Application of Combinatory Mechanism on RTOS UFS ACM for Risk Optimization
Автор: Padma Lochan Pradhan
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 6 vol.8, 2016 года.
Бесплатный доступ
At this fastest growing of information age, there is a rapid change of business, resources and technology, mean while increasing the requirement of electronic commerce for the sophisticated societies in around the globe. During this process increasing the uncertainty, un order, un safe and un setup due to un authorize users, hackers is a great issue for down time of communication system. Our objective to determine and resolve these uncertainty problems to develop this proposed combinatory ACM to optimize the accessibilities of resources and maximize quality of services for all the time and every time to co-op with pervasive, ubiquitous & autonomy system. The relation, function, operation, maintaince and services are the vital role for all aspect of multiples societies, business and technologies in around the cloud. Meanwhile, it will be more accountable for performance, fault tolerance, throughput, benchmarking on any computational services for all the time. We have to make more simplification, unification and step by step normalization by applying permutation & combinations on UFS ACM mechanism on distributed object oriented system on multi-dimensional work culture. This access control mechanism is preventing, detecting, correcting, verification and validation of the UFS ACM in background process of RTOS.
Access Control Mechanism, Unix File System, Real Time Operating System, Prevent, detect & correct(PDC), Risk Assessment
Короткий адрес: https://sciup.org/15011538
IDR: 15011538
Текст научной статьи Application of Combinatory Mechanism on RTOS UFS ACM for Risk Optimization
Published Online June 2016 in MECS
-
II. Architecture of the Operating System
This access control mechanism is a prerequzise preventive control. The objectives of an access control system are often described in terms of protecting system resources against inappropriate or undesired user access. From a business perspective, this objective could just as well be described in terms of the optimal sharing of information. After all, the main objective of IT is to make information available to users and applications. A greater degree of sharing may get in the way of resource protection; in reality, a well-managed and effective access control system actually facilitates sharing. A sufficiently fine-grained access control mechanism can enable selective sharing of information where in its absence, sharing may be considered too risky altogether [7], [15], [18].
The access control mechanism is the process of mediating each and every request to system resources, application and data maintained by the real time operating system and determining whether the request should be created, approve, granted or denied as per top management policy. The AC mechanism, management and decision is enforced by implementing regulations established by a security policy [7], [15], [18].
The access control is concerned with determining the allowed activities of legitimate users, mediating every attempt by a user to access a resource in the system. The complex information technology (IT) infrastructure can implement access control systems in many places and at different levels. The real time operating systems use access control to protect files and directories. The database management systems (DBMS) apply access control to regulate access to tables and views. The most commercially available application systems implement access control, often independent of the operating systems programing and DBMSs on which they are installed [7], [15], [18].
The real time operating system access controls will usually relay on hardware features provided by the processor, memory, and kernel or by associated memory management hardware. These system controls which memory addresses a given process can access [7], [15], [18].
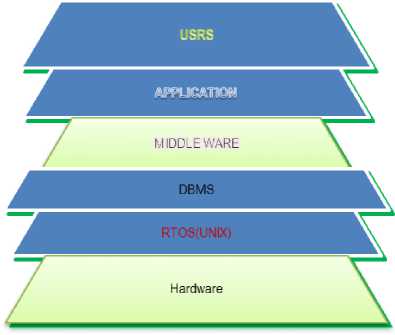
Fig.1. Multi-tire Architecture of Real time OS
-
III. Data Collection
Table 1. Sample of RTOS UFS data
|
SN |
Inode |
Subjects |
Link |
Owner |
Group |
Byte |
Date of File creation time stamp |
Objects( UFS ) |
Remarks |
RISK |
|
1 |
876345 |
drw-r--r-- |
1 |
e-com |
Usr |
1233 |
Jun 7 10:41 |
/etc/system |
Directory file |
High Risk |
|
2 |
123450 |
drwx------ |
2 |
e-com |
Usr |
1234 |
July 6 12.23 |
/etc/host |
Directory file |
High Risk |
|
3 |
098712 |
Dr-xr-xr-- |
1 |
sam |
Staff |
1024 |
Nov 2 00:10 |
/etc/ssh/sshd_con fig |
Directory file |
Low Risk |
|
4 |
908761 |
drwx-- |
1 |
sam |
SA |
1024 |
Dec 2 00.10 |
/etc/service |
Directory file |
High Risk |
|
5 |
012398 |
drwx-- |
1 |
USR |
GRP |
1024 |
July 6 12.23 |
/var/adm/messag e |
Directory file |
High Risk |
|
6 |
908123 |
- rwxrwxrw x |
3 |
e-com |
Staff |
Nov 2 00.10 |
Test.html |
Ordinary file |
High Risk |
|
|
7 |
786540 |
Dr-x------ |
6 |
e-com |
Usr |
512 |
May 3 12:31 |
Public |
Directory file |
High Risk |
|
8 |
765123 |
drwxr-xr--- |
1 |
sam |
Staff |
1024 |
Nov 2 00:10 |
Yourfile |
Directory file |
Medium Risk |
|
9 |
451230 |
crw------- |
1 |
root |
System |
0 |
Nov 2 00:10 |
/dev/rsd0a |
Character Spl File |
Medium Risk |
|
10 |
564321 |
brw-rw---- |
1 |
root |
System |
0 |
Nov 2 00:10 |
/dev/sd0a |
Block Spl File |
High Risk |
|
11 |
340999 |
lrwxrwxrw x |
1 |
ram |
Staff |
8 |
May 3 12:31 |
Zn.dat->gold.dat |
Link File |
High Risk |
-
IV. Problems Statement
-
V. Research Methodology
-
A. Define
|
Octal digital |
Binary representation |
Permission |
Role |
|
0 |
000 |
None/Blank (-) |
No body access (No Risk) |
|
1 |
001 |
execute only(x) |
Other-World (X) ( No Risk ) |
|
2 |
010 |
write only(w) |
Owner –USR(SU)(Risk) |
|
3 |
011 |
write and execute(wx) |
Owner –USR(Risk) |
|
4 |
100 |
read only( r ) |
Owner –USR(Top Mgmt)( Less Risk) |
|
5 |
101 |
read and execute ( r x) |
Owner –USR(Top Mgmt)( Less Risk) |
|
6 |
110 |
read and write (r w) |
Owner –USR(Developer) (Risk) |
|
7 |
111 |
read, write, and execute (r |
w x) Developer ( Business USR) (G)(Risk) |
Table 2(b). Interpreting Object Modes Pattern (Basic Architecture of Unix file system)
FIELD1
|
File Type |
Usr Access |
Group Access |
Other Access |
|||||||
|
Arttributes |
- |
r |
w |
x |
r |
- |
x |
r |
- |
x |
|
Position |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
|
Read Access |
• |
• |
• |
|||||||
|
Write Access |
• |
• |
• |
|||||||
|
Execute Access |
• |
• |
||||||||
|
Full Access |
d |
r |
• |
• |
||||||
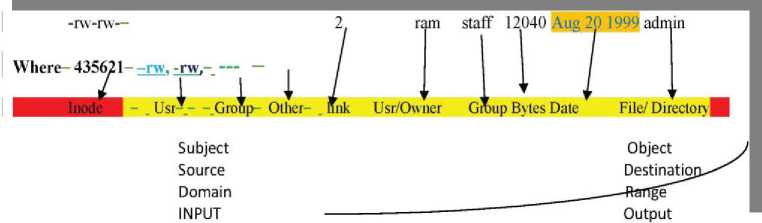
Fig.2. Internal UFS Structure
-
B. Design
We have to move forward to finding alternate solution and algorithm for Risk optimization based on combinatory theory. This scalable complex ACM definitely will be resolve our risk and security issue on complex real time system for multiple clients and location for all the times. We have to propose these eight objects is a set of elements as follows: {B, R, W, X, RW,
Table 3. Allocation of UFS Attributes on ACM as per required level of Mgmt.
|
Blank |
X |
W |
WX |
R |
RX |
RW |
RWX |
|
000 |
001 |
010 |
011 |
100 |
101 |
110 |
111 |
|
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
|
Nobody |
Any body |
Developer |
Developer |
Top Mgmt |
Top Mgmt |
Developer |
Developer |
Unordered (Uncertainty)
-
C. Development
Order (Certainty)
Table 4. Order Mechanism
|
br |
rb |
wb |
xb |
|
bw |
Rw |
wr |
xr |
|
bx |
Rx |
wx |
xw |
Note: this mechanism is more secure but not business oriented
An un order selections or arrangement of objects from a set of n objects is called a permutation (r-combination of n objects). It is denoted by C (n, r). If all the elements are distinct and non-repetition is not allowed, then by applying sum rule, it can be shown that:
C(n, r) = n (n-1) (n-2) ……. (n-r + 1) = n ! / r! (n-r) ! (un order-combination, Random )
We have to consider the set of eight objects {0, 1, 2, 3, 4, 5, 6, 7} = {0, X, W, WX, R, RX, RW, RWX)
Where n = 8, and r = 2, 3, 4, 5, 6, 7 and so on as shown in Tabular Form (Bernard, K. 2007).
Therefore we have to adjust our combination and permutations formula to optimize it by how many ways the objects (n=8) could be in order (because we are not interested in their order any more): nCr = , r!(n—г)!
where n>=1. Where n is the number of things to choose from, and we choose r of them (No repetition, un order, order may be does not matter) [3], [11].
—— era
C( 8,1) = 8 ! /1! (8-1)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/1!(7x6x5x4 x 3 x 2 x 1) = 8 ways possibilities of ACM
C( 8,2) = 8 ! /2! (8-2)! = 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/ 2! (6 x 5 x 4 x 3 x 2 x 1) = 28 ways possibilities of ACM
C( 8,3) = 8 ! /3! (8-3)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/3! ( 5 x 4 x 3 x 2 x 1) = 56 ways possibilities of ACM
C( 8,4) = 8 ! /4! (8-4)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/ 4!(4 x 3 x 2 x 1) = 70 ways possibilities of ACM
C( 8,5) = 8 ! / 5!(8-5)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/ 5! (3 x 2 x 1) = 56 ways possibilities of ACM
C( 8,6) = 8 ! / 6!(8-6)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/ 6!x2! = = 28 ways possibilities of ACM
C( 8,7) = 8 ! / 7!(8-7)!= 8 x 7 x 6 x 5 x 4 x 3 x 2 x 1/ 7!1 = = 8 ways possibilities of ACM
Note: We ha ve to make decision on better, faster and safer security and lower risk on distributed real time object oriented system.
P (4, 2) = 4!/ 2!(4-2)! = 6 ways/ possibilities
Table 6. High Risk
|
br |
rw |
wx |
|
bw |
rx |
bx |
Table 7. Medium Risk (Alpha Form)
|
brw |
brx |
bwx |
rxb |
rbx |
xwr |
|
rwx |
wxr |
xrw |
xrb |
rxw |
xwb |
|
wxb |
wrb |
wxr |
wbr |
rbw |
bwr |
|
rwb |
wrx |
xbr |
xbw |
wbx |
bxr |
Note: This mechanism is inefficient
Let us consider the set [b, r, w, x]. In how many ways (possibilities) can we select three of these letters (repetition is not allowed). P(4,3)= 4!/(4-3)!= 24
Table 8. Medium Risk (Octal Form)
NORMALIZED FORM FOR BUSINESS USR
Table 9. Medium Risk 1NF
|
SU |
G |
X |
G |
G |
SU |
|
SU |
SU |
SU |
G |
SU |
X |
|
X |
X |
SU |
X |
SU |
SU |
|
SU |
SU |
G |
SU |
X |
G |
Table 10. Medium Risk 2NF
|
SU |
X |
X |
B |
B |
SU |
|
SU |
SU |
SU |
B |
SU |
X |
|
X |
X |
SU |
X |
SU |
SU |
|
SU |
SU |
B |
SU |
X |
B |
(PAC) mechanism to optimize risk (Higher to Lower)
Action on ACM (Apply Preventive Control)
1NF: First Normal Form pl@pl-HP-15-Notebook- 1NF
PC:~/log$ chmod 701 menu*.* (ACTION )
pl@pl-HP-15-Notebook-PC:~/log$ ls –
SUBJECT OBJECT drwxr-xr-x 3 pl pl 4096 2014-11-11 12:26 kamal
Action on UFS ACM pl@pl-HP-15-Notebook-PC:~/log$ chmod 777 menu*.sh pl@pl-HP-15-Notebook-PC:~/log$ ls –l
NORMALIZED FORM FOR BUSINESS USR
-
D. Deployment of Combinatory UFS ACM
-
E. Experimental Test Mechanism on Real time UNIX Machine (Verificatio n)
We have to apply real time experiment on UFS ACM as follow
We can further apply the preventive access control
-
# chmod 777 menu*.sh
(ACTION) EVERY ONE R, W & X on U FS ACM #Ls -l(Review the Reaction) HIGH RISK
-
# chmod 666 menu*.sh
(ACTION) EVERY ONE R & W on UFS ACM
-
# Ls –l(Review the Reaction) HIGH RISK
-
- rw-rw-rw- 1 pl pl 727 2014-11-08 16:02 menu1.sh
-
- rw-rw-rw- 1 pl pl 461 2014-11-08 16:17 menu4.sh -rw-rw-rw- 1 pl pl 547 2014-11-08 16:37 menu5.sh
-
- rw-rw-rw- 1 pl pl 505 2014-11-09 16:52 menu.sh
-
# chmod 555 menu*.sh
-
#Ls -l(Review the Reaction) MIDDUEM RISK r-xr-xr-x 1 pl pl 727 2014-11-08 16:02 menu1.sh -r-xr-xr-x 1 pl pl 461 2014-11-08 16:17 menu4.sh -r-xr-xr-x 1 pl pl 547 2014-11-08 16:37 menu5.sh -r-xr-xr-x 1 pl pl 505 2014-11-09 16:52 menu.sh
2NF: 2nd Normal Form
#chmod 444 menu*.sh (ACTION)
#chmod 333 menu*.sh (ACTION)
#chmod 222 menu*.sh (ACTION)
ANY ONE WRITE THE UF S ACM- No S ecurity
#Ls -l(Review the Reaction)) HIGH RISK
-
- -w--w--w- 1 pl pl 461 2014-11-08 16:17 menu4.sh
-
- -w--w--w- 1 pl pl 547 2014-11-08 16:37 menu5.sh
-
- -w--w--w- 1 pl pl 505 2014-11-09 16:52 menu.sh
Now Proved the 3NF: 3rd Normal Form
#chmod 111 menu*.sh
(ACTION) EVERY ONE EXECUTE THE UFS ACM
-
# Ls -l(Review the Reaction) NO RISK & Secure
-
- --x--x--x 1 pl pl 727 2014-11-08 16:02 menu1.sh
-
- --x--x--x 1 pl pl 461 2014-11-08 16:17 menu4.sh
-
- --x--x--x 1 pl pl 547 2014-11-08 16:37 menu5.sh
-
- --x--x--x 1 pl pl 505 2014-11-09 16:52 menu.sh
#chmod 000 menu*.sh
(ACTION)NO ONE ACCESS THE UFS ACM- High Security
-
# Ls -l( Review the Reaction )
Remarks: No boby access on the Subject, That’s why blank ----------
-
VI. Out Comes on ACM Test
Graphical Representation:
If Preventive Control is more Risk is less [UFS ACM =k.1/R]. As per FUZZ’S LAW=> ACM= PC, PC=k. Cost: Where C is a Cost.
|
PC % |
RISK% |
CATEGORY( HML) |
Mgmt Action |
REMARKS |
|
20 |
80 |
High Risk |
Top Mgmt |
Low Cost |
|
40 |
60 |
High Risk |
Top Mgmt |
Low Cost |
|
60 |
40 |
Medium Risk |
Middle Mgmt |
Medium Cost ( Optimum Level ) |
|
80 |
20 |
Low Risk |
Operation & Services |
High Cost |
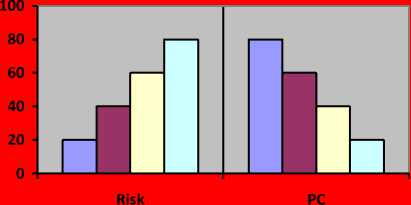
Graph 1. Risk Assessment Verses PC
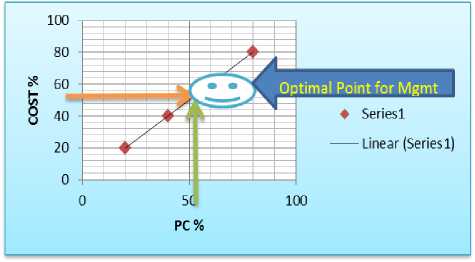
Graph 2. PC Verses Cost
Note: Preventive control is directly proportional to the cost
-
VII. Results
-
VIII. Conclusion
That’s why this security engineering is practically working as process of risk optimization and decision support system, when the sub system under uncertain, un ordered, and unsafe for all the time and every time.
Список литературы Application of Combinatory Mechanism on RTOS UFS ACM for Risk Optimization
- A.K. Gupta, Management Information System. New Delhi, India: S Chand Publishing, 2012.
- Adrian Waller, "Editorial: Special issue on Identity Protection and Management," Journal of information security and application, 19, 2014.
- Bernard Kolman, Discrete Mathematical Structures. New Delhi: Person Education India, 2007.
- Brendan Jennings and Rolf Stadler, "Resource Management in Clouds: Survey and Research Challenges, "Journal of Network System Management, Springer, Springer Science+Business Media, New York, February 2014.
- Diogo A. B. Fernandes, "Security issues in cloud environments: a survey, Intl. Journal of Info. Security, Springer. 13:113–170, 2014.
- Danny Bradbury, "Can Security and Privacy Co-exist?," Danny Bradbury Infosecurity. Volume 8, Issue 6, Pages 33–35, November–December 2011.
- Das Sumitabh, UNIX System V UNIX Concept & Application. Delhi, India: Tata McGraw Hill, 2009.
- Dario Forte, "Security audits in mixed environments," Network Security, Vol.3, No. 3, pp. 17-19, March 2009.
- Hwang Kai, Advance Computer Architecture. New Delhi, India: Tata McGraw Hill, 2008.
- John R Vacca, Computer and Information Security Handbook. Burlington, MA: Morgan Kaufmann, 2009.
- Joe. L Matt, Discrete Mathematics for Scientist and Mathematician. New Delhi: Person Education India, 2008.
- John B. Kramer, The CISA Prep Guide. New Delhi, India: Wiley Publishing Inc, 2003.
- Mathew Nicho Shafaq, "Identifying Vulnerabilities of Advanced Persistent Threats: An Organizational Perspective, "International Journal of Information Security and Privacy, 8(1), 1-18, January-March 2014.
- Nasir Abbas, Memory-Type Control Charts for Monitoring the Process Dispersion, Quality and Reliability Engineering International. Wiley, 30, 623–632, 2014.
- O' Reilly, Essential of System Administration. O' Reilly Media: USA, 1995.
- Shon Harrish, CISSP Exam Study Guide. New Delhi, India: Dreamtech, 2002.
- Shon Harrish, Security Management Practices. New Delhi, India: Wiley Publishing Inc, 2002.
- Sun-Microsystems, UNIX Sun Solaris System Administration. USA.
- Tong xin and Ban Xiaofang, "A Hierarchical Information System Risk Evaluation Method Based on Asset Dependence Chain," Intl. Jour. of Info & Network Security, 3, 3, 2014.
- Tanenbaum, Computer Network. New Delhi: Person Education India, 2009.
- Tim Thomas, "A Mandatory Access Control Mechanism for the Unix file system," Motorola Inc., Microcomputer Division, IEEE, 1988.
- Tanenbaum, Operating System Design and Implementation. New Delhi: Person Education India, 2010.
- William Stalling, Cryptography and Network Security. New Delhi: Person India, 2006.
- William Stalling, Operating System Internals & Design Principle. New Delhi, India: Person India, 2009.
- Weber Ron, Information System Control & Audit. New Delhi: Person Education India, 2002.


