An Efficient Embedding Technique in Image Steganography Using Lucas Sequence
Автор: Prithwish Das, Supriyo Ray, Atanu Das
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 9 vol.9, 2017 года.
Бесплатный доступ
Image steganography have been observed as one of the useful techniques to prevent unintended users to understand what information has been communicated over the network. Many crucial methods of image steganography include Discrete Cosine Transformation (DCT) based approaches. In this paper an efficient algorithm in image steganography is proposed extending DCT based approaches and incorporating number theory. The existing DCT algorithm is modified to increase randomness in the embedding technique with the help of Lucas sequence specifically. The effectiveness of the proposed method has been evaluated by computing Mean Square Error (MSE) and Peak Signal to Noise Ratio (PSNR). Results show that the proposed method has higher embedding capacity and increases a significant level of security by using Lucas sequence in addition to the advantages provided by existing DCT algorithm.
Discrete Cosine Transformation, Image Steganography, Lucas Sequence, Frequency Domain Data Hiding
Короткий адрес: https://sciup.org/15014229
IDR: 15014229
Текст научной статьи An Efficient Embedding Technique in Image Steganography Using Lucas Sequence
Published Online September 2017 in MECS
The process of hiding information and an effort to hide the existence of the embedded information is called Steganography. This new method of information hiding technique is becoming quite popular in a number of application areas recently [1, 3, 5]. Digital audio, video, and pictures are now a day’s provided with distinguishing but imperceptible marks, which may contain any hidden copyright notice or serial number or even help to prevent unauthorized copying directly. The goal of steganography is to avoid any kind of suspicion so that the existence of a hidden message can be drawn. It plays a better role of securing message than cryptography which only hides the content of the message not the existence of the message. A carrier is used to hide the original message such that any changes so occurred in the carrier are not observable [7]. Steganography is a useful method that allows secret transmission of information over and over the communications channel. When secret image is combined with the carrier image, it gives the hidden image or stego image. Suitable embedding algorithm is used to hide the secret image. This hidden image is difficult to detect without a suitable extraction algorithm.
In terms of development, there are two main algorithms in steganography. One is embedding algorithm another is extraction algorithm. The embedding process is mainly concerned with hiding a secret message within a cover or carrier (or container synonymously), and is the most important process of the two. It must be carefully constructed as third party always tries to intercept the message. So, a great deal of attention must be paid to ensure that the secret message goes unnoticed during transmission. On the other hand the extracting process is traditionally a much simpler process. It is simply an inverse of the embedding process, where the secret message is disclosed at the end by the receiver. If the cover message size is larger (in terms of data content — number of bits) relative to the hidden message or image, the easier it is to hide the latter. For example, a 24 bit bitmap image has 8 bits representing three colors – red, green and blue at each pixel – 256 shades of each basic color. So changing the least significant bit of any of these basic colors would make an extremely negligible change on that pixel – and possibly less on the image that it cannot be detected in naked eye. So the least significant bit can be easily used to store the stenographic message. So, if we change the LSB of each basic color of three adjacent pixels, we get 9 bits -- enough space to store an ASCII character. This is called LSB manipulation and a very conventional and simple stenographic implementation.
High frequencies and low frequencies relate to areas of high detail and low detailed areas respectively. Human eyes are less sensitive in high detailed areas so we can remove some of the high detail. This is the logic behind the JPEG compression process. That means one would not notice if some of it was not there. Human eyes are most sensitive in the plainer regions of an image. As the DCT values (referred to as coefficients) are modified when compressing, we can similarly change some of the values such that they hold message data. This is the reason why embedding in this fashion is much harder to detect from a stegoanalytical viewpoint than the spatial domain embedding process, as the stegoanalyst will have to do a bit more digging to find any artifacts of embedding.
We have proposed a different method in this paper although the above methods have implemented image steganography with some level of efficiency. To enhance randomness in the embedding algorithm we have used Lucas series [9] along with DCT coefficients to determine potential locations for storing message bits. Any other series of the type Lucas Sequence can be used in this algorithm like Fibonacci series, Pell numbers, Jacobsthal numbers etc. It enhances the general approach of our algorithm.
The following section II gives related literature with the present work. Section III demonstrated the proposed methods in details. Section IV demonstrated the results and corresponding analysis with the results. The paper is ended with a section on conclusion.
-
II. Related Works
The act of hiding information is not a new thing and it has been taken care of from very old times. How this task will be done is changing from time to time. In this digital age, this process is considered using various multimedia carrier among which image [2, 3] and audio [7] are found to be fostered most. [1] is noticed to be a good review of literature in recent time on this steganography domain where the authors provided most of the literatures describing the science from ancient time to the digital age. According to a recent survey [16] the image steganography techniques are broadly classified as follows: (1) spatial domain techniques (LSB matching, LSB replacement etc.), (2) transform or frequency domain techniques (FFT, DCT and DWT based methods), (3) spread spectrum techniques, (4) compressed domain techniques based on vector quantization, (5) distortion techniques, and (6) statistical techniques.
Among the above, two major categories of techniques are foster mostly towards hiding some information inside an image. One is in the frequency domain and another is in the spatial domain. DCT, DFT, and DWT [1, 2, 4, 5, 15] are mostly used mathematical techniques in the frequency domain where as LSB coding method is used in the spatial domain generally. [8] demonstrated a Lucas sequence (in number theory) based method encapsulated under LSB based technique [10]. [12] considered a ordering strategy based on snake scanning technique for making extension of the LSB method. The snake scanning technique of ordering is preceded by pixel value organization to reduce the data size and followed by optimal pixel adjustment process to minimize the the error or distortion. [14] has given a method incorporating pixel value differences (PVD) to change the LSB of the target image. The scheme also provides mechanism to get a layer structure including PVD revision of considered five pixels block wise. [15] tried to enhance the capacity of data hiding combining both the special domain and frequency domain methods. It includes LSB with DWT for this purpose using FPGA platform to get desired robustness and enhanced performances.
Present work used Lucas sequence in the DCT based method to increase randomness in the said frequency domain technique. Sometimes these conciliation processes are extended incorporating cryptographic methods (like RSA, DES etc) to enhanced the security schemes [3, 7] besides using other optimized hybrid soft computational models [11]. Selection of container image is another area of research where [13] explored image classification schemes to optimize and enhance the efficiency of steganographic techniques.
-
III. Proposed Methods
-
3.1 Lucas Sequence
-
3.2 Lucas Numbers
Normal image steganographic methods include spatial domain techniques mostly using LSB modifications. During the modification of LSB of container image, several schemes have been adopted among which schemes incorporating various numbers theoretic procedures are popular. On the other hand, bit modifications schemes are not considered immensely while taking care of frequency domain methods. The said schemes may incorporate various number theoretic processes such as Fibonacci sequence, Lucas sequence etc among which first one is simpler and well accepted than the last one. This work explored Lucas sequence for the said purpose. Following section first demonstrated the Lucas sequence and Lucas numbers before moving in to presenting the proposed steganographic methods along with its assumptions below.
In mathematics the Lucas sequences [10] are certain constant-recursive integer sequences that satisfy the recurrence relation
Xn=PXn-1+QXn-2 where P and Q are fixed integers. (1)
Examples of Lucas sequences are Fibonacci numbers, Pell numbers, Jacobsthal numbers and Lucas numbers.
Similar to the Fibonacci numbers, each Lucas number is defined to be the sum of its two immediate preceding terms, thereby forming a Fibonacci integer sequence. The first two Lucas numbers are L 0 = 2 and L 1 = 1 as opposed to the first two Fibonacci numbers F 0 = 0 and F 1 = 1.
The Lucas numbers may thus be defined as follows:
Г 2 if и =0
Ln={ 1 if и = 1(1)
(Ln-i + Ln-2 if и >1
The sequence of Lucas Numbers is 2, 1, 3, 4, 7, 11, 18, 29, 47, 76, 123, 199, …...
-
3.3 Assumptions
It is known that all methods are based on some associated assumptions. There are two primary assumptions in our proposed method. These assumptions are given below:
-
• Both parties (sender and receiver) have agreed on set of carrier image to be used.
-
• The means for exchanging required parameters are decided beforehand.
-
3.4 Embedding Procedure
With the above assumptions, following subsections present the proposed algorithms for embedding and extraction of data to and from a container image.
Usually embedding procedure incorporates methods of hiding information in the DCT coefficient of R, G and B matrices separately. Present scheme includes a procedure where information is distributed equally among R, G, and B matrices sequentially according to Lucas sequence. The scheme is presented below with the help of a block diagram given below in fig. 1.
Step 7.2: If key matrix value=1 and message bit=1, then add 1 to DCT coefficient if it is even.
Step 7.3: Repeat this for R1, G1 and B1 matrices depending on the value of Lucas series (section 3.6) until all message bit are embedded.
Step 8: Perform inverse DCT on R1, B1 and G1 after completion of embedding procedure.
Step 9: Combine R1, G1 and B1 to form the stego image.
The above algorithm is presented below with the help of a block diagram given in the following fig. 1 for better understanding and fostering implementation issues.
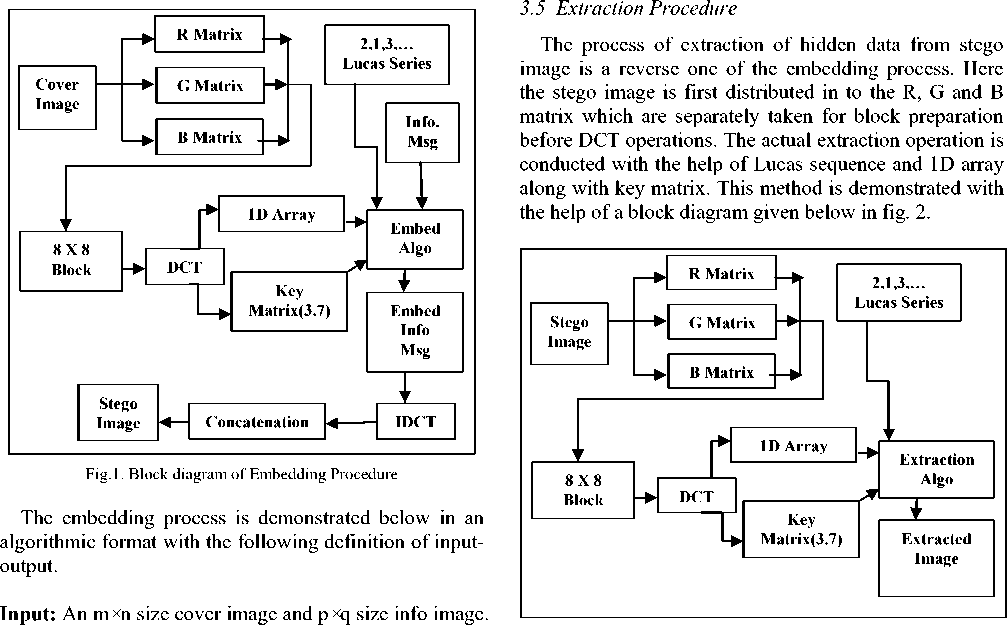
Output: Stego image of size m×n. f ig .2. b lock diagram of e xtraction p rocedure
Step 1: Select Carrier image from the set.
Step 2: Divide the cover image into R, G and B components.
Step 3: Divide each component R, G and B into 8×8 block.
Step 4: Find DCT coefficients of carrier image for each block.
Step 5: Perform quantization on each matrix (R, G and B) and generate matrices R1, G1 and B1.
Step 6: Traverse through each value of R1, G1 and B1 and generate key matrix Rkey1, Bkey1 and Gkey1 (section 3.7) respectively as follows:
Step 6.1: If DCT value ≠ 0 and value ≠ 1 then insert 1 in key matrices.
Step 7: Modify the LSB of DCT coefficients using message bits in each matrix depending on the Lucas Series (section 3.6).
Step 7.1: If key matrix value=1 and message bit=0, then subtract 1 from DCT coefficient if it is odd.
Input: Stego image of size m × n.
Output: Secret message of size p×q.
Step 1: Get the stego image.
Step 2: Divide the stego image into R, G and B components.
Step 3: Divide each component into 8×8 blocks.
Step 4: Find DCT coefficients of stego image for each block.
Step 5: Perform quantization on each matrix (R, G and B) and generate matrices R2, G2 and B2.
Step 6: Traverse through each value of R2, G2 and B2 and generate key matrix Rkey2, Bkey2 and Gkey2 (section 3.7) respectively as follows:
Step 6.1: If DCT value! =0 and value! =1 then insert 1 in key matrices.
Step 7: Traverse through each pixel in Stego image and Key matrices till end depending on the Lucas Series (section 3.6).
Step 7.1: If key matrix = 1 then check the DCT coefficient.
Step 7.1.1: If DCT coefficient is even, message bit=0.
Step 7.1.2: If DCT coefficient is odd, message bit=1.
Step 8: Obtain the secret image and display it on screen.
-
3.6 Use of Lucas Numbers
Both the embedding and extraction processes include use of Lucas numbers (section. 3.2) in the processes. The method of using Lucas number is presented below with help of an algorithm as follows
Step 1: Generate Lucas series.
Step 2: First element of the series is 2, which implies embed 2 bits of the secret message in appropriate locations of each R, G and B matrices respectively obtained from the cover image.
Step 3: Next element is 1, thus embed one bit each in appropriate locations of R, G and B respectively.
Step 4: Next elements are 3, 4, 7, 11 etc. The embed procedure using the Lucas Series is continued until all the bits of the message are embedded in appropriate locations.
Step 5: For extraction procedure, again generate Lucas Series on receiver side.
Step 6: First element is 2, which implies extract 2 bits of the secret message from appropriate locations of each R, G and B matrices respectively obtained from the stego image.
Step 7: Next element is 1, thus extract one bit each from appropriate locations of R, G and B respectively.
Step 8: Next elements are 3, 4, 7, 11 etc. The extraction procedure using the Lucas Series is continued until all the bits of the message are extracted from appropriate locations.
-
3.7 Key Matrix Generation
Embedding and extraction processes both include key matrix generation. Key matrices are used to identify the potential pixels where secret messages will be embedded. Fig. 3, fig. 4 and fig. 5 present this generation of key matrices (i.e. Rkey, Gkey, Bkey) from respective R, G, B components of the cover image respectively.
During embedding, first DCT values of each component matrices are generated after quantization. Then this quantized 2D matrix is converted to a 1D matrix (or array). Now this 1D matrix (or array) is transformed to get the desired key matrix. If DCT value is 0 or 1 then we put 0 in the corresponding cell of the 1D key matrix otherwise we need to put 1 in the corresponding cell of the said 1D key matrix. This process is repeated for all three component matrices. A similar process is followed during extraction with regard to key matrix generation.
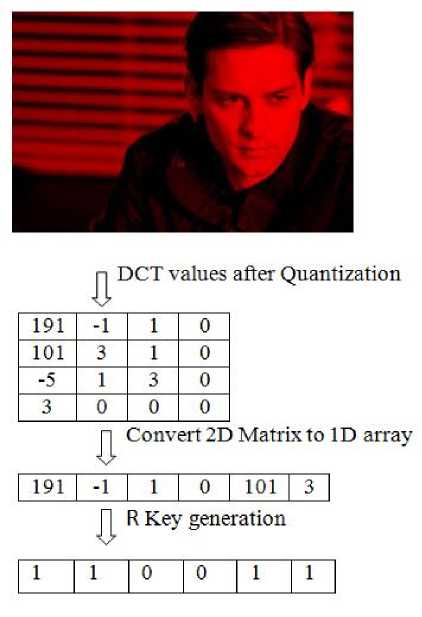
Fig.3. Key matrix generation for R component
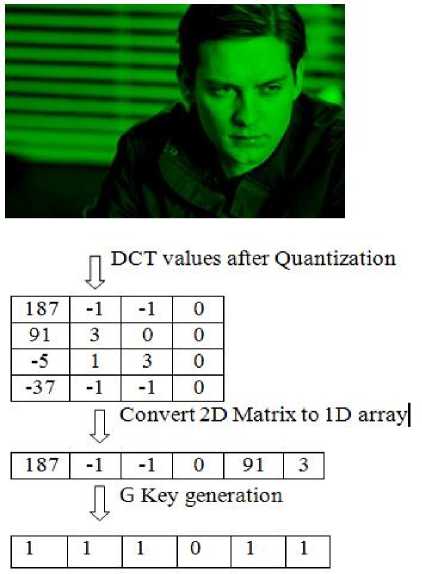
Fig.4. Key matrix generation for G component
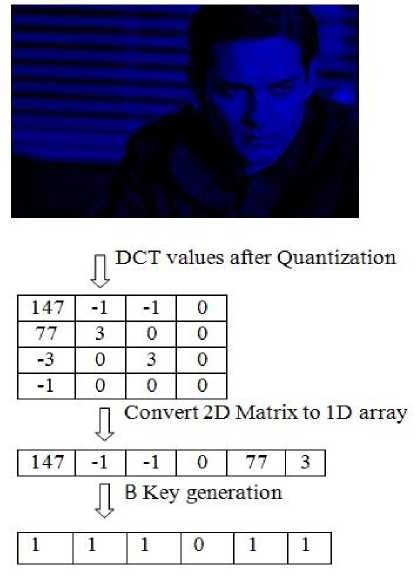
Fig.5. Key matrix generation for B component
-
IV. Experimental Results and Analysis
The proposed method has been implemented using MATLAB 7.9 software platform. This section demonstrates results of some typical experiments with two sample cover images given in the following fig. 6 and fig 7.

Fig.6. Cover Image (1)

Fig.7. Cover Image (2)
The first experiment presented here is with the cover image (2). Three columns of the Table 1 present a set of four message images, corresponding stego images and extracted message from the corresponding stego images respectively using cover image (2). It may be noted that the message intended to be hidden are taken as an image where the text is written for last three cases where as for the first experiment an image (without written text) is considered as message to be concealed.
Table1. Extracted images corresponding to different Message images
Message Image

HELLO HT FRIES IWASHPECTINGTOU. HAVEUSEENTHESUNRISETODAY1 «гам
МтАЫйяА WM<ipiK й^М^^м йиЫф11Й|й к^зж Z .

Extracted Output

НЕШ)№ПН) ЖЕИИ. жтатагеш ITWASSPECTACULAH.
$Ш$ь--М еябовйпофзи-' Sa^illp^l» п'ТОйЫпГа|!$!1^:1 cyiteiis .
^ ' ■ 1 z
M№

It has been observed that the found stego images after embedding is showing analogous appearance and having almost no degradation from qualitative perspective perceived by naked human eye.
To measure the imperceptibility of steganography, several quantitative efficiency metrics are used. Distortion between two different images is measured by considering MSE and PSNR. Higher value of MSE indicates dissimilarity between cover image and stego image. PSNR measures in decibels the quality of the stego image compared with the cover image. The higher PSNR values indicate better quality.
M N
«^MN^S^-f^m
1=1 j=1
PSNR = ^ю [м5ё]
Here M is the image height and N is the image width. We have calculated MSE and PSNR using the algorithm with Lucas series and compare it with the existing DCT based (without Lucas sequence) algorithm using MATLAB. Following Table 2 and Table 3 present the comparison of these two techniques with respect to MSE and PSNR respectively.
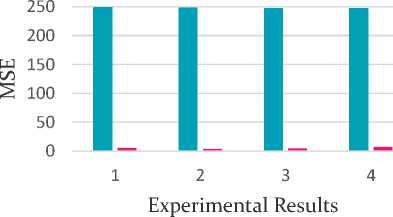
Table 2. Comparison of MSE values in carrier Image and stego Image
|
Experimental Results |
MSE (For existing algorithm) |
MSE (For proposed algorithm) |
|
1 |
249.3799 |
5.1211 |
|
2 |
248.1623 |
3.8515 |
|
3 |
248.1071 |
4.8348 |
|
4 |
247.6062 |
7.5329 |
Table 3. Comparison of PSNR values in carrier Image and stego image
|
Experimental Results |
PSNR (For existing algorithm) |
PSNR (For proposed algorithm) |
|
1 |
24.1622 |
41.0372 |
|
2 |
24.1834 |
42.2745 |
|
3 |
24.1830 |
41.2870 |
|
4 |
24.1918 |
40.3612 |
Fig. 8 and fig. 9 present the above comparison of techniques graphically using a bar diagram with respect to MSE and PSNR respectively.
These results indicate that embedding process introduces less perpetual distortion and higher PSNR. To measure the distortion introduced by the embedding in cover image, PSNR and MSE after embedding was observed for some images. It is found that MSE has considerably decreased by our proposed method compared to the normal DCT method. Also the PSNR is constantly above 40 dB as seen from Table 3 which means that the quality degradations could hardly be perceived by a human eye.
The second experiment reported the PSNR resulted by the proposed technique is divided in to two parts: (1) with varying cover image size and (2) with varying image payload (or amount of data of message image). Following fig. 10 presents the PSNR values with respect to size of the cover image.
Comparison of MSE (embed)
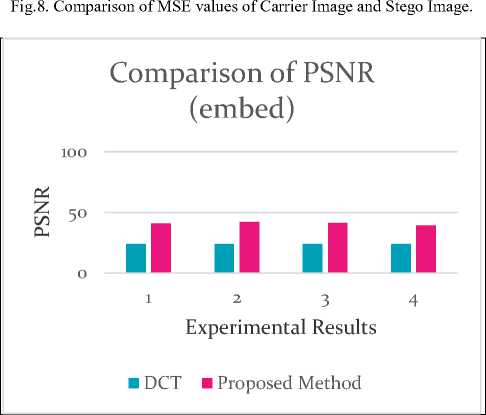
Fig.9. Comparison of PSNR between Carrier Image and Stego Image
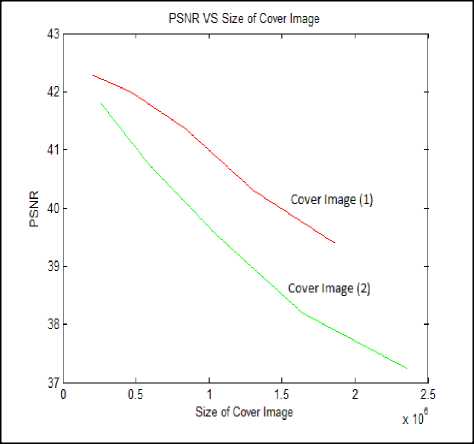
Fig.10. PSNR vs Size of cover image
DCT Proposed Method
From the trends of the curves in fig. 10 we can verify that with increasing size of the cover image our PSNR value is steadily decreasing. It may be noted that the payload value is constant in this case and set at 139×509. Base size of cover image (1) is 364×570 and cover image (2) is of base size 512×512. We have incremented each size with factors of 1.5, 2, 2.5 and 3. We have used the secret message image in row 2 from Table 1.
The following fig. 11 presents the results with a constant size of cover image 1536×1536 using image cover image (2). Here we have incremented the size of payload with a factor of 1.5, 2, 2.5 and 3. The two payloads that are used here are message image in row 1 and message image in row 2 from Table 1.
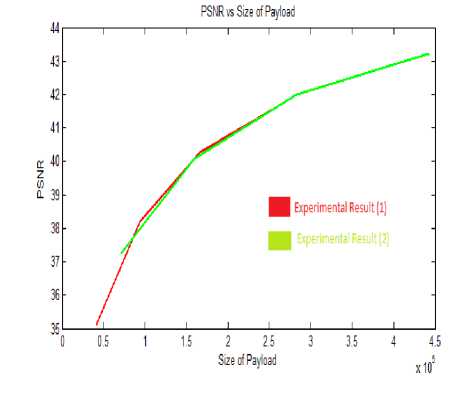
Fig.11. PSNR vs Size of Payload
The following Table 4 presents the PSNR values of fixed size ( 1536×1536) stego image with respect to amount of data embedded.
Table 4. PSNR values of Stego Image with increasing Payload
|
Amount of Data Embedded (in Bytes) or Payload |
PSNR (dB) |
Amount of Data Extracted (in Bytes) |
|
41616 |
35.1016 |
41616 |
|
70751 |
37.2291 |
70751 |
|
93636 |
38.1800 |
93636 |
|
159676 |
40.0832 |
159676 |
|
166464 |
40.2683 |
166464 |
|
260100 |
41.6437 |
260100 |
|
283004 |
42.0142 |
283004 |
|
443004 |
43.2086 |
443004 |
From Table 4 it is evident that the proposed method works more efficiently when the payload is increased for a fixed size of cover image. It may also be noted that PSNR is constantly increasing with the increase of payload. Also experiments have shown that the number of bytes of data embedded is equal to the number of bytes of data extracted from our stego image.
-
V. Conclusion
Frequency domain data hiding techniques are getting importance this days because of its’ potential to hide data more efficiently than special domain data hiding techniques. A new technique of data hiding using DCT algorithm and Lucas Sequence is proposed and implemented in this work. We can infer from our experimental results and analysis that our proposed steganographic embedding technique supports high amount of data encapsulation compared to normal DCT based methods. Because of the usage of Lucas sequence with DCT technique, the level of information hiding gets enhanced in comparison to the use of same with LSB [8]. This is due to the occurrence of embedding scheme in a transform domain. It may also be noted that use of Lucas sequence increases the randomness factor of information hiding and hence decryption or breaking time will expected to be enhanced.
The question of quality degradation of carrier or container image is also addressed in this work. This is judged from qualitative and quantitative perspectives. The quality degradation between the original container image and the stego image could hardly be perceived by human eyes (from qualitative perspective) as it has a PSNR value constantly above 40 dB (from quantitative perspective) . Thus our technique proves to be effective with respect to the criteria of perceptibility, capacity and robustness of a standard steganographic algorithm. Varied use of other sequences may provide improvements to the performance in the algorithm.
Список литературы An Efficient Embedding Technique in Image Steganography Using Lucas Sequence
- N D Jambhekar and C A Dhawale. “The Act of Steganography from Ancient Era to Digital Age”, IJCA Proceedings on National Conference on Knowledge, Innovation in Technology and Engineering, NCKITE-2015 (2), pp. 1-4, July 2015.
- Singla, Deepak, and Rupali Syal. "Data security using LSB & DCT steganography in images." Int. J. Of Computational Engineering Research Vol. 2, No.2, pp. 359-364, 2012.
- Amit Patel, Sai Prasad Kousika VNH “More Secure Way of Sharing Secret Text Message,” Int. J. of Science and Research, , Vol. 5(12), pp. 1563-1568, December 2016.
- Jahfar, C. “A Secure Steganography Technique using DCT and Modified RC4.", Int. J. of Interdisciplinary and Multidisciplinary Studies, Vol 2, No.6, pp. 61-65, 2015.
- G. Sudha Devi, and K. Thangadurai. "Image Steganography Based on Hybrid Discrete Wavelet Transform with Gabor Filter and Optimized Genetic Algorithm.", Int. J. of Computer Technology and Applications, Vol. 9(25), pp. 507-524, 2016.
- Abdullah, Ako Muhammad, and Roza Hikmat Hama Aziz. "New Approaches to Encrypt and Decrypt Data in Image using Cryptography and Steganography Algorithm," image Vol. 143(4), 2016.
- Adeel Jawed, Atanu Das, “Security Enhancement in Audio Steganography by RSA Algorithm”, Int. J. of Electronics and Communication Technology, Vol. 6, Issue 1, spl-1, pp. 139-142, Jan - March 2015.
- Alharbi, Fahd. "Novel Steganography System using Lucas Sequence." International Journal of Advanced Computer Science and Applications, Vol. 4(4), pp. 52-58, 2013.
- L. E. Dickson, “Recurring Series; Lucas' Un, Vn, History of the Theory of Numbers: Divisibility and Primality”, Dover Publications, New York , Vol. 1, pp. 393 -411, 2005.
- K. Thangadurai, G. S. Devi, “An analysis of LSB based image steganography techniques”, In Computer Communication and Informatics (ICCCI), 2014 International Conference, pp. 1-4. IEEE, Jan 3, 2014.
- Gerami, Parisa, Subariah Ebrahim, and Morteza Bashardoost. "Least significant bit image steganography using particle swarm optimization and optical pixel adjustment." Int. Journal of Computer Applications, Vol. 55, No. 2, 2012.
- Rajeev Kumar, Khushil K. Saini, and Satish Chand, “A New Steganography Technique Using Snake Scan Ordering Strategy”, Int. J. of Image, Graphics and Signal Processing, Vol. 6, pp. 25-32, 2013. DOI: 10.5815/ijigsp.2013.06.04.
- Seyyed Amin Seyyedi, Nick Ivanov, "Statistical Image Classification for Image Steganographic Techniques", Int. J. Image, Graphics and Signal Processing, Vol. 6, No. 8, pp.19-24, 2014. DOI: 10.5815/ijigsp.2014.08.03.
- Avinash K. Gulve, Madhuri S. Joshi, “A High Capacity Secured Image Steganography Method with Five Pixel Pair Differencing and LSB Substitution”, Int. J. of Image, Graphics and Signal Processing, Vol. 7, No. 5, pp. 66-74, 2015. DOI: 10.5815/ijigsp.2015.05.08
- Kalpana Sanjay Shete, Mangal Patil, J. S. Chitode, “Least Significant Bit and Discrete Wavelet Transform Algorithm Realization for Image Steganography Employing FPGA”, Int. J. of Image, Graphics and Signal Processing, Vol.8, No.6, pp.48-56, 2016. DOI: 10.5815/ijigsp.2016.06.06.
- Suhad Shakir Jaber, Hilal Adnan Fadhil, Zahereel I. Abdul Khalib and Rasim Azeez Kadhim, ―Survey on Recent Digital Image Steganography Techniques‖, Journal of Theoretical and Applied Information Technology, Vol.66, No.3, pp. 714-728, 31st August 2014.


