Energy Management and Network Traffic Avoidance Using GAODM and E-AODV Protocols in Mobile Ad-Hoc Network
Автор: Ramesh Vatambeti, Nrusingha Charan Pradhan, E. Sandhya, Surendra Reddy Vinta, V. Anbarasu, K. Venkateswara Rao
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 3 vol.15, 2023 года.
Бесплатный доступ
Because of the mobility of its nodes, MANET plays a significant role in mobile communication. As a result, network infrastructure is frequently changed, resulting in data loss and communication overheads. Despite this, the large packet size causes network congestion or traffic. The difficult task is efficient routing through a dynamic network. For node generation and energy management, the proposed approach in this paper employs GAODM (Geography-based Ad-hoc On Demand disjoint multipath) and E-AODM (Energy Ad-hoc On Demand Vector routing). The proposed GAODM routing protocol reduces congestion using Spider Monkey (SM) Optimization. The E- AODM protocol assesses the energy management solution based on parameters such as delay, energy consumption, routing overhead, and node energy. By choosing the best path through the network, the proposed protocol's effectiveness is increased. The proposed protocol reduces routing overload, delay, and congestion. The simulated results show that increasing the number of packets transmitted in the network using the proposed GAODM and E-AODM routing protocols over the existing protocols on NS 2 reduces node energy and, as a result, overload and delay.
MANET, GAODM, Intermediate Node, Congestion, Energy Consumption, Network Traffic
Короткий адрес: https://sciup.org/15018625
IDR: 15018625 | DOI: 10.5815/ijcnis.2023.03.06
Текст научной статьи Energy Management and Network Traffic Avoidance Using GAODM and E-AODV Protocols in Mobile Ad-Hoc Network
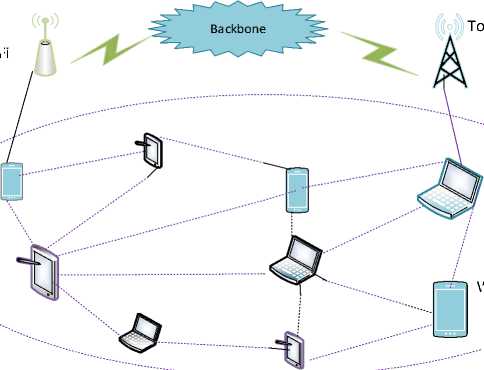
Ad hoc wireless moving networks are another name for mobile ad-hoc networks [1]. A MANET's node arrangement is irregular because it is naturally self-forming [2]. Because each node in a MANET moves randomly in all directions, it can change the link to other devices or nodes [3]. Different challenges exist in MANET to satisfy efficient communication [4]. They are as follows: energy consumption, MANET congestion, and fault tolerance (FT). Because node operation is based on battery power and a limited number of resources, energy assumption or consumption is a significant challenge in MANET [5]. MANET must be set up in rural or remote areas [6,7]. Because there is no way to replace the batteries in these areas [8,] the only way to avoid battery replacement is to keep the energy level at nodes low [9]. Fig.1 shows a representation diagram for the fundamentals of MANET.
Wi-Fi
Backbone
Wireless Ad hoc network
-
Fig.1. Fundamental of MANET
To extend the life of nodes by using less energy [10], and this low energy usage must avoid causing energy dissipation problems [11, 12]. The proper routing and maintenance of data is another challenge in MANET. MANET networks can operate independently or as part of a larger network [13]. There are multiple or single transceivers between the nodes, making the network highly dynamic and autonomous [14]. MANET is a type of WANET, and its current environment includes a routing network on the upper link layer of an ad hoc network [15]. MANETs are typically movable, self-forming peer-to-peer [16] and self-healing structures [17-19]. MANET communication requires radio frequencies ranging from 30 MHz to 5 GHz [20]. When the network's accessible load exceeds the permitted resource capacity, network congestion occurs [21], which can significantly reduce network throughput and lead to network collapse [22-24]. MANET makes use of shared resources as well as multiple senders competing for connection bandwidth [25-26]. As a result, the multipath protocol must manage the sender's data rate in order to keep the network from becoming overloaded [27-28]. This protocol's fault-tolerance (FT) will improve system reliability. It is classified into the following types:
-
• Caused by Node Failures
-
• Caused by Network Failure and Link failure
-
• Caused by the Transmission power and Energy
-
• Caused by message logging, check-pointing, reducing overload, etc.
The presence of faulty nodes in the system has an impact on the PDR. The goal of developing a fault-tolerant algorithm is to provide certain PDR guarantees even when there are faulty nodes in the network.
Key contribution related to this research is elaborated below:
• Develop the network layer with the use of GAODM_E-AODV protocol
• Initially Investigate all nodes through Knowledge based algorithm
• Determine the Energy of each node
• Calculate the node strength
• Construct the SMO
• Predict the node energy and find the optimal route for data transfer to avoid congestion.
• If there is any less energy node or the node became fault during the process then SMO can replace the node to another place. Renew the energy of each node while moving
2. Related Works
The organization of this paper is as follows. Section 2 describes the related work. Section 3 elaborates the system model and problem statement. Section 4 describes the proposed methodology and algorithm Section 5 explains results and discussion and conclusion detailed in section 6.
As a result of the frequent increase in IoT devices, a large number of messages have been transmitted, causing network congestion, which results in transmission delay and data loss. Nousheen Akhtar et al [30] developed a bandwidth (BW) aware routing system to eliminate congestion when large packets are transmitted to address this issue. Prior to transmission, this is accomplished by monitoring the available queue and residual bandwidth.
The network structure is frequently changed due to the random mobility of nodes. The data is transmitted directly via the nodes with the highest energy level. When the intermediate node selection period is reached, however, the route retrieval mechanism experiences increased routing overload. To address this, Harold et al [31] proposed the FD-AOMDV, which accelerates the path retrieval phase.
The occurrence of a fault in the network causes data loss and communication overhead in MANET. As a result, routing through the faultless node is a better solution in this case. Gnana Prakasi and Varalakshmi [32] explained a decision tree-based routing protocol in this paper. It predicts performance parameters such as Link Expiration Time, speed, node lifetime, and trip_ time in this protocol.
An ad hoc wireless network is formed with no use of any central or base nodes. Siva kumar and subair [33] proposed the Flooding based protocol for efficient routing. This protocol is used to predict the destination node, route and energy level of nodes via requesting messages. Following receiving a route response data from an end node to a source node, now it initialized as a cluster for transmission of a data in the direction of a destination.
Varalakshmi et al. [34] proposed a scheme for selecting highly trusted nodes to send data to the destination. The node in the network is first checked for its identity (normal or not) using the bottom-up parser approach, and its trust level is checked using shift-reduce operations. The method uses energy and the node's trust value as parameters to determine the detection ratio. The work is simulated in NS-2 to demonstrate its effectiveness.
3. System Model
The nodes in the MANET are movable, adaptable, and self-organizing. Every node in the network consumes some energy, but the amount varies due to node movement. Because of this, there is less usage of energy via the node, which may be reduced or increased, resulting in a data drop. If data drops arise, the lost data cannot be recovered again. Congestion occurs during transmission because a large number of nodes are interconnected in the MANET. To address all of these issues, energy-efficient multipath routing will be implemented. This category of routing is to monitor and predict the node strength of all nodes on a regular basis. Prior to data transmission, this protocol checks the battery level of each node, and if the node strength is low or faulty, it sends the route request to neighboring nodes and receives the reply beacons. The protocol then sends data to the destination via energy-efficient nodes. Multiple data streams sent through the same route cause network congestion, which this multipath routing technique also avoids. Fig.2. depicts the system model for an energy-efficient routing protocol in a MANET.
4. Proposed Methodology
To manage and evaluate energy, this study developed the GAODM and E AODV multipath routing algorithms. We can use a knowledge-based rule to calculate the energy level of all nodes. Simultaneously, the design of the SMO approach is to foresee the best route and collect data about node energy in fig.3 in order to make the data transfer in the most efficient way possible without causing congestion. If any of the nodes' energy is depleted or a fault occurs during the process, SMO can move the node to another location, acting as a fault tolerant mechanism. Finally, the data must be transferred in an optimal manner, without interruption or overload, in order to maintain network traffic and improve energy management.
-
4.1. GAODM
-
4.2. E- AODV Routing Protocol
Congestion will occur due to the large size of transmitted data. GAODM was created to address this issue. This technique was used in this research paper to alleviate network congestion. The nodes in the network communicate their own and neighboring node positions to the destination node. When there is congestion, this protocol finds and establishes the disjoint path. If the current node encounters congestion, it requests an alternate path from the next Hop ID. When the sender node wishes to send data to the receiver node, the source node calculates the Euclidian distance between the nearest node and the destination. The position and ID of the nearest nodes are stored in the next hop ID by each node, which is a unique feature of this protocol. When the Euclidian distance is calculated, the node selects the shortest path.
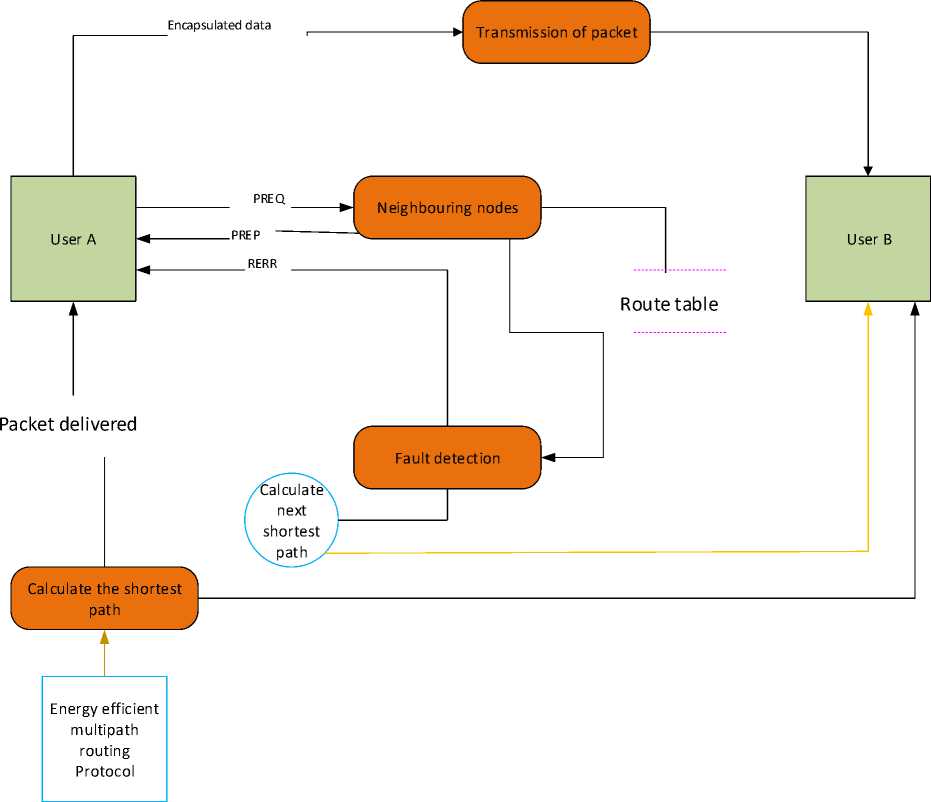
Fig.2. MANET system model for an energy-efficient routing protocol
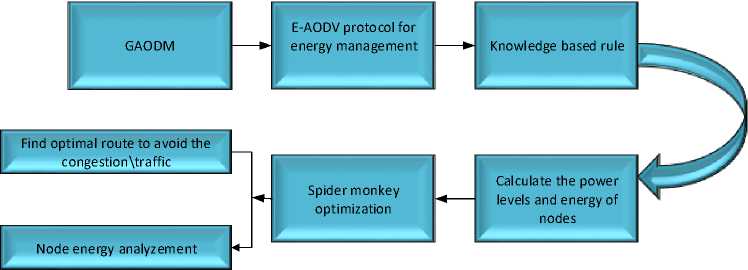
Fig.3. Proposed Methodology
Before transmission, the node sends a request message to the nearest node for the new path. As a result, because the route request contains all of the details about the sender node, it renews the status in the routing table. The route reply is then sent to the source node by the nearest node. The path should be chosen based on the response message. There is no energy management in the GAODM algorithm, which reduces battery lifetime. To avoid this, an energy-based AODV protocol is being developed in collaboration with GAODM. Only GAODM is used to create nodes, and the E-AODV protocol is used to manage the node's energy. The routing protocol's operating principle is based on E-AODV, and the node is created by GAODM.
All mobile nodes in the MANET are driven by batteries, which have inadequate energy resources. If the node consumes a large amount of energy, the energy in the node quickly depletes, causing the mobility devices to be turned off and disconnected from the network. As a result, energy consumption in the AODV protocol is a critical challenge, and this paper presents the E-AODV protocol for energy management. When a transmission node wants to send data to a receiver node, it first searches the routing table for the best route. If an optimal route exists, the data must be transmitted along that path. If the best route does not exist, it starts the route detection process by sending the route request to the nodes closest to it. The route request includes the source and destination IP addresses, as well as the sequence number and node strength. The energy efficient nodes can only participate in the route discovery task in this protocol, which increases the nodes' activation time. The energy assumed by the node Z x can be calculated using eqn. (1)
E(Z x ) E x Cu zx ,a) + E x (u zx ) + E o (u z x')
Where, u zx is represented as the energy consumption of transmitting and receiving node, E0 is represented as the coefficient of free space energy consumption and E x is denoted as the coefficient of multipath fading energy consumption.
The equilibrium distance ‘a’ is calculated in eqn. (2) using the formula a = 10
г |л-в| 10V
The nodes' energy level is then determined using the fuzzy knowledge-based rule. This is used to determine the best network path. In this case, the node's status is determined by its threshold energy value. Because data should only be transmitted via the strongest nodes. To improve node selection, this paper employs a fuzzy knowledge-based algorithm in conjunction with E-AODV.
Fuzzy knowledge-based rule :
If energy>threshold value
Then, the node is the strongest
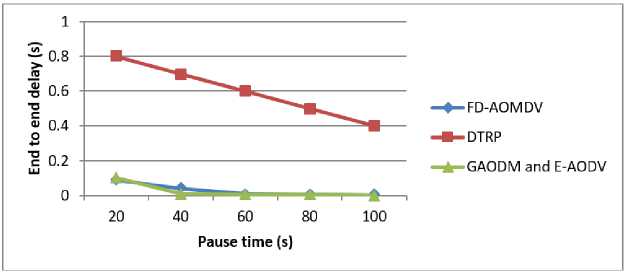
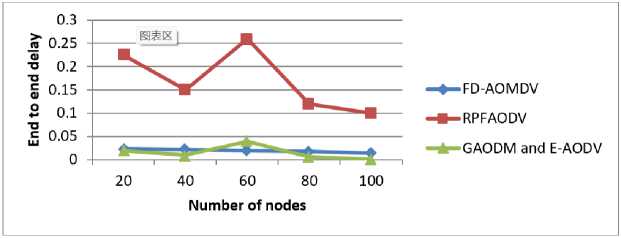
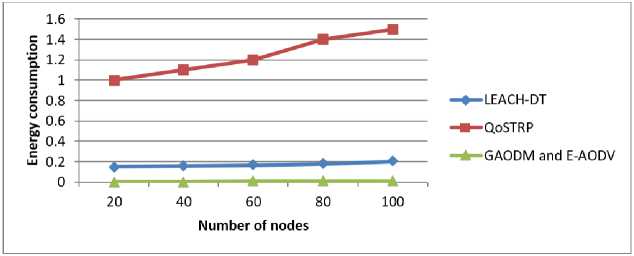
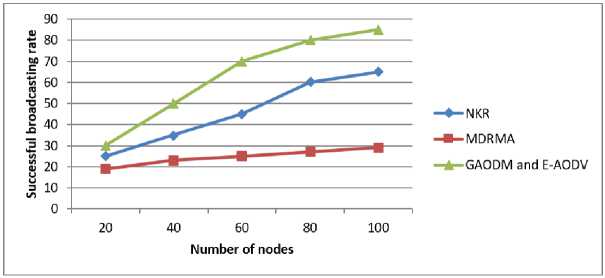
If energy Then, the node is weakest Following that, if any node has enough energy, the energy is added to the transmitting data as well. Furthermore, the energy-added data is broadcasted to the next neighboring node, and so on until the message reaches its destination. When the intermediary node receives the request message, it responds to the specific source node. Then it records and saves the history of neighboring nodes in the routing information table, which also includes the node's energy. This recorded data is then used to construct the reverse path of the reply data. If the response beacon runs out of time, it discards the data. If any of the nodes in the path do not have enough energy, the node disconnects from the network and initiates route maintenance by sending the link failure message. The algorithm reinitializes the path discovery mechanism after receiving an alert message. The forwarding node also maintains the reverse-path with the transmitter node. This is required to send the route's reply beacon to the corresponding source node. As a result, no client can communicate directly. The energy of nodes varies from time to time due to their mobility or moving nature. The multipath protocol is dependent on signal strength. High signal strength nodes are chosen for optimal routing. SMO is used to improve this. It renews the energy on a regular basis in this optimization and predicts the best route in the multipath protocol. This method will avoid congestion and ensure that high energy nodes are properly selected. 4.3. Spider Monkey (SM) Optimization The SM optimization algorithm is a highly effective and prevailing algorithm. This algorithm's implementation is simple, and it produces better results. This algorithm generates the best possible solution for the predicted one. SMO is dependent on the collective activities of SMs, and the fission-fusion system is used for spider monkey social relationships. Spider monkeys are found in groups of 50. SMs divided into small foraging groups to look for food. Each group of monkeys is looking for food on its own. Each group is led by a female SM who is only responsible for obtaining food resources. If the leader is unable to obtain the food, the leader divides the entire group into small groups, and each member of the group forages separately. The small subgroups are not permanent and may change throughout the day. However, the group must have a minimum of three members at all times. When the two groups of spider monkeys get closer, the male monkey makes a barking and calling sound. In the SMO, there are seven major steps. They are explained below. A. Population Initialization At first, In SMO n number of SMs generated an equally distributed primary population. The initialization of each SMj*as pursues in Eqn. (3), SMi*i* = SMMlnj. + (7(0,1) x (SMMaxj*-SMMlnj.) Where, SMi* (i* = 1,2,.....n) (nodes) denotes i*thSM in the population d-aspects vector, SMMinj< and SMMaxpare the limits of SM,*in they* direction and U(0,1) the similarly dispersed random number in the sort [0, 1]. B. Local Leader Phase The SM changes its location in this case based on information provided by the local leader. The new location is calculated after obtaining the fitness value. The expression for perturbation rate (pr) is expressed in Eqn. (4) PTiter* + 1 = Palter* + (—) Here, pTiter* is the current iteration value of pr and Tnl*is the total count of iterations. If the new location's fitness value is greater than the old location's fitness value, the SM replaces her old location with the new one. The fitness function is used to compare the new and current locations, resulting in greedy selection. The SM new renew equation is given in Eqn. (5), SM,^ = SM^* + U(0,1) x (LLk*r - SM^*) + U(-1,1) x (SMr.r - SMt«j«) (5) Where, SMi*;-*is the j*h aspect of the i*h SM, L'Lk*j* is the j*h aspect of the k*h local group leader location, SMr*,* is the j*h aspects of the k*th SM which are nominated randomly in the k*th group such that т* Ф i* and U(0,1) is the correspondingly disseminated random number in the sort [0, 1]. C. Global Leader Phase After the LLP, GLP begins which is based on a GL and experience of local group members is mentioned in Eq. (6) SMUewt*r= SMi*r + U(0,1) x (GLr- SM^*) + U(-1,1) x (SMr*,* - SMt«p) (6) Here, GL,* be the j*h location of a global leader andj*th £ {1,2.....d) is randomly selected catalog. Based on the probability (routing probability), the locations are changed by Eq. (7), ртЬ1* = 0.9 x fitness;* „ --+ 0.1 Max_fitness Where, fitness^ is the i*th fitness value of SM and Max- fitness is the maximum fitness of an entire group. The fitness of the next location SM is then estimated and compared to the previous location. Finally, the best location is selected from among those. D. GL Learning Phase In this case, greedy selection is used to renew the global leader's location, assisting in selecting the optimal output for all steps. This gives the selected population the location of the current SM has an optimal value and is marked as the GL's new best position. As a result, whether the GL location is renewed or not, the global Limit Count threshold increases by one. E. LL Learning Phase The location of the LL has been renewed in the same manner as the GLL phase. Then, compare the current location of the LL with the previous location to renew the location of a local leader. If the LL's position is not renewed, the local limit count is increased by one. F. LL Decision Phase The decision is made after the LL learning phase by updating the location of LL. If the local leader fails to renew the augmented count value, the entire group can rearrange their position by random initialization of an LL and GL which is mentioned in Eq. (8) ESMnew.** = Esm^j* + U(0,1) x (GLr- ESm.*.*) + U(0,1) x (ESm.*.* - ЬЁк*5*) (8) G. GL Decision Phase If the GL does not update their augmented count value after the learning phase, the total population is partitioned into a few small groups. Fig.4. Flowchart for proposed SMO H. Algorithm for Smo 1. Begin with population (nodes), then local (distance), and finally global leader (energy). 2. Estimate goodness (energy and distance between two nodes) by eqn. (9) and eqn. (10) in eqn. (5) EsmPj. = Ex(uzx, a) + Ex(Ux) + Eo(Uzx) (9) 1^-511 a = 10[ iov ] (10) while (ESM < Threshold) do a. To find the objective (energy), create new positions (nodes) for all group members. b. Use greedy selection to choose the best node from existing positions (present node) and newly generated positions (next node) based on goodness. c. Using equation (7), estimate the routing probability probi (routing table) for all nodes. d. Generate new locations for all nodes based on probi. e. Renew the routing table based on eqn. (9) and eqn. (10), by employing greedy selection on all groups. f. If any LL (node's distance) does not renew, the search is redirected to the next node. g. If the GL (energy) is not renewed, the group (route) is divided into several groups (Multipath) 5.1. Performance Analysis end while (Congestion is avoided, and the best available node is chosen.) The NS-2 software is used to test the efficiency and effectiveness of newly developed routing protocols. The developed scheme uses a multipath routing protocol to estimate node energy and avoid congestion. Finally, the proposed techniques are compared to some recent literatures, and this Ns-2 implementation outperforms the others. With a simulation period of 100 seconds, 100 nodes are formed within a 500 m * 400 m area. Each node is set up in a random mobility model with speeds ranging from 0 to 20 m/s, a transmission range of 200m, and an initial energy of 100 J. Table.1 illustrates basic simulation parameters and their values. Table 1. Simulation parameters Parameter Value Number of nodes 100 Simulation period 100 s Network dimensions 500 m*400m Mobility type Random way point Antenna type Omni directional antenna Node speed 0–20 m/s Traffic model CBR Initial Node energy 0-100 J Pause period 0, 10, 20, 30, 40, 50 MAC protocol IEEE 802.11 The following section compares the proposed scheme to existing schemes for various parameters such as delay, network traffic, throughput, PDR, and energy consumption such as FD-AOMDV [23], NKR algorithm [26], DTRP [24], MDRMA [27], LEACH-DT [29], QoSTRP [30], and improved AOMDV algorithm [28]. A. Mobility The routing overload of the proposed E-AODV protocol was analyzed with various nodes mobility. The mobility was varied from 20 m/s to 10 m/s. Mobility is nothing but the node has an ability to move freely and randomly within the network. Fig.5 depicts the performance of mobility speed with routing overload with proposed method mobility speed. When compared to the existing methods, the proposed method achieves the lowest routing overload in this graph. The lower the routing overload value, the better the output. 1 лааа IzUUU О 1АЛЛА - — J.UUUU > 8000 “> 6000 ЛЛАЛ - -■-NKR О ос 2000 - uaudivi ana t audv 20 40 60 80 100 Mobility speed Fig.6. Pause time Vs End to end delay Fig.7. Network size Vs End_ to _end delay C. Energy Consumed in the Network Fig.8 depicts a performance comparison of energy consumption versus total number of nodes. Less energy consumption yields better results. Because nodes consume so little energy, they consume a large portion of the remaining energy. The node with the most energy in the route is chosen as the optimal route. Fig.8. Number of nodes Vs Energy consumption D. Packet Delivery Ratio Fig. 9 depicts the PDR achieved by the proposed idea. As a result, when compared to existing methodologies, the proposed tactic produces better results. Fig.9. Number of nodes Vs Successful broadcasting rate GAODM and E-AODV routing algorithms are proposed in this research paper. It sprints multipath routing with less congestion and efficiently finds the disjoint path to reduce overloads. All nodes in the routing protocol have the maximum remaining energy, which must be selected for effectual path selection. The proposed simulation reduces the delay caused by multipath disjoint protocols. The simulation results for this research show that it reduces routing overload, transmission delay, and improves PDR when compared to NKR, FD-AOMDV, DTRP, QoSTRP, and other methods implemented in Network Simulator 2. It has improved in terms of PDR, delay, and routing overload, as shown in fig. 5 to 9. The proposed method has attained 97% of PDR, 0.0003 s of end-to-end delay, 3500 of routing overhead, 98% of throughput, and 0.01% of energy consumption.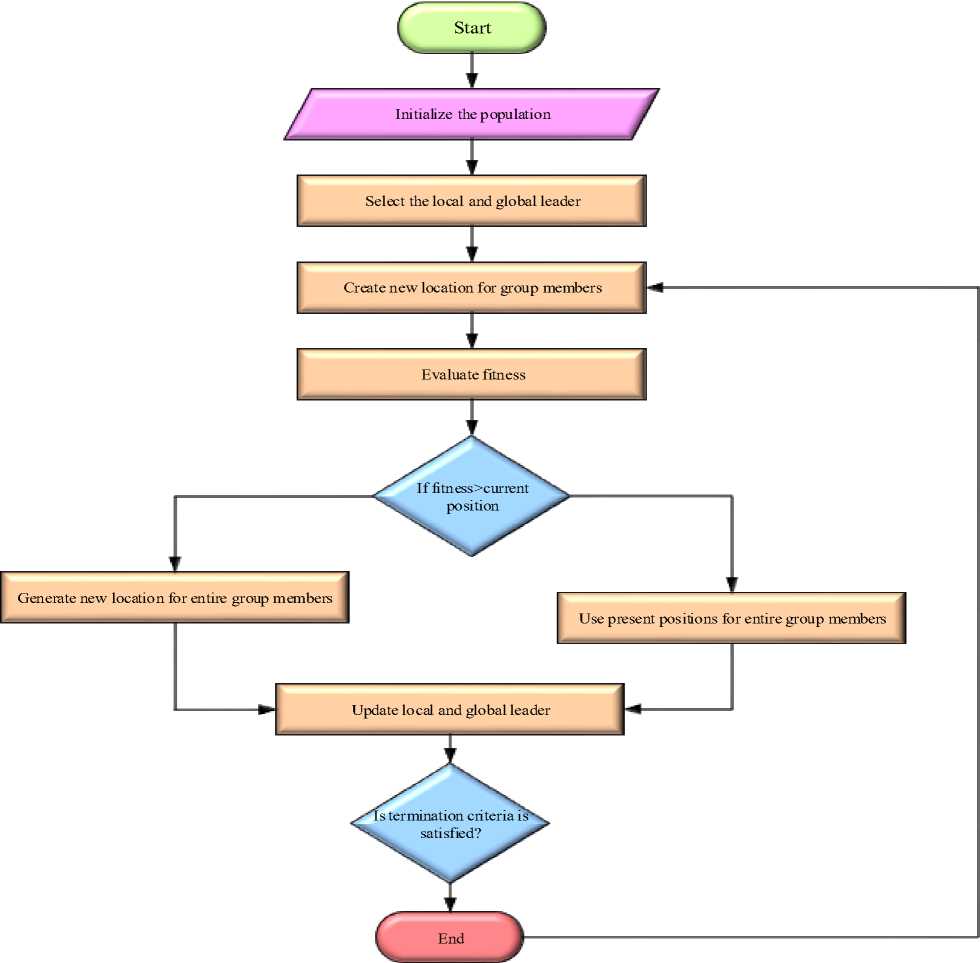
Список литературы Energy Management and Network Traffic Avoidance Using GAODM and E-AODV Protocols in Mobile Ad-Hoc Network
- Aravindhan, K., and C. Suresh Gnana Dhas. "Destination-aware context-based routing protocol with hybrid soft computing cluster algorithm for VANET." Soft Computing 23.8 (2019): 2499-2507.
- Bashir, Muhammad Nauman, and Kamaludin Mohamad Yusof. "Green Mesh Network of UAVs: A Survey of Energy Efficient Protocols across Physical, Data Link and Network Layers." 2019 4th MEC International Conference on Big Data and Smart City (ICBDSC). IEEE, 2019.
- Moreno, Jaime, et al. "Distributed Learning Fractal Algorithm for Optimizing a Centralized Control Topology of Wireless Sensor Network Based on the Hilbert Curve L-System." Sensors 19.6 (2019): 1442.
- Makhlouf, Amel Meddeb, and Mohsen Guizani. "SE-AOMDV: secure and efficient AOMDV routing protocol for vehicular communications." International Journal of Information Security (2019): 1-12.
- Shakir, Hasan Awni, Ravie Chandren Muniyandi, and Zulkarnain Md Ali. "Energy consumption in mobile AD Hoc network: Challenges and solutions." Journal of Theoretical and Applied Information Technology 97.3 (2019):755-764.
- Arulkumaran, G., and R. K. Gnanamurthy. "Fuzzy trust approach for detecting black hole attack in mobile adhoc network." Mobile Networks and Applications 24.2 (2019): 386-393.
- Chen, Bo-Wei, et al. "Self-Aware Autonomous City: From Sensing to Planning." IEEE Communications Magazine 57.4 (2019): 33-39.
- Prakash, Shiva, and Vikas Saroj. "A Review of Wireless Charging Nodes in Wireless Sensor Networks." Data Science and Big Data Analytics. Springer, Singapore, 2019. 177-188.
- Guidara, Amir, et al. "Energy-Efficient On-Demand Indoor Localization Platform based on Wireless Sensor Networks using Low Power Wake up Receiver." Ad Hoc Networks (2019): 101902.
- Mann, Palvinder Singh, and Satvir Singh. "Improved artificial bee colony metaheuristic for energy-efficient clustering in wireless sensor networks." Artificial Intelligence Review 51.3 (2019): 329-354.
- Anagnostou, Patroklos, et al. "Energy and power awareness in hardware schedulers for energy harvesting IoT SoCs." Integration 67 (2019): 33-43.
- Boddu, N., Boba, V. & Vatambeti, R. A Novel Georouting Potency based Optimum Spider Monkey Approach for avoiding Congestion in Energy Efficient Mobile Ad-hoc Network. Wireless Pers Commun (2021).
- Singh, Gurjeet, and Vijay Dhir. "Performance Analysis of Adhoc on Demand Distance Vector (AODV) and Destination Sequence Routing (DSR) protocols in Mobile Adhoc Networks (MANET)." Global Journal of Computer Science and Technology (2018).
- Zhao, Zhongliang, et al. "Software-defined unmanned aerial vehicles networking for video dissemination services." Ad Hoc Networks 83 (2019): 68-77.
- Das, Santosh Kumar, and Sachin Tripathi. "Intelligent energy-aware efficient routing for MANET." Wireless Networks (2018): 1-21.
- Parlin, Karel, et al. "Transferring the Full-Duplex Radio Technology from Wireless Networking to Defense and Security." 2018 52nd Asilomar Conference on Signals, Systems, and Computers. IEEE, 2018.
- Nosheen, Irum, Shoab A. Khan, and Fatima Khalique. "A mathematical model for cross layer protocol optimizing performance of software-defined radios in tactical networks." IEEE Access 7 (2019): 20520-20530.
- Yano, Kazuto, et al. "Achievable Throughput of Multiband Wireless LAN using Simultaneous Transmission over Multiple Primary Channels Assisted by Idle Length Prediction Based on PNN." 2019 International Conference on Artificial Intelligence in Information and Communication (ICAIIC). IEEE, 2019.
- Weston, Jeffery H., and Eric N. Koski. "Communications device serving as transmission control protocol (TCP) proxy." U.S. Patent No. 9,967,077. 8 May 2018.
- Sowmya, M. C., Shish Ahmad, and Preetam Suman. "Congestion avoidance and control mechanisms for MANET using AODV protocol: a survey." International Journal of Advanced Research in Computer Science. Special Issue 2 (2018): 19.
- Bala, Suman, Er Amandeep Singh Bhandari, and Charanjit Singh. "Securing AODV Network from Gray Hole attack by Routing Information Protocol." International Journal 4.2 (2018).
- Robinson, Y. Harold, et al. "Neighbor Knowledge-based Rebroadcast algorithm for minimizing the routing overhead in Mobile Ad-hoc Networks." Ad Hoc Networks 93 (2019): 101896.
- Darabkh, Khalid A., Mohammad G. Alfawares, and Saud Althunibat. "MDRMA: Multi-Data Rate Mobility-Aware AODV-Based Protocol for Flying Ad-hoc Networks." Vehicular Communications (2019): 100163.
- Li, Peng, Lu Guo, and Fang Wang. "A Multipath Routing Protocol with Load Balancing and Energy Constraining Based on AOMDV in Ad Hoc Network." Mobile Networks and Applications (2019): 1-10.
- Vatambeti, R., Sanshi, S. & Krishna, D.P. An efficient clustering approach for optimized path selection and route maintenance in mobile ad hoc networks. J ambient Intell Human Comput (2021). https://doi.org/10.1007/s12652-021-03298-3
- Kavidha, V., and S. Ananthakumaran. "Novel energy-efficient secure routing protocol for wireless sensor networks with Mobile sink." Peer-to-Peer Networking and Applications (2018): 1-12.
- Raja, R., and P. Ganeshkumar. "QoSTRP: A Trusted Clustering Based Routing Protocol for Mobile Ad-Hoc Networks." Programming and Computer Software 44.6 (2018): 407-416.
- R. Vatambeti, “A novel wolf-based trust accumulation approach for preventing the malicious activities in mobile ad hoc network,” Wireless Personal Communications, vol. 113, no. 4, pp. 2141–2166, 2020.
- Arumugham, Kowshika, and Vivekanandan Chenniappan. "Least Mobility High Power (LMHP) Dynamic Routing for QoS Development in Manet." Wireless Personal Communications 105.1 (2019): 355-368.
- Akhtar, Nousheen, et al. "Congestion Avoidance for Smart Devices by Caching Information in MANETS and IoT." IEEE Access (2019).
- Robinson, Y. Harold, et al. "FD-AOMDV: fault-tolerant disjoint ad-hoc on-demand multipath distance vector routing algorithm in mobile ad-hoc networks." Journal of Ambient Intelligence and Humanized Computing (2019): 1-18.
- Prakasi, OS Gnana, and P. Varalakshmi. "Decision Tree Based Routing Protocol (DTRP) for Reliable Path in MANET." Wireless Personal Communications (2019): 1-14.
- Venu, Sivakumar, and AMJ Md Zubair Rahman. "Energy and cluster based efficient routing for broadcasting in mobile ad hoc networks." Cluster Computing (2018): 1-11.
- Varalakshmi S. “Trust Computation Using Bottom-Up Parser Approach In MANET”, Information Technology In Industry, 18;9(1): pp.1236-41, Mar 2021.


