Image Watermarking Using 3-Level Discrete Wavelet Transform (DWT)
Автор: Nikita Kashyap, G. R. SINHA
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 3 vol.4, 2012 года.
Бесплатный доступ
We have implemented a robust image watermarking technique for the copyright protection based on 3-level discrete wavelet transform (DWT). In this technique a multi-bit watermark is embedded into the low frequency sub-band of a cover image by using alpha blending technique. The insertion and extraction of the watermark in the grayscale cover image is found to be simpler than other transform techniques. The proposed method is compared with the 1-level and 2-level DWT based image watermarking methods by using statistical parameters such as peak-signal-to-noise-ratio (PSNR) and mean square error (MSE). The experimental results demonstrate that the watermarks generated with the proposed algorithm are invisible and the quality of watermarked image and the recovered image are improved.
Image watermarking, 3-level DWT, wavelet transform, MSE, PSNR.
Короткий адрес: https://sciup.org/15010688
IDR: 15010688
Текст статьи Image Watermarking Using 3-Level Discrete Wavelet Transform (DWT)
Published Online April 2012 in MECS DOI: 10.5815/ijmecs.2012.03.07
With the widespread distribution of digital information over the World Wide Web (www), the protection of intellectual property rights has become increasingly important. These information, which include still images, video, audio, or text are stored and transmitted in a digital format. Information stored in digital format can be easily copied without loss of quality and efficiently distributed [1]. The digital watermark is then introduced to solve this problem. Digital watermarking is a branch of information hiding which is used to hide proprietary information in digital media like photographs, digital music, or digital video [2-3]. The ease with which digital content can be exchanged over the Internet has created copyright infringement issues. Copyrighted material can be easily exchanged over peer-to-peer networks, and this has caused major concerns to those content providers who produce these digital contents.
In order for a digital watermarking method to be effective it should be imperceptible, and robust to common image manipulations like compression, filtering, rotation, scaling cropping, and collusion attacks among many other digital signal processing operations. Current digital image watermarking techniques can be grouped into two major classes:
Spatial Domain Watermarking and Frequency Domain Watermarking.
Compared to spatial domain techniques [4], frequency-domain watermarking techniques proved to be more effective with respect to achieving the imperceptibility and robustness requirements of digital watermarking algorithms [5]. Commonly used frequency-domain transforms include the Discrete Wavelet Transform (DWT), the Discrete Cosine Transform (DCT) and Discrete Fourier Transform (DFT). However, DWT has been used in digital image watermarking more frequently due to its excellent spatial localization and multi-resolution characteristics, which are similar to the theoretical models of the human visual system. Further performance improvements in DWT-based digital image watermarking algorithms could be obtained by increasing the level of DWT.
-
II. RELATED WORK
In this section we will look into the review of digital watermarking used for images. It describes the previous work which had been done on digital watermarking by using DWT technique and other techniques, including the analysis of various watermarking schemes and their results.
Mistry [6] introduced digital watermarking methods-Spatial domain (like LSB) and transform domain (like DCT, DWT) methods. The spatial domain is the normal image space, in which a change in position in image directly projects to a change in position in space. Ex.-Least Significant bit (LSB) method. Transform Domain Method produce high quality watermarked image by first transforming the original image into the frequency domain by the use of Fourier Transform, Discrete Cosine Transform (DCT) or Discrete Wavelet transforms (DWT). Authors found that transform watermarking is comparatively much better than the spatial domain encoding.
Van et al. [7] proposed two LSB techniques. First replaces the LSB of the image with a pseudo-noise (PN) sequence, while the second adds a PN sequence to the LSB of the data. Another LSB data hiding method called Patchwork chooses n pairs (ai ; bi) of the points in an image and increases the brightness of the ai by one unit while simultaneously decreasing the brightness of bi. The problem with this paper is that data is highly sensitive to noise and is easily destroyed. Furthermore, image quality may be degraded by the watermark.
Blossom et al. [8] proposed a DCT based watermarking scheme which provides higher resistance to image processing attacks such as JPEG compression, noise, rotation, translation etc. In this approach, the watermark is embedded in the mid frequency band of the DCT blocks carrying low frequency components and the high frequency sub band components remain unused. Watermark is inserted by adjusting the DCT coefficients of the image and by using the private key. Watermark can then be extracted using the same private key without resorting to the original image. Performance analysis shows that the watermark is robust.
W. Hong et al. [9] proposed a robust digital watermarking scheme for copyright protection of digital images based on sub-sampling. The watermark is a binary image, which is embedded in discrete transform coefficient of the host image and not used in the original image. In this scheme, they had used chaotic map in watermarked image. However the result of watermark image is good and robust to attack.
Xia et.al [10] proposed a watermarking scheme based on the Discrete Wavelet Transform (DWT). The watermark, modeled as Gaussian noise, was added to the middle and high frequency bands of the image. The decoding process involved taking the DWT of a potentially marked image. Sections of the watermark were extracted and correlated with sections of the original watermark. If the cross-correlation was above a threshold, then the watermark was detected. Otherwise, the image was decomposed into finer and finer bands until the entire, extracted watermark was correlated with the entire, original watermark. Performance analysis shows that DWT is more robust to attack than DCT [8]. The problem with the proposed method is that this technique is susceptible to geometric attacks.
Akhil et al. [11] proposed a robust image watermarking technique based on 1-level DWT (Discrete Wavelet Transform). This method embeds invisible watermark into salient features of the original image using alpha blending technique. Experiment result shows that the embedding and extraction of watermark is depend only on the value of alpha. All the results obtained for the recovered images and watermark is identical to the original images.
-
G. Bhatnagar et al [12], presented a semi-blind reference watermarking scheme based on discrete wavelet transform (DWT) and singular value decomposition (SVD) for copyright protection and authenticity. Their watermark was a gray scale logo image. For watermark embedding, their algorithm transformed the original image into wavelet domain and a reference sub-image is formed using directive contrast and wavelet coefficients. Then, their algorithm embedded the watermark into reference image by
modifying the singular values of reference image using the singular values of the watermark.
M. Barni et al. [13] have developed an improved wavelet-based watermarking through pixel-wise masking. It is based on masking watermark according to characteristics of HVS. The watermark is adaptively added to the largest detail bands. The watermark weighing function is calculated as a simple product of data extracted from HVS model. The watermark is detected by correlation. The proposed method is robust to various attacks but this method is complex than other transform technique.
Kundur et al. [14] decomposed binary logo through DWT. The watermark is scaled by a salience factor, computed on a block by block basis, depending on local image noise sensitivity. It is then repeatedly added to the subbands of DWT decomposition of host image. Visual masking is thus exploited upto only block resolution. A binary code is embedded by suitably quantizing the coefficients of detail bands. For watermark recovery, the embedded binary code is estimated by analyzing coefficients quantization. Once the code is estimated, it is correlated and result is compared to a threshold chosen on the basis of a given false positive probability.
Most methods found in literature are highly complex and involve multiple execution stages. In this paper, we tried to propose a new simple methodology to hide a grayscale image within another grayscale image using 3-level DWT and the alpha-blending technique for the process of security.
-
III. Discrete Wavelet Transform (DWT)
Discrete Wavelet transform (DWT) is a mathematical tool for hierarchically decomposing an image [9]. It is useful for processing of non-stationary signals. The transform is based on small waves, called wavelets, of varying frequency and limited duration. Wavelet transform provides both frequency and spatial description of an image. Unlike conventional Fourier transform, temporal information is retained in this transformation process. Wavelets are created by translations and dilations of a fixed function called mother wavelet.
DWT is the multiresolution description of an image the decoding can be processed sequentially from a low resolution to the higher resolution [10]. The DWT splits the signal into high and low frequency parts. The high frequency part contains information about the edge components, while the low frequency part is split again into high and low frequency parts. The high frequency components are usually used for watermarking since the human eye is less sensitive to changes in edges [14].
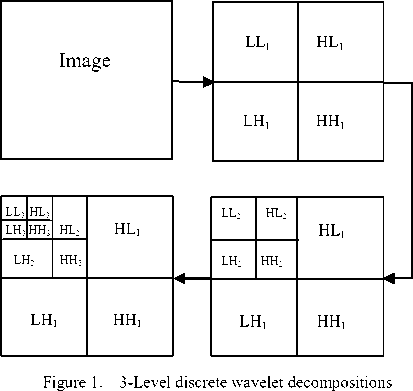
In two dimensional applications, for each level of decomposition, we first perform the DWT in the vertical direction, followed by the DWT in the horizontal direction. After the first level of decomposition, there are 4 sub-bands: LL1, LH1, HL1, and HH1. For each successive level of decomposition, the LL subband of the previous level is used as the input. To perform second level decomposition, the DWT is applied to LL1
band which decomposes the LL1 band into the four sub-
To perform third level decomposition, the DWT is applied to LL2 band which decompose this band into the four sub-bands – LL3, LH3, HL3, HH3. This results in 10 sub-bands per component. LH1, HL1, and HH1 contain the highest frequency bands present in the image tile, while LL3 contains the lowest frequency band. The three-level DWT decomposition is shown in Fig.1.
DWT is currently used in a wide variety of signal processing applications, such as in audio and video compression, removal of noise in audio, and the simulation of wireless antenna distribution [8]. Wavelets have their energy concentrated in time and are well suited for the analysis of transient, time-varying signals. Since most of the real life signals encountered are time varying in nature, the Wavelet Transform suits many applications very well.
-
IV. Proposed Watermarking Technique
Based on DWT technique, we propose a new watermarking algorithm for remote multimodal biometric authentication system. The proposed algorithm is divided into two parts, watermark embedding and watermark extraction.
-
A. Watermark Embedding
In this process firstly the gray scale host image is taken and 2-D, 3-level DWT (Discrete Wavelet Transform) is applied to the image which decomposes image into low frequency and high frequency components. In the same manner 2-D, 3-level DWT is also applied to the watermark image which is to be embedded in the host image. The wavelet used here is the wavelets of daubecheis. The technique used here for inserting the watermark is alpha blending [11, 15]. In this technique the decomposed components of the host image and the watermark are multiplied by a scaling factor and are added. Since the watermark embedded in this paper is perceptible in nature or visible, it is embedded in the low frequency approximation component of the host image.According to the formula of the alpha blending the watermarked image is given by bands LL2, LH2, HL2, and HH2.
WMI = k * (LL2) + q * (WM2) (1)
where WMI = low frequency component of watermarked image, LL3 = low frequency component of the original image obtained by 3-level DWT, WM3 = low frequency component of Watermark image, and k, q = Scaling factors for the original image and watermark respectively.
After embedding the cover image with watermark image, 3-level Inverse discrete wavelet transform is applied to the watermarked image coefficient to generate the final secure watermarked image. Fig. 2 shows watermark embedding process.
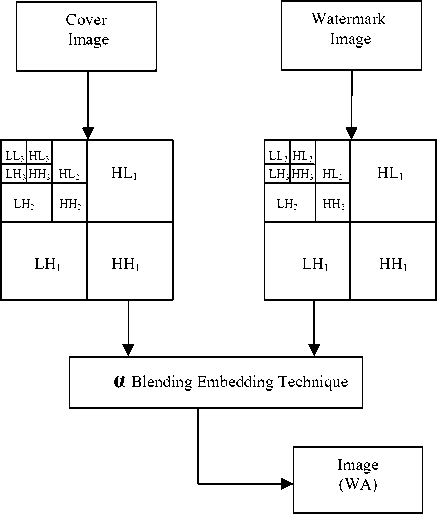
Figure 2. Watermark embedding technique
-
B. Watermark Extraction
In this process firstly 3-level DWT is applied to watermarked image and cover image which decomposed the image in sub-bands. After that the watermark is recovered from the watermarked image by using the formula of the alpha blending.
According to the formula of the alpha blending the recovered image is given by
RW = (WMI - k * LL3) (2)
where RW= Low frequency approximation of Recovered watermark, LL3= Low frequency approximation of the original image, and WMI= Low frequency approximation of watermarked image.
After extraction process, 3-level Inverse discrete wavelet transform is applied to the watermark image coefficient to generate the final watermark extracted image. Fig. 3 shows the watermark extraction process.
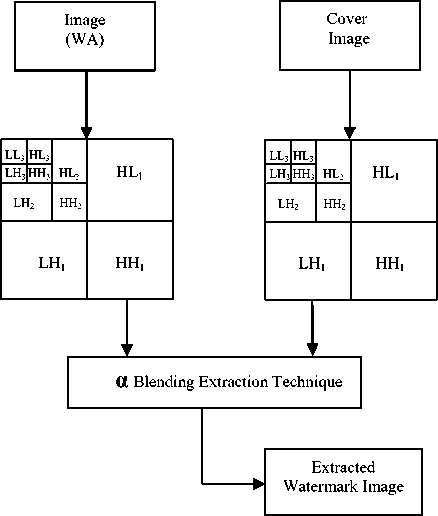
Figure 3. Watermark extraction technique
-
V. Experimental Results
We compared proposed 3-level 2-D DWT to the 2-level 2-D DWT technique. For both the technique we have used grayscale images Lena as original image and the cameramen’s image as the watermark. Both the images are of equal size of 256X256. Fig. 4(a) shows the original image and Fig. 4(b) shows the watermark image.
For embedding of watermark in the original image the value of scaling factor k is varied from 1.5 to 0.6 by keeping q constant and best result is obtained for k=0.98 for both 3 level and 2 level DWT. As the value of k is decreased further to 0.2 the watermarked image becomes darker and finally becomes invisible. Fig. 5 shows the watermarked image using 3-level discrete wavelet transform for different value of k.
For the process of recovering the watermark from the watermarked image the value of k is kept constant at 0.009 and q is varied from 1.5 to 0.6. For the higher values of q the watermark becomes almost invisible and as the value of q is reduced best result is obtained, and if q is further reduced the recovered watermark becomes darker and PSNR decreases. Fig.6 shows the recovered image using 3-level discrete wavelet transform for different value of q.

(a) Original Image

(b) Watermark
-
Figure 4. Original and Watermarked image

(a) For k=1.5, q=0.009

(b) For k=.98, q=0.009

(c) For k=.78, q=0.009

(d) For k=0.6, q=0.009
-
Figure 5. Watermarked images using 3-level DWT for various values of scaling factors k

Figure 6. Recovered images using 3-level DWT for various values of scaling factors q
The values of the MSE (Mean square error) and PSNR values of the scaling factors k and q for 1-level, 2-level
TABLE I.
Comparison of 1-level, 2-level and 3-level dwt for watermarked image in terms of mse & PSNR
|
q |
k |
MSE Level1 |
PSNR Level1 |
MSE Level2 |
PSNR Level2 |
MSE Level3 |
PSNR Level3 |
Observation |
|
1.5 |
0.009 |
3200 |
13.08 |
3156 |
13.14 |
3100 |
13.24 |
|
|
1.0 |
0.009 |
1.48 |
46.55 |
1.42 |
46.60 |
1.397 |
46.68 |
|
|
0.98 |
0.009 |
1.98 |
45.16 |
1.88 |
45.37 |
1.74 |
45.72 |
Best Result |
|
0.95 |
0.009 |
21.33 |
34.84 |
20.85 |
34.94 |
20.08 |
35.10 |
|
|
0.90 |
0.009 |
21.3 |
28.00 |
100 |
28.08 |
98.16 |
28.21 |
|
|
0.85 |
0.009 |
247 |
24.21 |
243 |
24.29 |
240 |
24.41 |
|
|
0.78 |
0.009 |
551 |
20.71 |
540 |
20.79 |
530 |
20.91 |
|
|
0.6 |
0.009 |
1890 |
15.36 |
1900 |
15.43 |
1800 |
15.54 |
TABLE II.
Comparison of 1-level, 2-level and 3-level dwt for Recovered image in terms of mse & PSNR
|
q |
k |
MSE Level1 |
PSNR Level1 |
MSE Level2 |
PSNR Level2 |
MSE Level3 |
PSNR Level3 |
Observation |
|
1.5 |
0.009 |
4450 |
11.65 |
4385 |
11.7 |
4300 |
11.79 |
|
|
1.0 |
0.009 |
6.4e-26 |
310 |
2.5e-26 |
304 |
5.3e-26 |
301 |
|
|
0.98 |
0.009 |
7.11 |
39.6 |
7.016 |
39.67 |
6.90 |
39.74 |
Best Result |
|
0.95 |
0.009 |
44.46 |
31.65 |
43.85 |
31.71 |
43.11 |
31.79 |
|
|
0.90 |
0.009 |
178 |
25.6 |
175 |
25.690 |
170 |
25.76 |
|
|
0.85 |
0.009 |
400 |
22.1 |
395 |
22.169 |
390 |
22.24 |
|
|
0.78 |
0.009 |
861 |
18.78 |
849 |
18.84 |
840 |
18.92 |
|
|
0.6 |
0.009 |
2850 |
13.58 |
2810 |
13.649 |
1800 |
15.54 |
-
VI. Conclusion
In this paper, an image watermarking technique based on a 3-level discrete wavelet transform has been implemented. This technique can embed the invisible watermark into salient features of the image using alpha blending technique. Experiment results shows that the quality of the watermarked image and the recovered watermark are dependent only on the scaling factors k and q and also indicate that the three level DWT provide better performance than 1-level and 2-level DWT. All the results obtained for the recovered images and the watermark are identical to the original images.
Список литературы Image Watermarking Using 3-Level Discrete Wavelet Transform (DWT)
- Ibrahim, R. and Kuan, T. S., Steganography Imaging (SIS): Hiding Secret Message inside an Image. Proceedings of the World Congress on Engineering and Computer Science, 2010, San Francisco, USA.
- Er-Hsien Fu, Literature Survey on Digital Image Watermarking, EE381K Multidimensional Signal Processing, 1998.
- L. Robert, T. Shanmugapriya, A Study on Digital Watermarking Techniques, International Journal of Recent Trends in Engineering, 2009.
- G. Rosline Nesa Kumari, B. Vijaya Kumar, L. Sumalatha, and Dr V. V. Krishna, Secure and Robust Digital Watermarking on Grey Level Images, International Journal of Advanced Science and Technology, 2009.
- Baisa L. Gunjal, R.R. Manthalkar, An overview of transform domain robust digital image watermarking algorithms, Journal of Emerging Trends in Computing and Information Sciences, 2010.
- Darshana Mistry, Comparison of Digital Watermarking methods, 21st Computer Science Seminar SA1-T1-7, IJCSE, 2010.
- R. G. van Schyndel, A. Z. Tirkel, and C. F. Osborne, A digital watermark, in Proc. IEEE Int. Conf. Image Processing (ICIP), 1994.
- Blossom Kaur, Amandeep Kaur, Jasdeep Singh, Steganographic Approach for hiding Image in DCT Domain, International Journal of Advances in Engineering & Technology, July 2011.
- W. Hong and M. Hang, Robust Digital Watermarking Scheme for Copy Right Protection, IEEE Trans. Signal Process, vo.l2, pp. 1- 8, 2006.
- X. Xia, C. Boncelet, and G. Arce, A Multiresolution Watermark for Digital Images, Proc. IEEE Int. Conf. on Image Processing, Oct. 1997.
- Akhil Pratap Shing, Agya Mishra, Wavelet Based Watermarking on Digital Image, Indian Journal of computer Science and Engineering, 2011.
- Bhatnagar, G. and Raman, B., A new robust reference watermarking scheme based on DWT-SVD, Elsevier B.V. All rights reserved, 2008.
- Barni M, Bartolini F, Piva, An Improved Wavelet Based Watermarking Through Pixelwise Masking, IEEE transactions on image processing, 2001.
- D. Kundur and D. Hatzinakos, Digital Watermarking using Multiresolution Wavelet Decomposition, Proceedings, IEEE International Conference Acoustic, Speech, Signal Processing, 1998.
- Nilanjan Dey, Anamitra Bardhan Roy, Sayantan Dey, A novel approach of color image hiding using RGB color planes and DWT, International Journal of Computer Applications, 2011.


