Improving Energy of Modified Multi-Level LEACH Protocol by Triggering Random Channel Selection
Автор: Jaspreet Kaur, Parminder Singh
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 12 vol.8, 2016 года.
Бесплатный доступ
The energy has undergone a major concern in wireless sensor networks. One direction of the LEACH protocol would be towards a future in which four levels will continue to dominate. The other direction would be towards to improve these levels further and increasingly smaller amount of energy consumption. The support provided by the LEACH protocol has been crucial in which upgrade these levels and build smart distributed network. The previous scenario is not motivated by the scientific altruism. They are large number of clients in the proposed scenario and therefore have a good reason to encourage a scalable alternative for communication. LEACH protocol to take a leaf out of the proposed scenario and it has a good energy saver, less energy consumption. The proposed scenario needs to be better understanding the catalytic role played by the previous three levels LEACH protocol. It should also see whether there is scope for deploying more nodes through collaboratively proposed protocol with three level protocols.
Throughput, LEACH Protocol, Multilevel, Interference
Короткий адрес: https://sciup.org/15011730
IDR: 15011730
Текст научной статьи Improving Energy of Modified Multi-Level LEACH Protocol by Triggering Random Channel Selection
Published Online December 2016 in MECS
Understanding and solving the challenges of sensor networks will require a unique framework. Such a framework needs to have four parameters: energy, Throughput, Delay and Interference. By their nature, systems comprise parameters that are distinct and yet inter-related. Sensor Nodes are crucial to fulfill the objectives of IEEE 802.15 standard. Sensor Network Protocol need to work on energy related issues. Base Station node provides a comprehensive report of the node communication and its issues that create problem in future. Base Station can create time-bound application so every node give confirmation on limited time. Sensor nodes have discovered a hidden node on the network and remove the entire path of the network. This information has been conveyed to each node on the network. Over hundred sensor nodes were imported in the first time and 97% were followed the base station node and the remaining were peer to per fashion. Every node on the network was look upon the sensor request or reply packet. Now as the request is complete the services go up with multiple devices, it is the time for other devices to ride on the path for message transmission. The base station has look upon the routing table and on the basis of routing table it decides to restart the process for data. In the earlier number of nodes failed to send the data again.
The node deployment is usually done randomly by scattering nodes in the sensor field. In some applications, actuators (anodes) that control various devices can also be positioned within the sensor network. A collector node (cnode), which is often more capable than the other nodes in the field, is also located either inside or close to the sensor field.
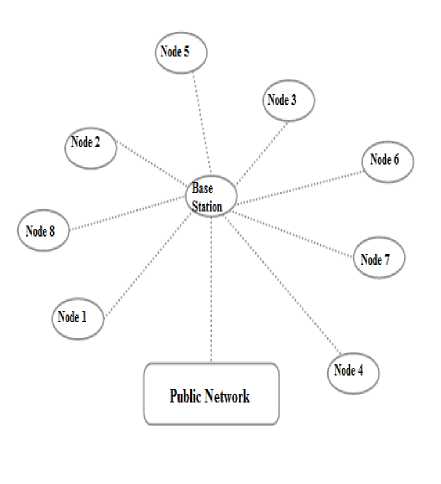
Fig.1.Wireless Sensor Networks [9]
Cnodes, usually called sinks or base stations, are responsible for collecting the sensed data from snodes and then serving the collected data to users. They are also responsible for starting task disseminations in many applications. The sensed data by snodes is conveyed through the sensor network by multiple hops in an ad hoc manner, and gathered in cnodes that can be perceived as the interface between sensor networks and users. Multiple sensor networks can be integrated into a larger network through the Internet or direct links between either cnodes or gateways.
-
A. Need of Multi-Level Protocol
The sensor nodes that have completed their communication be released from the occupied channel immediately. Noise level of the network has increased in every time and reduction policy applied by the given method. This method is improvement in the case of best channel selection. There are multiple interfaces to route the data in every corresponding direction that the particular node needs. Every interface attaches to each sensor node on the network and thus the performance graph increases. Noted that we maintained the performance factor in every level but still we are too far from performance of the network. Till now we are struggling.
-
II. Related Work
Ravi Kishore Kodaliet. al. [1], Pointed out multi-level LEACH protocol and every round has checked the energy level of each node. TDMA technique has deployed on the multi-level LEACH protocol and increased the performance of the network. On an average result have been analyzing values Joules in energy consumption, they added.
The other protocol analyzed by the authors [2], where the results has come down to previous approach results in wireless sensor networks. Divide and rule based technique applied on the density based network; while the throughput of the protocol value in previous work value comprising better in current work.
Heinzelman, et al. [3] Low energy adaptive clustering hierarchy (LEACH) is a cluster based protocol in which the role of a member node in the cluster is to sense the surrounding environment and transmit the sense data to the BS. The data collection area is randomly divided into several clusters. Based on time division multiple accesses (TDMA), the sensor nodes transmit data to the cluster heads, which aggregate and transmit data to Base station.
Kranthi K. Mamidisetty. al. [6], discussed dissemination of data or flooding. In this concept each and every node in the network sends the message to every node if the node does not want to that data from the source node. To avoid this spreading data all over the nodes in network, the author uses the multistage queuing network strategy.
Amit Patwardhan. al. [10], discussed path planning for wireless sensor network The author used 5*5 grid nodes means 25 nodes communicating with each other and performed four functions sleep, idle, listening and transmitting, with amount of energy consumption being in ascending order. The nodes used in the scenario maintain a constant path for all the traversals of the base node is equally bad since even this will result in the formation of energy holes in the network.
In [13] author addressed the issue related to throughput maximization and delay minimization and suggested the linear programming based solution. Author in [14] conducted a comprehensive study on the evaluation of LEACH based clustering protocols, where evaluation multilevel routing protocols on the basis of scalability and traffic constrain
-
III. Working With Multilevel Leach
Multi-Level LEACH protocol has been looked upon something that is synonymous with regulating sensor size and reproductive energy. The planning of the network is such that the vision of reaching out to an additional new sensor which was enters by the approval of base station node. The goal of this paper is to improvement of throughput and lesser delay during communicative node. It enforced the nodes to make a decision according to routing table and this decision relating to their recommunication, new communication or any link failures. Previous energy related issues are not optimal solution or contraception, especially nodes, must have say in decision to re-communication.
-
A. Comparing of LEACH and Its Variants
In this paper Table 1.1, shows the comparison of Three Levels with LEACH protocol and thus we analyzed that we need to modify these levels for improvement in the area of sensor network.
Table 1. Comparing Multi-Level LEACH Protocols
|
Parameter |
LEACH |
Level-1 |
Level-2 |
Level-3 |
|
Algorithm Implemented |
Every Node |
Base Station |
Centralized only |
Centralized only |
|
Scheduling |
TDMA |
No TDMA |
TDMA |
TDMA |
|
Energy Conserved |
Less |
Less |
Less |
More in Level 1 and Level-2 |
|
Coverage Area |
Less |
More than LEACH |
More than LEVEL-1 |
More than Level-2 |
|
Parameter |
LEACH |
Level-1 |
Level-2 |
Level-3 |
-
IV. Proposed Algorithm
The gap between proposed and previous approach is huge and there is trust deficit even more among the proposed approach. Proposed model pick up higher energy nodes from the network pool. If the centralized main node is ensured of a good linkage with communicating sensor nodes could benefit to route the data to other hundreds of nodes. The source node sent a message to provide additional amenities at node 15 near node 5 where a noted node dedicated to node 16 is located. This model is closely associated with MultiLevel LEACH and has a separate channel dedicated to each node. As the network is located in an area 1000 meter X 1000 meter, there is a facilitating to retransmission of packet, alarm collision in the channel to accommodating more sensor node. The main node has developed a channel of source node and receiver node. There has been spurt in the number of sensor nodes visiting in the cluster network which provides a separate channel dedicated to receiver node. The proposed work has completed the preliminary work including making random channel and to build channel to carry data or messages for the sensor networks. The algorithm after some modification would be applied to the network model. The main sensor node would be providing routing table and other necessary facilities to the entire sensor nodes on the network model. Referring ail [7] said various other. With the central sensor node rejecting the other node who did not give the MAC address to make amendments in the proposed algorithm. In the reply of MAC address given by the requesting node and is to be accepted by the central main node. If the node struggle for sending the data then central main node has assured to provide another shortest route for data transfer. Representatives of the sensor nodes in the network model have extent to support the central main sensor node.
Assume that if there are n antennas of the communicating nodes in the network and they want for communication, thus, we allocate the channels to each node on the network. We are calculating the power of the sensor nodes individually from equation 1.
Ps
Pr
For any path loss in the channel the equation 2 calculates the energy loss during link disconnection.
Ps
PL = log 10 n„
Fig.2. Multi-Path Wideband Channels
The multi-path communication has not possible in sensor networks due to narrowband channel selection technique. Thus, the energy consumption tends to increase such a way that affect the performance of the Multi-Level Network. Below figure 1.2, shows the multi- path channel selection but we adopt wideband channel to resolve the issues faces in narrowband selection technique.
Suppose there is channel pool C and ¥ C is the random channel selecting from the channel pool. The channel is selecting in such a way that no two channels with have a same frequency band. Then, the corresponding equation configure on the network simulation model.
¥c= +( d 2- d 1)+ Ps + Pr + t (3)
In the channel selection approach the delay has been calculated by subtracting d2, d1and observed time is shown in t.
-
V. Simulation and Results
During experiment conducted on a test bed of 100 sensor nodes, packet loss for each link was measured every minute for two hours under various topology setting. Although the majority of links were good, 10% of the nodes exhibited a packet rate loss greater than 2%. The test bed consisted of running the modified fixed probabilistic version of LEACH over a 100m x 1000m area. Each node has a transmission range of 250m, and the distance between two successive nodes was 180m and 200m. The constant bit rate (CBR) data traffic of 4packets/sec connecting node 0 to node 4 was used.
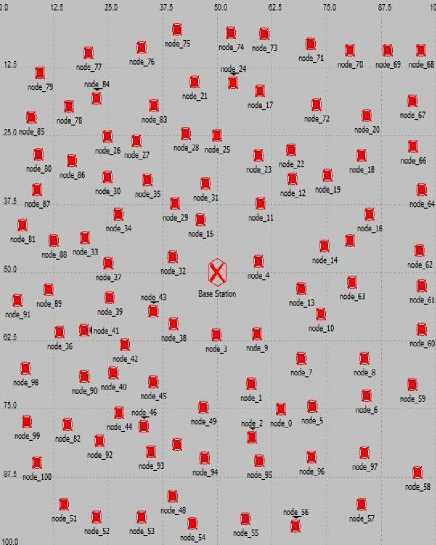
Fig.3. Multi-Level Experimental Model
In the Experimental model presented in Figure 2, nodes 3, 4, 9, 38, and 43 sense the presence of a nearby nodes. Nodes 3–4 each send a message to node 38 with their observed sensor data. Node 3 forwards the received messages, along with its own set of sensor readings, to the next node along the path to the base station.
Thus, node 3 sends a total of 5 messages, which are all subsequently relayed from node to node, until they reach the base station. In total, 29 messages are transmitted throughout the network. A reduction in communication and energy costs are possible if collected sensor data is aggregated prior to relaying.
-
VI. Analysis and Results
The following results have been calculating that was studied in figure 3 and now we are explain it results
-
A. Throughput
Throughput is typically defined as the rate at which messages are serviced by a communication system. It is usually measured either in messages per second or bits per second. In wireless environments it represents the fraction of the channel capacity used for data transmission. Throughput increases as the load on the communication system increases initially. After the load reaches a certain threshold, the throughput ceases to increase, and in some cases, it may start to decrease. An important objective of a MAC protocol is to maximize the channel throughput while minimizing message delay.
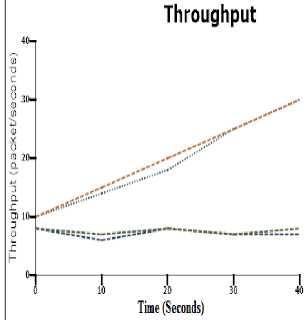
| Proposed Packet Sent
I Proposed Packet Reciered
■ Previous Packet Sent I Previous Packet Reciered
Fig.4. Throughput of the Multi-Level LEACH Protocol
From above figure (figure 4) clearly shows that the normalized throughput of Base Station increases to a maximum of 20 to 30 packets/seconds respectively when the sent is increased from 10 to 70% increases, and dropped to approximately 10 to 40 seconds respectively when the forwarding packet is increased. This throughput is examined in more than hundreds of nodes.
-
B. Channel interference
-
802.11 does not have support aided by transmit power for transmit power control (TPC), sub channelization or dynamic channel selection and support for adaptive (DCS). A number of PHY considerations were taken into account for the target environment. At higher frequencies, line of sight (LOS) is a must.
In adjacent channel interference, the signals in nearby frequencies have components outside their allocated frequency ranges, and these components may interfere with on-going transmissions in the adjacent frequencies. The range within the intended receiver may be subject to interference from other transmission sources, thereby causing the rate of transmission errors to be higher than desired. For the Physical layer configuration, the interference of individual sensor nodes varied from 0.3 to 0.9, with an overall average interference of 0.3 Watt for the entire sensor network.
The nodes with the best reliability were those placed closest to the sink node. Nodes located farthest from the sink node and along the edges of the sensor network exhibited the most packet loss. The hop count for messages to reach the destination varied from a minimum of 1 hop to maximum of 8 hops.
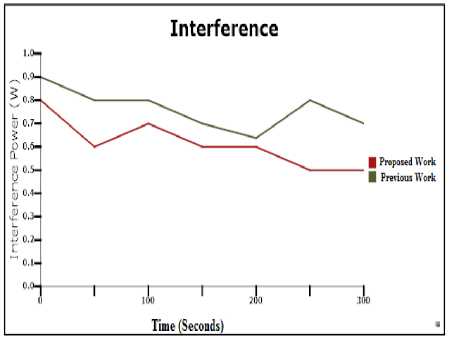
Fig.5. Channel Interference of Multilevel LEACH Protocol
-
VII. Conclusion
It should be analyzed from the results that we have analyzed from the section V1.
Table 2. Comparison of Interference
|
Parameter |
Minimum |
Average |
Maximum |
|
Previous Work |
0.6 |
0.7 |
0.9 |
|
Proposed Work |
0.5 |
0.6 |
0.7 |
As per the information received from the network simulator; the interference from the previous work is more than that of proposed work. The value is slightly down in the case of proposed when more than 50 nodes complete their communication and base station maintained the MAC Table.
Table 3. Comparison of Throughput
|
Parameter |
Minimum |
Average |
Maximum |
|
Packet Sent (Previous) |
7 |
7 |
8 |
|
Packet Receive (Previous) |
6 |
7 |
8 |
|
Packet Sent (Proposed) |
15 |
20 |
25 |
|
Packet Receive (Proposed) |
15 |
20 |
25 |
We have been studying the throughput of the network and we concluded that the proposed scenario gives higher value than previous work. This throughput figure out the comparison of packet received divided with packet sent. From the comparison table if we add some modification in the multi-level LEACH protocol as discussed in section4; the performance of the network remains high.
Acknowledgement
We wish to thank our parents for their good upbringing which help us to do good works in every field of life.
We would like to thanks all our professors in our respective departments to help and guide us in the ways we needed to get success in this field of research. Without their stimulating guidance, encouragement and suggestions, this research work would not have been possible. We also thank all faculty members of Information technology Department for constructive suggestions to improve the quality of this research work and providing such a great academic environment.
Finally, thanks to all our friends for their support and encouragement.
Список литературы Improving Energy of Modified Multi-Level LEACH Protocol by Triggering Random Channel Selection
- Jianli ZHAO, Lirong YANG, "LEACH-A: An Adaptive Method for Improving LEACH Protocol", Sensors & Transducers, Vol. 162, Issue 1, January 2014, pp. 136-140.
- Jiman Hong, Joongjin Kook, Sangjun Lee, Dongseop Kwon, Sangho Yi, "T-LEACH: The method of threshold-based cluster head replacement for wireless sensor networks", Inf Syst Front, Springer Science, 2009, pp.513-521.
- N.Israr, I.Awan, "Converge based inter cluster communication for load balancing in heterogeneous wireless sensor networks", Telecommun Syst, 2008, pp.121-132.
- S.Koteswararao, Dr. M. Sailaja, P. Ramesh, E. Nageswararao, V. Rajesh, "Sensor Networks Simulation in NS2.26" ,IJECT,2011, pp.251-254.
- Ravi Kishore Kodali, Naveen Kumar Aravapalli, "Multi-level LEACH Protocol model using NS-3", IEEE, 2014, pp.375-380.
- Gilbert Chen, Joel Branch, Michael J. Pflug, Lijuan Zhu, Boleslaw K. Szymanski, "SENSE: A Wireless Sensor Network Simulator", Advances in Pervasive Computing and Networking, Springer, 2004, pp.249-267.
- Amit Patwardhan, "Energy based path planning for wireless sensor networks", International Journal on Emerging Technologies, 2010, pp.16-18
- P. Chevillat, J. Jelitto, A. Noll Barreto, H.L. Truong, "A Dynamic Link Adaptation Algorithm for IEEE 802.11a Wireless LANs", IEEE, 2003,pp.1141-1145.
- A. Ahmad, K. Latif, N. Javaid, Z. A. Khan, U. Qasim, "Density Controlled Divide-And-Rule Scheme For Energy Efficient Routing In Wireless Sensor Networks", 2013.
- The Network Simulator - ns-2. http://www.isi.edu/nsnam/ns/
- Kiran Maraiya Kamal Kant Nitin Gupta, "Application based Study on Wireless Sensor Network", International Journal of Computer Applications, volume 21– No.8, 2011.
- Amir Akhavan Kharazian, Kamal Jamshidi, Mohammad Reza Khayyambashi, "Adaptive Clustering in Wireless Sensor Network: Considering Nodes with Lowest Energy", IJASUC, 2012, pp.1-12
- Amiya Nayak and Ivan Stojmenovic, "Wireless Sensor and Actuator Networks", Wiley, 2010.
- Jaspreet Kaur, Parminder Singh "Measuring the data routing efficacy in LEACH Protocol", IEEE INDIACom-2016.
- Parminder Singh "Comparative study between unicast and Multicast Routing Protocols in different data rates using vanet", IEEE February 2014, pp. 278-284.
- Sheffy Jasuja, Parminder Singh "Accountability of WMNs using BEB Algorithm", Volume 5, 2015
- Manish Kumar jha, Atul kumar pamdey, Dipankar pal, "Energy-efficient multilayer Mac protocol for wireless sensor network" n.209 216.
- Bachar Rachid, Haffaf Hafid "Distributing Monitioringfor wireless Sensor Networks: a Multi-agent approach", September 2014 IJCNIS 13-23.
- Kushlendra kumar pandey, Neetesh Purohit, Ajay Agarwal "Efficient Clustering Technique for cooperative wireless sensor network", IJCNIS 2014 40-4.
- Sachin Gajjar, Nilav Choksi, Mohanchur Sarkar, Kankar Dasgupta "LEFT: A Latency and Energy EfficientFlexible TDMA Protocol for Wireless Sensor Networks", IJCNIS januray 2015 vol 7 N2, pp 1-14.
- T.S. Rappaport. "Wireless communications: principles and practice", Prentice Hall, 2nd edition, 2002.


