Internet of Things: A Review on Technologies, Architecture, Challenges, Applications, Future Trends
Автор: Jaideep Kaur, Kamaljit Kaur
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 4 vol.9, 2017 года.
Бесплатный доступ
World Wide Web (1990's) and Mobile Internet (the 2000's) had consequential corroborated the way how people communicate. However, with evolution in technology, the cataclysm of Internet has stepped into a new phase-Internet of Things. Internet of Things, a prominent paradigm in the field of IT having a nominal intervention of humans allowing diverse things to communicate with each other, anticipate, sight, and perceive surroundings. IoT exploits RFID tags, NFC, sensors, smart bands, and wired or wireless communication technologies to build smart surroundings, smart Homes, quick-witted intelligence in medical care, ease of Transport, and more. This paper introduces IoT with emphasis on its driver technologies and system architecture. In addition to application layer protocols, we focus on identifying various issues and application areas of IoT as well as future research trends in the field of IoT. We have also highlighted how big data is associated with Internet of Things.
Applications, Architecture, Big Data, Economics, Internet of Things (IoT), Protocols
Короткий адрес: https://sciup.org/15011839
IDR: 15011839
Текст научной статьи Internet of Things: A Review on Technologies, Architecture, Challenges, Applications, Future Trends
Published Online April 2017 in MECS
-
I. Introduction
World Wide Web (1990’s) and Mobile Internet (the 2000’s) had consequential corroborated the way how people communicate. However, with an evolution in technology, the cataclysm of Internet has stepped into a new phase ‘Internet of Things-The next generation technology’.
Internet of things (IoT) provides a communication platform supporting person to person (P2P), Machine to Machine (M2M) and Person to Machine (P2M) interactions. Thus, IoT reckons to ‘Accumulate and Ubiquitous’. Fig. 1 shows Accumulate and Ubiquitous IOT.
Internet of Things- A prominent paradigm in the field of IT has a nominal intervention of humans, it is a network where miscellaneous things like animals, plants, vehicles, appliances, buildings dialogue information via the internet. IoT makes our surroundings smart by exploiting RFID tags, sensors, mobile phones, spime, Internet protocols, and wired or wireless communication technologies. The authors in [8] deployed Bluetooth Low Energy (BLE) technology for energy efficient smart homes. Tabish et al. [54] used 6LoWPAN to remotely monitor patient’s health.
IoT has been included in first six ‘Disruptive Civil technologies’ list by US National Intelligence Council(NIC) [85]. NIC also envisions IoT to be present in everything be it furniture, paper, food packages or anything by 2025. By 2020, CISCO gauge to approximately 50 billion IoT objects. In 1999, Kevin Ashton first coined the term ‘Internet of Things’.
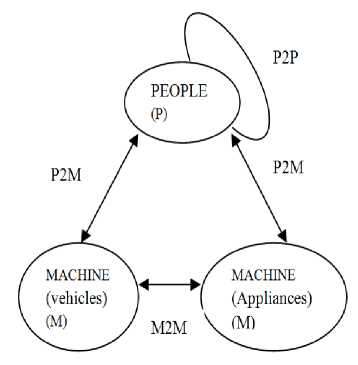
Fig.1.Accumulate and Ubiquitous IOT
Gubbi et al. define IoT as:
“ Interconnection of sensing and actuating devices providing the ability to share information across platforms through a unified framework, developing a common operating picture for enabling innovative applications. This is achieved by seamless ubiquitous sensing, data analytics and information representation with Cloud computing as the unifying framework [3]. ”
IoT sensors enable things (real/physical) to anticipate, sight, perceive and conduct jobs as living things do. For example, a wristband with embedded sensors monitor your sleeping and waking time and set an alarm accordingly, this wristband can then convey a message to the bath tub to start warming water and can even communicate to the coffee maker to prepare coffee. Thus, IoT cannot only sense things but it can also control and actuate things.
Things can be uniquely identified by assigning Identification through IPv6 addressing. Current IPv4 have the capability to address only 4.3 billion devices whereas IPv6 has an address space ranging from 2 to 128th power devices that count to trillions of devices. With Unique identification, things can be easily located, recognized and controlled via the internet. IoT is considered essential in performing everyday activities. It can connect, Monitor heterogeneous things around us, locate things present around the globe, automatically manage and control things .
Deploying IoT in our daily activities can the increase quality of life and can even help in the growth of the economy. By 2025, approximately 2-3 billion people will access the internet also economic growth caused by IoT is estimated to be in the range of $2.7 trillion to $6.2 trillion [55]. Table 1 shows various application areas and the percentage they have an impact on economic growth. From this Medical Care is found to benefit economic growth at the most followed by Manufacturing then Electricity.
Table 1. Percent of Economic Growth Caused By Deploying Iot in Various Application Arenas
|
APPLICATION ARENAS |
PERCENTAGE |
|
Medical Care |
41% |
|
Manufacturing |
33% |
|
Electricity |
7% |
|
Metropolitan Infrastructure |
4% |
|
Safety |
4% |
|
Resource Extortion |
4% |
|
Agriculture |
4% |
|
Vehicles |
2% |
|
Retail |
1% |
With IoT, many multinational software companies have switched to the physical world. For instance, Google collaborated with a thermostat company to create its mark in providing smart world/homes. IBM also leveraged IoT for traffic management and provides solutions for smart Grids. Various other companies such as Facebook, Apple envision IoT as its future technology.
IoT has a high significance in our day to day life. It has its vision in business, working and domestic domains such as assisted living, e-healthcare, industrial manufacturing, automation, management, smart transportation and abundant. In [8] [28] IoT is deployed for energy efficient smart Homes and Appliances, [33] deploys Arduino to monitor Air quality. Industry manufacturing processes are made efficient and more economic decisions are made with IoT [36] [27]. In [39] an author proposed an approach to control traffic congestions as well as provides smart car parking. IoT has its application in making green, safe and secure cities [31] [34].
Section II describes various components required for the functioning of IoT devices and various IoT technologies. These technologies include RFID which is the first hardware embedded in IoT devices, its main functionality is automatic identification, authentication, and tracking; Near Fields communication (NFC) - A wireless communication technology is capable of sharing data within the range of 10 cm; ZigBee is another communication technology based on IEEE 802.15.4; 6LowPAN – An IoT communication technology that adequate IPv6 packets to IEEE 802.15.4 specification and provides multi-hop delivery. This section further reviews the applications where these technologies have been utilized. Section III highlights IoT’s system Architecture. Section IV describes various application layer protocols and their comparison. Section V reviews proposals devised for various IoT complications such as energy efficiency, cost efficiency, availability, security, scalability, reliability. Section VI addresses application areas leveraged by IoT. Section VII highlights future research trends. Section VIII associates Big Data with IoT and Section IX concludes the paper.
-
II. Component Prerequisite for Internet of Things
This section describes various components required for the functioning of IoT devices and various IoT technologies. These technologies include RFID which is the first hardware embedded in IoT devices, its main functionality is automatic identification, authentication, and tracking; Near Fields communication (NFC) - A wireless communication technology is capable of sharing data within the range of 10 cm; ZigBee is another communication technology based on IEEE 802.15.4; 6LowPAN – An IoT communication technology that adequate IPv6 packets to IEEE 802.15.4 specification and provides multi-hop delivery. IoT exploits RFID tags, NFC, sensors, smart bands, and wired or wireless communication technologies to build smart surroundings, smart Homes, quick-witted intelligence in medical care, ease of Transport, and more.
There are three components that are required for proper functioning of IoT. These are:
-
1) Hardware and technologies – It incorporates sensors, actuators and other embedded devices and technologies.
-
2) Middleware – It comprises of repository and data analytic tools.
-
3) Display – It comprises of some presentation tools required for user interaction.
Fig. 2 shows various components that sum to IoT.
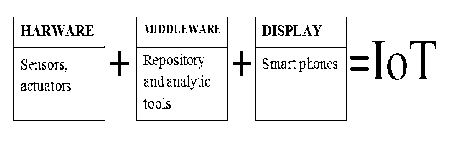
Fig.2. Various Components of IoT
This section expounds IoT components as follows:
-
A. Hardware
Hardware associated with IoT collects required data from the surroundings. IPv6, RFIDs, NFC, BLE, ZigBee, 6LowPan, WiFi, LTE (Long Term Evolution) are some enabling technologies that gather IoT data.
Radio Frequency Identification (RFID)
RFID is first technology that exists from the time when the concept of IoT was found in late 90’s. RFID is a hardware embedded in the device; its main functionality is automatic identification, authentication, and tracking. RFID consists of passive RFID tags and active RFID readers. Passive RFID tags do not operate on batteries and it conveys ID to the active RFID readers. Active RFIDs are associated with the battery and it initiates communication. Healthcare, supply chain management, automatic recycling are some applications of RFIDs.
Near Field Communication (NFC)
Near Fields communication (NFC) is a wireless communication technology that has the capability of sharing data among electronic devices within the range of 10 cm. NFC works at a high frequency of 13.56 MHz and up to 424 Kbps of the data rate. Smart transportation, IPv6 packet transmission are some application areas where NFC technology is leveraged.
ZigBee
ZigBee is another communication technology based on IEEE 802.15.4. It was standardized in 2003 later was revised in 2006. ZigBee provides high-level communication among IoT devices with coverage of 10100m. It also has its proficiency in monitoring, authentication but does not guarantee QoS. It is a costeffective technology and consumes less energy, so it can be deployed in electric meters, wireless light switches, industrial tools that require short-range data transfer. Applications include Smart Homes, Super Market and more.
Bluetooth low energy (BLE)
Bluetooth low energy (BLE) as the name suggests is a wireless technology that is proficient in reducing power consumptions, thus increasing the lifespan of devices. BLE uses shorter wavelength, operates in the range of 100m but have 15 times lower latency than traditional Bluetooth. It follows a master-slave approach. Almost all Smartphones are leveraging this technology to a greater extent. BLE is coherent in consuming energy as compared to ZigBee. Applications include Data transmission, Home appliances, Vehicle to Vehicle communication and more.
6LowPan
IPv6 over low-power wireless personal area network (WPANs) abbreviated as 6LowPAN is an IoT communication technology that adequate IPv6 packets to IEEE 802.15.4 specification. In 2007, IETF 6LowPAN working group follow this standard.
6LowPAN foreshortens transmission overhead by performing comparisons. It also supports multi-hop delivery [86] and is capable of providing security and protection in IoT environment. It operates in the range of 10-30 m. The datagram of 6LowPAN incorporates 4 types of 2 bit headers. 00 represents ‘No Header’ and jettison all those packets that discard to 6LowPAN. 01 typify to ‘Transmit Header’. This Header accomplishes multi-casting and constricts IPv6 header. 10 represent ‘Reticulation addressing’. It is capable of identifying IEEE 802.15.4 packets. 11 represent fragmentation. Applications include Intrusion detection system, Healthcare.
Table 2 illustrates Attributes of Technologies used in Internet of Things.
Table 2. Attributes of Technologies used in Internet of Things
|
Technology |
Proficiency |
Data Rate |
Range |
Applications |
|
RFID |
Authentication , Monitoring, Identification, Information Management |
Up to 640 kbps |
1-10m |
HealthCare[17], Supply chain Management [56], Automotive Recycling Industry[57], Object Tracking[58], warehouse management[59] |
|
NFC |
communicatio n, Security |
106 - 424 kbps |
≤ 10 cm |
Smart Transportation [60], Electronic Lock[61],IPv6 packet transmission[62] |
|
6LowPan |
Protection and Security |
20 250 kbps |
10-30 m |
Intrusion Detection System [63], HealthCare[64] |
|
BLE |
communicatio n, Reduce power consumption |
1 mbp s |
100 m |
Data transmission [65], Home appliances [66], Smart Home[8] |
|
ZigBee |
communicatio n, monitoring |
20 250 kbps |
10 100 m |
Smart Home[67], Super Market[68] |
-
B. Middleware
In order to aid repository and data analytics, a centralized system is a must. IoT paradigm results into the creation of abundant data. This data must be stored efficiently and intelligently in order to perform actuation and smart observations. A centralized system provides reliability. The data so generated by IoT can be stored in a cloud-based repository.
-
C. Display
Display components of IoT consist of those tools that provide user interaction with the scenario. Since most users of IoT are non-technical, it becomes a necessity to develop devices that are easy to operate and from which user can have maximum benefit from. Devices such as smart phones, smart tablets, 3D screen etc. fall under this category.
-
III. IoT System Architecture
IoT system architecture has the ability to perform interoperability among heterogeneous assets around us. Considering the aforementioned fact, the architecture of IoT should be flexible layered [1]. As there is no commonly accepted IoT architecture, authors proposed various architectures, few among them are SoA based architecture proposed by Atzori et al. [2] and five-layered architecture [86].
Applications
Service
Composition
Service
Management
Object Abstraction
Objects
(a)
BUSINESS LAYER
APPLICATION LAYER
CoAP, MQTT: XMPP, DDS, AMQP
SERVICE MANAGEMENT LAYER
OBJECT ABSTRACTION LAYER
OBJECTS PERCEPTION LAYER
(b)
Fig.3. (a) SoA (Service Oriented Architecture) [2] (b) Five Layered Architecture.
A brief introduction to the five layers of IoT system architecture is as follows:
-
A. Objects or assets layer (Perception layer)
The lowest layer of IoT architecture is responsible for gathering data from the surroundings wielding sensors and actuators. It is proficient in identifying location, monitoring room temperature and humidity, recording vehicle acceleration and more. It digitizes the sensed data and communicates to the object abstraction layer.
-
B. Objects Abstraction layer
Through various communication technologies counterpart RFID, ZigBee, 6LowPAN, WiFi, 3G/4G, BLE etc. this layer act as a bridge to transfer incoming digitized data from objects layer to the service management layer. This layer is also responsible for cloud computing functionalities [87].
-
C. Service Management layer
It is a middleware layer that after identifying the names and address provides service to its requestors. It is the layer with the help of which IoT is capable of connecting with heterogeneous things.
-
D. Application layer
The Application layer is associated with delivering services to the customers. For instance, it can give the acceleration of the vehicle as well as an exact location of the vehicle. Various application domains include Smart Home, Smart Grid, Intelligent Transport, Smart Factory, Quick-witted HealthCare intelligence and more. Application layer incorporates CoAP (Constrained Application Protocol), AMQP (Advanced Message Queuing Protocol), DDS (Data Distribution Service), MQTT (Message Queue Telemetry Transport), XMPP (Extensible Messaging and Presence Protocol) protocols. These protocols are discussed in next section.
-
E. Business layer
The Business layer also named as management layer manages all layers, activities, and service of IoT. It incorporates certain graphs, flowcharts, and models based on the data acquired from the application layer. This layer is capable of making effective decisions for big data analysis.
-
IV. Protocols associated with Application Layer of IoT
The Application layer of IoT system architecture furnishes user services by following certain rules and procedures called Application layer protocols. These protocols include:
CoAP (Constrained Application Protocol).
MQTT (Message Queue Telemetry Transport).
XMPP (Extensible Messaging and Presence Protocol).
AMQP (Advanced Message Queuing Protocol).
DDS (Data Distribution Service).
Among these CoAP and MQTT are most disseminate protocols. A detailed description of these protocols is discussed as follows:
-
A. Constrained Application Protocols (CoAP)
CoAP is a retransmission protocol that features request and response messaging. It was standardized by Internet Engineering Task Force (IETF) constrained Restful environment. CoAP was basically designed for resource constrained devices like WSN (Wireless Sensor Networks). The main functionality of CoAP is monitoring, controlling remote devices as well as guarantying message delivery. CoAP leverages HTTP commands GET, POST, PUT and DELETE for interactions between client and server. It relies on UPD (User Datagram Protocol).
CoAP is divided into two sub-layers namely message sub-layer and request/response sub-layer. The former ensures reliable communication based on exponential back off and later deals with REST communications.
CoAP is proficient in providing Datagram transport layer security (DTLS) that provides privileged message communication, minimizing communication overhead and monitoring resources by utilizing publish/subscribe mechanism. Confirmable, Non-Confirmable, Acknowledgment (Piggybacked) and Separate Response are four types of CoAP messages. CoAP has a 32 bit message format. Fig. 4 shows CoAP message format. It incorporates CoAP version (V), Transaction Type (T), OC (Option Count), Code and Message ID (M ID) in header field followed by Token, Options and Payload fields.
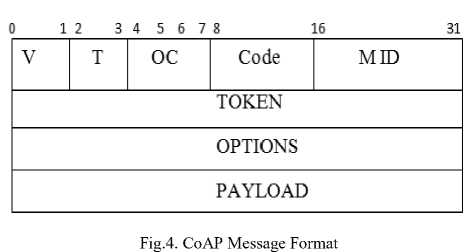
Various Application domains where CoAP is utilized are personal HealthCare Systems [9], Resource Sharing [10], Congestion Control [13], and Security [37].
-
B. Message Queue Telemetry Transport(MQTT)
MQTT is a lightweight messaging protocol that supports machine to machine communication. It relies on TCP. In comparison to CoAP, MQTT has higher throughput but lower Latency [88]. It was developed by IBM in collaboration with Arcom in 1999 and later was standardized as OASIS in March 2013.
MQTT utilizes Publish/Subscribe messaging mechanism and provides SSL (Service Socket Layer) encrypted link between client and Broker.
It has 3 QoS levels:
-
1) Fire and Forget – Fire the message and Forget i.e. no acknowledgment is received.
-
2) Delivered at least once – Message is delivered at least once and for each delivery acknowledgment is received.
-
3) Delivered exactly once – In order to guarantee message delivery, 4-way handshake procedure opts.
The Client-Server of MQTT comprises of 3 elements:
-
1) Subscriber.
-
2) Publisher.
-
3) Broker.
Every server in this architecture is referred to as broker. Client subscribes to a topic generated by the publisher. The Publisher on the other hand forwards the generated topic to the broker. For Instance, Consider three clients A, B, and C. Here Client A is a Publisher that publishes a topic ‘air humidity’ and Client B and C subscribes to this topic. Now, whenever Client A publishes the value of air humidity says 49 then the intermediate broker gives access of this value to all the subscribed Clients.
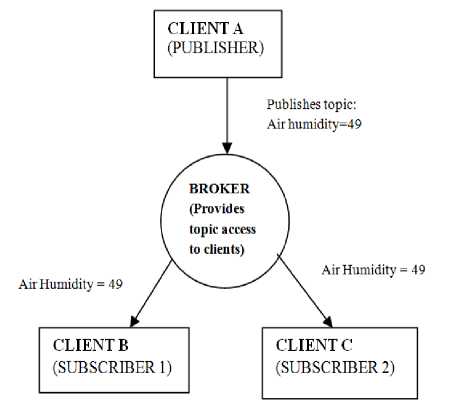
Fig.5. Publisher/ Subscriber MQTT Architecture
The message format of MQTT consists of four bytes header, 1-4 bytes length, variable length header and variable length message payload. Fig. 6 shows MQTT message format.
0 1 2 3 4 5 6 7
|
Message Type |
UDP |
QoS |
Retain |
|
Remaining Length |
|||
|
Variable Length Header |
|||
|
Variable Length Message Payload |
|||
Fig.6. MQTT Message Format
Applications include medical information sharing [21], power meters, observations and more.
-
C. Extensible Messaging and Presence Protocol (XMPP)
XMPP is an XML, TCP based Messaging protocol that was invented by Jaber open Source community to ensure SSL confidential message communication. It became an IETF instant messaging standard in 2002.
XMPP has its applications in social networking such as multi-user chat, video/voice calling and more. It is a platform independent protocol, have no QoS support and supports Publish/Subscribe and Request/ Response.
Two or more users exchange data in the form of XML Stanza. XML stanza is cleaved into 3 components.
-
1) Message – it identifies source and destination address, type and IDs.
-
2) Presence – it notifies updates to the customers.
-
3) Info/query – It pairs sender and receiver.
Shows XML Stanza of XMPP [1].
Список литературы Internet of Things: A Review on Technologies, Architecture, Challenges, Applications, Future Trends
- Al-Fuqaha, M. Guizani, M. Mohammadi, M. Aledhari, and M. Ayyash, "Internet of things: A survey on enabling technologies, protocols, and applications," IEEE Communications Surveys & Tutorials, vol. 17, no. 4, pp. 2347 – 2376, jun. 2015.
- L. Atzori, A. Iera, and G. Morabito. "The internet of things: A survey," Computer networks, vol. 54, no. 15, pp. 2787-2805, 2010.
- Gubbi, R. Buyya, S. Marusic, and M. Palaniswami, "Internet of Things (IoT): A vision, architectural elements, and future directions," Future Generation Computer Systems, vol.29, no. 7, pp. 1645-1660, 2013.
- Borgia, "The Internet of Things vision: Key features, applications and open issues," Computer Communications, vol. 54, pp.1-31, 2014.
- IERC Cluster SRIA, (2014). Internet of Things [Online]. Available: www.internet-of-things-research.eu/about_iot.htm
- T. Qiu, D. Luo, F. Xia, N. Deonauth, W. Si, and A. Tolba, "A Greedy Model with Small World for Improving the Robustness of Heterogeneous Internet of Things," Computer Networks, 2016.
- Jiang, F. Shen, S. Chen, K. Li, and Y. Jeong, "A secure and scalable storage system for aggregate data in IoT," Future Generation Computer Systems, vol. 49, pp. 133-141, 2015.
- M. Collotta and G. Pau, "Bluetooth for Internet of Things: A fuzzy approach to improve power management in smart homes," Computers & Electrical Engineering, vol. 44, pp. 137-152, 2015.
- F. S. Santos, H. O. Almeida, and A. Perkusich, "A personal connected health system for the Internet of Things based on the Constrained Application Protocol," Computers & Electrical Engineering, vol. 44, pp. 122-136, 2015.
- Y. Xue, and R. Deters, "Resource Sharing in Mobile Cloud-computing with Coap," Procedia Computer Science, vol. 63, pp. 96-103, 2015.
- Y. Mao, J. Li, M. Chen, J. Liu, C. Xie, and Y. Zhan, "Fully secure fuzzy identity-based encryption for secure IoT communications," Computer Standards & Interfaces, vol. 44, pp. 117-121, 2015.
- M. Marjanović, L. Skorin-Kapov, K. Pripužić, A. Antonić, and I. P. Žarko, "Energy-aware and quality-driven sensor management for green mobile crowd sensing," Journal of Network and Computer Applications, vol. 59, pp. 95-108, Jul. 2015.
- Betzler, C. Gomez, I. Demirkol, and J. Paradells, "CoCoA+: An advanced congestion control mechanism for CoAP," Ad Hoc Networks, vol. 33, pp. 126-139, Apr. 2015.
- P. Morreale, J. McAllister, S. Mishra, and T. Dowluri, "Turning Leaf: Ecovisualization for Mobile User Engagement," Procedia Computer Science, vol. 52, pp. 690-694, 2015.
- á. Villalba, J. L. Pérez, D. Carrera, C. Pedrinaci, and L. Panziera, "servIoTicy and iServe: A Scalable Platform for Mining the IoT," Procedia Computer Science, vol. 52, pp. 1022-1027, 2015.
- Chai, J. Choi, and J. Jeong, "An Enhanced Secure Mobility Management Scheme for Building IoT Applications," Procedia Computer Science, vol. 56, pp. 586-591, 2015.
- He and S. Zeadally, "An Analysis of RFID Authentication Schemes for Internet of Things in Healthcare Environment Using Elliptic Curve Cryptography," IEEE Internet of Things Journal, vol. 2, no. 1, pp. 72-83, Feb 2015.
- N. Kumar, N. Chilamkurti, and S. Misra, "Bayesian coalition game for the internet of things: an ambient intelligence-based evaluation," IEEE Communications Magazine, vol. 53, no. 1, pp. 48-55, 2015.
- S. Premnath and Z. Haas, "Security and Privacy in the Internet-of-Things under Timeand-Budget-limited Adversary Model," IEEE Wireless Communications Letters, Vol. 4, No. 3, June 2015.
- Pan, R. Jain, S. Paul, T. Vu, A. Saifullah, and M. Sha, "A Internet of Things Framework for Smart Energy in Buildings: Designs, Prototype, and Experiments," IEEE Internet Of Things Journal, vol. 2, No. 6, December 2015.
- Y. F. Gomes, D. F. S. Santos, H. O. Almeida, and A. Perkusich, "Integrating MQTT and ISO/IEEE 11073 for health information sharing in the Internet of Things," in 2015 IEEE International Conference on Consumer Electronics (ICCE), 2015, pp. 200-201.
- S. Collier, "The Emerging Enernet: Convergence of the Smart Grid with the Internet of Things." in IEEE Rural Electric Power Conference (REPC), 2015, pp. 65-68.
- M. Suresh, P. S. Kumar, and T. V. P. Sundararajan, "IoT Based Airport Parking System," in IEEE Sponsored 2nd International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), 2015, pp. 1-5.
- T. N. Pham, M. Tsai, D. B. Nguyen, C. Dow, and D. Deng, "A Cloud-Based Smart-Parking System Based on Internet-of-Things Technologies," IEEE Access, vol. 3, pp. 1581-1591, 2015.
- Kalmar, R. Vida, and M. Maliosz, "CAEsAR: A Context-Aware Addressing and Routing scheme for RPL networks," in 2015 IEEE International Conference on Communications (ICC), 2015, pp. 635-641.
- Zhu, V. Leung, L. Shu, and E. C-H. Ngai, "Green Internet of Things for Smart World," IEEE Access, vol. 3, pp. 2151-2162, 2015.
- R. Zhu, X. Zhang, X. Liu, W. Shu, T. Mao, and B. Jalaian, "ERDT: Energy-Efficient Reliable Decision Transmission for Intelligent Cooperative Spectrum Sensing in Industrial IoT," IEEE Access, vol. 3, pp. 2366-2378, 2015.
- Y-P. Kim, S. Yoo, and C. Yoo, "DAoT: Dynamic and energy-aware authentication for smart home appliances in Internet of Things," in 2015 IEEE International Conference on Consumer Electronics (ICCE), 2015, pp. 196-197.
- Hussain, R. Wenbi, A. L. d. Silva, M. Nadher, and M. Mudhish, "Health and emergency-care platform for the elderly and disabled people in the Smart City," Journal of Systems and Software, vol. 110, pp. 253-263, Sep. 2015.
- D. Rosário, Z. Zhao, A. Santos, T. Braun, and E. Cerqueira, "A beaconless opportunistic routing based on a cross-layer approach for efficient video dissemination in mobile multimedia IoT applications," Computer Communications, vol. 45, pp. 21-31, Apr. 2014.
- M. Castro, A. J. Jara, and A. F. Skarmeta, "Enabling end-to-end CoAP-based communications for the Web of Things," Journal of Network and Computer Applications, vol. 59, pp. 230-236, Oct. 2014.
- Luvisi and G. Lorenzini, "RFID-plants in the smart city: Applications and outlook for urban green management," Urban Forestry & Urban Greening, vol. 13, no. 4, pp. 630-637, 2014.
- Bekara, "Security Issues and Challenges for the IoT-based Smart Grid," Procedia Computer Science, vol. 34, pp. 532-537, 2014.
- S. Abraham, and X. Li, "A cost-effective wireless sensor network system for indoor air quality monitoring applications," Procedia Computer Science, vol. 34, pp. 165-171, 2014.
- S. Elmaghraby, and M. M. Losavio, "Cyber security challenges in Smart Cities: Safety, security and privacy," Journal of advanced research, vol. 5, no. 4, pp. 491-497, 2014.
- M. Nitti, R. Girau, and L. Atzori, "Trustworthiness management in the social internet of things," IEEE Transactions on Knowledge and Data Engineering, vol. 26, no. 5, pp. 1253-1266, May 2014.
- S. Raza, H. Shafagh, K. Hewage, R. Hummen, and T. Voigt, "Lithe: Lightweight secure CoAP for the internet of things," IEEE Sensors Journal, vol. 13, no. 10, pp. 3711-3720, 2013.
- Huang, Y. Meng, X. Gong, Y. Liu, and Q. Duan, "A novel deployment scheme for green internet of things," IEEE Internet of Things Journal, vol. 1, no. 2, pp. 196-205, 2014.
- Fuhong, L. Qian, Z. Xianwei, C. Yueyun, and H. Daochao, "Cooperative differential game for model energy-bandwidth efficiency tradeoff in the Internet of Things," China Communications, vol. 11, no. 1, pp. 92-102, Jan 2014.
- Y. Zheng, S. Rajasegarar, C. Leckie, and M. Palaniswami, "Smart car parking: Temporal clustering and anomaly detection in urban car parking," in 2014 IEEE Ninth International Conference on Intelligent Sensors, Sensor Networks and Information Processing (ISSNIP), 2014, pp. 1-6.
- P-Y. Chen, S-M. Cheng and K-C. Chen, "Information fusion to defend intentional attack in Internet of things," IEEE Internet of Things Journal, 1, no. 4, pp. 337-348, 2014.
- B. Kantarci and H. T. Mouftah, "Trustworthy Sensing for Public Safety in Cloud-Centric Internet of Things," IEEE Internet of Things Journal, vol. 1, no. 4, pp. 360-368, 2014.
- Kiljander, A. D'Elia, F. Morandi, P. Hyttinen, J. Takalo-Mattila, A. Ylisaukko-Oja, J-P. Soininen, and T. S. Cinotti, "Semantic interoperability architecture for pervasive computing and Internet of Things," IEEE Access, vol. 2, pp. 856-873, 2014.
- C. H. Liu, J. Fan, J. W. Branch, and K. K. Leung, "Toward QoI and Energy-Efficiency in Internet-of-Things Sensory Environments," IEEE Transactions on Emerging Topics in Computing, vol. 2, no. 4, pp. 473-487, 2014.
- P. P. Pereira, J. Eliasson, and J. Delsing, "An authentication and access control framework for CoAP-based Internet of Things," in 2014-40th Annual Conference of the IEEE Industrial Electronics Society, IECON, 2014, pp. 5293-5299.
- P. Castellani, M. Rossi, and M. Zorzi, "Back pressure congestion control for CoAP/6LoWPAN networks," Ad Hoc Networks, vol. 18, pp.71-84, 2014.
- R. Palattella, N. Accettura, L. A. Grieco, G. Boggia, M. Dohler, and T. Engel, "On optimal scheduling in duty-cycled industrial IoT applications using IEEE802.15.4 e TSCH," IEEE Sensors Journal, vol.13, no. 10, pp.3655-3666, 2013.
- Sun, X. Zhang, and Z. Li, "The internet of things (IOT) and cloud computing (CC) based tailings dam monitoring and pre-alarm system in mines," Safety science, vol. 50, no. 4, pp.811-815, 2012.
- S. F. Abedin, M. Alam, G. Rabiul, R. Haw, and C. S. Hong, "A system model for energy efficient green-IoT network," in 2015 IEEE International Conference on Information Networking (ICOIN), 2015, pp. 177-182.
- Atzori, A. Iera, G. Morabito, and M. Nitti, "The social internet of things (siot)–when social networks meet the internet of things: Concept, architecture and network characterization," Computer Networks, vol. 56, no. 16, pp. 3594-3608, 2012.
- C. Perera, A. Zaslavsky, P. Christen, and D. Georgakopoulos, "Ca4iot: Context awareness for internet of things," in 2012 IEEE International Conference on Green Computing and Communications (GreenCom), 2012, pp. 775-782.
- S. Fang, L. D. Xu, Y. Zhu, J. Ahati, H. Pei, J. Yan, and Z. Liu, "An integrated system for regional environmental monitoring and management based on internet of things," IEEE Transactions on Industrial Informatics, vol. 10, no. 2, pp.1596-1605, 2014.
- R. Vargheese and Y. Viniotis, "Influencing data availability in IoT enabled cloud based e-health in a 30 day readmission context." in 2014 IEEE International Conference on Collaborative Computing: Networking, Applications and Worksharing (CollaborateCom),2014, pp. 475-480.
- R. Tabish, A. M. Ghaleb, R. Hussein, F. Touati, A. B. Mnaouer, L. Khriji, and M. F. A. Rasid, "A 3G/WiFi-enabled 6LoWPAN-based U-healthcare system for ubiquitous real-time monitoring and data logging," in 2014 IEEE Middle East Conference on Biomedical Engineering (MECBME), 2014, pp. 277-280.
- J. Manyika, M. Chui, J. Bughin, R. Dobbs, P. Bisson and A. Marrs, Disruptive Technologies: Advances that Will Transform Life, Business, and the Global Economy. McKinsey Global Institute San Francisco, CA, 2013.
- B.Yan and G. Huang, "Application of RFID and Internet of Things in Monitoring and Anti-counterfeiting for Products," in IEEE International Seminar on Business and Information Management, ISBIM'08, 2008, vol. 1, pp. 392-395.
- T. Zhang, X. Wang, J. Chu, X. Liu, and P. Cui, "Automotive recycling information management based on the internet of things and RFID technology," in 2010 IEEE International Conference on Advanced Management Science (ICAMS),2010 , vol. 2, pp. 620-622.
- M-C. Chung, G. M. Lee, N. Crespi, and C-C. Tseng, "RFID object tracking with IP compatibility for the internet of things," In IEEE International Conference on Green Computing and Communications (GreenCom), 2012, pp. 132-139.
- Yanhui, "Internet of Things Application of RFID Technology in Warehouse Management," in Third International Conference on Instrumentation, Measurement, Computer, Communication and Control. 2013.
- T. Bojan, U. Kumar, and V. Bojan, "An internet of things based intelligent transportation system," in IEEE International Conference on Vehicular Electronics and Safety (ICVES),2014, pp. 174-179.
- P. Urien, "A secure cloud of electronic keys for NFC locks securely controlled by NFC smartphones," in IEEE 11th Consumer Communications and Networking Conference (CCNC), 2014, pp. 1120-1121.
- J. Park, S. Lee, S. H. Bouk, D. Kim, and Y. Hong, "6LoWPAN adaptation protocol for IPv6 packet transmission over NFC device," in 2015 Seventh International Conference on Ubiquitous and Future Networks (ICUFN),2015, pp. 541-543.
- C. Cervantes, D. Poplade, M. Nogueira, and A. Santos, "Detection of sinkhole attacks for supporting secure routing on 6LoWPAN for Internet of Things," in 2015 IFIP/IEEE International Symposium on Integrated Network Management (IM),2015 , pp. 606-611.
- T. N. Gia, N. K. Thanigaivelan, A-M. Rahmani, T. Westerlund, P. Liljeberg, and H. Tenhunen, "Customizing 6LoWPAN networks towards Internet-of-Things based ubiquitous healthcare systems," in IEEE NORCHIP, 2014, pp. 1-6.
- E. Boualouache, O. Nouali, S. Moussaoui, and A. Derder, "A BLE-based data collection system for IoT," in IEEE First International Conference on New Technologies of Information and Communication (NTIC),2015, pp. 1-5.
- Matsuoka, J. Wang, L. Jing, Y. Zhou, Y. Wu, and Z. Cheng, "Development of a control system for home appliances based on BLE technique," in 2014 IEEE International Symposium on Independent Computing (ISIC), 2014, pp. 1-5.
- W. Yiqi, H. Lili, H. Chengquan, G. Yan, and Z. Zhangwei, "A ZigBee-based smart home monitoring system." In 2014 IEEE Fifth International Conference on Intelligent Systems Design and Engineering Applications (ISDEA),2014, pp. 114-117.
- R. Chen, L. Peng, and Y. Qin, "Supermarket shopping guide system based on Internet of things." in IET International Conference on Wireless Sensor Network, 2010, pp. 17-20.
- M. Rathore, A. Ahmad, A. Paul and G. Jeon, "Efficient Graph-Oriented Smart Transportation Using Internet of Things Generated Big Data," 2015 11th International Conference on Signal-Image Technology & Internet-Based Systems (SITIS), Bangkok, 2015, pp. 512-519.
- Azzara, M. Petracca and P. Pagano, "The ICSI M2M Middleware for IoT-Based Intelligent Transportation Systems," Intelligent Transportation Systems (ITSC), 2015 IEEE 18th International Conference on, Las Palmas, 2015, pp. 155-160.
- R. S. H. Istepanian, A. Sungoor, A. Faisal and N. Philip, "Internet of m-health Things "m-IoT"," Assisted Living 2011, IET Seminar on, London, 2011, pp. 1-3.
- S. Das, M. Ballav and S. Karfa, "Application of IoT in detecting health risks due to flickering artificial lights," Advances in Computing, Communications and Informatics (ICACCI), 2015 International Conference on, Kochi, 2015, pp. 2331-2334.
- Y. Liu, J. Niu, L. Yang and L. Shu, "eBPlatform: An IoT-based system for NCD patients homecare in China," Global Communications Conference (GLOBECOM), 2014 IEEE, Austin, TX, 2014, pp. 2448-2453.
- A. Al-Taee, W. Al-Nuaimy, A. Al-Ataby, Z. J. Muhsin and S. N. Abood, "Mobile health platform for diabetes management based on the Internet-of-Things," Applied Electrical Engineering and Computing Technologies (AEECT), 2015 IEEE Jordan Conference on, Amman, 2015, pp. 1-5.
- K. Choubey, S. Pateria, A. Saxena, Vaisakh Punnekkattu Chirayil SB, K. K. Jha and Sharana Basaiah PM, "Power efficient, bandwidth optimized and fault tolerant sensor management for IOT in Smart Home," Advance Computing Conference (IACC), 2015 IEEE International, Banglore, 2015, pp. 366-370.
- C. Coelho, D. Coelho and M. Wolf, "An IoT smart home architecture for long-term care of people with special needs," Internet of Things (WF-IoT), 2015 IEEE 2nd World Forum on, Milan, 2015, pp. 626-627.
- V. Sivaraman, H. H. Gharakheili, A. Vishwanath, R. Boreli and O. Mehani, "Network-level security and privacy control for smart-home IoT devices," Wireless and Mobile Computing, Networking and Communications (WiMob), 2015 IEEE 11th International Conference on, Abu Dhabi, 2015, pp. 163-167.
- W. Li, C. Pi, M. Han, C. Ran, W. Chen and P. Ke, "A scheduling method for IOT-aided packaging and printing manufacturing system," in 2015 11th International Conference on Heterogeneous Networking for Quality, Reliability, Security and Robustness (QSHINE), Taipei, 2015, pp. 335-340.
- Khaleel, D. Conzon, P. Kasinathan, P. Brizzi, C. Pastrone; F. Pramudianto, M. Eisenhauer, P. A. Cultrona, F. Rusina, G. Lukac, M. Paralic, "Heterogeneous Applications, Tools, and Methodologies in the Car Manufacturing Industry Through an IoT Approach," in IEEE Systems Journal , vol.PP, no.99, pp.1-1,2015.
- H. Min and L. Junyu, "An Intelligent System for Precast Concrete Element Manufacturing Management Based on RFID Technology," Green Computing and Communications (GreenCom), 2013 IEEE and Internet of Things (iThings/CPSCom), IEEE International Conference on and IEEE Cyber, Physical and Social Computing, Beijing, 2013, pp. 1138-1143.
- Zhang Tianbo, "The Internet of Things Promoting Higher Education Revolution," in 2012 Fourth International Conference on, Multimedia Information Networking and Security (MINES), Nanjing, 2012, pp. 790-793.
- Pruet, C. S. Ang, D. Farzin and N. Chaiwut, "Exploring the Internet of "Educational Things"(IoET) in rural underprivileged areas," 12th International Conference on Electrical Engineering/Electronics, Computer, Telecommunications and Information Technology (ECTI-CON), Hua Hin, 2015, pp. 1-5.
- Kunkun and L. Xiangong, "Reliability Evaluation of Coal Mine Internet of Things," Identification, Information and Knowledge in the Internet of Things (IIKI), 2014 International Conference on, Beijing, 2014, pp. 301-302.
- V. V. H. Ram, H. Vishal, S. Dhanalakshmi and P. M. Vidya, "Regulation of water in agriculture field using Internet Of Things," 2015 IEEE Technological Innovation in ICT for Agriculture and Rural Development (TIAR), Chennai, 2015, pp. 112-115.
- National Intelligence Council, Disruptive Civil Technologies – Six Technologies with Potential Impacts on US Interests Out to 2025 –Conference Report CR 2008-07, (2008) [Online]. Available: http://www.dni.gov/nic/NIC_home.html.
- Khan, S. U. Khan, R. Zaheer and S. Khan, "Future internet: The internet of things architecture, possible applications and key challenges," in Frontiers of Information Technology (FIT), 2012 10th International Conference On, 2012, pp. 257-260.
- Z. Yang, Y. Peng, Y. Yue, X. Wang, Y. Yang and W. Liu, "Study and application on the architecture and key technologies for IOT," in Multimedia Technology (ICMT), 2011 International Conference On, 2011, pp. 747-751.
- Collina, M. Bartolucci, A. Vanelli-Coralli and G. E. Corazza, "Internet of Things application layer protocol analysis over error and delay prone links," Advanced Satellite Multimedia Systems Conference and the 13th Signal Processing for Space Communications Workshop (ASMS/SPSC), 2014 7th, Livorno, 2014, pp. 398-404.
- D. Borthakur, J. Gray, J. S. Sarma, K. Muthukkaruppan, N. Spiegelberg, H. Kuang, K. Ranganathan, D. Molkov, A. Menon and S. Rash, "Apache hadoop goes realtime at facebook," in Proceedings of the 2011 ACM SIGMOD International Conference on Management of Data, 2011, pp. 1071-1080.
- Xu, S. Huang, Y. Chen, K. Browny, I. Halilovicy and W. Lu, "TSAaaS: Time series analytics as a service on IoT," in Web Services (ICWS), 2014 IEEE International Conference On, 2014, pp. 249-256.
- C. Tsai, C. Lai, M. Chiang and L. T. Yang, "Data Mining for Internet of Things: A Survey," Communications Surveys & Tutorials, IEEE, vol. 16, pp. 77-97, 2014.


