptibility.
Ghazali Bin Sulong and et al [9] used the hybrid domain to watermark color images. They converted RGB color space into YCbCr color space before embedding the watermark. They used DWT and canny edge detection method. The prescribed method does not have good robustness as imperceptibility.
Hongshou Yan and Weimin Yang [10] used Hadamard transform (HT) in association with DWT to embed watermark. They embedded binary watermark image into the blue or green component of DWT and HT transformed cover image. Their prescribed method was robust to the common signal processing techniques.
In [11], author separated color components into R, G and B. They applied DWT to R component only up to two level. Then in HH sub-band, DCT was applied. Finally, SVD was used to embed the watermark. Performance was tested with various geometric attack and results found to be satisfactory. In [12] authors applied DWT to cover image first. They applied SVD to LL sub-band of and then applied DCT in U and V part of the result of SVD. Method applied was blind and survived Jpeg and Jpeg 2000 compression attack. In [13] original image is rearranged using zigzag sequence and DWT was applied in rearranged sequence. Then DCT and SVD are applied in all high bands LH, HL, HH. Watermarks are embedded modifying singular values of modified cover image. The Performance was tested with various geometric attacks and performs well. In [14] hybrid DWT and DCT based method was proposed. In [15] DCT wavelet transform of size 256*256 is generated using existing well known orthogonal transform DCT of dimension 128*128 and 2*2. This DCT Wavelet transform is used in combination with the orthogonal transform DCT and SVD to increase the robustness of watermarking. HL2 sub-band is selected for watermark embedding. The Performance of the proposed watermarking scheme is evaluated against various image processing attacks.
-
III. Concepts
This section details the proposed semi-blind watermarking scheme for copyright protection of digital images. The following subsections present the steps involved in the watermark embedding and extraction processes along with a brief description about the Slant transform, DWT and SVD
-
A. Slant transform
Slant transform is derived from saw tooth waveforms. A slant transform matrix has a constant basis vector corresponding to zero sequency and slant basis vector basis vectors monotonically decreases with sequency in the constant step from maximum to minimum. The matrix has sequency property and high energy compaction property [16]. The lowest order of slant matrix is 2 and 2 X 2 matrix is identical to Hadamard matrix. Twodimensional slant transform pair is given by
-
[f] = [S][F][S] T (1)
[ F ] = [ S ] T [ f ][ S ]
The Slant transform is a member of the orthogonal transforms. It has a constant function for the first row, and has a second row which is a slant function of the column index [4].
-
B. Discrete wavelet transform (DWT)
DWT can be used to identify the areas in host image to embed watermark effectively as it has excellent spatio frequency localization properties [11]. It decomposes an image into four non-overlapping multi-resolution subbands: LL read as low-low, is a lower resolution approximation image; HL read as high-low, is a horizontal component LH read as low-high, is a vertical component and HH, read as high- high, is the diagonal component of given image. LL represents the coarse-scale DWT coefficients while LH, HL and HH represent the fine-scale of DWT coefficients. To obtain the next coarser scale of wavelet coefficients, the sub-band LL is further processed until some final scale N is reached. In general, most of the image energy is concentrated at LL sub bands. Thus embedding watermarks in these coefficient sets may decrease image quality significantly. Embedding in the high-frequency coefficient sets could increase robustness significantly. HH sub-bands include the edges and textures of the image. Changes in such coefficients are not visible to human eye. Thus embedding the watermark in HH allows the watermark to be embedded without being perceived by the human eye [17].
-
C. SVD
Singular values of the image give very good stability. When a small value is added, it does not result too much variation. Hence Singular Value decomposition (SVD) in linear algebra is used to solve many mathematical problems [18].
Every real matrix A can be decomposed into product of three matrices
A = U I VT (2)
Where U and V are orthogonal matrices such that, UUT =1 and VVT = 1and ∑ is summation of diagonal entries λ1, λ2·gives the singular vectors of A. These diagonal entries are called as Singular Values of A and the decomposition is called as ‘Singular Value Decomposition’. Singular Values specifies the luminance of an image layer while corresponding pair of singular vectors specifies the geometry of the image layer [13].
In our previous work [19] Y channel of YCbCr performed better in image watermarking, so we chose the same channel here for color image watermarking.
-
IV. Proposed Methods
This paper proposes a new color image watermarking technique which is based on the Slant transform with DWT and SVD. Watermark image is processed through slant transform. Such transformed watermark is passed through SVD. On the other hand, Y component of the cover image is passed through DWT and SVD. Singular values of the cover image are replaced by that of watermark image. We used the cover image of size 512 x 512 and watermark image of size 32 x 32. Algorithm is realized in Matlab 2015 b.
Detail watermarking process and extraction processes are as follows:
-
A. Watermark embedding process
-
1. Read RGB color cover image C
-
2. Convert C into YCbCr color space
-
3. Separate Y, Cb and Cr components of color image
-
4. Get Y channel 2D-DWT transformed. Apply 2D-DWT four times on HH sub band.
-
5. Apply svd on HH4 to obtain singular values Sc
-
6. Read watermark image W
-
7. Get Ws by dividing W into nonoverlapping blocks and apply slant transform
-
8. Apply SVD on Ws to obtain singular values Sw
-
9. Embed watermark by replacing Sc by Sw using (3)
-
10. Reconstruct HH4 using inverse SVD
-
11. Construct watermarked image in YCbCr color space using inverse 2D-DWT function four times
-
12. Reconstruct watermarked RGB image W’ from YCbCr image
ScNEW = a * Sw (3)
-
B. Watermark extraction process
-
1. Read watermarked RGB image W’
-
2. Convert W’ into YCbCr color space
-
3. Separate Y, Cb and Cr components of color image
-
4. Get Y channel 2D-DWT transformed. Apply 2D-DWT further four times to HH sub band.
-
5. Apply SVD on HH4 to obtain singular values S’c
-
6. Read watermark image W
-
7. Get Ws by dividing W into nonoverlapping blocks and apply slant transform
-
8. Apply SVD on Ws to obtain values Uw and Vw
-
9. Retrieve watermark bits Sr using following
-
10. Reconstruct recovered watermark image using Uw, Sr and Vw reverse SVD and inverse slant transform
equation
Sr = S ’ c / a (4)
-
V. Experimental Results
In this section, experimental results of the proposed method are presented. Algorithm is realized in Matlab. The performance is evaluated using on Peak Signal to Noise Ratio (PSNR) and Normalized Cross-Correlation (NC). RGB color images (i.e., Lena, F-16 flight, pen, Zelda and boat) have been used as cover images and a 32×32 gray image has been used a watermark. Cover image and watermark images are shown in figure 1. Two major tests, imperceptibility and robustness are conducted with varying values of scaling factor α. Imperceptibility is a measure of transparency.

(c) (d)
w
(e)
Fig.1. Test images and watermark image (a) Mandrill (b) boat (c) Lena (d) F-16 Flight (e) Watermark.
The peak signal to noise ratio (PSNR) is typically used as a measure of the quality of a watermarked image. If W is original image and W’ is modified image then PSNR and NC are calculated using following relations:
PSNR = 10 log10
MSE
= z
[W ( u , v ) - W '( u , v )] N 2
(255*255) *3
MSE ( red ) + MSE ( blue ) + MSE ( green )
NC = ZZ W ( u , v )*W'(u,v)]
" VZZW(u,v)2 * VZZW?(u v)2
The efficiency of the proposed system is illustrated by showing PSNR value.
To determine the optimum value of α, it is varied from 0.01 to 0.1. Corresponding values of PSNR are recorded in table 1. Following figure 2 shows the watermarked image at different values of α.

(a)

(b)

(c)

(d)
Fig.2. Watermarked test images at different values of α.
Imperceptibility Test
To determine the better value of gain factor α, it is varied from 0.001 to 0.1. Corresponding values of PSNR are recorded in table 1. Maximum transparency recorded was 46.2956dB for F16 image at α=0.06 and minimum was 43.0161 dB for Mandrill image at α=0.1. Watermark image is extracted from watermarked image. Following table 2 NC values of extracted watermark images. Extracted watermarks are tabulated in table 3.
Table 1. PSNR values of different test images for Imperceptibility test (of Cover Image vs. Watermarked Image) at various values of α
|
α |
Mandrill |
Lena |
F 16 |
Boat |
|
0.01 |
49.6445 |
61.6895 |
62.061 |
62.917 |
|
0.02 |
50.2213 |
59.8283 |
60.1331 |
60.2002 |
|
0.03 |
50.54705 |
56.9924 |
57.1822 |
57.0009 |
|
0.04 |
50.71645 |
54.494 |
54.6186 |
54.4002 |
|
0.05 |
52.415 |
52.4389 |
52.5277 |
52.3194 |
|
0.06 |
49.47405 |
50.7319 |
50.7995 |
50.61 |
|
0.07 |
48.75135 |
49.2846 |
49.3384 |
49.1675 |
|
0.08 |
48.84135 |
48.0332 |
48.0776 |
47.9232 |
|
0.09 |
46.93985 |
46.9332 |
46.9709 |
46.8305 |
|
0.1 |
46.01685 |
45.9532 |
45.9859 |
45.8574 |
Table 2. NC values of different test images for Imperceptibility test (of Cover Image vs. Watermarked Image) at various values of α
|
α |
Mandrill |
Lena |
F-16 |
Boat |
|
0.01 |
0.9999 |
1 |
1 |
1 |
|
0.02 |
0.9999 |
1 |
1 |
1 |
|
0.03 |
0.9999 |
1 |
1 |
1 |
|
0.04 |
0.9999 |
1 |
1 |
1 |
|
0.05 |
0.9999 |
1 |
0.9999 |
0.9999 |
|
0.06 |
0.9999 |
0.9999 |
0.9999 |
0.9999 |
|
0.07 |
0.9999 |
0.9999 |
0.9999 |
0.9999 |
|
0.08 |
0.9998 |
0.9999 |
0.9999 |
0.9999 |
|
0.09 |
0.9998 |
0.9999 |
0.9998 |
0.9998 |
|
0.1 |
0.9998 |
0.9999 |
0.9998 |
0.9998 |
Table 3. Extracted watermarks at different values of α
|
α |
Mandrill |
Lena |
F-16 |
Boat |
|
0.01 |
w |
|||
|
0.02 |
w |
w |
w |
w |
|
0.03 |
w |
w |
w |
w |
|
0.04 |
w |
w |
w |
w |
|
0.05 |
w |
w |
w |
w |
|
0.06 |
w |
w |
w |
|
|
0.07 |
w |
w |
w |
w |
|
0.08 |
w |
w |
w |
w |
|
0.09 |
w |
w |
w |
w |
|
0.1 |
w |
w |
w |
w |
It is clear from observations that proposed method is able to detect and identify the embedded watermarks with accuracy.
Robustness tests
Robustness against geometric attacks
To evaluate the response of the watermarking scheme to geometric attacks, watermarked images were passed through histogram equalization, median filtering sharpening, negative and blurring attacks. Figure 3 shows the geometrically attacked watermarked images at different scaling factor α. Their corresponding normalized correlation is shown in table 4 and BER values are shown in table 5. Table 6 shows the extracted watermarks from watermarked images after geometrically attacked under different scaling factors.


(b)

(c)

(d)
Fig.3. Different attacks on different watermarked images at α=0.07.(a)histogram equalized Lena (b) Sharpened Boat (c)Negative F-16 Flight (d) Median Filtered Mandrill
Robustness test: general cropping attacks
To evaluate the response of the watermarking scheme to cropping, watermarked images were trimmed at different places as shown in figure 4 below.



(a)

(b)
(a) (b)

(c) (d)
(c)

(e)
(d)

(e)
Fig.5. Variously compressed watermarked images with different qualities (a) Q=10 (b) Q=50 (c) Q=75 (d) Q=100 (e)Jpeg 2000
Fig.4. Cropped watermarked Lena images at α=0.07.(a) Center trimmed (b) Down trimmed (c)Up trimmed (d) Left trimmed (e) right trimmed
Their corresponding normalized correlation is shown in table 7 and BER values are shown in table 8. Table 9 shows the extracted watermarks from watermarked images after cropping attacked under different scaling factors.
Robustness test: general compression
To evaluate the response of the watermarking scheme to JPEG compression, watermarked images were compressed under different scaling factors and different JPEG qualities Qs: 10, 50, 75 and 100. Figure 5 shows the JPEG compression of the various watermarked images at different scaling factor. Their corresponding normalized correlation is shown in table 10 and BER values are shown in table 11. Extracted watermarks are tabulated in table 12.
Robustness test: noise attack


(c)

(b)

(d)
Table 4. NC of original and extracted watermarks on normal geometric attacks
|
Image |
α |
Normal Blur |
Negative |
Sharpening |
Histogram Equalization |
Median Filtering |
|
Lena |
0.03 |
0.9308 |
0.958 |
0.9587 |
0.9496 |
0.9561 |
|
0.07 |
0.1133 |
0.9941 |
0.994 |
0.9912 |
0.9938 |
|
|
0.1 |
0.9936 |
0.9963 |
0.9963 |
0.9938 |
0.996 |
|
|
Boat |
0.03 |
0.9247 |
0.9636 |
0.9666 |
0.9249 |
0.961 |
|
0.07 |
0.9846 |
0.9931 |
0.9935 |
0.9767 |
0.9923 |
|
|
0.1 |
0.9927 |
0.9964 |
0.9963 |
0.986 |
0.9961 |
|
|
F-16 |
0.03 |
0.9265 |
0.9651 |
0.9675 |
0.9709 |
0.9617 |
|
0.07 |
0.9891 |
0.9964 |
0.9967 |
0.9947 |
0.9959 |
|
|
0.1 |
0.9951 |
0.9981 |
0.9981 |
0.9936 |
0.9978 |
|
|
Mandrill |
0.03 |
0.1426 |
0.9126 |
0.9089 |
0.9115 |
0.9119 |
|
0.07 |
0.956 |
0.9846 |
0.9844 |
0.9829 |
0.9832 |
|
|
0.1 |
0.9761 |
0.9918 |
0.9916 |
0.9904 |
0.9913 |
Table 5. BER of original and extracted watermarks on normal geometric attacks
|
Image |
α |
Normal Blur |
Negative |
Sharpening |
Histogram Equalization |
Median Filtering |
|
Lena |
0.03 |
0.1436 |
0.1279 |
0.125 |
0.126 |
0.126 |
|
0.07 |
0.1133 |
0.0947 |
0.0947 |
0.1035 |
0.0898 |
|
|
0.1 |
0.1016 |
0.0879 |
0.0898 |
0.0977 |
0.0898 |
|
|
Boat |
0.03 |
0.1396 |
0.124 |
0.126 |
0.1357 |
0.127 |
|
0.07 |
0.1201 |
0.0967 |
0.0957 |
0.1172 |
0.1006 |
|
|
0.1 |
0.1016 |
0.0918 |
0.0879 |
0.1016 |
0.0928 |
|
|
F-16 |
0.03 |
0.1348 |
0.1152 |
0.1143 |
0.124 |
0.1191 |
|
0.07 |
0.1084 |
0.0908 |
0.0918 |
0.0811 |
0.0996 |
|
|
0.1 |
0.1006 |
0.0781 |
0.0781 |
0.0898 |
0.0801 |
|
|
Mandrill |
0.03 |
0.1426 |
0.1338 |
0.1328 |
0.1338 |
0.1338 |
|
0.07 |
0.127 |
0.1025 |
0.1025 |
0.1064 |
0.1045 |
|
|
0.1 |
0.123 |
0.0986 |
0.0977 |
0.0986 |
0.0996 |
Table 6. Extracted watermarks on normal geometric attacks
|
Image |
α |
Histogram Equalization |
Normal Blur |
Median Filtering |
Negative |
Sharpening |
||
|
Lena |
0.03 |
w |
w |
W |
w |
w |
||
|
0.07 |
w |
w |
w |
w |
w |
|||
|
0.1 |
w |
w |
w |
w |
w |
|||
|
Boat |
0.03 |
w |
^ |
w |
^ |
w |
||
|
0.07 |
w |
w |
w |
w |
||||
|
0.1 |
V? |
w |
w |
w |
w |
|||
|
F-16 |
0.03 |
w |
ж |
w |
w |
w |
||
|
0.07 |
w |
w |
w |
w |
w |
|||
|
0.1 |
w |
w |
w |
w |
||||
|
Mandrill |
0.03 |
w |
w |
w |
||||
|
0.07 |
w |
W |
w |
w |
w |
|||
|
0.1 |
w |
w |
w |
w |
||||
Table 7. NC values on cropping attacks
|
Image |
α |
Cropping |
Cropping |
Cropping UP |
Cropping |
Cropping RIGHT |
|
Center |
DOWN |
LEFT |
||||
|
Lena |
0.03 |
0.8831 |
0.9669 |
0.9646 |
0.9613 |
0.966 |
|
0.07 |
0.9538 |
0.9954 |
0.9959 |
0.9956 |
0.9956 |
|
|
0.1 |
0.9551 |
0.9972 |
0.9975 |
0.9973 |
0.9973 |
|
|
Boat |
0.03 |
0.879 |
0.9779 |
0.9656 |
0.9687 |
0.9742 |
|
0.07 |
0.9424 |
0.9936 |
0.9958 |
0.9943 |
0.995 |
|
|
0.1 |
0.9519 |
0.9969 |
0.9974 |
0.9973 |
0.9973 |
|
|
F-16 |
0.03 |
0.8058 |
0.9818 |
0.9695 |
0.9763 |
0.975 |
|
0.07 |
0.8921 |
0.9989 |
0.9972 |
0.9981 |
0.9979 |
|
|
0.1 |
0.9017 |
0.9993 |
0.9985 |
0.9988 |
0.9988 |
|
|
Mandrill |
0.03 |
0.1309 |
0.1543 |
0.1289 |
0.1377 |
0.1572 |
|
0.07 |
0.1025 |
0.0977 |
0.1318 |
0.1104 |
0.1406 |
|
|
0.1 |
0.0986 |
0.0947 |
0.125 |
0.0967 |
0.1396 |
Table 8. BER of original and extracted watermarks on cropping attacks
|
Image |
α |
Cropping center |
Cropping DOWN |
Cropping UP |
Cropping LEFT |
Cropping RIGHT |
|
Lena |
0.03 |
0.1484 |
0.1289 |
0.126 |
0.1318 |
0.1279 |
|
0.07 |
0.1396 |
0.0918 |
0.0938 |
0.0918 |
0.0898 |
|
|
0.1 |
0.1416 |
0.082 |
0.0811 |
0.0918 |
0.083 |
|
|
Boat |
0.03 |
0.1553 |
0.1172 |
0.125 |
0.125 |
0.1221 |
|
0.07 |
0.1436 |
0.0957 |
0.083 |
0.0947 |
0.0898 |
|
|
0.1 |
0.1426 |
0.0869 |
0.0801 |
0.0869 |
0.0771 |
|
|
F-16 |
0.03 |
0.1641 |
0.1064 |
0.1182 |
0.1094 |
0.1143 |
|
0.07 |
0.1543 |
0.0693 |
0.0879 |
0.0752 |
0.085 |
|
|
0.1 |
0.1504 |
0.0654 |
0.0742 |
0.0625 |
0.0732 |
|
|
Mandrill |
0.03 |
0.9249 |
0.81 |
0.9368 |
0.9103 |
0.8294 |
|
0.07 |
0.9865 |
0.99 |
0.9402 |
0.9854 |
0.9464 |
|
|
0.1 |
0.9921 |
0.9947 |
0.9671 |
0.9935 |
0.9662 |
Table 9. Extracted watermarks on cropping attacks
|
Image |
α |
Cropping center |
Cropping DOWN |
Cropping UP |
Cropping LEFT |
Cropping RIGHT |
|
0.03 |
ж |
w |
w |
w |
||
|
Lena |
0.07 |
w |
w |
w |
w |
w |
|
0.1 |
w |
w |
w |
w |
w |
|
|
0.03 |
w |
w |
w |
w |
w |
|
|
Monarch |
0.07 |
w |
w |
w |
w |
w |
|
0.1 |
w |
w |
w |
w |
w |
|
|
0.03 |
X |
w |
w |
w |
||
|
Boat |
0.07 |
w |
w |
w |
w |
|
|
0.1 |
w |
w |
w |
w |
w |
|
|
0.03 |
ж |
w |
w |
w |
||
|
F-16 |
0.07 |
w |
w |
w |
w |
|
|
0.1 |
w |
w |
w |
w |
|
Mandrill |
0.03 |
w |
ж |
|||
|
0.07 |
w |
w |
w |
w |
w |
|
|
0.1 |
w |
w |
w |
w |
w |
Table 10. NC values of extracted watermark from different Jpeg compressed images
|
Image |
α |
10 |
50 |
75 |
100 |
Jpeg 2000 |
|
Lena |
0.03 |
0.8059 |
0.7171 |
0.8325 |
0.9561 |
0.9563 |
|
0.07 |
0.8716 |
0.853 |
0.9761 |
0.9939 |
0.994 |
|
|
0.1 |
0.8823 |
0.9897 |
0.9904 |
0.9963 |
0.9964 |
|
|
Monarch |
0.03 |
0.7284 |
0.8218 |
0.8887 |
0.9746 |
0.9737 |
|
0.07 |
0.7559 |
0.8933 |
0.9665 |
0.9944 |
0.9944 |
|
|
0.1 |
0.7394 |
0.9542 |
0.9905 |
0.9982 |
0.9983 |
|
|
Boat |
0.03 |
0.6405 |
0.7621 |
0.7894 |
0.9623 |
0.963 |
|
0.07 |
0.6351 |
0.8558 |
0.9855 |
0.993 |
0.9932 |
|
|
0.1 |
0.7369 |
0.9855 |
0.9958 |
0.9964 |
0.9965 |
|
|
F-16 |
0.03 |
0.6629 |
0.8805 |
0.9058 |
0.963 |
0.9637 |
|
0.07 |
0.8082 |
0.9869 |
0.9915 |
0.9962 |
0.9962 |
|
|
0.1 |
0.9476 |
0.9804 |
0.9949 |
0.9979 |
0.998 |
|
|
Mandrill |
0.03 |
0.7293 |
0.7512 |
0.8191 |
0.9114 |
0.9125 |
|
0.07 |
0.7316 |
0.9036 |
0.947 |
0.9845 |
0.9843 |
|
|
0.1 |
0.771 |
0.9595 |
0.9741 |
0.9917 |
0.9918 |
Table 11. BER values of extracted watermark from different Jpeg compressed images
|
Image |
α |
10 |
50 |
75 |
100 |
Jpeg 2000 |
|
Lena |
0.03 |
0.1602 |
0.1709 |
0.1553 |
0.1289 |
0.125 |
|
0.07 |
0.1563 |
0.1572 |
0.1367 |
0.0947 |
0.0928 |
|
|
0.1 |
0.1582 |
0.1172 |
0.1182 |
0.0879 |
0.0869 |
|
|
Boat |
0.03 |
0.1982 |
0.165 |
0.1572 |
0.127 |
0.126 |
|
0.07 |
0.2012 |
0.1543 |
0.1035 |
0.0986 |
0.0957 |
|
|
0.1 |
0.1699 |
0.0664 |
0.0879 |
0.0898 |
0.0898 |
|
|
F-16 |
0.03 |
0.1904 |
0.1475 |
0.1436 |
0.1182 |
0.1172 |
|
0.07 |
0.1602 |
0.0693 |
0.0771 |
0.0938 |
0.0938 |
|
|
0.1 |
0.1289 |
0.0635 |
0.0596 |
0.0781 |
0.0801 |
|
|
Mandrill |
0.03 |
0.1689 |
0.1641 |
0.1523 |
0.1328 |
0.1328 |
|
0.07 |
0.1689 |
0.1318 |
0.1201 |
0.1035 |
0.1025 |
|
|
0.1 |
0.166 |
0.1201 |
0.1152 |
0.1006 |
0.0986 |
Table 12. Extracted watermarks from different Jpeg compressed images
|
Image |
α |
Q=10 |
Q=50 |
Q=75 |
Q=100 |
Jpeg 2000 |
|
0.03 |
w |
w |
||||
|
Lena |
0.07 |
w |
w |
|||
|
0.1 |
w |
w |
w |
|||
|
0.03 |
w |
w |
||||
|
Monarch |
0.07 |
w |
w |
w |
||
|
0.1 |
w |
w |
w |
|||
|
0.03 |
w |
w |
||||
|
Boat |
0.07 |
w |
w |
w |
||
|
0.1 |
w |
w |
w |
w |
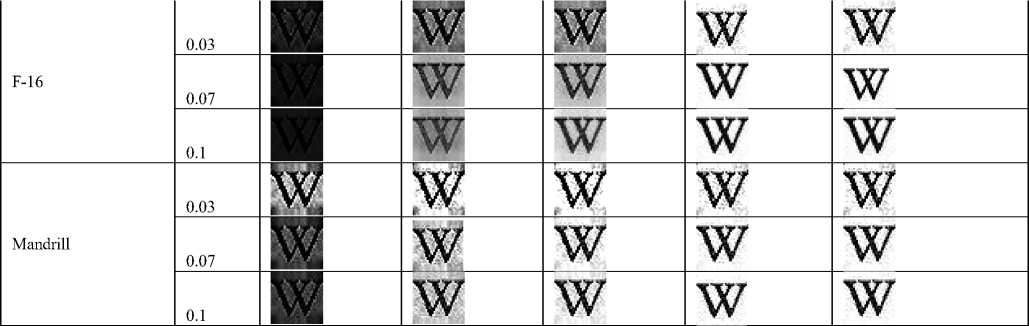
Table 13. NC values of extracted watermark from different noise attacked images
|
Image |
α |
Gaussian |
Salt and Pepper |
||
|
1% |
2% |
1% |
2% |
||
|
Lena |
0.03 |
0.6559 |
0.6203 |
0.7598 |
0.6869 |
|
0.07 |
0.8661 |
0.7953 |
0.9297 |
0.8926 |
|
|
0.1 |
0.9092 |
0.8562 |
0.9669 |
0.9343 |
|
|
Boat |
0.03 |
0.6557 |
0.6098 |
0.7775 |
0.7027 |
|
0.07 |
0.8542 |
0.7714 |
0.9437 |
0.8909 |
|
|
0.1 |
0.9169 |
0.8521 |
0.9639 |
0.9385 |
|
|
F-16 |
0.03 |
0.6674 |
0.6164 |
0.7896 |
0.6893 |
|
0.07 |
0.8404 |
0.7527 |
0.9392 |
0.8873 |
|
|
0.1 |
0.9093 |
0.8387 |
0.9691 |
0.9348 |
|
|
Mandrill |
0.03 |
0.6496 |
0.6123 |
0.7932 |
0.7124 |
|
0.07 |
0.8483 |
0.7597 |
0.9375 |
0.8904 |
|
|
0.1 |
0.9125 |
0.8553 |
0.9636 |
0.9359 |
|
Table 14. BER values of extracted watermark from different noise attacked images
|
Image |
α |
Gaussian |
Salt and Pepper |
||
|
1% |
2% |
1% |
2% |
||
|
Lena |
0.03 |
0.1816 |
0.1982 |
0.1611 |
0.1719 |
|
0.07 |
0.1367 |
0.1484 |
0.124 |
0.1348 |
|
|
0.1 |
0.1289 |
0.1396 |
0.1191 |
0.127 |
|
|
Boat |
0.03 |
0.1855 |
0.1982 |
0.1504 |
0.1689 |
|
0.07 |
0.1387 |
0.1553 |
0.125 |
0.1348 |
|
|
0.1 |
0.1299 |
0.1387 |
0.1162 |
0.125 |
|
|
F-16 |
0.03 |
0.1768 |
0.1943 |
0.1514 |
0.1729 |
|
0.07 |
0.1416 |
0.1602 |
0.127 |
0.1328 |
|
|
0.1 |
0.1328 |
0.1426 |
0.1172 |
0.126 |
|
|
Mandrill |
0.03 |
0.1807 |
0.1943 |
0.1494 |
0.166 |
|
0.07 |
0.1357 |
0.1631 |
0.127 |
0.1338 |
|
|
0.1 |
0.1309 |
0.1406 |
0.1221 |
0.1279 |
|
Table 15. Extracted watermarks from different noise attacked images
|
Image |
α |
Gaussian |
Salt and Pepper |
||
|
1% |
2% |
1% |
2% |
||
|
Lena |
0.03 |
w |
|||
|
0.07 |
w |
ж |
w |
||
|
0.1 |
w |
||||
|
Boat |
0.03 |
w |
ж |
||
|
0.07 |
ж |
w |
w |
||
|
0.1 |
w |
||||
|
F-16 |
0.03 |
Ж |
|||
|
0.07 |
w |
w |
w |
||
|
0.1 |
w |
w |
w |
||
|
Mandrill |
0.03 |
ж |
w |
я |
|
|
0.07 |
ж |
Comparison with other methods
In this section, we compared the performance of the proposed method with three other watermarking
approaches ( [20, 21]). The comparison is shown in tables 16, 17. Both approaches used images of 512 x 512 as cover image and 64 x 64 sized watermark image.
Table 16. Comparison with existing algorithm [20]
|
SN |
Parameter |
Existing method [20] |
Proposed |
|
1 |
Imperceptibility (PSNR) |
40.8811dB |
62.061dB |
|
Attacks (NC) |
1(NC) |
Proposed(NC) |
|
|
1 |
Jpeg 10 |
0.984005 |
-- |
|
2 |
Jpeg 50 |
0.768411 |
0.9897 |
|
3 |
Sharpening |
0.99701 |
0.9983 |
|
4 |
Center cropping |
0.94168 |
0.9631 |
|
5 |
Left side cropping |
0.911363 |
0.9991 |
|
6 |
Histogram Equalization |
0.943352 |
0.9947 |
|
7 |
down crop |
0.94168 |
0.9993 |
Table 17. Comparison with existing algorithm [21]
|
SN |
Parameter |
Existing method [21] |
Proposed |
||
|
1 |
Imperceptibility (PSNR) |
37.43 dB |
62.06 dB1 |
||
|
Attacks (NC) |
3(NC) |
3(BER) |
Proposed(NC) |
Proposed(BER) |
|
|
1 |
No attack |
-- |
-- |
1 |
0.0723 |
|
2 |
Jpeg 10 |
0.1432 |
0.3018 |
0.895 |
0.123 |
|
3 |
Jpeg 50 |
0.5487 |
0.1846 |
0.9897 |
0.0635 |
|
4 |
Jpeg 100 |
0.9596 |
0.0146 |
1 |
0.0205 |
|
5 |
Sharpening |
0.8782 |
0.0469 |
0.9983 |
0.0752 |
|
6 |
Blurring |
0.9598 |
0.0146 |
0.9951 |
0.1006 |
|
7 |
Gaussian Noise |
0.9598 |
0.0459 |
0.9169 |
0.1289 |
|
9 |
Left side cropping |
0.8571 |
0.0508 |
0.9991 |
0.0605 |
From above tables, we notice the following:
-
• The proposed method performs better than referenced literatures. Proposed method has better imperceptibility value than [20, 21]
-
• Existing methods [20 and [21] used single
watermark. In both cases, our proposed algorithm has better performance in any types of attacks except for blurring and noise. In blurring attack, [21] has better result than that of proposed method.
From the previous results, we may conclude that, overall, the proposed method has a better performance than the compared watermarking schemes [20, 21].
VI. Conclusion
In this paper, a robust, yet simple watermarking scheme based on the combination of Slant transform along with DWT and SVD domains is presented. Overall, the experimental results demonstrate that our scheme provides excellent robustness against multiple image attacks such as cropping, JPEG compression, histogram equalization, cropping, sharpening, blurring and negative attacks, etc. Besides, the quality of the watermarked image is satisfactory in terms of imperceptibility as the PSNR per watermarked image is over 62 dB.
Acknowledgement
We would like to thank fresh graduate Ph.D. fellowship program, University Grant Commission for providing the research grant. We are also thankful to Research Department, Institute of Engineering, Pulchowk, Tribhuvan University for support and guidance.
Список литературы A Semi-Blind Watermarking of Color Images Using Slant Transform, DWT and SVD
- S. H. Low, N. F. Maxemchuk, and A. M. Lapone, "Document identification for copyright protection using centroid detection," Communications, IEEE Transactions on, vol. 46, pp. 372-383, 1998.
- P. Singh and R. Chadha, "A survey of digital watermarking techniques, applications and attacks," International Journal of Engineering and Innovative Technology (IJEIT), vol. 2, pp. 165-175, 2013.
- H.-K. Pan, Y.-Y. Chen, and Y.-C. Tseng, "A secure data hiding scheme for two-color images," in Computers and Communications, 2000. Proceedings. ISCC 2000. Fifth IEEE Symposium on, 2000, pp. 750-755.
- A. T. Ho, X. Zhu, and J. Shen, "Slant transform watermarking for digital images," in Visual Communications and Image Processing 2003, 2003, pp. 1912-1920.
- X. Zhu and A. T. Ho, "A slant transform watermarking for copyright protection of satellite images," in Information, Communications and Signal Processing, 2003 and Fourth Pacific Rim Conference on Multimedia. Proceedings of the 2003 Joint Conference of the Fourth International Conference on, 2003, pp. 1178-1181.
- A. Latif and F. Rashidi, "A watermarking scheme based on the parametric slant-hadamard transform," Journal of Information Hiding and Multimedia Signal Processing, vol. 2, pp. 377-386, 2011.
- A. Tun and Y. Thein, "Digital Image Watermarking Scheme Based on LWT and DCT," International Journal of Engineering and Technology, vol. 5, p. 272, 2013.
- S. P. Murty, U. M. Bhaskar, and R. P. Kumar, "A Semi-Blind Reference Watermarking Scheme Using DWT-DCT-SVD for Copyright Protection," International Journal of Computer Science & Information Technology, vol. 4, p. 69, 2012.
- G. B. Sulong, H. Hasan, A. Selamat, M. Ibrahim, and S. Saparudin, "A New Color Image Watermarking Technique Using Hybrid Domain," International Journal of Computer Science Issues(IJCSI), vol. 9, 2012.
- H. Yan and W. Yang, "A Watermarking Algorithm Based on Wavelet and Hadamard Transform for Color Image," Journal of Software Engineering and Applications, vol. 6, p. 58, 2013.
- S. R. Hallur, S. Kuri, and G. H. Kulkarni, "Robust Digital Watermarking using DWT-DCT-SVD Algorithms for Color Image," International Journal of Current Engineering and Technology, vol. 5, pp. 2722-2726, August 2015.
- H.-T. Hu and L.-Y. Hsu, "Exploring DWT–SVD–DCT feature parameters for robust multiple watermarking against JPEG and JPEG2000 compression," Computers & Electrical Engineering, vol. 41, pp. 52-63, 2015.
- M. Rahman, "A DWT, DCT and SVD based watermarking technique to protect the image piracy," arXiv preprint arXiv:1307.3294, 2013.
- J. Guo, P. Zheng, and J. Huang, "Secure watermarking scheme against watermark attacks in the encrypted domain," Journal of Visual Communication and Image Representation, vol. 30, pp. 125-135, 2015.
- H. Kekre, T. Sarode, and S. Natu, "Hybrid Watermarking of Color Images using DCT-Wavelet, DCT and SVD," International Journal of Advances in Engineering & Technology, vol. 6, p. 769, 2013.
- P. Mali, B. Chaudhuri, and D. D. Majumder, "Some properties and fast algorithms of slant transform in image processing," Signal processing, vol. 9, pp. 233-244, 1985.
- A. Benoraira, K. Benmahammed, and N. Boucenna, "Blind image watermarking technique based on differential embedding in DWT and DCT domains," EURASIP Journal on Advances in Signal Processing, vol. 2015, p. 1, 2015.
- C.-q. Yin, L. Li, A.-q. Lv, and L. Qu, "Color image watermarking algorithm based on DWT-SVD," in Automation and Logistics, 2007 IEEE International Conference on, 2007, pp. 2607-2611.
- R. Koju and S. R. Joshi, "Comparative Analysis of Color Image Watermarking Technique in RGB, YUV, and YCbCr Color Channels," Nepal Journal of Science and Technology, vol. 15, pp. 133-140, 2015.
- M. lee and O.-J. Kwon, "Color Image Watermarking Based on DS-CDMA Using Hadamard Kernel," IEEE explore, 2008.
- D. K. Ramanjaneyulu, D. P. Pandarinath, and B. R. Reddy, "Robust and Oblivious Watermarking based on Swapping of DCT Coefficients," International Journal of Application or Innovation in Engineering & Management (IJAIEM), vol. 2, pp. 445-452, 2013.


