Comprehensive study of data aggregation models, challenges and security issues in wireless sensor networks
Автор: Veena I. Puranikmath, Sunil S. Harakannanavar, Satyendra Kumar, Dattaprasad Torse
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 3 vol.11, 2019 года.
Бесплатный доступ
The use of wireless sensor networks has been increasing tremendously in the past decades mainly because of its applications in military, medicine, under water survey and various other fields. Depending on the applications the sensor nodes are placed in different areas and the data sensed will be sent to the base station. The process of transmitting and receiving data sensed by the sensor nodes continues till the sensors have battery life. This leads to generate data redundancy and reduces efficiency of the network. In order to overcome the limitations faced by the wireless sensor networks, the fusion of data known as data aggregation is introduced. In data aggregation, the data sensed by the various nodes are aggregated and sent to the base station as a single data packet. In this paper, a brief review on various data aggregation methods, challenges and issues are addressed. In addition to this, performance parameters of various data fusion methods to measure the efficiency of the network are discussed. The design of single aggregator models are easy compared to the multiple aggregator models. However, the security to most of the data fusion schemes is provided by using message authentication code. It also uses public keys and symmetric to achieve end to end or hop by hop encryptions.
Data Aggregation, Authentication, Wireless Network, Nodes, Redundancy
Короткий адрес: https://sciup.org/15015674
IDR: 15015674 | DOI: 10.5815/ijcnis.2019.03.05
Текст научной статьи Comprehensive study of data aggregation models, challenges and security issues in wireless sensor networks
Published Online March 2019 in MECS DOI: 10.5815/ijcnis.2019.03.05
In recent days, the growth in the field of Wireless Sensor Networks (WSN) has increased with the applications such as military, medical, wild life hesitation and transportation. Figure 1 shows the general architecture of Wireless Sensor Network. The architecture of WSN consists of sensor nodes which are deployed in scattered way depending on the environment and the type of application. Each sensor node sends the collected information to the intermediate node followed by the base station (BS). Every time the transmission of information to the sink node and the base station leads to the consumption of energy of the nodes and reduces the network lifetime [3].
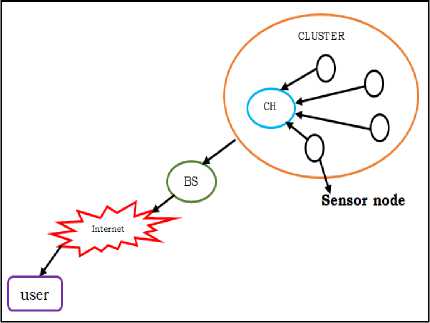
Fig.1. General Architecture of Wireless Sensor Network
Hence to develop an efficient wireless sensor network the parameters such as energy, reliability and fault tolerance, scalability, data delivery mode, quality of service and network dynamics needs to be considered. Sensor nodes play a vital role in wireless networks and their characteristics [2] are described as follows
-
• Limited battery life: The nodes don’t have the provision to recharge the battery if there is a small drop in its power. As a result of this, nodes are disposed after the completion of battery life.
-
• Low processing capabilities: The processing capacity of nodes will be low as they are designed only for a particular application in order to maintain low cost.
-
• Limited data storage capacity: Nodes don’t have more memory storage unit in order to maintain the battery life.
It is observed that WSNs suffers from various issues such as limited computational power, limited memory and battery power which leads in increasing the complexity for development of applications. In order to overcome the limitations faced by the WSNs, the method of Data Aggregation (DA) is introduced to aggregate the data from the various sensor nodes using the different aggregation approaches [12].
In this paper, a comprehensive study of various data aggregation approaches, challenges and issues are discussed in detail. The rest of the paper is organized as follows: section II deals with the Related Work and working principle of data fusion model. Section III describes the various Data aggregation Approaches. Section IV discusses the Issues and performance parameters of data aggregation models. The comparative study of different algorithms is discussed in Section V. advantages and limitations of the data fusion are explained in Section VI. The conclusion is presented in section VII.
-
II. Related Work
Data aggregation is a technique of gathering and aggregating the significant information to save the limited resources in the wireless sensor networks. The main purpose of data aggregation models is to collect and aggregate data in efficient way to improve the network lifetime [4]. When the sensor network is positioned in a hostile environment the issues such as security, confidentiality and integrity plays vital role in data fusion models. Figure 2 shows the general data aggregation model.
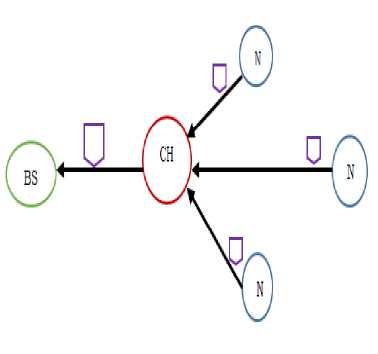
Fig.2. General Data Aggregation Model
The figure 3 shows the architecture of data aggregation [19, 31] the sensor data using different data gathering techniques in the process of data aggregation. The collected data from the sensor nodes gets aggregated by adopting various aggregation models such as centralized approach, tree based approach, In-network based approach and cluster based approach. Finally, the aggregated information transfers to the sink node through an efficient path.
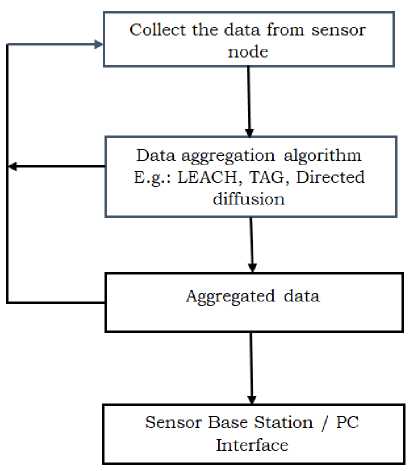
Fig.3. Architecture of Data Aggregation
-
A. Existing Work on Data Aggregation
Yang [1] describes the construction of data trees based on information entropy in the minimum spanning tree and theory of information entropy are applied to design the protocol in order to reduce the amount of consumption of energy during transmission. The entropy based data aggregation tree and greed prim tree algorithms are used to achieve the superior result. Frej et al., [2] presented a secure aggregate communication at a low cost and work with three layers of the network. The algorithm improves energy saving in the network and extends the network lifetime. Bagaa et al., [3] proposed an aggregation tree that extends the network lifetime through reducing the overhead on non-harvesting node as much as possible. In order to overcome the limitations, the model provides two solutions such as packet payload aggregation and accelerated packet payload aggregation. Sran et al., [4] adopted energy aware chain oriented sensor network protocol to reduce the consumption of energy by considering duty cycles as a parameter in the overall network. In addition to this, it also improves the performance of the network in terms of throughput and residual energy. Zhou et at., [5] described three data gathering solutions to improves the network lifetime of wireless sensor network by implementing three mixed-integration linear programming model. Vipan et al., [10] considered taxonomy of in-network aggregation for defining the main concepts and provides a comprehensive survey of data aggregation algorithms in wireless sensor networks.
-
B. Working Principle of Data Aggregation
The main purpose of data aggregation models is to collect and aggregate data in efficient way to improve the network lifetime. Figure 4 shows the working principle of data aggregation model [31].
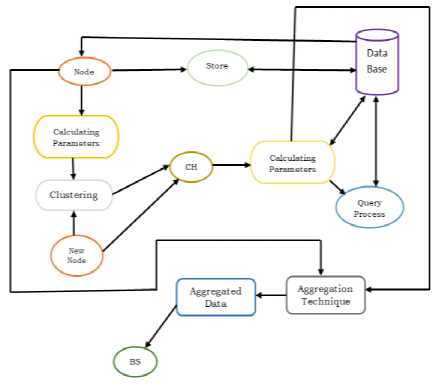
Fig.4. Working Principle of Data Aggregation Model
The following steps explain the working model of Data aggregation [2, 31]
Step 1: Selection of sensor nodes: Choose the sensor nodes which are deployed in defined area to collect the information and stores the values in database.
Step 2: Formation of Cluster: This includes obtain the information from sensor nodes, Choose and collect the appropriate nodes followed by grouping and evaluation to find the efficiency of the network are discussed below.
Step2a: Fetch information: Obtain the information from the established sensor nodes and measurable parameters such as Reduced Signal Strength Indication (RSSI), Time to Live (TTL), bandwidth and battery consumption.
Step2b: Choose the nodes: Select the nodes which are efficient and having minimum global cost.
Step2c: Collection of nodes: Gather all the sensor nodes which are eligible in Step 2b.
Step2d: Grouping: Group the nodes depending on step 2b, step 2c, evaluate and estimate the efficiency of the group or cluster.
Step2e: Evaluation: Check the efficiency of the network after grouping.
Step 3: Selection of Cluster Head (CH): Cluster heads are responsible for administration of all different sensor nodes and gathering the information from the sensor nodes within the cluster and communicate with the neighboring CH’s of the different cluster and updating the information. If a new node arrives in the network, the global cost of the node will be checked and is lesser than the existing node. Then the current CH will be replaced by the new node.
Step 4: Data Aggregation: The collection of data and the queries from the user-end are verified. As a result the data is transferred to the low level schemes through query process. Then, the aggregation of data is done by choosing any one of the aggregation approach. Data Aggregation process decides to locate a drop of data sent through a source node, to identify the various approaches in order to gather the information with aggregation nodes, to test the developed model in terms of correctness and security.
Step 5: Aggregated data will transfer to the base station for further use depending on the applications.
-
C. Attacks in Data Aggregation
In wireless sensor networks the process of gathering information may affected by several types of attacks, some of them are given in the table 1.
Table 1. Data Aggregation Attacks in WSN [19]
|
Sl. No. |
Types of attacks |
Reason of Attacks |
Resolved |
|
1 |
Repeat Attack |
Retransmission of same data without data freshness |
Assigning timeslot |
|
2 |
Denial of service attack |
Interference with radio frequency |
Using MAC |
|
3 |
Data Integrity Attack |
Adding false data |
Using digital signature and MAC |
|
4 |
Sybil attack |
Making multiple identities |
Using authentication schemes |
|
5 |
False packet and Malleability attack |
Addition of malicious node in the network |
Using Hash based Message Authentication Code |
|
6 |
Sinkhole attack |
Attacking traffic to the specified danger node |
Following proper routing and localization information |
|
7 |
Energy Drain attack |
Due to energy depletion |
Making use of natural energy resources such as solar power |
|
8 |
Sniffing Attack |
Hacking the information through malicious node |
Using protocols with confidentiality of information |
|
9 |
Physical Attack |
Due to lack security of symmetric key technique |
Use of asymmetric public key technique |
-
D. Goals of Data Aggregation
The goals of fusion models in the wireless sensor networks are described as follows
-
• Energy Efficiency: Every node in the network should sense the information as long as available. In data aggregation scheme fusion of information reduces the usage of nodes and leads to increase in its efficiency.
-
• Data accuracy: Data Accuracy is measuring the accuracy between the raw data and recovery data. During the process of aggregation, while collecting the information from the sensor node there is a chance to lose the information. Hence, the recovered data at the sink node is compared with the raw data to ensure the data accuracy.
-
• Network capacity saving: Aggregated node sends the less data to the sink node. This reduces energy consumption and increases the lifetime of the network as well as the capacity of network.
-
• Latency: Data Aggregation technique reduces the time delay between the collecting and transferring the gathered information to the sink node.
-
E. Motivation of Data Aggregation
Data Aggregation is a key approach to save the energy consumption in wireless sensor network. But, still data aggregation has challenges and needs to be overcome in order to improve the performance of the network [3]. In current algorithms, all aggregation approaches are dependent on raw data to form a cluster to aggregate the information. Sometimes, abnormal data frequently appears in raw data which leads in data instability and affects the performance of such approaches. In other cases, many aggregation applications are defined for a certain data types (e.g. Weather) or a type of network property (e.g. grid network), which decreases the adaptivity of these functions. This motivates to propose data independent aggregation models to improve the efficiency of the network.
-
III. Data Aggregation Approaches
In order to overcome the limitations of wireless sensor network, the various data fusion models are discussed to increase the efficiency of the overall network.
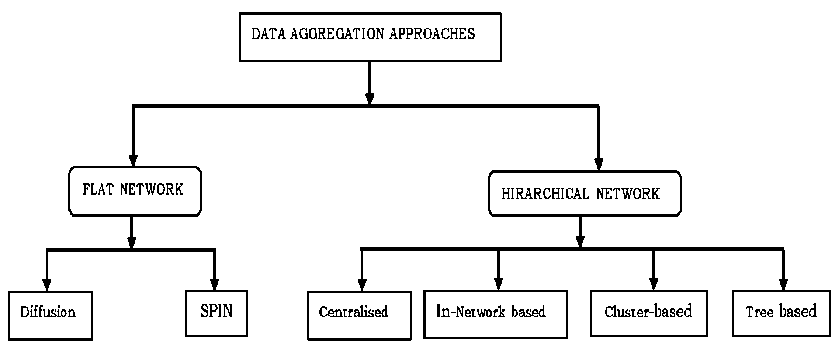
Fig.5. Different Data Aggregation Approaches
The brief classification of various data aggregation scheme is shown in figure 5.
-
4- Flat Networks: In Flat networks [31], each sensor node acts in the same way and are supplied with approximately the same battery power. In this case, data aggregation has centric routing where the sink node usually transmits a query message to the sensors via flooding. Finally, sensor nodes which have matching information to the sent query will responds back to the sink node through the message and the choice of the protocol depends on the type of specified application. There are two types of Flat approaches such as Direct Diffusion (DD) and Sensor Protocols for Information via Negotiation (SPIN).
-
• Direct Diffusion (DD): It is widely adopted in data aggregation models for wireless device networks. It is an application based and data centric method where each data produced by the sensor node is known as
attribute-value pairs. The DD technique reduces the redundancy and leads in minimizing the amount of transmission by combining the data from different nodes to the sink node. In addition to this, it also increases the lifespan of the network and reduces the energy consumption in the network. Here every node receives the interest and the interested nodes are kept for further use. If the interest is broadcasted by the network using hop by hop technique, then gradient square measure setups to confirm the data matching the query towards the requesting node. A gradient acts as reply to the nearer nodes from which the interest was received.
-
-I- Hierarchical Networks: In hierarchical scheme, the data aggregation method is applied at particular node which helps to reduce the number of data packets transmitted to the sink node. This results for modeling the energy efficient network by reducing the consumption of energy. Depending on the
applications, they are classified into four hierarchical techniques.
-
• Centralized Approach: In this approach, all the sensor nodes send data to a central node through the possible shortest route. All the information from the sensor nodes will be sent to the leader node (Header node), which is powerful and efficient node among all other nodes in the network. This header node performs the data aggregation from all sensor nodes and results in the single packet. Figure 6 shows the centralized data aggregation model.
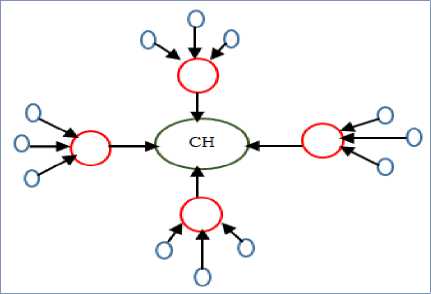
Fig.6. Centralized Approach
-
• Decentralized Approach: In this approach, all the sensor nodes are free to transmit and receive the data from all neighboring sensor nodes. Here, all the nodes act as an aggregator to sense the data which have same priority and in the absence of no single centralized node. This technique has several advantages in measuring scalability, dynamic change of node in case of node failure . f igure 7 shows the decentralized data aggregation model.
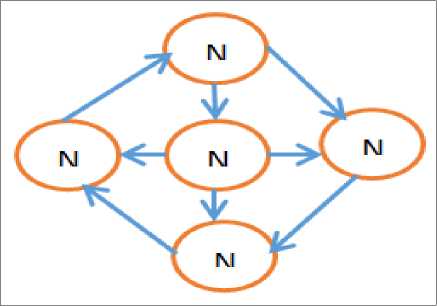
Fig.7. Decentralized Approach
-
• In-Network Approach: In this case, aggregation is processed by collection and routing the information through a multi-hop network which processes the data at intermediate nodes with the aim of reducing the consumption of resources. This in turn increases the lifespan of the network. The approach is classified into two sub categories such as aggregation with size reduction (combining and compressing the information packets received by a node from its
neighbors and reduces the length of packets) and aggregation without size reduction (merging information packets from the various neighboring nodes in to a single packet without processing the genuine information). The network arrangement of Innetwork is shown in figure 8.
Fig.8. In-network Approach
-
• Tree based Approach: In this method, the sensor nodes are arranged in the form of tree means hierarchical manner. Hence such type of an arrangement forms the data aggregation tree. In this approach the leaf nodes will send the gathered information to root node (sink node) through intermediate nodes (parent node). Here the aggregation process is carried out by parent node. The main concept to build this approach is to construct an energy efficient data aggregation tree or a shortest path routing tree using the rule viz., shortest path tree and so on.
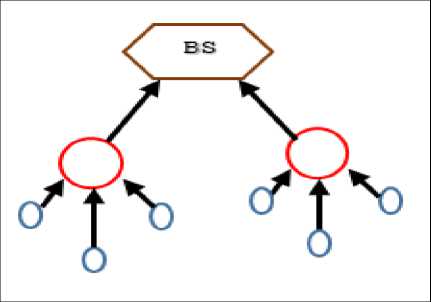
Fig.9. Tree based Approach
-
• Cluster based Approach: In cluster based approach the complete network is divided into various clusters and each cluster is formed by several sensor nodes. Next, each cluster possesses one header node named as cluster-head. The cluster heads process the aggregation and transmits the aggregated data to the sink node. This process reduces the overhead bandwidth as total number of data packets received by the sink node decreases.
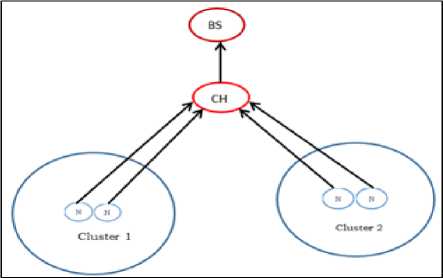
Fig.10. Cluster based Approach
-
IV. Issues and performance parameters of data
AGGREGATION MODELS
In this section the issues related to the data fusion methods and performance parameters to measure the efficiency are discussed. Performance of the data aggregation in the network is getting affected by the issues as follows:
-
A. Issues in Data Aggregation
-
4- Elimination of Redundancy: In wireless sensor network, sensor nodes sense the data of same pattern and forward it to the sink node. At the sink node, the energy is consumed to process the redundant data which leads to decrease in the lifetime of network. Hence in order to eliminate the redundant data in the fusion methodology, several techniques are discussed in detail. Some of them are as follows
-
• Aggregation of Data at Intermediate node: In this method instead of performing the aggregation at the sink node, the process will be carried out at the intermediate nodes. This helps to remove the redundancy and traffic load in the network. One of such algorithm is dynamically balanced spanning tree.
-
• Locality Sensitive Hashing: In this scheme, the length of the generated harsh code is small in size compared to original data. These generated codes are sent to the supervisor node. Based on the matching results of harsh code, the procedure of choosing the sensor node by the supervisor node is initiated. Further, the supervisor node obtains the count of redundant codes. If the generated harsh codes have similarity index more than the set threshold value then such codes are rejected. One of such algorithm is support vector machine based data redundancy elimination.
-
• Intra cluster and Inter cluster aggregation: In case of the intra cluster scheme, input data is compressed at source nodes and the same will be forwarded to the cluster. In case of inter cluster scheme, the aggregation is performed after the removal of redundant information and data compression is carried out inside the cluster by cluster head. Finally the compressed data is forwarded to the network. Some of the algorithms involved in this scheme are redundancy eliminated data dissemination, bandwidth
efficient heterogeneity aware cluster based data aggregation.
-
• Correlation coefficient: In this case, the data which is collected from the nodes is represented by an integer. The value of correlation coefficient (H) lies in between 1 to 10. The strong correlation of data results when the value of correlation coefficient reaches unity. As the correlation coefficient increases, its degree between the data decreases. If the correlation coefficient between two data reaches three, then data sends to the node in the network. Otherwise there is a need of normalization process to be adopted for elimination of data redundancy.
-
4- Delay: It is the difference between the time taken by the receiver to receive the packet and sender to send the same packet. The method of data aggregation reduces the redundancy but may result in network delay, as intermediate nodes hold the information back in order to aggregate the data from the farthest nodes. The delay is proportional to the number of hops between the farthest node and the sink node. The tree based approaches are discussed in detail to reduce delay are as follows
-
• Distributed data aggregation scheduling: In this algorithm, each node is allotted with particular time slot in the aggregated tree. One of the algorithms involved in this type is delay efficient data distributed aggregation.
-
• Minimum spanning tree creation: In this method, the communication between the source and destination node is carried out by choosing the minimum weight path and reduces the bandwidth consumption as well as delay in the network.
-
4- Accuracy: In data aggregation each node sends the data to the aggregated node and forwards it to the network. During this protocol, if any of the nodes in the network sends wrong information then it leads to an inaccuracy. Hence in order to maintain accuracy in data fusion methods there are several techniques such as linear classifier, context aware system and adaptively changing cluster size are considered.
-
• Linear classifier method: In this scheme, the sensor nodes are separated into two partitions with valid and invalid nodes based on the redundancy count of each node in the network. The same information which is partitioned will be forwarded to supervisor node. Finally, the information obtained from each cluster in the network is compared with the harsh code to classify as valid code.
-
• Context aware system: In this case, the data collected by the sensor nodes are checked against the rules of rule engine. The acceptance and rejection of data is decided based on the satisfaction of rules formed by the rule engine.
-
• Adaptively changing cluster size: In the network, variations of the cluster size helps to avoid the transmission of false information from source to destination nodes. Here, the cluster head lead the aggregation procedure and the data will be forwarded to the coordinator node. The ratio of amount of data
packets forwarded and the data packets received calculates the loss ratio. If the loss ratio of the node is high then the particular node in the cluster is removed from the network and addition of invalid nodes can be avoided. This technique increases the reliability and reduces the consumption of energy in the overall network.
-
4- Traffic Load: Here, the data fusion is carried out by cluster head alone and may suffer from heavy traffic load at the particular time period which leads in more consumption of energy in the network. Two methods are discussed in detail to overcome the traffic load issues in the network such as dynamic spanning tree approach and distributing role of cluster head.
-
• Dynamic Spanning Tree Approach: Based on the residual energy of nodes, new cluster head is selected for every round of aggregation in the network. Hence, these new selected nodes are considered to form new data aggregation tree known as minimum spanning tree.
-
• Distributing role of cluster head: In this scheme, after
completion of each round of data fusion in the network, residual energy of the node is calculated. If the result of residual energy reaches higher value then the node is considered as a cluster head. This procedure helps to make all the nodes to act as a cluster head once in their life time before the network ends.
-
B. Security issues in Data aggregation
Two types of Securities are required for data aggregation in wireless sensor network namely Confidentiality and data integrity. The confidentiality process helps to protect the sensitive [45] data transmission and passive attacks whereas the integrity helps to reduce the compromised sensor nodes in the network. There are two types of methods such as hop by hop encryption and end to end encryption for securing the data in wireless sensor network.
Table 2: General steps of hop by hop and end to end encryption [19]
Step1: Encryption process is initialized by sensing the nodes in wireless sensor network.
Step2: Decryption process in performed by considering aggregator nodes.
Step3: Aggregator nodes aggregates the result followed by encrypting the data again.
Step4: The sink node gets final aggregated result and decrypting the data again.
The general steps of hop by hop and end to end encryption mechanisms are tabulated in table 2.
-
-I- Energy Efficiency: Data aggregation process is adopted to increase the functionality of wireless sensor network. If the sensor node consumes the same amount of energy in every data aggregation round then the functionality of the wireless sensor network increases which results in efficient energy utilization.
-
-I- Network lifetime: The network lifetime decision is based on the number of data fusion rounds. In an application oriented area, the information is gathered before the percentage of collapsing sensor nodes reaches the specified time. Hence the lifetime of the network is number of rounds until the first node remains active. This reduces the consumption of energy of sensor nodes and leads to enhance the lifetime of network.
-
4- Latency: The parameter latency is measured based on the delay time taken by the receiver node (base station) to receive the packet sent by the sensor node (source node). The mechanisms such as data transmission, data aggregation and routing algorithms are affected by the delay factor.
-
4- Communication overhead: In data aggregation process, aggregator node is overloaded by the data sent from the sensor nodes which leads to the overlapping of information and results in complexity of the network.
-
-4- Data accuracy: Data accuracy is defined as the ratio of total number of data received at the base station (sink) to the total number of data generated from the source node.
-
V. Comparative Analysis of data aggregation
MODELS
This section mainly deals with the comparative study of various data fusion strategies with the issues like redundancy, delay, accuracy and traffic load which are tabulated in table 3 [11]. The various techniques we are studying are included with Dynamically Balanced Spanning Tree (DBST) [6] which helps to eliminate the redundant data in the network. The SVM based Data Redundancy Elimination (SDRE) [26] reduces the energy consumption and redundancy in the network. In inter cluster and intra cluster aggregation methods the Redundancy Eliminated Dissemination (REDD) [11] and Bandwidth efficient Heterogeneity aware Cluster based Data Aggregation (BHCDA) [27] are used to eliminate the redundancy in the network. A tree based Delay Efficient Data distributed Aggregation (DEDA) [26] is used to reduce the delay in the aggregated node. To maintain the accuracy and reliability in the network Energy Efficient Reliable Data Aggregation Technique (EERDAT) [28] is used which changes the size of cluster.
Table 3. Comparative study of various Data Aggregation Approaches
|
Algorithm |
Approach |
Delay |
Redundancy |
Accuracy |
Energy Consumption |
Traffic load |
|
DBST |
Tree Based |
Moderate |
Less |
Moderate |
Less |
Less |
|
SDRE |
Tree Based |
Less |
Less |
High |
Less |
Moderate |
|
REDD |
Cluster Based |
Less |
Less |
Moderate |
Less |
Moderate |
|
BHCDA |
Cluster Based |
Moderate |
Less |
Less |
Less |
Less |
|
DEDA |
Tree Based |
Less |
Moderate |
Moderate |
Moderate |
Moderate |
|
EERDAT |
Cluster Based |
Less |
Moderate |
High |
Less |
Moderate |
-
VI. Advantages and Limitations of Data Aggregation Models
The advantages of data aggregation process in wireless sensor network are described as follows:
-
4- Enhance the robustness and accuracy of information which is obtained by entire network.
-
-I - Data aggregation reduces the redundant information by adopting fusion processing mechanism.
-
4- It also reduces the traffic load and conserves energy of the sensors.
The limitations of data aggregation process in wireless sensor network are described as follows:
-
4- The cluster head or aggregator node may be attacked by malicious attacker during the transmission of fused data to the base station.
-
4- In case, if a cluster head is compromised then the base station (sink) cannot be ensuring the correctness of the aggregated data that has been send to it.
-
4- Several copies of the aggregate result may be sent to the base station (sink) by uncompromised nodes which increase the power consumption at these nodes.
-
VII. Conclusion
In order to overcome the limitations faced by the wireless sensor networks such as battery lifetime, data redundancy, energy consumption and efficiency of network, the method of fusing the data known as data aggregation is introduced. In data aggregation, the data sensed by the various nodes are get aggregated and sent to the base station as a single data packet. This paper addresses a comparative review on various data aggregation methods along with the challenges and issues involved in the network. The existing secure data aggregation schemes are classified on the basis of multiple and single aggregators. The multiple aggregator schemes are used for large network size whereas single aggregator scheme is used for small networks (where base is only the aggregator). The design of single aggregator is very easy compare to the multiple aggregator models. However, the security to most of the data fusion schemes is provided by using message authentication code. In addition to this it also use public keys and symmetric to achieve end to end or hop by hop encryptions.
Список литературы Comprehensive study of data aggregation models, challenges and security issues in wireless sensor networks
- M Yang, “Constructing Energy Efficient Data Aggregation Trees based on Information Entropy in Wireless Sensor Networks”, IEEE International Conference on Advanced Information Technology, Electronic and Automation Control, pp. 527-531, 2015.
- M Frej and K Elleithy, “Secure Data Aggregation Model in Wireless Sensor Networks”, IEEE International Conference on Machine Learning and Applications, pp. 332-334, 2015.
- M Bagaa, Younis and Balasingham, “Data aggregation tree construction strategies for increasing network lifetime in EH-WSN”, IEEE International Conference on Global Communications, pp.1-6, 2015.
- Sran, Kaur, Gurujeet and Sidhu, “Energy Aware chain Based Data Aggregation Scheme for Wireless Sensor network”, IEEE International Conference on Energy Systems and Applications, pp. 113-117, 2016.
- Fen Zhou, Z Chen, Song Guo and Jie Li, “Maximizing Lifetime of Data-Gathering Trees with Different Aggregation Modes in WSNs”, IEEE International Conference on Global Communications, pp. 1-6, 2015.
- Yunhe Li, Zhihua Yang, Bo Li, Qinyu Zhang, “Balanced Data Aggregation Method for WSN based on Compressed Network Coding”, IEEE International Conference on Advanced Information Management, Communications, Electronic and Automation Control, pp. 940-944, 2016.
- Camilo Lozoya, Mendoza, Torres and Miguel Grado, “Experimental Evaluation of Data Aggregation Methods Applied to Soil Moisture Measurement”, IEEE International Conference on Sensors, pp. 134-137, 2014.
- M Kamarei, M Hajimohammadi, A Patooghy and M Fazeli, “OLDA An Efficient On-Line Data Aggregation Method for Wireless Sensor Networks”, IEEE International Conference on Broadband, Wireless Computing, Communication and Application, pp. 49-53, 2013.
- Yunhe Li, Zhihua Yang and Qinyu Zhang, “Efficient Load Balance Data Aggregation methods for WSN based on Compressive Network Coding”, IEEE International Conference on Electronic Information and Communication Technology, pp. 111-115, 2016.
- Arora and T P Sharma, “In-network aggregation techniques and data management in wireless sensor networks”, International Journal of Advanced Computational Engineering and Networking, vol. 4, no.7, pp. 12-19, 2016.
- S Sirsikar and Samarth, “Issues of Data Aggregation Methods in Wireless Sensor Network”, Elsevier International Conference on Advances in Computing, Communication and Control, pp. 194-201, 2015.
- Ameya S B and Amol A Phatak, “Data Aggregation Techniques in Wireless Sensor Networks”, International Journal of Computer Applications, vol. 115, no. 10, pp. 21-24, 2015.
- T Wang, Ji Zhang, Yonglong Luo, K Zuo and X Ding, “An Efficient and Secure Itinerary based Data Aggregation Algorithm for WSNs”, IEEE International Conference on Big data, pp.433-440, 2017.
- M Yang, “Constructing Energy Efficient Data Aggregation Trees based on Information Entropy in Wireless Sensor Networks”, IEEE International Conference on Advanced Information Technology, Electronic and Automation Control, pp. 527-531, 2015.
- M B Frej and K Elleithy, “Secure Data Aggregation Model in Wireless Sensor Networks”, IEEE International Conference on Machine Learning and Applications, pp. 332-334, 2015.
- M Bagaa, M Younis and I Balasingham, “Data aggregation tree construction strategies for increasing network lifetime in EH-WSN”, IEEE International Conference on Global Communications, pp.1-6, 2015.
- S Sran, L Kaur, Gurujeet Kaur and S Sidhu, “Energy Aware chain Based Data Aggregation Scheme for Wireless Sensor network”, IEEE International Conference on Energy Systems and Applications, pp. 113-117, 2016.
- Fen Zhou, Z Chen, Song Guo and Jie Li, “Maximizing Lifetime of Data-Gathering Trees with Different Aggregation Modes in WSNs”, IEEE International Conference on Global Communications, pp. 1-6, 2015.
- Yunhe Li, Zhihua Yang, Bo Li, Qinyu Zhang, “Balanced Data Aggregation Method for WSN based on Compressed Network Coding”, IEEE International Conference on Advanced Information Management, Communications, Electronic and Automation Control, pp. 940-944, 2016.
- Camilo Lozoya, Gilberto Mendoza, Valentin Torres and Miguel Grado, “Experimental Evaluation of Data Aggregation Methods Applied to Soil Moisture Measurement”, IEEE International Conference on Sensors, pp. 134-137, 2014.
- M Kamarei, M Hajimohammadi, A Patooghy and M Fazeli, “OLDA An Efficient On-Line Data Aggregation Method for Wireless Sensor Networks”, IEEE International Conference on Broadband, Wireless Computing, Communication and Application, pp. 49-53, 2013.
- Yunhe Li, Zhihua Yang and Qinyu Zhang, “Efficient Load Balance Data Aggregation methods for WSN based on Compressive Network Coding”, IEEE International Conference on Electronic Information and Communication Technology, pp. 111-115, 2016.
- Arora and T P Sharma, “In-network aggregation techniques and data management in wireless sensor networks”, International Journal of Advanced Computational Engineering and Networking, vol. 4, no.7, pp. 12-19, 2016.
- S Sirsikar and Samarth, “Issues of Data Aggregation Methods in Wireless Sensor Network”, Elsevier International Conference on Advances in Computing, Communication and Control, pp. 194-201, 2015.
- Ameya and Amol Phatak, “Data Aggregation Techniques in Wireless Sensor Networks”, International Journal of Computer Applications, vol. 115, no. 10, pp. 21-24, 2015.
- T Wang, Ji Zhang, Yonglong Luo, K Zuo and X Ding, “An Efficient and Secure Itinerary based Data Aggregation Algorithm for WSNs”, IEEE International Conference on Big data, pp.433-440, 2017.
- Limin Shen, Jainfeng Ma, Ximeng Liu, Fushan Wei and Meixia Miao, “A Secure and Efficient ID-based Aggregate Signature Scheme for Wireless Sensor Networks”, IEEE International Journal on Internet of Things, vol. 4, no. 2, pp. 546-554, 2017.
- Ivan P, H Kalutarage, Yan Huang and Paul Miller, “A Fuzzy Multi-criteria Aggregation Method for Data Analytics: application to Insider Threat Monitoring” IEEE International conference on soft computing and intelligent systems, pp. 27-30, 2017.
- Yao-Yu, Tong Lin, Tan N guyen, Shao Chu, Bing Liu and Van Pham, “A new Overlap Circle Technique for reducing Data Aggregation time in Wireless Sensor Networks”, IEEE International Conference on System Science and Engineering, pp. 546-549, 2017.
- B Karthikeyan, R Kumar and Srinivasa Rao, “Energy Efficient Data compression and Aggregation Technique for Wireless sensor Networks”, IEEE International Conference on next generation electronic technologies, pp. 209-212, 2017.
- Haneul Ko, J Lee and S Pack, “Consistency Guaranteed and Energy Efficient Sleep Scheduling Algorithm with Data Aggregation for IOT”, IEEE International Conference on Wireless Communication, pp. 1-5, 2017.
- Youssef and R Yadav, “Survey on Several Secure Data Aggregation Schemes in WSN”, International Journal of Current Engineering and Technology, vol.6, no.4, pp.1154-1159, 2016.
- Akyildiz, W Su, Sankarasubraman and Cayirci, “A Survey on Sensor Networks,” IEEE Communications Magazine, vol. 40, no. 8, pp. 102-114, 2002.
- Kiran Maraiya, Kamal Kant and Nitin Gupta “Architectural Based Data Aggregation Techniques in Wireless Sensor Network: A Comparative Study”, International Journal on Computer Science and Engineering, vol. 3, no. 3, 2011.
- V Pandey, A Kaur and N Chand, “A review on data aggregation techniques in wireless sensor network”, International Journal of Electronic and Electrical Engineering, vol. 1, no. 2, 2010.
- Sumit C, Neha Singh, A Pathak and A K Vatsa, “Energy Efficient Techniques for Data aggregation and collection in WSN”, International Journal of Computer Science, Engineering and Applications, vol. 2, no. 4, 2012.
- Wen Liao and Hung Yang, “Energy-efficient Data Storage Scheme in Wireless Sensor Networks”, IEEE International Conference Network Operations and Management Symposium, pp. 478-481, 2012.
- Guorui Li and Ying Wang, “Efficient Data aggregation scheme leveraging time series prediction in WSN”, International Journal of Machine learning and Computing, vol. 1, no. 4. pp. 372-377, 2011.
- Prakash Patil and U Kulkarni, “SVM based Data Redundancy elimination for Data Aggregation in Wireless Sensor Networks”, IEEE International Conference on Advances in Computing, Communications and Informatics, pp. 1-6, 2013.
- D Mantri, Neeli R P and Ram Prasad, “Bandwidth Efficient Heterogeneity aware Cluster based Data Aggregation in Wireless Sensor Networks”, Springer International Journal on Wireless Personal Communications, vol. 76, no. 3, pp. 335-349, 2014.
- Basavaraj S M and S R Patil, “Energy Efficient Reliable Data Aggregation Technique for Wireless Sensor Networks”, IEEE International Conference on Advanced Communication Control and Computing Technologies, pp. 246-250, 2016.
- Sahana S and Amrutha R, “Data Aggregation In Wireless Sensor Networks”, Book on Data Aggregation in Wireless Sensor Networks, pp. 1-6, 2014.
- Bharuka K and Jinwala, “A Secured Data Aggregation Protocol for outlier detection in Wireless Sensor Networks using Aggregate message authentication code”, Book on Secured Data Aggregation Protocol in Wireless Sensor Networks, pp. 1-6, 2014.
- M. Dagar and S Mahajan, “Data Aggregation in Wireless Sensor Network: A Survey”, International Journal of Information and Computation Technology, vol. 3, no. 3, pp. 167-174, 2013.
- Rajashri Khannai, Salma S and Dattaprasad T, “Performance Analysis of Underwater Acoustic Communication using IDMA- OFCM- MIMO with Reed Solomon and Turbo Codes”, International Journal Computer Network and Information Security, pp 41-46, 2018.


