Application of CL multi-wavelet transform and DCT in Information Hiding Algorithm
Автор: Tao ZHANG, Shuai REN
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 1 vol.3, 2011 года.
Бесплатный доступ
Taking advantage of a feature that allows theenergy of an image would gather and spread on four components (LL2, LH2, HL2 and HH2) in the sub image after first-order CL multi-wavelet transform, and Using the advantage of Discrete Cosine Transform in application of information hiding, propose an Information Hiding scheme based on CL multi-wavelet transform and Discrete Cosine Transform (abbreviated as CL-DCT). LL2 is embedded module of robust parameters (optimized code of Chebyshev scrambling and Hash value of embedding information). Embed hiding Information in LH2 and HL2 with RAID1 and fragile sign in HH2. Select a different range of DCT coefficients in LH2, HL2 and HH2. The embedding sequence of each bit plane is traversal according to Knight-tour rout. Experimental results indicate that the proposed scheme can increase invisibility and robustness separately by 5.24% and 28.33% averagely. In particular, the scheme has better ability against cutting attacks. The scheme has certain ability against steganalysis such as Higher Order Statistics based on wavelet coefficients. Moreover, the scheme has excellent sensitivity of image processing.
Algorithms, wavelet transforms, information hiding, CL multi-wavelet transform, Discrete Cosine Transform, Chebyshev scrambling, genetic algorithm, Knight-tour rout
Короткий адрес: https://sciup.org/15010999
IDR: 15010999
Текст научной статьи Application of CL multi-wavelet transform and DCT in Information Hiding Algorithm
Published Online February 2011 in MECS
How to make the Information Hiding scheme have a better performance in terms of invisibility, robustness, sensitivity and anti-steganalysis becomes a research hotspot. Currently, the algorithm has not achieved four performances at the same time. The scheme based on space domain are good at invisibility, but can not meet the requirements of robustness and anti-steganalysis at the same time [1][2]. The scheme based on transform domain are good at robustness. Zhang et al [3] and Zhu et al [4] proposed Information Hiding scheme and digital watermarking scheme respectively based on discrete cosine transform (DCT) and discrete wavelet transform (DWT). They are robust enough against compression, but they are costly and low robust against cutting. and However, most algorithm are not strong in anti-steganalysis, and does not increase significantly [5][6].
Combination of different technologies can bring new ideas into Information Hiding. Taking advantage of the
CL multi-wavelet transforms and Discrete Cosine Transform in application of information processing, propose an Information Hiding scheme based on CL multi-wavelet transform and Discrete Cosine Transform. In particular, CL multi-wavelet transform can process multi-transformation at the same time, and satisfy compact sup-port and symmetry of the image processing. This new scheme is named as CL-DCT. Experiment results illustrate that CL-DCT is better than traditional algorithms as DWT-DCT and DCT-LSB in invisibility and robustness against image attacks such as JPEG2000, cutting, filtering and noise. Has certain ability against steganalysis such as Higher Order Statistics based on wavelet coefficients. Moreover, the CL-DCT has excellent sensitivity and against cutting to image attacks.
-
II. Information Hiding Algorithm design
A. Embedding region
In digital image processing based on the multi-wavelet transform, the energy distribution due to the order of decomposition and the direction of components. The energy distribution of CL multi-wavelet transform [7] provides a flexible information hiding strategy. Fig. 1 shows CL multi-wavelet first-order transformation to Lena image.

(a) Lena Normal
Figure 1. First-order CL multi-wavelet transform

(b) Lena CL first-order
Energy ratio of four First-order CL Multi-wavelet Transform sub-images is approximately as TABAL I [8].
TABLE I.
E nergy distribution of first - order CL multi - wavelet
|
CL transform LL 1 sub-image energy percentage of total image energy |
Each component energy distribution of LL 1 sub-image (%) |
|||
|
LL 2 |
LH 2 |
HL 2 |
HH 2 |
|
|
97.36 |
96.53 |
2.51 |
0.62 |
0.34 |
After CL multi-wavelet transform, the most energy not only concentrated in the first-order sub-image ( LL 1 ), but also concentrated in the first component of first-order sub-image ( LL 2 ).Based on the energy distribution of CL, Generating CL-DCT embedding region have four steps:
Step1. Transform the cover image with first-order CL multi-wavelet to obtain four sub-images. Embed robust parameters in LL 2 . Embed hiding Information in LH 2 and HL 2 . Embed fragile sign in HH 2 . See Fig. 2;
Figure 3. Bit Plane decomposition of 256 gray-scale Image
Step4. Decomposed HH 2 into lαβ color component and transform the β component into gray image [9]. Bit plane decompose to the gray image. The Bit Plane 2 is the embedding region in HH 2 . Fig. 3 shows a bit plane decomposition of normal Lena as a 256 gray-scale image.
B. Embedding rules
The embedded rules of CL-DCT are as follows:
Rule1. Odd and Even of DCT coefficient separately stand for 0 and 1;
Rule2. Embed information into LH 2 and HL 2 with RAID1, as shown in Fig. 4;
|
Robust Information LL 2 |
Embed Information LH 2 |
|
Embed Information HL 2 |
Fragile Sign HH 2 |
Figure 2. Embedded region strategy
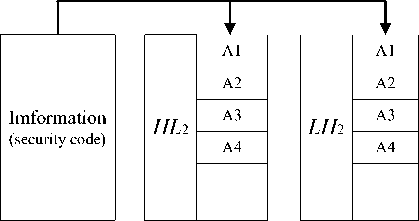
Figure 4. Knight-tour route
Step2. Transform LL 2 component ( N × N ) with DCT. Choose the interval distribution [( N 2 /4) - 1, N 2 - 1] of DCT coefficient as embedding region in LL 2 ;
Step3. Transform LH 2 and HL 2 ( N × N ) with DCT. Choose the interval distribution [( N 2/ 4) - 1,( N 2/ 2) - 1] of DCT coefficient as embedding region in LH 2 and HL 2;
Rule3. Order by [( N 2/4) - 1, N 2 - 1] to embed information into LL 2, and order by [( N 2 /4) - 1, ( N 2 /2) - 1] in LH 2 and HL 2;
Rule4. Order by Knight-tour route traversal to embed information into HH 2 . The Matrix of 9×9 Knight-tour is T . In the matrix T , “1” stands for the initial point of Knighttour rout [10].
1 34 3 16
4 173243
33 2 3564
18 5 6873

(a) Lena Normal

(b) Bit Plane 7

(c) Bit Plane 6
T = 81 74 63 70
6 198075
79 76 61 22
20 7 78 59
77 60 21 8
31 42 37 14 29 3615304138 6954392813 4465465340
67 72 55 1227
71 56 51 2611
50 9 24 5748
23 58 49 1025

(d) Bit Plane 5

(e) Bit Plane 4

(f) Bit Plane 3
According to the matrix tour route of 9×9 image.
T , Fig. 5 shows the Knight-

(g) Bit Plane 2

(h) Bit Plane 1

(i) Bit Plane 0
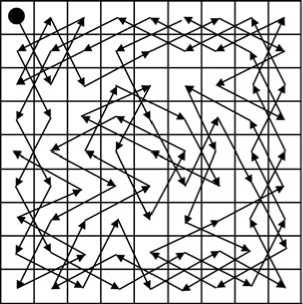
Figure 5. Knight-tour route
-
C. Embedding process
Information hiding scheme based on CL Multi-wavelet and CL-DCT divided into seven steps. Fig. 6 shows general process:
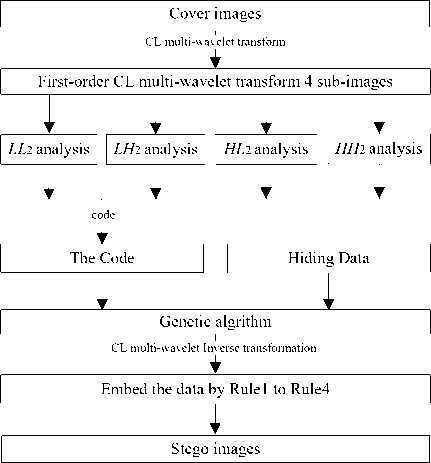
Figure 6. Embedding process for CL-DCT
Step1. Transform the cover image with first-order CL multi-wavelet to obtain four LL 1 sub-images;
Step2. Transform the LH 2 and HL 2 component ( N × N ) with DCT. Draw the data from DCT coefficient of LH 2 and HL 2 order by [0,( N 2/2) - 1] according to Rule2. The data separately denoted as CLL 1(2) and CLL 1(3) . CLL ^ = x^,x 2 2), l , x<2) and 0 < m < N2/2 .
CLL ( 3) = x (3) , x (3) , l , x ( 3) and 0 < n < N 2/2 . The final 11 , 2 ,, n .
analysis result denoted as C ;
C = ( x , , x 2 , l , x ) = ( x (2), x 22), l , x^,x <3) , x 23), l , x n , 3) ) (1)
Step3. Use Chebyshev mapping [11] of chaotic map algorithm to optimize information, as defined in (2) and (3). Suppose the parameter is μ, η and xk . The chaotic sequence after the Chebyshev mapping is Ch. The Pre- hiding bit series is Cpre. Scrambling formula is defined in (4), CIN =(b1,b2,l,b,) = (bx,bx,Kbm+„_pbm+„);
-1 < xk + i < П П < xk + i < 1
xk + 1 = cos ( ^ arccos( xk ) ) (3)
x
INpreh
Step4. In order to optimize the sequence of embedded bits with genetics algorithm [12], suppose F as the amount of the same bit value in matched positions between CIxN and C . The optimization model based on
CL-DCT is (5). Get the optimal solution xn' > П and ц' by genetic algorithms optimization;
F ( x„ , П , Ц ) = Max ^ ( x ® bi) (5)
Step5. Bring x n' > П and Ц into (2) (3) and (4) to get optimization embedded bits CIyN , CIN = by , by , K bn - 1 , bn . Embed CIN into DCT coefficients of LH 2 and HL 2 between ( N 2/4) - 1 and ( n 2/2) - 1;
Step6. Transform the LL 2 component ( N × N ) with DCT. LL 2 is the most robust region in four LL 1 sub-images. In order to judge and recover the imperfect information, The CL-DCT embed the check code of RAID1, optimized code of Chebyshev scrambling ( xn' > П and Ц ) and Hash value of embedding information (recorded as RL ) into DCT coefficient between ( N 2 /4) - 1 and N 2 -1;
Step7. HH 2 is the most vulnerable region in four subimages. Embed the Hash of embedding information (recorded as RH ). Receiver can judge whether the stego image is attacked by comparing RH and RL .
-
D. Extracting information
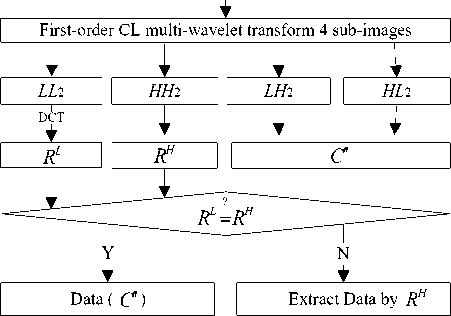
Extracting information is divided into five steps. Fig. 7 shows general process:
Stego images
CL multi-wavelet transform
-
Figure 7. Process for Extracting Information
Step1. Transform the cover image with first-order CL multi-wavelet and get four LL 1 sub-images;
Step2. Transform LL 2 , LH 2 and HL 2 component with DCT. Draw the RL from LL 2 component. Draw the data from LH 2 and HL 2 component with the order in the Knight-tour route, and denoted as C ′′ . Draw the RH from HH 2 ;
Step3. if RL = RH .The C ′′ is the secret information. if RL ≠ RH .The process continues;
Step4. if RL = RH .The C ′′ is the secret information. if RL ≠ RH .The process continues;
Step5. Draw the check code of RAID1 from LL 2 component and use them to process C ′′ and get final secret information.
-
III. Information Hiding Algorithm design
-
A. Invisibility and Robustness Analysis
Use high energy component LL 1 as information hidden area, the energy percentage of which is about 97.36% in the total image energy. This feature satisfies robust basic requirement of hiding area.
Main hidden area of information are LH 2 and HL 2 components, the energy of which is much lower than the energy of LL 2 (energy distributions of LL 1 are 2.51% and 0.62%, energy percentages of the total energy are 2.51% and 0.60%).
This characteristic meets the invisible basic condition of hiding area. Choose high frequency of DCT coefficients in high energy component LL 2 , meeting invisible hiding area rule of DCT. Choose low frequency of DCT coefficients in medium energy components LH 2 and HL 2, which qualifies robust hiding area rule of DCT. The general design idea of information hiding algorithm based on CL multi-wavelet and DCT is hiding information in low energy area of high energy component. This design can satisfy robustness and invisibility and solve the opposition between them well.
-
B. Anti-Steganalysis Analysis
The information hiding analysts generally use “all black” characteristic of LH 2 and HL 2 in CL component to analyze hidden information. Without obvious texture and pattern feature, information hidden in LH 2 and HL 2 is easily to expose.
Considering about the above, choose high frequency coefficient interval of DCT as hiding area to avoid information hiding analysis effectively. With consistent statistical properties of Chebyshev traversal and Knighttour route, zero mean white noise [13, 14], hidden information is of good distribution and hidden characteristics, thus improve the anti-steganalysis of algorithm. β components of HH 2 in lαβ color space are grayed to satisfy sensitive perceptivity and anti-steganalysis based on general LSB analysis.
C. Sensitivity Analysis
Hide Hash value in LL 2 robust unit with highest energy and LL 2 fragile sign unit with lowest energy. By contrast judgment on Hash value, the system can have sensitive perception against distortion.
IV. Simulation Experiment
Simulation environment of the algorithm is Matlab7.0.0.19920. Cover image is Lena (256×256) as shown in Fig. 8(a). Stego image is binary image Baboon (64×64) as shown in Fig. 8(b).
A. Invisibility Experiment
Fig. 8(c) shows stego image based on CL-DCT. PSNR
value equals 41.3295. It shows that this method is of
better invisibility.

(a) Cover image
(b) Hiding information

(c) Stego image
Figure 8. Hiding and result of CL-DCT
Invisibility is determined by Information content. Embed information in 200 images randomly. 2 k is used to denote bit quantity (0 ≤ 2 k ≤ 4096). Fig. 9 shows the PSNR of different embedding quantity. The experimental results indicated that when k ≤ 12, it is of better
invisibility (PSNR ≥ 41.3295).
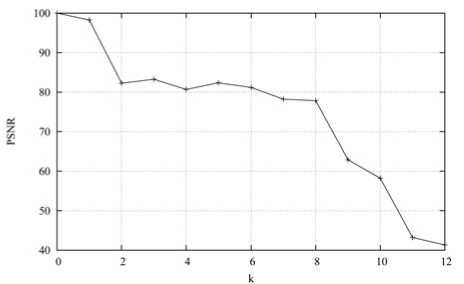
Figure 9. Experiment of embedding dense and corresponding Invisibility
B. Robustness Experiment
Define texture evaluation and modification rate of binary image ( n × n pixels) separately in (6) and (7).
n -1 n -1
∑∑ f ( i , j ) ⊕ f ( i + µ , j ± η )
w =
i =0 j =0
2 n 2
p =
∑∑ f ( i , j ) ⊕ f ′( i , j )
n 2
Where n = N /2 d , d e {1,2, L ,log2( N - 1)} . f ( i , j ) and f '( i , j ) are separately for the pixel at ( i , j ) of normal and extraction image with n × n pixels.
Robustness test algorithm is defined in (8). Q is robustness test value and Q e [0,1] . In the following experiments, μ = η =1. Expand Q 100 times to accommodate judgment habit.
Q = w ( 1 - p ) (8)
Fig. 10 shows the result of different attacks such as JPEG2000 compression, cutting, filtering and noise.
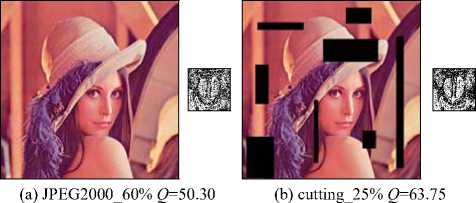

(c) mean filter_[3,3] Q =73.01
(d) wiener2 filter_[3,3] Q =61.36

(e) Gaussi _ μ =0, σ 2=0.003 Q =75.79
(f)' salt & pepper '_ d =0.15 Q =45.30
Figure 10. Results of robustness experiment
Images are vulnerable to compression and cutting attacks, Fig. 11 shows the Q ’s value corresponding to ratio of these attacks.
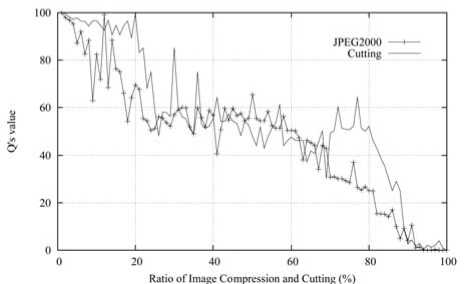
Figure 11. JPEG2000 and cutting experiment compression below 75%, cutting below 83%, common filtering and adding noise.
-
C. Experiment of ability against steganalysis
Higher order statistics detection algorithm based on wavelet coefficients (HOSWC) is a general detection algorithm [15]. Use the algorithms above-mentioned to analyze the performance of CB2-CFS. Experiment results are shown in Fig. 12 and Fig. 13.
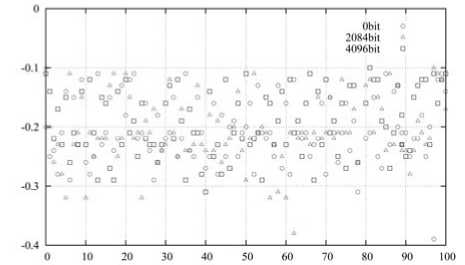
Objective Images (ps)
Figure 12. Steganalysis experiment result of HOSWC to CL-DCT
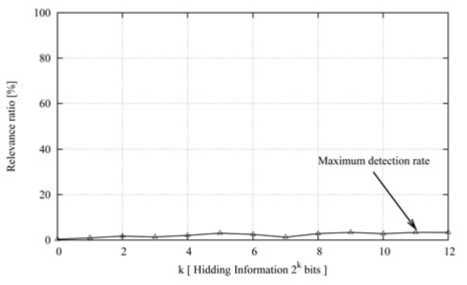
Figure 13. Steganalysis detection rate of HOSWC to CL-DCT
Fig. 12 shows there is no one or more threshold value found to recognize which pictures embedded information in 100 images. Use 1000 images to test, as shown in Fig. 13, largest detection rate below 3.3%. Experiments show that CL-DCT is of better anti-steganalysis.
-
D. Experiment of sensitivity to image attacks
Sensitivity to image attacks is the peculiar characteristic in CL-DCT. Comparing RL with RH indicates the algorithm has excellent sensitivity of image processing. TABLE II lists the detectable rate when JPEG2000 compression ratio is 5%, random cutting ratio is 5%, [3, 3] median filter, Gaussian ( μ =0, σ 2=0.003) and ' salt & pepper '( d =0.15). The average of detectable rate is 99.72%.
According to experiment, embedded information can be identified when Q reach about 30. Fig. 10 and Fig. 11 show that CL-DCT is robust against JPEG2000
TABLE II.
D etectable rate of attacks
|
ATTACKS |
JPEG2000 |
Cutting |
Filtering |
Gaussian |
' salt pepper ' |
|
Detectable rate |
99.98% |
99.94% |
99.98% |
98.79% |
99.92% |
-
E. Experiments of invisibility comparison
According to PSNR, CL-DCT has advantages in invisibility compared with DWT-DCT and DCT-LSB. TABLE III shows that invisibility increases by 6.00% averagely when embedding rate is 25%.
TABLE III.
I nvisibility comparison based on PSNR
|
Algorithm |
CL-DCT |
DWT-DCT |
DWT-LSB |
|
PSNR |
41.3295 |
38.3270 |
39.9501 |
-
F. Experiments of robustness comparison
Fig. 14, Fig. 15 and TABLE IV show robustness comparison results when embedding rate is 25% based on the Q ’s value.
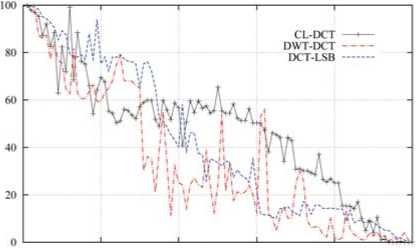
О 20 40 60 80 IOO
Ratio of Image JPEG2000 Compression (%)
Figure 14. Compression comparison
The Q ’s value of CL-DCT in JPEG2000 compression is 44.7315. DWT-DCT is 32.9980, and DCT-LSB is 42.6989. Indicate CL-DCT is better robustness at JPEG2000.
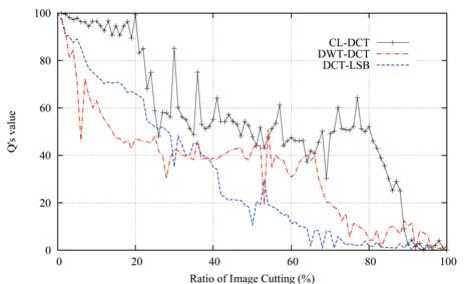
Figure 15. Cutting comparison
The Q ’s value of CL-DCT in cutting is 50.4678. DWT-DCT is 33.7810, and DCT-LSB is 31.0311. Indicate CL-DCT is better robustness at cutting.
TABLE IV.
RTV comparison of filtering and noise
|
Attacks |
Information Hiding Algorithm |
||
|
CL-DCT |
DWT-DCT |
DCT-LSB |
|
|
[3,3] median filter |
72.11 |
45.33 |
60.11 |
|
[3,3] wiener2 filter |
60.54 |
58.74 |
49.60 |
|
Gaussi ( μ =0, σ 2=0.003) |
72.17 |
46.90 |
60.14 |
|
' saltpepper '( d =0.15) |
43.54 |
53.48 |
42.15 |
TABLE IV show that CL-DCT have better performance in robustness under filter and noise except compared with ' salt & pepper ' noise of DWT-DCT.
-
V. Conclusions
Propose an Information hiding scheme based on CL and DCT. Take advantage of the energy distribution ratios in the four sub-images after first-order CL multiwavelet transformation, and use DCT to generate the DCT coefficients. Change the DCT coefficient to achieve information hiding. Chose LL 1 , the energy of which accounts for 97.36% of the total image energy, as the algorithm hiding area. The feature of LL 1 can meet the basic requirement of robustness hiding area. The main information hiding areas are LH 2 and HL 2 , the energy of which is much lower than the energy of LL 2. The energy of LH 2 and HL 2 separately account for 2.51% and 0.62% of LL 1 , and approximately account for 2.44% and 0.60% of the image total energy. The energy feature of LH 2 and HL 2 can meet the basic requirement of invisibility hiding are. Choose high frequency DCT coefficients of LL 2 component according to invisibility rule of DCT hiding area. Choose low frequency DCT coefficients of LH 2 and HL 2 according to robustness rule of DCT hiding are. The statistical properties of Chebyshev traverse and zero mean white noise are consistent [16], which is of good distribution and hiding characteristics to improve anti-steganalysis. Decompose HH 2 according to lαβ color space. Hide information with LSB method in β components after gray-scaling which can meet the requirement of sensitivity and anti-steganalysis against common analysis based on LSB.
The future work is focus on alternating selection of bit plane, choosing embedded module and robustness parameters in LL 2 in order to improve invisibility, robustness and tampering perception. Especially research on applications in information hiding based on the theory of Image Multiscale Geometric Analysis [17].
Acknowledgment
This work was supported by The Graduate Starting Seed Fund of Northwestern Polytechnical University (NPUZ2010). This work also has been supported by the National Defense Fund of China (C2720061361) and the
National Science and Technology Major Special Project (2008ZX03006)
The authors wish to thank all the reviewers for their valuable comments and suggestions that improved the quality of this paper.
Список литературы Application of CL multi-wavelet transform and DCT in Information Hiding Algorithm
- Chang Chin-Chen, Tseng Hsien-Wen. Data hiding in images by hybrid LSB substitution, Proceedings of the 3rd International Conference on Multimedia and Ubiquitous Engineering (MUE 2009), 2009:360-363.
- Li Xiao-long, Zeng Tie-yong, Yang Bin. Improvement of the embedding efficiency of LSB matching by sum and difference covering set, Proceedings of the 2008 IEEE International Conference on Multimedia and Expo (ICME 2008), 2008:209-212.
- Daqi Zhang, Shiru Qu, and Baosheng Kang, “A More Secure Information Images Using Hiding Technology for Digital DWT and DCT”, Journal of Northwestern Polytechnical University, Northwestern Polytechnical University Press, Xi’an, P.R.China, 2007, 25(3), pp. 378- 382.
- Gengming Zhu, Nong Sang, Desheg Xiang, Shaobo Zhang, “Watermark Algorithm Research and Simulation Based on Different Frequency Coefficients”, in Proceedings of International Conference on Advanced Computer Theory and Engineering (ICACTE 2008), Phuket, THAILAND, IEEE COMPUTER SOC, USA, 2008, pp. 271-275.
- Sun, X.. Robust adaptive image watermarking using visual models in DWT and DCT domain, Information Technology Journal, 2010, 9(3):460-466.
- Lu Wei, Sun Wei, Lu Hong-tao. Robust watermarking based on DWT and nonnegative matrix factorization, Computers and Electrical Engineering, 2009, 35(1):183-188.
- Chui C. K., Lian J. A. A Study of orthonormal multiwavelets, Applied Numerical Mathematics, 1996, 20(3): 273-298.
- HUANG Zhuo jun, MA Zheng-ming. Statistical Analysis of Multiwavelet Image Transform, Journal ofImage andGraphics, 2001.12, (6A):1198-1203.(in Chinese)
- TaiYu-wing, Jia jia-ya, Tang Chi-keung. Proceedings of the 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, (2005), 1:747.
- Paris, L., “Heuristic strategies for the knight tour problem”, in Proceedings of IC-AI 2004 & MLMTA 2004, CSREA PRESS, Athens, 2004, pp. 1121-1125.
- Boyd J. P.. Chebyshev and Fourier spectral methods. Canada: General Publishing Company, 2001.
- Goldberg, D.E., Genetic Algorithms in Search, Optimization, and Machine Learning, Addison Wesley Publishing Company, PISCATAWAY, USA, 2007, pp. 237-251.
- Prasadh K., Ramar K., Gnanajeyaraman, R. Public key cryptosystems based on chaotic-chebyshev polynomials, Proceedings of the 2009 International Conference on Intelligent Agent and Multi-Agent Systems (IAMA2009), 2009, Article number:5228035.
- SHI Jun. Chaotic and Its Performance Analysis Based on Chebyshev Mapping, Modern Electronics Technique, 2008, 31(23): 93-96. (in Chinese)
- Hany F., Siwei L. Higher-order Wavelet Statistics and their Application to Digital Forensics, IEEE Workshop on Statistical Analysis in Computer Vision, 2003, 8: 94.
- Prasadh K., Ramar K., Gnanajeyaraman, R. Public key cryptosystems based on chaotic-chebyshev polynomials, Proceedings of the 2009 International Conference on Intelligent Agent and Multi-Agent Systems (IAMA2009), 2009.
- Licheng Jiao, Biao Hou, Shuang Wang, and Fang Liu, Image Multiscale Geometric Analysis: Theory and Applications Beyond Wavelets, Xidian University Press, Xi’an, P.R.China, 2008.


