Genetic Algorithm Based Image Steganography for Enhancement of Concealing Capacity and Security
Автор: Jyoti, Md. Sabir
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 7 vol.5, 2013 года.
Бесплатный доступ
This paper proposes a Genetic Algorithm based steganography for enhancement of embedding capacity and security. Steganography is a method to provide secret communication between sender and receiver by concealing message in cover image. LSB bit encoding method is that the simplest encoding method to cover secret message in color pictures and grayscale pictures. Steganalysis is a method of detecting secret message hidden in a cover image. RS steganalysis is one of the most reliable steganalysis which performs statistical analysis of the pixels to successfully detection of hidden message in an image. This paper presents a secured steganography method using genetic algorithm to protect against the RS attack in color images. The proposed steganography scheme embeds message in integer wavelet transform coefficients by using a mapping function. This mapping function based on GA in an 8x8 block on the input cover color image. After embedding the message optimal pixel adjustment process is applied. By applying the OPAP the error difference between the cover image and stego image is minimized. Frequency domain technique is used to increase the robustness of proposed method. Use of IWT prevents the floating point precision problems of the wavelet filter. GA is used to increase the hiding capacity of image and maintains the quality of image. Experimental results are shows that the proposed steganography method is more secured against RS attack as compared to existing methods. Result showed that Peak signal to noise ratio and image utilization, 49.65 db and 100% respectively.
Steganography, Integer Wavelet Transform (IWT), Genetic Algorithm (GA), RS Analysis, Peak Signal to Noise Ratio (PSNR)
Короткий адрес: https://sciup.org/15013010
IDR: 15013010
Текст научной статьи Genetic Algorithm Based Image Steganography for Enhancement of Concealing Capacity and Security
Published Online June 2013 in MECS and Computer Science
The standard and thought of “What You See Is What You Get (WYSIWYG)” which we have a tendency to encounter typically while printing images or other materials, is not any longer precise and wouldn’t fool a steganographer as it does not always hold true. Images are over what we see with our Human Visual System (HVS); therefore, they can convey over 1000 words [1]. Steganography, the art of hiding messages inside other messages, is now gaining more popularity and is used on various media such as text, images, sound, and signals. However, none of the existing schemes can yet defend against all type of detection attacks. Using Genetic Algorithms which based on the mechanism of natural genetics and the theory of evolution, we can design a general method to guide the steganography process to the best position for data hiding [2].
In recent years, many productive steganography strategies have been proposed. Among all the strategies, LSB (least significant bit) replacement technique is wide used due to its simplicity and huge capacity. The bulk of LSB steganography algorithms embed messages in spatial domain, such as BPCS, PVD. Some others, such as Jsteg, F5, Outguess, embed messages in DCT frequency domain (i.e. JPEG images). In the LSB steganography, secret message is regenerate into binary string. Then the least significant bit-plane is replaced with the binary string. The LSB embedding achieves smart balance between the payload capability and visual quality. However, the LSB substitution method flips one half of the least-significant bits. So the artifacts in the statistics of the image area unit are easy to be detected [2].
This proposed system presents a novel technique to increase the data hiding capacity and the imperceptibility of the image after embedding the secret message. Wavelet transform method is used because it has the capability to offer some information on frequency-time domain simultaneously. This proposed work embeds the secret message inside the cover media with the least distortion and high image quality. We use Genetic Algorithm to minimize the variation between cover image and stego image by using image blocks strategy. Block based strategy preserve the cover image property and reduces the algorithm complexity as compared to single pixel substitution. In proposed work
Optimal Pixel Adjustment Process also applied to minimize the error difference between the cover and stego image.
The proposed work has been designed and implemented in the MATLAB 7.10.0.499 (R2010a). By this work best results have been obtained as compared to existing works. The proposed steganography model reduces the embedding error and provides higher embedding capacity. Detection of message existence will be very hard for those stego images that produced using the proposed method. This work shows the highest embedding capacity and security against Reversible Statistical attack.
The remainder of the paper is organized as follows. In section II, a review of the necessary background required to effectively implement our algorithm is presented. The proposed system architecture is described in Section III. The proposed algorithm is described in Section IV. After that, experimental result analysis and discussion are discussed in section V. We draw our conclusion in the VI section and future scope in last section.
-
II. Background Work
Elham Ghasemi, Jamshid Shanbehzadeh and Brahram ZahirAzami [3] propose a novel steganography scheme based on Integer Wavelet Transform and Genetic Algorithm. Simulation results show that the scheme outperforms adaptive steganography technique based on integer wavelet transform in terms of peak signal to noise ratio and capacity i.e. 35.17 dB and 50% respectively.
R. O., El.Sofy and H.H.Zayed [4] provide high hiding capacity up to 48% of the cover image size. In this paper, they have tried to optimize these two main requirements by proposing a novel technique for hiding data in digital images by combining the use of adaptive hiding capacity function that hides secret data in the integer wavelet coefficients of the cover image with the optimum pixel adjustment (OPA) algorithm.
Souvik Bhattacharya, Avinash Prashad and Gautam Sanyal [5] incorporate the idea of secret key for authentication at both the ends in order to achieve high level of security. In this paper, a specific image based steganography technique for communicating information more securely between two locations is proposed.
Kong et al. [6] proposed a new Steganalysis approach based on both complexity estimate and statistical filter. It is based on the fact that the bits in the LSB plane are randomized when secret bits are hidden in LSB plane.
Farhan and Abdul [7] have presented their work in message concealment techniques using image based steganography.
Adnan Gutub e.t. al. [8] depicts the random pixel manipulation methods and the stego-key ones in the propose work, which takes the least two significant bits of one of the channels to indicate existence of data in the other two channels. This work showed good results especially in the capacity of the data-bits to be hidden with relation to the RGB image pixels.
Shiva Kumar e.t. al [9] proposed Performance Comparison of Robust Steganography based on Multiple Transformation Techniques (PCRSMT). The cover image is divided into 64 blocks of 4*4 each and DWT is applied to every block. The resulting 1 to 64 blocks of vertical band of 2x2 each are isolated and IWT is applied to get 1x1 blocks. The DWT and IWT are applied to payload and IWT coefficients of payload are embedded with that of cover image. IDWT and IIWT are applied to derive stego image. In addition, error detection and correction technique is also applied to ensure more secured communication. It is seen that the robustness and capacity of hiding are improved with very little tradeoffs in PSNR.
Ali Al-Ataby and Fawzi Al-Naima [10] propose a modified high capacity image steganography technique that depends on wavelet transform with acceptable levels of imperceptibility and distortion in the cover image and high level of overall security.
Wang e.t. al. [12] presented a new steganography based on genetic algorithm and LSB.
Chen and Lin [13] propose a new steganography technique which embeds the secret messages in frequency domain to show that the PSNR is still a satisfactory value even when the highest capacity case is applied. By looking at the results of simulation, the PSNR is still a relaxed value even when the highest capacity is applied. This is due to the different characteristics of DWT coefficients in different subbands. Since, the most essential portion (the low frequency part) is kept unchanged while the secret messages are embedded in the high frequency sub-bands (corresponding to the edges portion of the image), good PSNR is not a imaginary result. In addition, corresponding security is maintained as well since no message can be extracted without the “Key matrix” and decoding rules.
In recent research works few algorithms have been proposed which consist of the marginal statistics that are preserved for achieving more security. Previous methods have less data hiding capacity and security against Reversible Statistical attack. As we increase the secret data length distortion increases in the final stego image as compared with cover image. All the previous works provide the basic idea to hide the data behind the image by using LSB substitution. There is no idea discussed about the increasing capacity of data so no effect on image and how to ban the RS attack. This is a critical issue in steganography model that how we increase the hiding capacity of an image or cover media without any distortion in the image quality and how to protect the method against the RS attack.
Flipping
Evaluate Regular and Singular Block Values (R M, R -M , S M , S -M )
Perform 2D-IWT
Perform RS Analysis
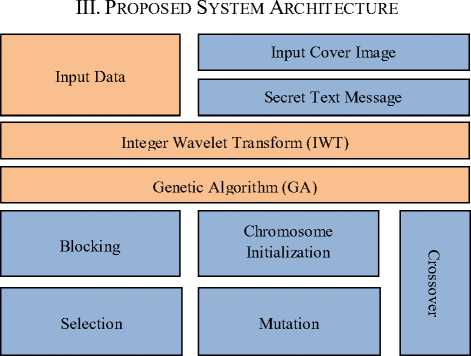
Fig. 1 Proposed system architecture
The above mentioned figure represents the general system functionalities of the developed algorithmic rule. The general system operate can be summarized by observant the figure mentioned above. The figure represents the real operative steps of the developed style. In the processing the program helps so as give a program to handle the developed model and to access the developed module. At the origination, the cover image is selected for embedding the information. Then the text data or the message is to be hand-picked so, so as to accomplish the motive of steganography the stego key appointed so at the opposite terminal the information can be retrieved by the key. Once the Key has been provided, the real application development for the RS analysis will be started with the assistance of strong GA improvement. In this technique at first the message is to be embedded in cover image. Genetic algorithmic rule is enjoying an important role for embedding more and more data in the image. In the architecture of the developed system the integer to integer wavelet transform has been done. Once the information has been embedded into the image file, then it's able to be transmitted over the channel. On the opposite hand at the receiver terminal or the extraction terminal with the accurate assignment of the stego key the information is retrieved accurately.
In the proposed work a specific image based steganographic method for hiding information in the frequency domain of the colored image is proposed. The proposed approach works by converting the colored image in frequency domain using integer wavelet transform technique through lifting scheme.
The main objective of proposed work is to improvement in hiding capacity without any distortion in image and maintains the image quality with security against serious attacks by using genetic algorithm and integer wavelet transform. The proposed method embeds the data in integer wavelet transform coefficients that based on GA and then apply OPAP algorithm to optimize the pixel adjustment for minimize the error difference between input and output image.
-
IV. Proposed Algorithm
-
A. Data embedding algorithm
The proposed method for data hiding comprises of the following steps:
-
1. Take the input standard cover image.
-
2. Take the secret text message.
-
3. Apply the secret key (in digits only).
-
4. Perform the Integer Wavelet Transform of the input cover image using lifting scheme.
-
5. Add primal ELS to the lifting scheme.
-
6. Perform integer lifting wavelet transform on image.
-
7. Divide the input cover image in 8*8 blocks.
-
8. Select any of the wavelet coefficients (redundant coefficients) from the obtained high frequency coefficients.
-
9. Generate 64 genes containing the pixels numbers of each 8x8 blocks as the mapping function.
-
10. Initialize empty matrix to store the wavelet values.
-
11. Obtain 8 x 8 blocks for R G B.
-
12. Concatenate all coefficients together.
-
13. Store the coefficient in new image.
-
14. Embed in K-LSBs IWT coefficients each pixel according to mapping function.
-
15. Select any one of the pixels from RGB.
-
16. Now the selected coefficients are processed to make it fit for modification or insertion.
-
17. Fitness evaluation is performed to select the best mapping function.
-
18. The secret message plus the message length is embedded into this processed coefficients.
-
19. This modified coefficient is now merged with the unmodified coefficients.
-
20. Calculate embedded capacity.
-
21. Apply Optimal Pixel Adjustment Process on the image.
-
22. Convert image to binary.
-
23. Finally, the inverse 2D-IWT on each 8x8 block is applied to obtain the Stego image.
-
24. Stego image will be obtained.
-
B. Data extraction algorithm
The proposed method for data extraction comprises of the following steps:
-
1. Take the desired stego image.
-
2. Apply the secret key same as given in embedding process.
-
3. Divide the stego image into 8x8 blocks.
-
4. Extract the transform domain coefficient by 2D IWT of each 8x8 block
-
5. Find the pixel sequences.
-
6. Select the desired pixels to process it.
-
7. Extract K-LSBs in each pixel.
-
8. Process the selected pixels coefficient to make it fit for extraction.
-
9. Now extract the message length and the secret message from these processed coefficients.
-
10. Secret message will be obtained.
-
C. RS-analysis algorithm
The proposed method for RS analysis comprises of the following steps:
-
1. Create function for non-positive flipping (F-)
-
2. Create function for non-negative flipping (F+)
-
3. Change LSB as per flipping
-
4. Initialize Relative number of regular block after positive flipping (R+) = 0;
-
5. Initialize Relative number of Singular block after positive flipping (S+) = 0;
-
6. Divide Stego Image into 8 x 8 blocks
-
7. For a modified block B, apply the non-positive flipping F - and the non-negative flipping F + on the block. The flipping mask M + and M - are generated randomly. The result is B' + and B' - .
-
8. Estimate F (B' + ), F (B' - ) and F (B).
-
9. Iterate step 1 and 2 for 1000 times. Define four variables to categorize the blocks by comparison of F (B' + ), F (B' - ) and F (B).
-
10. Calculate cumulative correlation (C)
-
11. Calculate correlation for non-positive flipping (Cn)
-
12. Calculate correlation for non-negative flipping (Cp)
-
13. Estimate P +R , the count of the occurrence when the block is regular under the non-negative flipping.
-
14. Estimate P +S , the count of the occurrence when the block is singular under the nonnegative flipping.
-
15. Estimate P -R , the count of the occurrence when the block is regular under the non-positive flipping.
-
16. Estimate P -S , the count of the occurrence when the block is singular under the non-positive flipping.
-
17. If Cn>C
-
18. Increase P -R
-
19. P -R = P -R +1
-
20. Else
-
21. Increase P -S
-
22. P -S = P -S +1
-
23. If Cp>C
-
24. Increase P +R
-
25. P +R = P +R +1
-
26. Else
-
27. Increase P +S
-
28. P +S = P +S +1
-
29. Compare P +R to P +S and P -R to P -S , and therefore the labels of the block are determined
-
30. If P +R / P +S >1.8
-
31. Label of the block ‘R+’
-
32. If P +S / P +R > 1.8
-
33. Label of the block 'S+'
-
34. If P -R /P -S > 1.8
-
35. Label of the block 'R-'
-
36. If P -S / P -R > 1.8
-
37. Label of the block 'S-'
-
38. At last, the blocks are categorized into 4 groups R+R-, R+S-, S +R-, S +S-
-
39. Reject the block which doesn’t fall in Step 38
-
40. Use genetic Algorithm for minimizing R- block
The blocks, which are not included in the 4 categories, are not processed in following steps. Compared with the cover image, the amounts of (R+ R-) and (S+ R-) blocks are increased in the stego-images. This phenomenon can be detected by the steganalysis method RS analysis. The final target of the proposed algorithm is to decrease the amount of R- blocks. Therefore genetic algorithm is deployed to adjust them to maintain the visual quality of image as in follow section.
-
D. Optimization technique or genetic algorithm
The proposed method for genetic algorithm comprises of the following steps:
-
1. Perform Chromosome Initialization Steps.
-
2. Select every 3 adjacent pixels in the block
-
3. Initialize maximum Fitness as 0
-
4. Initialize Alpha as 0.88
-
5. Flip second lowest bit randomly for number of time
-
6. For kk = 1: length (Block)-2
-
7. Chrom = Block (kk:kk+2);
-
8. Cp = non_negative_flipping (Chrom);
-
9. Cn = non_positive_flipping (Chrom);
-
10. Initialize e1 and e2 as 0
-
11. Compute Correlation (C, Cn, and Cp)
-
12. If Cn
-
13. e1 = 1;
-
14. End
-
15. If Cp > C
-
16. e2 = 1;
-
17. End
-
18. Apply PSNR = SNR (Chrom-Cn); // See Line-7
-
19. Apply FITNESS = alpha*(e1+e2) +PSNR
-
20. If fitness>maxfitness
-
21. maxfitness = fitness;
-
22. Chrommax = Cp;
-
23. crossover = crossover+1;
-
24. End
-
25. Replace chromosome with new one
-
26. Compute P-S and P-R
-
27. If P -S > P -R
-
28. Block is successfully adjusted
-
29. End
-
30. Compute difference, diff1 = P +R - P -R
-
31. Compute difference, diff2 = P +S - P -S
-
32. If diff1>0.05*diff2
-
33. Adjust the next block
In the proposed technique, the blocks are labeled before the adjustment. Thus, the computational hardness is reduced. The use of the genetic method avoids the exhausting searching and the algorithm is easy to be implemented.
V. Experimental Results Analysis and Discussion

a) Lena Image (JPG, 512x512)

b) Baboon Image (JPG, 512x512)

a) Lena image after embedding 4-LSBs

b) Baboon image after embedding 4-LSBs
Fig. 3 Images after embedding the secret data
Fig. 2 Input cover images
The proposed work is done on 2 set of data image as shown in previous section. Both cover images have utilization of 100% and their respective accomplished results of reversible statistical analysis are as follows:
Table 1 Various values for lena image
|
For Lena |
Initial Value |
After Embedding |
After OPAP |
|
R m- R -m |
0.0097783 |
0.0076353 |
0.0057934 |
|
S m -S -m |
0.0029662 |
0.011807 |
0.0093702 |
Table 2 Various values for baboon image
|
For Baboon |
Initial Value |
After Embedding |
After OPAP |
|
R m -R -m |
0.0059805 |
0.0076353 |
0.0056089 |
|
S m -S -m |
0.0076634 |
0.011807 |
0.0023989 |
The tables 1 and 2 have shown the values of |R m -R -m | and |S m -S -m | that represent the RS-steganalysis on the regular and singular block. It can be seen that the value of |R m -R -m | and |S m -S -m | increases from initial value before embedding and after embedding that exhibits a strong correlation in potential of RS-analysis and the designed module. At initial stage, the values are less, after embedding the message, values increases and finally after applying optimal pixel adjustment process values are decreasing. Human visual system is not able to differentiate the colored images with PSNR more than 36 dB. This proposed work embedded the messages in the k-LSBs, for k=4 and have received PSNR more than 40 (Table 3) which is considered to be a good achievement.
Table 3 Comparison of hiding capacity and PSNR for 4-LSBs
|
Cover Image |
Hiding Capacity (bits) |
Data Size (KB) |
PSNR (dB) |
|
Lena |
2137696 (4-LSBs) |
260 |
46.83 |
|
Baboon |
2137696 (4-LSBs) |
260 |
49.65 |
Table 4 Maximum hiding capacity and PSNR obtained from proposed method and its comparison with the existing methods
|
Cover Image |
Method |
Max. H. C. (bits) |
Max H. C. (%) |
PSNR (dB) |
|
Lena |
Proposed method |
2137696 |
70% |
46.83 |
|
A steganographic method based on IWT and GA [3] |
1048576 |
50% |
35.17 |
|
|
An Adaptive steganography technique based on IWT [4] |
986408 |
47% |
31.8 |
|
|
Baboon |
Proposed method |
2137696 |
70% |
49.65 |
|
A steganography method based on IWT and GA [3] |
1048576 |
50% |
36.23 |
|
|
An Adaptive steganography technique based on IWT [4] |
1008593 |
48% |
30.89 |
The above Table 4 clearly states that the proposed method is much more superior in terms of maximum hiding capacity and in terms of PSNR.
Fig. 4 shows the histogram of input cover images. Now the various algorithms such as data embedding, RS analysis and genetic applied on the cover images. The output stego image histogram after embedding the data is represented in Fig. 5.
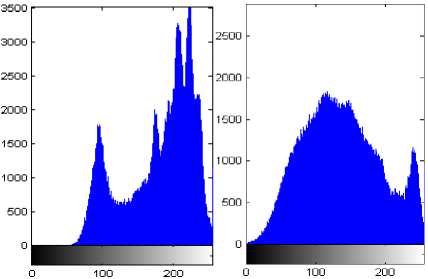
Fig. 4 Input cover image histogram
Fig. 3 shows the images after embedding with 4-LSBs. As we compare these embedded images with the input cover images (fig. 2), we realize that there are no significant changes in images. The embedded images look like the same as cover images. So the attackers cannot realize in between the communication of two parties that secret message is embedded in these images.
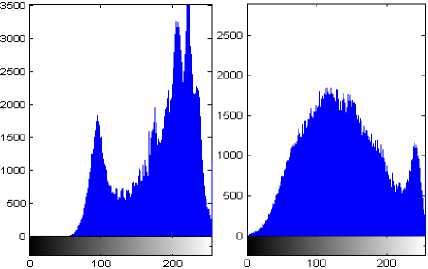
Fig. 5 Output stego images histogram of k=4 for embedding data
Fig. 5 shows that image for k=4 that there is little significant change in the stego-image histogram for 4-LSBs images, thus it is secured against any statistic attack.
[3] Method
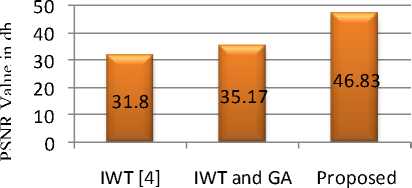
PSNR (db) for lena image
Fig. 6 PSNR comparison for lena image
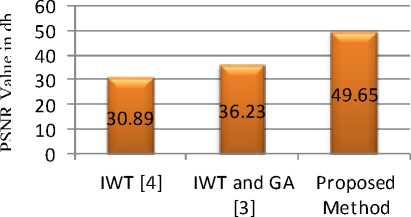
PSNR( db ) for baboon image
Fig. 7 PSNR comparison for baboon image
Fig. 6 and fig. 7 highlights the comparison of the obtained PSNR between our proposed method and methods in [3], [4]. Hence, it can be seen that the proposed system has better performance in compared to majority of the Steganographic techniques using integer wavelet transform and genetic algorithm with RS analysis.
-
VI. Conclusions
Steganography is a method that provides secret communication between two parties. It is the science of hiding a data or message or information in such a secure way that only and only sender and recipient are aware about the presence of the message. The main advantage of this type of secures communication or we can say steganography is that it does not make any attention about the message to attackers or we can say does not attract the attackers. Strongest steganalysis method which known as RS analysis detects the secret hidden message by using the statistical analysis of pixel values.
The main aim of this proposed work is to develop a steganography model which highly RS-resistant using Genetic algorithm and Integer Wavelet Transform. This proposed work introduced a novel steganography technique to increase the capacity and the imperceptibility of the image after embedding. This model enables to achieve full utilization of input cover image along with maximum security and maintain image quality. GA employed to obtain an optimal mapping function to lessen the error difference between the cover and the stego image and use the block mapping method to preserve the local image properties. In this proposed method, the pixel values of the stego image are modified by the genetic algorithm to retain their statistical characteristics. So, it is very difficult for attacker to detect the existence of the secret message by using the RS analysis technique. We applied the OPAP to increase the hiding capacity of the algorithm in comparison to other systems. However, the computational complexity of the new algorithm is high. Further, implementation of this technique improves the visual quality of the stego image same as input cover image. But, as we increase the length of the secret message, the chance of detection of secret hidden message by RS analysis also increases. The simulation results showed that capacity and imperceptibility of image had increased simultaneity. Also, we can select the best block size to reduce the computation cost and to increase the PSNR using optimization algorithms such as GA. However, future works focus upon the improvement in embedding capacity and further improvement in the efficiency of this method.
-
VII. Future Scope
This proposed work is restricted to specific functionality only. The proposed work is experimented on single computer system, not on any network. Standard input cover image is only used in this steganography method. Proposed method is not applicable on audio, video and other biometrics yet. Large message steganography cannot be performed as the embedding capacity confines the data feed.
This work could be extended to following future enhancement:
-
1. Improve the data embedding capacity and more security against all types of attacks.
-
2. Security design experimented over multiple computers or network.
-
3. The data hiding technique apply to audio, video and other biometrics.
-
4. The steganography for bulk data be performed without the embedding capacity confines the data feed.
-
5. Protect the system against histogram attack.
Список литературы Genetic Algorithm Based Image Steganography for Enhancement of Concealing Capacity and Security
- A. Cheddad, J. Condell, K. Curran and P. Mc Kevitt, Digital Image Steganography: Survey and Analysis of Current Methods, Signal Processing, Volume 90, Issue 3, March 2010, Pages 727-752.
- Samir Kumar Bandyopadhyay, Tuhin Utsab Paul and Avishek Raychoudhury, Genetic Algorithm Based Substitution Technique of Image Steganography, Journal of Global Research in Computer Science, Volume 1, No. 5, December 2010.
- Elham Ghasemi, Jamshid Shanbehzadeh and Bahram ZahirAzami, A Steganographic method based on Integer Wavelet Transform and Genetic Algorithm, 978-1-4244-9799-7/111$26.00 ©20 11 IEEE.
- R.O., El.Sofy, H.H.Zayed, An adaptive Steganographic technique based on the integer wavelet transforms 978-1-4244-3778-8/09/$25.00 ©2009 IEEE.
- Souvik Bhattacharya, Avinash Prashad, Gautham Sanyal, "A Novel approach to develop secure image based Steganographic model using Integer wavelet transform", 2010 International Conference on Recent Trends in Information, Telecommunication and Computing, 978-0-7695-3975-1/10 $25.00 © 2010 IEEE.
- X. Kong, T. Zhang, X. You, and D. Yang, "A new steganalysis approach based on both complexity estimate and statistical filter", In Proc. IEEE Pacific-Rim Conf. on Multimedia, vol. LNCS 2532, 2002, pp. 434–441.
- Farhan Khan and Adnan Abdul-Aziz Gutub, "Message Concealment Techniques using Image based Steganography", The 4th IEEE GCC Conference and Exhibition, Gulf International Convention Centre, Manamah, Bahrain, 11-14 November 2007.
- Adnan Gutub, Mahmoud Ankeer, Muhammad Abu-Ghalioun, Abdulrahman Shaheen, Aleem Alvi, "Pixel indicator high capacity technique for RGB image based steganography", WoSPA 2008 – 5th IEEE International Workshop on Signal Processing and its Applications, University of Sharjah, Sharjah, U.A.E. 18 – 20 March 2008.
- K B Shiva Kumar, K B Raja, R K Chhotaray, Sabyasachi Pattnaik, "Performance Comparison of Robust Steganography Based on Multiple Transformation Techniques", Int. J. Comp. Tech. Appl., Vol 2 (4), 1035- 1047, IJCTA | July-August 2011.
- Ali Al- Ataby, and Fawzi Al-Naima, "A Modified High Capacity Image Steganography Technique Based on Wavelet Transform", The International Arab Journal of Information Technology, Vol. 7, No. 4, October 2010.
- T.C. Manjunath, Usha Eswaran, "Digital Steganography Implementation for colored Images using Wavelet", International Journal of Communication Engineering Applications-IJCEA- Vol 02, Issue 04; July 2011, ISSN: 2230-8520; e-ISSN-2230-8539
- Shen Wang, Bian Yang and Xiamu Niu, "A Secure Steganography Method based on Genetic Algorithm", Journal of Information Hiding and Multimedia Signal Processing, Volume 1, Number 1, January 2010.
- Po-Yueh Chen and Hung-Ju Lin, "A DWT Based Approach for Image Steganography", International Journal of Applied Science and Engineering 2006. 4, 3: 275-290.


