Analysis and Estimation of Noise in Embedded Medical Images
Автор: C Nagaraju, S S ParthaSarathy
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 3 vol.7, 2015 года.
Бесплатный доступ
Patient information is embedded inside the medical images for the storage or transmission, or healthcare applications. In medical image processing, various types of noises corrupt the image quality. There is a need of measure specific noise for a particular image is required for the evaluation of robustness for embedding techniques used for hiding patient information in medical images. It is very important to obtain precise images to facilitate accurate analysis and estimation of noise in embedded medical image. The current work is focused towards studying the effect of specific noise which affect particular medical image. The strength of the medical image is tested by introducing several attacks to the embedded medical images. The statistical quantity measures like peak signal-to-noise ratio (PSNR), signal-to-noise ratio (SNR) and normalized root mean square error (NRMSE) are employed to measure the quality of the output medical image.
Embedding, Healthcare, Medical Image, Noise, Patient Information, Robustness
Короткий адрес: https://sciup.org/15013537
IDR: 15013537
Текст научной статьи Analysis and Estimation of Noise in Embedded Medical Images
Published Online February 2015 in MECS
A Digital Watermark includes data, image or any secret piece of information embedded inside a host image or a video sequence to provide rightful ownership [1] and to prevent misuse of the image, video or data. Further, these techniques extended to carry vital information [2] inside a cover image or video for transmission and reception under privacy. Data Hiding Technique should have the robustness [3], Visual imperceptibility and an Optimal Embedding Capacity [4]. Hiding information inside image or other media in such a way that no-one apart from the sender and intended recipient even realizes there is a hidden information [5-8].
The image with hidden information is transformed from the source. The Receiver side incorporates the watermark extraction process where hidden information is collected at this location. In between the embedding and extraction process, there is communication channel which is predominant with noise which tends to corrupt and degrade the watermarked image. The effects of those channel disturbances [11] can be simulated by addition of noise, rotating the watermarked image and cropping the image which is equivalent to a person trying to destroy the vital piece of hidden information.
In medical image processing, it is very important to obtain precise images to facilitate accurate observations for the given application. Low image quality is an obstacle for effective feature extraction, analysis, recognition and quantitative measurements. Therefore, there is a fundamental need of noise reduction from medical images. There are currently a number of imaging modalities that are used for study of medical image processing. Among the newly developed medical imaging modalities, Magnetic Resonance Imaging (MRI) and Ultrasound imaging are believed to be very potential for accurate measurement of organ anatomy in a minimally invasive way. In this paper, MR image and Ultrasound image are experimented to remove noise. MRI is a powerful diagnostic technique. However, the incorporated noise during image acquisition degrades the human interpretation, or computer-aided analysis of the images. Noise in MR images obeys a Rician distribution. Unlike additive Gaussian noise, Rician noise is signaldependent and consequently separating signal from noise is a difficult task. Ultrasound imaging is widely used in the field of medicine. It is used for imaging soft tissues in organs like liver, kidney, spleen, uterus, heart, brain etc. The common problem in ultrasound image is speckle noise which is caused by the imaging technique used that may be based on coherent waves such as acoustic to laser imaging.
Medical imaging is a method used to create images of the human body for clinical purposes or medical science. Diagnostic imaging includes a wide variety of scans, examinations and image modalities that are used in the medicine field such as X- Ray, computed tomography (CT), magnetic resonance imaging (MRI) and ultrasound (US) X- Ray, CT, MRI and ultrasound images are widely used in the field of medicine. These images are used for imaging soft tissues in organs like liver, chest, kidney, spleen, uterus, heart, brain etc. Unfortunately, medical images are affected by a various number of noises such as Poisson, Rician, Gaussian and impulse noise (salt and pepper noise).The common problem in these image is noise which is caused by [9, 10] different area.
Embedding patient information inside medical image has attracted attention of researchers nowadays. Instead of focusing on the study of noise on embedded medical image authors attempted to develop a new methodology which includes impact of specific noise on a particular medical image.
According to the watermarking, an attack is any processing that may mess up detection of the watermark or communication of the information provided by the watermark. The processed, watermarked data is then called attacked data. Robustness against attacks is an important issue for watermarking schemes. Attacks are generally occur during transmission of the watermarking image. There are many major attacks and they are tested in the proposed work.
The main source of noise in digital images arises during image acquisition or during image transmission. Major factors that affecting the amount of noise in the medical image is acquiring images with CCD camera, sensor temperature and light levels. Medical images are corrupted during transmission from source to destination. The principal reason is noise which is interfering in the channel during transmission [12]. The noisy image model is given by
Nr (i,j) = l(i, j) + Ni, j) (1)
Where I ( i , j ) the original image pixel is value and N ( i , j ) is the noise in the image and Nr (i , j ) is the resulting noise image . t he entire process of the proposed method is given in the form of flowchart in figure 1.
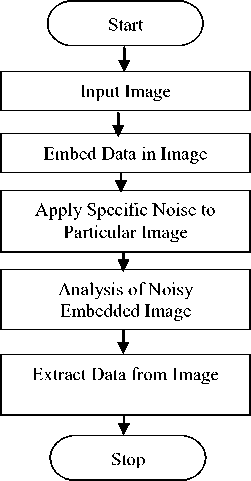
Fig. 1. Flow chart of proposed scheme
Different Noise Model which results in degrading image quality of the specific modality are discussed below.
-
A. Poisson noise [ X-Ray]
The noise in X-Ray imaging is sculptural with Poisson noise [14]. X-Ray photons incident on a receptor surface in random pattern and can’t force them to be evenly distributed over the receptor surface. One spot of the receptor surface might collect a lot of photons than another spot, even once each the spots are exposed to identical average X-Ray intensity. Using gamma or X-Ray photons most of the image noise is produced by the random behavior of the photons that are distributed within the image. This is known as quantum noise. Every individual photon could be a quantum of energy. It is the quantum structure of the X-Ray beam that makes quantum noise [13].
A Poisson model assume that each pixel x of an image f ( x ) is drawn from a Poisson distribution of parameter Я = f 0 ( x ) where f is the original image to recover. The Poisson density is given as
P (f( x ) = k ) =
Я е Я k !
-
B. Rician Noise
Rician noise which arises from complex Gaussian noise corrupts the MR images. The Rician probability density function for the corrupted image intensity x is given by
P(x ) =
x exp c2
—
x2 + k
2c2
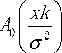
Where k is the underlying true intensity, σ is the standard deviation of the noise, and A0 is the Modified zeroth order Bessel function of the first kind.
-
C. Speckle Noise
Speckle noise is a granular noise that inherently exists in and degrades the quality of the Ultrasound image. Speckle noise is random and deterministic along with it has negative impact on ultrasound image. The effect of radical reduction in contrast resolution is the key factors in reducing quality of ultrasound image compare to other image modality. According to literature, speckle noise is known as “texture”, and may possibly contain useful diagnostic information [15]. In General speckle model is represented as,
Ei,j ) = / ( i , j ) * s ( i , j ) + Ki, j ) (4)
where E ( i , j ) is the Noisy image, I ( i , j ) and K ( i , j ) is the multiplicative and additive component of the
Speckle noise. Considering multiplicative component and ignoring additive component of the noise, equation (1) is modified as;
E ( i, j ) = / ( i , j ) * s ( i , j ) (5)
-
D. Impulse Noise
Impulse noise is frequently encountered in medical image during acquisition, storage and processing. The presence of impulse noise in medical image may be either relatively high or low. Due to this it degrades the image quality and causes some loss of image information details. Salt and pepper is one of the important noises among several types of impulse noise.
-
a. Salt and Pepper Noise
Salt and pepper noise is a typical form of impulse noise in a medical image which represents itself as randomly occurring white (salt) and black (pepper) pixels. The salt-and-pepper noise is also known as shot noise. Faulty memory locations, malfunctioning pixel elements in the camera sensors, or timing errors in the process of digitization will results in impulse noise. For 8-bit image the typical value for pepper noise is 0 and 255 for salt-noise.
-
E. Additive White Gaussian Noise Model Channel Noise
During transmission several types of noises usually degrade the quality of the medical images [15].White noise is the most important type of noise that occurs in communication system and is assumed to be additive. In communication system, it is often assumed that the noise is a stationary additive white Gaussian (AWGN) with power spectral density such that
G n ( / ) = N (6)
where Gn (f) is spectral density and N0 is the noise power. As per central limit theorem overall noise can be modeled as Gaussian. AWGN is a random statistical noise in the background of a communication channel. The purpose of hiding the patient information inside the medical image is to transmit diagnosis information of the patient from one clinic to another through open networks. As a result of transmission through the channel, channel noise could get added to the embedded image which could affect the accuracy of recovery of data at the receiver end [11]. To study the effect of channel noise, AWGN noise is generated and added to the embedded image.
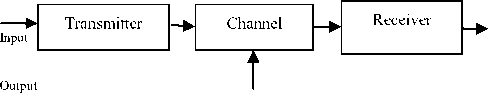
Noise
Fig. 2. Communication Channel
-
III. Performance Parameters
In order to measure the quality of the image at the receiver side, following parameters are used.
-
A. Mean Square Error (MSE)
The MSE is the cumulative square error between embedded image (image with patient information) and the original image which is defined by
1 X -1 Y -1 . .
ME = . Z Z[- ') — EM )] 2 (7)
XY i -0 j =0
Where, I is the original image and E is the embedded image and X and Y are the dimensions of the images.
-
B. Peak Signal to Noise Ratio (PSNR):
PSNR is the ratio between maximum possible power of a signal and the power of distorting noise which affects the quality of its representation. It is defined by:
PSNR = 20 log!0| 4ax ^ I 4 MSE
where max^ = 255 is the maximum intensity value that exists in the original image. A lower value for MSE means lesser error, results in high value of PSNR. Logically, a higher value of PSNR is good. Lower MSE (and a high PSNR), you can recognize that it is a better one.
-
C. Bit error rate (BER)
The most meaningful criterion for evaluation of performance of communication systems is the bit error rate (BER).To measure the quality of the proposed algorithm Bit error rate (BER) is determined after the recovery of patient information from the medical image. BER is a measure of how well bits are transferred end-to-end. BER is the ability to receive error-free information, even the medical image is affected by factors such as signal-to-noise and other distortion factors.BER is given by
BER =
jV error
N bits
where Nerror is the number of bits received in error and Nbits is the total number of bits received. BER is expressed as ten to a negative power, for example, a transmission might have a BER of 10-5, meaning that on average, 1 out of every 100,000 bits transmitted exhibits an error [4].
-
IV. Results
This section presents a detailed results and discussion obtained by the authors in the present work. The results are presented through tables and snap shots. Impulse noise and AWGN affect all types of image modality. CT image is chosen for salt and pepper noise a type of impulse noise and MRI for AWGN. The proposed method is applied on more than 100 image modality with different sizes. However the present paper shows one of them of size 128 * 128. MSE, PSNR and BER are the measurable statistical parameters, used to study the quality of interleaved images. These are the important quantitative assessment parameters adopted in the image community. The ASCII codes of the encrypted text shown in Figure 4(b) are broken into bits and interleaved into the Least Significant Bits of the image modality. Different types of attacks are applied on particular image modality which will be affected by specific type of noise. One among that resulting image is shown in Figure 3(b).
Figures 3a and 3b exhibits that the visual quality of image is always guaranteed before interleaving and after interleaving Patient information even after adding noise signal into original image. Since LSB of a pixel changes its brightness by one part in 256 interleaved image quality is not degraded which is shown in the figure 3b. It was observed that LSB technique ensure minimum degradation to original image. The PSNR and MSE values were calculated for various image modalities, with and without adding noise to the embedded image. The results obtained for images of different modalities were averaged and tabulated separately for different kinds of attacks. From the table (1) to table (5) it is clear that proposed algorithm will results in minimum MSE and maximum PSNR even when patient information is embedded inside the medical image. High PSNR or a lower MSE [16], indicates an image with minimum degradation. PSNR of the present method for the various attack on specific medical image prove that reconstructed image will match the original image. Similarly, according to the report of [17], a PSNR value in the range 20-40 indicates that the resultant image is a very good match to the original image. In accordance with this report, the results shown in table (1) to table (5) of the proposed algorithms produce PSNR values in the range 30dB to 50dB proving that the proposed algorithms does not degrade the images with the patient information inside the medical image. From the observation of figure 4(a) and 4(b), patient information embedded inside the medical image, is recovered at the receiver with zero BER, which is the most requirements for embedding Techniques.

a Original image b. Interleaved Image with Noise c. Received image
Fig. 3. Data Embedding
THE AIMS HEART FOUNDATION
BG Nagar
Name of the Doctor: Dr. Kumar
Name of the Patient: Pratham
Age: 50 years
Address: 1 st cross, Javaranahalli.
Case history:
Date of Admission: 05-08-2010
Result: T Wave inversion
Diagnosis: Suspected MI
Treatment: Sublingual Nitroglycenn.
ÔÅÁt»ÆÌÓtÅÁ»ÒÔtÂÎÖÍ¿»ÔÆÎÍ ¼ÄtÍãéãó
Вабё^юЮ^ёЧб "^jaz®№ ^al9tбetбe9t^бaббo t^o tEoiao ÍãîçtðètõêçtÐãõëçïõ¯Ðóãõêãî
»e? t ^tucaoo
»$$o^oo tzto6taoooo tEaoaoaiaeaiie ¾ãôçtêëôõðóù¯
^a6$tdet»$toooedi t®|-ffi--j®Zffi
Òçôöîõ¯tÔtØãöçtëïöçóôëðï ¿ëãéïðôëô¯tÓöôñçåõçætÌÆ
Oo9a61916 tdoaleleOaMe6odelua<;ir
THE AIMS HEART FOUNDATION
BG Nagar
Name of the Doctor: Dr. Kumar
Name of the Patient: Pratham
Age: 50 years
Address: 1 st cross, Javaranahalli.
Case history:
Date of Admission: 05-08-2010
Result: T Wave inversion
Diagnosis: Suspected MI
Treatment: Sublingual Nitroglycenn.
-
a. Original Patient Information
-
b. Encoded Patient Informatio
c. Decoded patient Information
Fig. 4. Encode and Decode of Patient Information Performance Metrics With and Without Attacks on the Watermarked Image
Table 1. Poisson Noise
|
Image Modality with Size |
Embedded Image |
Embedded Image with Noise |
||
|
PSNR |
MSE |
PSNR |
MSE |
|
|
X-Ray 128 *128 |
71.4101 |
0.0047 |
31.1006 |
50.4684 |
|
71.7218 |
0.0044 |
28.9344 |
83.1077 |
|
|
71.0842 |
0.0051 |
29.4162 |
74.3800 |
|
|
71.1902 |
0.0049 |
31.7900 |
43.0605 |
|
|
63.9979 |
0.0259 |
31.8317 |
42.6487 |
|
|
71.2622 |
0.0049 |
30.2459 |
61.4450 |
|
|
70.9638 |
0.0052 |
32.1067 |
40.0323 |
|
|
71.3541 |
0.0048 |
30.6878 |
55.5014 |
|
|
71.3913 |
0.0047 |
29.9705 |
65.4687 |
|
|
71.3355 |
0.0048 |
30.4143 |
59.1089 |
|
Table 5. AWGN with Different Variance
|
Image Modality with Size |
Embedded Image |
Embedded Image with Noise |
||
|
PSNR |
MSE |
PSNR |
MSE |
|
|
MRI 128 *128 |
71.6220 |
0.0045 |
29.7750 |
68.4834 |
|
71.5632 |
0.0045 |
29.2232 |
77.7599 |
|
|
71.0495 |
0.0051 |
28.9994 |
81.8732 |
|
|
71.8034 |
0.0043 |
29.9259 |
66.1440 |
|
|
71.2260 |
0.0049 |
29.6415 |
70.6199 |
|
|
70.8798 |
0.0053 |
29.1763 |
78.6047 |
|
|
71.2441 |
0.0049 |
28.4067 |
93.8445 |
|
|
70.8632 |
0.0053 |
28.4435 |
93.0526 |
|
|
71.4101 |
0.0047 |
29.5752 |
71.7074 |
|
|
70.8302 |
0.0054 |
29.9637 |
65.5714 |
|
Table 2. Rician Noise
|
Image Modality with Size |
Embedded Image |
Embedded Image with Noise |
||
|
PSNR |
MSE |
PSNR |
MSE |
|
|
MRI 128 *128 |
69.321 |
0.0032 |
33.676 |
53.684 |
|
71.362 |
0.0029 |
45.047 |
70.465 |
|
|
62.065 |
0.0017 |
31.276 |
67.577 |
|
|
67.256 |
0.0022 |
32.726 |
81.402 |
|
|
67.406 |
0.0020 |
35.993 |
75.415 |
|
|
69.790 |
0.0031 |
43.401 |
40.247 |
|
|
70.329 |
0.0028 |
47.620 |
41.439 |
|
|
71.432 |
0.0027 |
46.378 |
60.324 |
|
|
67.472 |
0.0021 |
35.069 |
54.496 |
|
|
68.529 |
0.0024 |
42.418 |
83.309 |
|
Table 3. Speckle Noise
|
Image Modality with Size |
Embedded Image |
Embedded Image with Noise |
||
|
PSNR |
MSE |
PSNR |
MSE |
|
|
ULTRAS OUND 128 *128 |
70.797 |
0.0050 |
38.973 |
8.235 |
|
70.863 |
0.0053 |
39.306 |
7.629 |
|
|
71.622 |
0.0045 |
40.028 |
6.460 |
|
|
71.154 |
0.0051 |
39.991 |
6.515 |
|
|
71.335 |
0.0040 |
40.011 |
6.486 |
|
|
71.372 |
0.0047 |
40.347 |
6.001 |
|
|
70.980 |
0.0052 |
35.146 |
9.879 |
|
|
71.226 |
0.0049 |
41.105 |
5.040 |
|
|
70.980 |
0.0052 |
39.109 |
7.983 |
|
|
70.732 |
0.0055 |
39.414 |
7.440 |
|
Table 4. Salt and Pepper Noise
|
Image Modality with Size |
Embedded Image |
Embedded Image with Noise |
||
|
PSNR |
MSE |
PSNR |
MSE |
|
|
CT 128 *128 |
66.261 |
0.015 |
49.776 |
0.684 |
|
66.772 |
0.013 |
51.451 |
0.465 |
|
|
65.865 |
0.016 |
50.517 |
0.577 |
|
|
66.792 |
0.013 |
52.080 |
0.402 |
|
|
71.563 |
0.004 |
51.945 |
0.415 |
|
|
66.792 |
0.013 |
54.202 |
0.247 |
|
|
71.563 |
0.004 |
51.703 |
0.439 |
|
|
66.792 |
0.013 |
53.013 |
0.324 |
|
|
66.226 |
0.015 |
51.170 |
0.496 |
|
|
66.792 |
0.013 |
53.222 |
0.309 |
|
-
V. Conclusion
This paper has presented a technique of analysis and estimation of noise during embedding patient information inside medical image. Different image modalities like X- Ray, MRI, CT and Ultrasound are used to study the effect noise on specific image. The results from the snap shot conclude that impact of specific noise after interleaving patient data inside the medical image visually agreeable. Robustness of the proposed algorithm is tested and analyzed by applying attacks to the medical image with patient data will not degrade in its quality. Calculating PSNR and MSE between original image and interleaved image with and without noise indicates that proposed algorithm is more resistive to noise attack and embedded patient information is recoverable without any distortion even in the case of attack. From the result it concludes that BER is observed to be zero, since the Patient data is recovered from interleaved image without a single data byte of loss occurred during retrieval time.
-
[1] Y. Wang, J. F. Doherty and R. E. Van Dyck, “A WaveletBased Watermarking Algorithm for Ownership Verification of Digital Images”, IEEE Transactions on Image Processing, Vol. 11, Issue 2, pp. 77-88, 2002.
-
[2] Chun Shien Lu, H.Y.M.Liao, “Multipurpose watermarking for image authentication and protection”,IEEE Transactions on Image Processing., Vol.10, Issue 10, pp.1579-1592, 2001.
-
[3] V. Licks and R. Jordan, “Digital Image Watermarking Robust to Geometric Transformations”, Proceedings of 2000 International Conference Image Processing (ICIP 2000), Vol. 3, pp. 690-693, 2000.
-
[4] Dipti Prasad Mukherjee, Subhamoy Maitra, Scott T. Acton, “Spatial domain Digital Watermarking of Multimedia Object for Buyer Authentication”, IEEE Transactions on Multimedia, Vol. 6, No.1,pp. 1- 15, 2004.
-
[5] Ran-Zan Wang, Chi- Fang Lib, and Ja- Chen Lin, “Image hiding by optimal LSB substitution and Genetic algorithm”, 2001 Pattern Recognition Society. Published
by Elsevier Science Ltd.\
-
[6] Ghoshal N., Mandal, J. K. “A Bit Level Image Authentication/Secrete Message Transmission
Technique(BLIA/SMTT)”, Association for the Advancement of Modelling & Simulation Technique in Enterprises (AMSE), AMSE journal of Signal Processing and Pattern Recognition, Vol. 51, No. 4, pp. 1-13,France, 2008.
-
[7] Ghoshal N., Mandal, J. K. et al., “Masking based Data Hiding and Image Authentication Technique (MDHIAT)”, proceedings of 16th International Conference of IEEE on Advanced Computing and Communications ADCOM-2008, ISBN: 978-1-4244-2962-2,December 14-17th, Anna University.
-
[8] Ghoshal N., Mandal, J. K. et al., “Image Authentication by Hiding Large Volume of Data and Secure Message Transmission Technique using Mask
(IAHLVDSMTTM)”, Proceedings of IEEE international Advanced Computing Conference IACC, 2009, ISBN:978-981-08-2465-5, March 6-7th, Thapar University,Patiala, India.
-
[12] Aaron S. Cohen and Amos Lapidoth, “The Gaussian Watermarking Game”, IEEE transactions on Information Theory, Vol. 48, No. 6, June 2002.
-
[13] D.T. Kuan and A.A. Sawchuk, “Adaptive noise smoothing filter for images with signal dependent noise,” IEEE Trans. Pattern Anal. Mach. Intell., vol. PAMI-7, no. 2, pp. 165–177, 1985.
-
[14] P.Subbuthai, K.Kavithabharathi S.Muruganand
“Reduction of types of Noises in dental Images” International Journal of Computer Applications Technology and Research Volume 2– Issue 4, 436 - 442, 2013.
-
[15] S.Sudha, G.R.Suresh and R.Sukanesh, “Speckle Noise Reduction in Ultrasound Images by Wavelet Thresholding based on Weighted Variance”, International Journal of Computer Theory an Engineering, Vol. 1, No. 1, April 2009. pp. 1793-8201.
-
[16] Schneier, M. and Abdel-Mottaleb, M. (1996) “Exploiting the JPEG compression scheme for image retrieval”, IEEE Trans. Pattern Anal. Mach. Intell., Vol.18, No. 8, Pp. 849–853.
-
[17] Zhang, Y. (1998) “Space-Filling Curve Ordered Dither”, Elsevier, Computer & Graphics Journal, Vol. 22, No. 4, Pp. 559-563.
Список литературы Analysis and Estimation of Noise in Embedded Medical Images
- Y. Wang, J. F. Doherty and R. E. Van Dyck, "A Wavelet-Based Watermarking Algorithm for Ownership Verification of Digital Images", IEEE Transactions on Image Processing, Vol. 11, Issue 2, pp. 77-88, 2002.
- Chun Shien Lu, H.Y.M.Liao, "Multipurpose watermarking for image authentication and protection",IEEE Transactions on Image Processing., Vol.10, Issue 10, pp.1579-1592, 2001.
- V. Licks and R. Jordan, "Digital Image Watermarking Robust to Geometric Transformations", Proceedings of 2000 International Conference Image Processing (ICIP 2000), Vol. 3, pp. 690-693, 2000.
- Dipti Prasad Mukherjee, Subhamoy Maitra, Scott T. Acton, "Spatial domain Digital Watermarking of Multimedia Object for Buyer Authentication", IEEE Transactions on Multimedia, Vol. 6, No.1,pp. 1- 15, 2004.
- Ran-Zan Wang, Chi- Fang Lib, and Ja- Chen Lin, "Image hiding by optimal LSB substitution and Genetic algorithm", 2001 Pattern Recognition Society. Published by Elsevier Science Ltd.\
- Ghoshal N., Mandal, J. K. "A Bit Level Image Authentication/Secrete Message Transmission Technique(BLIA/SMTT)", Association for the Advancement of Modelling & Simulation Technique in Enterprises (AMSE), AMSE journal of Signal Processing and Pattern Recognition, Vol. 51, No. 4, pp. 1-13,France, 2008.
- Ghoshal N., Mandal, J. K. et al., "Masking based Data Hiding and Image Authentication Technique (MDHIAT)", proceedings of 16th International Conference of IEEE on Advanced Computing and Communications ADCOM-2008, ISBN: 978-1-4244-2962-2,December 14-17th, Anna University.
- Ghoshal N., Mandal, J. K. et al., "Image Authentication by Hiding Large Volume of Data and Secure Message Transmission Technique using Mask (IAHLVDSMTTM)", Proceedings of IEEE international Advanced Computing Conference IACC, 2009, ISBN:978-981-08-2465-5, March 6-7th, Thapar University,Patiala, India.
- L. Gagnon and A. Jouan, Speckle filtering of SAR images – "A comparative study between complex-wavelet-based and stan dard filters", SPIE Proc. 3169, 80 (1997).
- B. Aiazzi, L. Alparone, and S. Baronti, IEEE Trans. on "Geoscience and Remote Sensing" 36 (5), 1466 (1998). DOI:10.1109/36.718850.
- Nopporon Chotikakamthorn and Natapon Pantuwong,"Attacks on Feature–based Affine-invariant watermarking method", the fifth international conference on computer information technology (CIT'05) 2005.
- Aaron S. Cohen and Amos Lapidoth, "The Gaussian Watermarking Game", IEEE transactions on Information Theory, Vol. 48, No. 6, June 2002.
- D.T. Kuan and A.A. Sawchuk, "Adaptive noise smoothing filter for images with signal dependent noise," IEEE Trans. Pattern Anal. Mach. Intell., vol. PAMI-7, no. 2, pp. 165–177, 1985.
- P.Subbuthai, K.Kavithabharathi S.Muruganand "Reduction of types of Noises in dental Images" International Journal of Computer Applications Technology and Research Volume 2– Issue 4, 436 - 442, 2013.
- S.Sudha, G.R.Suresh and R.Sukanesh, "Speckle Noise Reduction in Ultrasound Images by Wavelet Thresholding based on Weighted Variance", International Journal of Computer Theory an Engineering, Vol. 1, No. 1, April 2009. pp. 1793-8201.
- Schneier, M. and Abdel-Mottaleb, M. (1996) "Exploiting the JPEG compression scheme for image retrieval", IEEE Trans. Pattern Anal. Mach. Intell., Vol.18, No. 8, Pp. 849–853.
- Zhang, Y. (1998) "Space-Filling Curve Ordered Dither", Elsevier, Computer & Graphics Journal, Vol. 22, No. 4, Pp. 559-563.


