Iris Biometric Authentication used for Security Systems
Автор: Vanaja Roselin.E.Chirchi, Laxman.M.Waghmare
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 9 vol.6, 2014 года.
Бесплатный доступ
Pupil detection and iris localisation using scanning method and feature extraction is performed with five level decomposition techniques, with these two proposed algorithm we could achieve efficient and fast person authentication in biometric security systems. Statistical performance evaluation is also performed using parameters False acceptance rate (FAR), False rejection rate (FRR), Correct recognition rate (CRR), Equal error rate (EER), Match ratio etc, using CASIA database.
Feature extraction, haar wavelet transformation, FAR, FRR, Feature vector size, Computational time
Короткий адрес: https://sciup.org/15013413
IDR: 15013413
Текст научной статьи Iris Biometric Authentication used for Security Systems
Published Online August 2014 in MECS
Biometrics, which refers to authentication based on his or her physiological or behavioral characteristics, its capability to distinguish authorized person and an unauthorized. Since biometric characteristics are distinctive as it cannot be forgotten or lost, for identification person has to be present physically. Biometric is more reliable and capable than traditional knowledge based and token-based techniques. Biometric has drawback i.e., if compromised then it is difficult to replace. Among all biometrics such as fingerprint, facial thermogram, hand geometry, face, hand thermogram, iris, retina, voice, signature etc., Iris-based identification is one of the most mature and proven technique. Iris is colored part of eye and it is protected by eyelid and cornea as in Fig.1.Security with iris is more reliable as compared to other biometrics. Spoofing is very difficult with respect to iris pattern and thus cannot be compromised easily. In practical situation it is observed that iris part is occluded by interference of eyelids and eyelashes, improper eye opening, light reflection and image quality is degraded because of low contrast image and other artifact. Advantages of Iris is that it is not subject to the effects of aging which means it remains in a stable form from about age of one until death . The use of glasses or contact lenses has little effect on the representation of the iris and hence does not interfere with the recognition technology [17][22].
Our experiment uses wavelets such as Haar, db2, db4 for feature extraction and Hamming distance classifier used for matching process.
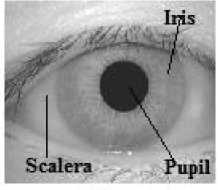
Fig.1: Structure of Iris
Contribution to the thesis is enhancement of person identification and recognition by reducing complex mathematical burden and simplifying system complexity cost in terms of time. The contribution to the research is efficient pupil detection using scanning algorithm and fast feature extraction using five level decomposition techniques to iris images.
The paper is organized in the following manner; section I Introduction to iris biometric system, section II Related work, section III System model with preprocessing steps such as image acquisition, iris localization, normalization, feature extraction and Matching. Experimental results and discussion in section IV, finally conclusion in section V.
-
II. Related work
Various approaches exist in the past for iris recognition for person identification which includes John Daugman’s Iriscode [4]. However proposed work uses Haar decomposition for iris feature extraction to get 348-bits iris code for effective iris recognition. Advantages of haar wavelet decomposition are its computational simplicity and speed. This method is less likely to be affected by environmental factors as compared to Gabor wavelet The Iris Recognition system’s main work role is to provide compact and significant feature extraction algorithm for iris images with reduced false rejection rate. The extracted feature should have high discriminating capability and the segmented iris image should be free from artifacts. Daugman [4] used a multiscale quadrature two- dimentional(2-D) Gabor filter to demodulate phase information of an iris image to create an Iriscode for authentication by comparing the Iriscode stored in database. Li Ma et al. [14] extracted features using spatial filter, this technique first converts the round image of the iris into rectangular pattern by unwrapping the circular image. Wildes et al. [16] uses Laplacian pyramid for analysis of the Iris images. Boles and Boashash [19] uses zero-crossing method with dissimilarity functions of matching. Lim et al. [18] 2D Haar Transform for feature extraction and classifier used are initialization method of the weight vectors and a new winner selection method designed for iris recognition. A. Poursaberi and H. N. Araabi [1] [2] use wavelet Daubechies2 for feature extraction and two classifiers such as Minimum Hamming Distance and Harmonic mean. L. Ma et al., [11] class of 1-D wavelet i.e., 1-D Intensity signals for feature extraction and for feature matching they have used expanded binary feature vector with exclusive OR operations. Md. Rabiul Islam et al., [16] used 4-level db8 wavelet transform for feature extraction and hamming distance with XOR for pattern matching. In our proposed research work we will be using wavelet family i.e., Haar wavelet, db2 wavelet and db4 wavelet for feature extraction and perform comparison on the basis of their performance evaluation. We also use Hamming Distance classifier to matching binary strings with enrolled entity in the database. To fasten the matching speed, a lower number of 90 bits are used in composing the iris code, as compared with other methods such as 2048 bits in [1] [2].
-
III. System model
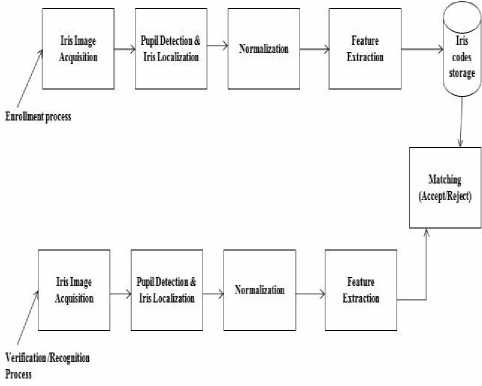
Fig.2: step by step process of system model
-
A. Image acquisition
In this research paper we are using publicly available database i.e., Institute of Automation, Chinese Academy of science (CASIA)[20] containing 756 grayscale images of eye with 108 unique eyes or classes and seven different images of each eye are considered for our work.
-
B. Iris localization
-
a. Pupil Detection using Scanning method
Scanning method for pupil detection is implemented which is contribution to our research work. Daugman [4] uses Integro differential operator which has mathematical burden to system, wildes [16] uses gradient based edge detection, Poursaberi and Araabi [1] uses image morphological operator and suitable threshold. Our proposed algorithm is as follows:
Step1: Read the original image from database.
Step2: Draw Histogram of original image and calculate threshold value of pixel intensity for pupil.
Step3: Mark and fix LF as start point on x-axis and begin scanning on x-axis, as pupil is darker part of the eye we get dark pixel only and assign them to 0 and where we get the grey pixel that is end of the dark pixel mark and fix it as RT and assign them to 1.
Step4: Mark and Fix UT and scan on y-axis we get dark pixel assign them to 0 and where the dark ends mark and fix it to LB assign the value as 1.
step5: To locate center C of pupil compute,
_ Г ^+ДТ ^ /' ИТ+ДВ 'П 2 /'X 2
Step 6: Determining pupil radius PR
PR1= abs (RT-C) ;PR2= abs (C-LF) ;PR3= abs (UB-C) ;PR4= abs(C-UT) ;Pradius_array [PR1, PR2, PR3, PR4];
PR=max [Pradius_array]
Now we can locate four points on the circumference of the pupil with LF(left), RT(right), UT(UpperTop), and LB(LowerBottom) as shown in Fig.3.Using region of interest based on color, we can detect the pupil but we must know the threshold value of pupil intensity. To find the threshold value of pupil intensity, draw the histogram of original image, which gives graphical representation between numbers of pixels v/s pixel intensity. As the pupil is black in color, the pupil pixel intensity lies closer to zero. Pupil has moderate size. Determine maximum number of pixels for intensity value, which is closer to zero. That value is threshold value of pupil intensity. If some noise occurs with pupil image, due to eyelids or eyelashes remove it. This means that there are certain pixels which lies near the pupil are of part of the iris section but having gray levels in the range of 0 to 5O. Fig.4 the original image from database, Fig.5 shows histogram of image, Fig.6 image with only pupil constructed using thresholding.
-
b. Iris radius
In our research work iris radius is calculated (as in eq1) [1].
Where 38 is pixel defined in [1], add this to pupil radius to obtain Iris radius. Therefore removing iris part from total part we get major part of Iris.
normalization (isolated image for lower half) F ig.12 Enhanced iris Fig.13 Region of interest. The remapping of this image I (x,y) from raw Cartesian coordinates to polar coordinates I (r, 9 ) can be represented (as in eq 2).
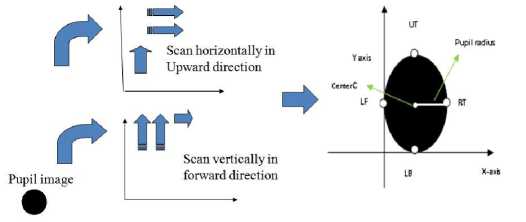
Fig.3: Four coordinate points (UpperTop(UT), LowerBottom(LB), left(LF), and right(RT)) and Center point
Where r radius lies in the unit interval (0, 1) and 9 is the angle between (0, 2π). The eq. 2 yields from eq. 3 and eq.4 and they are
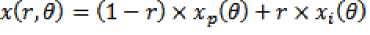

Fig. 4: Original image from database
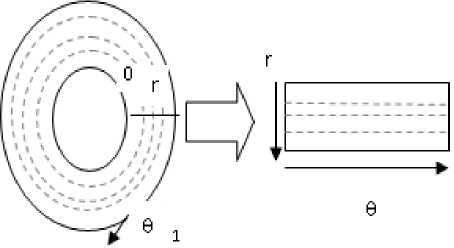
Fig. 7: Daugman’s Rubber sheet model with annular iris zone is stretched to a rectangular block and dashed lines are sampling circles.
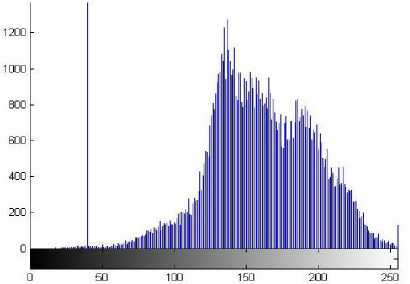
Fig.5: Histogram of original image

C. Iris normalization
vixxs) = il - rj x y/.S) - r x ^(5j (4)
where (xp( 9), yp( 9 )) and (x i ( 9 ), y i ( 9 )) are the coordinates of pupil and iris boundary points respectively.
The rubber sheet model removes the deformations, hence results to 180X32 unwrapped sizes.
-
D. Feature extraction
The iris has abundant texture information, so to provide accurate recognition of individual extract the pattern of the iris image with out noise so that quality of matching will be enhanced. Our proposed system uses Haar,db2 and db4 wavelet for feature extraction. The following steps for feature extraction.
-
1. Apply Haar Wavelet up to 5-level decomposition.
-
2. Using 4th level, 5th level decomposition details constructed the feature vectors.
-
3. Feature vectors are represented in the form of 0 and 1.
-
4. Store these feature vectors.
-
• Steps for normalizing Iris image.
-
• Use of Daugman’s rubber sheet model as in Fig.7
-
• Fixing the size of normalized figure.
Remapped image is called normalized image, which is remapped for lower 180 degrees and following figures shows the results, Fig.8 shows original image Fig.8 localized iris and Fig.10 and Fig.11 iris
In the research work of M. Nabti et. al.,[19] proposed the feature extraction using wavelet maxima components first and then applying Gabor filter bank to extract all features. The decomposition level considered by Shimaa M. Elserief et. al., [22] are four level using 2D discrete wavelet transform(DWT) with four sub bands at each stage. Proposed system consider the five level decomposition with 2D(DWT) as in Fig.14. Why 5-level decomposition? because decomposing images with a wavelet transform yields a multi-resolution from detailedimage to approximation image in each levels, considering image of size N X M (320 X 280) and decompose upto Kth level where K=1,2,3,4,5.The quadrants(subimages) with in images as the LH,HL,HH represents detailed ie images for horizontal, vertical and
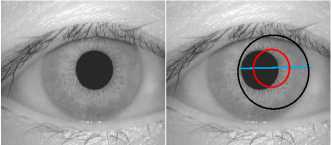
Fig.8: original image Fig.9: Localized iris

Fig.10: Normalization of original image
Pupil Asymmetry

Eyelid occlusion
Fig.11: Lower half isolated iris image

Fig.12 : Enhanced iris

Fig.13 Region of interest
diagonal orientation in the first level. The subimages LL corresponds to an approximation image that is further decomposed resulting in two level wavelet decomposition. We obtain 5th level wavelet tree showing all detail and approximation coefficients these levels are CV1 to CV5(vertical coefficient), CH1 to CH5(horizontal coefficient), CD1 to CD5( diagonal coefficient). After 5th level image size can become small to be useful.
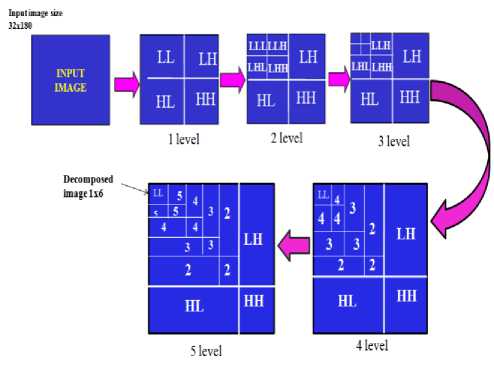
Fig. 14: 5- level haar wavelet decomposition
E. Matching
Step 1: Compare Query image feature vector with stored image feature vector of database.
Step 2: Hamming Distance is calculated for each image feature vector.
Step 3: Finally Calculate minimum Hamming Distance.
The Hamming Distance (HD) between two Boolean vectors is defined (as in eq (5)).
hd = ^7=1cAQ)e свю
Where CA and CB are the coefficients of two iris images, N is the size of the feature vector, Ex-OR is the Boolean operator that gives a binary 1 if the bits at the position j in CA , CB are different and 0 if they are similar.
-
• If HD<= Threshold then Match successful.
-
• If HD> Threshold then Match unsuccessful i.e. different person or left and right eye iris of the same person.
-
IV. Experimental Results And Discussion
-
A. Results
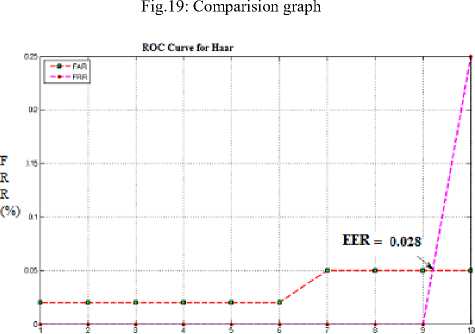
The training iris images are 756 and testing images are 100 as in Fig.15.Score distribution and frequency distribution of Intra class (testing the image with in the class) and Inter class (testing the image with other class) are calculated and plotted as in Fig.16 and Fig.17 with mean 0.38, and sigma 0.08 along with its descriptive summary as in table2 and table3. We also achieve false match rate and false non match rate for system with encouraging results interms of false Non match rate is 0.25% and false match rate is 0.11% for Haar wavelet.
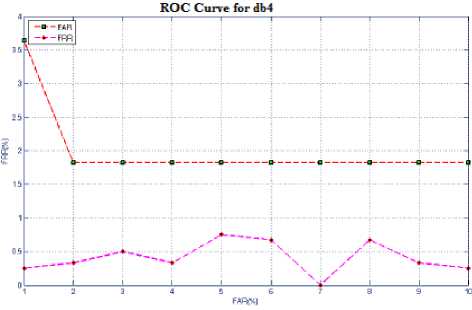
Fig.18 signifies the score distribution for imposter and genuine with different hamming distance, it states that if HD decreases FAR decreases and FRR increases and if HD increases, FAR increases and FRR decreases, this leads to plot ROC curve for haar, db2 and db4 which is as in Fig.20, Fig.21 and Fig.22. We can observe that error rate with respect to db2 and db4 are more as compared to Haar. Therefore it states that haar wavelet for feature extraction with 5-level decomposition is having reduced error rate. Feature vector table for Haar, db2 and db4 as in table1.
-
B. Comparision and Discussion
The previous existing proposed methods of iris recognition by Daugman [4], Wildes [16], Boles et al. [19], Li Ma et al. [11] are the best know. Moreover they explain and present different way of details for iris recognition in identification and verification modes. Poursaberi [1] works on wavelet for partially occluded iris texture image, Li Ma[16] also works on iris texture analysis and give encouraging results as comparing other methods Daugman results are quite encouraging in terms of accuracy and efficiency. Therefore, we analyze and compare our proposed work with exiting methods. Our method is using CASIA Iris database for verification and identification modes and found that our results are also encouraging in terms of accuracy, efficiency and reduced computational complexity. We make comparison of our results with methods [1, 4, 11, 16, 19] of published results. Table4 and Fig. 19 give the comparison in terms of CRR and EER.
-
C. Future work
Our experimental results demonstrates that enhance method for pupil extraction and five level decomposition for iris image has significantly encouraging and promising results in terms of EER and CRR. Our Feature work will include:
-
• Improving effectiveness in matching in terms of computational cost time.
-
• We are also currently working on global textural analysis with more levels of decomposition with accurate feature
-
• Extraction for larger database similar to Daugman’s methods.
-
V. Conclusion
In this paper, enhancing iris recognition algorithm based on Haar wavelet with quality texture features of iris within feature vector, even though obstruction of eyelashes and eyelids and our proposed method also works perfect for narrowed eyelid as it consider small part of the iris even though it is occluded. So, it increases the overall accuracy of the system with less computational cost in terms of time as compared with methods of Daugman [4] and Li Ma [11] and achieves high recognition rate with reduced EER, FAR, FRR. The results also show the performance evaluation with different parameters with different class of variations i.e., Inter class hamming distance variation and Intra class hamming distance variation.
Acknowledgment
I would like to show great sense of gratitude to Institute of Automation, Chinese academic of science (CASIA) for providing database to do my research work. I would also thankful to my college MBES COEA for their constant support to carry out my work.
Fig.15: Some CASIA V1 Iris testing images
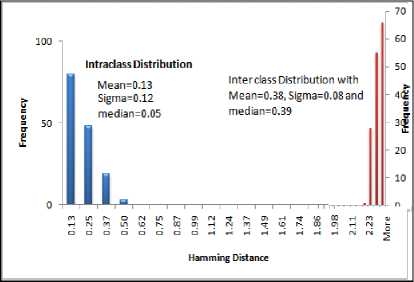
Fig.16: frequency distribution of HD for intraclass and interclass
Distribution
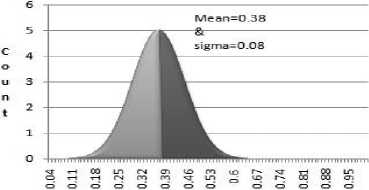
Hamming Distance
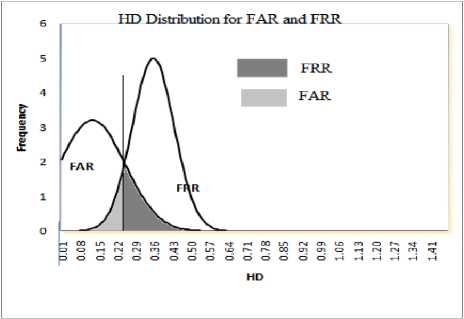
Fig.18: score distribution for imposter and genuine for different hamming distance
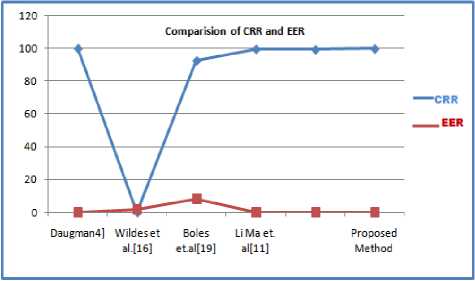
Table 1: 5-level decomposed technique for Haar, db2, db4
|
Wav elet algo rith m |
Norm alized image size |
cA1 ,cH 1 cV1, cD1 |
cA2, cH2 Cv2, cD2 |
cA3 ,cH 3 cV3, cD3 |
cA4, cH4 cV4, cD4 |
cA5, cH5 cV5, cD5 |
Feat ure Vec tor |
|
Haar |
32 X 180 |
16x 90 |
8x45 |
4x2 3 |
2x12 |
1x6 |
1x9 0 |
|
Db2 |
32 X 180 |
17x 91 |
10x4 7 |
6x2 5 |
4x14 |
3x8 |
1x2 40 |
|
Db4 |
32 X 180 |
19x 93 |
13x5 0 |
1 0x 28 |
8x17 |
7x12 |
1x6 60 |
FAK(%)
Table2: Descriptive summary of Interclass distribution
|
Descriptive summary of Interclass distribution |
|
|
Mean |
0.38 |
|
Standard Error |
0.01 |
|
Median |
0.39 |
|
Mode |
0.42 |
|
Standard Deviation |
0.08 |
|
Sample Variance |
0.01 |
|
Kurtosis |
7.10 |
|
Skewness |
-1.55 |
|
Range |
0.51 |
|
Minimum |
0.01 |
|
Maximum |
0.52 |
Fig.20:ROC curve for Haar
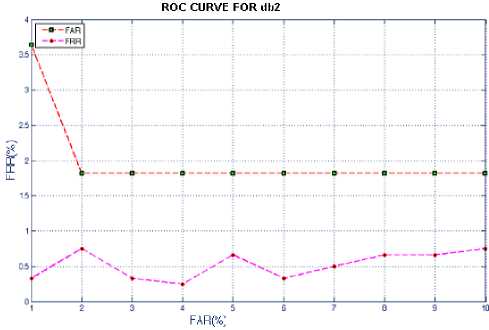
Table3: Descriptive summary of Interclass distribution
Descriptive summary of Intraclass distribution
|
Mean |
0.13 |
|
Standard Error |
0.02 |
|
Median |
0.05 |
|
Mode |
0.01 |
|
Standard Deviation |
0.12 |
|
Sample Variance |
0.02 |
|
Kurtosis |
-1.73 |
|
Skewness |
0.32 |
|
Range |
0.33 |
|
Minimum |
0.01 |
|
Maximum |
0.34 |
Fig.21:ROC curve for db2
F ig.22:ROC curve for db4
Список литературы Iris Biometric Authentication used for Security Systems
- A. Poursaberi and H. N. Araabi, (2005),” Iris Recognition for Partially Occluded Methodology and Sensitivity Analysis”, EURASIP journal on Advances in Signal processing, Vol. 2007, Article ID 36751.
- A.Poursaberi and B.N.Araabi (2005),” A Half Eye Wavelet Based for Iris Recognition”, proceeding of the 2005, 5th International Conference on Intelligent Systems Design and Applications (ISDA’05.
- Amol D. Rahulkar, R.S. Holambe Feb 2012, ”Half-Iris Feature Extraction and Recognition using a New Class of Biorthogonal triplet Half-Band Filter Bank and Flexible k-out-of-n: A postclassifier”, IEEE Transactions on Information Forensics and Security, Vol. 7, No.1.
- J.Daugman (2002), “How Iris Recognition works”, proceedings of 2002 International conference on Image processing, vol.1.
- J.Daugman Jan 2004, “How Iris Recognition works, IEEE Transactions on Circuits and systems for video Technology”, Vol. 14, No. 1.
- J.Daugman (2001), “Statistical Richness of Visual Phase Information: Update on recognizing persons by Iris patterns”, International Journal of computer vision, Vol.45, No.1, pp.25-38.
- Jafar M. H. Ali, Aboul Ella Hassanien, (2003), “An Iris Recognition System to Enhance E-security Environment Based on Wavelet Theory”, AMO-Advance Modeling and Optimization, vol. 5, No. 2
- John Daugman, (Nov 2006),” Probing the Uniqueness and Randomness of IrisCodes: Results from 200 Billion Iris Pair Comparisons”, Proceedings of the IEEE, Vol. 94, Issue: 11, pages: 1927-1935.
- L.Ma, Y.wang, T.Tan (2002), “Iris recognition Based on multichannel Gabor Filtering”, Proc. of the 5th Asian conference on computer vision, vol.I, pp.279-283.
- L.Ma, Y.wang, T.Tan(2002), “Iris Recognition using Circular Symmetric Filters”, proc. of the 16th International Conference on pattern recognition, vol.II, pp.414-417.
- Li Ma, T. Yunhong Wang, and D. Zhang, (2003), “Personal identification based on iris texture analysis”, IEEE Transactions on Pattern Analysis and machine Intelligence, vol.25, no.12.
- Li Ma, Tieniu Tan, Yunhong Wang and Dexin Zhang, (June 2004), “Efficient Iris Recognition by Characterizing Key Local Variations”, IEEE Transactions on Image processing, Vol. 13, No.6.
- Li. Ma, et al. (2004), “Local Intensity Variation Analysis for Iris Recognition”, Elsevier- Pattern Recognition, vol.37, No.6, pp.1287-1298.
- Mayank vatsa, Richa singh, Afzel Noore (Aug. 2008),” Improving Iris recognition performance using segmentation, Quality Enhancement”, Match Score Fusion, and Indexing, IEEE Transactions on Systems, Man, and Cybernetics B, Cybern., vol. 38, no. 4, pp.1021-1034.
- R.P.wildes (1999),” Iris Recognition: An Emerging Biometric Technology”, Proceeding of the IEEE, vol. 85, pp 1348-1363.
- R.Wildes, J.Asmuth, G. Green,S. Hsu, R. Kolczynski, J. Matey and S.McBride(1996), “ A machine-vision system for Iris Recognition”, Machine vision and Applications, vol.9, pp1-8.
- Richard Yew Fatt Ng, Yong Hour Tay, Kai Ming Mok 2007, “A Review if Iris Recognition Algorithm”, IEEE Transaction, DOI 978-1-4244-2328-6/08.
- S.Lim, K. Lee, O. Byeon, T. Kim, (June 2001),” Efficient Iris Recognition through Improvement of Feature Vector and Classifier”, ETRI Journal, Vol. 23, No. 2, pp. 61-70.
- W.Boles and B.Boashash, (April 1998), “A Human Identification Technique using Images of the Iris and wavelet transform”, IEEE Transactions on signal processing, Vol. 46, No. 4.
- http://www.sinobiometrics.com/resources.htm.
- Md. Rabiul Islam, Dr. Wang Yin Chai, Asma Khatun (2010), “Partial Iris Image Recognition Using Wavelet Based Texture Features”, International Conference on Intelligent and Advance Systems (ICIAS).
- V.K.Narendira Kumar, Dr.B.Srinivasan” Performance of personal Identification system technique using Iris Biometric Technology”, IJIGSP- MECS Publication, Vol.5, Pg No. 63-71, April 2013.


