Hybridization of Discrete Wavelet and Singular Value Decomposition using Redundant Wavelet for Robust Video Watermarking
Автор: Sakshi Batra, Harpal Singh
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 5 vol.8, 2016 года.
Бесплатный доступ
The distribution of multimedia has revolutionized the web technology at very fast pace. Duplication of computerized information are created and conveyed through the web technology. Unlawful acts, for example, tampering, forging, copyright isolations and frauds on multimedia data are becoming very common in the society. Digital watermarking is one such innovation that has been produced to shield multimedia data from illegal manipulations. The advancement of technical solutions in view of watermarking method for copyright assurance has been a subject of active research amid the most recent decade. In this paper, hybridization Discrete Wavelet Transform (DWT) and Singular Value Decomposition (SVD) using redundant wavelet is proposed for robust digital video watermarking. The results of combining the two transform using redundant wavelets shows that the performance of proposed video watermarking scheme is enhanced and satisfies the requirement of imperceptibility. The presented results also showed that the scheme has the capacity to withstand an assortment of video processing attacks.
Digital Watermarking, Discrete Wavelet Transform, Discrete Cosine Transform, Discrete Fourier Transform, Singular value decomposition
Короткий адрес: https://sciup.org/15013977
IDR: 15013977
Текст научной статьи Hybridization of Discrete Wavelet and Singular Value Decomposition using Redundant Wavelet for Robust Video Watermarking
Published Online May 2016 in MECS DOI: 10.5815/ijigsp.2016.05.05
Opulent speed computer networks, the Internet and the Web technology have changed fundamentally the way in which digital information is conveyed [1]. The boundless and simple gets to multimedia contents and eventuality to make endless duplicate without having loss of extensive loyalty have propelled the necessity for advanced authentic administration. Digital watermarking is an innovation that can fill this need. A far reaching numerous watermarking plans have been offered to shroud copyright marks and other data in computerized pictures, video, sound and other sight and sound articles [2].
Words generally can't do a picture justice. But, there are numerous marvels which are not satisfactorily caught by a solitary stationary photograph. The undeniable liberty to stationary picture is video. The video turns into a critical device for the amusement and educational diligent. Though the amusement diligent is losing billions of dollars consistently because of the new data business where the computerized information can be copied and re-conveyed at basically no expense. One conceivable answer for this issue is video watermarking. This includes the expansion of an impalpable and imperceptible mark to video document. The implanted watermark ought to be impervious to normal strategies of signal processing, and, in the meantime, it ought not to disturb the original video file’s quality [3]. The principle reason of digital watermarking is to insert data impalpably and vigorously in the hostile information [4]. Regularly the watermark having data about the source, ownership, destination, replica control, transaction and so on.
The rest of the paper is organized as follows. In section two, we briefly describe the related work. Section three gives the overview of video watermarking and related issues. Present scenario is defined in section four. The watermark embedding and extraction process of the proposed video watermarking are described in section five. In section six, the experimental results and discussions are presented. The conclusions based on the experiential results and study are stated in section seven.
-
II. Related Work
N. R. Bamane et al. [1] performs a near investigation in light of robustness and computational multifaceted nature of diverse watermarking algorithms. In this paper they have performed a study on accessible video watermarking systems, feasibility ponder on watermarking strategies meeting the necessities and they have recommended the transform domain method for digital video watermarking with respect to implanting imperceptible watermarks behind the video. The execution investigation demonstrated in this paper for diverse watermarking systems considering distinctive Parameters. By observing this paper one can say that DWT and PCA systems have better execution as analyzed than different strategies.
Bibi Isac et al. [2] give a survey of a few of the proposed picture and video watermarking methods utilizing neural systems. A large portion of these strategies given in this paper have possessed the capacity to fulfill the fundamental necessity of watermarking i.e. the extraction procedure does not require the original signal or at the end of the day, the algorithm is visually impaired. Additionally in few papers it is found that work is done in spatial domain, while others work are completed in frequency domain by using transformation techniques. The neural systems that are utilized incorporate Back propagation Network (BPN), Counter Propagation Network (CPN), Full Counter Propagation Network and Cellular Neural Network (CNN). The robustness of these algorithms are tested regarding different assaults like blurring, median filtering attack, low-pass filtering attack , cropping attack and salt and pepper noise attack. Each of these algorithms has their own favorable circumstances and weaknesses portrayed in this paper.
Prachi V. Powar et al. in [3] has proposed a scheme using matlab simulink and has embedded a watermark in a video resulting in the watermarked video being robust against various attacks that can be carried out on that video. The authors carried out implementation of robust video watermarking scheme using Discrete Wavelet Transform. Due to multi resolution characteristics of DWT the scheme proposed in this paper is robust against several attacks.
-
S. Nafees Ahmed et al. in [4] presented a video watermarking algorithm which is robust against the attacks of frame dropping, averaging and statistical analysis, in this video data embedding scheme the embedded secret data is randomly segmented and reconstructed without knowing the original host video. Secret data is embedded in individual video frames using the frequency domains of DWT. Finally they have compared PSNR reading for the Original Video & Watermarked Video. Their proposed technique works on gray-scale images. A binary image was used as a watermark.
Jigar Madia et al. in [5] proposed a watermarking technique to authenticate the video to tactically place watermark in multiple frames of video. The proposed algorithm used dynamic frame selection process making it impossible to find a pattern in selection. They furthermore provide a corruption technique to corrupt the videos if information is tried to be extracted with incorrect keys. The proposed algorithm is a unique blend of both visible and invisible watermarking techniques aimed at providing secure and efficient watermarks across a video. They have implemented and experimented it using Java and some third party software’s like 'Video to JPEG Convertor' and 'Total Video Convertor'.
M. Mohamed Sathik et al. in [6] proposed an innovative watermarking scheme which utilizes the perceptual information of the image content to generate watermark. According to this, the disparity values between the low frequency subband of wavelet domain and rescaled version of original image are identified as the watermark and disordered with the help of Arnold transform. According to this paper, a binary watermark pattern was constructed from the content of the host image itself and was disordered with the help of Arnold transformation.
Lama et al. [7] proposed two video watermarking algorithms which are based on the algebraic transform of Singular Value Decomposition (SVD) and achieving fair level of imperceptibility but fail to achieve reasonable robustness against most of the attacks
Hamid Shojanazeri et al. in [8] presented the state of the art in video watermarking techniques. It provides a critical review on various available techniques. In addition, it addresses the main key performance indicators which include robustness, speed, capacity, fidelity, imperceptibility and computational complexity and hence, concluded that watermarking techniques in frequency domain have better performance than schemes proposed in spatial domain.
Rowayda A. Sadek et al. in [9] proposed an experimental survey for the SVD as an efficient transform in image processing applications. Despite the well-known fact that SVD offers attractive properties in imaging, the exploring of using its properties in various image applications is currently at its infancy. Since the SVD has many attractive properties have not been utilized, this paper contributes in using these generous properties in newly image applications and gives a highly recommendation for more research challenges.
-
S. S. Bedi et al. in [11] presented a novel technique to protect the copyright information by embedding a bit map image as watermark into the frames of videos in such a way in could be extract to proof the ownership from the video contents.
The Literature review carried out still has some flaws and drawbacks. Many of existing watermarking schemes are not able to properly protect videos as are not robust against attacks such as crop attack, rotation, mean and median filtering. Video Watermarking is subjected to various issues such as being exceptionally vulnerable to piracy attacks, including frame averaging, frame dropping, frame swapping, statistical analysis which are not present in image watermarking. By development in possible ways of piracy in multimedia, researchers design more complex algorithms to cover the robustness and fidelity of videos while this complexity make overhead and is in contrast with real time applications. The quality of an extracted watermark is too bad due to various attacks during transmission and noise. As per the survey, Watermark is not very robust or it doesn’t withstand malicious attacks.
-
III. Video Watermarking
The abrupt increment in watermarking stake is most likely because of the expansion in interest over copyright assurance of content. Nonetheless, current innovation does not ensure their copyrights legitimately [12]. In the ancient times, encryption and control access methods were utilized to ensure the ownership of media. There are some attractive qualities of productive watermarking strategies, embracing impalpability, robustness, and security. Impalpability is the level of perception similitude in between the first and watermarked signals. To implant the watermark in a discrete, inconspicuous form such that the watermark is unpretentious under easygoing perception [5]. Robustness is the watermark's strength upon controls for example, lossy compression, linear and nonlinear filtering, scaling, and cropping. Security is the watermark's capacity to oppose antagonistic assaults. Assaults are not constrained to evacuation of the watermark, yet rather incorporate watermark judgment or falsification, conspiracy, and uncertainty assaults. Clearly, it is attractive to have a subtle, powerful, and secure watermarking procedure.
Advanced watermarking has as of late been reached out from static pictures to video [13]. Numerous algorithms have as of now been depicted in the literature. It goes from the basic adjustment of watermarking algorithm at first intended for static pictures to the meaning of particular video watermarking plan. Evidently any picture watermarking strategy can be stretched out to watermark videos, yet actually there are many challenges that need to meet by video watermarking strategies as compared to that in image watermarking plans, for example, expansive quantity of intrinsically excess information in between frames, the unbalance between the motion and motionless locales, continuous prerequisites in the video broadcasting and so forth [6].
-
IV. Present Scenario
The expansion of digitized media because of the fast development of arranged interactive media frameworks has made a dire requirement for copyright enforcement advances that can secure copyright ownership of multimedia objects [14]. Noticeable characteristics of possession or realness have been utilized for a considerable length of time as stamps, seals, marks. In any case, with the present circumstance of information control innovations, vague computerized imprints are required.
All together for a computerized watermarking procedure to be viable it ought to be subtle, and strong to regular picture controls such as compression, filtering, rotation, scaling cropping, mean, median assaults among various advanced signal handling operations.
Furthermore, by advancement in conceivable methods for piracy in multimedia, analysts outline more unpredictable calculations to cover the power and loyalty of recordings while this multifaceted nature make overhead and is interestingly with real time applications [7]. The nature of an extracted watermark is too bad because of different attacks during transmission and noise.
Fundamentally in video watermarking, watermark can be implanted in spatial domain and transform domain. Generally utilized frequency-domain transforms include the Discrete Wavelet Transform (DWT), the Discrete Cosine Transform (DCT), Discrete Fourier Transform (DFT) and Singular Value Decomposition (SVD) [15]. Nonetheless, DWT has been utilized as a part of digital image watermarking as often as possible because of its astounding spatial localization and multi-resolution attributes, which are like the hypothetical models of the human visual framework. Transform domain techniques are vigorous when contrasted with spatial domain methods. This is because when picture is reverse changed, watermark is conveyed sporadically over the picture, making the assailant hard to peruse or adjust. Because of the certainty of restriction in both spatial and recurrence space, wavelet change is the best ideal transform among every single other transforms. And we consider the Singular Value Decomposition (SVD), which could be an alluring change for watermarking [8]. Generally, SVD is utilized in image compression and other signal processing scenarios.
-
V. Problem Formulation
Selling and Marketing of art works is easier utilizing multimedia methods and web yet it likewise accompanies the hard truth that such technique gets to be vulnerable to anti business activities like copying, Thus Copyright Protection is of most extreme significance to encourage widespread and fool proof utilization of such propelled advancements. Digital Watermarking is one such method that fire walls content owners from mischievous elements. In simpler terms, a watermark is utilized as data to approve the information and ensure copyrights.
Video watermarking that need extraordinary attention to be applied while working with it. Video Signal frames are inherently superfluous in nature and because of the substantial measure of digital data included; they turn out to be very exposed to pirate attacks, which utilize strategies, for example, frame swapping, frame dropping and frame averaging to execute this heinous crime. Such regions are relatively more vulnerable to statistical comparison and removal of watermarks from the same. Furthermore, Original Videos should not be utilized amid watermark detection because of its substantial size and the element of inconvenience that it carries with itself. To overcome such issues, another video watermarking strategy is thus proposed. The issues specified above can be understood by applying scene change detections and scrambled watermarks in a video. To increase the robustness of the scheme, several hybrid approaches are proposed.
-
VI. Proposed Work
A new blind video watermarking algorithm is proposed in light of the Singular Value Decomposition and Discrete Wavelet Transform. The watermarks can be identified without the original video or whatever other data of the first solitary values. This paper describes a digital video watermarking algorithm based on combining two transforms; DWT and SVD.
This system uses different techniques of embedding watermarks on different layers by using Hybrid systems. Discrete Wavelet Transform, Redundant Wavelet Transform and Singular Value Decomposition techniques, all these techniques are used in this work. This process is blind as the watermark values are changed into binary values. The new watermarking scheme proposed is based on hybrid model using singular values from watermark image after resizing and using singular values of the wavelet decomposed frame’s selected layer and also embedding the watermark key obtained using key generation with watermarks decomposed orthogonal values and embedding in the 4-level decomposition of the selected low energy band of the decomposed band.
Hence, there is no need of the original video in the extraction algorithm. This facilitates a blind check of the embedded binary signature by matching the watermark generated signature with the user key. In case the signatures do not match, it is extracted as per the second embedding algorithm. Moreover, essential steps have been taken to overcome the chances of Visual Perceptibility Degradation caused due to watermarking so that the robustness of this technique.
Fig. 1 shows the block diagram for the Proposed Watermarking Embedding Process which uses Discrete Wavelet Transform (DWT), Redundant Wavelet Transform (RWT) and Singular Value Decomposition (SVD) techniques. Moreover, it uses a Secret key which is entered by the user at the embedding time and the same key is used for the extraction for the watermark at the extraction time. And in this technique there are two possible ways of extracting watermarking one is simple technique which is combination of DWT and SVD and other is Alternate technique that is combination of DWT and RWT.
Fig. 2 shows the block diagram for the Proposed Watermarking Extraction Process As discussed in the Embedding process a secret key is used for the embedding and extraction of the watermark. Thus, if key doesn’t match then a simple message will be given that Key doesn’t match, Watermark cannot extract. Moreover, when key is entered during extraction process then it will matches that previous and decide whether simple extraction will be there or alternate extraction.
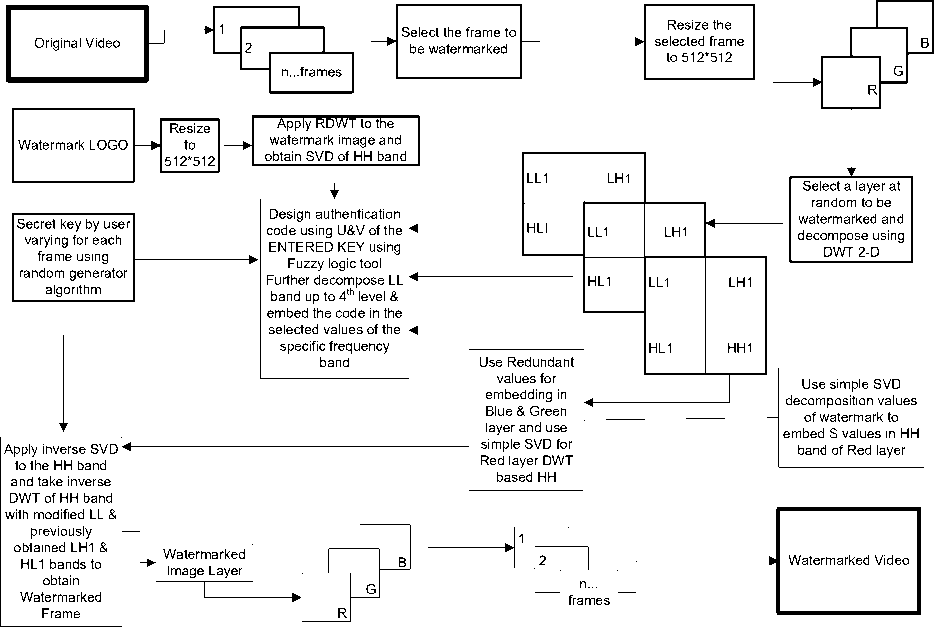
Fig.1. Proposed Watermarking Embedding Process
Video to frames
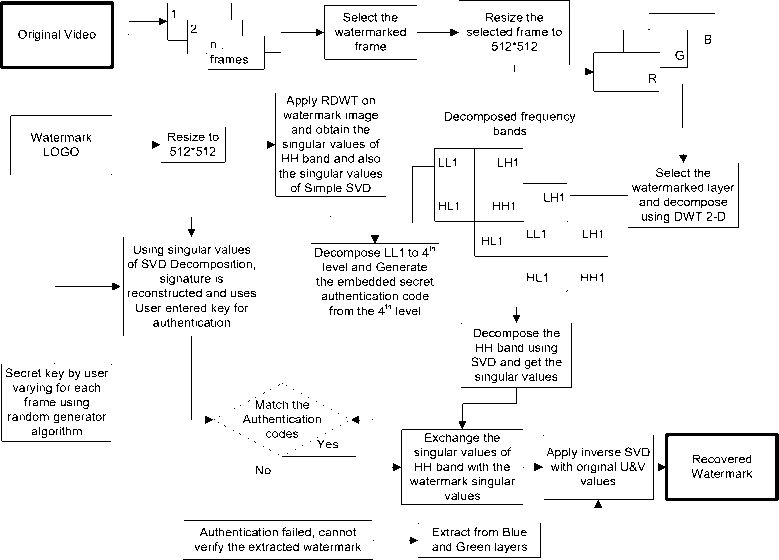
Fig.2. Proposed Watermarking Extraction Process
-
VII. Results
Various analyses were implemented to accept perceptual quality, robustness and security of the proposed watermarking plan. Their outcomes and examination are as per the following:
Robustness: Subsequently implanting the watermark, an accustomed arrangement of assaults was applied on the watermarked video frames to check the strength of the plan. The different assaults are median filtering, rotation, cropping and noise attack.
Perceptual quality: Peak-signal-to-noise ratio (PSNR), correlation coefficient and Similarity Index are utilized as a standard to conform perceptual similitude between original and watermarked picture. The PSNR of the watermarked video and Correlation coefficient is utilized as a standard to measure resistivity of plan upon different assaults.
The Correlation is used to measure the visual quality of watermarked frames. Hence, PSNR values for all frames, Correlation values and Structure Similarity index for all frames has been carried out for the proposed scheme and values for selected frames shown in the following table. As shown in the table 2, following are the correlation values of the extracted frames after applying various attacks. Fig. 3 shows extracted watermark with or without attacks. We have seen from experimental results that before applying attacks, almost we have extracted the watermark successfully. The results are also better for one group of attack than another group of attacks on the watermark embedded in video frames. Hence, after applying various attacks, watermark is visible which proves its robustness.
Table 1. PSNR, Correlation and SSIM Value without Attacks
|
Quality Parameters Frame No. |
PSNR |
Correlation |
SSIM |
|
2 |
30.128 |
0.9389 |
0.9978 |
|
7 |
28.708 |
0.9486 |
0.9976 |
|
16 |
29.881 |
0.9061 |
0.9977 |
|
22 |
30.192 |
0.9127 |
0.9977 |
|
28 |
29.795 |
0.9127 |
0.9976 |
|
32 |
29.751 |
0.9406 |
0.9976 |
|
34 |
30.540 |
0.9055 |
0.9979 |
|
35 |
31.692 |
0.9106 |
0.9981 |
Table 2. Correlation Values after Applying Various Attacks
|
Attacks Frame No. |
Crop |
Median |
Rotation |
Noise |
|
2 |
0.9972 |
0.9007 |
0.9915 |
0.8982 |
|
7 |
0.9239 |
0.8077 |
0.9911 |
0.9178 |
|
16 |
0.9966 |
0.8188 |
0.2920 |
0.8686 |
|
22 |
0.9963 |
0.8711 |
0.3305 |
0.8731 |
|
28 |
0.9973 |
0.8401 |
0.9911 |
0.8811 |
|
32 |
0.9965 |
0.8873 |
0.9913 |
0.9020 |
|
34 |
0.9972 |
0.8522 |
0.9912 |
0.8654 |
|
35 |
0.9007 |
0.9171 |
0.9915 |
0.8577 |
SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI
SAKSr- SA.W-f SAKSHI S.iXSHI M« XV<>" SA\^ №1;
Sa’,?■:■:. sa.! SAKS IT SASS. SAKrA.
(a)
SAKSHI SAKSHI SAKSHI SAKSHI SAKS I It SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKS HI SAKS) 11 SAKSHI SAKSIII
SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI
(b)

(c)
SAKSHI SAKSHI SAKSHГ SAKSHI SAKS!IE SAKSHI SAKSHI SAKSHI SAKS Ell SAKSHI SAKSHI SAKSHI SAKSHI SAKSI"
SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI SAKSHI
(d)

(f)
(e)
Fig.3. Extracted Watermark (a) Original Watermark, (b) Without Attack, (c) Crop Attack, (d) Median Attack, (e) Rotation Attack, (f) Noise Attack
-
VIII. Conclusion
This paper describes a combined SVD-DWT digital video watermarking algorithm. In this, a watermark is embed in the video frames in two forms using SVD portioning of the watermark, the video frames are portioned into layers (RGB) and DWT sub-band decomposition of host video, for providing copyright protection as well as reliability. In this manner, the proposed scheme utilizes distinctive strategies of embedding watermarks on different layers by using Hybrid systems. The Robustness of this technique is completed by an assortment of attacks. Besides, the proposed algorithm is robust to assaults like cropping, median, noise and rotation attack. The proposed plan fulfills the prerequisite of imperceptibility and robustness for a feasible watermarking plan. To improve the fidelity of the scheme, key generation and wavelet based key embedding watermarking scheme is presented. Additionally, a blind procedure is done so it needn't bother with original data at the time of extraction and detection process. The robustness of our strategy is shown utilizing diverse attacks applied on the video content.
Список литературы Hybridization of Discrete Wavelet and Singular Value Decomposition using Redundant Wavelet for Robust Video Watermarking
- N. R. Bamane and S. B. Patil (2013), Comparison & Performance Analysis of different Digital Video Watermarking Techniques', International Journal of Scientific & Engineering Research, January-2013, Volume:4, Issue:1, ISSN: 2229-5518.
- Bibi Isac and V. Santhi (2011), "A Study on Digital Image and Video Watermarking Schemes using Neural Networks", International Journal of Computer Applications (0975 – 8887) Volume 12– No.9, January 2011.
- Prachi V. Powar and S. S. Agrawal (2013), 'Design Of Digital Video Watermarking Scheme Using Matlab Simulink', IJRET, May 2013, Volume:2, Issue: 5, ISSN: 2319 – 1163.
- S.Nafees Ahmed, B.Sridhar and C. Arun (2012), 'Robust Video Watermarking based on Discrete Wavelet Transform', International Journal of Computer Network and Security (IJCNS), Jan-Mar 2012, Vol 4. No 1, ISSN: 0975-8283.
- Jigar Madia, Kapil Dave, Vivek Sampat and Parag Toprani (2012), 'Video Watermarking using Dynamic Frame Selection Technique', National Conference on Advancement of Technologies – Information Systems & Computer Networks (ISCON – 2012) Proceedings published in International Journal of Computer Applications® (IJCA).
- M. Mohamed Sathik and S. S. Sujatha (2012), 'A Novel based invisible Watermarking Technique for Digital Images', International Arab journal of e-Technology, January 2012, Vol 2, No. 3.
- Lama Rajab, Tahani Al-Khatib and Ali Al-Haj (2009), 'Video Watermarking Algorithms Using the SVD Transform', European Journal of Scientific Research, ISSN 1450-216X, Vol.30 No.3 (2009), pp.389-401.
- Hamid Shojanazeri, Wan Azizun Wan Adnan and Sharifah Mumtadzah Syed Ahmad (2013), 'Video Watermarking Techniques for Copyright protection and Content Authentication', International Journal of Computer Information Systems and Industrial Management Applications (2013), Volume: 5, pp. 652–660, ISSN: 2150-7988.
- Rowayda A. Sadek (2012), 'SVD Based Image Processing Applications: State of The Art, Contributions and Research Challenges', International Journal of Advanced Computer Science and Application (IJACSA), 2012, Vol. 3, No. 7.
- Mohan A Chimanna and S. R. Khot (2013), 'Digital Video Watermarking Techniques for Secure Multimedia Creation and Delivery', International Journal of Engineering Research and Applications (IJERA), March -April 2013, Vol. 3, Issue 2, ISSN: 2248-9622.
- S. S. Bedi, Rakesh Ahuja and Himanshu Agarwal (2013), 'Copyright Protection using Video Watermarking based on Wavelet Transformation in Multiband', International Journal of Computer Applications, March 2013,Volume 66– No.8,ISSN: 0975 – 8887.
- C. Hsu (1998), "DCT-Based Watermarking for Video," IEEE Trans. Consumer Electronics, vol. 44, no. 1, pp. 206-216, Jan. 1998.
- Ashish M. Kothari and Ved Vyas Dwivedi (2013), "Video Watermarking – Combination of Discrete Wavelet & Cosine Transform to Achieve Extra Robustness", I.J. Image, Graphics and Signal Processing, 2013, 3, 36-41.
- Swati Tiwari and R. P. Mahajan (2012), 'A Secure Image Based Steganographic Model Using RSA Algorithm and LSB Insertion', International Journal of Electronics Communication and Computer Engineering, 2012, Volume 3, Issue 1, ISSN 2249 –071X.
- Himanshu Agarwal, Rakesh Ahuja and S.S.Bedi (2012), "Highly Robust and Imperceptible Luminance Based Hybrid Digital Video Watermarking Scheme for Ownership Protection", I.J. Image, Graphics and Signal Processing, 2012, 11, 47-52.


