An Energy Efficient and Secure Clustering Protocol for Military based WSN
Автор: Prachi
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 1 vol.9, 2017 года.
Бесплатный доступ
Less contiguous nature of military applications demands for surveillance of widespread areas that are indeed harder to monitor. Unlike traditional Wireless Sensor Networks (WSNs), a military based large size sensor network possesses unique requirements/challenges in terms of self-configuration, coverage, connectivity and energy dissipation. Taking this aspect into consideration, this paper proposes a novel, efficient and secure clustering method for military based applications. In any clustering based approach, one of the prime concerns is appropriate selection of Cluster Heads and formation of balanced clusters. This paper proposes and analyzes two schemes, Average Energy based Clustering (AEC) and Threshold Energy based Clustering (TEC). In AEC, a node is elected as Cluster Head (CH) if its residual energy is above the average energy of its cluster whereas in case of TEC, a node is elected as Cluster Head if its residual energy is above the threshold energy. Further, both AEC and TEC choose nodes as CHs if their distance lies within safety zone of the Base Station. In this paper, aim is to come up with a solution that not only conserves energy but balance load while electing safe nodes as CHs. The performance of proposed protocols was critically evaluated in terms of network lifetime, average residual energy of nodes and uniformity in energy dissipation of nodes. Results clearly demonstrated that AEC is successful in incorporating security whilst increasing overall lifetime of network, load balance and uniform energy dissipation.
Energy, Clustering, Protocol, Sensor, Network, Military
Короткий адрес: https://sciup.org/15011741
IDR: 15011741
Текст научной статьи An Energy Efficient and Secure Clustering Protocol for Military based WSN
Wireless sensor Networks (WSNs) are used by the Military for a diversity of purposes ranging from surveillance, enemy tracking and army protection [1]. Network Centric Warfare (NCW) [2] incorporates the idea of networking sensors, commanders and attackers to reduce the operational gap, increase protection, precision and speed of reaction to conduct effective operations. NCW is explored by many military forces across the world to facilitate mobility, increase Intelligence, Surveillance and Reconnaissance capabilities in a flexible and autonomous battlefield where commanders can see, decide and shoot in real time due to pre-awareness of situation. Usage of these systems leverages military to implement new decisions incrementally and quickly to stay ahead in terms of security and requirements of soldiers instead of taking one modernization decision and applying it across army for decades as done in the past.
However, advantages of WSN comes up with several limitations in terms of limited energy due to battery operated sensors which in turn leads to short network lifetime and limited abilities in terms of storage, computation and communication. Moreover, sensors are deployed in harsh environments at remote locations without human intervention.
However, majority of challenges such as energy, delay are application driven. For example, in a habitat monitoring application, there is no bound on acceptable delay however in case of a military based WSN where nodes are more often deployed in enemy area so they can be easily captured by the enemies; even a small delay is unacceptable.
Although a significant amount of research is already done in traditional sensor networks, off-the-shelf sensor network fails to offer the solution due to tactical constraints and unique requirement of remote and large sized surveillance environments. Solutions already developed for military based sensor models can operate in small geographical region with a few numbers of nodes but not in remote and large sized environment with thousands of randomly deployed nodes because uniform, planned deployment and monitoring of sensors is possible in the small geographical area but not in military based large scale applications where nodes are randomly through different aerial methods in an uncontrolled manner to form an adhoc network [3-4].
Further, efficient utilization of battery remains a very crucial issue for wireless sensor networks. According to pottie et al. [7], communication consumes 80% of node’s energy. Especially, in case of remote battlefield it became next to impossible to recharge them [6-8]. Therefore, uniform dissipation of energy among sensor nodes is crucial to ensure entire region coverage and prolong the network lifetime by efficient utilization of sensor nodes battery.
It is clear from the literature [9-10] that cluster based approaches optimize network bandwidth, energy efficiency, service delivery, filter duplicate values while addressing scalability and reducing number of relayed packets to the BS at the same time. In case of clustering, nodes are grouped in the form of clusters where each cluster has a CH and rest of the nodes acts as member nodes of that cluster. However, a CH dissipates more energy than a member because CH has extra responsibilities to carry out. This leads to quick energy depletion of CHs and nodes acting as CHs will die very quickly. This will create a vacuum in the network. Therefore, role of CH should be shared among network nodes to ensure load balancing. Moreover, clustering is also capable of handling data redundancy caused by densely deployed sensors in a very effective manner by using data aggregation techniques at the Cluster Head level.
Additionally, unlike other WSNs military based WSN are deployed in human areas therefore security became a very critical concern. Especially in remote, large size networks security of CHs plays a very important role. Once captured, CHs can reveal more sensitive information about a group of nodes and hence threaten the security of the entire network.
Taking this goal into consideration, a safe and energy efficient clustering protocol for a remote and large size military based WSN should be designed to cater the special needs of such networks.
The remaining sections of this paper are organized as follows: Section II discusses about the Related work in this field. Section III discusses the basis of protocol. A novel Average Energy based Clustering protocol is proposed in Section IV. Simulation results and analysis is presented in Section V. Section VI concludes the paper.
-
II. Related Work
A number of clustering protocols have been introduced in recent literature for WSNs. However, this section focuses on important ones.
Low Energy Adaptive Protocol (LEACH) [11] was the first dynamic clustering protocol proposed for Wireless Sensor networks. It assumed that every node is reachable from in a single hop. It assigns each node a fixed probability to nominate itself as CH on the basis of number of CHs required and number of times that node has been CH so far. Election of CHs and formation of clusters occurs after each iteration so residual energy of nodes is not taken into consideration before re-initiating clustering process again and again. This leads to lots of energy dissipation. Additionally, LEACH set no limits on number of minimum or maximum member nodes in a cluster. Therefore, LEACH left many loopholes.
To tackle the problem of randomized CHs and residual energy, LEACH-C [12] was presented where CHs are elected at optimal locations to ensure coverage of entire network. Authors implemented centralized LEACH-C where BS decides which node should act as a CH on the basis of information sent by all nodes regarding their location and energy levels to the BS. However, this increases lots of data transmission in the direction of the BS and congest transmission lines.
Younis et al. proposed Hybrid Energy-Efficient Distributed Clustering (HEED) [13], a multi-hop clustering protocol proposed for WSN. It chooses the
CHs on the basis of distance among nodes. This protocol mainly focuses on the method of CH selection. It selects the CHs on the basis of residual energy. Nodes determine which cluster to join on the basis of intra-cluster communication cost.
Energy Efficient Clustering Scheme (EECS) [14] was presented by Ye et al. where candidate CHs broadcast their residual energy to neighboring candidates and a node elect itself as CH if it doesn’t find any neighboring candidate with more than its residual energy. It focuses on dynamic sizing of cluster on the basis of cluster distance from the BS.
Zahmati et al. proposed Energy Efficient Protocol with Static Clustering (EEPSC) [15] where members of a cluster will remain same, only CH changes on the basis of election criteria. This protocol selects a node as CH if it has maximum energy in a particular region. It provides better results in comparison to previously proposed protocols because instead of re-establishing cluster again and again (dynamic clusters) this protocol use static clusters, only CHs are updated periodically on the basis of node’s residual energy. However, EEPSC often selected nodes located near boundary as CHs. This causes an increase in communication overhead of nodes located on opposite boundary. To provide spatial distribution of nodes in the network and gain better results, Enhanced Energy Efficient Protocol with Static Clustering (EEEPSC) was presented by Chaurasiya et al. [16].
Both EEPSC and Enhanced EEPSC selected temporary CH that adds overhead to both the protocols. Nayak et al. addressed these issues in Front Leading Energy Efficient Cluster Heads (FLEECH) protocol [17]. FLEECH outperforms the EEEPSC because it also considers the distance of a node to all its neighbours while electing a node as CH. Although the alive node retention rate is greater in this protocol but it suffers from the problem of improper area division and load unbalance.
Improved energy aware distributed clustering protocol (EADC) [18] was proposed in 2016 by V Gupta to extend the network lifetime in different scenarios.
It is clear from the above discussion that majority of earlier proposed cluster based architectures focused only on efficient energy utilization but failed to incorporate other quality of service parameters[19] such as security, node degree, etc. Taking this factor into account, this paper propose a clustering protocol where members of clusters are fixed but role of energy intensive CH is shared among all the nodes.
-
III. Basis for Protocol
This section discusses about the radio based energy dissipation model and various parameters that are taken into consideration while designing the protocol.
-
A. Radio Energy Model
Hein Zelman et al. [11] proposed a radio based energy dissipation model to calculate the energy consumption by sensor nodes. The proposed model uses both free space as well as multipath fading channel model according to the distance between transmitter and receiver. If distance between 2 devices is less than threshold then free space model with d2 is used otherwise multipath fading model with d4 is used. According to this model, transmitter dissipates energy to run radio electronics and power amplifier and receiver dissipates energy to run radio electronics. Therefore, to transmit a m-bit message over a distance d using this model, the radio energy expenditure is given as:
ETxm m, d ) = «
m * E elec
+ m* e/s * d 2, if d < d0
m * E elec
+ m * e mp * d 4 , f d ^ d o
>
where, threshold
o
E fs
^ ^ mp
To receive a m-bit message, energy expenditure by the radio is
ERX ( m )= m * Eelec (2)
where, Eelec =50nJ/bit is the energy required to run transmitter/receiver circuitry, = 10pJ/bit/m2 is the energy consumed by the amplifier for shorter distance and = .0013pJ/bit/m4 is the energy consumed by the amplifier over longer distances. Energy expenditure for data aggregation (EDA) is 5nJ/bit/message.
In a homogenous WSN, CHs are selected from all the nodes on the basis of certain parameters, parameters may vary according to the requirement of application. All the non-cluster nodes forward their sensed information to the
CH. CH aggregates all information and forwards it to the BS. Let n number of nodes are randomly distributed over a geographical area A*A. If l number of clusters exists in the network then ideally each cluster should carry
I n )
I у I nodes per cluster. Subsequently, there will be 1 CH
and
n 1 I
--1 I members in a cluster.
l J
Therefore, energy consumed by a CH in receiving the information from its members, aggregating and forwarding it to the BS is given as:
Eek c * SM * I у - 1 I + E da * SM * у + E tx ( m , d ) (3)
where, SM= number of bits in the message send by the sensors to their CH.
Energy consumed by a non-CH in receiving the broadcast message from CHs and transferring the sensed information to the CH in the cluster is given as:
E elec * CM * l + E tx ( m , d ) (4)
where, CM= number of bits in the message send by the CHs.
-
B. Important parameters
This subsection discusses the different parameters that are taken into account while designing clustering protocol for a military based WSN:
-
• Security: Wireless Sensor Networks are used in military applications for monitoring militant activities like tracking of enemies and force protection. In case of clustering, CH is the critical node that holds and processes data for its member nodes. Once captured, it can reveal lots of sensitive information to the adversaries. To ensure protection of militants, network nodes are divided into 2 categories: safe and unsafe nodes. Assuming the BS as safest position in the network, nodes within safety threshold distance from the BS are considered as safe nodes whereas the nodes outside the safety threshold distance (lying in enemy territory) are considered as unsafe.
-
• Energy: Sensor nodes possess limited energy and once deployed in a battlefield environment or enemy territory, it became very difficult to recharge them. In case of clustering, major portion of energy is consumed due to frequent re-election of CHs and formation of cluster. To minimize the energy dissipation of battery operated sensors, instead of running CH election process periodically it should be invoked as rarely as possible. It will reduce communication cost significantly.
-
• Node proximity: Node proximity is average distance of neighboring nodes to a node. Nodes are considered within neighborhood of a node if they are within its transmission range. If average distance of neighboring nodes to a node is less than transmission distance of messages within a cluster will be reduced and this will result in reduction in transmission distance and enhance overall lifetime of the network.
-
• Node degree: Every CH can support only a predefined number of members to ensure proper medium access control functioning. If a CH involves more number of members then more delay will occur because nodes need to wait longer for their turn. This delay can be very critical in battlefield environment and cause life threatening situations. Clustering algorithm should take this thing into account and assign equal number of members to each CH.
-
• Transmission range: Since longer transmission consumes more energy so nodes should be assigned to their nearest CH. If the degree of a CH reaches to its maximum then node will be assigned to next nearest CH. The PDF document should be sent as an open file, i.e. without any data protection.
-
IV. Average Energy based Clustering (AEC) Protocol
-
A. Assumptions
This subsection discusses the assumptions about proposed clustering protocol:
-
• The WSN formed by the nodes and the communication links can be represented with the help of an undirected graph G= (V,E), where V denotes the set of nodes v i and E denotes the wireless links e i .
-
• Every node has a unique ID and is randomly deployed in the 2-dimensional geographical region.
-
• All nodes are static and battery operated i.e. they possess limited amount of energy.
-
• Nodes possess the capability to adjust their transmission power according to their roles either as a CH or as a normal node.
-
• All sensor nodes are homogenous in nature i.e. they possess same capabilities in terms of transmission range, battery, etc i.e. they are homogeneous in nature.
-
• The BS is considered as a trusted and powerful node with unlimited battery, huge processing power and a pre-determined location.
-
• Every node possesses the data aggregation capability to reduce the amount of redundant information.
-
B. Proposed Protocol
Based on the above discussion, a new energy efficient, safe weight based clustering protocol is proposed in this paper that takes into consideration the above factors. Weightage of parameters can vary according to the application requirements. Proposed ES-WCP runs in three phases: CH election phase, cluster formation phase and data transmission phase.
-
• CH election phase:
During the CH election phase, first 3 factors i.e. security, energy and node proximity are taken into consideration with weight coefficients α, β and γ respectively. Last 2 factors, node degree and transmission range are taken into consideration in cluster formation phase.
During the 1st round,
-
a. Assign value to weight coefficients α, β and γ such that a + в + Y = 1
-
b. Initialize safety_threshold to a fixed value according to the military application requirement.
-
c. Determines security of all network nodes by calculating the distance of node from the BS:
for every node vt E G do end for
-
d. Initialize Security Index of network nodes
for every node vt E G do set v.SI = 0
end if end for
-
e. Calculate distance of a node from its neighbors DNi:
for every node v E G do
DN = £ dist (v,., v) if dist (v,., vy)< trange
VjEV, v * vj where trange is the transmission range of v E G .
end for
-
f. In the 1st round, current energy of every node v . CE is same.
-
g. Now, determine the Weight factor:
for every node v E G do
W = a * v . SI + в * vt -CE + Y * ( - DN )
end for
DN i is taken as negative because average distance should be minimum.
-
h. Initialize countCH as round(0.1*n); //10% of nodes are required to act as CH Set of CHs, S E V ( G ) as {φ};
for every node v E G do if countCH>0
Assign node with maximum W i to the set of CHs and remove this Wi from the list
S= v4 with max ( W ),...
countCH--;
end if end for
To avoid frequent re-election of CHs in subsequent rounds, CHs elected in the first round evaluate the average energy of their cluster periodically whenever the current energy of CH is below the cluster’s average energy, member with maximum Wi in the cluster will be elected new CH. In AEC, 10% of the network nodes are chosen as CH to balance between transmission distance and aggregation.
-
• Cluster formation phase:
In this phase, nodes are assigned to their nearest CH in the network to ensure network connectivity, minimize transmission distance of messages, energy consumption and enhance overall lifetime of the network. If degree of the nearest node reaches to its maximum then AEC assigns the node to next nearest CH to ensure load balance and minimize latency in data transmission.
for every vt G G do broadcast a message to nodes within transmission range.
end for for every for every node vt G G do select nearest CHi such that vt G 5 if Degree(CH) < Ideal _ Degree
Assign v i to CH i else
Assign vi to next nearest CHi end if end for
-
• Data Transmission Phase
After the election of CHs and formation of clusters, next step is to transmit data from the network nodes to the BS. Cluster nodes can directly transmit data to their CH. However, this paper focuses on military based applications and nodes lying near to the BS have given higher priority by making a tradeoff between security, energy and intra cluster distance. However, there may arise situations where distance between node and their CH may be comparatively large. This may leads to quite substantial energy dissipation while transmission. To avoid such kind of situation, AEC facilitates multi-hop transmission for intra-cluster communication if distance between a node and its CH is large.
Moreover, to minimize amount of transmission and hence energy dissipation nodes send data to their CH turnwise. To achieve this objective, AEC uses TDMA as medium access control protocol. This protocol also helps us to avoid collision among nodes within a cluster.
-
V. Simulation Results and Analysis
In this section, AEC and TEC protocol are implemented and their performance is evaluated and tested through several simulations in a MATLAB environment [20]. Performance of AEC protocol is compared with TEC protocol to compare the scenario where instead of electing a new CH whenever its current energy is less than average energy of cluster, new CH is chosen only when energy of current CH falls below a certain threshold. Both the protocols have been implemented and evaluated by using the simulation parameters as described in Table 1.
Table 1. Simulation Parameters
|
Parameters |
Value |
|
Network Area |
100*100m2 |
|
No. of Nodes |
100 |
|
Safety Threshold of monitoring area |
60m |
|
Base Station Location |
(50,50) |
|
Topology |
Random |
|
Initial energy of network nodes |
2 Joule |
|
Packet size |
4000 bits |
|
Transmission Range |
30m |
|
Energy Threshold |
0.5 J |
-
A. Simulation Environment
Our simulation environment consists of 100 nodes randomly deployed in a 100m*100m geographical region. The BS is located in the center of geographical region. All nodes have a transmission range (trange) of 30m. Safety threshold for the network nodes is set as 60m.
-
B. Discussion and Results
To evaluate AEC protocol, around 25 simulations are carried out and average values are captured for parameters (network lifetime (α), average residual energy of nodes (β) and uniformity in energy dissipation (γ)) to get more accurate results. This section provides experimental results and discussions. The value of weight coefficient used for simulation were α=0.4, β=0.4 and γ=0.2. These values are arbitrary and can be changed according to application requirements.
-
• Network lifetime: WSN survival time can be determined with the help of number of dead nodes at a particular instance of time.
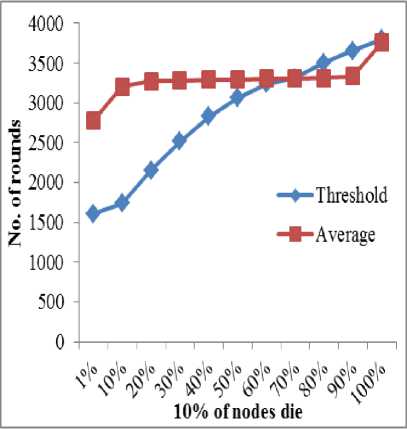
Fig.1. Network Survival W.R.T Number of Rounds
To determine the network survival time, we evaluate dead rate of AEC and TEC w.r.t number of rounds. During the simulation, value of threshold energy is set as 0.5J. Figure clearly depicts that AEC simply outperforms the TEC. In case of TEC, initial three nodes die in 1607th, 1611th and 1650th rounds respectively whereas in case of AEC, first three nodes die in 2783th, 2877th and 3011th rounds respectively. Moreover, it is evident from fig. 1 that 70% of network nodes die more quickly in TEC in comparison to AEC.
-
• Average Residual Energy of Nodes: In order to understand the trend in energy dissipation, average of residual energy of network nodes in different rounds is shown in Table 2 for Threshold Energy based Clustering with Average Energy based Clustering. Initially, every node is assigned 2J energy. With every communicating round, some energy of each network node is consumed either in the role of a network node or in the role of a CH. It is clear from the above table that difference in average residual energy increases with number of rounds.
Table 2. Average Residual Energy of Nodes
|
No. of Rounds |
TEC |
AEC |
|
100 |
1.9127 |
1.9145 |
|
200 |
1.8254 |
1.8287 |
|
300 |
1.7380 |
1.7432 |
|
400 |
1.6507 |
1.6575 |
|
500 |
1.5634 |
1.5720 |
|
600 |
1.4761 |
1.4870 |
|
700 |
1.3888 |
1.4015 |
|
800 |
1.3015 |
1.3161 |
|
900 |
1.2141 |
1.2305 |
|
1000 |
1.1270 |
1.1451 |
|
1100 |
1.0419 |
1.0598 |
|
1200 |
0.9571 |
0.9741 |
-
• Uniformity in Energy dissipation: Network
connectivity is another crucial issue [13-15] in military based sensor networks. Missed or delayed information due to few isolated nodes, may result in a wrong decision on a battlefield. Real-time data dissemination to higher authorities (the Base Station) became more crucial in military applications due to sensitivity of mission. To ensure entire network coverage, uniform energy dissipation is a must.
In case of TEC, random energy dissipation is observed throughout the network lifetime. Some of the network nodes possess relatively less energy in comparison to other nodes of the network at a particular instance of time. However, in case of AEC, energy dissipation is very uniform among the nodes. Figure 2 shows trend in energy dissipation in nth round, in this example 500th round.
Uniform energy dissipation helps in coverage of entire network for a longer period of time because in case of TEC some nodes dissipates more energy than others and there is possibility that these nodes die before the rest of the network. This can cause coverage problem in the network which can be very critical for a military based application.
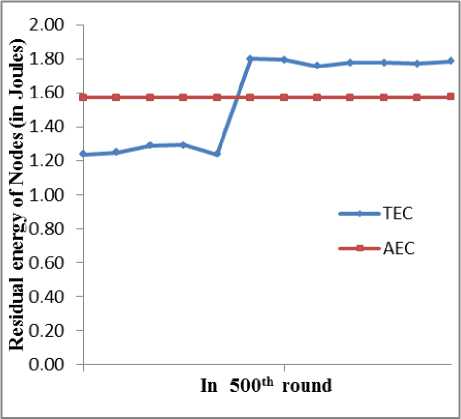
Fig.2. Residual Energy of Nodes in 500th Round
-
VI. Conclusion
This paper proposed a safe and energy efficient clustering protocol for military based WSN. Safety of nodes is taken into consideration while selecting nodes as CHs because nodes lying in enemy territory may cause huge losses in terms of human life in a military based environment. However, if all nodes near to the BS are elected as CHs then this leads to quick energy depletion of secure nodes and creates vacuum between the BS and rest of the network. AEC chooses nodes as CHs on the basis of weight determined in terms of safety index, current residual energy and node proximity. To ensure load balancing, role of CH is circulated among the network nodes. Whenever current energy of a CH is lesser than average energy of all members of a cluster then new CH is elected from the members of the cluster on the basis of maximum weight at that point of time. Performance of AEC protocol is compared with TEC protocol and results show that average energy based CH selection procedure helps in uniform energy dissipation over the network. This further helped us to achieve coverage of the entire geographical region and enhance overall network lifetime in comparison of TEC protocol.
Список литературы An Energy Efficient and Secure Clustering Protocol for Military based WSN
- L. Lamont, M. Toulgoat, M. Déziel, and G. Patterson, "Tiered wireless sensor network architecture for military surveillance applications," Proc. of the 5th International Conference on Sensor Technologies and Applications, SENSORCOMM 2011, Nice, France, August 21-27, 2011
- I. Bekmezci and F. Alagöz, "Energy efficient, delay sensitive, fault tolerant wireless sensor network for military monitoring," Int. J. Distributed Sensors Network, vol. 5, no. 6, pp. 729–747, 2009.
- David S. Alberts, John J. Garstka, Frederick P. Stein, "NETWORK CENTRIC WARFARE: Developing and Leveraging Information Superiority", 2nd Edition, CCRP Press.
- K. Sohrabi et al., Protocols for self-organization of a wireless sensor network, IEEE Personal Communications, vol. 7, no. 5, 16–27, 2000.
- Pottie G. J., Kaiser W. J., "Wireless Integrated Network Sensors", Communications of ACM, Vol. 43, No. 5, pp. 51-58, May 2000, DOI: 10.1145/332833.332838.
- S. K. Singh, M. Singh, and D. K. Singh, "Routing protocols in wireless sensor networks—a survey," International Journal of Computer Science & Engineering Survey, vol. 1, no. 2, pp. 63–83, 2010.
- G. Kalpana and T. Bhuvaneswari, "A survey on energy efficient routing protocols for wireless sensor networks," International Journal of Computer Applications, vol. 86, no. 12, pp. 12–18, 2011.
- Q. Cao, T. Abdelzaher, T. He, and R. Kravets, "Cluster-based forwarding for reliable end-to-end delivery in wireless sensor networks," in Proceedings of the 26th IEEE International Conference on Computer Communications (IEEE INFOCOM '07), pp. 1928–1936, Anchorage, Alaska, USA, May 2007.
- Mhatre V., Rosenberg C., "Design Guidelines for Wireless Sensor Networks: Communication, Clustering and Aggregation", Ad hoc Networks, Vol. 2, no. 1, Jan. 2004, pp. 45-63.
- M. Dohler, "Kumar's, Zipf's and Other Laws: How to Structure a Large-Scale Wireless Network?", Annals of Telecommunications, vol. 63, no. 5-6, pp. 239-251, Jun 2008.
- Heinzelman W. B., Chandrakasan A., Balakrishnan H., 'Energy Efficient Communication Protocol for Wireless Microsensor Networks', 33rd IEEE International Conference on System Sciences, ISBN: 0-7695-0493-0, Jan-2000
- Heinzelman W. B., Chandrakasan A., Balakrishnan H., 'An Application-Specific Protocol Architecture for Wireless Microsensor Networks', IEEE Transactions on Wireless Communications, Vol. 1, Issue 4, ISBN: 1536-1276, pp. 660-670, Oct-2002.
- O. Younis and S. Fahmy, "HEED: A Hybrid Energy-Efficient Distributed Clustering Approach for Ad Hoc Sensor Networks," IEEE Transactions on Mobile Computing, vol. 3, no. 4, Oct-Dec 2004.
- M. Ye, C. Li, G. Chen, and J. Wu, EECS: An Energy Efficient Clustering Scheme in Wireless Sensor Networks, National Laboratory of Novel Softaware Technology, Nanjing University, China. 2006
- Amir Sepasi Zahmati, B. Abolhassani, A. A. B. Shirazi, A. S. Bakhtiari, 'Energgy Efficient Protocol with Static Clustering', World Academy of Science, Engineering and Technology, International Journal of Computer, Electrical, Automation, Control and Information Engineering, Vol. 1, No. 4, 2007.
- Chaurasiya S. K., Pal T., Bit S. P., "An Enhanced Energy-Efficient Protocol with Static Clustering for WSN", International Conference on Information Networking (ICOIN), ISBN: 978-1-61284-661-3, pp. 58-63, Jan 2011.
- Nayak B. K., Mishra M., Rai S. C., Pradhaan S. K., 'A Novel Cluster Head Selection Method for Energy Efficient Wireless Sensor Network', IEEE International Conference of Information Technology (ICIT), ISBN: 978-1-4799-8083-3, pp. 53-57, Dec-2014.
- Vrinda Gupta, Rajoo Pandey, An Improved Energy Aware Distributed Clustering Protocol for Wireless Sensor Networks, I. J. Computer Network and Information Security, Jun 2016, vol. 8, no. 6, 29-37
- Hamid Karimi, Mehdi Kargahi, Nasser Yazdani, "Energy-Efficient Cluster-Based Scheme for Handling Node Failure in Real-Time Sensor Networks", 2009 Eighth IEEE International Conference on Dependable, Autonomic and Secure Computing
- MATLAB - The Language of Technical Computing www.mathworks.com/products/matlab/


