Helper Feedback based Medium Access Control Protocol: A Reliable Co-operative MAC Scheme for MANET
Автор: Nidhi Newalkar, Piyush Kumar Shukla, Sanjay Silakari
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 2 vol.7, 2015 года.
Бесплатный доступ
A novel multirate media access control based co-operative scheme has been proposed. It has been observed that any co-operative scheme gives a better performance only if the helper nodes selected to, relay the transmission from source to destination are reliable enough. Murad Khalid et.al has already proposed a protocol [24] where more than one helper nodes are selected to improve the reliability, so that if one fails the other can be used as a backup. But in this paper focus is on selection of reliable helpers. If a helper node has a high data rate, has successfully relayed traffic in the past and also has some minimum amount of energy left , not only for relaying traffic for others but also to conduct its own transmissions, then it acts as a suitable candidate to be chosen as a helper node. Such a co-operatives scheme enhances the throughput, reliability and overall performance of the network.Simulation has been conducted to show that the proposed scheme performs better than the.
MANET, MAC, Co-operation, Helper-Feedback, Reliable
Короткий адрес: https://sciup.org/15011386
IDR: 15011386
Текст научной статьи Helper Feedback based Medium Access Control Protocol: A Reliable Co-operative MAC Scheme for MANET
Published Online January 2015 in MECS DOI: 10.5815/ ijcnis.2015.02.06
IEEE 802.11 provides physical layer multirate capability[1]. This implies that the data can be transmitted at different rates depending upon the physical channel condition. When the signal to noise (SNR) ratio is high then high data rate is to be used to get the necessary bit error rate (BER) .IEEE 802.11a supports data rates of 6,9,12 … 54 Mbps. Whereas IEEE 802.11 b supports data rates of 1,2,5.5 and 11 Mbps.This multirate capability can be efficiently exploited at the MAC layer which is closest to the physical layer by introducing the new paradigm called co-operation. Cooperative transmission [2] utilizes the indirect link between the source and the destination. This indirect link is via neighbour nodes called helpers or relay nodes[3]. These relay nodes have a better link quality to both the sender and the receiver than the direct link between sender and he receiver. Hence they can be efficiently used to improve the transmission success rate.
In figure1 suppose station S1 wants to send data to station S2. The data rate of the link between S1 and S2 is 2 Mbps, which show that the link is weak. If there exists another station S3 neighbouring to both stations S1 and S2 and the data rates from S1 to S3 is 5.5 Mbps and from S3 to S2 is 11Mbps, which implies that the channel condition is much better than the direct link. Assume the length of the packet to be L. The delay observed in the path S1-S3-S2 would be ((1/5.5) + (1/11)) L ms .So the actual data rate would be (5.5*11) /(5.5+11) = 3.7 Mbps which is much better than 2 Mbps. In [4] Nidhi et. al has suggested HF-MAC (Helper Feedback MAC) which suggest how multirate capability can be efficiently utilized, by the use of two helper nodes, having different data rates. The protocol proves to be robust, in case the direct transmission from source to destination fails. As two helper nodes have been used, one of the nodes can be used as a backup.


S2
2 Mbps

S3
Fig. 1: Co-operative Data Transmission
Apart from data rate, the HF-MAC protocol [4] discuss two important parameters. First being the energy or power constraint and the second being reliability. Energy is important for any node to relay data as well as to perform its own task. So, if the node spends all its energy relaying traffic, it will not be able to conduct its own networking tasks. So, the protocol uses only those nodes whose energy is greater than some minimum threshold level which is predetermined. Also, the reliability issue of helper nodes is taken into consideration, so that only those nodes are used which help in successful transmission. Hence, the protocol provides higher throughput and reliability based on this a co-operative MAC protocol can be devised to improve the throughput and reduce the delay.The details and the algorithm of HF-MAC will been discussed in this paper.And the improved simulation results are shown thereafter.
Sendonaris in [5] was the first one to bring out the concept of co-operation in 2003.Wireless medium has a broadcast nature and the co-operative communication takes that advantage by overhearing the ongoing transmissions, in case of weak and unreliable wireless links.
Co-operative communication can be applied in various networks like ad-hoc[6], mobile, sensor[8], mesh[7] and the latest vehicular network [9]. Co-operation is not just relaying or forwarding source’s data but it has many other flavors too. Nodes like source and the relays can co-operate to forward the data together, they can cooperate in deciding the contention window size and can also co-operate in detecting and removing the attacker nodes.
-
II. Literature Review
-
2.1 Co-operation at Physical layer
-
2.2 Co-operation at MAC layer:
-
2.3 Co-operation at the Network Layer
The notion of co-operation can be incorporated at different layers like the lower three layers (media layers) called physical layer, data link layer and the network layer [10]. Later in the following sections we will see the advantages of incorporating the co-operation at MAC layer compared to the physical layer and the network layer. Hence, our work is based on co-operation at the MAC layer.
Physical layer is the lowest layer of the OSI model. J.N. Laneman, G. W. Womell, and D. N. C. Tse [11], introduced a scheme, where the source sends the data to the intermediate node, if the destination is too far. The intermediate node amplifies the data signals and forwards it to the destination. Amplification is done to mitigate the effects of channel fading and interference. Similar to the amplification the relay decodes [12] the data sent by the source and then sends the encoded information to the destination. T. M. Cover and A. A. E. Gamal in [13] discuss the physical layer protocol where the relay node does the data compression and sends it to the destination. The compressed data is decompressed and combined with the received data at the destination end. Sendonaris E Erkip and B. Aazhang in [14] have proposed that the relay node stores the data sent by the source and then forward it to the destination.
At the MAC layer co-operation was implemented by means of relays. The thinking on concept of relays started in 2003 with rPCF (Relay Point Co-ordinated Function) by H. Zhu and G. Cao [15]. If the direct link has a low data rate and there exists a relay node such that links from source to relay and relay to a destination provides better data rate , then transmission can proceed using the relay node. Further same concept has been applied in Distributed Co-ordination Function (DCF) by introducing rDCF (Relay Distributed Co-ordination Function) [3]. A willing list is maintained by each neighbouring node (Nr) and an entry (Ni to Nj) is added if the Nr finds that the transmission rate is improved if done via Nr. This willing list is periodically advertised. If Ni gets this willing list from Nr and finds its entry then it adds it to its relay table.Another protocol named EMR (Efficient Multi-rate Relaying MAC) [17] works as a secondary protocol over primary network layer protocol which forms the main route and the main route is converted into multirate route by using EMR For the relay selection the effective throughput is calculated for various combinations of source relay and destination which is mapped to a priority value. Another protocol called DAFMAC (Decode and Forward MAC) [18] uses distributed timers for the selection of relays, where each potential relay transmits only after its delay timer expires. If the relay node does not hear ACK after SIFS duration [32-34] it sends data to the destination. Another timer based relay selection protocol is the CCBF [8] ,which uses a metric called EADV (expected advance). The node having positive value of EADV starts a timer. The node whose timer expires sends a CTS message, in response to the RTS sent by the source. CoopMAC (Cooperative MAC) protocol [16] proposed by P. Liu, Z. Tao, S. Narayan uses RSSI(Received Signal Strength Information) for the relay selection , RSSI is also used RM-MAC (Relay multi-rate MAC) [19]. Here the path via relay node is chosen only if better data rate is achieved. But in UtdMAC (University of Texas Dallas) [20] path via relay node is only kept as a backup in case direct transmission is failing. In RID (Relay with Integrated Data) [21] as well as ARC-MAC (Active Relay Based Co-operative MAC) [22] the high data rate relays which are used to assist transmissions also gain by helping. When the source transmits data to the destination via the relay, the relay encapsulates its data packet into the source data packet, and this new combined data packet is sent to the destination. In CORELA (Co-operative Relaying Enhanced Link Adaptation) [23] an enhanced link adaptation algorithm has been described. The protocol gives advantage of both the co-operative relaying and link adaptation. By cooperative relaying, reliability is improved and by link adaptation, the bandwidth efficiency is improved. Murad
Khalid et al. [24] described a co-operative MAC Protocol which makes use of two best relays on the basis of the data rate information sent by them in the RR (Relay Response) frame .The second relay is the backup relay. The two best relays are selected such that total transmission time through the first relay path plus the backup relay path is less than the direct transmission time between the source and destination.
In [31] Nidhi Newalkar et.al has been presented a comparative analysis of the various co-operative medium access control protocols. The various protocols have been compared on the basis of number of relays selected for data transmission, the selection procedure of the relays, various forms of handshake procedures applied. This study is constructive and valuable if a new protocol is to be designed. As, it can incorporate the advantages of various protocols and at the same time exclude the disadvantages of previous protocols if any.
-
2.3.1 Credit based approach:
-
2.3.2 Reputation based approach:
-
2.4 Advantages of MAC Layer co-operation
One such credit based approach is applied by using models like Packet purse model and Packet trade model developed by L. Button and J.P. Hubaux in [25]. Here a currency is introduced called nuggets, a micropayment system. The nodes that use the service has to pay for it in nuggets and the nodes that provide the service are remunerated. Hence nodes are motivated to increase their number of nuggets by relaying traffic i.e. by providing service to others. One such similar scheme is introduced by S. Zhong called SPRITE (Simple Cheat Proof Credit Based system) [26]. A new service is introduced called Credit Clearance Service (CSS),which is a centralised system which uses receipt of forwarded message for remunerating the forwarding station.
Another is the reputation based approach where the node reputation is made using observations and past history. A scheme called CORE (Collaborative reputation mechanism to enforce node cooperation in mobile ad-hoc networks) [27] defined three kinds of reputations. First is the Subjective Reputation, the second one being Indirect Reputation and last one being Functional Reputation .Subjective Reputation is the direct reputation which a node observes about other nodes. Indirect Reputation, as the name suggests is the reputation information provided by other nodes. And the functional reputation is formed by a weighted combination of subjective and indirect values. Another Co-operative algorithm based on the game theory was introduced by Vikram Srinivasan, et.al. [28] called GTFT (Generous Tit For Tat) .It has been developed to decide whether a node will accept or reject a relay request If a node has relayed more traffic than what it should or the amount of traffic relayed by the node is greater than the amount of traffic relayed for the node by others, then it would reject the request also being generous on some occasion by agreeing to relay even if it does not get the reciprocal amount of help. But this strategy was for the infinite time duration. A scheme based on rigorous analysis was introduced named FITS (A Finite-Time Reputation System for Cooperation in Wireless Ad-hoc Networks) [29]. FITS has two schemes: the first scheme is very simple, but needs a Perceived Probability Assumption (PPA); the second scheme uses more sophisticated techniques to remove the need for PPA. FITS is designed for reputation game that lasts for a finite amount of time.
The various co-operation strategies have been discussed in different layers. But the survey shows that MAC Layer co-operation is better than Network Layer.
The reasons are as follows:
-
1. Queuing delay is observed at the network layer, which is not there in the MAC layer. This is the delay when the relay node has lot many packets in the queue. In the MAC layer the packets check for the availability of the channel then only they are sent on the network. But in the network layer several routing issues arise before the packet transmission in the network. So, MAC layer provides faster retransmission
-
2. The control packets transmitted are more in the network layer i.e. RReq (Route Request), RRep
(Route Reply) before actual data transmission begins. This increase the network overhead.
So, we can conclude that MAC layer co-operation is much better than the network layer co-operation.
-
III. HF-MAC Protocol
-
3.1 Protocol Details
-
HF-MAC (Helper Feedback Medium Access Control) is an extension to the existing 2rcMAC protocol. In that, two relays were used to transmit data between the source and the destination. One relay acts as a helper and the other relay acts as a backup which jumps in to transmit the data if ACK is not received or some failure in the transmission occurs dueto interference or collision. But this protocol does not consider the reliability of relays .The relays are high data rate nodes but may fail to transmit data due to interference or some other reasons. In HF-MAC proposed as shown in figure 2, in order to choose the helper nodes, three parameters have been taken. First is the data rate between the source and relay and the relay and destination. Second is the relay reliability and the third is the energy left inthe relay to transmit the source’s data to the destination.
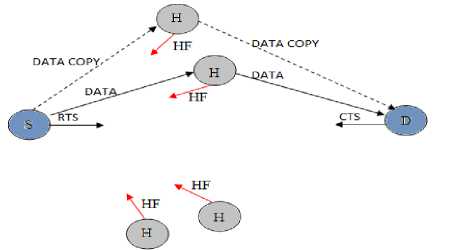
Fig. 2: HF-MAC
-
1. When the nodes are idle they passively monitor the neighbour’s ongoing transmissions. The transmission power is fixed, so the difference of the transmission power and the received power gives the idea of path loss and ultimately the rate.
-
2. Whenever a packet arrives in the source (S) node’s buffer, it senses the channel. If the channel is found idle then after DIFS duration, the source sends the RTS frame. But if the channel is found busy then transmission is deferred and node goes into back-off.
-
3. If the Request to Send (RTS) is correctly received by the destination (D) and it has no pre running transmissions, it sends the Clear to Send (CTS) to the source. The RTS and the CTS messages are
-
4. Each helper node being a part of an ad-hoc network has some limiting constraints like limited battery life, limited computation capacity and limited storage area. Here we assume that the nodes are nor selfish nor malicious. They just help the transmissions and in return this help may also be reciprocated to them by others. Now a problem arises when multiple helpers offer help at the same time. This contention between the helpers may be resolved by using Helper Feedback frame (HFF). The HFF as in figure 3 is an eight slot frame with 7 bits per slot. Each slot represents a different rate category [44].
-
5. After the HFF are received by the source node, it starts its search for the optimal helpers (h1, h2).
broadcasted in the wireless channel, so they are overheard by the neighbouring nodes, which may act as helpers for better throughput.
For instance, the third and fourth slots are for contention among hepers, with each relay having a combined rate of 1.69 Mb/s (2 * 11/ 2 + 11). The HF frame has a duration of 60 μs [43]. Each helper node remains precisely coordinated after receiving the CTS message and knows when the HF frame starts and ends. A helper node on the basis of the source-to-helper node and helper-to-destination node data rate estimation, decide on the suitable rate slot and then sends a single-bit feedback in a randomly picked bit interval location of the HF frame. The helper nodes remain idle if they do not meet the rate requirements in the HF frame slots.
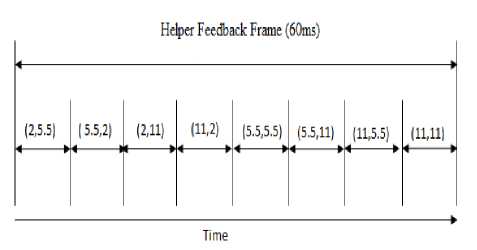
Fig. 3: HF frame
The helpers are called optimal if:
-
(i) For the first helper h1
Combined Rate :
(Rc = (RSh1*Rh1D) / (RSh1+Rh1D))
-
(ii) For the second helper h2
-
(iii) Rh2D> (α/ (α-1))RSD, where α = Rc/RSD
-
(iv) Power constraint > Min Power
-
(v) Helper Reliability > Threshold
Algorithm :
-
1. BEGIN
-
2. INITIALIZE NODE = IDLE
-
3. CHANEL SENSING
-
4. If (NODE_BUFFER == EMPTY) GOTO 2
-
5. NODE HAS DATA TO SEND
-
6. If (CHANNEL == BSY) RandomBackoff
-
7. If (CHANNEL == IDLE for DIFS duration )
-
8. { send RTS to DEST_NODE
-
9. Wait for SIFS duration
-
10. If ( CTS_RECEIVED == FALSE) THEN Random Backoff GOTO 3
-
11. Else Wait for HF_FRAME
-
12. If(HF_FRAME_RECEIVED == FALSE)
-
13. { Send DATA to DEST_NODE
-
14. If (CHK_SUCCESS == TRUE) GOTO END
-
15. Else FAILURE GOTO 3
-
16. } Else
-
17. { SELECT 2_BEST_ HELPERS such that
-
18. ((RATE == REQ)&&(NO_OF_FAIL
-
19. If(2_BEST_ HELPERS_SELECTED == TRUE)
-
20. { Send DATA to 2_BEST_ HELPERS
-
21. HELPER_1 send DATA to DEST_NODE
-
22. If (CHK_SUCCESS == TRUE) GOTO END
-
23. Else send DATA via HELPER_2
-
24. If (CHK_SUCCESS == TRUE) GOTO END
-
25. Else { NO_OF_FAIL ++
-
26. If (RETRY_LIMIT_EXCEEDED == TRUE)
-
27. { DELETE packet from BUFFER
-
28. GOTO 1
-
29. } Else GOTO 6
-
30. }
-
31. ElseIf(1 HELPER FOUND == TRUE)
-
32. { Send DATA to DEST_NODE
-
33. If (CHK_SUCCESS == TRUE) GOTO END
-
34. Else{ Send DATA via HELPER
-
35. If (CHK_SUCCESS == TRUE) GOTO END
-
36. Else { NO_OF_FAIL ++
-
37. If (RETRY_LIMIT_EXCEEDED == TRUE)
-
38. { DELETE packet from BUFFER
-
49. GOTO 1
-
40. } Else GOTO 6
-
41. }}}}}
-
42. END
(POWER>MIN_POWER)
CHK_SUCCESS
-
1. If (ACK_RECEIVED after SIFS == TRUE)
-
2. { SUCCESS
-
3. RETURN TRUE}
-
6. If the above conditions are met by the two helpers they will be called optimal and will be engaged for the further transmission. This is shown in figure 4. Now, the source sends data to both the helpers. The first best helper sends the data first. But, if due to some interference or collision, if the acknowledgement (ACK) is not received by the source within 2SIFS duration then the parameter of the node (No. of failures) is incremented. And then immediately the second relay jumps in to forward the data to the destination. If the destination receives the data, it sends ACK. If ACK is not received within the time span, the no. of failures of this node is also incremented. Then the selected helpers clear there buffers and backoff is applied.
-
7. If only one optimal helper is identified then the source uses it for backup purpose and uses the direct transmission strategy. This is shown in figure 5.But if both the direct transmission as well as the backup helper fails then the No. of failures of backup helper is incremented and back-off is applied.
-
8. If no optimal helper is found as in figure 5,then any helper is chosen which gives better data rate.
-
9. If no helper feedback is received then direct transmission strategy is adopted where after the RTS and CTS exchange between the source and the destination.The DATA frame is sent to the destination, and after SIFS duration ACK sent by the destination is received by the source .
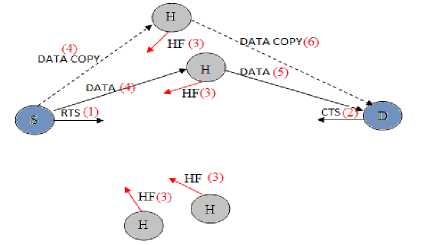
Fig. 4: HF-MAC with two optimal helpers
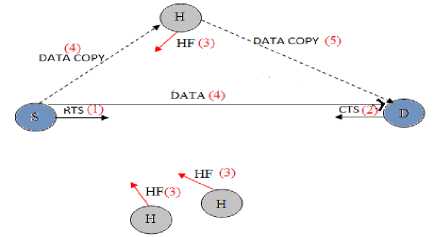
Fig. 5: HF-MAC with one or no optimal helper
The flowchart for the above algorithm is shown below in figure 6.
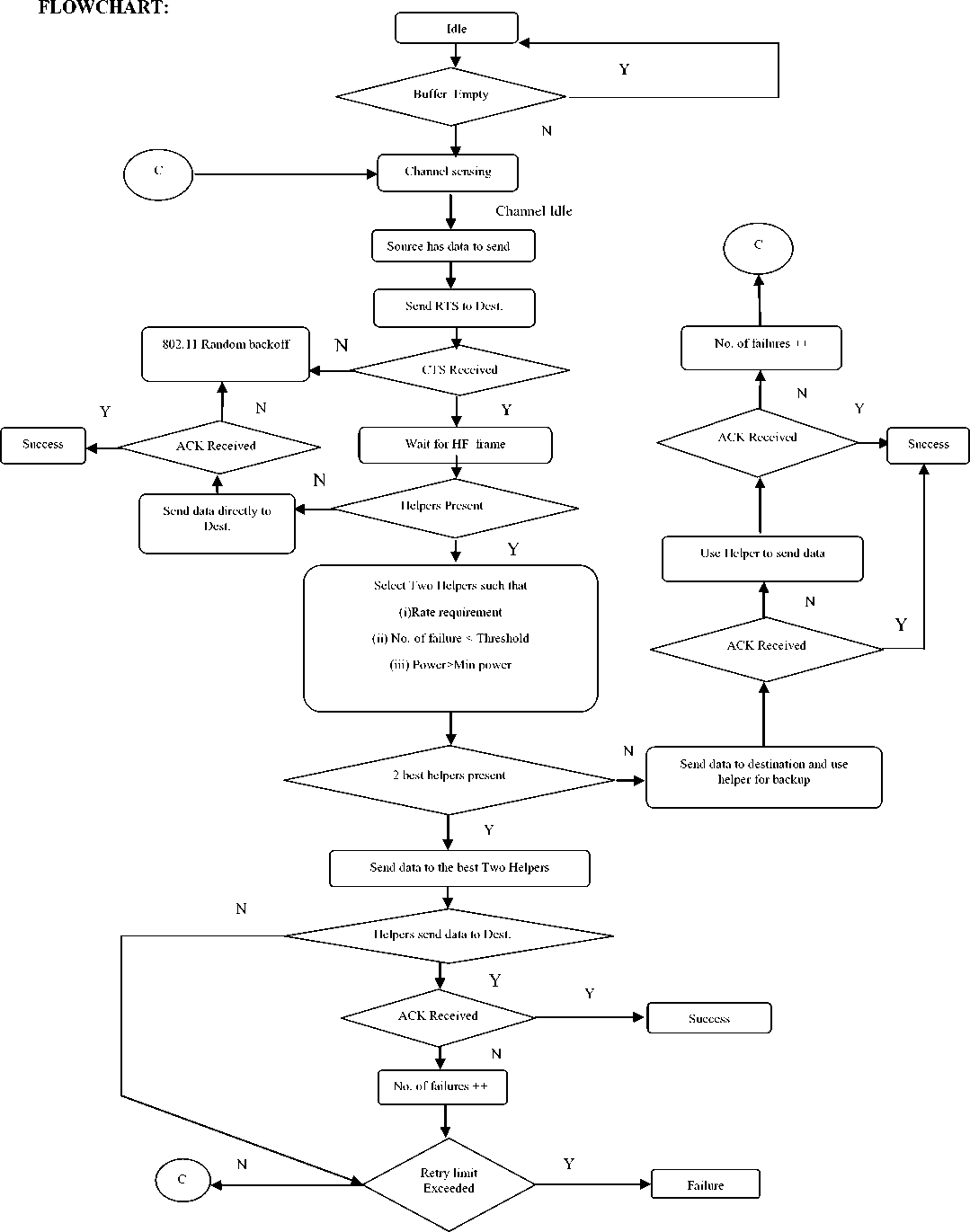
Fig. 6 : Flowchart of HF-MAC Protocol
-
IV. Simulation Results
In this section , we use NS-2 to evaluate the performance of HFMAC in comparison to the existing protocols IEEE 802.11 MAC and the protocol proposed [24] by Murad Khalid et al. called 2rcMAC.First we simulated and environment where all nodes of the ad-hoc network are in the transmission range.We vary the number of nodes from 10 to 50.All the nodes are randomly distributed.The important simulation parameters are listed in Table 1.Comparative graphs for the network throughput , packet delivery ratio and end to end delay are shown in figure 7 , figure 8 and figure 9 respectively.
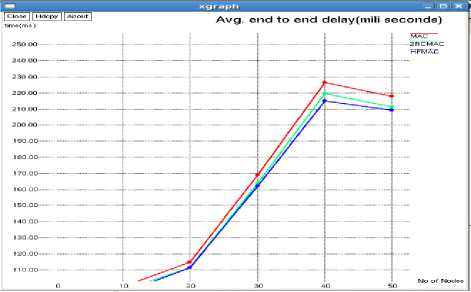
Figure 9: End to end delay versus No. of nodes
Table 1 : Important Parameters of Simulation
|
Parameter |
Value |
|
MAC header/PHY header |
272 bits / 192 bits |
|
RTS/CTS/ACK |
160bits/112bits/112 bits |
|
CW min / CW max |
32 slots /1024 slots |
|
Slot time/ SIFS/ DIFS |
20 µs /10 µs/ 50 µs |
|
Retry limit |
7 |
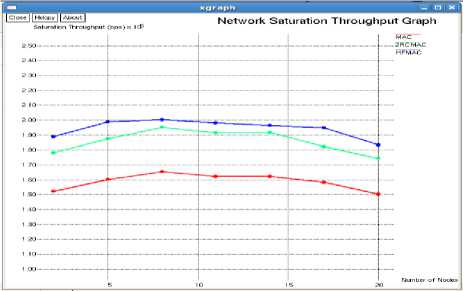
Fig. 7: Throughput versus No. of nodes
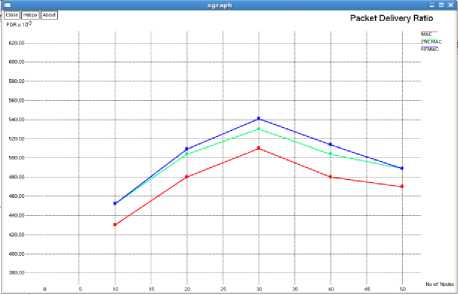
Figure 8: Packet Delivery Ratio versus No. of nodes
-
V. Conclusion
The proposed protocol proves to be robust, in case the direct transmission from source to destination fails. As two helper nodes are being used, one of the nodes can be used as a backup. Apart from data rate, the protocols discuss two important parameters. First being the energy or power constraint and the second being reliability. Energy is important for any node to relay data as well as to perform its own task. So, if the node spends all its energy relaying traffic, it will not be able to conduct its own networking tasks. So, the protocol uses only those nodes whose energy is greater than some minimum threshold level. Also, the reliability issue of helper nodes is taken into consideration, so that only those nodes are used which help in successful transmission. Better performance in terms of Throughput, PDR and Delay has been received. The simulation is run for a maximum of 50 nodes and it is observed that the throughput obtained is best when the number of nodes are 10 or 20.So, the protocol performs its best when node density is less.
In future attacker and malicious nodes can be identified and discarded .These nodes may disrupt the proper functioning of the network. So, the protocol can be extended to study such kind of nodes, bring in more security and take appropriate action against them. Currently HF-MAC has been implemented for the ad-hoc network with very less mobility; it can be further enhanced to work on other kinds of networks like VANET (Vehicular Ad-hoc Network) and Delay Tolerant Network (DTN) network, where the node mobility is very high and also sensor networks.
Список литературы Helper Feedback based Medium Access Control Protocol: A Reliable Co-operative MAC Scheme for MANET
- A. Kamerman and L. Monteban, "WLAN-II: A high performance wireless LAN for the unlicensed band," Bell Labs Technical Journal, summer 1997.
- A. Nosratinia, T.E. Hunter, and A. Hedayat, "Cooperative communication in wireless networks," IEEE Communications Magazine, vol. 42, no. 10, pp. 74–80, April 2004.
- H. Zhu and G. Cao, "rDCF: A relay-enabled medium access control protocol for wireless ad-hoc networks," in Proceedings of IEEE INFOCOM, 2005.
- Nidhi Newalkar, Sanjay Silakari and Piyush Kumar Shukla, "A Reliable Co-operative MAC Scheme with Helper Feedback". International Joint Conferences on CIIT 2012,CENT 2012, CSPE 2012 & CIITCom 2012 Springer LNICST pp. 192-197, Chennai, 3 – 4 Dec . 2012.
- A. Sendonaris, E. Erkip and B. Aazhang, "User Cooperation Diversity , Part I: System , IEEE Transactions on Communications , vol. 51, no. 11, Nov. 2003.
- J.M. Bahi, M. Eskandar and A. Mostefaoui, "A robust cooperation approach for mobile multimedia ad-hoc networks", IEEE 2008.
- Klaus Fosmark, "Cooperative Communication in Mesh Networking", Available: http://grouper.ieee.org/groups/802/15/pub/05/15-05-0129-00-0005-cooperative-communication-in-mesh-networking.ppt
- Long Cheng, Jiannong Cao, Canfeng Chen, Hongyang Chen, Jian Ma and Joanna Izabela Siebert, "Cooperative contention-based forwarding for wireless sensor networks". IWCMC, July 2010, Caen, France.
- Tingting Chen and Liehuang Zhu, "Stimulating co-operation in vehicular ad-hoc Network: A coalitional game theoretic approach". IEEE Transactions on Vehicular Technology Vol 60, No. 2 February 2011.
- Piyush Kumar Shukla, Sarita Singh Bhadauria, Sanjay Silakari, "Attack Resilient & Adaptive Medium Access Control Protocol, " IJCSIS (International Journal of Computer Science & Engineering), Vol. 11. No. 03, March, 2013.
- J.N. Laneman, G. W. Womell, and D. N. C. Tse, "An efficient protocol for realizing cooperative diversity in wireless networks," in Proc. IEEE International Symposium on Information Theory (ISIT), June 2001.
- J. N. Laneman and G. W. Wornell, Energy- efficient antenna sharing and relaying for wireless networks," in Proc. IEEE wireless communications and networking, Sept. 2000.
- T. M. Cover and A. A. E. Gamal, "Capacity theorems for the relay channel," IEEE Transactions on Information Theory vol. 25, no. 5. Sept 1979.
- A. Sendonaris, E. Erkip and B. Aazhang, "User Cooperation Diversity , Part I : System , IEEE Transactions on Communications , vol. 51, no. 11, Nov. 2003
- H. Zhu and G. Cao, "On improving the performance of IEEE 802.11 with relay-enabled PCF," Mobile Networking Appl. (MONET), vol. 9, no. 4, pp. 423–434, Aug. 2004.
- P. Liu, Z Tao and S. Narayan, "CoopMAC A co-operative MAC for wireless LANs". IEEE J. Sel. Areas Communication vol. 25 Feb 2007.
- J. S. Pathmasuntharam, A. Das, and K. Gupta, "Efficient multi-rate relaying (EMR) MAC protocol for ad hoc networks," in Proc. Of IEEE ICC'05, Seoul, Korea, July 2005.
- Brett Hagelstein , Mehran Abolhasan, Daniel Franklin and FarzadSafaei, "An efficient opportunistic cooperative diversity protocol for IEEE 802.11 networks , IWCMC, 2010, Caen, France.
- WenbinZhang ,Xiaozong Yang and Shaochuan Wu , "A new improved MAC scheme: RM-MAC", 6th International ICST Conference on communications and networking in China (CHINACOM), Aug 2011.
- N. Agarwal, D. ChanneGowda, L. Kannan, M. Tacca, and A. Fumagalli, "IEEE 802.11b cooperative protocols: A performance study," in Proc. networking, vol. 4479, LNCS, 2007, pp. 415–426.
- Sayed, S., "RID Relay with integrated data for multi-rate wireless cooperative networks". 5th international conference on Broadband Communications, Networks and Systems, BROADNETS 2008.
- Chang-Yeong Oh and Tae-Jin Lee "MAC protocol using cooperative active relays in multi-rate wireless LANs", IFIP International Conference on wireless and optical communications networks, 2009.
- Kaleshi, D. and Zhong Fan, "CORELA: A cooperative relaying enhanced link adaptation algorithm for IEEE 802.11 WLANs" 8th International symposium on wireless communication systems, 2011.
- Murad Khalid, Yufeng Wang, In ho Ra and Ravi Shankar, "Two relay based co-operative MAC protocol for wireless ad-hoc network". IEEE Transactions on vehicular technology Vol 60, No. 7 September 2011.
- L. Buttyan and J.P. Hubaux, "Enforcing service availability in mobile ad-hoc WANs", Proc. of Workshop on Mobile Ad-hoc networking and Computing (MobiHOC), Boston, USA, August 2000.
- Zhong, S., "Sprite: A simple, cheat-Proof, credit-based system for mobile ad-hoc networks". Proceedings of IEEE Infocom. San Francisco, CA, USA, 2003.
- P. Michiardi and R. Molva, "Core: a collaborative reputation mechanism to enforce node cooperation in mobile ad hoc networks". Communication and Multimedia Security Conference September 2002.
- Vikram Srinivasan, Carla Fabiana and PawanMuggehalli, "An analytical approach to the study of co-operation in wireless ad-hoc network", IEEE Transactions on wireless communications Vol 4, No. 2 March 2005.
- Tingting Chen, Fan Wu, and Sheng Zhong, "FITS: A finite-time reputation system for cooperation in wireless ad-hoc networks". IEEE Transactions on computers. , vol. 60, no. 7, July 2011.
- Piyush Kumar Shukla, Sarita Singh Bhadauria, Sanjay Silakari "ARA-MAC: A Qualifying Approach to improving Attack Resiliency and Adaptability in Medium Access Control Protocol for WLAN 802.11," International Journal of Computer Applications (0975 – 8887) Volume 49– No. 19 , pp.01—10, 2012.
- Nidhi Newalkar, Sanjay Silakari and Piyush Kumar Shukla, "Comparative Analysis of Co-operative MAC Schemes," ISCOS, International Symposium on Cloud and Services Computing, IEEE, Conference, pp. 42-48, 2012.
- Saman Atapattu, Yindi Jing, Hai Jiang, "Relay Selection Schemes and Performance Analysis Approximations for Two-Way Networks", IEEE TRANSACTIONS ON COMMUNICATIONS, VOL. 61, NO. 3, PP. 987-998, March, 2013.
- Bin Cao, Gang Feng, Yun Li, and Chonggang Wang, "Cooperative Media Access Control With Optimal Relay Selection in Error-Prone Wireless Networks", IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 63, NO. 1, pp. 252-265, Jan. 2014.
- Xiaoyan Wang, Jie Li and Feilong Tang, "Network Coding Aware Cooperative MAC Protocol for Wireless Ad.-Hoc Networks," IEEE Transactions on Parallel & Distributed System, Vol. 25, No. 1, pp. 167-179, January, 2014


