IAMIN: An infrastructure-aware middleware for the reconfiguration of unstructured Peer-to-Peer overlay networks
Автор: Morteza Alizadeh, Arash Ghafouri, Mohsen Sharifi
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 5 vol.11, 2019 года.
Бесплатный доступ
Peer to peer networks have become one of the most popular networking methods because of their flexibility and many use cases such as file sharing and distributed computations. Unstructured overlay peer to peer networks are one of key components of peer to peer systems that are considerable because of their low cost in network construction and maintenance. One of the main challenges in unstructured peer to peer overlay networks is the topology mismatch between overlay network and the underlying physical infrastructure. The root of this challenge is lack of awareness about peers in the network infrastructure during connection to and disconnection from overlay network, in addition to the neighbor selection mechanism in the overlay network. Different types of awareness of network infrastructure includes awareness of the location of internet service providers. Also awareness of proximity, geographical location and resources of peers. In this article we present a middleware which configures overlay network by using public measurements and the estimated delay among peers in order to have the most conformity with the topology of physical infrastructure. To evaluate the performance, our middleware is implemented on the top of Gnutella which is an unstructured overlay peer-to-peer network. Our simulations show that our middleware enhances the conformity of overlay network to the topology of physical network infrastructure. In addition, it improved the average throughput and the average delay.
Peer to Peer, Overlay Networks, Physical Networks, Infrastructure aware, Middleware
Короткий адрес: https://sciup.org/15015685
IDR: 15015685 | DOI: 10.5815/ijcnis.2019.05.02
Текст научной статьи IAMIN: An infrastructure-aware middleware for the reconfiguration of unstructured Peer-to-Peer overlay networks
Published Online May 2019 in MECS
Distributed systems are considered as one of the most popular computer systems. Peer to peer networks are distributed systems which present different specifications in comparison to the architecture of client-server architecture. Nodes can play the role of client and server concurrently by having symmetric roles. This specification causes better strength and more resistance of network against failure of nodes and the problems of obstruction and system bottlenecks [1], [2]. Nowadays peer to peer systems are so popular and two thirds of the traffic of internet network is consisted of peer to peer networks traffic. In comparison to client-server systems, all nodes in this type of networks have the capability of sharing their resource and also using resources that others share [1].
The main problem of peer to peer systems is scalability. These systems use overlay networks to overcome the scalability problem. Overlay which is a virtual network of physical and virtual nodes made on the top of physical network. The same problem causes some challenges including lack of awareness about physical infrastructure, coordination of resources, network traffic, security and privacy.
In unstructured overlay peer-to-peer networks, files are placed completely random and have no relation with the topology of network. Unstructured systems are the most popular systems in today's internet. In these systems maintenance of topology is so simple, but two serious problems in these systems severely decrease the efficiency [4].
The first problem is searching based on inefficient flooding requests for accessing contents. Blindly torrential requesting a query through peers or super peers is the most popular searching mechanism used in unstructured peer-to-peer systems. In this mechanism, a query will be distributed and redistributed again to the time of satisfying a special criterion [4].
The second problem is topology unconformity between overlay network and underlying physical network. This lack of conformity of the virtual network built on top of the physical network could occur in any distributed system based on overlay networks. This phenomenon occurs because of the lack of awareness from physical network during the formation of overlay networks [13], [15], [16].
In figure 1, overlay network 1, is unmatched so that for sending a package from A to B, this package passes through physical infrastructure of the peers B, E, C and D and at the end it will return to peer B. But there is no such a problem in overlay network 2 and this overlay network is a matched overlay network.
A problem that we are going to solve in this article is lack of conformity of overlay network to the physical network. In this regard, we present a middleware that tries to configure this network based on physical network leveraging the awareness of physical infrastructure during the formation of overlay network. Also by passing time, it configures formed network by using its awareness of physical infrastructure.
Organization of the rest of the article is as follows. In the second section related works in this field are studied and pros and cons of each protocol was investigated and at the end of this section. A classification of related works is presented as well. In the third section, informed middleware from presented infrastructure for unstructured peer-to-peer networks is introduced and explained. In the fourth section, at first some explanations are noted about the way of simulation of proposed middleware and then along with introducing the criteria of evaluation, results arising of its performance evaluation is presented. At the end in the fifth section along with concluding discussion, we propose future research ideas in this field.
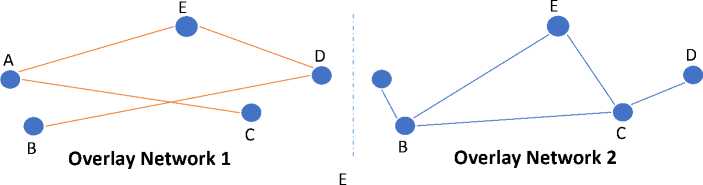
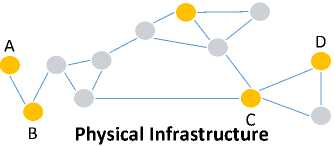
Network
Fig.1. Display Matched and Unmatched Overlay Networks to Physical Infrastructure Network
-
II. Related Works
As it is mentioned before, the lack of awareness from underlying physical networks during the construction of overlay networks causes lack of conformity of virtual network to the physical network. Several researches to address mentioned challenge are performed which this study followed two solutions as its main route. The first solution is based on the improvement of formed topology of overlay network and tries to achieve conformity after its formation. The second solution is to achieve conformity in the topology formation stage. then after this stage by using one of present awareness of physical infrastructure. They communicate in overlay network of nodes with limited number of their neighbors as a topology. By changing physical network, these communications will be updated. We can divide overlay networks in three classes based on the method of neighbor selection.
The first class is unaware overlay networks in which neighbors are connected to each other based on identity of nodes in a logical environment. Unstructured overlay networks such as Gnutella, Can and Chord work based on distributed hash table which are examples of agnostic overlay networks. Gnutella is one of the first unstructured peer-to-peer networks. Gnutella is a decentralized protocol for distributed searching on a flat topology of peers [6, 5]. Simplicity in connection to peer to peer network and no needs for any knowledge about network topology can be considered as positive points of this system. Such design is highly flexible against peers entering or leaving the system. Random selection of neighbor peers is resulted in lack of conformity to the topology of infrastructure and also imposing traffic in physical network. In addition to this method, torrential publishing remained as an unsolved challenge in this protocol [18], [14].
The second class is called proximity-aware overlay networks that includes overlay networks which act freely in the selection of nodes from routing table to some extent. Pastry, tapestry, LTM and ACE overlay network use this approach by selecting nodes that are physically close. ACE protocol in 2004 was introduced by Liu [4] investigated torrential publishing of searching and the lack of conformity of the topology of overlay network and could respond to these challenges in each stage locally with the awareness about a small portion of the topology and delay. One of the negative points of ACE protocol is the lack of reconfiguration of overlay networks. Also based on the fact that awareness of each peer in this protocol is at most two-step neighbours, which has a heavy overhead. Liu in 2005 presented another overlay network named LTM or location aware protocol [7] which this protocol tries to correct communications locally by triple investigation of related peers in overlay network and retrieving delay among them. This protocol also tries to find more suitable neighbors and shorter delay towards present neighbors by discovering other peers. In fact, this protocol in comparison to ACE protocol will have more depth for finding suitable neighbors. Among weak points of this protocol are communication correction in this protocol locally and only by triple investigation of peers and communication among them. Also change of topology and finding new neighbors in each stage, only with informing peers with the distances of two steps and one by one is performed which this work is imposes high overload in networks with high scale to network [4].
In 2007 Wu et al presented a protocol named laptop [8]. they used the concept of geography for constructing a hierarchical overlay network to formulate a selforganized and informed overlay network. The main concentration in laptop is on declining routing time and providing high scale along with fault tolerance. In this protocol because of tree form of each peer, it should send its request only to the peer of its parent that because of this reason, there is need to the recognition of peers with more resources and because of tree form each peer should send its demand to the peer of its parent which this issue is resulted in sending all demands to higher level and at last to the level 1 and also this problem is resulted in appearing single point of failure in peers in higher levels and failure of each peers in this protocol would result in deleting all peers of their child and children from system.
In table (1) all related works based on neighbor selection method and awareness degree has been shown.
Table 1. A review on Related Works
|
The awareness of the physical network information. |
The method of neighbour selection |
Overlay Networks |
||||||
|
Resource -aware |
Geographical location |
Delay Time |
Internet Service Provider |
Network -aware |
Proximit y-aware |
Unaware |
||
|
Indirect |
Direct |
|||||||
|
Gnutella (6.0) [9] |
||||||||
|
Kazaa/Fast Track [10] |
||||||||
|
ACE [4] |
||||||||
|
LTM [7] |
||||||||
|
LAPTOP [8] |
||||||||
|
Juniper [11] |
||||||||
|
Extended CAN (ECAN) [12] |
||||||||
-
III. Infrastructure Aware Middleware
-
3.1. Basic Definitions
-
3.1.1. Definition of Optimal Overlay Network
Utilization and maintenance of information and parameters of physical network such as the location of the internet service providers, delay time, geographical zone and resources of peers for improving different aspects of the performance of peer to peer systems are defined as the awareness of physical network. Information collection of physical network through measurement, computation and estimation of different parameters of physical network is performed and collected information by peer to peer system for construction, updating and management of overlay network. Lack of awareness through physical network makes it difficult for the quality of services and it causes inefficiency in routing, overload and longer delay even for non peer to peer traffic.
With the purpose of addressing some challenges which the lack of awareness from physical network arises, we present an underlay aware middleware for the configuration of structured overlay in peer-to-peer networks. This middleware in two separated complementary phases tries to create an overlay network based on infrastructure.
In the following definitions are provided to better understand IAMIN.
An optimal overlay network is a network that has the most conformity with its underlying physical network which follows one of the following definitions:
-
• First definition: For each three peers in overlay network as the names of A,B and C, if one package of network such as peer A by peer C will be sent to peer B in overlay network, this package in physical infrastructure does not pass two times from any physical node.
-
• Second definition: For each three peers in overlay network as the names of A, B and C, if nodes (A, B) and (B, C) exist in overlay network. The cost of node (A, C) in physical network is more than the cost of nodes (A, B) and (B, C). The purpose of node (A, B) is the relation between peer A and B so that a peer will not be the member of overlay network among them.
-
3.2.1. First phase: Confining the neighbor selection state space
-
3.1.2. The definition of Landmarks
landmarks and also by help of the measurement of delay between peers limits the space of neighbor selection for new peer. In the second phase, new peers by using the parameters of delay time by direct measurement will select the number of hop among peers and also the definition of optimal overlay network of their neighbors.
Landmarks play the main role in this phase. one of main problems in aware overlay networks is high cost of the measurement of delay among peers caused by high scale of peer to peer networks. it is time-consuming and expensive and optimal neighbor selection will be nearly impossible.
To solve this problem, we use the idea of landmark to estimate delay between peers. In fact, by computing delay time among peers and landmarks, we estimate calculated vector comparison for the distance among peers. For example, in the following figure, delay between peer 1 and peer 2 is predicted using of landmarks 1, 2 and 3.
Each landmark is a fixed physical node inside the network which keeps a table containing all the information of all peers inside the network. This information includes the name and the vector of delay between peer and landmarks. Each landmark has a table like table 2 in which the address of peers are kept along with delay of each peer.
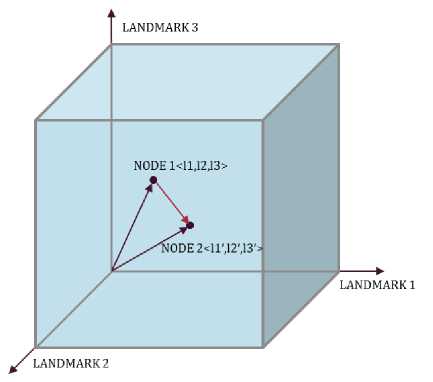
Table 2. The Information of Peers in Landmarks
|
Peer Address |
The Vector of Delay Time |
|
Peer Address 1 |
< la ,l7.,l4,l4 > |
|
Peer Address 2 |
|
|
Peer Address 3 |
< l '; ,l^l^l ^ > |
|
Peer Address 4 |
|
|
... |
|
|
Peer Address N |
|
Fig.2. The method of Calculation and Comparison to the Delay Time
Vector
-
3.1.3. Delay Measurement Methods
The delay time between any two peers in system can be accurately measured or predicted.
-
• Accurate measurement: In this method, delay can be accurately measured by the utilization of sending a package or the method of routing.
-
• Prediction method: To use the prediction method, it is enough for each node in the system to know the latency of a small set of other nodes (usually neighbors or landmarks. Next, delay between two nodes is predicted by comparison of calculated vector
-
3.2. The Introduction of Proposed Middleware
-
3.2.2. Second phase: Creating Optimal Overlay Network
This middleware in the first phase by using several
In fact, by this method, we confine neighbor selection space for each peer. so that applied limitation will have least cost and be smarter. By measuring delay between each peer and landmarks, there will be a vector that indicates approximate situation of each peer to landmarks.
Each peer after generating a delay vector, sends request to landmarks which includes its delay vector. In continue landmarks store their delay vector and the closest landmark sends a list of closest peers to the applicant peer. Next the applicant selects p peers as its neighbors. The comparison of vectors will be performed using K nearest neighbors algorithm.
This phase will be started by receiving the list of nearest peers from landmark. Applicant peer after receiving the list of proposed peers from landmark, at first using direct computation method calculates delay and distance based on number of nodes between itself and peers in the proposed list. After calculating these two parameters for m peer in list, p peers will be selected as neighbor candidates. In the next stage, new peer sending requests proceeds to receive neighbors table of selected peers. Selected peers once received this request will reply back list of their neighbors to the new peer. Next, the new peer tries to modify its table of neighbors based on the relation between itself and other peers, then sends it to them. The modification method is that in the table each peers searches the name of p-1 of other peer and in case of finding name of each one, by the comparison of three link costs which is measured between itself and other two peers discards the link having the highest cost and registers other two connections.
For example, as it is shown in figure 3, peer A has received three peers C, F and D from overlay network as proposed peer and by sending request received neighbors
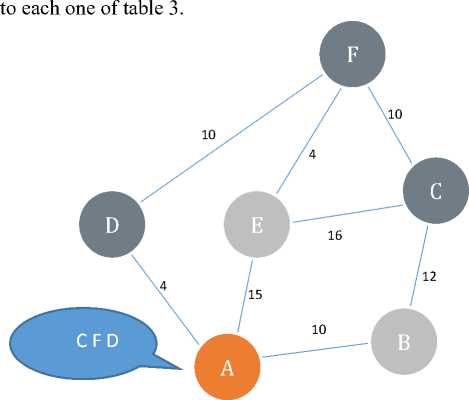
Fig.3. The method of Middleware Functionality in the Second Phase
The goal of peer A is the selection of two peers as neighbors in overlay network. For this purpose, this peer analyzes three parameters in the table selects peers C and D as neighbor based on the lower cost that the neighbor of peer F has towards peer C and based on placing peer F in the list of neighbor peer D.
Table 3. The Information of Selected Peers
|
Hop count |
Cost |
Neighbor List |
|
|
C |
2 |
22 |
(G,8), (H,8), ... |
|
D |
1 |
4 |
(F,10), (I,17), ... |
|
F |
2 |
14 |
(D,10), (J,26), ... |
-
3.3. Architecture of Proposed Middleware
-
3.4. Primitives of Proposed Middleware
-
3.4.1. Join Primitive
For infrastructure aware configuration of unstructured peer to peer networks and accessing an overlay network having the most conformity with physical infrastructure, a set of multiple primitives and sub-primitives should interact with each other. The interaction architecture of these primitives and sub-primitives displayed as a layered architecture in figure 4.
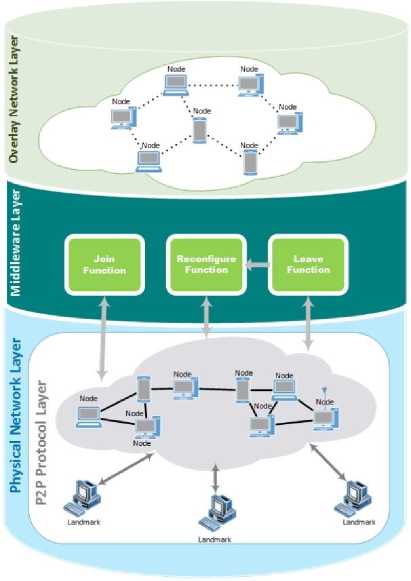
Fig.4. The Architecture of IAMIN
Proposed middleware has three primitives named Join, Leave and Reconfiguration that by calling each primitive from peers, a process is performed that its details is as follows:
This primitive can be called by each peer in overlay network. After calling this primitive, a set of activities occur in the form of process and at the end peer receives a list from its neighbor in overlay network as the output. In table (4) the process that occur as pseudo-code by calling this primitive is shown.
Table 4. The Execution Process of Join Primitive
Start
-
1 Peer A receive the address of all Landmarks by Bootstrap
server;
-
2 For Each of Received Landmark's address do
-
3 Peer A Send and receive a packet to the landmark and
determine its Delay Time as well as
Create its Delay_Time_Vector;
-
4 End For
-
5 Peer A Send its Delay_Time_Vector to Nearest Landmark
and Request All Peer of Landmark;
-
6 The Mentioned Landmark Save the Received
Delay_Time_Vector on Own Table and Send
List of All its Peers to Peer A;
-
7 Peer A Receive List of All Landmark's Peers that its size is
M Peer;
-
8 For Each of M peer do
-
9 Peer A Determine Delay Time between Itself and Other
Peer;
-
10 End For;
-
11 Peer A with respect to The Definition of an Optimal
-
3.4.2. Leave Primitive
Network and Obtained Parameters Select G Peer as Neighbors;
End
This primitive is called during leave or exit of each peer in which neighbors and landmarks will be informed of this exit and necessary proceedings as reconfiguration will be performed. In table 5, the set of proceedings which occur with calling this primitive are displayed as pseudo-code.
Table 5. The Execution Process of Leave Primitive
Start
-
1 If (Peer A Want to Exit of Network) Then
-
2 For Each of Peer A's Neighbors do
-
3 Peer A Send Message to the Neighbor and
Notify it
-
4 End For
-
5 For Each of Peer A's Landmarks do
-
6 Peer A Send Message to the Landmark and
Notify it
-
7 End For
-
8 End If
-
9 If (Landmarks Receive The Exit Message from Peer A) Then
-
10 For Each of Peer A's Landmarks do
-
11 Landmark Delete Peer A's
Delay_Time_Vector of Own Table
-
12 End For
-
13 End If
-
14 Neighbor Peers Whom have Received the Exit Message Can
Reconfigure Own Network for the Identification of New Neighbor
End
Definition of an Optimal Network and Obtained Parameters
Select G Peer as Neighbors;
-
14 Break;
-
15 Case Coming The Periodic Configuration Deadline:
-
16 For Each of Received Landmark's
address do
-
17 Peer A Send and receive a
packet to the landmark and determine its Delay Time as well as its create
Delay_Time_Vector;
-
18 End For
-
19 Peer A Send its
Delay_Time_Vector to Nearest Landmark and
Request All Peer of Landmark;
-
20 The Mentioned Landmark Save
the Received Delay_Time_Vector and
Send List of All its Peers to Peer
A;
-
21 Peer A Receive List of All
Landmark's Peers that its size is M Peer;
-
22 For Each of M peer do
-
23 Peer A Determine Delay Time
between Itself and Other Peer;
-
24 End For;
-
25 Peer A with respect to The
Definition of an Optimal Network and Obtained
Parameters Select
G Peer as Neighbors;
-
26 Break;
-
27 End Switch End
-
3.4.3. Reconfiguration Primitive
The reconfiguration primitive is called in two situations. The first situation is when a peer leaves a network. In this state, the neighbors of that peer by investigating a series of network parameters and in the situation of decreasing or increasing over threshold calls this primitive. The second situation by calling primitive by peer in specific periods and for performing process of reconfiguration is happened.
In table 6, the set of proceedings are displayed as pseudo-code which occur by calling this primitive.
Table 6. The Execution Process of Reconfiguration Primitive
Start
-
1 Switch (Call_Reason)
-
2 Start Switch
-
3 Case Peer A Leave Its Network :
-
4 For Each of Received Landmark's
address do
-
5 Peer A Send and receive a packet to the
landmark and determine its Delay Time as well as
Create its Delay_Time_Vector;
-
6 End For
-
7 Peer A Send its
Delay_Time_Vector to Nearest Landmark and
Request All Peer of Landmark;
-
8 The Mentioned Landmark Save the Received
Delay_Time_Vector and
Send List of All its Peers to Peer A;
-
9 Peer A Receive List of All
Landmark's Peers that its size is M Peer;
-
10 For Each of M peer do
-
11 Peer A Determine Delay Time
between Itself and Other Peer;
-
12 End For;
-
13 Peer A with respect to The
-
IV. Simulation and Evaluation
-
4.1. Evaluation Criteria
-
4.2. Results
In this part at first we explain the way we simulated our middleware. Next we will continue by introducing evaluation criteria, we investigate the evaluation of presented middleware.
Evaluation of our underlay aware middleware is done using the simulator environment NS-2. For this purpose we implemented our middleware on the top of Gnutella overlay network and as an integrated overlay network with middleware in NS-2.
The topology of the network we used in this experiment is made by module GT-ITM in which the minimum bandwidth of network connections is 1.5 Mbps and maximum 155Mbps for limited number of connections to main nodes in network. Also maximum and minimum speed of connections are recognized respectively 448ms and 7ms. Total time of each experiment is 100 s. In performed simulation, whole number of nodes inside network is 750 that the number of 100 nodes play the role of hub and router and connected each other with fixed topology. 650 nodes have the possibility of connection to overlay network in which during multiple experiments, the number of 40,55,70,85,100 and 115 nodes are connected to overlay network.
To evaluate the performance of presented middleware, we concentrated on three network performance criteria and also we investigated the average throughput, the average delay and the average number of hops by packets.
Since presented middleware is to provide more conformity between topology of overlay network with the topology of physical network infrastructure, hence last criterion shows success rate of our study.
For evaluation, we considered Gnutella overlay network in previous and next states of the implementation of presented middleware on network and then investigated them based on mentioned evaluation criteria. Results gained by comparison will be explained in following. It is necessary to note that each designed point in the figures of the following images are an average of 30 simulations with confidence interval 95%.
In the first part, we evaluated proposed middleware and Gnutella network based on the average throughput.
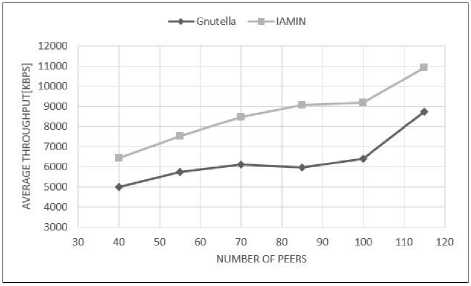
Fig.5. The Average Throughput According to the Peer Number
As it is shown in figure 5, the average throughput in performed experiments for Gnutella overlay network with proposed middleware has considerable improvement that in it has 30 percent increasing towards Gnutella common overlay network. This improvement indicates high rate of receiving packages in network that occurred because of decreasing delay in receiving packages.
In the second part, by calculating sending time and receiving each sending packet inside network, we computed delay for each packet and then we investigated the average delay for proposed middleware and Gnutella overlay network in experiment.
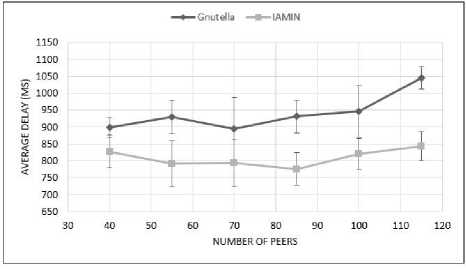
Fig.6. The Average Delay According to the Peer Number
The result of experiments for calculating the average delay in figure 6 is displayed and it indicates that the average delay decreased by 15 percent. These improvements reach each other in their most limit to 200ms that will have significant effect in response time for user requests. In network parameters 100ms of time can be effective in which the situation of a network will be changed from a network with low efficiency to a network with suitable efficiency. This decrease shows decreasing of the length of passed route in physical network by each peer.
In the third part, the average of the number of passed steps is investigated. The evaluation of this criterion for recognizing the effect of proposed method is so important. Decreasing this criterion indicates more conformity of the topology of overlay network with physical network infrastructure. In this experiment, we achieved results by calculating the number of passed steps for each packet inside network by computing their average that is observed in the following figure.
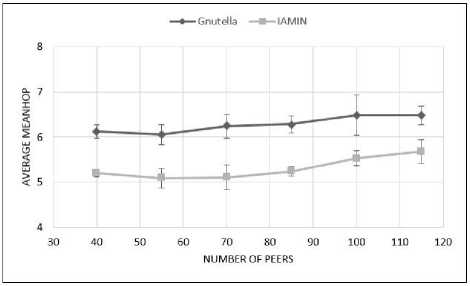
Fig.7. The Number of Passed Steps According to the Peer Number
As it is observed in figure 7, the number of passed steps in proposed middleware towards Gnutella common overlay network in average which shows one step or 15 percent of decreasing.
The results of performed experiments in simulation before and after applying proposed middleware to Gnutella peer to peer overlay network indicate the accuracy of this claim that improved our proposed solution in terms of middleware based on topology conformity of overlay network with the topology of physical network infrastructure was improved in an unstructured peer to peer overlay network as Gnutella that its result is the improvement of parameters of networks such as average throughput, delay and steps number.
-
V. Conclusion and Future Works
In this article we presented an underlay aware middleware for the configuration of unstructured overlay networks to solving the challenge of the lack of awareness of overlay networks from physical infrastructure. Next we introduced middleware design through two phases. This middleware in the first phase estimates the distance among peers by calculating delay among peers, landmarks and comparing measured vectors and confines the space for the selection of neighbor for each peer. In the second phase, this
Unstructured Peer-to-Peer Overlay Networks possibility will be provided that peers by using direct computation method of delay and also the computation of the number of present nodes between itself and the set such as close peers based on definition of optimal overlay network selects its neighbor so that there will be the most conformity with physical infrastructure and presented middleware has three main primitives named of Join, Leave and Reconfiguration that based on it, there are functions that in fact perform main processes of middleware. For evaluating underlay aware middleware and its performance study in simulator environment NS-2 we performed experiments then we evaluated Gnutella overlay network before and after adding proposed middleware based on the average throughput, delay and the average number of passed steps by packets. Based on the results of evaluation, proposed middleware in addition to decreasing 15 percent in the number of passed steps of the packages that indicates increasing conformity of the topology of overlay network with the topology of physical network infrastructure, it could increase the average throughput by 30 percent and decrease the average of delay by 15 percent.
Список литературы IAMIN: An infrastructure-aware middleware for the reconfiguration of unstructured Peer-to-Peer overlay networks
- G. F. Coulouris, J. Dollimore, T. Kindberg and G. Blair, "Distributed ?Systems International Computer Science Series", Addison-Wesley / Pearson Education Limited, 5th Edition, May, 2011.
- A. S. Tanenbaum and M. Van Steen, "Distributed Systems: Principles and Paradigms", Prentice Hall, 3th Edition, January, 2002.
- L. Massoulie, A.-M. Kermarrec and A. Ganesh, "Network Awareness and Failure Resilience in Self-Organizing Overlay Networks", The 22nd International Symposium on Reliable Distributed Systems, IEEE, Italy, October, 2003.
- Y. Liu and e. al., "A Distributed Approach to Solving Overlay Mismatching Problem", The 24th International Conference on Distributed Computing Systems, IEEE, Japan, March, 2004, pp. 132-139.
- P. Ganesan, Q. Sun and H. Garcia-Molina, "Yappers: A Peer-to-Peer Lookup Service Over Arbitrary Topology", INFOCOM 2003, Twenty-Second Annual Joint Conference of the IEEE Computer and Communications, USA, March, 2003, vol. 2, pp. 1250-1260.
- Y. Chawathe, S. Ratnasamy, N. L. L. Breslau and A. S. Shenker, "Making Gnutella-like P2P Systems Scalable", The Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, Germany, August, 2003, pp. 407-418.
- Y. Liu, L. Xiao, X. Liu, L. M. Ni and X. Zhang, "Location Awareness in Unstructured Peer-to-Peer Systems", IEEE Transactions on Parallel and Distributed Systems, February, 2005.
- C. Wu, D. Liu and R. Hwang, "A Location-Aware Peer-to-Peer Overlay Network", International Journal of Communication Systems, January, 2007, vol. 20, pp. 83-102.
- Q. He and e. al., "Mapping Peer Behavior to Packet-Level Details: A Framework for Packet-Level Simulation of Peer-to-Peer Systems", 11th IEEE/ACM International Symposium on Modeling, Analysis and Simulation of Computer Telecommunications Systems, USA, October, 2003, pp. 71-78.
- E. K. Lua, J. Crowcroft, M. Pias, R. Sharma and S. Lim, "A Survey and Comparison of Peer-to-Peer Overlay Network Schemes", IEEE Communications Surveys & Tutorials, April, 2004, pp.72-93.
- F. Araujo and L. Rodrigues, "GeoPeer: A Location-Aware Peer-to-Peer System", Third IEEE International Symposium on Network Computing and Applications, USA ,September, 2004.
- C. Tang and Z. Xu, "Utilizing Proximity Information in an Overlay Network", Tang, C. and Xu, Z., Hewlett-Packard Development Co LP, U.S. Patent Patent No. 7.788.400, August, 2010.
- S. Manel and B. Mahfoud., "An Adaptive P2P Overlay for MANETs", The International Conference on Distributed Computing and Networking, India, January, 2015.
- Woungang, F. H. Tseng and Y. H. Lin, "MR-Chord: Improved Chord Lookup Performance in Structured Mobile P2P Networks", IEEE Systems Journal, September, 2015, vol. 9, no. 3, pp. 743-751.
- S. Cherbal, A. Boukerram and A. Boubetra, "A Survey of Locality-Awareness Solutions in Mobile DHT Systems", 12th International Symposium on Programming and Systems (ISPS), Algeria, April, 2015, pp. 1-7.
- H. Shen, G. Liu and L. Ward, "A Proximity-Aware Interest-Clustered P2P File Sharing System", IEEE Transactions on Parallel and Distributed Systems, USA, June, 2015, vol. 26, no. 6, pp. 1509-1523.
- S. Zhou, Y. Zhou and J. Luo, "Research on Simulators for Peer-to-Peer Systems", Third International Conference on Computer Science and Network Technology (ICCSNT), China, October, 2013, pp. 726-731.
- R. Hasan, M. A. Rony, S. A. Chowdhury and M. A. Rizwan, "A Self Adaptive Super Peer based Topology for Unstructured P2P System", EUROCON, Croatia, July, 2013, IEEE, Zagreb, pp. 218-225.


