Enhanced Image Watermarking Technique using Wavelets and Interpolation
Автор: Sandeep Kaur, Himanshu Jindal
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 7 vol.9, 2017 года.
Бесплатный доступ
Image provides complete detailed information for thing or object. It is considered as an important aspect of analyzing the details of various objects or environments of real life applications. From analyzing or studying images, various techniques come into existence. These include zooming, watermarking, hazing, and compression. Each has its own advantages and disadvantages with respect to various implicit functions defined for the techniques. The research paper focuses on watermarking techniques. The techniques of watermarking have their advantages and outperforms better when combined with wavelets transformations (DWT) followed by interpolations. The wavelets and interpolations provide a good quality enhanced and zoomed watermarked images at the time of its encoding and decoding processes. The images are embedded with sample images considered as hidden information. After the extraction process image interpolation method is applied to the image to get a quality image. The process is suggested in order to view the changed pixels of images after encoding of two images. The combination of DWT watermarking and interpolation provides 52% better results when compared to existing techniques.
Watermarking, LSB (Least Significant Bit), DCT (Discrete Cosine Transform), spatial, frequency, Blind, Non-Blind, DWT (Discrete Wavelet Transform)
Короткий адрес: https://sciup.org/15014202
IDR: 15014202
Текст научной статьи Enhanced Image Watermarking Technique using Wavelets and Interpolation
Published Online July 2017 in MECS DOI: 10.5815/ijigsp.2017.07.03
An image refers to a visual perception which has the same appearance of the object. The word image is also used for two dimensional pictures like pie chart, graph and map etc. An image is formed because light passes from an object in a number of directions. There are various methods that are applied on images to view its perspective or using images for various applications. These methods are compression, zooming, dehazing, histogram equalization and image watermarking. The image compression is used to compress images for sending image faster than usual image. Zooming refers to zoom the pixel to find the unknown pixels. Dehazing is the process for removing haze/fog from images to get clear image. Image Watermarking is a strategy that encloses a secret code known as watermark in the digital image. This process is called watermark embedding process. In image watermarking, a cover image is used to hide secret image and a key is used for security purpose. Image watermark prevents data from unauthorized access, recovery and manipulation. A watermark should be confidential so that only authorized user can access or modify the information. Watermarking technique is important for fortification of images. When a person tries to access data in an illegal manner, on the basis of retrieved watermark alteration can be detected. When sharing digital data over the internet multimedia contents are exchanged, then copyright infringement issues come into the images.
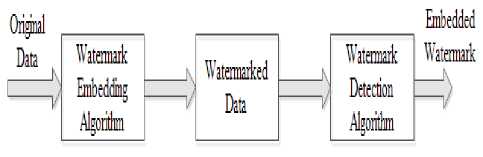
Fig.1. Stages in Image watermarking
Every algorithm of the watermarking process consists of two stages:
-
> Watermark embedding : For watermark implanting process, the sources of information are hided as watermarked and a key to guarantee the security of process.
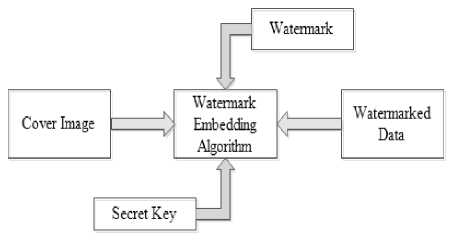
Fig.2. Watermark embedding process
> Watermarking extraction : The yield of embedding procedure that is watermarked will be the contribution of the extraction process. The kind of key relies on the sender that it is open or private. Utilizing a specific watermarking extraction method, the original information is recovered from the watermarked information.
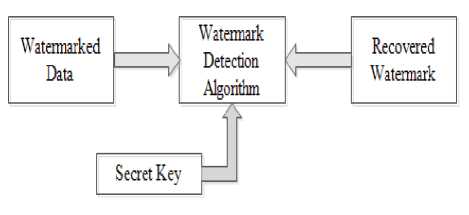
Fig.3. Watermark detection process
Various techniques used for image watermarking are discussed as under:
-
i. LSB Watermarking Technique: LSB stands for Least Significant Bit. In this process, the watermark embedding is carried out by selecting a subset of pixels. After this, the least significant bits are substituted with watermark bits. This technique is not approachable practically as the watermark can easily be obtained by an intruder. But copy control is an advantage of this technique.
-
ii. DCT based Watermarking: Discrete Cosine
Transform (DCT) strategy offers greater robustness and security in contrast to LSB watermarking. It disintegrates the image into blocks of 8x8 pixels, DCT is applied on each block, DCT co-efficient with midfrequency range are taken up and used for watermark embedding. The images are modified and finally inverse DCT is applied to recover the original data.
-
iii. Spatial domain and Frequency Domain: These are very simple strategies. In these, watermark is simply applied in the pixel domain without the application of any kind of transform. Frequency domain offers more robustness by hiding the watermark in the noisy region than in the smoother region.
-
iv. Blind and Non Blind watermarking: In blind watermarking technique, the watermark information is extracted without the original data and by just scanning the source document. In non-blind watermarking, the watermark is extracted by using the original data. The non-blind watermarking is more robust than the blind watermarking technique.
-
v. DWT based Watermarking: It is the most useful technique. It disintegrates the image into high and low frequency quadrants. Further, the low frequency quadrant is disintegrated into low and high frequency regions, which is repeated until the complete signal has been disintegrated. It is better than DCT in terms of quality of the image produced.
In digital image processing watermarking is used to develop many applications some of these are:
-
i. Copyright Protection: Digital watermark is used to identify and copyright ownership, for example a logo of any particular organization. For identification of owner a watermark can be attached to the digital data. High level of robustness is required for this process, so watermark cannot be removed by the unauthorized user. Watermark is used to control the piracy of copyrighted data when transfer over the internet.
-
ii. Finger Printing: Finger prints are the unique identity of a person. In digital watermarking, this concept is used to identify the true owner of the information. Detection of watermark from any unauthorized user describes the identification of the person who manipulated the original data.
-
iii. Broadcast Monitoring: To monitor the broadcasting of TV channels and radio news watermarking techniques are used. In commercial advertisement to check whether the advertisement is broadcasted, a digital watermark is embedded. Watermarking System gets broadcast signals and searches for watermarks to identify at what time on which channel the advertisement is broadcast.
-
iv. Medical Applications: The patient’s information embeds as watermark to remove the ambiguity in searching the medical record. The watermark can be visible or invisible depends on the embedding algorithm. In medical applications, this technique is used to identify that the reports are not edited by unauthorized persons.
-
v. Identity Card/Passport Security: In passport or ID cards, watermark is included in the form of name, profile picture and address of the person. Verification of ID card is done by extracting and comparing the watermark with written text. By including watermark in the application, it provides more security level.
In summary, the watermarking embedding and extraction process is beneficial to real world for the security purposes and hiding the information inside images to protect them from intruders. Therefore, the paper focuses on DWT based watermarking in combination with interpolation to embed and extract images. The images produced after extraction provides a good quality image. The existing methodologies for watermarking studied by few researchers are explained in the next section.
The organization of the paper is as follows. Section II discusses the related works carried out by researchers. Section III describes the preliminary studies of watermarking by DWT and interpolation. The proposed algorithm and results are discussed in Section IV. The proposed technique’s comparison is shown in Section V. Finally, Section VI draws the main conclusion.
-
II. Related Works
The image watermarking has key role for providing security to images with the form that it also develops good quality hidden images on extraction. Therefore, the images are produced using Discrete Wavelet Transform (DWT) and Discrete Cosine Transform (DCT) . These images are compared with threshold value that provides good quality image having higher threshold [12]. The authors tried to improve the quality by combining the images produced by DWT and DCT . The proposed method is quite slower. In improvement to this approach few researchers suggested nearest neighbor value interpolation technique which interpolated the known pixels to generate new pixels in its neighbors [10] [13]. The approach is quite beneficial to provide good image but fairly reduces the image’s quality. Even, few pixels get distorted or blurred with forming new pixels. As far as security of images is concerned, authors compare the watermarking methods based on DWT and DCT [8] [14]. The techniques are based on frequency and low amplitude but the images produced are cropped at corners. In improvement to this approach, frequency based embedding using DCT is suggested which considers pseudo random sequence of real numbers [3] [11]. The outcome suggests for extracted image of good quality but few pixels got distorted due to compression by DCT . To provide decompression, interpolation technique namely kriging is proposed by F. A. Jassim [4]. The produced images are more sophisticated and the approach has better results for grayscale images. Few researchers try to improve the methodology of watermarking by using images as block wise via digital signature [5]. This method is used for detecting tampered pixels and to rectify them using hash codes. In [1] [15], the authors surveyed various interpolation techniques like nearest neighbor, bilinear, bi-cubic and pixel replication and suggest that pixel replication is smoother in providing good quality zoomed images. These techniques are also used to remove the distortion from the image and make a sharper image. The researchers reviewed various watermarking methods and its application in the real world with respect to security in various domains [6] [7]. The authors in [2] introduced SVD and LSB based image watermarking technique. These are used to watermark RGB images. Moreover, the LSB provides better results than SVD as it considers each pixel by bits. In summary, there are approaches towards watermarking, interpolation to watermark an image and to extract image having full contents. Also, there are no distortion and image is of good quality. Therefore, this paper focuses on producing extracted watermarked image using DWT and interpolation. The approach is more robust and the image quality is improved. The proposed methodology is described in the next section.
-
III. Prelimanaries
Before working on the proposed approach, the various existed approaches are explained with its working in the subsections. The proposed method uses Discrete Wavelet Transform (DWT) to improve the quality of images as DWT provides functionality to decompose the image into sub-bands by virtue the user can easily correct the blurriness, noise present in images. The methodology for DWT is combined with spline interpolation in order to find the newly formed pixels after correcting images (making images free from noise, blurriness). The working of DWT and spline interpolation is explained as under.
-
A. Discrete Wavelet Transform (DWT)
In DWT , two types of filters are applied on the available frequency. These two types of filters are low pass filter and high pass filter. These filters divide the available frequency in exactly two halves. And process is applied onto each row, then to each column and collect their own frequencies from the available frequency . So, the filtering process results into two dimensional array of coefficients. This array consists of four bands low-low, high-low, low-high and high-high. Low-low band is further decompose into four bands to attain its second level decomposition. The low-low band is used for decomposition as it is easy to process. Moreover, the low-low filter has highest importance as compared to all other bands. The following figures show two level view DWT.
|
LLi |
HLi |
|
LHi |
HH1 |
Fig.4. First level decomposition of DWT
|
LLi |
HLi |
HLi |
|
LHi |
HHi |
|
|
LHi |
HHi |
|
Fig.5. Second level decomposition showing sub-bands of DWT
The DWT provides better quality images to know the unknown or newly formed pixels and for decompressing images using interpolation. Following steps shows the encoding and decoding process of DWT. Image decomposition by Discrete Wavelet Transform.

Fig.6. Output pepper image of DWT
This technique includes very low frequencies do high frequency can be easily discarded without any loss of quality. There are various interpolation techniques that include spline, linear, bi-linear, cubic, bi-cubic and nearest neighbor interpolation. Out of these, spline outperforms better and is discussed in the next subsection.
Algorithm 1: Improved Discrete Wavelet Transform
Watermarking Algorithm
-
1: start
-
2: A ^ image //host image
-
3: B ^ image // information to be stored
-
4: apply DWT (A) and DWT (B)
-
5: embed (A, B) // embedding images A and B
-
6: calculate PSNR (AB, X) // finding PSNR for watermarked
image.
-
7: Decompose ‘X’ into four sub-bands say (a1, a2, a3, a4)
using DWT with ‘haar’ wavelet
-
8: for i = 1,..,3 // differentiating R , G , B colors of each of 4
sub-bands
-
9: b[i] ^ a1(:,:,i)
-
10: c[i] ^ a2(:,:,i)
-
11: d[i] ^ a3(:,:,i)
-
12: e[i] ^ a4(:,:,i)
-
13: end for
-
14: for i =1,..,3 // interpolation applied on each sub-band
-
15: w1[i] = interpolate(b,i) //using spline
-
16: w2[i] = interpolate(c,i)
-
17: w3[i] = interpolate(d,i)
-
18: w4[i] = interpolate(e,i)
-
19: end for
-
20: for i =1,..,3
-
21: Combine the updated sub-bands into single image
using inverse DWT
-
22: end for
-
23: calculate PSNR (A, X) //finding PSNR for output and
original images
-
24: calculate size(A)
-
25: end
The postulated strategy is applied upon some well known benchmark images as shown below:
-
B. Spline Interpolation
The spline interpolation is used to approximate the unknown pixel data for a given image to enhance the size of the given image. The new points are determined with respect to some known points. The spline takes into consideration, a larger domain of pixels in order to produce better interpolation results. This technique is faster and provides zoomed images of better quality.
-
IV. Proposed Algorithm and Experimental Results
The image watermarking technique has been proposed using DWT . The DWT watermarking technique interpolates images with simple and easy methodology. It constructs a multi resolution representation of images. DWT split image into different quadrants range from high frequency to low frequency. The proposed methodology has been applied upon images and their PSNR values have been calculated. The algorithm for the process is explained as under:

(a)

(b)

(c)

(d)

(e)

(f)

(g)

(h)

(i)

(j)

(k)

(l)
Fig.7. Watermark input images (a) Kids (b) Airplane (c) Baboon (d) Flower (e) Lena (f) Pears (g) Peppers (h) Fruit (i) Tree (j) Boat (k) Baby (l) Football
These sample images are used as hidden information/ images. The images are watermarked using DWT watermarking and a host or cover image is selected under which the above watermarked images are hidden. The cover images are shown in Figure 8.

(a)

(b)
Fig.8. Cover images (a) Children (b) Kitten
Using the DWT watermarking technique, the input images are embedded into the cover images and the PSNR values for these embedded images is calculated as shown in Table 1 and the embedded output images are shown in Figure 9.
Table 1. PSNR value of images after embedding using DWT
|
S. No |
Backend Images |
Image Size |
PSNR ( d B) |
|
1 |
Kids |
111 KB |
15.4620 |
|
2 |
Airplane |
88 KB |
16.4493 |
|
3 |
Baboon |
114 KB |
16.5350 |
|
4 |
Flower |
52 KB |
13.7064 |
|
5 |
Lena |
101 KB |
15.3106 |
|
6 |
Pears |
103 KB |
16.4391 |
|
7 |
Peppers |
68 KB |
14.7837 |
|
8 |
Fruit |
106 KB |
14.9215 |
|
9 |
Tree |
98 KB |
13.6269 |
|
10 |
Boat |
81 KB |
12.7172 |
|
11 |
Baby |
60 KB |
18.9339 |
|
12 |
Football |
77 KB |
12.7230 |

(a)

(b)

(f)

(c)

(g)


(h)

(e)

(i)

(j)

(k)

(l)
Fig.9. Embedded Images (a) Kids (b) Airplane (c) Baboon (d) Flower (e) Lena (f) Pears (g) Peppers (h) Fruit (i) Tree (j) Boat (k) Baby (l)
Football
Table 2. PSNR values of images after extraction
|
S. No |
Extracted Images |
Image Size |
PSNR ( d B) |
|
1 |
Kids |
59 KB |
29.4454 |
|
2 |
Airplane |
53 KB |
25.6327 |
|
3 |
Baboon |
71 KB |
28.4237 |
|
4 |
Flower |
39 KB |
33.8150 |
|
5 |
Lena |
51 KB |
32.3233 |
|
6 |
Pears |
56 KB |
29.6019 |
|
7 |
Peppers |
43 KB |
29.5121 |
|
8 |
Fruit |
46 KB |
30.2201 |
|
9 |
Tree |
48 KB |
27.4855 |
|
10 |
Boat |
40 KB |
21.9217 |
|
11 |
Baby |
38 KB |
25.3304 |
|
12 |
Football |
39 KB |
36.0528 |
After the embedding process is complete, the original images are extracted by applying DWT and again the PSNR values and the sizes of the extracted images are recorded as shown in Table 2 which indicates a little bit decrease in the image size and the extracted images are shown in Figure 10.

(a)

(b)

(c)

(e)

(f)

(i)

(j)

(g)

(h)

(k)

(l)
Fig.10. Extracted Images (a) Kids (b) Airplane (c) Baboon (d) Flower (e) Lena (e) Lena (f) Pears (g) Peppers (h) Fruit (i) Tree (j) Boat (k) Baby (l) Football
After the extraction process is over, the extracted images are zoomed by applying the combination of DWT along with spline interpolation in order to get good quality images. Then, PSNR values are calculated for zoomed extracted images as shown in Table 3 and the zoomed images are shown in Figure 11.
Table 3. PSNR values of extracted images after applying interpolation
|
S. No |
Zoomed Images |
Image Size |
PSNR ( d B) |
|
1 |
Kids |
164 KB |
75.8826 |
|
2 |
Airplane |
144 KB |
70.8692 |
|
3 |
Baboon |
144 KB |
67.7574 |
|
4 |
Flower |
97 KB |
80.9368 |
|
5 |
Lena |
137 KB |
74.0650 |
|
6 |
Pears |
132 KB |
74.8824 |
|
7 |
Peppers |
110 KB |
76.5470 |
|
8 |
Fruit |
155 KB |
71.8532 |
|
9 |
Tree |
104 KB |
69.0631 |
|
10 |
Boat |
103 KB |
77.5116 |
|
11 |
Baby |
88 KB |
75.4988 |
|
12 |
Football |
101 KB |
77.3693 |

(d)

(a)

(e)

(b)

(f)

(c)

(g)

(h)

(i)

(j)

(k)

(l)
Fig.11. Extracted Zoomed Images after applying interpolation (a) Kids (b) Airplane (c) Baboon (d) Flower (e) Lena (f) Pears (g) Peppers (h) Fruit (i) Tree (j) Boat (k) Baby (l) Football
-
V. Comparison with Existing Techniques
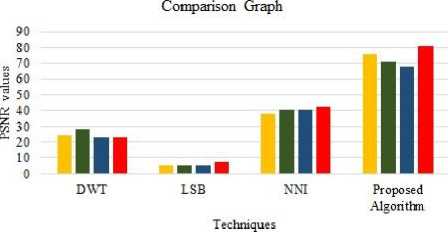
It is important to study about the existing techniques and then compare the results of the proposed algorithm with the existing algorithms to check the improved output. The PSNR value of the four images is taken from different algorithms and is compared with the proposed algorithm. The proposed algorithm gives better PSNR values as shown in the Table 4 and Figure 12.
Table 4. Comparison of PSNR values of proposed algorithm with existing algorithms
|
Images Techniques |
Kids |
Airplane |
Baboon |
Flower |
|
DWT |
24.5815 |
28.3717 |
23.2008 |
22.7428 |
|
LSB |
5.5329 |
5.4591 |
5.3279 |
7.7171 |
|
NNZ |
37.9295 |
40.4585 |
40.8771 |
42.3827 |
|
Proposed Algorithm |
75.8826 |
70.8692 |
67.7574 |
80.9368 |
Kids ■ Airplane ■ Baboon ■Flower
Fig.12. Comparison graph
This Table 4 describes different values of images on which different techniques had been applied by various developers. PSNR values are recorded parallel to the proposed algorithm for different images. The calculated overall result difference is more than 52% as an average of all values when it is compared with other values. The comparison graph shows the difference of output between proposed algorithm and existing algorithms. It is identified among the existing techniques and operations that the PSNR values are low as compared to the proposed algorithm that has been carried out in this paper. Thus, usage of DWT enhances the image quality.
Table 5. Comparison of proposed method with existing researches
|
Images Techniques |
Lena |
Pepper |
Airplane |
Baboon |
|
Zhang et al. (2009) [6] |
33.6223 |
31.7465 |
30.4934 |
32.4623 |
|
Jiansheng et al. (2009) [8] |
31.5003 |
32.0763 |
35.5801 |
33.3359 |
|
Jiechao et al. (2010) [17] |
33.9879 |
34.3757 |
32.2515 |
30.3891 |
|
Lin et al. (2012) [16] |
32.2454 |
32.6584 |
35.3798 |
30.5001 |
|
Chaturvedi and Basha (2012) [11] |
52.4298 |
51.4669 |
58.3925 |
50.4330 |
|
Pal and Chandra (2013) [9] |
39.6754 |
40.5447 |
34.7876 |
35.4231 |
|
Tonge et al. (2014) [10] |
42.7281 |
47.8144 |
43.3626 |
46.0149 |
|
Proposed Algorithm |
74.0650 |
76.5470 |
70.8692 |
67.7574 |
To distinguish that the proposed method is superior with the existing approaches suggested by researchers, another comparison is made with them. It is justified with the comparison that the proposed technique outperforms better producing good quality images that can be easily watermarked or extracted. The comparison is made with four different images taken into consideration in the process of watermarking. The comparison is shown in Table 5 and Figure 13.
The comparison graph shows the difference of output between proposed algorithm and existing algorithms.
Comparison with Existing Algorithms
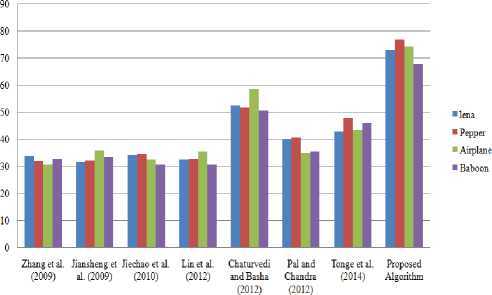
Fig.13. Comparison with Existing Researches
When observed the values graphically, it is identified that the existing techniques and operations performed on different images provides PSNR values. These PSNR values are low as compared to the proposed algorithm that has been carried out in this thesis work. Using DWT , to implement the image it enhances the image quality.
-
VI. Conclusion and Future Scope
In this paper, a novel image watermarking technique has been developed. Various digital image watermarking strategies have been studied. Out of these techniques, DWT based Watermarking technique is better and easy to implement. In existing techniques, only watermarking technique is applied but in this algorithm, after watermark extraction, image interpolation technique is applied to zoom the image. The image interpolation technique is used to get the hidden and improved information stored in the image. Using DWT for watermarking, it provides 52% better results as compare to other images. The method of image watermarking and interpolation can be extended for sending hidden text stored in images in military agencies. The work can also be extended for communicating encrypted images in underwater communication. Moreover, the work can be extended to provide images free from color that are added due to the cover image.
Список литературы Enhanced Image Watermarking Technique using Wavelets and Interpolation
- Yunis and E. H. Abdurrahmal , ”Comparison Among Some Image Zooming Methods”, College of Basic Education Researchers Journal, Vol. 12, No. 3, pp. 761-774 2013.
- Yadav and A. Yadav, “Comparison of SVD-Watermarking and LSB-Watermarking Techniques”, International Journal of Computer Science and Mobile Computing, Vol. 3, No. 5, 2014.
- Ram,” Digital Image Watermarking Technique Using Discrete Wavelet Transform And Discrete Cosine Transform”, International Journal of Advancements in Research and Technology, Vol. 2, No. 4, pp. 19-27, 2013.
- F. A. Jassim, “ Image Inpainting by Kriging Interpolation Technique”, World of Computer science and Technology Journal (WSCIT), Vol. 3, No. 5, 2013.
- Woo, and S. D. Lee, “Digital Watermarking for Image Tamper Detection using Block-Wise Technique”, International Journal of Smart Home, Vol.7, Issue 5, pp.115-124, 2013.
- J. Zhang, S. Ma, Zhang, and D. Zhao, “Fast and Effective Interpolation Using Median Filter”, Pacific-Rim Conference on Multimedia, pp. 1176–1186, 2009.
- L. K. Saini and V. Shrivastava, “A Survey of Digital Watermarking Techniques and its Applications”, International Journal of Computer Science Trends and Technology (IJCST), Vol. 2, No. 3, pp. 70-73, 2014.
- M. Jiansheng, L. Sukang, and T. Xiaomei, “A Digital Watermarking Algorithm based on DCT and DWT”, International Symposium on Web Information Systems and Applications Nanchang, China, 2009.
- M. Pal and T. Chandra, “Zooming Digital Images using Interpolation Techniques”, International Journal of Application or Innovation in Engineering & Management (IJAIEM), Vol. 2, No. 4, 2013.
- M. Tonge, P. K. Malviya, and A. Gupta, “Implementation of Digital Watermarking Algorithm based on DWT and DCT”, International Journal of Advanced Engineering and Global Technology, Vol. 2, Issue 1, 2014.
- N. Chaturvedi and S. J. Basha, “Comparison of Digital Image Watermarking Methods DWT & DWT-DCT on the Basis of PSNR”, International Journal of Innovative Research in Science, Engineering and Technology, Vol. 1, No. 2, 2012.
- R. Dubolia, R. Singh, S. S. Bhadoria and R. Gupta, “Digital Image Watermarking by using Discrete Wavelet Transform and Discrete Cosine Transform and Comparison based on PSNR”, Proceedings of International Conference on Communication Systems and Network Technologies, pp. 593-596, 2011.
- R. Olivier and C. Hanqiang, “Nearest Neighbor Value Interpolation” , International Journal of Advanced Computer Science and Applications, Vol. 3 , No. 4, pp. 25-30, 2012.
- R. V. Totla, and K. S. Bapat, ”Comparative Analysis of Watermarking in Digital Images using DCT and DWT”, International Journal of Scientific and Research Publications, Vol. 3, Issue 2, 2013.
- S. Kaur, J. Kaur, I. Kaur, “Interpolating Images Toward Near Future: A Survey”, International Research Journal of Advanced Research in Computer Science and Software Engineering, Vol. 6, No. 5, pp. 527-530, 2016.
- T. C. Lin, T. K. Truong, S. H. Hong, and L. Wang, “Novel Approaches to the Parametric Cubic-Spline Interpolation”, Image Processing and Computer Vision, Vol. 4, pp. 448-454, 2012.
- W. Jiechao, L. Zhiwei, and Z. Min, “Two New Proposed Image Zooming Methods”, in International Conference on Wireless Communications Networking and Mobile Computing, pp 1-4, 2010.


