Local Entropy-based Non Blind Robust Image Watermarking: Case of Medical Images
Автор: Lamri Laouamer, Mohannad Alswailim
Журнал: International Journal of Image, Graphics and Signal Processing @ijigsp
Статья в выпуске: 2 vol.16, 2024 года.
Бесплатный доступ
Medical image, watermarking, spatial domain, local entropy, imperceptibility, robustness
Medical image, watermarking, spatial domain, local entropy, imperceptibility, robustness
Короткий адрес: https://sciup.org/15019440
IDR: 15019440 | DOI: 10.5815/ijigsp.2024.02.02
Текст научной статьи Local Entropy-based Non Blind Robust Image Watermarking: Case of Medical Images
Medical data is certainly one of the most sensitive and personal data. However, they are far from being the most secure and safe from cyber-attacks. It is not the fact that the number of risky medical images belonging to individuals is increasing that is worrying, but also above all a lack of action to effectively protect this increasing personal data. Obviously, confidentiality, securing content, integrity and privacy of such data has become a serious issue.
Most of the research focusing on securing medical images aims to protect its contents sent over untrusted networks by applying different cryptographic solutions: symmetrical [1], asymmetrical [2] or even homomorphic [3]. Cryptographic solutions seem to be cumbersome with asymmetric encryptions which require a lot of computation; symmetric encryptions which should protect the encryption keys and homomorphic encryptions which generate random keys with high complexity in terms of processing despite their efficiency. These constraints make the medical images protection in real-time applications a somewhat difficult task.
A lot of researches in recent years have focused on watermarking, which seemed more adequate to deal with this problematic. Watermarking can be achieved according to the targeted objective either for integrity, authenticity, confidentiality and proof of ownership. The image watermarking is a technique allowing to embed in an image with a visible or/invisible way (depending on the objective of the watermarking solution), information called watermark.
The watermark can be embedded in the whole image or in specific regions called regions of interests in a visible or invisible manner without altering the visual quality of the watermarked image. This watermark must be resistant to different image processing attacks especially for robust watermarking schemes where the attacked watermarks should resist to different type of geometric and non-geometric attacks.
Digital watermarking systems can be classified according to several criteria, in particular: 1) the type of watermarking: robust [4], fragile [5] and semi-fragile [6]; 2) the watermark embedding domain: spatial [7] or frequency [8]. The spatial domain refers to the embedding of the watermark directly on the pixels of the host image without any preprocessing [9, 10]. The purpose of frequency watermarking is to embed the watermark after applying spectral transforms on the host image [11, 12, 13].
In this paper, we propose a new non-blind approach for medical images in spatial domain. The approach exploits one of the most image significant features called Local Entropy (LE) which consists of detecting the disorder regarding pixels distribution. Through this feature we can detect unstable areas by determining a threshold s determined through the histogram of the Local Entropy image. This process is achieved both for embedding and extracting phases.
2. Related Work
Authors in [14], proposed a medical image watermarking by creating a mask of the host image by a binary image. This purpose has as goal to identify the regions of interests to incrust the encrypted watermark at these regions to achieve an acceptable imperceptibility. This process is achieved in spatial domain within LSB pixels of the host image. Both watermark embedding and extracting processes are based on using Field Programmable Gate Array (FPGA). Authors show that the imperceptibility, security and payload issues are appreciably substantial. The proposed approach gave more interesting results especially against some cutting edge.
In [15], authors suggest a robust watermarking technique in the spatial domain by involving the discrete Fourier Transform. The technique is based on the link between the DC component of DFT matrix and the real pixel values by exploiting also quantization technology both for the embedding and extraction processes. The color images are preprocessed to obtain a 2 × 2 images blocks. The DC component of DFT in each block is computed and quantized, and the change of the DC component is assigned to each pixel value by the derived formula. The idea is to embed a one-bit watermark into one block. Meanwhile, a matrix containing the changes values on blocks are used in the extraction side. The experimental results show that this approach is efficient without applying any attacks.
Authors addressed the authentication issue through medical image watermarking in [16]. A blind and fragile watermarking has been proposed based on a self-embedding on image pixels. The approach has as objective to detect the altered zones. The self-embedding is favorably reputed for fragile watermarking since it consists to detect easily the tampered regions within host image. In return, self-embedding generates a high False Positive Rate. So to deal with this constraint authors proposed that every pixel of the image dynamically generates eight self-mutating offsprings and gets associated with them tightly at bit level. After that, a single authentication bit is selected using 16 × 1 multiplexer for each pixel. Authors show that the approach has a high imperceptibility and detect the altered zones with accuracy around 90%.
In [17], a new approach for tamper detection has been introduced by embedding multiple watermarks based on the principle component of the host image in order to make more power the security of contents. Likewise, a fragile watermarking based on LZW compression algorithm was proposed to incrust hidden data on the compressed ROI regions of the host images which make helpful the watermarking scheme to tackle the tampering attacks. This scheme is reversible by applying the decoding LZW on the encoded regions. Authors show that the proposed approach presents an acceptable imperceptibility and robustness and a quite good tamper detection accuracy.
Authors in [18] consider the watermarking performance as an optimization issue with multiple objectives exploiting the swarm techniques and especially the conventional weighted aggregation. Authors proposed a technique which is considered as an intentionally applied form of noise used to randomize quantization error called dither modulation with a uniform quantizer. This approach has been tested against several scenarios of attacks and the achieved results were very satisfied especially in term of imperceptibility.
3. Image Local Entropy
The eye is the basic organ of human vision. It comprises a set of elements which makes it possible to receive the incident radiation, and to form the image of the objects perceived and to process the information collected. Visual sensitivity is one of the most developed sensory modalities for humans. It results from the combination of several parameters: brightness, color, size, shape, movement, depth, etc… Many features can deceive the human visual system to hide information where the human eye cannot detect such as hiding data in highly textured zones, the blue component of the RBG image, contrast, etc.
The image features extraction consists to find the most significant attributes which can effectively respresent an image either for colors, edges, corners, textures, shape, etc… by reducing the image size. It is also important to a different way to represent an image in a normalized representation for the objective to reduce the computational time and fasting different processing tasks [19]. It is also important to know information relative on which pixels of the image are represented, detection of redundancies, calculation of the disorder of which the distribution of pixels is concerned, etc.
In this section, we are interested on a very promising approach in information theory and computer vision called Local Entropy (LE). Local Entropy of an image can be defined as a technique which focuses on detecting and measuring the disorder that an image may have. For example, black points in the middle of white areas and white points in black walls cause disorder, and therefore cause an increase in entropy, i.e. an increase in the amount of disorder.
The principle of LE is inspired from Shannon entropy [20]. Shannon entropy is a mathematical function which, intuitively, corresponds to the quantity of information contained or delivered by an information source as the case of an image. In other words, the Shannon entropy quantitatively represents the uncertainty that reigns in the information emanating from the source; it then indicates the quantity of information necessary for the receiver to be able to unambiguously determine what the source has transmitted. More receivers receives information about the transmitted message, more the entropy (uncertainty) regarding this message increases.
Given a discrete random variable X , with possible outcomes x_1, ..., x_n, which occur with probability P(x_ 1), ..., P(x_n) . The entropy of X ( H(x) ) is formally defined according to equation 1.
H(x) =-Y^P^Xi^logP^Xi) (1)
Therefore, it is necessary to define a continuous spatial domain фх с ф and we can define the local entropy of фх as illustrated in equation 2:
EMX) = - ^^ $фх P (у, ф^одР (у, фх)dy у с фх (2)
Where Р (у, фх) is defined in equation 3:
Р(У,фх) = I (У) ^J^dz, у с фх
Figure 1 shows an example of local entropy calculation of three images where each output pixel contains the entropy value of the 9×9 neighborhood around the corresponding pixel in the input image.

(a)

(b)
Fig. 1. (a) Host images, (b) corresponding local entropy images
Likewise, Figure 2 shows the different histograms of the host images (pixel intensity depending on the number of occurrences of each pixel). Similarly, the histograms of local entropy images (local entropy values depending on their number of occurrences) are well illustrated.
Medical image segmentation can be helpful to understand and analyze the image content. This technique makes it possible to properly exploit the image through the detection of objects, ambiguities and de-noising areas within an image. Local entropy is one of the suitable techniques used for medical image segmentation through several applications such as the differentiation of tissue from existing bones, image coarse segmentation, brain segmentation for detection of tumor, Fracture Detection, etc.



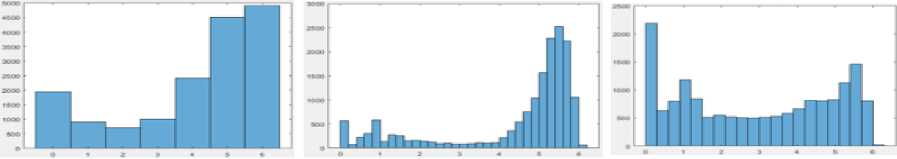
Fig. 2. Histograms of the host images and their corresponding local entropy images
4. Proposed Watermarking Scheme
Local entropy is a measure of uncertainty or randomness in an image. It can be useful to define local image complexity by de-noising and removing tissue through an image and making the image segmentation more efficient based on the differentiation of the existing objects. It is more suitable for medical images comparing to the other conventional feature extraction.
The general watermark scheme including watermark embedding process, application of different attacks either geometric or non-geometric and watermark extraction process are presented. Watermark embedding will be performed on the host image and a watermark with an linear interpolation which allows to properly control or even manipulate the visibility / invisibility of the embedded watermark by setting the factor d with diferent values between ]0,1[. Similarly we perform some attacks to alter some regions in a random way to detect the tampered zones through the original watermark w and the attacked watermark w a . The approach was evaluated on a medical images sample [21] with a dataset of 100 grayscale images representing different textures. The general proposed image watermarking scheme is illustrated in figure 3.
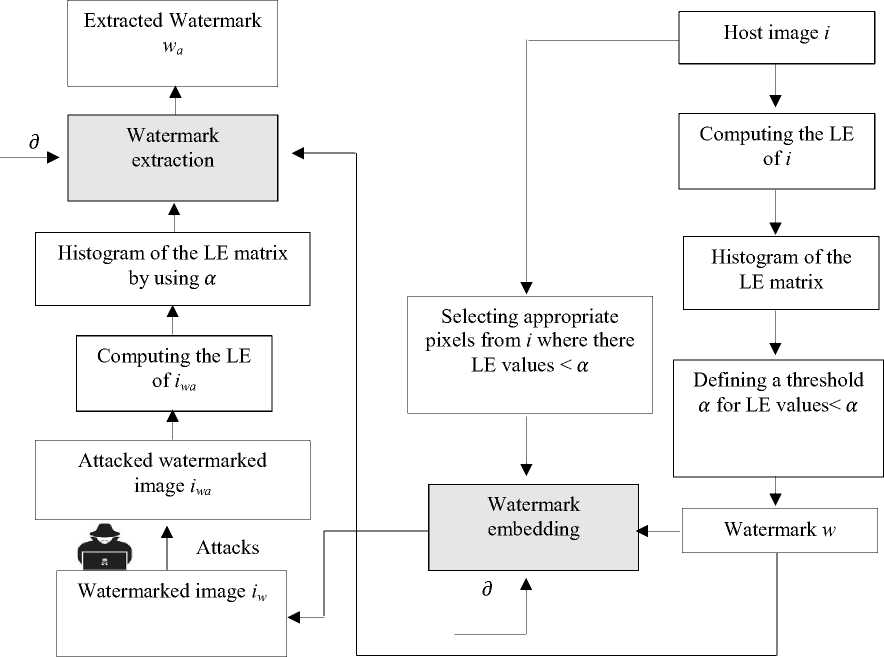
Fig. 3. Proposed image watermarking scheme.
The principle of the proposed approach based on local entropy is mainly based on two main aspects. the first aspect allows us to know or distinguish the areas of the image which represent more disorder from those which represent less disorder. This makes possible to choose the areas suitable by the watermark embedding and to reduce also the watermark payload in order to minimize the computational time both for watermark embedding and extraction.

Brain
Colon
Head
Leg
Shoulder
Spine
Fig. 4. Sample of the used images for our experimentation
The threshold can be defined randomly but for our watermarking purpose it is more advised to choose this value by taking only the Local entropy matrix values which are less than α. This can be useful to reduce the number of pixel concerned by the watermarking. The sample of the used images in our tests are illustrated in figure 4. We have choosen a variety of medical images with different textures and color distributions.
-
4.1. Watermark embedding phase
In this phase a watermark will be embedded in the host image represented by the local entropy values inferior of a defined threshold a based on the local entropy histogram. The parameter a represents the less Local Entropy values. The embedding process is achieved by a linear interpolation as illustrated in equation 4. Through this equation controling the visibility of watermark will be achieved by varying the valus of d £ ]0,1[ . More d is close to 1 more the watermark is invisible and more 5 is close to 0 more the watermark will dominante the host image which mean that the watermark will be visible more than the host image.
iw = (1- d)w + di (4)
Figure 5 illustrates an example in how to make watermark visible, semi-visible and invisible through different values of d.
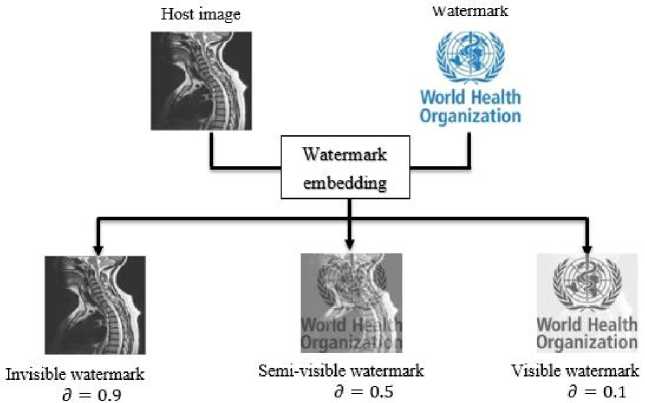
Fig. 5. Controling visibility/invisibility of watermark.
To guarantee the imperceptibility of the watermark for all used medical images, the factor d was set to a value of 0.9 (watermark becomes invisible). Figure 6 illustrates watermark embedding process by taking as inputs the host images i , watermark w and as outputs the watermarked image iw .

Fig. 6. Watermarked medical images i w .
-
4.2. Scenario of atacks
-
4.3. Watermark extraction phase
In order to evaluate the reliability of the proposed approach in terms of imperceptibility and robustness of the watermark embedded in host image, we applied a scenario of geometric and non-geometric attacks on the watermarked images using a well-known benchmark in watermarking field called Stirmark benchmark [22]. Stirmark possesses many attacks such JPEG compression, median filtering, convolution, rotation, adding noise and cropping. The purpose of these attacks is to alter the watermark itself and not the watermarked image in order to lose all evidences of watermark ownership . Figure 7 illustrates a set of attacks performed on the watermarked images.
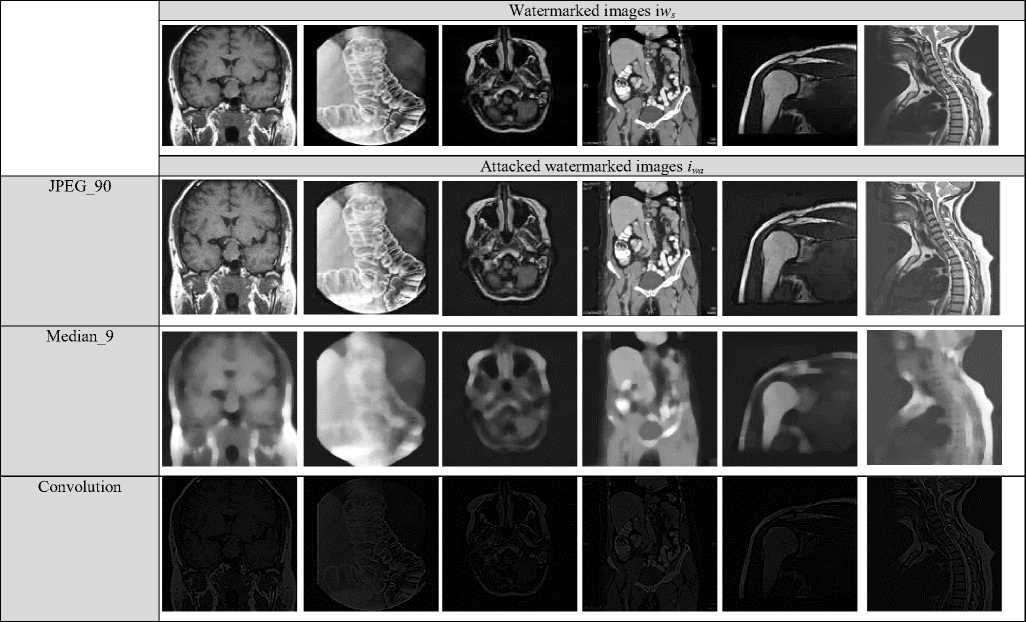
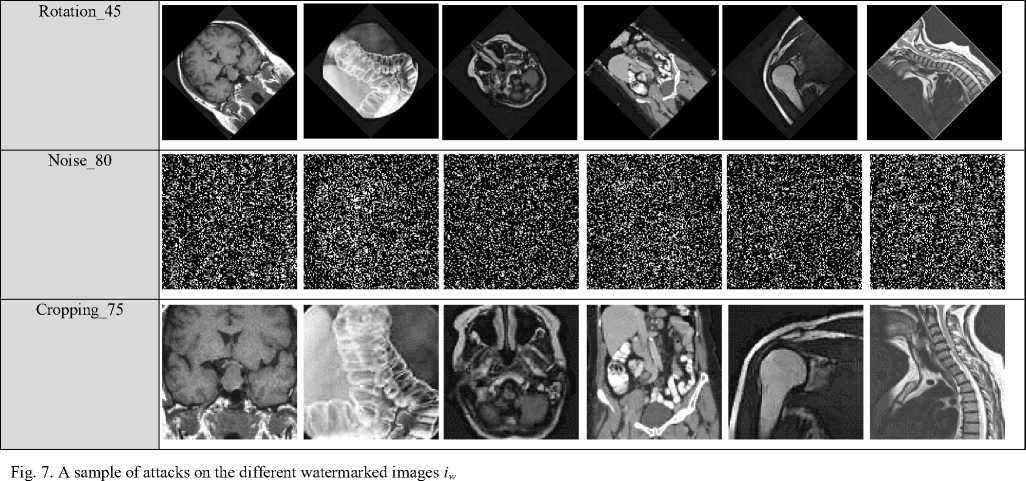
The step of extracting the watermark consists to extract the watermark images wa for each attack. This process is performed with the inverse operation of watermark embedding as defined in equation 5. This step requires as input the attacked image i wa as well as the original watermark w since the watermark system is non-blind and as output the extracted watermark w a . This process operates as the embedding process regarding the definition of the local entropy values and which uses the same value of Ct in the watermark embedding. Figure 8 illustrates the extracted watermarks against each attack.
Wa = 1W “ 3
—
1-3 .
V lwa 3
|
Attacks |
Extracted watermark images w a Brain Colon Head Leg Shoulder Spine |
|
JPEG_90 |
•r u _ • \ ^ ^ г \ T H л Wr Hr v^ Wr •Ф; t Ф 5 Ф -Ф- -Фа OJ ^TH^ 1 ^TH^ ^ TH^ ^TH^ ^TH^ ^TH^ |
|
Median_9 |
Ф Ж Ж ® Ж ЛЛС. '^* г"’1’ |
|
Convolution_2 |
vTHr \1Нс Т и :А: -А- -А- -А- ^/ТНС* ^тн^ ^тн^ ^ тн^ "ЧтнС* ^ тис* |
|
Rotation_45 |
V С Т М Т W V ^ ^ г •Ф: - • ;Л: :л: : -А- ^тн^* ^тнС* ^ rut* ^тн'-* ^ гн^ *<тн^* |
Noise_80

Cropping_75

Fig. 8. Extracted watermarks for each attack.
5. Results and Evaluation
The performance of the proposed watermarking system was evaluated according to three essential aspects: imperceptibility and robustness. Each aspect is measured through well-known metrics in image processing.
-
5.1. Imperceptibility
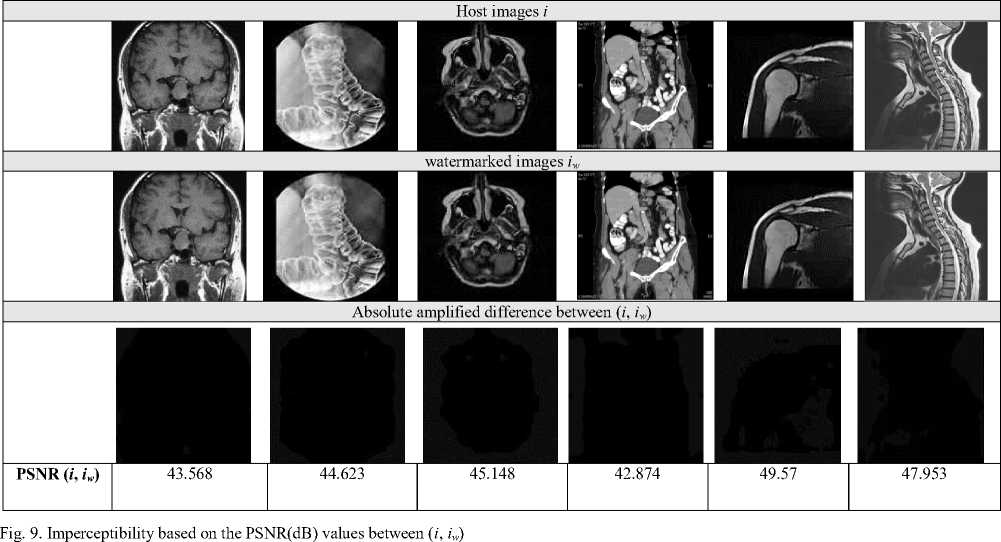
It's obvious that when embedding watermark within a host image it may alter the visual quality of the watermarked image compared to the host one. This alteration should be minimal as much as possible. Perceptual quality is measured by two well-known metrics: Peak Signal Noise Ratio (PSNR) and structural similarity index measure SSIM. A perfect similarity between two images by PSNR and SSIM measures can be expressed by a value of infinity in case of PSNR ( PSNR ^ от) and with a value of 1 in the case of the SSIM.
PSNR [23] is a logarithmic function of Mean Square Error (MSE) interpreted as a corrected version of the Signal-to-Noise Ratio. A PSNR value that exceeds 34db means a similarity between two images. A high similarity between two given images is expressed when P NR^w. The PSNR is calculated using equation 6:
PSNR = 10log 10 (—----------2) dB (6)
SS^ Z p=i Z q=i (l(P,q)-lw(p,q))
Where i(p,q) and i w (p,q) are the pixels ( p,q ) in the original image i and the watermarked image i w respectively. M *N is the size of the image.
The Structural Similarity Index (SSIM) [24] is a perceptual metric to measure the image quality degradation caused by compression losses when transmissiing data. The SSIM calculation is given by Equation 7. It is basically a combination between three keys feautures : structure, luminance and contrast to compare between two image.
SSIM =
(Z^ wl+wa +C l ) (2G wwa +C z ) &w+V wa +C 1 )(° w +a wa +C z )
Given that:
-
µ w and µ wa are respectively the average of w and w a .
-
a?, °wa w are respectively the variance of w and wa .
-
σ wwa is the covariance of w and w a .
-
5.2. Robustness
C 1 =( k 1 L )2, C 2 =( k 2 L )2 with k 1 =0.01 and k 2 =0.03.
L is the dynamic range of the pixel intensity (typically 2#bitsperpixel -1 ).
Figure 9 shows the obtained PSNR values between the host images i and the corresponding watermarked images i w .
Note that the most used metrics to evaluate the imperceptibility in most watermarking schemes are either the PSNR or The Structural Similarity Index (SSIM) which are both considered as perceptual metrics that quantify image quality degradation.
Robust watermarking system consists of hiding a signal, called a watermark, in a host signal while respecting perceptibility constraints. In this case, it must be possible to guarantee that the information embedded can withstand transformations (lawful and/or unlawful); the information must remain present even if the digital image has suffered degradation. A good watermarking system is therefore a system that resists to non-desynchronizing attacks but also to desynchronizing attacks. A desynchronizing attack can result in a global or local geometric deformation (rotation, translation, scaling, etc.). Robustness against geometric transformations remains one of the most difficult problems in image watermarking. The geometric deformation will cause a synchronization error which can significantly deteriorate the extraction and/or the detection of the watermark. For this, we measure the robustness of the proposed watermarking system through two metrics widely used in watermarking. The first metric called Correlation Coefficient (CC) as defined in equation 9 while the second metric is Bit Error Ratio (BER) as shown in equation 10.
Correlation Coefficient (CC) [23] represents the similarity between the original image and the attacked one. This coefficient is ranged in [1,-1]; if CC=1 this means that two images are highly identical, if CC=0 this means that two images are completely different. This metric is computed according to equation 8:
C C(w,wa)
________X p=i X q=i (w(p,ci)-w^(p,ci))(w(p,ci)—Va^(p,ci))_________ ^&^^=™(РЯ)-^Ря)) (X p= 1X q= 1wa(p,q)-w ^ (p,q)2)
Where W ij , wa ij are intensities of pixel (i, j ) in the original watermark image w and the extracted watermark wa respectively. The images w , w a are the means intensities of respectively the watermark image w and the extracted watermark wa.
BER [23] (Bit Error Rate) is the quotient of erroneous attacked image bits on the total number of original image bits. It is expressed in percentage as defined in equation 9.
BER(w,wa) = 1 Z^1w(i) ® wa(i) x 100% (9)
Table 1 presents the achived values of the three used metrics ( CC, SSIM and BER) related to the robustness and this for each attack.
Table 1. Extracted watermarks and their corresponding CC, SSIM and BER values
|
Extracted watermarks w a |
||||||
|
Brain |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9854 SSIM=0.9525 BER=11.3% |
CC=0.9308 SSIM=0.881 BER=16.2% |
CC=0.9971 SSIM=0.972 BER=7.08% |
CC=0.9959 SSIM=0.9567 BER=8.13% |
CC=0.4611 SSIM=0.1294 BER=32.07% |
CC=0.9975 SSIM=0.9776 BER=7.1% |
|
|
Colon |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9764 SSIM=0.9178 BER=10.7% |
CC=0.8853 SSIM=0.8442 BER=16.7% |
CC=0.9831 SSIM=0.9346 BER=10.2% |
CC= 0.9912 SSIM=0.9297 BER=7.06% |
CC=0.4707 SSIM=0.1277 BER=29.12% |
CC=0.9489 SSIM=0.9191 BER=13.2% |
|
|
Head |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9847 SSIM=0.9291 BER=11.41% |
CC=0.9826 SSIM=0.9315 BER=11.56% |
CC=0.9940 SSIM=0.9628 BER=7.2% |
CC=0.9732 SSIM=0.9042 BER=10.79% |
CC=0.5036 SSIM=0.1449 BER=34.57% |
CC=0.9916 SSIM=0.9470 BER=6.58% |
|
|
Leg |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9909 SSIM=0.9386 BER=7.24% |
CC=0.8936 SSIM=0.8193 BER=16.9% |
CC=0.9943 SSIM=0.961 BER=7.36% |
CC=0.9851 SSIM=0.9322 BER=7.49% |
CC=0.4771 SSIM=0.1277 BER=30.75% |
CC=0.9776 SSIM=0.9402 BER=10.83% |
|
|
Shoulder |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9821 SSIM=0.9081 BER=11.61% |
CC=0.9515 SSIM=0.8344 BER=12.96% |
CC=0.9786 SSIM=0.9411 BER=8.09% |
CC=0.9768 SSIM=0.9021 BER=8.2% |
CC=0.4927 SSIM=0.1368 BER=36.47% |
CC=0.9759 SSIM=0.9011 BER=8.32% |
|
|
Spine |
JPEG_90 |
Median_9 |
Convolution_2 |
Rotation_45 |
Noise_80 |
Cropping_75 |
|
CC=0.9238 SSIM=0.8609 BER=14.86% |
CC=0.8861 SSIM=0.8154 BER=17.87% |
CC=0.9822 SSIM=0.9041 BER=7.28% |
CC=0.9696 SSIM=0.9119 BER=9.5% |
CC=0.4544 SSIM=0.1280 BER=30.61% |
CC=0.9527 SSIM=0.8784 BER=12.74% |
|
5.3. Performance analysis
In order to evaluate the performance of the proposed watermarking scheme, we will argue the results obtained in terms of CC, BER and SSIM. Firstly, when we look in the correlation coefficients (CC) values, we note that most obtained values are very close to 1 except against noise attack where the CC is so far from 1. The same interpretation in the case of Similarity Index Measure (SSIM), where most of these values are also very close to close 1 except against noise attack. For the Bit Error Ratio (BER), we see that in almost cases except the noise attacks too, the values of BER are very low in terms of percentage which means that there is a very small loss between the original watermark and their corrsponding extracted one.
We can interpret the weakness of watermark robustness against noise attack by the fact that many black and white pixels are added to the watermarked image and this implicitly and integrally influences the values of local entropy (LE) and the visibility of the watermarked images.
Likewise, we conducted a comparison between the proposed approach with some valuable researches in [25, 26, 27]. As we have already mentioned, watermarking approaches operating in the spatial domain are less robust than those operating in the frequency domain. Our approach operates in the spatial domain, and despite this we will compare it with approaches operating in the frequency domain [25, 26, 27] in order to considerably evaluate the proposed approach. This comprarison will be conducted in terms of PSNR, CC and BER. it should be noted that while reading table 2 we see that the proposed approach remarkably excceds the achived metrics results in [25, 26, 27].
Table 2. Comparison between the proposed approach and approaches in [25, 26, 27] in terms of PSNR, CC and BER.
|
Approach in [25] |
Approach in [26] |
Approach in [27] |
Proposed approach |
|
|
Average of PSNR (dB) |
41.477( For Gain Factor k = 6) |
37.45 |
39.63 |
44.848 |
|
Average of CC |
0.8639 |
0.7842 |
0.8013 |
0.9538 |
|
Average of BER (%) |
- |
17.245 |
16.324 |
13.63 |
The comparison study has been made with the most relevant spatial techniques as illustrated in table2. Likewise, we chose these techniques since they represent the same almost tests experimentations. Likewise, it is very important to evaluate the proposed approach in terms of computational time especially to real time application purpose. we did not carry out this comparison with the approaches proposed in [25, 26, 27] for the reason that the used machines and processors are different which makes this comparison inappropriate.
6. Conclusion
We presented in this paper a new non-blind watermarking scheme for medical images. The approach proposed is based on one of the fundamentals of computer vision for understanding the image in terms of ambiguity, detection of redundancies, calculation of the disorder in which the distribution of pixels is concerned. This approach is mainly based on the calculation of the local entropy of the image which allows us to know or distinguish the areas of the image which represent more disorder from those which represent less disorder. This is achieved through the definition of a threshold from the histogram of the distribution of local entropy values to decide about the nature of the existing zones. From this principle, we have developed a watermarking scheme in which the watermark embedding consists only of areas with low entropy values. This also reduces considerably the calculation time both for watermark embedding and extraction since only specific areas are considered by watermarking. We measured the reliability of the proposed approach in terms of imperceptibility measured by the PSNR as well as the robustness of the watermark against several geometric and non-geometric attacks based on well-known metrics such as CC, SSIM and BER. The obtained results are very interesting and reflect the robustness of the proposed approach. We even conducted a comparison between the proposed approach with some relevant researches in medical image watermarking hence our approach presents superiority compared to those approaches.
Acknowledgment
We would like to express our gratitude to the reviewers for their precise and succinct recommendations that improved the presentation of the results obtained.
Conflict of Interest
The authors declare no conflict of interest.
Список литературы Local Entropy-based Non Blind Robust Image Watermarking: Case of Medical Images
- Pi-Yun Chen, Jian-Xing Wu, Chien-Ming Li, Chao-Lin Kuo, Neng-Sheng Pai, Chia-Hung Lin. "Symmetric Cryptography With Shift 2n-1, Hash Transformation, Optimization-Based Controller for Medical Image Infosecurity: Case Study in Mammographic Image", IEEE Photonics Journal, Vol. 12, Issue. 3, 2020.
- Santhosh Kumar B.J., Anjali Nair, Roshni Raj V.K , "Hybridization of RSA and AES algorithms for authentication and confidentiality of medical images", 2017 International Conference on Communication and Signal Processing (ICCSP), 2017.
- A.M. Vengadapurvaja, G. Nisha, R. Aarthy, N. Sasikaladevi, " An Efficient Homomorphic Medical Image Encryption Algorithm For Cloud Storage Security”, Procedia Computer Science, Vol. 115, pages: 643-650, 2017.
- José A.P.Artiles, Daniel P.B.Chaves, Cecilio Pimentel, "Robust image watermarking algorithm using chaotic sequences ", Journal of Information Security and Applications, Vol. 68, 2022.
- Neena Raj N.R, Shreelekshmi R ," Fragile watermarking scheme for tamper localization in images using logistic map and singular value decomposition", Journal of Visual Communication and Image Representation, Vol. 85, 2022.
- Pascal Lefèvre, Philippe Carré, Caroline Fontaine, Philippe Gaborit, Jiwu Huang," Efficient image tampering localization using semi-fragile watermarking and error control codes", Signal Processing, Vol. 190, 2022.
- Peter Adjei Fordjour and Wang Shuo-Zhong,"Spatial domain technique for visible watermarking”, Journal of Shanghai University (English Edition), Vol. 7, pages: 384–388, 2003.
- G. S. Kalra, R. Talwar & H. Sadawarti," Adaptive digital image watermarking for color images in frequency domain", Multimedia Tools and Applications, Vol. 74, pages: 6849–6869, 2015.
- Qingtang Su, Yugang Niu, Qingjun Wang, Guorui Shenga," A blind color image watermarking based on DC component in the spatial domain", Optik, Vol. 124, Issue 23, pages: 6255-6260, 2013.
- Jobin Abraham Varghese Paul," An imperceptible spatial domain color image watermarking scheme" Journal of King Saud University - Computer and Information Sciences, Vol. 31, Issue 1, pages: 125-133, 2019.
- C.Lakshmi, K.Thenmozhi, John Bosco Balaguru Rayappan , Rengarajan Amirtharajan," Encryption and watermark-treated medical image against hacking disease - An immune convention in spatial and frequency domains", Computer Methods and Programs in Biomedicine, Vol. 159, pages: 11-21, 2018.
- Ming Tang, Fuken Zhoub," A robust and secure watermarking algorithm based on DWT and SVD in the fractional order fourier transform domain", Array, 2022.
- S. Thakur, A. K. Singh, Basant Kumar & S. P. Ghrera," Improved DWT-SVD-Based Medical Image Watermarking Through Hamming Code and Chaotic Encryption", Advances in VLSI, Communication, and Signal Processing, pages: 897–905, 2019.
- Sandeep Bal, Sanjay Das, Soumadeb Dutta, Souma Das, Debamita Biswas, Abhishek Basu, " FPGA Realization of Medical Image Watermarking", 2018 IEEE Electron Devices Kolkata Conference (EDKCON), 2018.
- Hongjiao Cao, Fangxu Hu, Yehan Sun, Siyu Chen, Qingtang Su, " Robust and reversible color image watermarking based on DFT in the spatial domain", Optik, Vol. 262, 2022.
- Shivendra Shivani, " Verifiable medical images for E-healthcare: A novel watermarking approach using robust bit-wise association of self-mutating offsprings of pixels", Microprocessors and Microsystems, Vol. 90, 2022.
- Hanan S. Alshanbari, "Medical image watermarking for ownership & tamper detection", Multimedia Tools and Applications, Vol. 80, pages: 16549–16564, 2021.
- Yenner J. Díaz Núñez, Anier Soria Lorente & Stefan Berres, "Medical Image Watermarking with Separable Moments", Progress in Artificial Intelligence and Pattern Recognition, IWAIPR 2021, pages: 370–379, 2021.
- B. Sree Vidya , E. Chandra, " a Entropy based Local Binary Pattern (ELBP) feature extraction technique of multimodal biometrics as defence mechanism for cloud storage ", Alexandria Engineering Journal, Elsevier, Vol. 58, pages: 103–114, 2019.
- Shannon, C.E. (1948) A Mathematical Theory of Communication. Bell System Technical Journal, 27, 379-423. http://dx.doi.org/10.1002/j.1538-7305.1948.tb01338.x
- https://barre.dev/medical/samples/
- "Stirmark 4.0 ". https://www.petitcolas.net/watermarking/stirmark/ , 1998.
- Musab Ghadi, Lamri Laouamer, Laurent Nana, Anca Christine Pascu, "A Novel Zero-Watermarking Approach of Medical Images Based on Jacobian Matrix Model ", Security and Communication Networks, Wiley, Vol.9, Issue 18, pages: 5203-5218, 2016.
- Lamri Laouamer, Omar Tayan, "An Efficient and Robust Hybrid Watermarking Scheme for Text-Images ", International Journal of Network Security, Vol. 18, Issue. 6, pages: 1152-1158, 2016.
- Rohit Thanki, Surekha Borra, Vedvyas Dwivedi, Komal Borisagar. An efficient medical image watermarking scheme based on FDCuT–DCT. Engineering Science and Technology, an International Journal. Volume 20, Issue 4, pages :1366-1379, 2017.
- Xiaobing Kang, Fan Zhao, Yajun Chen, Guangfeng Lin, Cuining Jing" Combining polar harmonic transforms and 2D compound chaotic map for distinguishable and robust color image zero-watermarking algorithm" Journal of Visual Communication and Image Representation, Vol. 70, 102804, 2020.
- Zhiqiu Xia, Xingyuan Wang, Bing Han, Qi Li, Xiaoyu Wang, Chunpeng Wang, Tingting Zhao, " Color image triple zero-watermarking using decimal-order polar harmonic transforms and chaotic system" Signal Processing, Vol. 180, 107864, 2021.


