Anti-jamming and Power Minimization Interference Nulling in Uplink MIMO-NOMA Technique
Автор: Suprith P.G., Mohammed Riyaz Ahmed, Mithileysh Sathiyanarayanan
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 6 vol.16, 2024 года.
Бесплатный доступ
Non-orthogonal Multiple Access (NOMA) provides use of the power domain to boost system efficiency in the spectrum. This letter explores the use of a new transceiver design and non-orthogonal multiple access (NOMA) for MIMO uplinks. The overall energy use can be reduced while still meeting individual rate requirements by utilizing a new NOMA implementation scheme with group interference cancellation. Jamming attacks can target NOMA communication. MIMO technology is used to implement anti-jamming regulations in NOMA systems. While subsequent interference cancellation utilized to get rid of between groups interference, interference nulling at the transmitters and equalizers at the jointly designed receivers for improved power system efficiency. Where the transmitter is side, interference nulling techniques have been developed. By using the above technique, the total power consumption (dBm) which it required which it is less when compare to traditional technique like orthogonal multiple access (OMA). The outcomes of the simulation show that, in comparison to both signal alignment NOMA and orthogonal multiple-use communication, the proposed NOMA scheme typically requires less power.
Cumulative Distribution Function, Interference Nulling, MIMO NOMA, Power Allocation
Короткий адрес: https://sciup.org/15019545
IDR: 15019545 | DOI: 10.5815/ijcnis.2024.06.08
Текст научной статьи Anti-jamming and Power Minimization Interference Nulling in Uplink MIMO-NOMA Technique
This is used to generate a straight forward kind of reliability for blind network estimation methods, blocks synchronizers, and straight self-rehabilitation balancing filter banks. These methods are straightforward, small in data size, implementable online, and retain consistency (after the necessary modifications) despite the existence of sparse coloured noise [1]. You can see it by utilising the advantages of the identical connection the distance between the channel's inputs and outputs are the sub domains that the channel's impulse travels are quiet when there is no noise order and channel actions based on impulse are only influenced by the finite minimum squares flattening error sequence [2]. NOMA performs well when used in conjunction with other tried-and-true wireless communications techniques, including beam forming, communication collaboration, multiple-input multiple-output (MIMO), coding in space, time and coding for networks [3]. The exponential studies are carried both high signal-to-noise ratios (SNR) (small cell radius) as well as a poor SNR (big cell radius) in order to achieve more meaningful outcomes [4]. Massive-access scenes are made possible via a user-pairing-based suboptimal uplink multiple-access method which is created through the use of NOMA and OMA [5]. Issues with current NOMA research contributions are potential solutions are discussed [6].
When a secondary transmitter has no CSI on its connections to primary recipients, it may be possible to apply a straight forward matrix eigen value, eigen vector calculation to get the optimum answer to the QCQP problem. This is a considerably quicker technique than solving the QCQP right away [7]. The fifth generation (5G) wireless systems will be able to accommodate a variety of requirements, like high throughput, huge connection, better fairness, and low latency and reliability [8]. A user admission technique that is the best in terms of sum rate and total individuals admitted is proposed where the users' signal-to-interference-plus-noise ratio thresholds are equal [9]. The total transmit power should be reduced within the limits of the signal-to-interference-plus-noise ratio, a preceding design utilising a closed-form beam forming as well as the accompanying technologically effective incremental the design of power allocation (PA) is proposed [10]. Several rate-adjustment algorithms take user rate proportionality into consideration; as a consequence, they are marked as rate-adjustment methods with constrained-fairness [11]. By forcing the jamming signal to zero at every receiver when the BS's transmit power is insufficient, the transmit interference power can be maximised [12]. To tackle the optimisation challenge and its algorithmic challenge, we recommend a periodic approach with assured agreement to provide an upper bound and a sub optimal solution in more common circumstances [13]. If the jammer has improved its strategy, it is demonstrated that the optimal duration of training is greater than the number of transmitting antennae and nearly half of the block's total length at low signal-to-jamming-and-noise proportion [14]. Even if perfect alignment can be reduced to increase the anti-jamming performance, the second strategy, which maximises the ratio of received signal-to-interference including noise (SINR), is advocated [15].
A base station's power distribution is described as an equaliser in a NOMA system with several antennas and a smart jammer, in which the base station, acting the leader chooses the transmit power on many antennas first, and the jammer, acting as the follower, chooses the jamming power to prevent users from moving [16]. With the aid of Taylor series approximations and semi definite relaxation (SDR) techniques, the initial problem of non-convex power reduction turns become an achievable one [17]. A novel MIMO-NOMA architecture is offered to handle uplink and downstream transmissions using the concept of signal alignments. Randomization based on open loops beam forming, that is highly effective in terms of the amount of feedback data received from the individual using the terminal, the transmitter beam forming (pre-coding) matrix is managed [18]. Under certain scientific conditions, the state of equilibrium is globally most effective at minimising total power consumption [19].
A literature overview on improved efficiency, collaborative relaying, simulated blockage, power allocation schemes and disturbances within management will be addressed in the second part of this article. The system's design will be clarified in the third section. The suggested interfering eliminating technique appears in the fourth section. Discussion and results of the study are provided in the fifth part. The sixth section of the planned research assignment includes the outcome.
2. Related Works
Because of perceived availability and susceptibility to wireless methods, safe communication remains an important challenge for NOMA networks. Because the quality of service (QoS) demands for users remain the identical, especially in NOMA systems, the power used to transmit of the individual using the weak channel must be highest for conducting SIC, thereby rendering it easy for others to capture. Many studies have been done since Wyner's ground breaking studies [20] on improving the effectiveness of encrypted communication utilising secure physical layer methods as beam forming optimised performance [21, 22], collaborative relaying [23, 24], synthetic blocking [25, 26], and disturbance under control [27-29].
When the network's user base is substantial, a standard NOMA system gives severe interference and a larger likelihood of outages [30, 31]. Butterfly optimisation technique with multi-objective sum rate used in the NOMA power distribution network attempts to maximize the network's overall sum rate while maintain fairness among users. It achieves this by allocating power to the users based on their channel quality and priority [32]. In interference nulling using IRS, an IRS is placed from the transmitter to the receiver to selectively reflect or refract the electromagnetic waves in a manner that minimises the interference at the receiver. This is achieved by using the IRS to create nulls in the radiation pattern of the interfering signals, which eliminate the receiver's interference [33]. One approach for developing interference immunity a method employs adaptive filters, which are digital filters that can adjust their coefficients in response to changing input signals. These filters can be utilised to calculate the interference signal and subtracting it from the signal received [34].
3. System Design
Fig. 1 shows a macro cell upload with a distance of R will be taken into consideration in this article, with a BS at the center and evenly distributed U users all through the macro cell’s coverage. As an appropriate user of the wireless channel, we study a MIMO system with flat fading, N t transmit and N r reception terminals. Additionally, a jammer delivers a deliberately noisy signal with the primary goal of decreasing the legitimate user's data rate. While an authorized user sends a signal, it is transmitted by,
P = Un + e + i (1)
Where the signal vector that was transmitted N t and the signal vector received N r are represented respectively by x and y. The matrix of channel gains is U, received interference is e, with entries that are independently shipped with zero-mean complex the unbiased random variables and that have identical dispersion, we presume that U is in a circle symmetric. With entries that are independently shipped with zero-mean complex the Gaussian random variables and that have identical dispersion, we presume that U is in a circle symmetric. Without affecting generality, the distinctions between the data points U and i are adjusted to one.
Each block's data transmission phase is preceded by a first training period. L p symbol periods and L d symbol periods are both used respectively, are the lengths of the phases of training and data collection. Via way of L p pilot symbols that the transmitter sends during the training phase, the receiver calculates U. P p and P d , respectively, for training and data transfer, determine the signal strength (per symbol). Moreover, jammers introduce phoney noise into frequencies signals in addition to the transmission from the authorized user. During the training and data phases, P p and P w , respectively, indicate the strength of the jamming signal.
U3
Base
Station
U1

U2

Fig.1. Transmissions over uplinks while under attack
We have created an N r and L p matrix by combining the symbol vectors that were received during training.
Zo = URo + eo + io
Where Ro is the pilot matrix, the noise and jamming matrix is eo and io respectively. The calculation approach known as linear minimum mean square error (LMMSE) estimator is
Ũ=T o [R+ o R o +(R s +1)I]-1R+ o
The orthogonal pilots are then used to provide the variance of each H component
σ2 = [1 + P p L p ]-1
h̃ N t (P w +1)
Pw+1
P w +1+ P p L p⧸ N z
The possible data rate, the maximum of which is governed by the permitted user's ergodic capacity, is the goal function of the previously described optimization problems. The total energy invested in the instruction period ∅ and γ accordingly.
∅P L (1-∅)P L
Pp = , Pd =
Lp Ld
The jammer we have, so
γP w L (1-γ)P w L
P wp = L p , P wd = L d
Despite the fact that the ergodic capacity's precise meaning is unknown, what follows is a frequently employed lower bound as below
C LB = L L d exp[log 2 ⁄I+ρ eff H o N H t o+ ]
Where Ho and H are statistically equivalent the percentage Ld⁄ explains the capacity loss caused by training overhead, the SNR reported by
(1-σ2h ̃ )P d PdPpLp⁄Nt
P w d+1+σ2h ̃ P d ρeff P w d+1[P w d+1+P d P p L p ⁄N t ]+P w d+1
The goal of the function employed to optimize training duration and energy allocation was this feasible rate for the lower bound of ergodic capacity.
4. Proposed Block Diagram
The suggested interference nulling algorithm's block diagram is depicted in fig. 2. The precoders and corresponding equalizers for each group of users in this portion are jointly created. Create an input binary data set first, with a single base station and four randomly selected users. To further reduce overall power consumption, an optimization problem is created. Another benefit is the conversion of the original optimization problem into a tractable one employing the precoding design.
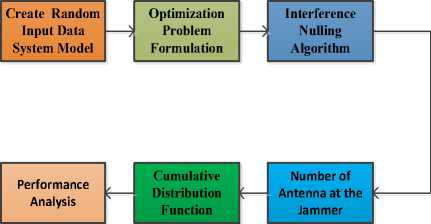
Fig.2. Proposed interference nulling algorithm
Module 1. Formulations for Optimization Issues
Ĉl = DlR(GkNk + ∑jk=j+1 G j N j + G j Z j + m), for 1 ≤ k ≤ K - 1 (9)
$ ^(G k N k + G j Z j +m) (10)
Where Gk is an equalizer for the group of individuals. The group of users' equalizer can be written as
Rk=(HkHHk+Lk)-1Hk , for 1≤k≤K(11)
With, Lk= Lk+1 + HkH+1Hk+1, for 1≤k≤ K-1(12)
Lk = NPj HjHHj + ρ2JNB
The matrix of covariance jammer frequencies detected at the BS should be identified, according to a precoding in accordance arrangement. These details are obtained by blind estimating the channel in the absence of a training sequence. The SINR in order to ith stream in the k th class uth users can also be written
SINR k,t,i =
[(H k,t D k,t t[i])H ](HkHH k +Q k )-1(H k,u D k,u t[i])2
(H k,t D k,t t[i])H(HkHH k +Q k )-1ω k,t,i (HkHH k +Q k )-1(H k,t D k,t t[i])
With, ω k,t,i =H k HH k + L k - H k,t V k,t [i](V k,t [i]H(H k,t H))
Substitute (15) in (14), we get
SJNR _ [(H k,t V k,t t[i])H](HHH k +Q k )-1(H k,t V k,t t[i])
k,u,i i-(H k,t V k,t t[i])H(H H H k +Q k )-1(H kt Vt[i])
This is one way to put the optimization problem into words:
min«=E^1Tr{V H Vw} (17)
D k,t
Z ‘ k, 1 log2(1 + SINR k,t,i ) > y^ t (18)
Where, у* is the required minimum rate for Kth group of Uth users.
Module 2. Interference Nulling Algorithm
Reduce the impact of the jammer and other groups' interference. The common form of the equivalent system matrix is designed as,
H k = Q K [-] k A k
Where, [-]k an unbroken matrix and the diagonal matrix. There is a chance to express the precoder of the Kth group's Uth user as
Dk,t = H-MH^t
Where, [-]fc.t = [[-]fc[S^^+i]],..., [[-]fc[^-1^]](21)
Ak,u = diflS{[Ak] Z^l1 lkJ + 1, Z^l1 lkJ + 1........[Ak] Z^l1 lkJ Z“-i lkJ(22)
The SINR can be written as, SINRk,u,f = [Ak,u]2(23)
The objective function i9 can be represented as
5 = Zk=1ZUk=1TrKu,nk,u,Ak,u} = Zk=1 Z^U Z^^u]2 [Ak,u]f,f(24)
n . = [-]HuQkH-SH-uQk[-]k,a(25)
min 5 = Zk=1 Zu=1 Zi=,1[Ak,u]2 [Ak,u]ff(26)
Dk,u
Zi>g2[1+[Ak,u]2] >«khu,Vk,u
[-]H[-]k = lZlk,uu=1(28)
Where the constraint on orthogonally in (28) ensures that provided in a unitary manner (19).
Algorithm 1. Interference Nulling Procedure.
For k=K:1
Construct the interference matrix and covariance analysis Qk and compute unbroken matrix [-]fc by the interference nulling algorithm for u= 1.Uk.
Determine {[л к , и ] ? } for u=1.,Uk , f=1.,sk , u . and find the diagonal matrices л к , и for u=1.,Uk.
Evaluate the interference matrices Dk , u find the equalizer Rk at the BS for u=1..., Uk.
End for.
5. Results and Discussions
This part presents the proposed scheme's overall power consumption. The obtained simulation results are compared with the SA-OMA and SA-NOMA, and table 1 shows the variables that are taken into account. The outlined approach highlights the between-group impediments and blocks through Q 1/ 2 each group's predetermined codes matrix is shown under (19). It's due to the SIC reception at the base station enables equally nearby and distant users to communicate over more time-frequency possibilities. The obtained results indicate several streams of data take in significantly less power over just one stream of data for every user. The reason for this is the fact that a MIMO network using multiplexing in space uses less power to transmit to achieve a comparable rate of transmission. The efficiency gain of the suggested NOMA system using several date streams is higher than that achieved using one time channel compared to the NOMA method.
Table 1. Variables considered for result
|
Sl No. |
Variables |
Values |
|
1. |
Noise Power |
-99 |
|
2. |
Path loss exponent |
3.5 |
|
3. |
Users per group, number |
6 |
|
4. |
Antenna count at the BS |
10 |
|
5. |
Various user groups |
03 |
|
6. |
The jammer's antenna count |
01 |
|
7. |
Antenna count at the user |
10 |
|
8. |
Users total group |
03 |
|
9. |
Signal to Noise Ratio |
10 |
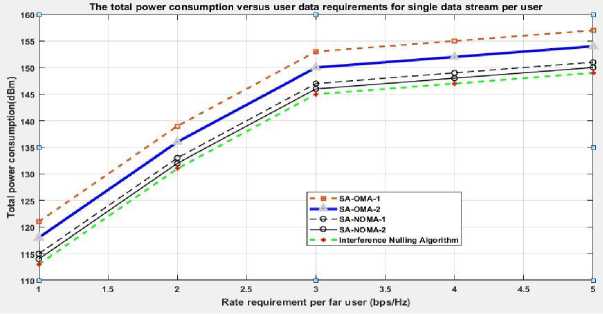
Fig.3. Power Consumption versus data rate per far user
-
5.1. Comparison with the Conventional Plans
-
5.2. Energy Consumption of Cumulative Distribution Function (CDF)
The OMA programmed users from both close and far are planned for equivalent as well as orthogonal spatial assets. It has been observed that the bare minimum standards for all schemes lead to an increase in power use. The necessary SINR should be enhanced as the per-user minimum rate rises, which calls for more power resources. It is observed in fig. 3 the proposed interference nulling algorithm takes less power in comparison to the SA-NOMA and conventional OMA schemes. The NOMA-1 and NOMA-2 take less power when compare to the OMA-1 and OMA-2. First, some useful signals may have spatial directions that are close to those of jamming interference during transmissions of interference nulling algorithms. After that, the amount of energy used will be raised to meet the SINR requirements. Fig. 4 for the proposed algorithms, the amount of energy used for the interference nulling algorithm is less than the other conventional techniques.
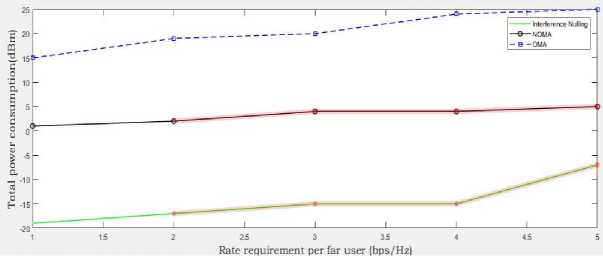
Fig.4. Total power consumption in comparison to one data packet
The CDF in Fig. 5 depicts the overall power utilisation for a single data stream per user. The power of transmission CDFs for the projected NOMA systems are constantly next in relation to the SA-NOMA CDFs on the left. Because the iterference nulling procedure is collaboratively created in the suggested ways, each user can acquire a sufficiently high channel gain.
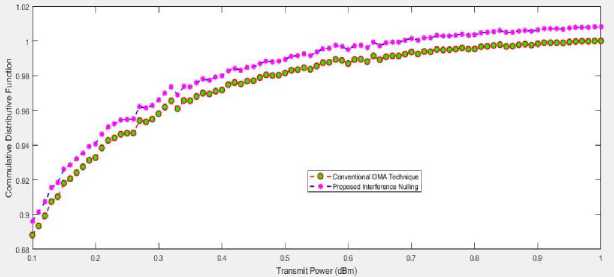
Fig.5. CDF for the total power consumption of only one stream of data
Fig. 6 depicts the CDF for total power use across multiple information streams for each end user. The suggested methods' CDFs for total transmit powers appear to converge faster to 1. It implies that the transmission capacity of the offered algorithms focuses on lower values. The SA-NOMA system approach is more official channel- thoughtful than the proposed NOMA system, as indicated by the fact that the transmission energy distribution for The SA-NOMA system is becoming more popular out across an extensive spectrum.
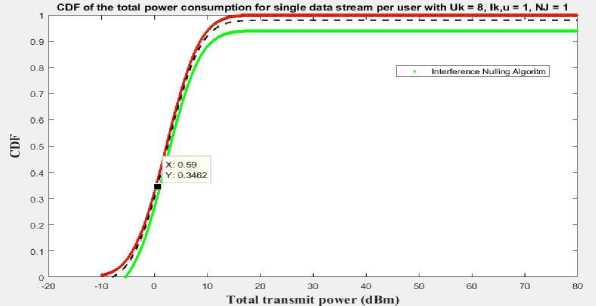
Fig.6. CDF for a multiple data stream's overall power consumption
5.3. User Count in the Cell Area
5.4. Number of Antenna at the Jammer
6. Comparison Assessment
Fig. 7 depicts the overall power utilisation for various user group sizes. It is demonstrated that as the number of user groups rises, the initial power usage reduces. Power usage remains steady after reaching a minimum level. It's because as the number of groups grows, so do the number of SIC operations. As a result, there will be less user interference.
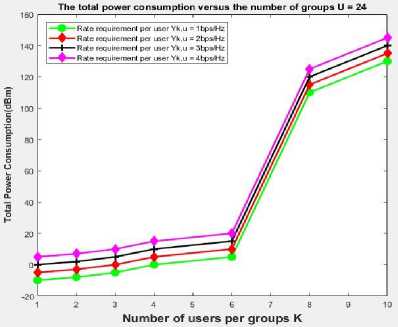
Fig.7. Number of users versus power consumption
Fig. 8 shows a graph of the jammer's overall power consumption for various antenna counts. With more antennas installed at the jammer to accommodate various transmit rate requirements, the power consumption is seen to be slightly reduced. It demonstrates the proposed NOMA method is resistant to a variety jamming transmitters. This is because the number of antennae on the jammer rises, as well as the number of spatial directions in which interference from the jammer occurs, but the power of the interference in each direction decreases.
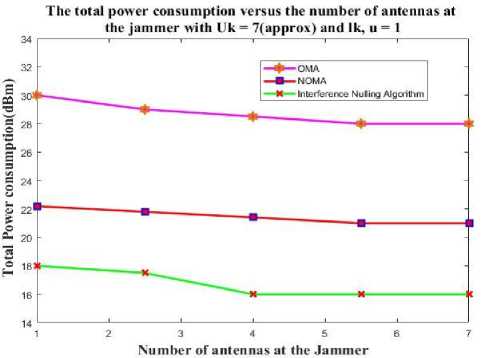
Fig.8. Total amount of power used by the jammer
In terms of the achievable data rate, this part examines and contrasts the interference nulling techniques. The current studies include SA-OMA1, SA-OMA2, SA-NOMA1, and SA-NOMA2 are employed to assess the effectiveness of the interference nulling technique. The performance contrast of the data rate that could be accomplished with the interfering nulling algorithm is shown in Table 2. When compared to other conventional procedures, the achievable data rate of interference nulling strategies for the user1 is 115 (dBm), which is less by -42.2%. Similarly, the obtained power level for user5 is also 145 (dBm), which is -7% decreases. The capabilities of the signal obtained are represented in table 3. The cumulative distribution function is simulated the transmit power is taken from -20 to 80 (dBm). For example, at power level 10 the obtained CDF value 0.87 which is less than the other conventional techniques. From this the transmission capabilities are taken at lower values. By using interference nulling techniques, it is approaching more to the value 1, thus it improves the NOMA spectral efficiency. The NOMA network is developing here with a number of users. Since superposition coding and SIC decoding are used in NOMA networks, user disturbance is kept to a minimum.
Table 2. Interference nulling techniques with a feasible data rate
|
Techniques |
Power Consumption (dBm) |
||||
|
User1 |
User2 |
User3 |
User4 |
User5 |
|
|
SA-OMA1 |
125 |
134 |
141 |
145 |
154 |
|
SA-OMA1 |
122 |
131 |
138 |
142 |
151 |
|
SA-NOMA1 |
199 |
128 |
135 |
139 |
148 |
|
SA-NOMA2 |
117 |
124 |
126 |
143 |
146 |
|
Interference Nulling Algorithm |
115 |
122 |
124 |
141 |
145 |
Table 3. Single data stream per user
|
Transmit Power (dBm) |
Interference Nulling Technique |
NOMA |
OMA |
|
-5 |
0.01 |
0.05 |
0.07 |
|
-3 |
0.08 |
0.12 |
0.13 |
|
-1 |
0.12 |
0.23 |
0.19 |
|
0 |
0.29 |
0.37 |
0.25 |
|
1 |
0.34 |
0.38 |
0.39 |
|
3 |
0.50 |
0.52 |
0.55 |
|
5 |
0.61 |
0.69 |
0.71 |
|
7 |
0.76 |
0.81 |
0.83 |
|
9 |
0.85 |
0.88 |
0.91 |
|
10 |
0.87 |
0.91 |
0.93 |
|
20 |
0.93 |
0.97 |
0.97 |
|
30 |
0.94 |
0.98 |
1 |
|
50 |
0.94 |
0.98 |
1 |
|
70 |
0.94 |
0.98 |
1 |
|
80 |
0.94 |
0.98 |
1 |
7. Conclusions and Future Works
MIMO-NOMA system for uplink, an anti-jamming predetermined codes design has been presented in this paper. With the help of group signal delays, a novel structure for multi-group NOMA signals has been introduced in the design that is suggested. Interference nulling algorithm has been created to address the issue of power minimization. The precoders and equalizers have been simultaneously improved to reduce the overall resource usage while still satisfying the minimal rate requirement of the clients by considering actual covariance information of jammer signals into consideration. According to the simulation results, suggested NOMA schemes outperform in terms of power use, both SA-NOMA and their OMA region, regardless of whether the jamming interference covariance matrix is perfect or sample. By the implementation of reduce the power consumption we can improve the NOMA system's spectrum efficiency. The performance analysis leads to the conclusion that the interference nulling technique outperforms other traditional procedures. The feasible data rate rises when the user's power usage falls by -42.2% at the user1. To ensure the reliability of NOMA, this is that we are going to examine the constantly changing decoded sequence SIC during our subsequent studies.
Acknowledgements
Thanks for allowing us access to the experiments and LAB Data sets, School of Electronics and Communication, REVA University, Bangalore.
Список литературы Anti-jamming and Power Minimization Interference Nulling in Uplink MIMO-NOMA Technique
- Scaglione, Anna, Georgios B. Giannakis, and Sergio Barbarossa. "Redundant filterbank precoders and equalizers. I. Unification and optimal designs." IEEE Transactions on Signal Processing 47.7 (1999): 1988-2006.
- Tong, Lang, and Qing Zhao. "Joint order detection and blind channel estimation by least squares smoothing." IEEE Transactions on Signal Processing 47.9 (1999): 2345-2355.
- Islam, SM Riazul, Nurilla Avazov, Octavia A. Dobre, and Kyung-Sup Kwak. "Power-domain non-orthogonal multiple access (NOMA) in 5G systems: Potentials and challenges." IEEE Communications Surveys & Tutorials 19, no. 2 (2016): 721-742.
- Shi, Zheng, Guanghua Yang, Yaru Fu, Hong Wang, and Shaodan Ma. "Performance analysis of MIMO-NOMA systems with randomly deployed users." In 2018 IEEE Global Communications Conference (GLOBECOM), pp. 1-7. IEEE, 2018.
- Chen, Shuang, Kewu Peng, and Huangping Jin. "A suboptimal scheme for uplink NOMA in 5G systems." 2015 International wireless communications and mobile computing conference (IWCMC). IEEE, 2015.
- Liu, Yuanwei, Zhijin Qin, Maged Elkashlan, Zhiguo Ding, Arumugam Nallanathan, and Lajos Hanzo. "Non-orthogonal multiple access for 5G and beyond." arXiv preprint arXiv:1808.00277 (2018).
- Zhang, Ying Jun Angela, and Anthony Man-Cho So. "Optimal spectrum sharing in MIMO cognitive radio networks via semidefinite programming." IEEE Journal on Selected Areas in Communications 29.2 (2011): 362-373.
- Ding, Zhiguo, Xianfu Lei, George K. Karagiannidis, Robert Schober, Jinhong Yuan, and Vijay K. Bhargava. "A survey on non-orthogonal multiple access for 5G networks: Research challenges and future trends." IEEE Journal on Selected Areas in Communications 35, no. 10 (2017): 2181-2195.
- Zeng, Ming, Animesh Yadav, Octavia A. Dobre, Georgios I. Tsiropoulos, and H. Vincent Poor. "Capacity comparison between MIMO-NOMA and MIMO-OMA with multiple users in a cluster." IEEE Journal on Selected Areas in Communications 35, no. 10 (2017): 2413-2424.
- Wang, Hong, Shu-Hung Leung, and Rongfang Song. "Precoding design for two-cell MIMO-NOMA uplink with CoMP reception." IEEE Communications Letters 22, no. 12 (2018): 2607-2610.
- Sadr, Sanam, Alagan Anpalagan, and Kaamran Raahemifar. "Radio resource allocation algorithms for the downlink of multiuser OFDM communication systems." IEEE communications surveys & tutorials 11, no. 3 (2009): 92-106.
- Zhao, Nan, Wei Wang, Jingjing Wang, Yunfei Chen, Yun Lin, Zhiguo Ding, and Norman C. Beaulieu. "Joint beamforming and jamming optimization for secure transmission in MISO-NOMA networks." IEEE Transactions on Communications 67, no. 3 (2018): 2294-2305.
- Chang, Zheng, Lei Lei, Huaqing Zhang, Tapani Ristaniemi, Symeon Chatzinotas, Björn Ottersten, and Zhu Han. "Energy-efficient and secure resource allocation for multiple-antenna NOMA with wireless power transfer." IEEE Transactions on Green Communications and Networking 2, no. 4 (2018): 1059-1071.
- Zhou, Xiangyun, Dusit Niyato, and Are Hjorungnes. "Optimizing training-based transmission against smart jamming." IEEE Transactions on Vehicular Technology 60, no. 6 (2011): 2644-2655.
- Zhao, Nan, F. Richard Yu, Ming Li, and Victor CM Leung. "Anti-eavesdropping schemes for interference alignment (IA)-based wireless networks." IEEE Transactions on Wireless Communications 15, no. 8 (2016): 5719-5732.
- Xiao, Liang, Yanda Li, Canhuang Dai, Huaiyu Dai, and H. Vincent Poor. "Reinforcement learning-based NOMA power allocation in the presence of smart jamming." IEEE Transactions on Vehicular Technology 67, no. 4 (2017): 3377-3389.
- Alavi, Faezeh, Kanapathippillai Cumanan, Zhiguo Ding, and Alister G. Burr. "Beamforming techniques for nonorthogonal multiple access in 5G cellular networks." IEEE Transactions on Vehicular Technology 67, no. 10 (2018): 9474-9487.
- Ding, Zhiguo, Robert Schober, and H. Vincent Poor. "A general MIMO framework for NOMA downlink and uplink transmission based on signal alignment." IEEE Transactions on Wireless Communications 15, no. 6 (2016): 4438-4454.
- Wang, Hong, Rongbin Zhang, Rongfang Song, and Shu-Hung Leung. "A novel power minimization precoding scheme for MIMO-NOMA uplink systems." IEEE Communications Letters 22, no. 5 (2018): 1106-1109.
- Wyner, Aaron D. "The wire‐tap channel." Bell system technical journal 54, no. 8 (1975): 1355-1387.
- Lv, Tiejun, Hui Gao, Ruohan Cao, and Jian Zhou. "Co-ordinated secure beamforming in $ K $-user interference channel with multiple eavesdroppers." IEEE Wireless Communications Letters 5, no. 2 (2016): 212-215.
- Cao, Yang, Nan Zhao, F. Richard Yu, Minglu Jin, Yunfei Chen, Jie Tang, and Victor CM Leung. "Optimization or alignment: Secure primary transmission assisted by secondary networks." IEEE Journal on Selected Areas in Communications 36, no. 4 (2018): 905-917.
- Fan, Lisheng, Rui Zhao, Feng-Kui Gong, Nan Yang, and George K. Karagiannidis. "Secure multiple amplify-and-forward relaying over correlated fading channels." IEEE Transactions on Communications 65, no. 7 (2017): 2811-2820.
- Fan, Lisheng, Xianfu Lei, Nan Yang, Trung Q. Duong, and George K. Karagiannidis. "Secrecy cooperative networks with outdated relay selection over correlated fading channels." IEEE Transactions on Vehicular Technology 66, no. 8 (2017): 7599-7603.
- Zhu, Fengchao, Feifei Gao, Minli Yao, and Hongxing Zou. "Joint information-and jamming-beamforming for physical layer security with full duplex base station." IEEE Transactions on Signal Processing 62, no. 24 (2014): 6391-6401.
- Zhao, Nan, Yang Cao, F. Richard Yu, Yunfei Chen, Minglu Jin, and Victor CM Leung. "Artificial noise assisted secure interference networks with wireless power transfer." IEEE Transactions on Vehicular Technology 67, no. 2 (2017): 1087-1098.
- Zhao, Nan, F. Richard Yu, Ming Li, and Victor CM Leung. "Anti-eavesdropping schemes for interference alignment (IA)-based wireless networks." IEEE Transactions on Wireless Communications 15, no. 8 (2016): 5719-5732.
- Zhao, Nan, Fen Cheng, F. Richard Yu, Jie Tang, Yunfei Chen, Guan Gui, and Hikmet Sari. "Caching UAV assisted secure transmission in hyper-dense networks based on interference alignment." IEEE Transactions on Communications 66, no. 5 (2018): 2281-2294.
- Zhao, Nan, F. Richard Yu, Ming Li, Qiao Yan, and Victor CM Leung. "Physical layer security issues in interference-alignment-based wireless networks." IEEE Communications Magazine 54, no. 8 (2016): 162-168.
- Higuchi, Kenichi, and Yoshihisa Kishiyama. "Non-orthogonal access with random beamforming and intra-beam SIC for cellular MIMO downlink." In 2013 IEEE 78th Vehicular Technology Conference (VTC Fall), pp. 1-5. IEEE, 2013.
- Qureshi, Soma, and Syed Ali Hassan. "MIMO uplink NOMA with successive bandwidth division." In 2016 IEEE Wireless Communications and Networking Conference, pp. 1-6. IEEE, 2016.
- Gangadharappa, Suprith Pamarahalli, and Mohammed Riyaz Ahmed. "Power Allocation Using Multi-Objective Sum Rate Based Butterfly Optimization Algorithm for NOMA Network." International Journal of Intelligent Engineering & Systems 15, no. 4 (2022).
- Jiang, Tao, and Wei Yu. "Interference nulling using reconfigurable intelligent surface." IEEE Journal on Selected Areas in Communications 40, no. 5 (2022): 1392-1406.
- Kartsan, I. N., V. N. Tyapkin, D. D. Dmitriev, A. E. Goncharov, P. V. Zelenkov, and I. V. Kovalev. "Synthesis of an algorithm for interference immunity." In IOP Conference Series: Materials Science and Engineering, vol. 155, no. 1, p. 012019. IOP Publishing, 2016.


