Ensemble learning approach for weapon recognition using images of wound patterns: a forensic perspective
Автор: Dayanand G. Savakar, Anil Kannur
Журнал: International Journal of Image, Graphics and Signal Processing @ijigsp
Статья в выпуске: 11 vol.10, 2018 года.
Бесплатный доступ
This paper presents a forensic perspective way of recognizing the weapons by processing wound patterns using ensemble learning that gives an effective forensic computational approach for the distinguished weapons used in most of crime cases. This will be one of the computational and effective substitutes to investigate the weapons used in crime, the methodology uses the collective wound patterns images from the human body for the recognition. The ensemble learning used in this proposed methodology improves the accuracy of machine learning methods by combining several methods and predicting the final accuracy by meta-classifier. It has given better recognition process compared to single individual model and the traditional method. Ensemble learning is more flexible in function and is better in the wound pattern recognition and their respective weapons as it overcomes the issue to overfit training data. The result achieved for weapon recognition based on wound patterns is 98.34%, from existing database of 800 images of pattern consisting of wounds of stabbed and gunshots. The authenticated experiments out-turns the preeminence of projected method over the widespread feature extraction approach considered in the work and also compares and suggest the false positive recognition verses false negative recognition. The proposed methodology has given better results compared to traditional method and will be helpful in forensic and crime investigation.
Classifiers, Ensemble, Forensic, Recognition, Patterns, Weapons, Wound
Короткий адрес: https://sciup.org/15016006
IDR: 15016006 | DOI: 10.5815/ijigsp.2018.11.01
Текст научной статьи Ensemble learning approach for weapon recognition using images of wound patterns: a forensic perspective
Published Online November 2018 in MECS
In last decade, crime and forensic department is advanced in automation and intellectual recognizing technologies and sequences of processing the data. Forensic science department expertise in enclosing comparisons of biometric, handwritten data, handguns, and sharp metal marks, that can be related or irrelated to suspect with a crime by crime laboratories. Shoe and vehicle tires patterns also comes under pattern recognition domain. This kind of investigations proceeds with comparing collected evidence at crime scene or from the suspicious persons with existing database. Bite pattern analysis can also be included to forensic investigations, though it is processed in the area of forensic dentistry as an aide of dental recognition and is not conducted by crime investigation labs. One of method required in crime investigation laboratories is that of wound patterns-based weapon recognition of sharp metals and gunshots. The literature provides acceptable characteristics of injuries on victims from various types of gunshots and sharp metals. Most forensic science concerning wound patterns are analyzed by doctors or medical experts; generally, they get the wounds of the dead victims but not the living attacker. The analysis of wounds will undoubtedly have carried by the crime or forensic investigator. The purpose of this analysis to point out however important studies of a complex stabbed and gunshots wound patterns in ruthless homicide directed to the weapon recognition. A set of sharp metal and gun weapons are selected that are considered as a universal range of the weapons which are commonly identified and collected by forensic investigators in many of the crime cases. Researchers have conceded the importance of machine vision in the process of pattern recognition. This is the purpose of more precise and reliable methods need to be implemented, processed and compared to the work of other researchers. In order to implement method of recognition with high accuracy, the ensemble learning is proposed in this paper. Ensemble learning benefits in improvising accuracy of the machine learning by combining several different models [Vadim Smolyakov]. The proposed approach gives a superior prescient execution contrasted with a solitary model. That is the reason gathering strategies put first in numerous renowned machine learning rivalries. The proposed methodology framework is as shown in section 3. 2.
-
II. Related Work
-
III. Proposed Methodology
A general framework of the proposed methodology for weapons recognition based on wound patterns is shown in Figure 1. This methodology consists of the following stages: Image acquisition, pre-processing, segmentation, features extraction and recognition using ensemble learning. In the pre-processing, the elimination of noise is performed on the captured image such that the image is prepared for better segmentation and further extracting features from region-of interest. In recognition stage using ensemble learning, from the set of training images features are primarily extracted and the database is prepared accordingly and ensemble learning is trained (base-level models and meta-classifier is trained from the outcome of base-level models). Then, from the set of test image database whose features are extracted, are tested using trained ensemble learning, the result of all recognitions is measured and the accuracy is calculated.
Training / Testing Phase
Image Acquisition

Image Preprocessing

Segmentation

Features Extraction
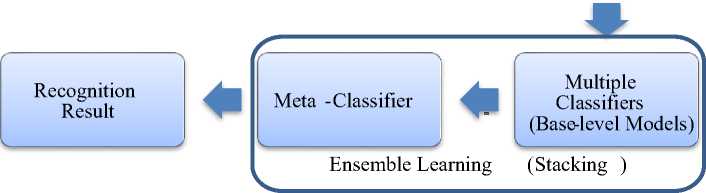
Fig. 1 Block Diagram of Proposed Methodology
-
A. Image Acquisition
The images were captured using color digital camera under controlled conditions with respect to crime investigation. The camera with a zoom focal point 14x central length and close-up 1x. The Images were obtained with 300 x 400 resolution in estimate, for the example pictures see figure 2. The controlled condition shows that there won't be any further harms made to casualties' body and at uncommonly wound area. The area of an image displaying the actual image is referred to as the main area due to shape. In this work, we assume that all the images have same resolution, but images with different resolutions can be resampled to a common resolution. The first stage of our approach is to detect region of interest in each image, from which features will be extracted. The quality of the images is improved by applying the preprocessing method of sharpening to acquire differential and correct measurable features using spatial filtering.

(a) (b) (c) (d)

(e)
(f)
(g)
Fig.2. Images of wound patterns on human body caused by different weapons (a) Kitchen Single-edged knife (b) Kitchen fork (c) Starshaped screwdriver (d) Double-edged knife (e) .410 shotgun wound (f) .38 caliber bullet wound (g) wound from .38 Special revolvers (h) wound created from 9mm automatic rifle

(h)
-
B. Image Preprocessing
Image preprocessing can altogether enhance the consistency of a visual review. Some of filtering channel forms in images that strengthen or decrease certain image points of interest which empower a less demanding or quicker assessment.
Spatial Filtering – Filtering is one of imperative process in image handling. It is utilized for the image improvement, noise lessening, edge recognition, and sharpening. Spatial filtering can be performed utilizing the convolution task as show in Eq. 1 and the figure 3 shows the histogram of spatial filtering steps.
s(x,y)= Z m^-M^ Z N^-N^ h^n^s-m^-n) (1)
where p(a, b) is Gaussian filtering mask of size A x B.
(b)
(c)
Fig.3. Histogram images of spatial filtering (Input sample is figure 2a) (a)Original Image (b) After Gaussian filtering mask (c)Final image from spatial filtering
-
C. Segmentation
Impeccable image segmentation is allocating every pixel to the precise object. To be sure, as a result of the way these digital images are acquired, this might be incomprehensible, since a pixel may straddle the "genuine" limit of items, with the end goal that it mostly has a place with at least two objects. In this proposed methodology, threshold-based image segmentation is used, which is highly suitable for the patter classification applications. Thresholding is the most common method used for segmenting object from the image. Thresholding process is remapping operation g of grey values defined by Eq.2:
**={?:^ (2)
Where x is grey value, and t is threshold value, thresholding does map grey-valued to the binary image. After thresholding process, the image will be divided into two segments, recognized by the 0 and 1 values of pixels. Many methods are available to choose appropriate threshold value for a segmentation. The common method to set the threshold value is by interactively; till the satisfying segmentation result is achieved, the users compare, manipulate and revise the threshold value.
-
D. Feature Extraction
In the fields of machine learning, pattern classification and image processing, it starts with features extraction from the essential input of estimated information and assembles determined qualities known as features proposed to be useful and non-repetitive, empowering to the resulting learning and simplification steps, and in some cases the enhanced human elucidations. Features extraction is identified with diminished in dimensionality. When an algorithm processes the large input data and it is suspected to be redundant, then that can be changed into decreased features set named as feature vector, characterizing the underlying features subset known as feature choice. The chosen features are relied upon to involve fitting data from the information (refer table 1 for chosen features), with the goal that the coveted undertaking can be performed utilizing the diminished portrayal rather than the extensive variety of initial data. The algorithm for feature extraction is as given in algorithm 1.
Table 1. List of Features for Recognition of Weapons
|
Sr. No. |
Name of the Features |
|
1 |
Area |
|
2 |
Perimeter length |
|
3 |
Bounding box |
|
4 |
Convex Hull |
|
5 |
Compactness |
|
6 |
Central Moments |
|
7 |
Size-Invariant |
|
8 |
Eccentricity |
|
9 |
Gray-Level Co-occurrence Matrix (GLCM) |
|
10 |
Correlation |
|
11 |
Shape Signature |
|
12 |
Shape Matrix |
Texture, Size and Shape features - Texture, size and shape parameters have an effect on however the objects are created through segmentation. The resulting objects will be improved for spectral or abstraction homogeneity if the value of texture, size or shape parameters are high. Among the various standards, the user can modify the values of smoothness and density of the objects. There will be balancing between the texture, shape and size parameters, i.e., higher the value of texture then higher the impact on segmentation and lower value for shape will have less impact. If texture and shape parameters are unit equal, then it will have uneven amount of impact on the outcome of segmentation.
Algorithm 1: Feature Extraction
Input: Segmented Image
Output: Extracted Features Vector
Step 1: Reading of the Segmented image consist of region-of-interest
Step 2: Computing the following Geometric Features from the image
Step 2.1 Perimeter: The assessment of the perimeter of an object is regularly and essential part of any set of rules designed for image processing. Contour features inclusive of perimeter allow distinguishing a number of the objects having the equal area. The perimeter is given by equation Eq.3 and to avoid overestimation 0.95 value used as multiplier.
P(R) = (0.95) x ∑ i M = - 0 1length(c i ′) (3)
1 for c = 0, 2,4, 6
With length (c) = {
√2 for c = 1, 3, 5, 7
Step 2.2 Area: Approximately all image recognition applications need to calculate the dimensions of the objects in given input image. The key feature normally used for such calculation is the area of the object. In most of image processing, the object area is frequently measured as “number of pixels inside the object”. i.e., after segmentation of objects, number of pixels inside each closed object/region indicates the area of the object/region. Simply count image pixels that make up region is given by equation Eq.4:
A(R) = | R | = N (4)
Step 2.3 Bounding Box: Bounding boxes is an input data to be characterize the possible region of interest. In wide-range, every feature recognition algorithm returns the region of interest in terms of pixel coordinates, height and width. The initial coordinates along with height and width in terms of pixels, minimum axis-parallel box that encloses all points in R is given by equation Eq.5:
BoundingBox(R) = 〈 u min , u max , v min , v max 〉 (5)
Step 2.4 Convex Hull: Both boundary and morphological methods are used for the computing of convex hull for a finite point set S - αi and xi is a point within the region-of-interest of the image. With the given equation Eq. 6 used to compute convex hull:
C= {∑| i S = | 1 α i x i | ( ∀ i ∶ α i ≥0) ∧ ∑| i S = | 1 α i =1 } (6)
Step 2.5 Compactness: The compactness of object defined as the ratio between the square of the perimeter to the area of the object. This measure is called compactness and is defined as follows:
P2(R)
Compactness =
Where P(R) is perimeter and A(R) is area of region-of-interest R. Compactness will basically vary from lengthy-slender objects (have high compactness values) to circular objects (have small compactness values).
Step 3: Computing Statistical Shape Features
Step 3.1 Central Moments: Central moments is computed based on characteristic properties w.r.t. its centroid. Centroid of a binary region is the mathematical mean of all (x, y) coordinates in the region is given by Eq.8:
x̅ = 1 ∑ (u,v)ϵ R u and y̅ = 1 ∑ (u,v)ϵ R v (8)
Centroid is only specific case of more general concept of moment, moment (ordinary) of the order (p, q) for the discrete function I(u, v ) is given equation Eq.9:
m pq = ∑ (u,v)ϵ R I(u,v).upvq (9)
Step 3.2 Size-invariant: Moments are one of the known parameters in image processing and analysis, subsequently they derive invariants w.r.t. explicit classes transformation. The word invariant moments are frequently ill-treated in this context. Nevertheless, the moment invariants are defined as “the moments that are invariants in themselves are the central moments”. Sizeinvariant features can be obtained by scaling central moments uniformly by some factor s
Size_Invariant = s(p+q+2) (10)
Step 3.3 Eccentricity: It is computed using the derived values of semi-major axis a and semi-minor axis b of object from the image by using the equation Eq. 11, we get the eccentricity E:
E = √1 - b2/a2 (11)
Step 3.4: Shape signature denotes shape by a onedimensional function defined from shape boundary points. In the proposed methodology, we have selected to compute the centroid distance function as there are many shape signatures available. From the binary shape boundary consists of L pixels in input image, each pixel has the coordinates x(t), y(t) with t=0, 1…., L-1.
Centroid distance function is given by r(t) in Eq. 12 denotes the distance of the boundary points from the centroid (g x , g y ) to object circumstances in input image.
r(t) = √[(x(t) - g x )2 + (y(t) – g y )2] (12)
Step 3.5: Shape matrix is defined as “sparse selection of shape”, it is easily get affected by noise. A shape description based on the relative areas of the shape within concentric rings (Ci) positioned in the center of the mass. The invariant area-ratio Xi is computed using Eq.13:
X i = A(S ∩ C i )/A(C i ) (13)
Where A ( · ) is the area function and S is shape of the object.
Step 4: Computing Texture features
Step 4.1 Gray-Level Co-occurrence Matrix (GLCM):
GLCM is “defined over an image to be the distribution of co-occurring pixel values (grayscale values, or colors) at a given offset”. Image with p different pixel values, the pxp co-occurrence matrix C is defined over n x m image I, parameterized by an offset (Ax, Ay), as given in Eq.14:
C ∆ x ,∆ y (i,j) nm
= ∑∑{ x=1 y=1
10,,
I(x, y) = i and I(x+ ∆x ,y+ ∆y) = j otherwise here i and j are values of pixel; x and y are the spatial locations in the image I; and I(x,y) indicates pixel value at pixel (x, y).
Step 4.2: Correlation is defined as “relation between spatial domain processing with frequency domain processing” and is also to determine the degree of likeness between data sets
∑ x,y [(xy)P(x,y)]-μ x μ y
Correlation =
σ x σ y
where, μx , μy are means and σx , σy are standard deviations.
-
E. Ensemble Learning
In machine learning and statistics, ensemble learning procedures use many learning algorithms to get higher prognostic performance that may be obtained from any of the fundamental learning algorithms alone. in contrast to an applied math ensemble in natural philosophy, that is typically immeasurable, a machine learning ensemble consists of solely a finite set of different models, however usually permits for way more versatile structure to exist among those alternatives. associate degree ensemble learning is itself a supervised learning formula, as a result of it may be trained and so it may be tested on unknown samples. The trained ensemble, therefore, represents one proposition. This proposition, however, isn't essentially contained at intervals the proposition house of the models from that it's designed. Thus, ensembles learning may be exposed to own additional flexibility within the functions they'll represent. This flexibility will change them to overfit the training information over one model would, however in follow, some ensemble techniques particularly sacking tend to cut back issues relating to overfitting of the training information. by experimentation, ensembles tend to provide higher results once there's a considerable diversity among the models. several ensemble learning, therefore, ask for to encourage diversity among the models they combine. Though maybe non-intuitive, additional random algorithms like random decision trees may be won’t turn out to be a strong ensemble than terribly deliberate algorithms like entropy-reducing decision trees. Employing a diversity of robust learning algorithms, however, has been shown to be simpler than victimization techniques that arrange to build easy and easier models so as to market diversity. Whereas the quantity of module classifiers of associate degree ensemble encompasses a nice impact on the accuracy of prediction. A priori process of ensemble size and also the rate of enormous information streams builds this even additional important for ensemble classifiers. The advantage of this methodology will fall into 3 basic ensemble learning techniques. Ensemble ways are metaalgorithms that combine many machine learning techniques in one analytical model so as to reduce variance (bagging), bias (boosting), or enhancing predictions (stacking). Ensemble ways may be divided into 2 groups:
-
(i) Sequential ensemble learning is the bottom learner generated consecutively. The fundamental motivation of successive ways is to use the dependence among the bottom learners. The overall performance may be boosted by advisement antecedently misclassified samples with higher weight.
-
(ii) Parallel ensemble learning is the bottom learners generated in parallel. the fundamental motivation of parallel ways is to use independence between the bottom learners since the error may be reduced dramatically by averaging.
Most ensemble ways use one base learning formula to provide homogeneous base learners, i.e. learners of a similar kind, resulting in homogeneous ensembles. For the planned methodology uses heterogeneous learners, i.e. learners of various sorts, resulting in heterogeneous ensembles. so as for ensemble ways to be additional correct than any of its individual members, the bottom learners need to be correct and numerous as achievable.
Stacking – In this proposed methodology, stacking is employed to enhance the predictions from the base classifiers. Stacking is associate degree of ensemble learning technique which makes combinations of various classification or regression models through the meta-classifier/regressor. The base level model is trained with an entire training set, next, the outputs of the base level model is used to train the meta-model. The base level generally includes various learning algorithms and thus stacking ensembles are typically heterogeneous. The algorithm 2 below summarizes stacking.
Algorithm 2: Ensemble Classifier - Stacking
Input: Training data D = [х,у}™ 1
Output: Ensemble classifier EC
Step 1: Training of base-level classifiers for k=1 to K do training of em w.r.t D end for
Step 2: Construction of new data set from predictions for i=1 to m do
De = {x ,' , у , }, where X i = {e i (x [ ), ..... ем(х^ end for
Step 3: Train a meta-classifier train EC w.r.t De
Return EC
Base-level Classifiers and Meta-Classifier - Base-level classifier models within the proposed methodology consists of SVM, Random Forest, and Naive Bayes are base classifiers whose predictions are combined by supplying regression as a meta-classifier. We will see the combination of models which will achieve better accuracy by the use of stacking classifier. The figure 4 shows that stacking achieves higher accuracy than individual classifiers, it clearly shows no signs of overfitting. Applying regression as metaclassifier that could be a methodology with suitable regression line, y = f(x), as y is categorical variable and the standard use of this model is for given set of predictors x, predicting y. The predictors will be continuous, categorical or a combination of each of the specific variable y, in general, will assume totally different values. Within the simplest case y is binary which means that it will assume either the values “1 or 0”. In first case, we tend to have decision model as binomial regression, since the variable to predict is binary, however, applying regression may be predicted for a variable which might assume quite 2 values. In the second case, we tend have decision model as multinomial regression.
-
IV. Results and Discussion
Fascinatingly, the proposed methodology is competitive with respect to the recognition by human experts. In this, where the database of images to recognize is so less, and where the perfect recognition is required, the method would thus, be quite useful. The experiments illustrate that the method obtained better results on available images database representing various wound patterns. Indeed, this will rightly applicable to any image recognition problem and is practically effective and efficient. Proposed approach is evaluated on different image database concerning with the recognition of wounds and their weapons of cause. Moreover, we successfully applied it on database of 800 images with recognition results are better than the other methods. In this, we evaluated the potential of method by its performances on two different datasets of images. The application of our method is straightforward and we compare its results with traditional method which has manual human verification and comparison with individual classifiers. The properties of the proposed method are defined as attractive, computational, efficient and possible interpretation based on results. Essentially, measuring of the accuracy of models is to predict accurately for database of unknown images. It has shown that it is possible to identify the weapons based on wound patterns that describes the type of weapon used in homicidal cases. For this purpose, different weapons were considered for the recognition and their images of wounds were acquired. The wounds were preprocessed with spatial filtering and segmented using threshold. Texture features, size, shape and geometric measures were extracted from the wounds to find features that define the wound patterns and weapon of cause. The proposed methodology is suitable for classifying the wound pattern and its weapon of cause. We have not found computational approach in the open literature where wound with weapon of cause is identified based on the wound patterns using images but there is traditional method which involves a manual human verification that has many disadvantages-human error and data manipulation. The methodology used most common in identification is post-mortem investigation by medical practitioners, where a comparative study between the weapons and wounds was performed in order to determine the compatibility and declare the result. As per the survey medical practitioners identifies and classifies the weapons with the accuracy of 72.3% to 95% that has variations in result from one medical practitioner to other, the methodology used is manual so in some cases manipulation of data is done and also includes human error whereas digitization of the identification and classification reduces the human error, can avoid manipulation of data and also gives high accuracy. The accuracies obtained for the proposed methodology is 98.34%.
The proposed methodology has given better accuracy results in comparison with traditional method with an accuracy varying from 75% to 92%, this variation is from one person and another which involves human errors and manipulation of data [26] and also in comparison with individual classifiers 91.73% of SVM, 94.35% of Random forest and 88.89% of Naïve Bayes classifier (refer figure 4 and table 2). The system suggested an advantage of proposed methodology with comparing with defined inform clinical decision-making and that diminishes the likelihood of unsuccessful recognition.
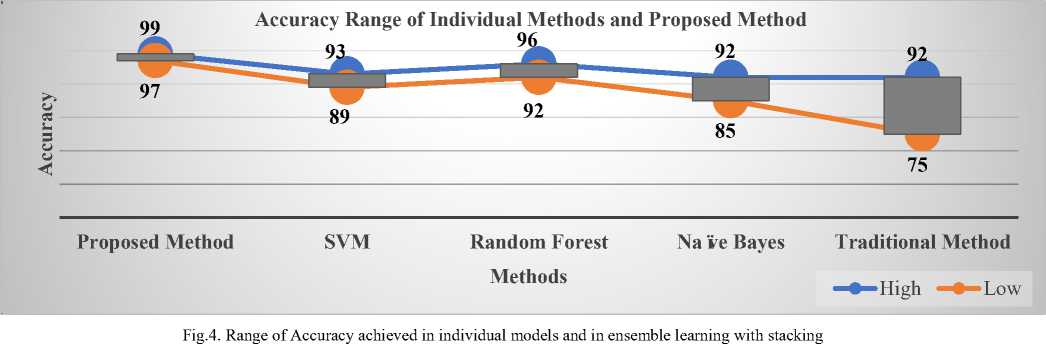
Table 2. Accuracy of individual models, traditional method and stacking ensemble learning with respect to different weapons’ wound patterns
|
Type of Weapons’ wound pattern |
SVM |
Random Forest |
Naïve Bayes |
Proposed Method |
Traditional Method |
|
Single-edged knife |
93.1 |
96.2 |
92.3 |
98.6 |
|
|
Kitchen fork |
92.7 |
93.7 |
87.2 |
97.7 |
-6 2 S s.O 25 ^ я 1 I £ 8 S о p^ g |
|
Star shaped screwdriver Double-edged knife |
93.3 91.8 |
96.1 92.1 |
91.5 88.3 |
99.4 98.5 |
|
|
.410 shotguns wound .38 caliber S & W bullet wound |
92.6 89.2 |
95.4 93.5 |
89.6 85.6 |
98.6 97.8 |
|
|
.38 Special revolvers; |
89.5 |
93.5 |
86.2 |
97.6 |
|
|
9mm automatic rifle |
91.6 |
94.3 |
90.4 |
98.5 |
-
V. Conclusion
In addition to the methods studied in this article, it is common to use ensembles in learning by training diverse and precise classifiers. Diversity will be achieved by changeable architectures, hyper-parameter settings and training procedures. Ensemble learning methods have been efficacious in setting best performance on challenging datasets. The experimental study shows a better method is proposed for recognizing weapons using wound patterns images with two different databases (one for training and other for testing) in comparison with traditional method and individual classifiers. The performance results show that the average recognition accuracy of the proposed method is better than these individual methods for the available database. That is, the accuracy of the proposed method is 98.34% for the whole database of wound patterns. This accuracy for the proposed method is near to perfect recognition for the whole database. For the proposed method on the wound patterns images acquired from the crime scenes, the results of this experiment indicated that the proposed method had a higher recognition accuracy than other methods. Moreover, future research should focus on executing the proposed method on bigger databases.
Список литературы Ensemble learning approach for weapon recognition using images of wound patterns: a forensic perspective
- Shuaibur Rahman, M. N. A. Khan, (2016) "Digital Forensics through Application Behavior Analysis", International Journal of Modern Education and Computer Science (IJMECS), Vol.8, No.6, pp.50-56.
- Rubayyi Alghamdi, et.al., (2016) “Hidden Markov Models (HMM) and Security Applications”, International Journal of Advanced Computer Science and Applications, Vol. 7, Issue 2, pp:39-47.
- Adeleh Farzad, Rahebeh Niaraki Asli, (2015), "Recognition and Classification of Human Behavior in Intelligent Surveillance Systems using Hidden Markov Model", IJIGSP, vol.7, no.12, pp.31-38.
- Varsha Dixit and Anupam Agrawal, (2015), “Real Time Hand Detection & Tracking for Dynamic Gesture Recognition”, International Journal of Intelligent Systems and Applications, Vol. 08, pp: 38-44 Published Online July 2015 in MECS.
- Dayanand G Savakar, Anil Kannur (2015) “A Genetic algorithm and Bayesian approach for recognition & classification of weapon based on the stab wound patterns caused by different sharp metal”, International Journal of Computer Engineering and Applications, Volume IX, Issue I, pp: 01-12.
- Dayanand G. Savakar and Anand Ghuli, (2015), “Digital Watermarking as distributed noise by Discrete Wavelet Transformation, Fast Fourier Transformation and Fast Walsh-Hadamard Transform to study the sensitivity between Robustness and Fidelity”, International Journal of Computer Application, Issue 5, Vol.1, pp 102-107, ISSN: 2250-1797.
- Dayanand G. Savakar and Anand Ghuli, (2014), “Digital Watermarking-A Combined Approach by DWT, ChirpZ and Fast Walsh-Hadamard Transform”, International Journal of Computer Technology and Applications (IJCTA), Vol. 5 No.6, pp 2006-2010, ISSN 2229-6093.
- Song Bo, (2012) “Automated wound recognition system based on image segmentation and Artificial Neural Networks”, IEEE International Conference on Bioinformatics and Biomedicine, pp: 11-16.
- Gitto L., Vullo A., Demari G.M., (2012) “Recognition of the murder weapon by the analysis of a typical pattern of sharp force injury”, Italian Journal of Legal Medicine, Vol: 01, Issue No. 1, pp: 04-14.
- Ying Bai; Dali Wang, (2011)"Evaluate and identify optimal weapon systems using fuzzy multiple criteria decision making", Proceedings of IEEE International Conference on Fuzzy Systems, pp: 1510-1515.
- Suapang P., et.al., (2011),” Tool and Firearm Recognition System Based on Image Processing”, Proceedings of 11th International Conference on Control, Automation and Systems, pp: 178 – 182
- Kaliszan M., Karnecki K., Akçan R., (2011) “Striated abrasions from a knife with non-serrated blade— recognition of the instrument of crime on the basis of an experiment with material evidence”, International Journal of Legal Medicine, Vol: 125, Issue No. 5, pp: 745–748
- Ajay Kumar N, ChenyeWu, (2011) “Automated human recognition using ear imaging”, Journal of Pattern Recognition, Elsevier Ltd., pp: 1-13.
- Basavaraj S. Anami and Dayanand G. Savakar, (2011), “Suitability of Feature Extraction Methods in Recognition and Classification of Grains, Fruits and Flowers”, International Journal of Food Engineering, Vol.7, Issue 1, Article 9, pp: 1-28, Publisher: Berkeley Electronic Press, Berkeley, U.S.A.
- Francisco Veredas, et.al, (2010),” Binary Tissue Classification on Wound Images with Neural Networks and Bayesian Classifiers”, IEEE transactions on medical imaging, Vol: 29, Issue2, pp: 410-426.
- Anil Jain and Jung-Eun Lee, (2009), “Scars, marks, and tattoos: a soft biometric for identifying suspects and victims”, Journal of SPIE, the international society for optics and photonics, pp: 01-02
- B.S. Anami, D.G. Savakar, (2009), “Effect of Foreign Bodies on Recognition and Classification of Bulk Food Grains Image Samples”, Journal of Applied Computer Science and Mathematics, Vol.3(6), pp: 77- 83.
- F.A. Andaló, A.V. Miranda, A.X. Falcão, (2009),” Shape feature extraction and description based on tensor scale”, Journal of Pattern Recognition, Elsevier Ltd, pp:1-11.
- B. S. Anami, Dayanand G. Savakar, (2009), “Recognition and Classification of Food grains, Fruits and Flowers Using Machine Vision”, International Journal of Food Engineering, Vol.5, Issue 4, pp: 1-25.
- M. Brandon Westover and Joseph A. O’Sullivan, (2008) “Achievable Rates for Pattern Recognition”, IEEE transactions on Information Theory, Vol: 54, Issue No. 1, pp: 299-320.
- Li Dongguang, (2008) “Firearm Recognition System Based on Ballistics Image Processing”, Proceedings of CISP '08, Congress on Image & Signal Processing Vol: 3, pp:149-154
- Jie Liu1, Jigui Sun, Shengsheng Wang, (2006) “Pattern Recognition: An overview”, IJCSNS International Journal of Computer Science and Network Security, Vol:6, Issue No.6, pp: 57-61
- Qi Peter Li, and Biing-Hwang Juang, (2006) “Study of a Fast-Discriminative Training Algorithm for Pattern Recognition”, IEEE transactions on neural networks, Vol: 17, Issue No. 5, pp-1212-1221
- T. Plattner, B. Kneubuehl, M. Thali, U. Zollinger, (2003) “Gunshot residue patterns on skin in angled-contact and near contact gunshot wounds”, Forensic Science International, Elsevier publication, Vol. 138, pp:68-74.
- Candida Ferreira, (2001) “Gene Expression Programming: A New Adaptive Algorithm for Solving Problems”, Journal of Complex Systems, Vol. 13, issue 2, pp: 87-129.
- I.R. Coyle, D. Filed and P. Wenderoth (2009),” Pattern Recognition and Forensic Recognition: The Presumption of Scientific Accuracy and Other Falsehoods”, Criminal Law Journal, Vol. 33, Issue 4, pp:214-226
- Louis Wehenkel, et.al., (2006), “Ensembles of extremely randomized trees and some generic applications”, RTE-VT workshop, Paris, May 29-30


