Integrity Analysis of Multimedia File Transmission between Mobile Phones
Автор: Sweta Deana Bye. Dhondoo, Vidasha. Ramnarain-Seetohul, Razvi. Doomun
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 9 vol.6, 2014 года.
Бесплатный доступ
Mobile forensics deals with evidence from mobile devices. Data recovered from the mobile devices are helpful in investigation to solve criminal cases. It is crucial to preserve the integrity of these data. According to research carried out [1], it has been noted that not all data extracted from mobile phones have discrepancies in hash values during integrity verification. It has been reported that only the Multimedia Messaging Service message type showed a variation in hash values when performing data extraction. The main objective in this work is to study the variance in the content of the graphic files transferred between mobile phones via Bluetooth or MMS. We also determine the causes of such variations, if any, while checking the graphics file integrity. Different parameters including distance and file format have been varied and a series of test were conducted using: mobile sets of same make same model, same make different model and different make different model on different graphic file formats of different sizes. Results obtained confirmed that there was no alteration of graphic files during Bluetooth transmission. However, while transmitting the graphic files through Multimedia Messaging Service, results showed notable alteration level for graphic files of certain file format and size.
Mobile devices, Mobile forensics, Bluetooth, Multimedia Messages, graphic file
Короткий адрес: https://sciup.org/15011339
IDR: 15011339
Текст научной статьи Integrity Analysis of Multimedia File Transmission between Mobile Phones
Published Online August 2014 in MECS DOI: 10.5815/ijcnis.2014.09.04
The population of mobile phone users is increasing rapidly worldwide. Hence over the last few years, mobile forensics has been gaining much attention from researchers and has become an active area of research. Data recovered from the mobile devices namely the phonebook information, appointment calendar information, text messages, call logs, photos; audio, video recordings and multimedia messages are helpful in investigation and in solving criminal cases. For mobile forensic investigation, data integrity implies correctness of data from evidence collection to reporting in court of law. Data integrity check proves correctness of data that is there is no alteration to the evidence. Cryptographic hashing algorithms, e.g. MD 5 and SHA, are used to verify the integrity of the evidence (data) obtained from the mobile devices. If there is a single bit change in the data during/after evidence extraction, recomputed hash values will differ. Research works have proven that there is a problem occurring during transmission of graphic files by Multimedia Messaging Service (MMS). The content of the graphic files undergoes alteration during the transmission by MMS. MMS is an extension of the basic Short Message Service (SMS). It is a standard way of transferring messages that involve multimedia content to and from mobile devices. The MMS standard possesses the ability to generate messages with text, sound, video and images. MMS messages may comprise of multiple pages known as slides; each slides consisting of its own text, sound, video and images. MMS can be sent from one mobile device to another mobile device and from a mobile device to an email address. Different mobile sets support different picture resolution. Studies [1] concluded “inconsistencies occur when mobile device graphic files are transferred using MMS”. The file size of the graphic files does change during transmission through MMS, thus causing a change in recomputed hash value. The study carried out in [2] showed that transfer of graphic files via MMS showed different hash values even between the same make and model of phone. Previous research work on this alteration happening during MMS transmission has been minimal. Most research done have mentioned about an existing variation in MMS transmission with little focus on the grounds behind this alteration. The aim of this research work is to further investigate on the causes of graphic files changes during transmission by Bluetooth or MMS and determine the different parameters not included in past studies for the existing variations. Different parameters including distance , file format ,file size and network carrier have been varied and a series of test was conducted using: mobile sets of same make same model (SMSM), same make different model (SMDM) and different make different model (DMDM) on different graphic file formats of different sizes.
This rest of the paper is organized as follows: Section II describes the related works and section III presents the methodology used. Experimental results are explained in section IV and discussions are reported in section V. Finally, section VI concludes the paper.
Ikb 25kb I 60kb HOkb 250kb 500kb 810kb 1200kb 1500kb 18OOkb
200Ckb 255Okb
-
II. Related works
MMS can be sent from one mobile device to another mobile device and from a mobile device to an email address. MMS is viewed as a complicated standard employed by mobile phones due to its numerous challenges. One of its major challenges remains carriers and mobile make/models incompatibility . As incompatibility exists between mobile manufacturers and even between mobile carriers, risks of "interoperability" issues are high. Different mobile devices support different picture resolution; some support low-resolution while others support higher. With time, mobile sets are evolving faster and with higher resolution capabilities. As reported in [3], there are some limitations in the MMS SMIL specification. Most are related to the limited screen size and limited processing capabilities of different mobile devices available at that time [3]. According to research carried out [1], MMS hash values for transmitted graphic files were found to be inconsistent within different mobile device families. The hash inconsistencies were related to different mobile device MMS format implementations. Hence research works have proven that there is a problem occurring during graphic file MMS transmission at the level of the hash values which alter; compromising the quality and authenticity of MMS content.
-
III. Methodology
A series of test was conducted using different mobile sets through two different local carrier networks. The mobile sets include:
-
• set of Same Make Same Model – SMSM : Nokia C2-01
-
• set of Same Make Different Model – SMDM : Nokia Asha 311
-
• set of Different Make Different Model – DMDM : Sony Ericsson Txt Pro
Mobile sets were used for the graphic file transmission while a personal computer was used as workstation for the hashing and other analysis processing. Different test series were simulated and processed via the workstation. The results of each series were compared to note the different observations obtained from each test. For both Bluetooth and MMS graphic file transmission, same original graphic files were used. In this study, graphic files with format bmp, gif, jpg and png have been used. Fifty-two graphic files have been chosen to carry out the tests. Selection of the fifty two files were based on the file format, file size and file dimension. The file size were ranged from 1kb to 2550kb; chosen at random interval. The file size of each 13 graphic file for each formats were as follows:
-
A. Test for Bluetooth
Parameters involved for Bluetooth tests were:
-
• Distance: Tests were conducted at 1 meter
interval up to 10 meters.
-
• Other interfering devices such as radio,
television, other mobile devices
-
• Space:
Tests were carried out:
o within same room (1 to 5 meters) – closed space o within same open space (1 to 10 meters) – without obstacles between the transferring devices and o within different space (1 to 10 meters) – with obstacles between the transferring devices like walls
-
• Time:
Taking time into consideration, tests were conducted at peak hours and during other periods as well. Test series were repeated thrice a day; early morning, mid-day and evening.
-
• Four different graphic file formats used were: bmp, gif, jpg and png
-
• Different graphic file size were used: 1kb to 2550kb
The different test series conducted for Bluetooth are listed in the table 1 below.
Table 1. Bluetooth Test Series
Test Category Test Series (Sending original graphic files)
SMSM Nokia C2-01 s ending to an other Nokia C2-01
Nokia C2-01 sending to Nokia Asha 311
SMDM Nokia Asha 311 sending to Nokia C2-01
Nokia C2-01 sending to Sony Ericson Txt Pro
DMDM Sony Ericson Txt Pro sending to Nokia C2-01
Bluetooth Simulation
Fig. 1. below illustrated the process of the Bluetooth test series:
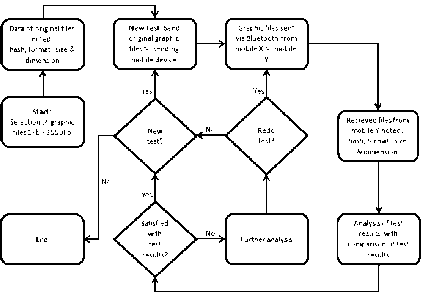
Fig. 1. Bluetooth Test Series Flowchart
Step 1: The comparative study for Bluetooth began by extracting a list of original graphic file from the mobile set X to the workstation.
Step 2: All the hashing process were computed on the original graphic file (from mobile X) individually on the workstation. Information including image dimension, image size in kb, image file format, image RGB/HSV and Exif information about of each image was noted.
Step 3: From the mobile set X, the same list of graphic files was sent to another mobile set Y via Bluetooth.
Step 4: The list of graphic files received on mobile set Y was hashed and other image information was recorded.
Step 5: The hash values obtained for test series on mobile set Y were compared to the known start value of mobile set X (Hash value of original files to those of received files). The graphic files were transferred from the mobile devices to the workstation and vice versa before and after Bluetooth and MMS transmission by using USB cable in order to ensure integrity of data.
-
B. B.MMS Simulation
The table 2.0 below describes the test series conducted for MMS over carrier A and B. Fig 2 illustrates each step.
Table 2.0: MMS Test Series
Test Category Test Series (Sending original graphic files)
Nokia C2-01 sending to another Nokia C2-01
SMSM Nokia C2-01 sending to the same set Nokia C2-01 (itself)
Nokia C2-01 sending to Nokia Asha 311
SMDM Nokia Asha 311 sending to Nokia C2-01
Nokia C2-01 sending to Sony Ericson Txt Pro
DMDM Sony Ericson Txt Pro sending to Nokia C2-01
Test Category Test Series (Resending early received graphic files)
|
SMSM |
Nokia C2-01 resending to Nokia C2-01 |
|
SMDM |
Nokia C2-01 resending to Nokia Asha 311 |
|
DMDM |
Nokia C2-01 resending to Sony Ericson Txt Pro |
Test Category Test Series (Receiving devices sending to early sending device)
SMSM Nokia C2-01 sending to Nokia C2-01
SMDM Nokia Asha 311 sending to Nokia C2-01
DMDM Sony Ericson Txt Pro sending to Nokia C2-01
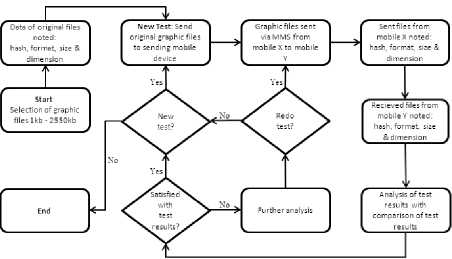
Fig. 2. MMS Test Series Flowchart
Step 1: The comparative study for MMS began by extracting a list of original graphic file from the mobile set X to the workstation.
Step 2: All the hashing process were computed on the original graphic file (from mobile X) individually on a workstation. Information including image dimension, image size in kb, image file format, image RGB/HSV and Exif information of each image was noted.
Step 3: From the mobile set X, the same list of graphic files was sent to another mobile set Y via MMS transmission.
Step 4: The images information of the sent images from mobile set X were again noted and the hash value was computed for each graphic file.
Step 5: The list of graphic files received on mobile set Y was hashed and other image information was recorded.
Step 6: The hash values obtained for test series on mobile set Y were compared to the known start value of mobile set X (Hash value of original files to those of sent ones and those of received files).
-
IV. Experimental results
The 13 original graphic files of each file format were hashed and noted with their original dimension, size and format. Fig. 3 shows the information retrieved about the 52 original graphic files.
|
TSERIES |
IMAGE FILES |
ORIGINAL |
||
|
Name |
Hash Values |
Dimension |
Size Format |
|
|
bmp_ 1 KB. bmp |
758c98e4a7565953e9a4a9ad0661 f2b5 |
20x20 |
0.34 bmp |
|
|
Original |
gif_lKB.gif |
a9f4d741 a35ec8528839e3 fd5 fa30092 |
32x32 |
0.52 gif |
|
< Ikb |
jpg_lKB.jpg |
al99cae88d60412b8Oe6bce4OOf2d757 |
33x20 |
0.88 jpg |
|
png_lKB.png |
fe924a666fab(te509fb23996da30a97f |
64x64 |
0.68 png |
|
|
bmp_2KB.bmp |
200264812blObObca55735cb3eb6896d |
44x22 |
1.99 bmp |
|
|
Original |
gif_2KB.gif |
17993da81c611 !23a3d66fad207f47d5 |
29x35 |
1.99 gif |
|
2kb |
jpg_2KB.jpg |
3ae c7 aa6O8f73e719ee dd8c456173da9 |
64x64 |
199 jpg |
|
png_2KB.png |
1775a0ce09fdf7 2ce5a72dbcb769222c |
32x32 |
1.99 png |
|
|
bmp_25KB.bmp |
af97fdc3a256dl4b43e34b28c4eaad47 |
181x133 |
24.9 bmp |
|
|
Original |
gif_25KB.gif |
630b392c8 fdcf03b85 973d577da01 daO |
50x50 |
24.9 gif |
|
25kb |
jpg_25KBjpg |
6a63a3ac3991 ff6eee645ae fc9c94185 |
800x490 |
24.9 jpg |
|
png_25KB.png |
abb77a2ldea420b5ec 160I4899fd59b7 |
400x300 |
24.9 png |
|
|
bmp_60KB.bmp |
ее f2O8d75 b69f44b9d76e 8de41 c08b23 |
300x201 |
59.9 bmp |
|
|
Original |
gif_60KB.gif |
40 lc7a6O771dd672878333723d2bd2eb |
88x88 |
59.9 gif |
|
60kb |
jpg_60KB.jpg |
6d31 b31374f2e3a9Bdfabd243af593cf |
640x393 |
59.9 jpg |
|
png_60KB.png |
3 8c24850fd83dl b5affl)500a0dbd0916 |
700x700 |
59.9 png |
|
|
bmp_llOKB.bmp |
0e903f5c 2d2ca3147e d9be3c6O2ba35e |
332x113 |
109 bmp |
|
|
Original |
gif_l 10KB.gif |
163O2ObO2a5al4dlec2f5ba8c4lbl2de |
203x186 |
109 gif |
|
llOkb |
jpg_HOKH.jpg |
4a5O41c7ec 153fe610b63a7354fe00d5 |
665x425 |
109 jpg |
|
png_l lOKB.png |
06b7 ГОс 19d29fiO45a91 Ia96f7963669 |
195x250 |
109 png |
|
|
bmp_250KB.bmp |
677f76575a24ecl 89cla945ff6fedef2 |
348x245 |
249 bmp |
|
|
Original |
gif_25OKB.gif |
80e97dafab9296a75bb336856991 c624 |
310x180 |
249 gif |
|
250kb |
jpg_250KB.jpg |
ab933913ba25652d514c64a239f59fal |
1001x653 |
249 jpg |
|
png_250KB.png |
025cb9cd2af4284235Oecf569edfffd |
400x302 |
249 png |
|
|
bmp_500KB.bmp |
b 19019760978555fbe4c4a394098da3f |
585x292 |
499 bmp |
|
|
Original |
gif_500KB.gif |
50c6ea7e9e0e7 d!9c2a58f 13e 281 fb55 |
500x285 |
499 gif |
|
SOOkb |
jpg_500KH.jpg |
cb8127b42a578ad4c141е977 13628ba3 |
1004x677 |
499 jpg |
|
png_500KB.png |
d4a63559e f40e72dd2O6c612e3bd8a20 |
700x479 |
499 png |
|
|
bmp_810KB.bmp |
bff 15d8d25aada02edabc86b51 bc9330 |
576x480 |
810 bmp |
|
|
Original |
gif_8IOKB.gif |
134693e4b6e61125cOc7932f4O3b5332 |
513x593 |
810 gif |
|
SlOkb |
jpg_81OKB.jpg |
03325071e4c35a0fd58dafe6442dc5dd |
1024x957 |
SI0 jpg |
|
png_8 lOKB.png |
0d7 !4fe5ea64add901bf37ba68fcc7a5 |
700x525 |
810 png |
|
|
bmp_1200KB.bmp |
44b448e342b512e Od 10cacd3f99e3e2a |
1022x400 |
1198 bmp |
|
|
Original |
gif_1200KB.gif |
0cba6cfaadef 1 e500f6b7 bd58bd6772b |
400x165 |
1198 gif |
|
1200kb |
jpg_1200KB.jpg |
8bb2319049c6 5e068df7bd4a799ec6a8 |
836x1922 |
119S jpg |
|
png_ 1200KB.png |
47b6 8b41 C3a68da3 0dfbf078d7f0a51a |
1000x1000 |
1198 png |
|
|
bmp_1500KB.bmp |
388e5d204bd549fafc601 Ia8cdbb588d |
703x546 |
1499 bmp |
|
|
Original |
gif_1500KB gif |
33886b27bd678dQ7369f52e921016666 |
350x198 |
1499 gif |
|
1500kb |
jpg_ 1500KB.jpg |
e6f898ddc3ba6975b9776f2f3a8f35 9e |
1858x1858 |
1499 jpg |
|
png_ 1500KB.png |
9386aS33ec7946d7435b7a9cdc808cd6 |
777x630 |
1499 png |
|
|
bmp_l800KB.bmp |
76ca77Da5bf52ae94cf8b2dd7427e 1 d |
1203x510 |
1798 bmp |
|
|
Original |
gif_1800KB.gif |
9f383d4c273520aa33dae30997aOe9da |
500x150 |
1798 gif |
|
IBOOkb |
jpg_1800KB.jpg |
bd60bc2bl bcdl 21 Ье5эЬ3848447э3829 |
1050x1485 |
1798 jpg |
|
png_ 1800KB.png |
7612855a524c !9bP 6321 e 137a348b 18 |
990x816 |
1798 png |
|
|
bmp_2000KB. bmp |
41 a57 le fa 14c85aa8ea 138ae8706a42f |
1214x562 |
1999 bmp |
|
|
Original |
gif_2000KB.gif |
15f4d4940665f 1 a6c40c574002a800db |
360x640 |
1999 gif |
|
2IIOOkb |
jpg_2000KB.jpg |
e54faaf5d212eaa7a34c6352f7f8b9d6 |
1500x1500 |
1999 jpg |
|
png_2000KB.png |
lacl 195eb29ee965d6f6e7b2d8d77026 |
1152x864 |
1999 png |
|
|
bmp_2550KB.bmp |
129fb283 33ff9 lelee7574bb06353262 |
1280x680 |
2550 bmp |
|
|
Original |
gif_2550KB.gif |
4eb262df-te450d4dl289cdal 1799195 8 |
360x640 |
2550 gif |
|
255Okb |
jpg_2550KB.jpg |
ab6bd0ae70ecdc9dc44504d2d00b893b |
1575x2362 |
2550 jpg |
|
png_2550KB.png |
e9d363e26f24498d427f8565ebe 196ee |
1280x800 |
2550 png |
|
Fig 3: retrieved results
Test series for Bluetooth
Test Category SMSM
SMDM
DMDM
Test Series (Sending original graphic files) Nokia C2-01 sending to another Nokia C2-01 Nokia C2-01 sending to Nokia Asha 311 Nokia Asha 311sending to Nokia C2-01
Nokia C2-01 sending to Sony Ericsson Txt Pro
Sony Ericsson Txt Pro sending to Nokia C2-01
Bluetooth Acquisition % SMSM-SMDM-DMDM
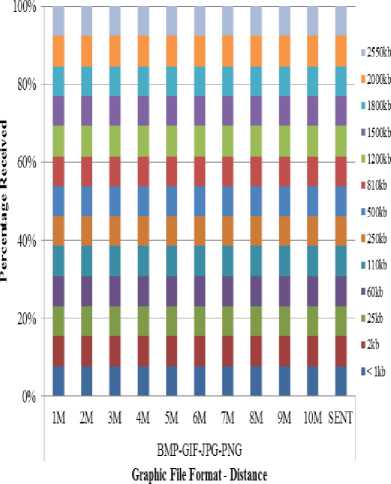
Fig. 4. Percentage of graphics files vs. distance
The graphic files were received as they were sent i.e. same as the original graphic files. As Fig. 4 illustrates, graphic files transmission via Bluetooth were sent at 100%. Hence there was no alteration in file size, dimension, file format or hash value independent of distance and other interference devices or frequencies for SMSM, SMDM and DMDM. Graphic files sent using Nokia Asha 311 and Sony Ericsson Txt Pro via Bluetooth to Nokia C2-01 resulted in same data. No alteration in file size, dimension or hash values.
As stated in past studies, bandwidth could lead to data lost if too limited. However, in this study, the transmission of graphic files showed no variation in the data transferred most probably as no high level compression is required to transfer graphic files compared to video transmission.
Direct communication between Bluetooth devices (no intermediate) can as well explain the 100% acquisition rate of graphic files via Bluetooth. Even with other interfering parameters, results show that not all interference affects Bluetooth graphic file transmission. Future works can confirm whether transmission variation can arise with Bluetooth if there is interference in the same frequency range of Bluetooth.
Test series for MMS
|
Test Category |
Test Series (Sending original graphic files) |
|
SMSM |
Nokia C2-01 sending to another Nokia C2-01 Nokia C2-01 sending to the same set Nokia C2-01 (itself) |
|
SMDM |
Nokia C2-01 sending to Nokia Asha 311 Nokia Asha 311sending to Nokia C2-01 |
|
DMDM |
Nokia C2-01 sending to Sony Ericsson Txt Pro Sony Ericsson Txt Pro sending to Nokia C2-01 |
|
Test |
Test Series (Resending early received |
|
Category |
graphic files) |
|
SMSM |
Nokia C2-01 resending to Nokia C2-01 |
|
SMDM |
Nokia C2-01 resending to Nokia Asha 311 |
|
DMDM |
Nokia C2-01 resending to Sony Ericsson Txt Pro |
|
Test |
Test Series (Receiving devices sending to |
|
Category |
early sending device) |
|
SMSM |
Nokia C2-01 sending to Nokia C2-01 |
|
SMDM |
Nokia Asha 311 sending to Nokia C2-01 |
|
DMDM |
Sony Ericsson Txt Pro sending to Nokia C2-01 |
Result obtained shows that jpeg file showed variation below 500 kb on carrier A. Gif files were received as sent on both carrier A and B. However, for other formats like bmp, png, data below 500 kb showed no variation between original, sent and received file via all mobile sets and carriers. Hence, alteration between sent and received files occurred only through carrier A. These are illustrated in Fig. 5, 6 and 7.
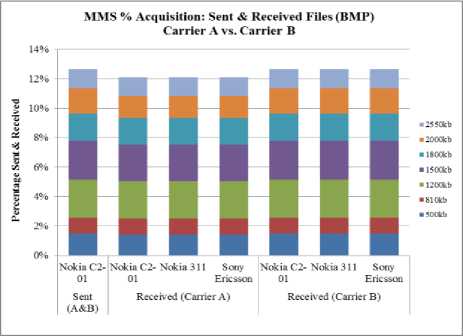
Fig. 5. Sent and Received BMP files
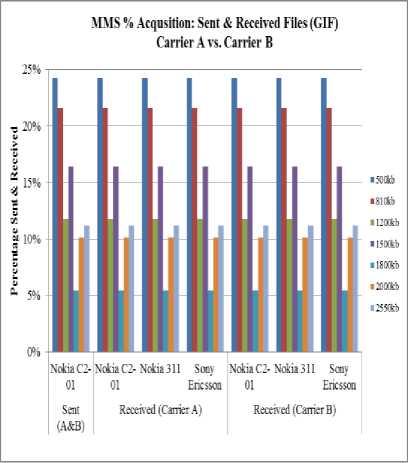
Fig. 6. Sent and Received GIF files
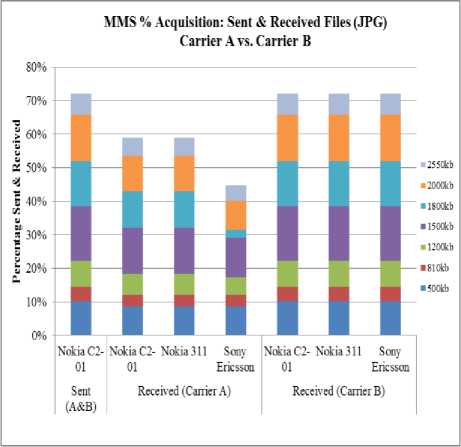
Fig. 8. Sent and Received JPG files 500-2550 kb
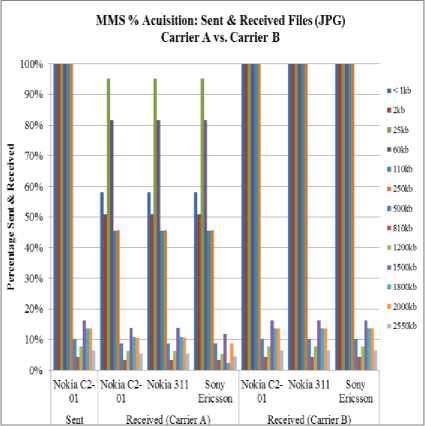
Fig. 7. Sent and Received JPG files
Fig. 8 illustrates variations of JPG files of size 5002550 kb on carrier A and carrier B. Result shows that there is variation on only carrier A.
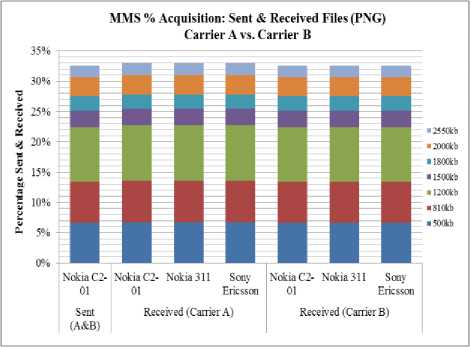
Fig. 9. Sent and Received PNG files
All JPG files have shown variation on carrier A. Results shows that file size less than 1 kb also shows variation on carrier A. However, no alteration was observed in received files via carrier B for jpg files.
Fig. 9 illustrates the variation of PNG files over carrier A and carrier B. Result concludes that there is an increase in file size over carrier A while in carrier B no variation was noted for files sent and received.
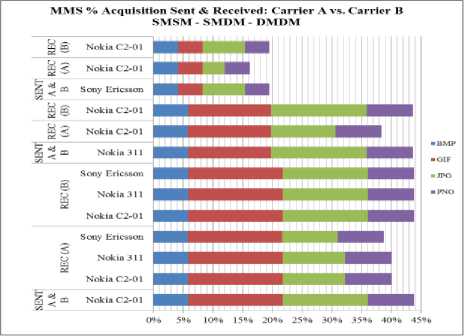
Fig. 10. Sent and Received BMP, GIF,JPG and PNG files
|
Original |
From |
From |
From |
|
JPG |
Nokia C2- |
Nokia Asha |
Sony |
|
Files >= |
01 |
311 |
Ericsson |
|
500kb |
SMSM |
SMDM |
TP |
|
DMDM |

Fig. 10 summarizes the MMS tests over carriers A and B using different mobile sets. The alteration between original files and sent files remain same over both carriers and using the different mobile sets. However, received files over carrier A showed alterations while no variations were noted from data sent via carrier B . Via carrier A, SMSM and SMDM showed same alteration on the received files. For DMDM, the alteration was different from the two other sets. Carrier B noted 100% of acquisition rate from what was sent from SMSM, SMDM and DMDM.
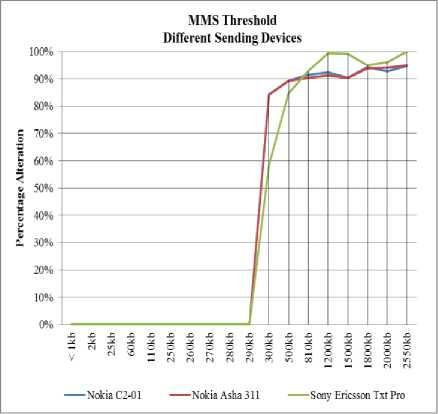
Fig. 12. MMS Threshold
Fig. 11 shows how the jpeg files vary when sent over carrier A and carrier B from different mobile sets. Results conclude that the file size and file dimensions are changing.

836x1922 522x1200 696X1600 160x120

1499kb – 244kb – 244kb – 12.7kb –
1858x1858 1200x1200 1200x1200 160x120

1499kb – 103kb – 103kb – 144kb –
961x953 484x480 484x480 484x480

1999kb – 272kb – 272kb – 77.6kb –
1500x1500 1200x1200 1200x1200 480x480

2550kb – 165kb – 274kb – 0.96kb –
1575x2362 800x1200 1067x1600 160x120
Fig. 11. Variation of JPG files for SMSM, SMDM and DMDM
Fig. 12 shows the range of graphic files tested with the upper limit at 290kb for the three device sets. The percentage of sent files size to that of the original files size was calculated to obtain the percentage of alteration in sent files. Results obtained independent of carrier used. Various facts and findings were brought to light following the test series. Past research [1] showed that alteration do occur on graphic file transmission via MMS. According to research carried out [2] which revealed that the transfer of a graphic file via MMS showed different hash values, even between the same make and model of phone; findings in this study confirm this fact not only on SMSM but also on SMDM and DMDM. However, 100% acquisition rate of MMS graphic file transmission was noted for a specific range of files size. Results showed that graphic files lesser or equal to 290kb were sent as they were originally on all three sending devices. Despite this fact, receiving devices used on carrier A and B were retrieving different files. Upon receiving devices, alteration was detected on all jpg files (original jpg files and files converted to jpg) on carrier A while carrier B showed no alteration on all received files compared to the sent files. On the sending device, for graphic files greater than 500kb, alteration occurs somewhere between 290kb – 300kb (exclusive).
-
V. Discussion
The three elements which altered were: the graphic file size, dimension and format. On the sending devices, all processed files led to a considerable decrease in the file size and dimension. At this level, all processed files were converted to jpg format. On the receiving devices, for large graphic files mainly, file size altered either by a considerable decrease or a slight increase while the file dimension incurred a reduction only on device of DMDM over carrier A.
It was observed that the decrease in file size occurring via carrier A were due to changes in pixel level, i.e. the intensity of RGB was different on sent and received files. The HSV level was also altered on the two graphic files. Files which were of png format by origin and which were converted to jpg format after conversion showed a slight increase on the receiving device and that increase was consistent on the three receiving models. All jpg file (by origin png) had an increase in saturation level. One hypothesis could be that the increase in saturation is bringing this slight increase in file size for all jpg file which were of png format by origin. Due to increase in intensity, with an increase in saturation, it may bring slight increase in file size. As all receiving devices on carrier A showed the same increase in size, we presume that the carrier is working out the files in such a way that a fix and consistent change is occurring on each transfer. In this case, the conversion method is particular to the carrier.
Graphic files of jpg format by origin were sub-sampled during the transmission from 4:4:4 (1 1) where resolution is full to 4:2:0 (2 2) where horizontal and vertical resolution is reduced by half; affecting again the quality of the file. The Exif information of bmp and png files by origin both showed same extracted sub-sample data. However, bmp files decreased while png files increased on receiving devices.
Sub-sampling 4:2:0 includes different sampling scheme which is regarded as a complex format [3]. This system of sub-sampling may be distinct to the carrier. This brings to another assumption about the contrasting behavior of both jpg files (bmp/png by origin) could be that the scheme used may be different at carrier A level.
The Exif information extracted showed that the files were indeed manipulated over carrier A but not over carrier B. JFIF of sent files was of version 1.01 while upon received the version changed to 1.02. This fact again demonstrates that the file is certainly influenced by the network before it is sent on the receiving device over carrier A.
All the alteration which occurred on network A did not happened over network B. This fact demonstrated that network A did manipulate the MMS content rather than the receiving devices.
-
A. When does the alteration occur – factors affecting the file?
On the sending device: The decrease in file size is happening primarily before the graphic file is sent; on the sending device itself during the message conversion to MMS where the files are cropped or resized to suit MMS transfer supported by particular sending device. More than 98% of the size of the original graphic file decrease in this process as the dimension of the file has decreased significantly. Thus, while attaching a particular graphic file, major decline in size happen due to large compression and/or conversion process specific to the sending device. It has been noted that all test series show the same results using carrier A and B in this phase; the sending phase.
Over the network: The network phase however reveals dissimilar results which help towards a conclusion about network role in MMS graphic file transmission. Test series carried out with same graphic files on different carriers A and B confirm that the network does influence graphic file transmission via MMS. The file sent through carrier A caused a decrease in file size; namely on all jpg files either they were of jpg format by origin or after conversion to jpg on the sending device. Not only was the size of the jpg file altering for SMSM, SMDM and DMDM but also for DMDM, some large jpg files dimension were further reduced considerably upon receiving device over carrier A.
The one main question which was unanswered till then was: was it the network which brought this alteration on the receiving device or was it the receiving device which was altering the files during the retrieval phase? Hence, the same test series were conducted on another local carrier using SMSM, SMDM and DMDM to resolve this part of the puzzle. The test results on carrier B uncovered this part by showing 100% acquisition rate of the sent files on all receiving devices. That is, even if the original files were not same as the sent file; which changed during the attachment process on the sending device – same scenario as carrier A, the received files on all three models SMSM, SMDM and DMDM were all identical to the sent files. Hence, that it was not the receiving device, but rather the network which was responsible for any alteration happening during test series on carrier A.
-
B. Why did the alteration happen?
The alteration from original file to the sent file happening on the sending device confirms that the alteration is happening because the sending device supports different file size and dimension. Each device has its own way of processing images.
The Sending device: The sending device plays a major role in the alteration of the graphic file. In order to suit the individual sending device, an integrated process in the sending device manipulates the graphic file accordingly before the transfer.
This is why most large files could not be processed by the Sony Ericsson Txt Pro set whereas the two other sets handled the file successfully. Not only was the processing of the different sending devices different but files from 1kb to 290kb did not change in terms of size and dimension during the attachment of the file on the sending device. This was mainly because of the capacity of the sending device which determined whether the conversion process would take place or not. Additional tests were conducted and it could be deduced that each sending device had its own way of proceeding with an MMS; however, the MMS file size capacity of the device was the key. The sending devices checked whether the files were within its support capacity regardless of its dimension.
-
1. If the graphic file was within its support capacity in terms of file size:
-
a) if the file dimension was large (dimension predetermined in the device), the conversion process started by cropping and/or resizing. The file was reduced in dimension leading to a decrease in file size and a change in file format from current format to jpg format
-
b) else if the file dimension were too large, the device could not proceed with any conversion, a message was displayed to inform the user that the processing of the image had failed
-
c) else if the file dimension was within limits, the file was attached as it was; no change in file size nor dimension or any other elements
-
2. If the graphic file was beyond its support capacity in terms of file size, the device either:
-
a) triggered the processing of the image automatically.
The file was thus resized leading to a reduction in file dimension and size and a change in file format b) prompted the user for the next action, either to proceed with downscaling and/or cropping and so on. The file size, dimension and format were again compromised
Any of the two actions mentioned above could either fail or succeed depending on various factors which were specific to the sending device. Test series showed that Sony Ericsson Txt Pro cropped large files while the two other models resized large files. At the sending device level, the network had no link to the file manipulation as carrier sent graphic files on all sending devices were similar over carrier A and B. Some additional tests carried out showed that depending on the capacity that a sending device could support, the graphic file would be manipulated to better fit the MMS transmission over the particular device.
The three sets used for this research work showed rather same support capacity of graphic file. The test series showed that files less or equal to 290kb with not too large dimensions (~1300x1300) were not changing as the devices seemed to support the size and dimension. However, the same size tested with larger dimension showed that the processing of the file failed. This proved that sending devices did control the initiation of graphic file transmission. However, it might be that other sets support smaller or bigger files which would avoid a decrease in file size, dimension or format. In order to double check this particular finding, a second test was carried out on received files from SMDM (Nokia Asha 311) and DMDM (Sony Ericsson Txt Pro) where the received files of the two receiving devices were resent through Nokia C2-01.
The second test series of resent files confirmed the fact that:
-
i) graphic files which were already adapted to MMS and to the sending device did not alter again on the sending device,
-
ii) ii) carrier A did change all jpg resent file again and each time the MMS content would go through its MMSC. However, carrier B once more showed no alteration on receiving devices. This fact concluded that carrier A was designed to manipulate all jpg files of any size and dimension.
The network’s MSSC level: MMS past research [5] addressed the interoperability challenges involved for mobile terminal capabilities. According to the paper[5], multimedia content might not be entirely compatible with the capabilities of the receiving device. The recipient MMSC could identify content formats incompatibilities and handle them properly [6]. Therefore, the addressee MMSC was in charge for providing services such as image resizing, and media simplification depending on the configuration and the capability of the recipient. However, content adaptation depended on service providers. If the network was content adaptation enabled, its MMSC controlled MMS contents. The findings about network manipulation over the graphic file were thus justified. According to [7], before multimedia messages were dispatched, various processing could be applied depending on the MMSC in order to better adapt the particular content to set standards and other protocols. Before delivering content, some MMSCs might incorporate a conversion service that attempted to adjust the multimedia content into a format suitable not only to its environment but to the receiving device as well. It was this process which was mentioned above as the “content adaptation" process. A notable adjustment ‘Image Simplification’ was highlighted [7]. Image simplification discarded plain regions of an image having a lot of color variation and edges. Content adaptation according to legacy device could explain the different results which cropped up in the test series. For the same graphic files (all jpg files) received on SMSM and SMDM, no alteration occurred on file dimension over carrier A. However, on receiving device of DMDM, the same file incurred a reduction file dimension. The alteration in graphic file at MMSC level would depend on the degree to which a particular carrier had been designed for adjustment of “content adaptation”. Therefore, following the test results obtained over carrier A and B for SMSM, SMDM and DMDM; it was understandable that carrier A had been designed with “content adaptation” and/or other conversion method as far as MMS contents were concerned. Carrier A did control all jpg files by origin or after conversion irrespective of the size and dimension or other feathers. Carrier B had not yet shown any kind of MMS content manipulation at its MMSC-end; thus it was deduced that it did not support content adaptation or any other kind of conversion so far.
Hence, results showed that there was no alteration in Bluetooth transmission. However, transmissions by MMS did cause some alteration. The alteration was mainly due to different processing of the graphic files by different mobile sets. For SMSM and SMDM, the test results obtained were identical in terms of size, dimension and file format. Hence the altered and non-altered graphic files results were consistent for those two series. For DMDM, some results were identical to the other two series. However, at a certain point, the test results differed from those of SMSM and SMDM. Hence, mobiles of different make and different models process graphic files differently and results concluded that during transmission by MMS, the graphic files were cropped, resized or downscaled.
-
VI. Conclusion
In view of finding grounds behind hash value variation for graphic files between mobile devices, a comparative study involving a set of test series was proposed and carried out. Bluetooth graphic file transmission showed no alteration on SMSM, SMDM and DMDM. MMS graphics file transfer operated in a different way compared to Bluetooth. Hash value variations were detected on both sent and received graphic files via MMS on the three different devices. However, according to test results, the receiving devices were not responsible for the alteration; but rather on variables such as the sending device and the MMS network used.
Alteration in graphic files via MMS included size, dimension and format, both before sending and during transmission over a particular network. Apart from alteration in hash values due to changes in file size, dimension and format, altered files showed differences in
RGB and HSV level and Exif information retrieved. It was observed that alteration depended on the sending devices; the capacity it supported for MMS transmission and this feature was particular to each mobile make and model. Limited processing capabilities of mobile devices could compromise the MMS content. As each device processed in its own way, variations on same files over different sending devices differ. At the carrier level, content adaptation might have been employed on messages content in order to convert them into messages more adapted and exchangeable in terms of size, dimension and format. At this level, the receiving device as well as some MMSC’s would manipulate the message content after validating the legacy receipt so as to better adapt the receiving file to the recipient device. MMSC which were not designed for content adaptation or any other conversion did not manipulate the message content, hence leaving the content intact.
Therefore, Bluetooth seemed to be much more reliable and stable as graphic file transmission method. However, its limitation to 10 meters made MMS an interesting and useful way of transferring data. With MMS graphic file transmission, even if at the network level there was no content manipulation, the sending device’s MMS capacity was a key player in graphic file variation. Graphic file transmission via MMS might not alter until and unless the files sent from the sending devices were within its capacity. Any file beyond its support capacity would be processed and changed before being sent. The graphic file size, dimension and format were not the only important elements, but the carrier network over which the MMS passed through was also an essential aspect that should be considered. As a result, if the MMS was sent within the sending device’s capacity, the user might be already reducing the risk of altering its MMS content.
Future Work
Based on the results of this research, it is recommended to carry further test on the given test series using other mobile devices make and model with newer technology, like Android if suitable over other carrier network. In this study, the focal parameters were graphic file size and format. The file size threshold was achieved from the series of tests carried on different sending devices. The same test can be performed focusing on graphic file dimension in order to find out the limit of graphic file in terms of dimension.
Список литературы Integrity Analysis of Multimedia File Transmission between Mobile Phones
- Danker, S., Ayers, R. & Mislan, R.P., 2009. Hashing Techniques for Mobile Device Forensics, Small scale digital device forensics journal [online], 3 (1).
- Dankner, S., 2009, Viability of Using Hash Values in Mobile Forensics, Exeter: Author.
- Borgström, K., 2008. Multimedia Messaging Service Components for Web 2.0. Master of Science Thesis. K T H Information and Communication Technology.
- Katz D., Gentile R., 2005. Embedded Media Processing [online]. U.S, Newnes.
- Coulombe, S ,Grassel G., 2004. Multimedia Adaptation for the Multimedia Messaging Service. IEEE Communications Magazine, 42 (7), 120–126.
- Ghaderi, M., Srinivasan, K., 2005. Multimedia Messaging Service: System Description and Performance Analysis. IEEE Communications Magazine, 198 – 205.
- Wei-Qi, Y., 2007. Multimedia simplification for optimized MMS synthesis. ACM Digital Library, 3 (1), 1-23.
- Comverse, 2009. MMS Is Growing in More Ways than One: The Dimensions and Implications of Surging MMS Growth.U.S: COMVERSE.
- Kornblum, J., 2006. Identifying almost identical files using context triggered piecewise hashing. Digital Investigating 3S.
- Le Bodic, G., 2003. Multimedia Messaging Service: An Engineering Approach to MMS [online]. England, Wiley.
- Saylor, M., 2012. The Mobile Wave: How Mobile Intelligence Will Change everything [online]. U.S, Vanguard Press.
- Sobieraj, S.C., 2008. Mobile Device Forensics Case File Integrity Verification. Thesis (Master). Purdue University.
- Soinio, A., 2004. Viewing Multimedia Messages with 3GPP SMIL in a Size Driven Mobile Terminal. Master of Science Thesis. Abo Akademi University.
- Sridevi M.E, Vijayakuymar V.R,Anuja R 2012. A survey on various compression methods for medical images, I.J Intelligent Systems and Applications,2012,3,13-19.DOI: 10.5815/ijisa.2012.03.02
- Kaur P, Chhabra N., 2012. Image Segmentation Techniques for noisy digital images based upon Fuzzy logic-A review and Comparison, I,J Intelligent Systems and Applications,2012,7,30-36. DOI 10.5815/ijisa.202.07.04


