An Efficient Optimized Neural Network System for Intrusion Detection in Wireless Sensor Networks
Автор: Shridhar Sanshi, Ramesh Vatambeti, Revathi V., Syed Ziaur Rahman
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 6 vol.16, 2024 года.
Бесплатный доступ
In the realm of wireless network security, the role of intrusion detection cannot be overstated in identifying and thwarting malicious activities within communication channels. Despite the existence of various intrusion detection system (IDS) approaches, challenges persist in terms of accurate classification and specification. Consequently, this article introduces a novel and innovative approach, the African Vulture-based Modular Neural System (AVbMNS), to address these issues. This research aims to detect and categorize malicious events in wireless networks effectively. The methodology begins with preprocessing the dataset and extracting relevant features. These extracted features are then subjected to a novel training technique to enhance the detection and classification of network attacks. The integration of African Vulture optimization significantly enhances the detection rate, leading to more precise attack identification. The research's effectiveness is demonstrated through validation using the NSL-KDD dataset, with impressive results. The performance analysis reveals that the developed model achieves a remarkable 99.87% detection rate and 99.92% accuracy when applied to the NSL-KDD dataset. Furthermore, the outcomes of this novel model are compared with existing approaches to gauge the extent of improvement. The comparative assessment affirms that the developed model outperforms its counterparts, underscoring its effectiveness in addressing the challenges of intrusion detection in wireless networks.
Intrusion Detection, African Vulture Optimization, Modular Neural System, Wireless Sensor Network, Detection Rate, Attack Classification
Короткий адрес: https://sciup.org/15019544
IDR: 15019544 | DOI: 10.5815/ijcnis.2024.06.07
Текст научной статьи An Efficient Optimized Neural Network System for Intrusion Detection in Wireless Sensor Networks
In recent times, network-based technologies have been widely used in different fields such as marketing, engineering, the educational field, business, and social communities [1]. Simultaneously, security threats are increasing due to the widespread use of network applications [2]. Moreover, the development of attacking approaches reduces confidentiality and network performance. Thus, several network security techniques are developed to prevent attacks on the WSN [3]. These security approaches enhance the confidentiality rate, data integrity, and resource availability [4]. However, these security approaches are not applicable to large-scale networks. Therefore, the Intrusion Detection System (IDS) was modelled to estimate the attacks and network traffic [5]. The IDS is a real-time-based supervisory network flow model that collects information about the packets and traffic in the network [6]. Thus, it is helpful in identifying malicious events and attacks by inspecting the network packets. Furthermore, it is capable of detecting and classifying attacks like Probe [7], Denial of Service (DoS) [8], Root to Local (R2L) [9], and User to Root (U2R) [10]. These attacks are specified based on the behaviour of the nodes and users in WSN. The IDS is generally classified into two types: anomaly-based and misuse-based [11]. In the misuse-based approach, the attack features are detected by comparing the malicious activity with the predefined signature. As a result, it can only detect known network attacks [12]. In an anomaly-based approach, malicious activities are recognized based on behaviour change. Therefore, it can detect known and unknown attacks by analyzing the behavior of the nodes [13].
Moreover, to estimate the network traffic and flow, different machine learning approaches like support vector machines, conventional neural systems, and decision tree algorithms are incorporated into the IDS system [14]. In ML-based methods, the dataset is pre-processed, and the features are reduced using the feature selection process [15]. However, filtering the dataset is more complex and time-consuming in the conventional neural system. Moreover, the feature analysis module includes feature selection and ranking. Using fewer features reduces detection accuracy and rate [16]. Furthermore, traditional neural system filtering mechanisms are used to preprocess and select the features. But, using filters increases the network's cost and complexity. Among the existing neural approaches, the convolutional neural system identifies malicious events with a better detection rate [17]. In CNN, the accuracy parameter is improved by reducing the features. However, the processing of a huge dataset is complex in this approach. Thus, to overcome the demerits faced by neural systems, several optimization algorithms, such as ant-lion optimization [18], honey pot optimization [19], artificial bee colony optimization [20], etc., are utilized in IDS.
The incorporation of an optimization algorithm enhances the network's performance. However, the computational complexity and false alarm rate in these approaches are higher. Thus, several hybrid methods, like the IDS approach based on Improved Particle Swarm Optimization, the security approach based on the recurrent neural system, and the ML approach for AE attack detection based on the manifold decision algorithm, are developed to overcome the demerits faced by the convolutional neural system. But they face issues in implementation, time complexity, and false alarm rate. Thus, this article developed a novel hybrid optimized neural approach to overcome the existing algorithms' demerits and improve the detection rate and accuracy.
Contributions of the Paper
The primary contributions of this article can be outlined as follows:
• Data Collection: The article begins by gathering network data from a standard source, which is subsequently imported into the system for analysis.
• Novel Hybrid AVbMNS Design: A novel hybrid approach, the African Vulture-based Modular Neural System (AVbMNS), is introduced with a specific focus on intrusion detection parameters.
• Data Preprocessing: The trained dataset undergoes a unique preprocessing method to eliminate error values and enhance data quality.
• Feature Extraction and Classification: The article proceeds to extract relevant features from the preprocessed data and employs them to classify malicious events in the network.
• Comparative Analysis: The research evaluates the developed model's performance through a comparative analysis, considering key metrics such as accuracy, false alarm rate, execution time, and detection rate.
2. Related Works
The presented work is organised as follows: in Section 2, existing works related to IDS are listed with merits and demerits, in Section 3, the problem of current techniques is described, in Section 4, the developed IDS model is explained with an algorithm and flowchart, in Section 5, the performance and working of the developed model is described with a case study, and in Section 6, the work is concluded. The comparative analysis confirmed that the developed model produced better results.
Some of the Recent Works Related to IDS are Described as Follows
Security threats in wireless sensor networks have recently increased as a result of malicious users in the communication channel. Thus, detecting the malicious user in the channel is critical in WSN to provide users with security and privacy. Therefore, Ting Zhang et al. [21] developed a novel IDS approach based on Improved Particle Swarm Optimization. This technique is a hybrid of support vector machines and principal component analysis. This reduces energy consumption and delays in the channel. However, the detection rate and accuracy are low.
IDS plays a vital role in providing security to the users and data in network applications. Thus, T. Thilagam and R.
Aruna [22] designed a novel security approach based on a recurrent neural system. This method combines the features of a convolutional neural network and ant-lion optimization. The primary objective of this approach is to detect attacks in a cloud environment. This approach is validated with the CICIDS-2018 dataset, and the results are estimated. However, the implementation complexity is greater with this approach.
Nowadays, machine learning (ML)-based approaches are widely used in IDS as they reveal the attack flows. Different ML-based methods are developed to protect the data from attacks. However, they cannot recognize specific attacks like adversarial example (AE) attacks, etc. Thus, Ning Wang et al . [23] developed an ML approach for AE attack detection based on the manifold decision algorithm. This model is validated with the NSL-KDD and CICIDS datasets. This method accurately detects AE attacks. However, the detection accuracy is low for other network attacks.
In a large-scale network, detecting and classifying attacks using a single node is a very complex process. Moreover, providing privacy to the users is one of the major concerns of the WS network. Hence, GAO Liu et al. [24] presented a blockchain-based hybrid IDS framework with a decentralized Software Guard Extension technique. The main objective of this approach is to provide privacy to the users and estimate the network's trust. The performance is analyzed in terms of security, privacy, and incentive parameters. However, the specification of the attack is not supported by this approach.
The widespread use of network applications increased the number of malicious activities on the network. Thus, providing security to the network application is one of the challenging factors. Moreover, the surface for attacks is increasing daily due to the growth of interconnected devices. Most of the IDS approaches provided the best solution for known attack detection. However, unknown attack detection is still a challenging one. Thus, Ramin Atefinia and Mahmood Ahmadi [25] presented a modular deep neural system with multiple architectures to detect and classify unknown attacks. This work was verified with the CICIDS dataset, and the outcomes were determined. However, the implementation cost is higher with this approach.
3. System Model with Problem Statement
In a Wireless Sensor Network (WSN), an intrusion detection system plays a significant role in providing security and privacy to the users in the channel. In the existing IDS model, the user features are selected in the feature selection module and then processed to detect the malicious user. However, limiting feature selection reduces detection rate and accuracy. Moreover, in existing approaches, there is no filtering mechanism. Thus, intrusion detection in the case of large data sets is very complex and consumes more time. The existing system and its problem statement are described in Fig. 1.
Users
Inefficient IDS Model
Fig.1. System model and its problem statement

Feature Selection Phase
In addition, false intrusion detection reduces the user's security level in the communication channel. Although different IDS approaches have been developed, they face attack detection and classification issues. Moreover, the outcome obtained by the existing approaches is low. This motivated me to develop an optimized IDS framework to overcome the shortcomings of the existing approaches.
4. Proposed Avbmns for Intrusion Detection
A novel hybrid African Vulture-based Modular Neural System (AVbMNS) was developed to detect malicious events in the wireless sensor network. The developed model combines the attributes of the African Vulture Optimization [26] and the modular neural system [27]. Initially, wireless network data (NSL-KDD) was collected from the standard site and imported into the system. The presented AVbMNS framework is represented in Fig 2.
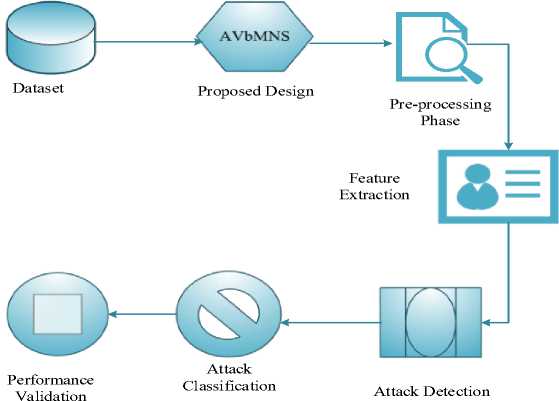
Fig.2. AVbMNS framework
Here, the dataset is trained to remove errors in the preprocessing phase. Then, the errorless data enters the feature extraction module. In this module, the attack features are extracted from the dataset. Furthermore, the extracted features are trained in the system to classify the type of attack. Furthermore, the identified attack types are specified using the developed model. Moreover, the designed model is estimated and compared with the existing approach to validate its robustness.
-
4.1. Design of AVbMNS
-
4.2. Pre-processing Module
-
4.3. Feature Analysis Module
A novel intrusion detection scheme was modelled based on the African vulture optimization and the modular neural network. Initially, the network data (NSL-KDD) was collected from the standard site (Kaggle) and imported into the Python system. Then, the designed hybrid model was developed in the system with attack detection parameters. The dataset initialization is expressed in Eqn. (1).
Here, Wsd denotes the network dataset, f indicates the function for dataset initialization, ws refers to the data present in the dataset, Q represents the features present in the dataset, and h denotes the total count of data samples present in the dataset.
After initialization, the dataset is trained using the proposed approach. Then, the trained dataset is pre-processed to eliminate the error values present in the dataset. In the pre-processing phase, the null values, noise features, and error values are removed. The pre-processing of the dataset is expressed in Eqn. (2).
Ws^SlUXWs,^) (2)
Where, У refers to the pre-processing function, / indicates the pre-processing variable, and 77 denotes the error features. Thus, only the errorless data enters into the feature analysis module. The pre-processing module improves the attack classification and reduces the system's complexity.
The pre-processed dataset contains normal as well as abnormal (attack) features. In the feature extraction module, the features useful for attack detection are tracked and extracted. Moreover, the meaningless features are removed in this process. The feature analysis is expressed in Eqn. (3).
k(Q) — j EUQ - Q u )2 — Qu A
Where, К denotes the feature extraction variable, A the feature tracking variable, Qu the meaningless features, and Qu the useful features. Furthermore, these tracked features are trained in the system to classify the malicious events in the WSN. Then, based on the trained features, the attacks are detected. The attack detection is expressed in Eqn. (4).
(if (T q — 0); Attack
d iff (Jq — 1); Benign
Where, Ad denotes the attack detection function and T q indicates the trained features. If the trained feature is "0," the system detects it as "Attack". Similarly, if the trained feature is "1," the system identifies it as "Benign". Furthermore, the attack types such as probe, U2R, R2L, and DoS attacks are specified. Here, the attack types are specified based on attack features. The attack specification is expressed in Eqn. (5).
A Sp — 4
Where, ASp denotes the attack specification variable and A f indicates the attack features. If the attack feature is equal to "1", it is specified as "DoS." If the A f is equal to "-1," it is classified as a probe attack; if the A f is equal to "0," it is categorized as "U2R," and if A f it is equal to 2, it is identified as an R2L attack. In addition, the flow of the attack detection process is represented in pseudocode format in algorithm 1.
Algorithm 1: AVbMNS
// Initialization of NSL-KDD dataset
Pre-processing Phase()
{ int Y',x;
// initializing the pre-processing variable
Y ' (Wsd)^ x(W sh-i])
// removing the noise/null features from the trained dataset
}
Feature_ Analysis ()
{ intA,K;
// Initializing the feature tracking variable
K(Q) — A(Q - Qu) * Q u
// the meaningless features are eliminated, and useful features are extracted
}
Attack_ Detection ()
{ if(TQ — 0)
{
Attack; //if the trained features are equal to “0”, it is identified as “Attack”
} else ( Benign)
//if the trained feature is equal to "1", then it is detected as "Normal."
}
} stop
The flowchart of AVbMNS is represented in fig 3.
//Importing NSL-KDD dataset to the system
Dataset Initialization
AVbMNS Design
//Training the dataset using the presented approach
//Developing the proposed method with dete ction parameters
Training Dataset
Pre-processing Phase
//Extracting the normal and abnormal features
//Removing the error values from the dataset
Feature Extraction
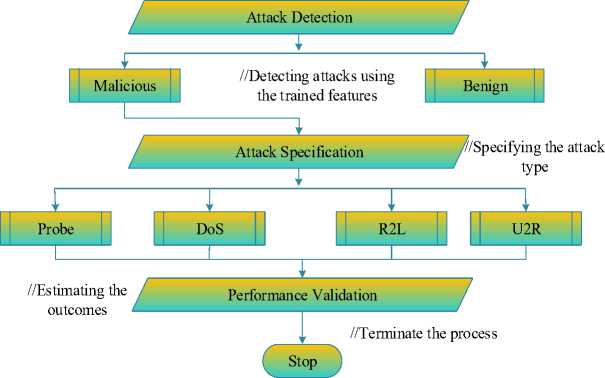
Fig.3. Flowchart of AVbMNS
The designed model is executed and implemented, and the results are estimated in terms of detection rate, accuracy, false alarm rate, and execution time.
5. Result and Discussion
This article developed a hybrid, optimized IDS framework to detect and classify attacks in the WSN. To validate the presented model, network data (NSL-KDD) was taken and imported into the system. The trained dataset is pre-processed, and the feature analysis extracts meaningful features. Furthermore, the extracted features are trained using the developed algorithm to detect and specify the attack. The developed IDS model is implemented in the Python software, and the performance metrics are estimated. The implementation parameters are described in Table 1.
Table 1. Parameter Description
|
Parameter Description |
|
|
OS |
Windows 10 |
|
Platform |
Python |
|
Version |
3.10 |
|
Dataset |
NSL-KDD |
|
Attack Types |
DoS, Probe, R2L, U2R |
Furthermore, the obtained results are compared with the existing approaches to test the robustness of the developed model. In addition, the enhancement score is also determined by the comparative assessment. The performance analysis proves that incorporating an African vulture and a modular neural system enhances the performance of the WSN.
-
5.1. Case Study
To describe the working process of the designed model, a case study was created. The NSL-KDD dataset was initially downloaded from the Kaggle site and integrated into the system. Normal and attack features are included in the imported dataset. After that, the African vulture optimisation and modular neural system were integrated to form a revolutionary approach. Furthermore, the imported dataset is trained with the newly devised approach. Furthermore, the trained dataset is pre-processed to filter out any errors or null values. The pre-processed dataset contains both useful and insignificant features. Thus, in the feature analysis module, the meaningful characteristics are retrieved and the nonsensical parts are deleted. The retrieved features include both harmful and non-malicious elements. Figure 4 depicts the process of the developed model.
Training Dataset

Pre-processing

Attack Classification
NSL-KDD Dataset

Dataset
Feature
Analysis
Training Features
Fig.4. AVbMNS workflow
As a result, the retrieved characteristics are trained to distinguish between normal and pathological features. In addition, the established approach specifies the sort of assault. The NSL-KDD dataset includes normal, DoS, U2R, probe, and R2L characteristics. Once the attack is detected, the attack type is also mentioned in the developed model. By training and testing the dataset, the proposed model is validated in the Python environment. In this case, 67% of the dataset is used for training, while 33% is used for testing. Furthermore, the constructed model's performance is estimated in terms of accuracy, false alarm rate, execution time, and detection rate. A comparison study is also used to validate the effectiveness of the developed model.
-
5.2. Comparative Analysis
By comparing the findings of the created model with those of the current methodologies, the robustness of the presented approach is validated. Existing approaches for comparison include Modified Binary Grey Wolf Optimisation with Support Vector Machine (MBGWO_SVM) [28], Fuzzy-based Nearest Neighbourhood Algorithm (FbNNA) [29], and Collaborative Optimised Intrusion Detection System with Artificial Bee Colony Approach (COIDS_ABCA) [30].
-
A. Accuracy
The system's accuracy defines the attack classification rate, which is how correctly the presented model classifies the attack type. It is estimated using the true-positives, true-negatives, false-positives, and false-negatives. The accuracy of the model is expressed in Eqn. (6).
Aq’ =
ip ' +in ' ip ’ +in ’ +jp ’ +jn ’
Where, Aq ‘ denotes the accuracy, ip' refers to the true-positive, in indicates true-negative, jp ‘ and jn' represents false-positive and false negative, respectively. The comparison of accuracy is represented in Fig. 5.
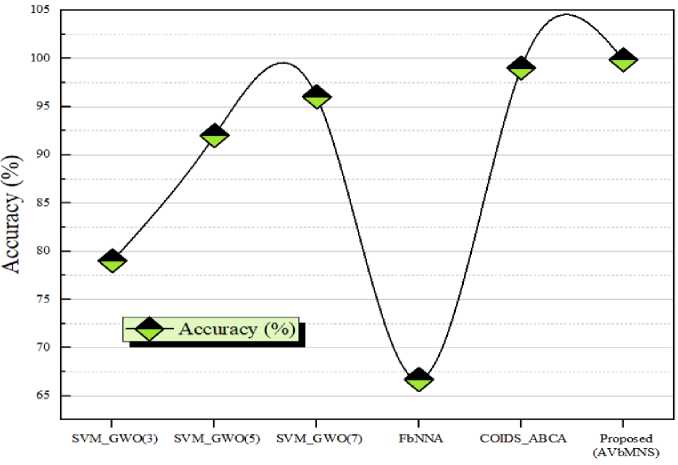
Fig.5. Comparison of accuracy
The developed model's accuracy is compared to existing methodologies to validate that the proposed model's attack classification rate is high. The accuracy is compared to existing techniques such as SVM_GWO with three wolves, SVM_GWO with five wolves, SVM_GWO with seven wolves, FbNNA, and COIDS_ABCA in this case. The known strategies achieve accuracy rates of 79%, 92%, 96%, 66.7%, and 99%. However, the proposed approach has a high accuracy of 99.87%. This demonstrates that the created model outperformed previous intrusion detection methods in terms of accuracy.
-
B. Detection Rate
The detection rate indicates the true positives attained by the system over the total true positives and false negatives. The detection rate is expressed in Eqn. (7).
D
R
ip ' ipi+jru
Where, D denotes the detection rate. The comparison of detection rates is represented in Fig 6.
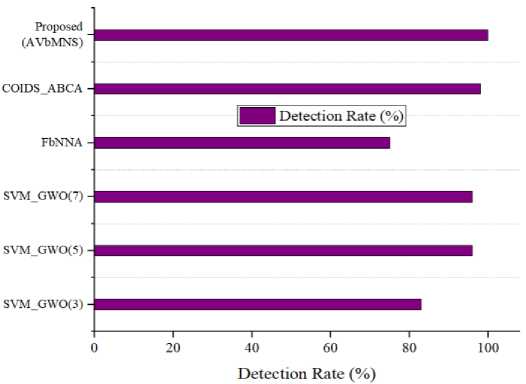
Fig.6. Comparison of detection rate
The existing approaches, such as SVM_GWO with 3 wolves, SVM_GWO with 5 wolves, SVM_GWO with 7 wolves, FbNNA, and COIDS_ABCA, attained detection rates of 83%, 96%, 96%, 75%, and 98%, respectively. But the developed model earned a higher detection rate of 99.92%. The African vulture optimization in the designed model accurately tracks and identifies the attacks in the WSN.
-
C. False Alarm Rate and Execution Time
The false alarm rate (error rate) indicates a false-positive value attained over true-negative and false-positive. The false alarm rate is represented in Eqn. (8).
FAR
ip ' inr+jpr
Where, denotes the false alarm rate. Moreover, the execution time is defined as the time consumed by the
, AR , developed model to complete the entire IDS process. The execution time calculation is represented in Eqn. (9).
ET = FT- ST
Here, E denotes the execution time, F represents the finishing time, and S indicates the start time. The comparison of execution time and false alarm rate is represented in Fig 7.
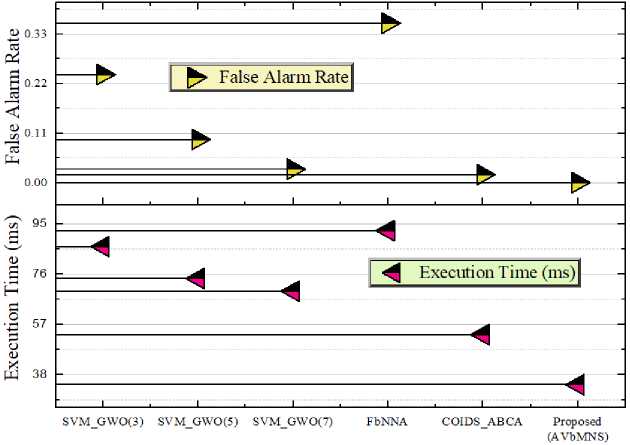
Fig.7. Comparison of execution time and false alarm rate
The time taken by the existing approaches such as SVM_GWO with 3 wolves, SVM_GWO with 5 wolves, SVM_GWO with 7 wolves, FbNNA, and COIDS_ABCA is 86.4ms, 74.4ms, 69.6ms, 92.4ms, and 53.2ms, respectively. But the designed model takes less time of 34.3ms to execute and complete the entire process. Similarly, existing approaches and designed models estimate the false alarm rate. The false alarm rate achieved by the existing techniques is 0.24, 0.096, 0.03, 0.354, and 0.018, respectively. But the designed model earned less false alarm rate of 0.00024. The overall comparative assessment is tabulated in table 2.
Table 2. Comparative assessment
|
Techniques |
Accuracy (%) |
Detection Rate (%) |
False Alarm Rate |
Execution Time (ms) |
|
MBGWO_SVM(3) |
79 |
83 |
0.24 |
86.4 |
|
MBGWO_SVM(5) |
92 |
96 |
0.096 |
74.4 |
|
MBGWO_SVM(7) |
96 |
96 |
0.03 |
69.6 |
|
FbNNA |
66.7 |
75 |
0.354 |
92.4 |
|
COIDS_ABCA |
99 |
98 |
0.018 |
53.2 |
|
Proposed (AVbMNS) |
99.87 |
99.92 |
0.0024 |
34.3 |
The comparative analysis verifies that the developed model earned better performances than others. Thus, the presented IDS model accurately detects and classifies the attacks in WSN.
5.3. Discussion
6. Conclusions
The presented IDS approach was designed and verified in the python environment. The primary objective of the developed model is to detect malicious events in the WS network. Moreover, the presented model was validated with an
NSL-KDD dataset, and the results are estimated. The African vulture optimization in the proposed approach improves the detection rate and accuracy. The performance analysis of the presented model is tabulated in table 3.
Table 3. Performance analysis
|
Metrics |
Performance |
|
Accuracy (%) |
99.87 |
|
Detection Rate (%) |
99.92 |
|
False Alarm Rate |
0.0024 |
|
Execution Time(ms) |
34.3 |
For the NSL-KDD dataset, the designed model attained 99.87% accuracy and 99.92% detection rate. Moreover, the false alarm rate (error rate) is very low that is 0.0024, and the overall implementation time is 34.3ms in the developed model. Furthermore, obtained results are compared with the existing approaches to validate the robustness of the developed model.
In the presented study, a unique AVbMNS framework was created to detect and classify harmful events in the WSN. The proposed method was implemented and evaluated using the NSL-KDD dataset. The designed model's pre-processing approach removes mistakes and null features. Furthermore, in the feature extraction module, useful features are extracted and subsequently trained to classify the attacks. Incorporating African vulture optimisation improves attack detection and precision. Furthermore, the assaults in the NSL-KDD dataset are described using the presented method. The work provided here is carried out in a Python context, and the results are estimated. Furthermore, the estimated results are compared to existing methodologies in order to validate the efficacy of the provided model. A comparison analysis reveals that the developed model improves accuracy by 0.87% and detection rate by 1.92%. Furthermore, the developed model reduces the false alarm rate and execution time by 0.0156 and 18.9 ms, respectively. The existing models achieved nearly 98% of detection rate and 53.2ms of execution time, where the proposed model achieved 99% of detection rate and 34.3ms of execution time. In future work, the attacks can be detected by implementing different deep learning techniques with hybrid optimization model in real-time environment.
Список литературы An Efficient Optimized Neural Network System for Intrusion Detection in Wireless Sensor Networks
- Yang, Zaoli, et al. "Measuring topic network centrality for identifying technology and technological development in online communities." Technological Forecasting and Social Change 167 (2021): 120673.
- Shaukat, Kamran, et al. "A review on security challenges in internet of things (IoT)." 2021 26th International Conference on Automation and Computing (ICAC). IEEE, 2021.
- Rajasoundaran, S., et al. "Secure opportunistic watchdog production in wireless sensor networks: a review." Wireless Personal Communications 120.2 (2021): 1895-1919.
- Velasco, Francisco Alcaraz, Jose Manuel Palomares, and Joaquin Olivares. "Lightweight method of shuffling overlapped data-blocks for data integrity and security in WSNs." Computer Networks 199 (2021): 108470.
- Keserwani, Pankaj Kumar, et al. "A smart anomaly-based intrusion detection system for the Internet of Things (IoT) network using GWO–PSO–RF model." Journal of Reliable Intelligent Environments 7.1 (2021): 3-21.
- Macherla, H., Kotapati, G., Sunitha, M.T., Chittipireddy, K.R., Attuluri, B., Vatambeti, R., “Deep learning framework-based chaotic hunger games search optimization algorithm for prediction of air quality index”, Ingénierie des Systèmes d’Information, Vol. 28, No. 2, pp. 433-441, 2023.
- Jahromi, Amir Namavar, et al. "Toward Detection and Attribution of Cyber-Attacks in IoT-Enabled Cyber–Physical Systems." IEEE Internet of Things Journal 8.17 (2021): 13712-13722.
- Ravindra, C., Kounte, M.R., Lakshmaiah, G.S. et al., “ETELMAD: Anomaly Detection Using Enhanced Transient Extreme Machine Learning System in Wireless Sensor Networks”, Wireless Pers Commun 130, 21–41 (2023). https://doi.org/10.1007/s11277-023-10271-0
- Imrana, Yakubu, et al., "A bidirectional LSTM deep learning approach for intrusion detection", Expert Systems with Applications 185 (2021): 115524.
- Melo, Roberto Vasconcelos, et al., "ISM-AC: An immune security model based on alert correlation and software-defined networking", International Journal of Information Security 21.2 (2022): 191-205.
- Afzal, Sabeeha, and Anjna Jayant Deen., "Anomaly-Based Intrusion Detection System Through Deep Neural Network", Proceedings of Third International Conference on Communication, Computing and Electronics Systems. Springer, Singapore, 2022.
- Sharon, Andrea, et al., "An Intelligent Intrusion Detection System Using Hybrid Deep Learning Approaches in Cloud Environment", International Conference on Computer, Communication, and Signal Processing. Springer, Cham, 2022.
- Om Kumar, C.U., Marappan, S., Murugeshan, B. et al., “Intrusion Detection Model for IoT Using Recurrent Kernel Convolutional Neural Network”, Wireless Pers Commun., 129, 783–812 (2023). https://doi.org/10.1007/s11277-022-10155-9
- Afuwape, Afeez Ajani, et al., "Performance evaluation of secured network traffic classification using a machine learning approach", Computer Standards & Interfaces 78 (2021): 103545.
- Nafis, Nur Syafiqah Mohd, and Suryanti Awang.. "An enhanced hybrid feature selection technique using term frequency-inverse document frequency and support vector machine-recursive feature elimination for sentiment classification", IEEE Access 9 (2021): 52177-52192.
- Halim, Zahid, et al.,"An effective genetic algorithm-based feature selection method for intrusion detection systems", Computers & Security 110 (2021): 102448.
- Ghanei, Hadis, Farnoush Manavi, and Ali Hamzeh., "A novel method for malware detection based on hardware events using deep neural networks", Journal of Computer Virology and Hacking Techniques 17.4 (2021): 319-331.
- Yin Chuanlong, Zhu Yuefei, JinlongFei G., He Xinzheng “A deep learning approach for intrusion detection using recurrent neural networks”, IEEE Access, 5 (2017), pp. 21954-21961
- Limouchi, Elnaz, and Imad Mahgoub., "Reinforcement Learning-assisted Threshold Optimization for Dynamic Honeypot Adaptation to Enhance IoBT Networks Security", 2021 IEEE Symposium Series on Computational Intelligence (SSCI). IEEE, 2021.
- Priyadarsini, Pullagura Indira., "ABC-BSRF: Artificial Bee colony and borderline-SMOTE RF algorithm for intrusion detection system on data imbalanced problem", Proceedings of International Conference on Computational Intelligence and Data Engineering: ICCIDE 2020. Springer Singapore, 2021.
- Zhang, Ting, et al. "An Evolutionary-Based Approach for Low-Complexity Intrusion Detection in Wireless Sensor Networks", Wireless Personal Communications (2021): 1-24.
- Thilagam, T., and R. Aruna., "Intrusion detection for network-based cloud computing by custom RC-NN and optimization", ICT Express 7.4 (2021): 512-520.
- Wang, Ning, et al., "Manda: On adversarial example detection for network intrusion detection system", IEEE Transactions on Dependable and Secure Computing, 2022.
- Liu, Gao, et al., "SeDID: An SGX-enabled decentralized intrusion detection framework for network trust evaluation", Information Fusion 70 (2021): 100-114.
- Atefinia, Ramin, and Mahmood Ahmadi., "Network intrusion detection using multi-architectural modular deep neural network", The Journal of Supercomputing 77.4 (2021): 3571-3593.
- Abdollahzadeh, Benyamin, Farhad Soleimanian Gharehchopogh, and Seyedali Mirjalili, "African vultures optimization algorithm: A new nature-inspired metaheuristic algorithm for global optimization problems", Computers & Industrial Engineering 158 (2021): 107408.
- Varela-Santos, Sergio, and Patricia Melin, "A new modular neural network approach with fuzzy response integration for lung disease classification based on multiple objective feature optimization in chest X-ray images", Expert Systems with Applications 168 (2021): 114361.
- Safaldin, Mukaram, Mohammed Otair, and Laith Abualigah, "Improved binary gray wolf optimizer and SVM for intrusion detection system in wireless sensor networks", Journal of ambient intelligence and humanized computing, 12.2 (2021): 1559-1576.
- Sinha, Somnath, and Aditi Paul.,"Neuro-fuzzy based intrusion detection system for wireless sensor network", Wireless Personal Communications, 114.1 (2020): 835-851.
- Elsaid, Shaimaa Ahmed, and Nouf Saleh Albatati, "An optimized collaborative intrusion detection system for wireless sensor networks", Soft Computing 24.16 (2020): 12553-12567.


