IPSEC and SSL as solutions for the enterprise network security
Автор: Sichkar V.N.
Журнал: Juvenis scientia @jscientia
Рубрика: Технические науки
Статья в выпуске: 1, 2018 года.
Бесплатный доступ
When a company starts to build enterprise network, the information technology department always faces the question about which protocol to choose for building a Virtual Private Network (VPN). The answer is not obvious because each protocol has its own pros and cons. Priority of the selection of the protocol to build the VPN depends on specific criteria. These criteria can be the required type of access for users, the level of the network security, the level of data security, necessity of scalability for the network in future, etc. At the moment the most reliable protocols are considered to be Internet Protocol Security (IPSec) and Secure Socket Layer (SSL). This paper discusses and analysis the demand of using these protocols separately or simultaneously.
Ipsec протокол, ipsec protocol, ssl протокол, ssl protocol, vpn, network security, enterprise network, data security, encryption of data transfer
Короткий адрес: https://sciup.org/14110462
IDR: 14110462 | УДК: 004.056.55 | DOI: 10.15643/jscientia.2018.01.004
Текст научной статьи IPSEC and SSL as solutions for the enterprise network security
Introduction . Today, the company employees should have access to different enterprise applications from various types of devices. It means, either user currently is in a remote office, either in hotel room or home uses a laptop, portable device or a computer in an internet cafe, he needs to have a simple access to enterprise resources to complete his work without losing productivity. In addition, business partners or customers of the company need access to relevant resources and applications. Therefore, data protection during access to the enterprise network has to be implemented.
All kinds of the internet networks are sensitive to a large number of threats, for example, obtaining access by deception, loss of privacy, loss of data integrity, denial of service, etcetera [1]. The main purposes of the tools that provide the safe data transmission process are confidentiality, integrity, and authentication.
Confidentiality of the data includes protecting data from illegal listening [2]. And the most common way for this protection is encryption. The implementation of encryption algorithms is quite simple, despite the complexity of mathematical algorithms they use. But using encryption reduces the system performance. That is why, the solution in some cases can be implemented using the hardware encryption, in order to free the protective device from the additional load.
Integrity of the data means the identity of sent data and received data. In order to solve such problems, the hashing algorithms are used. These algorithms, based on the source of the message, calculate the hash – either a digital signature or hash of fixed length. Each side of communication process produces the same operation and compares the received and calculated value. Thus, the conclusion about the integrity of the received message are made.
Authentication allows to prove that the person from other side is really who he claims to be.
All of these properties should be inherent in any security protocol, but they can be implemented in a different form. Currently, the most reliable protocols are considered to be IPSec and SSL [3]. But each of them has both disadvantages and advantages and the main question here is how to use them in the enterprise network.
VPN based on IPSec . VPN connection based on IPsec, can offer to the companies a simple and efficient method of routing packets between nodes, providing an opportunity to establish a secure connection and sustainability in accordance with the needs of the most demanding network environments. This is the alternative of renting a private line allows for the companies to use the Internet infrastructure to quickly expand the enterprise network for geographically remote offices.
Using the IPSec protocol, the transferred data encapsulates and passes through the Internet inside IP packets. The VPN gateway receives the encapsulated datagram, decrypts them and sends them to the recipient. Traffic from the VPN gateway is treated as if it came from user on a local network. As a result, the VPN connection gives to the user full and permanent access to the network. It is ideal to maintain permanent links and share resources between users in geographically distributed offices to enhance productivity of large enterprises.
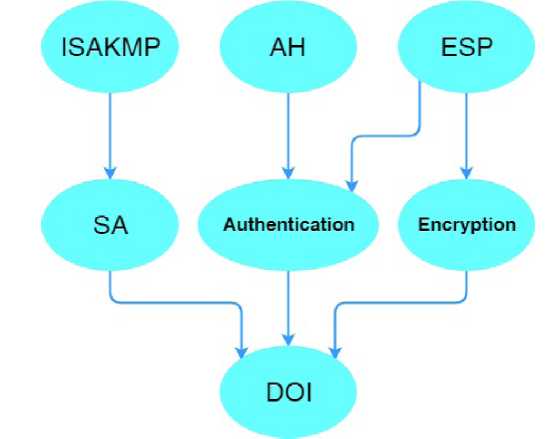
IPSec protocol provides data source authentication, cryptographic closing of the transmitted packets of the message, verifies its integrity and authenticity, and also partial protection against traffic analysis [4]. In accordance with the information exchange the IPSec security architecture is divided into three levels as it is shown on the figure 1.
ISAKMP
ESP
Authentication
Encryption
DOI
Fig. 1. The Architecture of IPSec protocol security
The upper level consists of the three protocols: Internet Security Association Key Management Protocol (ISAKMP), Authentication Header Protocol (AH), and Encapsulating Security Payload (ESP).
ISAKMP is responsible for negotiations of parameters of the virtual channel and key management ensuring overall management of the protected virtual connections, including the development of encryption algorithms, as well as the generation and distribution of key information.
AH protocol is responsible for authentication of the data source, verifying the integrity and authenticity after reception, and also it is responsible for the protection from the impose of repeated messages.
ESP protocol contents protection that provides a cryptographic closing of the transmitted packet messages.
The use in IPSec two different protection protocols of the virtual channel (AH and ESP) is due to the practice in many countries to restrict the export or import crypto technologies. Each of these protocols can be used both independently and at the same time [5].
The middle level of the IPSec security architecture consists of the algorithm for authentication and algorithm for encryption. This level also includes the algorithm for the agreement of the relevant parameters and control keys – Security Association (SA).
The foundation role in the architecture of the IPSec protocol implements Domain of Interpretation (DOI), which is a database that stores information about the protocols and the IPSec algorithms, their parameters, etc.
In some cases, the VPN access with IPSec protocol to the enterprise network may be unnecessary or impossible. For example, a mobile user who needs to check email or receive documents does not need a dedicated line for access to all resources. In addition, this level of access can cause a security risk, if an endpoint with which the user comes, is unsafe or can be easily compromised. The use of VPN with IPsec in this case represents the open door to the local network, so devices that are not covered by corporate security policy should not be allowed to connect the enterprise network.
Another point when considering VPN with IPsec is the management of resources necessary to implement and maintain. For all remote points of access, the software has to be installed and configured. And if organization provide remote access to hundreds or thousands of mobile users, the process of installing, upgrading, configuring, and managing all clients can be difficult and expensive. That is why the SSL technology for VPN has found wide application for solving the problem of remote access of mobile users or customers.
VPN based on SSL . This type of the connection uses different methodology for transmitting enterprise's data via the Internet. Instead of relying on network settings and security at the endpoints, SSL VPN uses HTTPS (Hyper Text Transfer Protocol Secure). For the VPN based on SSL there is no need to implement special software as each browser and email client has these protocols. Figure 2 shows a structure of this connection. Due to the fact that SSL is implemented at the transport level, a secure connection is established “from of end-to-end” [6]. SSL VPN connection between the mobile user and the internal network of the enterprise happens via a network connection at the application level, in contrast to open tunnel connections IPSec VPN for network level.
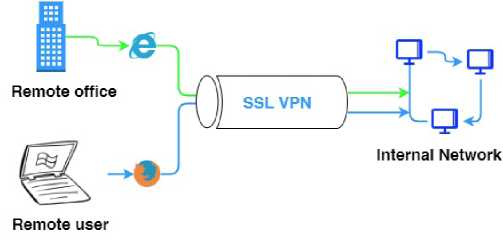
Fig. 2. Structure of SSL VPN connection
The advantage of SSL is that it has two levels – SSL Record Protocol and the SSL Handshake Protocol. As the carrier medium, can be selected the TCP Protocol, which together with SSL Record Protocol forms the so-called core SSL, on top of which can overlap with other protocols. SSL Handshake Protocol is used to authenticate the sides and to agree the specified encryption algorithm and key exchange. Also, another advantage is its independence from the programs and the platforms on which it is used.
Most of the users have faced with SSL, without even knowing it. The SSL technology installed on any device with access to the network, which uses a standard web browser and its settings. SSL operates independently of the operating system. SSL VPN is an ideal tool for mobile workers and users of remote offices.
SSL VPN also provides a detailed audit that enables enterprises and service providers to comply with many required standards. Although IPsec VPN provides user authentication, this protocol cannot provide the precise control of what user is viewing or has access to. Unlike IPSec VPN, SSL VPN has the ability to provide differentiated access and to submit reports of visits in accordance with the requirements of the various regulations.
Another advantage of SSL VPN is to ensure the security of the endpoint. If the networks IPSec VPN require obviously a certain level of security endpoints, SSL VPN provides dynamic security checks the endpoint before the session and periodically during it.
Conclusions . As can be seen from the analysis of the characteristics of these two protocols IPSec and SSL, they are not interchangeable and can function both separately and simultaneously. The choice of protocol for enterprise VPN network can be made according to the specific criteria by answering five questions.
What is the type of access required for users of the VPN? If the full-featured permanent connection to the enterprise network is required, then recommended choice is IPSec. For the temporary connection, for example, a mobile user or using a public computer, with the purpose of gaining access to certain services, such as email or database, the recommended protocol is SSL that allows to organize the VPN for each individual service.
Is the user an employee of the company? If yes, then the device he uses to access enterprise network via IPSec VPN can be configured in some certain way. If the user is not an employee of the company, it is recommended to use SSL. This will allow to limit guest access to only certain services.
What is the level of security of the enterprise network? For the high level of the network security policy the recommended choice is IPSec. Indeed, the security level of IPSec offers a much higher level than SSL, because of the usage of configurable program by the user side and the security gateway on the enterprise network. For the average level recommended choice is SSL protocol enabling access from any terminal. If the level of security can range depending on the services from medium to high, then the recommended choice is the combination of the IPSec and SSL protocols.
What is the security level of data transmitted by the user? If the security level of data is high, the recommended choice is IPSec. If the level is average, the recommended protocol is SSL. And if the choice is depending on the services and can be medium or high, then the recommended choice is the combination of the two protocols.
What is more important – the rapid deployment of a VPN or scalability of the network in the future? For the rapid deployment of the VPN with minimal cost, the recommended protocol is SSL. In this case there is no need to implement special software on the user side as in the case of IPSec. For the future scalability of the network, the recommended choice is IPSec. If the company needs both – the rapid deployment and scalability in the future, then the recommended choice is a combination of IPSec and SSL protocols. SSL should be implemented in the first stage to provide fast access to all necessary services with the subsequent implementation of IPSec.
Список литературы IPSEC and SSL as solutions for the enterprise network security
- Rosu S.M., Dragoi G. VPN Solutions and Network Monitoring to Support Virtual Teams Work in Virtual Enterprises//Computer Science and Information System. 2011. Vol.8(1). Pp. 1-26.
- Maurer U., Ruedlinger A., Tackmann B. Confidentiality and integrity: a constructive perspective//TCC Springer. 2012. Pp. 209-229.
- Rosu S.M., Dragoi G. Virtual Enterprise Network General Architecture.//8th International Conference on Communications. Bucharest, Romania. 2010. Pp. 313-316.
- Zaharuddin M.H.M., Rahman R.A., Kassim M. Technical comparison analysis of encryption algorithm on site-to-site IPSec VPN//International Conference on Computer Applications and Industrial Electronics. Kuala Lumpur, 2010. Pp. 641-645.
- Dayananda M.S., Kumar A. Architecture for Intercloud Services Using IPsec VPN//Second International Conference on Advanced Computing & Communication Technologies. Rohtak, Haryana, 2012. Pp. 463-467.
- Gallo C., Michelangelo B., Michele P. Virtual Private Networks//Encyclopedia of Information Science and Technology/IGI Globa, 2015.
- Casado M., Freeman M.J., Pettit J., Luo J., Gude N., McKeown N., Shenker S. Rethinking enterprise network control//Transactions on Networking. 2009. Vol.17. Pp. 1270-1283.
- Ward J., Peppard J. Strategic planning for information systems//John Wiley & Sons Press. UK, West Sussex, 2002.
- Rosu S.M., Dragoi G. Virtual Enterprise Network General Architecture.//8th International Conference on Communications. Bucharest, Romania, 2010. Pp. 313-316.
- Coretti S., Maurer U., Tackmann B. Constructing confidential channels from authenticated channels -public-key encryption revisited. Advances in Cryptology//ASIACRYPT Springer, 2013. Part I. Pp. 134-153.


