CEAACK – A Reduced Acknowledgment for Better Data Transmission for MANETs
Автор: J.Sathiamoorthy, B.Ramakrishnan
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 2 vol.8, 2016 года.
Бесплатный доступ
fvA MANET is a set of mobile nodes which works in a dynamic changing network and it is capable of communicating with each other efficiently where all the nodes perform a dual role as that of a transmitter and a receiver. Hence MANETs do not use any centralized administration for communication due to this reason they are more vulnerable to attacks. So MANET uses special technique called EAACK, which uses special acknowledgment messages to avoid intruder communication. So due to this type of authentication, more acknowledgment messages are transferred in between two nodes, which increases delay in communication. Hence this drawback reduces system performance. In this paper we propose a new clustering technique in EAACK called CEAACK. Our proposed technique shows better performance when compare to the normal EAACK technique, which drastically reduces the number of acknowledgment packets during authentication process which achieves a good energy efficiency network and better data transmission. Further, this technique consumes low energy and in the process provides better efficiency in data transmission in MANETs.
Mobile Ad hoc NETwork (MANET), Enhanced Adaptive Acknowledgment (EAACK), Clustered Enhanced Adaptive Acknowledgment (CEAACK), Cluster, Base Station
Короткий адрес: https://sciup.org/15011502
IDR: 15011502
Текст научной статьи CEAACK – A Reduced Acknowledgment for Better Data Transmission for MANETs
A "Mobile Ad hoc Network" (MANET) is an autonomous system of mobile routers (and associated hosts) connected by wireless links. This union of routers and hosts forms an arbitrary graph. The routers can move randomly and has the capability to organize themselves arbitrarily. Due to this, changes in the network’s wireless topology may occur rapidly and are also unpredictable. MANETs can work in a standalone manner, or, if required, can be connected to a larger internet. The strength of the connection can change rapidly over time or even go out of the communication range. Nodes have the ability to connect, go out of range during the communication process. It is imperative that the nodes in the communication range must work throughout the period that data is being transmitted.
Mobile Ad hoc Network (MANET) consists of independent mobile nodes that can communicate with each other via radio waves. Mobile nodes in the same radio range can directly communicate, while those nodes that are not in the same radio range can communicate with the help of intermediate nodes. Due to their distributive nature these networks can work without the support of a proper infrastructure .This same feature also renders the network more vulnerable to attacks.
Each radio terminal is powered by an energy limited power source (such as rechargeable batteries).
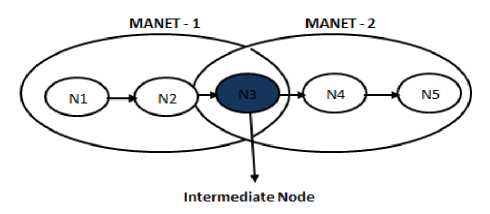
Fig.1. A MANET
The power consumption of each radio terminal could be divided into three parts, namely, power consumption for data processing inside the RT, power consumption to transmit its own information to the destination, and finally the power consumption when the RT is used as a router, i.e. forwarding the information to another RT in the network. Again, energy consumption is a critical issue in ad hoc networks.
The characteristics of these networks are:
-
• Communication without a wired network
-
• Nodes act as both hosts and routers
-
• No centralized administration or infrastructure
-
• Mutual trust between nodes
-
• Dynamic network topology
-
• Frequent routing updates
-
• Autonomous, no infrastructure needed
-
• Can be set up anywhere
-
• Energy constraints
-
• Limited security
-
-
• All sensor nodes use single-hop transmission or Multi-hop transmission to communicate with the Base Station
-
A. Layout of the Wireless Sensor Network
The wireless sensor network is group of sensor nodes, at the time of packet transmission all the nodes corporate each other and transmit the data packet to the user through gateway sensor node. The below figure shows structure of wireless sensor network.
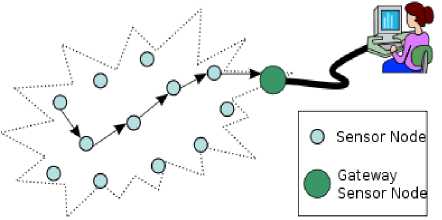
Fig.2. Wireless Sensor Networks
Assuming that a wireless sensor network consist of 4 nodes(SN01 to SN04) with one Cluster Head(CH).Within each cluster sensor nodes send data to the cluster head. The cluster head collects the data from each node. The cluster head compresses the data obtained from the member nodes and then transmits it to the base station or user.
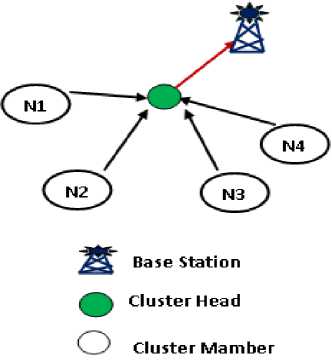
Fig.3. A Cluster in a MANET
Wireless sensor networks have the following characteristics (WSN):
It includes three kinds of nodes:
-
1. Sensor nodes have limited energy. They can sense their own residual energy and have the same architecture;
-
2. Cluster Head (CH) of each cluster directly communicates with the base station. It is like a mediator between the cluster member and the base station.
-
3. The Base Station (BS) has no energy restrictions and is far away from the area of the sensor nodes.
In single hop the cluster head of each group communicates directly with the base station. If the base station is far from cluster, the Cluster Head (CH) communicates with the Base Station (BS) via other CHs located near the BS, which is a multi-hop cluster model.
-
• Sensor nodes sense the environment at a fixed rate and always sends data to the BS
-
• Sensor nodes revise the transmission power of the wireless transmitter based on the distance
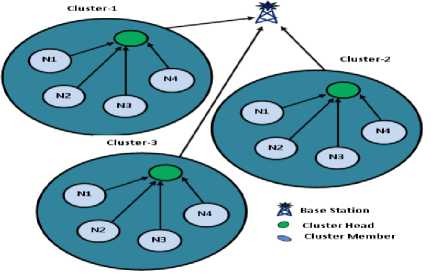
Fig.4. A CEAACK Cluster
-
II. Related Work
A communication protocol, LEACH (Low Energy Adaptive Cluster Head) algorithm is used .This protocol employs a hierarchical clustering approach which is done with the help of the information received from the BS. In order to conserve energy the BS keeps changing the cluster membership and the CH. The selection of the CH can be carried out with the help of the LEACH protocol.
The CH is responsible for the collection and aggregation of information from its sensors, which are then passed on to the BS. The purpose of changing the CH periodically is to conserve energy and to make sure the network setup does not get disconnected due to the CH’s failure. In other words the CHs are selected on a rotation basis so as to provide constant energy for data transmission. This rotation of CHs is distributed evenly so that no node is singled out and therefore loses its energy (battery power) completely.
While forming clusters the network follows two basic steps to select the CH and also to transfer the data from the cluster members to the CH. The first phase known as the Set-up phase is used to set up the clusters and also to schedule the cluster creation process. The second state, the Steady-State phase uses TDMA (Time Division Multiple Access) for data transmission.
-
III. Clustering
-
A. The CEAACK Cluster Formation:
CEAACK is integrated with clustering and a routing protocol in Wireless Sensor Networks (WSN).the main goal is to reduce the energy consumption while creating clusters. The energy conserved is applied to data transmission which indirectly increases the life of the wireless sensor network.
With the help of the CEAACK protocol the nodes can transmit data to the CHs. The CHs in turn aggregate the data received from its members, compresses it and then forwards it to the BS. Each node uses a CEAACK Cluster Head Selection algorithm to determine whether it would become the CH for a particular session. CEAACK assumes that each node has enough energy to directly reach the BS or at least the nearest CH.
A node which has been a CH cannot do so again for ‘N’ number of sessions. ‘N’ here can be a predetermined threshold based on the battery power of the nodes. Thus, each node has a 1/ N probability of becoming a cluster head in each session. After a session the node which is not a CH joins a cluster whose CH is closest to this node.
The CH is also responsible for preparing the schedule for each of the nodes in its cluster for the purpose of data transmission. Nodes of a cluster use TDMA to communicate with the CH based on this schedule. Even this communication between the cluster members and the CH is done with minimum energy consumption. During their time slot each member only need to keep their radio on.
However, there are a few disadvantages in selecting a CH.
-
• Due to the probabilistic nature of the CH selection, sometimes two CHs which are very close to each other can be selected which invariably increases the energy depletion
-
• The number of CHs selected may sometimes be more or less than the preferred number of CHs required
-
• If a CH is located at the edge of a network ,it is more likely that the other nodes will have to spend a lot of energy transmitting to the CH
-
• CPU cycles are wasted in threshold calculation and random number generation in each round which will consume energy unnecessarily
-
IV. Existing Approach (EAACK)
EAACK is an acknowledgement based authentication approach consisting of three modules, namely, ACK (ACKnowledgement), S-ACK (Secure ACK) [1] [2] and MRA (Misbehavior Report Authentication) for the purpose of secure data transmission[3].
ACK: A data packet is sent from the source to the destination node with the help of intermediate nodes. If the packet is received successfully at the destination, the destination node will send an ACK packet on the reverse route. In case the source node does not receive an ACK from the destination within a predetermined time, it sends a S-ACK data packet in order to detect the misbehaving node along the route [1] [2].
S-ACK: Whenever a data packet is sent, the third consecutive station along the route is responsible for sending a S-ACK packet to the first station within a specific threshold time. If the S-ACK packet is not received within the specified time, nodes 2 and 3 are declared malicious by node 1.Node 1 also updates the source node with this information. In order to confirm this report the source node uses the MRA mode. S-ACK is an improved version of TWOACK [2].
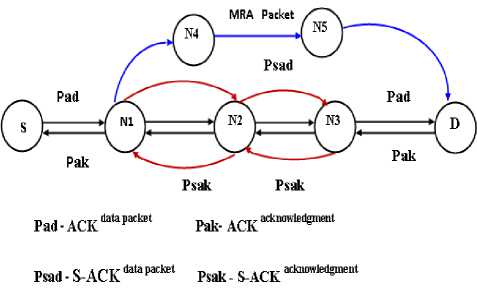
Fig.5. EAACK Architecture
MRA: This scheme identifies the misbehaving nodes based on the report sent by node N1 from the S-ACK scheme. Upon receiving the MRA packet the destination node searches its local database containing packet information. If the packet has been received, the destination concludes that the received report is a false one. If not the MRA report is trusted and accepted by the destination. The major drawback in this scheme is that it requires complex authentication procedures during acknowledgements. Authentication is done before data packets are routed which causes high computational delay. Due to this the performance of the network goes down and the quality of service is affected and very high energy is spent. The network soon goes down because of the high energy spent.
-
V. Our Proposed Concept (CEAACK)
In this paper we suggest a cluster based authentication scheme by forming clusters and cluster head. This method saves energy and also improves data transmission to a great extent. To select the CH a CH election is conducted to select one of the nodes in the cluster as the head node. All information pertaining to the cluster is maintained by the cluster head. This includes the number of nodes in the cluster and the route to each node.
The CH needs to communicate with all of its members and also with the members of other clusters as well. Communication with members of other clusters can be carried through the respective CHs or by using gateways. Communication involves three steps. The CH firstly receives data from all its members, compresses it and then transmits this data to the BS or other CHs as required.A well suited CH has the ability to conserve energy and also to improve the performance of the network.
Fig.6. Shows NS2 Simulation Screen Scenario for EAACK
The cluster members communicate to their CH .The ACK packets are sent by the members to their CH in the form of SACK and 2ACK packets .This is similar to the EAACK approach. The CH‘s responsibility is to compress all the ACK packets received from its members and route it to the BS. The BS sends MRA packets to each of the cluster members within the cluster. The base station does not communicate directly with the cluster head since it has to determine whether each of the cluster member is working or malicious.
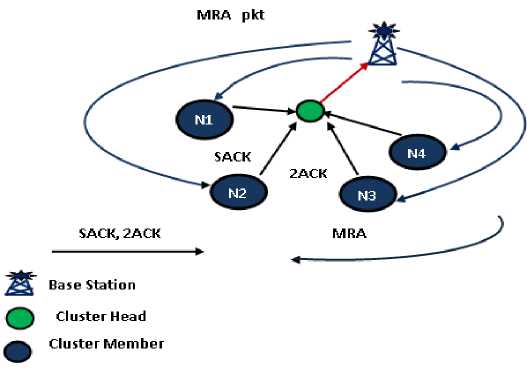
Fig.7. Architecture of CEAACK
Fig.8. NS2 Simulation Screen Scenario for CEAACK
The performance of the network depends on the selection of an efficient CH. A CH is selected based on various factors. Factors including the proximity of the
CH to the other nodes, energy, delay throughput and the PDR (Packet Delivery Ratio) ratio of the nodes are considered .We propose a new algorithm named CEAACK Cluster Head Selection Algorithm which will help in selecting an efficient CH from a group of nodes.Fig.8 shows NS2 simulation screen scenario for CEAACK.
-
A. CEAACK Cluster Head Selection Algorithm
Two important factors decide whether the status of a node in a cluster as that of a CH or as a node member. They are
-
1. Cluster node Energy Level
-
2. Traffic Load
We calculate N (CH) value based on these two factors. A cluster node with max (N(CH) ) is suitable for cluster head. The formula for calculating N(CH) is given in equation(1)
N(CH) = E(SN) + 1 I R(SN) (1)
Where,
N(CH) - New cluster Head
E(SN) - Energy of selected node
R(SN) - Range of selected node
The two figures in fig. 9 shows the various stages of Energy Level and Traffic Load, which used for selecting Cluster Head.
-
B. Pseudo Code
The cluster head in a MANET plays an important role in synchronizing the traffic and to effectively transfer packets with the minimum delay. For this purpose the cluster head is selected based on parameters like the energy of the node, the load it can handle and the current status of the node. These parameters are used as a filter to find the strongest node among all other contenders.
We have tried to develop a pseudo code where the above mentioned parameters are considered while selecting a cluster head from a group of nodes.
A combination of these selection parameters are given in table 1 where the parameters are considered in the various combinations of their current state.
Calculate N (CH) - New(Cluster Head)
For Cluster Head Selection
During the selection of cluster head If Cluster node
Table 1. Selection of a Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
High |
Very Low |
Selected |
|
Very High |
Very Low |
Selected |
|
Very High |
Low |
Selected |
|
Very High |
Medium |
Selected |
For instance in table 2 the selection of the cluster head is based having a very high energy level but a very low traffic load .This node can be selected as a Cluster Head (CH).Again, a node with a very high energy level and minimal traffic can be selected too.
For Cluster Head Selection
During the selection of cluster head
If Cluster node
Table 2. Selection of a Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Very Low |
Very Low |
Selected |
|
Low |
Medium |
Selected |
|
Low |
High |
Selected |
|
Medium |
High |
Selected |
|
Medium |
Very High |
Selected |
In table 3 we analyze a different scenario where the energy level may be very low, but if the traffic load is low or medium, the node can still be selected since the traffic load is not too heavy to cause interruption in transmission
A cluster node with max value of N(CH) is suitable for cluster head.
Else If Cluster node
Table 3. Selection of a New Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Low |
Very Low |
Selected |
|
Low |
Low |
Selected |
|
Medium |
Low |
Selected |
|
Medium |
Medium |
Selected |
|
High |
High |
Selected |
Looking at the parameters discussed in table 4 we can see that even if the two main parameters tend to be the same the cluster head is selected based on the fact that though the energy level is medium or low, if the load tends to be slow at that point of time, the node can handle the network and can be selected as the CH. Even if the traffic load is high the node can be selected provided the energy of the node is very high.
A cluster node with max value of N(CH) is suitable for cluster head
Else If Cluster node
Table 4. Selection of a New Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Very Low |
Very Low |
Selected |
|
Low |
Medium |
Selected |
|
Low |
High |
Selected |
|
Medium |
High |
Selected |
|
Medium |
Very High |
Selected |
Similarly for the rest of the clusters these parameters discussed above are considered in various combinations to ensure that the best cluster head is selected for a session. This ensures that for every session requiring a new cluster head, the best one is selected in order to carry on the transmission effectively without any delay. This is illustrated in table 5 through table 7.
A cluster node with max value of N(CH) is suitable for cluster head.
Else If Cluster node
Table 5. Selection of a Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Low |
Very Low |
Selected |
|
Low |
Low |
Selected |
|
Medium |
Low |
Selected |
|
Medium |
Medium |
Selected |
|
High |
Very High |
Selected |
A cluster node with max value of N(CH) is suitable for cluster head.
Else If Cluster node
Table 6. Selection of a New Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Low |
Very Low |
Selected |
|
Low |
Low |
Selected |
|
Medium |
Low |
Selected |
|
Medium |
Medium |
Selected |
|
High |
Very High |
Selected |
A cluster node with max value of N(CH) is suitable for cluster
Else Cluster node
Table 7. Selection of a new Cluster Head
|
Energy Level |
Traffic Load |
Cluster Node Status |
|
Very Low |
Low |
Selected |
|
Very Low |
Medium |
Selected |
|
Medium |
High |
Selected |
|
Very Low |
Very High |
Selected |
|
Low |
Very High |
Selected |
-
VI. Experimental Analysis
An analysis of the following factors provides us with an insight into the performance differences between EAACK and CEAACK
-
• Throughput
-
• Delay
-
• Energy
-
• Packet Delivery Ratio(PDR)
Throughput:
It is the rate of successful message delivery over a communication channel. This data may be delivered through a certain network node. The throughput is usually measured in bits per second (bit/s or bps), and sometimes in data packets per second or data packets per time slot.
Packet Delay:
It is an important design and performance characteristic of a Data communication network. The delay of a packet specifies how long it takes for a data bit to travel across the network from one node or to another. It is typically measured in multiples or fractions of seconds.
Energy:
It plays a very important role in packet delivery. The actual meaning of energy is power required to forward the packet to next node without any dropping of packet. Generally a node with high energy acts as a Cluster head.
Packet Delivery Ratio (PDR):
pdr =n o . of p ackets received / n o . of p ackets s ent (2)
Comparative Analysis of EAACK and CEAACK
A Comparison of the above said factors between EAACK and CEAACK is performed to analyze the effect of using the two techniques discussed in this paper. Based on it we can see that CEAACK gives a better performance than EAACK.In future these comparisons can be used to set up a network that is high on performance and low on energy consumption. Studying the network in terms of clusters helps us understand the nature and the reliability of the network. We can see that throughput is low in CEAACK but the packet delivery ratio is higher in CEAACK when compared to EAACK. Subsequently the delay between packets is lesser and the energy spent is also low in CEAACK, giving it an overall better performance than EAACK. The idea is to achieve better delivery performance and consume as less energy as possible which is achieved through CEAACK.
The graph in fig.13 shows the packet delivery of CEAACK is very effective when compare with EAACK.
The key for the graph is given below
EAACK CEAACK
Based on the parameters mentioned above a comparative study is done to assess the difference in transmission with respect to EAACK and CEAACK
Comparison of Throughput- EAACK and CEAACK
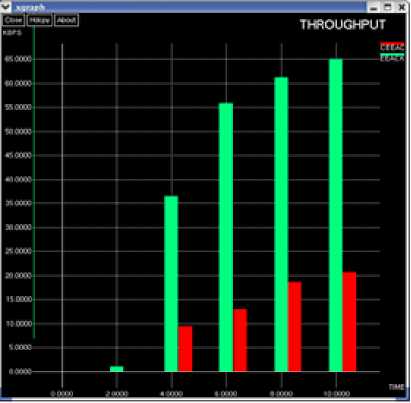
Fig.10. Throughput -EAACK and CEAACK
Comparison of Packet Delay between EAACK and CEAACK
The graph in fig.11 shows the packet delay of CEAACK when compared with EAACK.
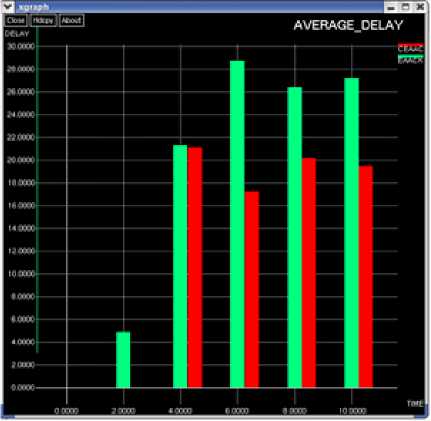
It can be seen that the delay in the deliver of packets is much higher in EAACK when compared to the average delay in CEAACK. This will definitely improve network
Performance as the delay is much reduced in CEAACK thus making transmissions faster than EAACK.
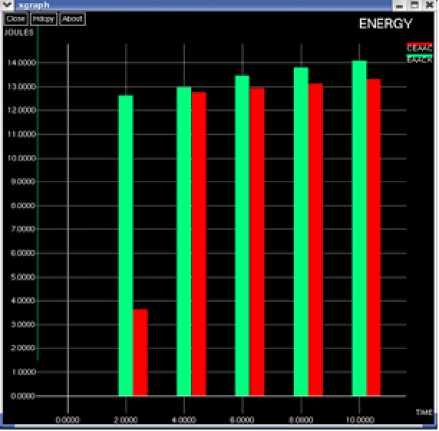
Comparison of Energy between EAACK and CEAACK
The graph in Fig.12 compares the energy between EAACK and CEAACK. The graph, which shows that energy consumed is higher in EAACK.
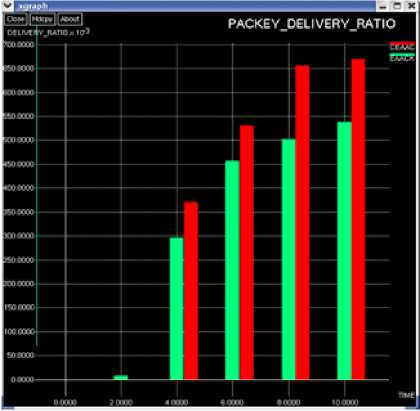
Comparison of Packet Delivery Ratio EAACK and CEAACK
The graph in Fig.13 compares the packet delivery ratio between EAACK and CEAACK.
The PDR of CEAACK is much higher than EAACK which shows that by involving the cluster head concept in MANETs we can improve the efficiency of transmission to be better than EAACK.
Initially EAACK may have showed a greater throughput than CEAACK but in terms of all other major parameters, CEAACK outperforms EAACK. The transmission is much more effective using CEAACK.
VII. Conclusion and Future Enhancement
In this research paper, we have proposed an Energy Efficiency and delay reduction method named CEAACK, which is a combination of EAACK [IDS] by implementing Clustering technique specially designed for MANETs. This technique is then compared with the existing IDS EAACK in various scenarios with the help of the NS2 simulator. We compare some factors of EAACK with CEAACK, which includes energy, delay, throughput of the nodes, packet delivery ratio of the node (PDR) etc. The results obtained showed increased performance in EAACK. Which is achieved by implementing the Clustering technique called CEAACK Cluster Head Selection Algorithm which helps to select the cluster head between different time intervals from the group of nodes. The outcome of this approach is evident in the amount of energy that can be saved by implementing this approach in the wireless sensor network. Furthermore this approach also reduces delay by controlling acknowledgment packets and improves data transmission in MANETs.
To increase the merits of our research work, we plan to focus on the following issues in our future research:
-
1) Analyze the performance of CEAACK in real time
network environment instead of a software simulation(NS2)
-
2) Studying the impact of the different types of attacks and compare the energy, delay, throughput of the nodes and packet delivery ratio (PDR) of both EAACK and CEAACK
-
3) Adopting Advanced cryptography techniques to reduce the network overhead caused by digital signature
Список литературы CEAACK – A Reduced Acknowledgment for Better Data Transmission for MANETs
- Chinmay K.Nayak, G.K.AbaniKumar, Parida, Das," Detection of Routing misbehavior in MANET with 2ACK schene, Vol.2, No.1, Jan. 2011.
- R.Balakrishna, M.MuralimohanReddy, U.Rajeswar Rao, G.A, Ramachanndra, "Detection of Routing Minbehavior in MANET", using 2ACK", IEEE International Advance Computing Conference (IACC 2009), Patiala, India, pp 6-7 March 2009.
- Elhadi M. Shakshuki, Senior Member, IEEE, Nan Kang, and Tarek R. Sheltami, Member, IEEE" EAACK—A Secure Intrusion-Detection System for MANETs" IEEE Transactions on Industrial Electronics, Vol. 60, No. 3, March 2013.
- Prof. Poonam Gupta, Sarita Chopde," Detection of routing misbehavior in MANET using improved 2ACK ", IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p- ISSN: 2278-8727Volume 9, Issue 1 (Jan. - Feb. 2013), pp 53-60.
- Aishwarya Sagar Anand Ukey, Meenu Chawla, "Detection of Packet Dropping Attack Using Improved Acknowledgement Based Scheme in MANET", IJCSI- International Journal of Computer Science Issues, Vol. 7, Issue 4, No 1, July 2010.
- Yongguang Zhang HRL Laboratories, Wenke Lee Department of Computer Science North Carolina State University Raleigh," Intrusion Detection in Wireless AdHoc Networks "MobiCom 'Proceedings of the 6th annual international conference on Mobile computing and networking pages 275-283, 2000.
- A. Singh, M. Maheshwari and N. Kumar, "Security and trust management in MANET," in Communications in Computer and Information Science, vol. 147. New York: Springer-Verlag, pp. 384–387, 2011.
- B. Sun, "Intrusion detection in mobile ad hoc networks," Ph.D. dissertation, Texas A&M Univ., College Station, TX, 2004.
- S. Marti, T. J. Giuli, K. Lai, and M. Baker, "Mitigating routing misbehavior in mobile ad hoc networks," in Proc. 6th Annu. Int. Conf. Mobile Computer Network, Boston, MA, pp. 255–265, 2000.
- K. Liu, J. Deng, P. K. Varshney, and K. Balakrishnan, "An acknowledgment-based approach for the detection of routing misbehavior in MANETs," IEEE Trans. Mobile Comput., vol. 6, no. 5, pp. 536–550, May 2007.
- Sunilkumar, S. Manvia, Lokesh B. Bhajantrib, and Vittalkumar K. Vaggac, "Routing Misbehavior Detection in MANETs Using 2ACK", journal of telecommunication and information technology, pp. 105–11, April 2010.
- Kiran Maraiya, Kamal Kant, Nitin Gupta," Efficient Cluster Head Selection Scheme for Data Aggregation in Wireless Sensor Network "International Journal of Computer Applications (0975 – 8887) Volume 23– No.9, June 2011.
- Indranil Gupta, Denis Riordan , Srinivas Sampalli," Cluster-head Election using Fuzzy Logic for Wireless Sensor Networks " CNSR 'proceedings of the 3rd Annual Communication Networks and Services Research Conference page 255-260, 2005.
- K.Ramesh and Dr. K.Somasundaram "A Comparative Study of Cluster head Selection Algorithms in Wireless Sensor Networks "International Journal of Computer Science & Engineering Survey (IJCSES) Vol.2, No.4, November 2011.


