Extending the WSN lifetime by Dividing the Network Area into a Specific Zones
Автор: Mishall H. Awaad, Wid A. Jebbar
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 2 vol.7, 2015 года.
Бесплатный доступ
LEACH protocol is considered the best in the WSN protocols in extending the network lifetime and reduces energy loss, but LEACH suffers from the problem of the correct distribution of the nodes correlation with CHs. In this paper, we propose an improved protocol called LEACH-Z(LEACH zones), this protocol improves the distribution of clusters by making the clusters near the base station(BS) large(greater number of nodes) and the clusters are far from BS small(lesser number of nodes), where divides the network area to parts(zones), be part of a larger when close to the BS in addition to preventing the election of CHs in the region far from the BS and thus conserve energy this means that the nodes will remain alive as long as possible, this makes nodes gather more information. The results proved that the LEACH-Z is better than the original LEACH and more optimizations to reduce energy consumption.
LEACH-Z, LEACH, WSN, zone, routing, base station, lifetime network
Короткий адрес: https://sciup.org/15011384
IDR: 15011384
Текст научной статьи Extending the WSN lifetime by Dividing the Network Area into a Specific Zones
Published Online January 2015 in MECS DOI: 10.5815/ ijcnis.2015.02.04
The wireless sensor networks are becoming widespread, and the newly WSN are used in a broad range of applications such as military applications, health, household, environmental control, security [1], and other applications. WSNs usually contain thousands or hundreds of thousands of sensors. Sensor network placed in these applications in two ways:
-
- Random design (such as the distribution of sensors by helicopter)
-
- Fixed design (such as the distribution of sensors in the office to alert the fire)
Information will be grouped by sensors and is sent to the BS.
In wireless sensor networks relate wirelessly. Each sensor consists of a microcontroller, sensor unit, storage unit, radio transceiver unit and power [2]. The purpose of these nodes is to monitor environmental conditions such as temperature, light, sound, objects movement, vibrations [1] or other. The possible deployment of the sensor networks in places that cannot arrive humans under very difficult environmental conditions such as high alpine environments or earthquakes. With the development of wireless sensor networks have emerged many routing protocols, which can be divided into:
-
- Plane routing protocols (such as DD and SAR and SPIN [3] and Romor Routing etc.)
-
- Level routing protocols (such as LEACH and PAGASIS and TEEN etc. [1])
In wireless sensor networks, nodes energy is used to transfer and receive data. The balancing energy consumption of nodes and prolong the lifetime of the network depends on the routing algorithm [4] (good or bad). Therefore good routing algorithm must balance energy consumption to extend the network lifetime without increasing the complexity of calculation [3]. The nodes energy is a fundamental restriction in WSNs, Therefore, to resolve the problem of energy consumption in WSN, there are efficient routing protocols proposed and used such as LEACH, PAMAS and HEED [1]. The main objective of routing protocols is to find improvements in energy efficiency and reliable transport of data to the base station.
Among the many routing protocols, LEACH is one of the first and major improvements on reviews clustering; several clustering algorithms are based on the architecture and the idea of LEACH. LEACH protocol is one of the most popular hierarchical routing protocols for wireless sensor networks [1]. The idea is to form clusters of nodes sensing depending on the strength of the received signal and the use of CHs (cluster heads) as routers to the sink (base station) [5]. LEACH divides the entire network into several clusters, and the time of implementation of the network is divided into several rounds. At each round, cluster head is selected randomly in LEACH. LEACH protocol is more mature in solving the energy balance, but it still contains defects such as network survival time and others. In this paper provided us with a more efficient solution than the original LEACH protocol in energy consumption by dividing the network area into zones.
But before clarifying in details the proposed protocol let`s take a look to the previous studies
There are many papers focused on the energy consumption and routing in sensor networks. Here are some of the previous papers related to our work are as follows:
F. Xiangning and S. Yellin proposed research study LEACH protocol, by improving the method of selecting the cluster head and make the nodes which have more energy to be CH in the next round. They also used the communication mode of single hop to multi hop between CH and BS [5].Z. PENG and X. Li proposed selection algorithm of cluster-head through the change round time by sensor network status. Sensor network energy consumption has become few and thus the lifetime of the network has become long [6]. W. Xiaoping, L. Hong and L. Zhang proposed an improved routing algorithm depends on the LEACH protocol, which includes clusterhead selecting, multi-hop routing and building of its path. Improved routing algorithm provided a high-energy and helped extend the network lifetime [7]. W. Jun, Z. Xin et al proposed a new routing algorithm called LEACH-SC (LEACH-selective cluster), this method includes the node connected with the CH which is closer to the center point between the node and BS [8]. In this paper, we used a different method to get a correct and accurate routing and to extend in the lifetime of sensor network, the results have been positive and good and that will explain later.
The rest of this paper is organized as follows: section two describes the LEACH protocol in details and shows its algorithm and defects of LEACH protocol, section three presents LEACH-Z( its description, its algorithm and the analyzing for it), finally section four discuss the conclusion.
-
II. Leach Protocol
LEACH (Lower Energy Adaptive Clustering Hierarchy) protocol is a routing protocol proposed by Wendi B. Heinzelman, et al [9]. It is the first hierarchical routing protocol in Wireless Sensor network. In this protocol the nodes are divided into only two types of categories; normal sensor nodes and cluster heads. At first the normal sensor nodes are grouped together and form clusters and among all the sensor nodes in a cluster one node are chosen as a cluster head node.
A- LEACH Protocol Algorithm
The operation of LEACH is broken up into rounds as in fig.1, where each round begins with a set-up phase, when the clusters are organized, followed by a steadystate phase, when data transfers to the base station occur [5] [6].
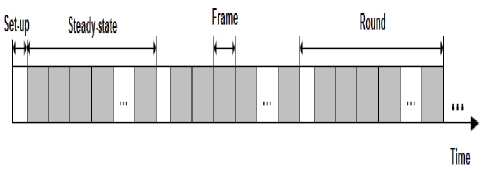
Fig 1: Time line showing operation of LEACH
-
- Set-up phase
In the set-up phase when the clusters are organized, the LEACH sets a threshold value T(n) first, and then sensor node i generates a random number between 0 and 1 automatically by distributed computing .If the random number < T(n), the node will become the cluster-head of the current round r, and common nodes join in the nearest cluster. After a period of data transmission, the network starts cluster reconstruction of the new round [10].
-
- Steady-state phase
The steady-state phase duration is usually much longer than set-up phase duration. However, the first phase is more important, in which sensor nodes are allowed to elect themselves as cluster-heads randomly, and then divided into clusters [6]. Each node that becomes the cluster head (CH) will create a TDMA (Time division multiple access) schedule for the sensor nodes within the cluster. That allows the radio components of each non-CH node to be turned off all times except during their transmit time fig.2 shows the cluster formation algorithm of LEACH. [11].
Threshold T(n) is determined by the following[3][10] [12]:
T ( n M
P
1 - P x [ r mod ( 1/p )]
[ 0,
otherwise
Where [8],
-
n = given number of nodes.
p = the priori probability (e.g. =0.05) of a node being elected as a cluster-head.
r = a random number between 0 and 1 that is selected by a sensor node. If this random number is less than the threshold value T (n), then the respective node becomes the cluster-head.
G = the set of nodes that were not accepted as cluster head in the last “1/p” events.
Elected cluster head node broadcasts a message about the first node cluster to the entire network [13] [14]. The rest nodes of the network decide to join which cluster according to signal strength of the received information, and notify the corresponding cluster head node, completing the establishment of the cluster [10]. The cluster heads combine and compress the data and forward it to the base station [15], therefore it extends the life span of major nodes.
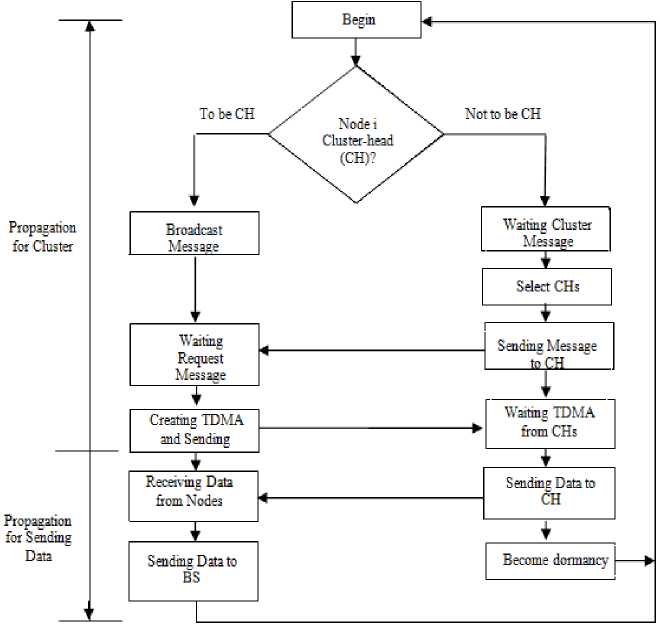
Fig 2: Cluster formation of LEACH protocol
-
B- LEACH Defects
LEACH protocol is best protocols in wireless sensor networks to address energy consumption, but contains a number of flaws are as follows:
-
1. Because that node associated with the CH closest, in some cases, not the closest is the best because of the CH be far from the BS.
-
2. If CH was selected at the farthest point of the area of the network (100 * 100 m2), which will be very far from the BS, and thus an increase in energy consumption.
-
III. LEACH-Z Protocol
Set of features we added to the original LEACH protocol to be the result LEACH-Z protocol, these features increased energy efficiency. LEACH-Z addresses the problems in the original protocol, these problems are the long distance between CH and BS, and the nodes die quickly in rounds and shortness of network lifetime. In the following subsections will explain in detail the LEACH-Z protocol:
A- Description of LEACH-Z
In this section, we will explain the features that we added to the original LEACH protocol,
The first thing that has been made was to divide the whole area that the sensors exist in it into four partitions (near, mid, far, and very far); the node pointed as NEAR, MID, FAR, or VERY FAR according to their distance from the B.S., then a small area (5 meters) from (0-5) allocated and prevented the selection of C.H. in that area; the purpose of that is because that area is so far from the B.S. and fig.3 will clarify that.
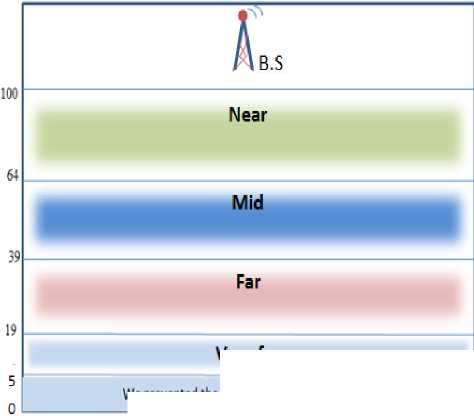
Very far
We prevented the selection of a CH. in this area
Fig 3: The division of the whole area in to four parts
Also the "attachment process" has been controlled so.
What is the meaning of controlling the attachment process?
After the division of the whole area into four parts; what happened to control the attachment process was as follow:
- The number of the nodes in each part has been counted
- The number of the C.H.s in each part counted too
-
- The attachment between the nodes and their C.H.s has been allocated in the same area;
For example, if the node belongs to the nearest part so its C.H. must be from its part too must be from the nearest part also; and so on; maybe someone will ask why has been restricted the attachment in the same part?
The answer so easily is to decrease the consumption of the power that the original LEACH protocol suffering from when the node and its C.H. so far from each other.
As denoted above the attachment happened only between the C.H and the node which belong to the same area, but with conditions; so what are those conditions?
-
1. When there is more than one C.Hs in the same part; so what has been made was counting the distance between the node and that C.Hs, if those distances have been found so close to each other; so in this case the node will attach to the closest C.H. to the B.S...
-
2. But if the distances between a node and that C.Hs have been found not so close to each other; then the node will attach to the closest one to it.
-
3. In this case that rule 'the rule of attachment from the same part' will be broken; because sometimes after so many rounds, maybe will find a particular part with no C.H. so in this case its allowed to the nodes to attaching to the nearest C.H. from the above part from that node part.
And the scenarios in fig.4 will clarify all those cases:
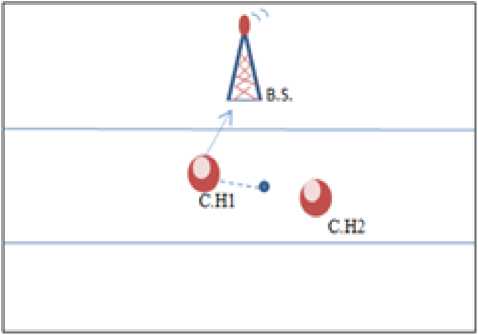
Fig 4 A: the case that the C.H so close from the node
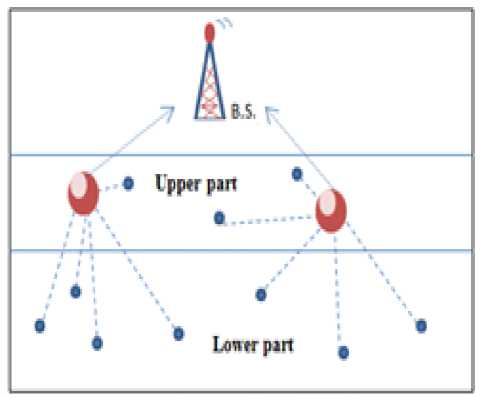
Fig 4 B: the case of no C.H. in a particular part
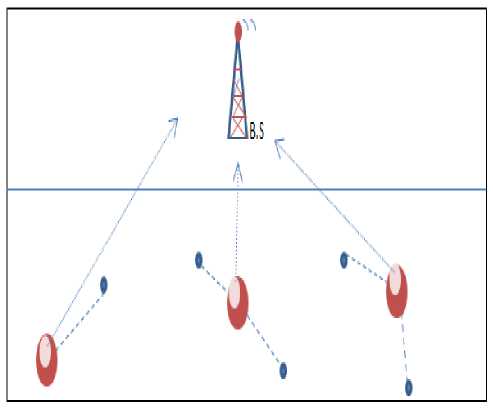
Fig 4 C: the case of more than one C.H in one part but far from each other as clear from fig.4:A that both of the C.H.s are so close to the node so in this case the node will attach to the C.H which closest to the B.S; so the node will attach to C.H.1 the nearest to the B.S.
While in B. as clear the lower part with no C.H. so in this case the rule will be broken and made the nodes attaching to the closest C.H. to them from the upper part. In C the distances between the nodes and the C.H.s are not so close to each other so in this case every node will attach to closest C.H. to it.
B- LEACH-Z Algorithm
In this section, the algorithm LEACH-Z will be illustrated by the flow chart in fig.5.
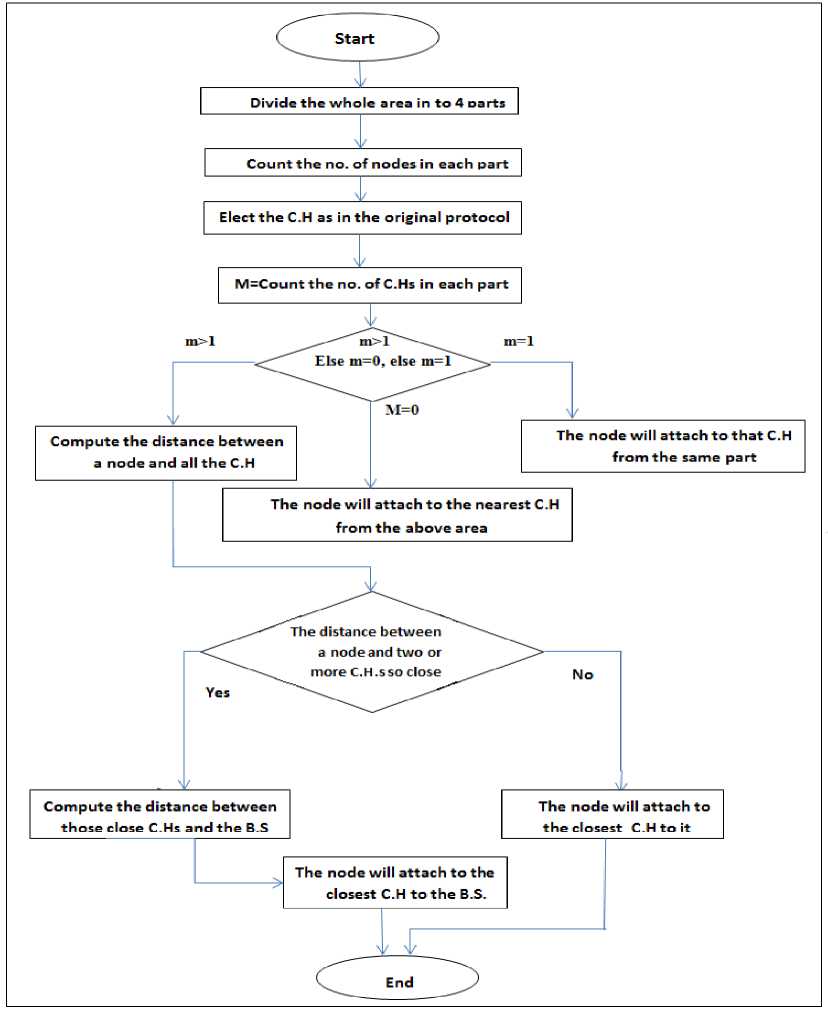
Fig 5: the process of the nodes and C.Hs attachment
The LEACH-Z algorithm led to an increase in network lifetime and reduces energy consumption, and therefore that the LEACH-Z protocol is more efficient than the original protocol. In the next section the simulation results of the two protocols will be explained in detail.
C- Results analyzing of LEACH-Z
Before getting involve in the results we must point to the fact that, this analyzing is based on a 1000 implementation for both the original protocol and the improved protocol, and the parameters that we used in the program implementation was as follow (table 1):
Table 1: Simulation parameters
|
Parameter |
Values |
|
No. of Nodes |
100 |
|
Simulation area |
100x100 m2 |
|
Base station location |
(50,170) |
|
Node energy |
0.5J |
|
Rounds |
800 |
|
Size of Packet |
6400 byte |
|
Meta-data |
200 byte |
So after the implementation has been found that the improved protocol more efficient in several aspects these aspects are:
-
- The number of rounds.
-
- The first node dies.
-
- The number of nodes remaining in 500 rounds, the number of nodes remaining in 700 Rounds
-
- And the number of nodes remaining final (an increase in the lifetime network).
But have been noticed that the results of the original protocol possible to be better than the improved protocol in a few cases. One of those cases is the death of the first node; some times in the original protocol is better than the improved protocol based on this method so we found a reason for that;
Because we allocated the attachment between the nodes and the C.H.s in the same parts; so maybe sometimes the distance between a particular node and the C.H from a previous part to that node part will be closest to that node more than any other C.H. in its own part; as that shown in fig.6:
If its constrained on both the (red nodes) in fig.6 A and B, its can see in the improved protocol that the distance between the red node in the last part and the blue C.H in the previous part nearest than the distance between that node and the C.H. from the same part that this node belong to; and because we allocated the attachment in the same part then it will attach to that C.H which exist in its own part.
While if a look has been taken to the original protocol will see, that node attaching to the blue C.H. "the nearest one"; so in this case that red node in the original protocol will waste power lesser than in the improve one.
That was the reason that sometimes the original protocol better than the improved one.
Has been found that the overall results of the improved LEACH protocol is more efficient and better performance and more perfect when node opt for CH appropriate and is therefore best to reduce the power consumption (i.e., an increase in network lifetime) of the original protocol.as shown in fig.7 which shows the efficiency of the improved protocol in the aspects of first dead node, the remaining node, number of dead node in the round 500(the middle of the whole 1000 experiments), and the number of dead nodes in round 700.
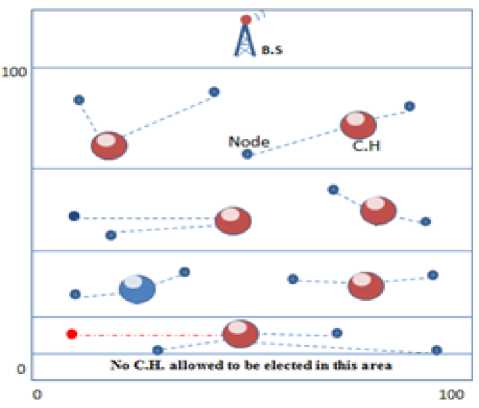
Fig 6 A: Improved protocol
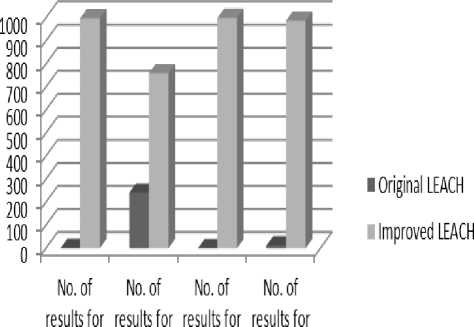
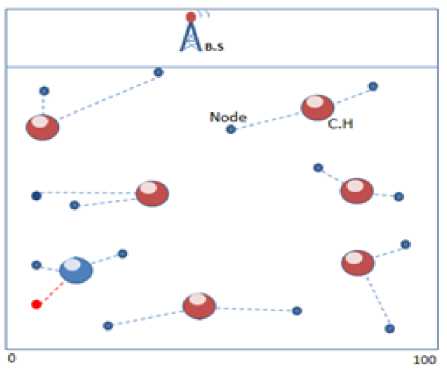
Fig 6 B: Original protocol
remaining first dead the dead the dead nodes nodes nodesin Nodesin
500 round 700 round
Fig 7 comparisons between original and improved protocols
IV. CONCLUSION
As the main task of LEACH protocol is to reduce the power loss, so we proposed LEACH-Z protocol, LEACH-Z to enhance LEACH protocol from those problem that this protocol suffering from which cause wasting the power as denoted in a previous section, our proposed protocol has been proved its efficiency in enhancing the original protocol in the aspects of, first dead node, increasing the remaining node after each round, decreasing the acceleration in the death of the nodes, and help in minimizing the wasted power as we saw that in the section (Results analyzing of LEACH-Z),
which led at the end to enable the sensors to collect more information than the original LEACH can do, which is the main purpose of using the WSNs.
Acknowledgment
We would like to express our very great appreciation to the reviewers for their valuable suggestions and comments.
Список литературы Extending the WSN lifetime by Dividing the Network Area into a Specific Zones
- J. Zheng and A. Jamalipour, "Wireless Sensor Networks a Networking Perspective", book, ISBN: 978-0-470-16763-2, © 2009 IEEE.
- M. I. Hossain , M. M. Rahman, and T. K. Godder., "Improving Energy Efficient Clustering Method for Wireless Sensor Network", International Journal of Information Technology and Computer Science, Vol. 5, No. 9, PP.73-79, 2013.
- M. O. Farooq, A. B. Dogar, and G. A. Shah, "MR-LEACH: Multi-hop Routing with Low Energy Adaptive Clustering Hierarchy", 2010 Fourth International Conference on Sensor Technologies and Applications, ©2010 IEEE.
- M. Belkadi, R. Aoudjit, M. Daoui, and M. Lalam, "Energy-efficient Secure Directed Diffusion Protocol for Wireless Sensor Networks", International Journal of Information Technology and Computer Science, Vol. 6, No. 1, PP.50-56, 2014.
- F. Xiangning and S. Yulin, "Improvement on LEACH Protocol of Wireless Sensor Network", International Conference on Sensor Technologies and Applications, © 2007 IEEE.
- Z. Peng and X. Li, "The Improvement and Simulation of LEACH Protocol for WSNs", College of Information Engineering Capital Normal University Beijing China, ©2010 IEEE.
- W. Xiaoping, L. Hong, L. Gang, "An Improved Routing Algorithm Based On LEACH Protocol", Journal: International Symposium on Distributed Computing and Applications to Business, Engineering and Science, © (2010) IEEE.
- W. Jun and Z. Xin, "A Distance-based Clustering Routing Protocol in Wireless Sensor Networks", Journal: IEEE 12th International Conference on Communication Technology, (2010).
- D. K. Patel, M. P. Patel, and K. S. Patel, "Scalability Analysis in Wireless Sensor Network with LEACH Routing Protocol", ©2011 IEEE.
- L.Q. GUO, Y. XIE, C. H. YANG, and Z. W. JING, "Improvement on LEACH by Combining Adaptive Cluster Head Election and Two-Hop Transmission", ©2010 IEEE.
- C. Zhang, l. Liu, H. Li, and X. liang, "Two-Level Routing Protocol for Mobile Sensor Network Based on LEACH Algorithm", ©2010 IEEE.
- N. Kumar and J. Kaur, "Improved LEACH Protocol for Wireless Sensor Networks", ©2011 IEEE.
- V. Katiyar, N. Chand, G. C. Gautam, and A. Kumar, "Improvement in LEACH Protocol for Large-scale Wireless Sensor Networks ", ©2011 IEEE.
- Wei Bo Hu Han-ying Fu Wen, "An Improved LEACH Protocol for Data Gathering and Aggregation in Wireless Sensor Networks ", © 2008 IEEE.
- M. Tong and M. Tang, "LEACH-B: An Improved LEACH Protocol for Wireless Sensor Network", ©2010 IEEE.


