Method for Cyberincidents Network-Centric Monitoring in Critical Information Infrastructure
Автор: Zhengbing Hu, Viktor Gnatyuk, Viktoriia Sydorenko, Roman Odarchenko, Sergiy Gnatyuk
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 6 vol.9, 2017 года.
Бесплатный доступ
In this paper the method of network-centric monitoring of cyberincidents was developed, which is based on network-centric concept and implements in 8 stages. This method allows to determine the most important objects for protection, and predict the category of cyberincidents, which will arise as a result of cyberattack, and their level of criticality.
Cyberincident, ICT, ITS, network-centric concept, monitoring, criticality, KDD 99 base, CERT/CSIRT
Короткий адрес: https://sciup.org/15011856
IDR: 15011856
Текст научной статьи Method for Cyberincidents Network-Centric Monitoring in Critical Information Infrastructure
Given the dynamics of development and globalization of information and communication technologies (ICT) implementation and use of ICT in most areas of public life has become outstanding relevance. This process includes: development of the interactive communication and information exchange (social networks, e-mail sharing, instant messaging, video and Internet telephony); computerization and automation of manufacturing processes and most areas of public life (creation of local (corporate) computer networks, systematization of information in databases, platforms for collaboration users, sharing resources, VoIP and video communication, electronic documents, customer relationship management system (CRM); enterprise resource planning system (ERP), information security management system, monitoring and access control); Internet-banking, ecommerce, instant money transfer and more. All of these procedures, the operation of which is providing by ICT, is quite critical, even for the average citizen, especially in terms of the information that circulates in them. The emergence of cyberincidents (events that can disrupt cyber security (confidentiality, integrity and availability of information in cyberspace) [1]) and, consequently, violations of the regular mode of operation of the entire system can cause considerable damage.
The work includes original research and proposes new method of network-centric monitoring of ITS incidents implemented in 8 phases: classification of cyberattacks, detecting the type of cyberattack, categorization of cyberincidents, forming the set of rules cyberincidents extrapolation, determination the objects of protection, determination the impact of cyberincidents on ITS components, identification of the most critical components of the ITS, ranking the degree of cyberincidents danger. On the input is filed, the set of measurement standards of cyberattacks parameters, set of current parameters that recorded by sensors, statistic of ITS incidents, categories of ITS incidents, ITS components; and on the output we get: the type of cyberattack, forecasted incident as a result of realized cyberattack, the level of incident criticality, impact assessment of incidents categories on ITS components, the most critical ITS components.
-
II. Analysis of The Research and Problem Statement
Today there are many works devoted to the research of detection of unauthorized activities in ICT, for example, in [3] carried out a comparative analysis of intrusion detection system (IDS) using virtual honeypots (Honeypot) last generation Honeynet GenIII (Autograph, PADS, PAYL, COVERS, DIRA, DOME, Minos, Paid, Vigilante, HoneyStat etc.), which have different mechanisms of intrusion detection and working with different input data. Work [4] contains a detailed analysis of the systems and tools of crisis management in various fields, including a prediction, identification, assessment and crisis response. Although most of the examined systems are based on the use of sensors (sensors) and collected statistics, however such systems can’t be used in cyberspace to manage information (cybernetic) security, since they do not operate with real parameters of cyberspace. Considering this, it is not possible the prediction of defeat by cyberincidents also for specific components of Information and Telecommunication Systems (ITS) as components of cyberspace and, consequently, it is not possible to control resistance (countermeasures) and elimination of consequences of various categories of cyberincidents.
-
III. The Concept of Network-Centric Monitoring of Cyberincidents
Anti-emergence and elimination of cyberincidents consequences through the facilities that are combined by information networks into a single system includes: 1) Constant computer monitoring of potentially dangerous places and objects to determine the necessary measures for eliminating the consequences of each type of possible cyberincidents; 2) Implementation of necessary measures of preparation for the elimination of consequences of possible groups of cyberincidents; 3) Establishment of goals for parallel elimination of possible types of cyberincidents, their synchronization, coordination and ranking; 4) Implementation of parallel strategies purposes, their interaction and synchronization of resources used; 5) The formation of a possible set of parallel operational impacts, their scheduling, synchronization and maneuvering resources management dynamics.
Network-centric monitoring system combines monitoring tools at all levels and areas of governance into a coherent whole. It should provide proof of all necessary information to recipients in real time or close to it, in process of receipt, very importantly, by using the information gained at all levels and areas of control. This approach allows dramatically improve the understanding of the situation by the leaders at all levels, increase the level of interaction and implement the synchronization of efforts by the horizontal and vertical control. It should be noted that the violation of even one of these principles can lead to serious complications. Network-centric concept is focused not only on effective management of available technical, financial and on other means, but also to achieve information superiority in economics, politics, social sphere, etc., providing the system's ability to quickly adapt to transient conditions and to transfer the functions of strategic and operational control vertically and horizontally according to the needs of the existing situation. For this network-centric monitoring should provide real-time complex multilevel analysis of streams separate, uninformative and often contradictory initial information about new facilities or processes and dynamic of parameters changing. The system should be able to change the logic of the analysis of the existing situation as far as changing information sources and new information, which was receive about the situation. Failure of one or more local monitoring subsystems should not lead to the collapse of all network-centric monitoring.
When working response teams with cyberincidents of type CERT / CSIRT [10] according to specified concept we set sequence (Fig. 1): in ITS happens a certain event of information security E1 ... En (according to [2] in meaning of event of information security, we understand identified system behavior , service or network, that points to a possible breach of information security, policy, control facilities failure or previously unknown situation that may be relevant to information security) caused by cyberattacks CA1 ... CAn [11] as well as unintentional actions that coming on the sensors S1 ... Sn (sensors of network-centric monitoring system of cyberincidents can be sources of information such as intrusion detection/prevention systems IDS / IPS [23, 24], integrity monitoring systems, firewalls, honeypot systems, analyze vulnerabilities systems, exploits, operating systems, different applications (including specialized detection systems of cyberincidents with type SIEM), anti-virus and anti-spam systems, user requests in systems such as Service Desk or Help Desk etc.) which identifies and fixes cyberincidents I1 ... In in particular set of parameters, comparing with relevant patterns.
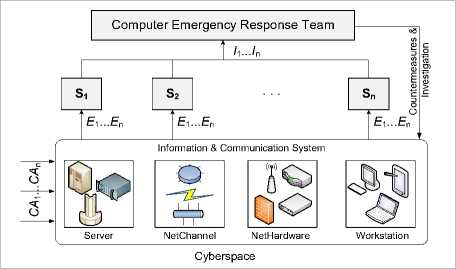
Fig.1. Implementation Scheme of Cyberincidents Network-Centric Monitoring Concept
Network-centric monitoring is determined by that for each management system of cyberincidents forms a network of agents (sensors). The overall management system of cyberincidents region or state can be displayed as a complex network of interconnected centers (teams) campus type, each of which is able to: have a clearly defined goal of the functioning; act in accordance with its rules and algorithms; manage a database containing the requested information; use the results of monitoring, responding to them by their actions; take their own initiative; send and receive messages from other systems and join with them in interaction.
-
IV. Method for cyberincidents network-centric
MONITORING
On the basis of this conception the method for cyberincidents network-centric monitoring in general is based on the following sequence of events (Fig. 2): identified and classified at several levels cyberattacks (based on a comparison of current parameters with the parameters listed in the database templates attacks, such as KDD 99 (2 level classification), CAPEC (4 level classification) etc. [12-14]) may cause for cyberincidents who belong to one of the categories (in various fields these categories may be different, for example CERT-UA [15] defines 7 categories of incidents which indicated in Fig. 2). Cyberincident which may arise because of attack could potentially harm the components of ITS (a set of information and telecommunication systems which are acts in data processing as a coherent whole [16]), for example, according to [15] can be identified 4. Definition of ITS components that require protection (objects of protection) will minimize the impact of cyberincidents on them. In addition, in the case of simultaneous occurrence of incidents is important to predict the level of danger for more effective treatment and adequate response (investigation) by teams CERT / CSIRT.
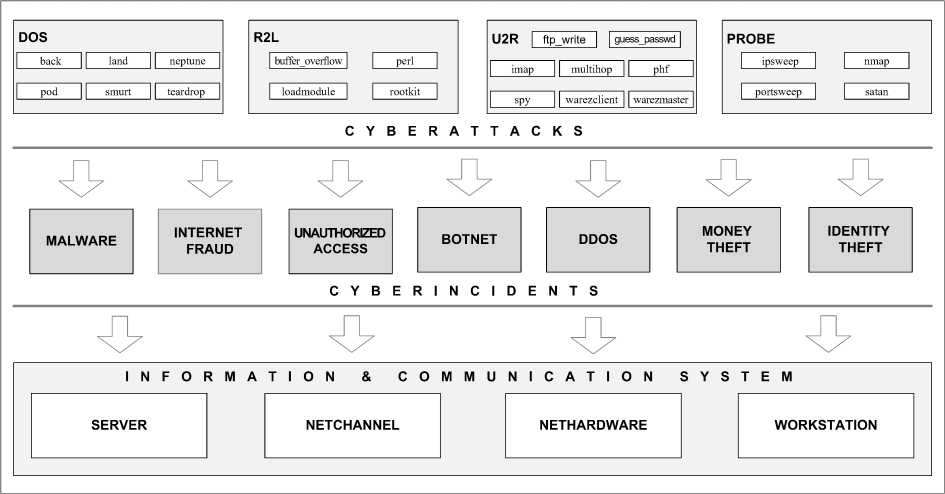
Fig.2. General Scheme of Method for Cyberincidents Network-Centric Monitoring
The proposed method for cyberincidents networkcentric monitoring implements in 8 phases: classification of cyberattacks, detecting the type of cyberattack, categorization of cyberincidents, forming the set of rules cyberincidents extrapolation, determination the objects of protection, determination the impact of cyberincidents on ITS components, identification of the most critical components of the ITS, ranking the degree of cyberincidents danger.
Phase 1 – Classification of cyberattacks. For this stage we ask the set of cyberattacks parameters standards CA that may occur in the ITS:
{J CA i } = {CA 1 , CA 2 ,...,CA n }, (1)
i=1
where CA c CA, (i = 1, n), n - cyberattacks quantity, and mi
CA. = {|JCAj} = {CAii, CA 12, ..., CA.}, (2) j=1
where CA (j = 1, m) – subsets of the subclasses of iji cyberattacks.
Considering (2) write the expression (1) as follows:
{U CA 1 } = { U { 0 CA j }} = {{ CA ., . CA ,, , ..., CA..... }, i=1 i=1 j=1
{CA ,1, CA ,2 , ... , CA 2 . },..., {CAn 1, CAn 2 , ... , CA . }},(j = 1.)
Subsets of the subclasses of cyberattacks CAy c CAj define as:
r ij
CA,= s=1 Then the expression (3) with considering (4) will where CA (s = 1, r.) - parameters that describes ijs ij receive as follows: cyberattacks CAy; r - parameters quantity. n nmi n mi rij {U CAi}={U{UCAj}}=WU cAjs}}}= = {{{САШ ,GA112,...,GAur1 MGA.i ,СЛ,22 ,...,€Ai2r },...,{СА1 „,„CAi „.„GA, m ,m 1}}, {{СА 211 ,СА 212 ,...,СЛ 21 Г| },{СЛ 221 ,СА 222 ,...,СА 22 r },.,{СА 2 „ 21 ,СА 2 „ 22 ,...,СА 2 m 2.2 }}, {{СЛ n 11 ,СЛ n 12 ,...,СЛ „ 1 п },{СА „ 21 ,СА n 22 ,...,СА , 2,2 },...,{СА РСА nm 2,..., СА w_}}}. For example, using that contains 5 million of cyberattacks parameter sets and normal behavior (from KDD 99 base), if n = 4 , according to the expression (1) we will get the following: Using the expression (2), and data from the Table 1, for example if m = 6, m = 4, m = 8, m = 4 , we get: {U СА i} = {СА1, СА 2 ,САз ,СА 4 } = i=1 СА^иСАij} = {САи, САи, ..., СА^} =, j=1 {СА DOS .СА .СА .СА 1 = , ^^ R2L , V-^ U2R , V,^1 probe} = {СADos.|, САDOS,2,..., СADOS,6 = {DOS, R2L, U2R, PROBE}. BACK,DOSLAND,DOSNEPTUNE, where СА, = САПО = DOS, СА2= САК2, = R2L , СА, 1 DOS 2 R2L 3 = СА U2R = U2R, СА4 = СAPROBE = PROBE — cyberattacks classes from KDD 99 base. Consider the cyberattacks classes in details (Table. 1): DOSPOD,DOSSMURT,DOSTEARDROP} = = {BACK, LAND, NEPTUNE, POD, SMURT, TEARDROP}, Table 1. Cyberattacks from KDD 99 Class Subclass 1. DOS 1.1. BACK, 1.2. LAND, 1.3. NEPTUNE, 1.4. POD, 1.5. SMURT, 1.6. TEARDROP 2. R2L 2.1. BUFFER_OVERFLOW, 2.2. PERL, 2.3. LOADMODULE, 2.4. ROOTKIT 3. U2R 3.1. FTP_WRITE, 3.2. GUESS_PASSWD, 3.3. IMAP, 3.4. MULTIHOP, 3.5. PHF, 3.6. SPY, 3.7. WAREZCLIENT, 3.8. WAREZMASTER 4. PROBE 4.1. IPSWEEP, 4.2. NMAP, 4.3. PORTSWEEP, 4.4. SATAN where (V, = СADos,1 = DOSbacK = BACK , ^2 = СADOS,2 = DOS LAND = LAND, СА^ = СADOS,3 = DOSNEPTUNE = NEPTUNE , СА1,4 = СADOS,4 = DOSpoD = POD, СА1,5 = САdos,5 = DOSsmurt = SMURT, СА^ СADOS,6 = DOSteardrop = TEARDROP - cyberattacks subclasses of class DOS according to KDD 99 base (Table 1). Under the specified classes in the Table 1 according to [15] will understand the following: 1. Denial of Service (DOS) – cyberattacks the denial of service, which are characterized by generating a large volume of traffic, that leading to congestion and blocking server (including 6 subclasses of cyberattacks); 2. Remote to User (R2L) – cyberattacks, which are characterized by obtaining illegitimate (unregistered) user unauthorized remote access to the management information (including 4 subclasses of cyberattacks); 3. User to Root (U2R) – cyberattacks that provides unauthorized empowerment of illegitimate (unregistered) users to the level of local superuser (administrator) (including 8 subclasses of cyberattacks); 4. Probing (PROBE) – scanning ports cyberattacks to obtain confidential information (including 4 subclasses of cyberattacks). СА2 = {(J САj }= {СА1,1 , СА1,2 , СА1,3 , СА1,4 }= j=1 = {САR2L,1 , R2L,2 , R2L,3 , R2L,4 = {R2LBUFFER_OVERFLOW ,R2LPERL , R2LLOADMODULE ,R2LROOTKIT }= = {BUFFER_OVERFLOW, PERL, LOADMODULE, ROOTKIT}, where = = = С/А 1,1 С/А R2L,1 BUFFER OVERFLOW BUFFER OVERFLOW, СА, = САМ, = R2LPE„.= 1,2 R2L,2 PERL PERL , СА, з = СА^, = LOADMODULE , СА, 4= 1,3 R2L,3 1,4 САМ1 4= R2Lrootк| = ROOTKIT - cyberattacks R2L,4 ROOTKIT subclasses of class R2L according to KDD 99 base (Table 1). СА3 = {и СА Ц} = {СА1,1, СА1,2, ^, СА1,8} = j=1 = {СAu2R,1, СAu2R ,2,..., СAu2R ,8} = {U2R ftp write, U2R guess paSSWD , U2Rimap , U2RMULTIHOP, U2RPHF, U2RSPY, U2RWAREZCLIENT , U2RWAREZMASTER }= = {FTP_WRITE,GUESS_PASSWD, IMAP, MULTIHOP, PHF,SPY, WAREZCLIENT, WAREZMASTER} where СA1,1=СAU2R,1=U2RFTP_WRITE=FTP_WRITE, СA1,2=СAU2R,2=U2RGUESS_PASSWD=GUESS_PASSWD, СA1,3 = СAU2R,3 = U2RIMAP = IMAP, СA1,4 = СAU2R,4 = U2RMULTIHOP=MULTIHOP, СA1,5=СAU2R,5=U2RPHF = PHF , СA1,6 = СAU2R,6 = U2RSPY = SPY , СA1,7= СAU2R,7 = U2RWAREZCLIENT = WAREZCLIENT, СA1,8 = СAU2R,8 = U2RWAREZMASTER = WAREZMASTER – cyberattacks subclasses of class U2R according to KDD 99 base (Table 1). CA4 = {Q| CAij} = {CAi4 , CA.,2, CAm, CAm } = j=1 “ {CA PROBE,1, CA PROBE, 2, CAPROBE,3, CAPROBE,4}= ={PROBEIPSWEEP , PROBENMAP , = {IPSWEEP, NMAP,PORTSWEEP,SATAN}, where СA1,1 = СAPROBE,1 = PROBEIPSWEEP?= IPSWEEP , СA1,2 = СAPROBE,2 = PROBENMAP = NMAP , СA1,3 = PROBE,3 PORTSWEEP = PORTSWEEP , СA1,4 = СAPROBE,4 = PROBESATAN = SATAN – cyberattacks subclasses of class PROBE according to KDD 99 base (Table 1). Each of the attacks, which belong to one of these classes, is represented as a tuple of parameters [13]: < D, PT, S, F, SB, DB, L, WF, U, H, NFL, LI, NC, RS, SA, NR, NFC, NS, NAF, NOC, IHL, IGL, C, SC, SR,SSR,RR,SRR, (11) SSER, DSR, SDHR, DHC, DHSC, DHSSR, DHDSR, DHSSPR, DHSDHR, DHSR, DHSSR, DHRR, DHSRR > All the above parameters of a tuple are divided into 4 categories [12, 13]: 1. Characteristics of the individual TCP-connections (Table 2); 2. Characteristics of content (Table 3); 3. Characteristics of traffic using the two-second time window (Table 4); 4. Characteristics of the destination host (Table 5). PROBEPORTSWEEP,PROBESATAN} Table 2. Characteristics of the Individual TCP-Connections Code Name Description Data type D duration connection time (in seconds) continuous PT protocol_type protocol type, ie tcp, udp, etc. discrete S service target service that used, ie http, telnet, etc. discrete SB src_bytes the number of bytes transferred from the source to destination at one connection continuous DB dst_bytes the number of bytes transferred from destination to the source at one connection continuous F flag status of connection: normal, error discrete L land If the source and the receiver has the same numbers of ports, the parameter takes the value of “1”, if not – “0” discrete WF wrong_fragment the total number of damaged fragments in a particular connection continuous U urgent the number of urgent packets in a particular connection. Urgent packet -it is a packet in which URG bit of urgency was enabled continuous Table 3. Characteristics of Content Code Name Description Data type H hot the number of “hot” indicators that are includes at content, such as entry into system directories, creation and execution of programs continuous NFL num_failed_logins the number of authorization failures continuous LI logged_in Authorization status: “1” - authorization is successful, “0” - failed discrete NC num_compromised the number of compromised conditions continuous RS root_shell “1” if an administrator rights were received, “0” - if not discrete SA su_attempted “1” if there was an attempt to get administrator rights or if an administrator rights were received, “0” - if not discrete NR num_root the number of administrative access, or the number of operations performed by an administrator in a particular connection continuous End of Table 3 NFC num_file_creations the number of operations of the files creation in a particular connection continuous NS num_shells the number of requests for access to the administration shell continuous NAF num_access_files the number of operations with access control file continuous NOC num_outbound_cmds the number of outgoing commands in ftp session continuous IHL is_hot_login “1” if the authorization belongs to the “hot” list ie administrators,”0” - if not discrete IGL is_guest_login ”1” if the authorization belongs to the guest account, “0” - if not discrete Table 4. Characteristics of Traffic using the Two-Second Time Window Code Name Description Data type C count the number of connections to the target host during the time interval of 2 seconds continuous SR serror_rate % of connections with error type SYN for the host source continuous RR rerror_rate % of connections with error type REJ for the host source continuous SSR same_srv_rate % of connections to the service continuous DSR diff_srv_rate % of connections with different services continuous SC srv_count the number of connections to the current service (port number) for the last 2 seconds. continuous SSER srv_serror_rate % of connections with error type SYN for the source service continuous SRR srv_rerror_rate % of connections with error type REJ for the source service continuous SDHR srv_diff_host_rate % of connections with different hosts continuous Table 5. Characteristics of the Destination Host Code Name Description Data type DHC dst_host_count the number of connections to the host continuous DHSC dst_host_srv_count the number of connections to the service continuous DHSSR dst_host_same_srv_rate % of connections to the service on this host continuous DHDSR dst_host_diff_srv_rate % of connections with different services on this host continuous DHSSPR dst_host_same_src_port_rate % of connections to this host with current source port number continuous DHSDHR dst_host_srv_diff_host_rate % of connections to the service from different hosts continuous DHSR dst_host_serror_rate % of connections with error type SYN for this destination host continuous DHSSR dst_host_srv_serror_rate % of connections with error type SYN for this destination service continuous DHRR dst_host_rerror_rate % of connections with error type REJ for this destination host continuous DHSRR dst_host_srv_rerror_rate % of connections with error type REJ for this destination service continuous By using the expressions (3-5) will forms the value r (i =1,n, j =1,m ) . For example, KDD 99 base as shown in Table 1-5 rij= 41(i=1,4, m1=6, m2=4, m3=8, m4=4) . As if СA we choose the set of cyberattacks parameters standards from KDD 99, than СA=СA and then we get: CAKDD = {U CA i} = {U {0 CAij}} = {U {0 {U CA ijs}}} = i=1 i=1 j=1 i=1 j=1 s=1 = {{{CA1,1,1, CA1,1,2 , eee, CA1,1,r1 }, {CA1,2,1, CA1,2,2 , —,CA1,2,r2}, *••’ {CA1,m1,1, CA1,m1,2 , •**, CA1,m1,rm1}}, {{CA2,1,1, CA2,1,2 , —, CA2,1,r1 }, {CA2,2,1, CA2,2,2 , —, CA2,2,r2 },—, {CA2,m2,1, CA2,m2,2 ,—, CA2,m2,rm2}}, {{CAn11,CAn12,...,CAn1r },{CAn21,CAn22,...,CAn2r },...,{CAnm 19CAnm 2,...,CAnm r }}} = 11 n,1,1, n,1,2 , , п,1,Г1 , * n,2,1, n,2,2 , , n,2,r2 *, , t n,mn ,1, n,mn ,2 , , n,mn ,rmn > > > { { {CA1,1,1, CA1,1,2 ,•••, CA1,1,41}, {CA1,2,1, CA1,2,2 ,’”, CA1,2,41 }, ”’, {CA1,6,1, CA1,6,2 {{CA 2,1,1 {{CA 3,1,1 , , CA CA 2,1,2 , L3,1,2 , ...,CA ..., CA 2,1,41 3,1,41 },{CA },{CA: 2,2,1 , '3,2,1 ’ CA2,2,2 , .•*, CA2,2,41}, .•*, {CA2,4,1, C A CA3,2,2 , ••*, CA3,2,41}, ••*, {CA3,8,1, CA; 2,4,2, 3,8,2 ’ ,...,CA1>6>41}}, •••, CA 2,4,41}}, —,CA3,8,41 }}, {{CA4,1,1, CA4,1,2 , ••*, CA4,1,41 }, {CA4,2,1, CA4,2,2 , *”, CA4,2,41}, eee, {CA4,4,1, C A4,4,2 , •••, CA4,4,41 }}}= = {{ {CAdos,1,1, CAdos,1,2 ,---, CAdos,1,41}, {CADOS,2,1, CADOS,2,2 ’".’ CADOS,2,41}’---’ {CADOS,6,1, CADOS,6,2,---, CADOS,6,41} }, {{CAR2L,1,1, CAR2L,1,2 ,---, CA] { {CAU2R,1,1, CAU2R,1,2 ,”*, CA1 1R2L ,1,41 ■ U2R ,1,41 }, {CAr2l,2,1, CAR2L,2,2 ,--., CAR2L,2,41 L---, {CAR2L,4,1, CAR2L,4,2,--., CAR2L,4,41} }, }, {CAU2R,2,1, CAU2R,2,2,---, CAU2R,2,41 L---, {CAU2R,8,1, CAU2R,8,2,--., CAU2R,8,41} }, {{CAPROBE,1,1, CAPROBE,1,2,...,CAPROBE ,1,41},{CAPROBE,2,1, CAPROBE,2,2 ,.", CAPROBE,2,41 L"., {CAPROBE,4,1, CAPROBE,4,2 ,..., CAPROBE,4,41} }}= = {{{DOSback ,1, DOSBACK,2,..., DOSback ,41MdOSLAND,1,DOSland,2,..., DOSLAND ,41},.", {DOSTEARDROP,1, DOSTEARDROP,2,--., DOSTEARdROP,41} }, { {R2Lbuffer_overflow,1, R2LBUFFER_OVERFLOW,2 ,..., R2Lbuffer_overflow,41}, {R2LPERL ,1, R2LPERL ,2,..-, R2LPERL ,41},.--, {R2LROOTKIT,1, R2LROOTKIT,2,--., R2LROOTKIT,41} }, { {U2Rftp_write,1 , U2RFTP_WRITE,2 ,---, U2RFTP_WRITE,41}, {U2Rguess_ passwd,1 , U2RGUESS_PASSWD,2,-.-, U2RGUESS_PASSWD,41},-.-, {U2RWAREZMASTER,1, U2RWAREZMASTER,2, •">U2RWAREZMASTER,41} }, {{PROBEipsweep ,1, PROBEIPSWEEP ,2,---,PROBEipsWeep,41},{PROBENMAP ,1, PROBEnmap ,2,-.-, PROBEnmap ,41},---, {PROBEsatan ,1, PROBEsatan ,2,---, probeSATAN ,41}}}= = {{{DOSback, d , DOSback , pt ,..., DOSBACK, DHSRR}, {DOSland,D , DOSland,pt ,--., DOSLAND,DHSRR}’-..’ {DOStEARDROP,D , DOSTEARDROP,PT ,---, DOSTEARDROP,DHSRR}},{ {R2LBUFFER_OVERFLOW,D , R2LBUFFER_OVERFLOW,PT,---, R2LBUFFER_OVERFLOW,DHSRR}, {R2LPERL,D , R2LPERL,PT ,---, R2LPERL,DHSRR},---, {R2LrOOTKit,d , R2Lrootkit,pt ,-.-, R2LROOTKIT,DHSRR} }, { {U2Rftp_write,d , U2RFTP_WRITE,PT ,..., U2RFTP_WRITE,DHSRR}, {U2RGUESS_PASSWD,D, U2RGUESS_PASSWD, PT ,..., U2RGUESS_PASSWD, DHSRR },.--, {U2RWAREZMASTER,D , U2RWAREZMASTER,PT ,---, U2RWAREZMASTER,DHSRR} }, {{PROBEipsweep , d , PROBEIPSWEEP, PT ,--., PROBEIPSWEEP, DHSRR}, {PROBENmap , d , PROBENMAP,PT,---, PROBENMAP,DHSRR},-.-, {PROBEsatan , d , PROBEsatan , pt ,---, SATAN, DHSRR}}}= = {{{BACKd , back pt ,..-, BACKdhsrr },{LAND d , LAND pt ,--., LANDdhsrr },---, {TEARDROP^, TEARDROP^ t ,---, TEARDROP }}, { {BUFFER_OVERFLOWZ) , BUFFER_OVERFLOWpt ,---, buffer_overflow srr }, {PERL^,PERLPr,---,PERL ;..--,;ROOTKIT ,ROOTKITr,---,rootkit ^}}, {{FTP_WRITEs , FTP_WRITEpt ,-.-, ftp_write^^}, {GUESS PASSWD ,GUESS PASSWD t,-..,GUESS PASSWD wJ,..., D PT DHSRR {WAREZMASTER^, WAREZMASTER^ T,---, WAREZMASTER SRR}}, {{IPSWEEP^, IPSWEEP^ T,---, IPSWEEP,^}, {NMAPs , NMAPPT,---, NMAP^SRR },..., {SATAN^, SATAN T,---, SATAN^SRR}}, whereCA1,1_1 = CAdoSJJ = DOSback ,1 = CA4,4,1 = CAprobe,4,1 = PROBEsatan ,1 = DOSBACK,D =BACKd ’ CA1,1,2 CADOS,1,2 DOSBACK,2 PROBESATAN,D = SATANd ’ CAn,m„ ,2 = CA4,4,2 = DOSBACK,PT =Backpt , CA1M = CA1,1,4I= CAdos,1,41 = CAprobe,4,2 = PROBEsATAn,2 = PROBEsatan,pt = SATANрт , DOSBACK,41 = DOSBACK,DHSRR =BACKdhsrr,•"’ CAn,mn,1 = CAn,mn,rmn= CA4,4,41 = CAprOBE,4,41 = PROBESaTaN,41 = PROBE = SATAN - parameters subsets SATAN, DHSRR DHSRR of the subclasses of cyberattacks. According to the set of cyberattacks parameters standards (8) will forms the set of current parameters SP , that recorded by the sensors at the time period T : q SPT = {jsP } = {spT ,SP2,...,sp; }, (13) z=1 where (z = 1, q), q - number of current parameters. For example, using the expression (13) for the particular case [13], if r = q = 41(Vi,j) considering (11), we get: SPT = {J SP} = ;SP/ ,SP2T ,...,SP4TJ = z=1 ={Dτ,PTτ,...,DHSRRτ}. Phase 2 – Identification the type of cyberattack. For comparison, current parameters which were records by sensors with standard parameters of cyberattacks introduce logic function of equivalence: I1, when x = y, E (x, У) = ^ , [0, when x ^ y. For example, at the time period T = 1 the set of parameters signatures, which were measured by ITS sensors, entering to the system (descriptions of the parameters are shown in Tables 2-5): SP1={184, tcp, telnet, SF, 1511, 2957, 0, 0, 0, 3, 0, 1, 2, 1, 0, 0, 1, 0, 0, 0, 0, 0, 1, 1, 0.00, 0.00, 0.00, 0.00, 1.00, 0.00, 0.00, 1, 3, 1.00, 0.00, 1.00, 0.67, 0.00, 0.00, 0.00, 0.00}. Categorization of cyberattacks occurred by comparing the input data SP with attacks templates (according to (12)), comparing each of given in (11) parameters using the functions of equivalence (15). As a result, the cyberattack with R2L class and buffer_overflow subclass was classified. Phase 3 – Categorization of cyberincidents. For implementation of this phase we define the set of cyberincidents I that may arise as a result of cyberattacks СA : n I = {Uli} = {I1,l2,-,In}, (i = 1, П), (16) i=1 where n – number of possible cyberincidents types. For example, according to the most common types of contemporary computer threats, according to [11] under the categories of cyberincidents will understand (Table 6). Table 6. Categories of Cyberincidents According to CERT-UA Code Category Description Definition MW Malware Defeat ITS by viruses and others malicious software One of the most common ways of infection is drive-by download - infection the users computer when visiting malicious website. Viruses: network worms (networm) is the subclass of viruses that infect computers and looking for ways to spread the network, creating their own copies; trojan programs are programs, that designed for hidden (under the guise of something else) entering the system, usually with malicious intent; rootkits are the set of programs designed to hide the fact of “presence” intruders in the system (computer); keyboard spyware (keylogger) are providing record all of the interruptions that come into the system input at the moment of pressing keys on the keyboard; advertising systems (adware) is malicious software designed to impose advertising means, as an example, blocking user actions by “popup window” that contains advertising material) IF Internet Fraud Implementation of Internet fraud Phishing attack is prompting the users to enter their authentication information (login, password, banking information) and other information by assurance of users the veracity and authenticity of false (specially created for this) network resources (including a link, which is needed to go) such as mail, websites designed for Internet banking, login page in social networks, etc; vishing is type of fraud to obtain from user during a call information that is necessary for attacker by using different methods of persuasion . One of the varieties of “social engineering” UA Unauthorized Access Unauthorized access to information resources and ITS Targeted hacking - actions aimed at violating the regular mode of operation of the system, violation of the availability of services (components), obtaining of unauthorized access to confidential information, violation of the integrity of information etc; website defacement attack it is changing the content of the main page of the website, in result at the moment of website visiting instead of the usual content displayed something else (the inscription “hacked by”, obscene or vulgar phrases / pictures, etc.) BN Botnet Bot networks The set of computers, which were infected by malicious software, resources of which (both informational and industrial) through a special command-control servers (C & C) are illegally used by hackers (ZeuS, SpyEye, Carberp, Rustock, Kelihos, Pandora, BlackEnergy) End of Table 6 DD DDoS Implementation of DDoS-attacks A distributed network attack, which through a large number of sources is intended to disrupt the availability of the service (automated system) by exhausting its computing resources MT Money Theft Money Theft Unlawful appropriation of the persons funds which implemented by hackers using the resources of cyberspace IT Identity Theft “Identity theft” Unauthorized acquisition of personal data of individuals, which allows an attacker to operate ( to sign documents, get access to resources, use the services, etc.) on its behalf (as one of the authentication mechanisms of individuals can be used the electronic digital signature) Next, using the expression (16) and data from the Table 6, if n = 7 we get: I={ Ii}={I1,I2,I3,I4,I5,I6,I7}= i=1 = {IMW,IIF,IUA,IBN,IDD,IMT,IIT} = = {MW, IF, UA, BN, DD, MT, IT}, where I1=IMW=MW,I2=IIF=IF, I4=IBN=BN,I5=IDD=DD,I6=IMT=MT, I = I = IT – categories of cyberincidents. Phase 4 – Forming the set of cyberincidents extrapolation rules. To implement this phase is necessary to form a set of basic rules R [6]: g R = {(>,} = {R1,R2,...,Rg}, (i = 1,g), (18) i=1 where g – number of basic rules. Similarly to the approach described in [17-20], based on expert evaluation (which does not require large time cost for statistical data forming) is forming a set of rules (17) that establishes connections between subclass of cyberattack CA and category of cyberincident I . Using subclasses of cyberattacks (Phase 1), the implementation of which may cause occurrence of cyberincidents (Phase 3) and considering (17) experts calculates a probability value PR ... PR (normalized from 0 to 1 or percentage) of the occurrence of cyberincident in implementing of a specific class of cyberattacks (19). PR = PRCA1I1 PRCA2I1 PRCA1I2 PRCA2I2 PRCA1In PRCA2In (19) PRCAmI1 PRCAmI2 PRCAmIn Thus, using the statistics describing empirical data of the occurrence of cyberincidents as result of cyberattacks, experts generate probability value PRCA I ... PRCA I and the corresponding set of rules R (17), which are presented in the following form: Rg = (PR^ > PRHm) ^ In, (20) where PR – is the probability threshold value at which experts believe in the emergence of cyberincident I as a result of cyberattack CA (based on analysis of statistics of cyberincidents). For example, if m = 22 (Phase 1), n = 7 (Phase 3) experts on the basis of statistics of cyberincidents domestic mobile operator for the last year (Fig. 3) are filling the matrix (19) establishing a connection between the buffer_overflow cyberattack subclass defined in Phase 2 and categories of cyberincidents that have been identified (17) in Phase 3 (Table 7). Thus, forming probabilities PRMW PRIF PRIT vbuffer _ overflow, bUuffe_ _ overflow , * * *, bbuffrr _ overflow considering the time period T , at which bufferjoverflow cyberattack was implemented. Further, based on the analysis of statistical data is set threshold probability value of cyberincident occurrence PR (with this matter the expert analyzes of the attacks that took place simultaneously and determines their differential impact for the occurrence of cyberincident). Next, for the example if PRUm = 0,15 the expression (20) can be represented as follows: R = (PRMWe _ overflow > 0,15) ^ mw ; R = (PRbfe_overflow > 0,15) ^ UA;R3 = (PRBNNe_overflow > 0,15) ^ BN. Fig.3. Statistics of Cyberincidents Presented In Categories Table 7. The Example of Assessment of the Cyberincident Probability in Implementing Cyberattack Cyberincident Cyberattack MW IF UA BN DD MT IT buffer_overflow 0,18 0,01 0,52 0,21 0,06 0,015 0,005 Because of the formed rules R1, R2 and R3 can be concluded that buffer_overflow cyberattack which is implemented at the time period may cause to occur of three types of incidents: Malware (18%), Unauthorized Access (52%) and Botnet (21%). This data is then used to determine the effect of cyberincidents to objects of protection (Phase 6). Phase 5 – Determination of protection objects. To determine protection objects we will form their set O: n O={иOi}={O1,O2,...,On},(i=1,n), (21) i=1 where n – number of protection objects. For example, as objects of protection may be the components of ITS. Thus, the input data at this phase are the categories of cyberincidents (defined by Phase 3 method) and ITS components (ITS components can be defined according to [11]). ITS is an environment in which can occur cyberincidents, typical structure of ITS according to [11, 21, 22] given in Table 8. Table 8. The set of ITS Components According to CERT-UA Code ITS component Description Definition SV Server Server equipment Computers with high performance and technical characteristics; usually designed to one or more specific services, such as email exchange, databases, IP-telephony, file storage, etc. NC NetChannel Data transferring environment Fiber optic lines, cable with type of “twisted pair” telephone cables, wireless data channels (Wi-Fi, WiMAX, Bluetooth) NH NetHardware Active network equipment and communications equipment Switches, routers, modems, wireless access points, telephony and security devices (firewalls, intrusion detection / prevention systems, etc.) WS WorkStation Automated workplaces of employees Desktops, laptops, mobile devices Next, using the expression (21) and data from the Table 8, if n = 4 we get: O={4Oi}={O1,O2,O3,O4}= i=1 {OSV,ONC ,ONH,OWS } = ( ) {SV, NC, NH, WS}, where O = O =SV, O = O =NC,O =O =NH,O =O =WS – protection 3 NH 4 WS objects (ITS components). Phase 6 – Identification of cyberincidents impact on ITS components. To determine the impact of the cyberincidents which are categorized in Phase 3, on the ITS components that are determined in Phase 5, experts are encouraged to score U impact of the cyberincident on ITS component (23). Cyberincident that having a greater impact, gets a lower score (1, 2), less influential – bigger (3, 4) [23, 24]. Table 9. Impact Assessment of Cyberincidents on the Components of ITS ITS components Assessments of cyberincidents by types MW IF UA BN DD MT IT SV 2 3 2 1 1 4 4 NC 3 4 4 2 2 4 4 NH 3 4 3 3 3 3 3 WS 1 1 1 1 1 1 1 The input data are assessing the impact of cyberincident categories on the ITS components. Thus, in case of the occurrence of three cyberincident categories the most impact exposed are such ITS components as WorkStation and Server. Phase 7 – Identifying of the most critical components of the ITS. Input data at this phase is ITS components (Phase 5). This phase is implemented in two steps: Step 1. The scoring by experts. Experts define data U ... U (23), adding in every cell one of the signs: O1I1 OmIn “important” (>) “less important” (<) and “equivalent” (=). Determining the most critical component of ITS may be made, for example, by pairwise comparisons (the main advantage is the opportunity of expert to focus on two objects at a time – this advantage is evident with increasing quantity of evaluation objects) and the number of tables should comply the number of experts. In order to determine the most critical component of ITS may be used one of the following in [25] methods, ranging, multiple comparisons, Delphi method, normalization method, vector benefits method, cluster analysis method, method of rank transformation, utility function approximation method and so on. In Table 9 each k -th expert replacing signs of the ratio on value (score) rk by the rule: 1, if a, > a,, ij * selection R is determined by: rjk = ^2, if ai = a, 3, if at < a}, where a, a – ITS components to be compared. Step 2. Coordination of the statements of experts. Then performs the coordination of matrix of each expert Rk , in result is forming reduced matrix of collective benefits [9]. Coordination can be performed by various algorithms. Table 9 used 3 point scale (<, >, =). Can be used larger point scales. In case of violation of transitivity advantages the situation when the matrix is not a ranking * R , may arise, that is not to determine benefits. Then constructed a ranking R that is closest to the group opinion. By denoting d(R,R*) the distance between R and R*, we get the request d(R,R*)min. Group KK У d(R*, Rk) = min У d(R, Rk). (25) k=1 ReR(n) k=1 Calculated score WC of each criteria as the sum rk (perhaps some other algorithm, it is important to reflect the “weight” of criteria which specified in the experts paired comparisons of criteria) and defines the place of criteria in the ranking RC . Table 10 filled on the basis of agreed estimates of experts concerning the most critical components of the ITS. Output data of this phase is the assessment of the criticality of ITS components. For example, if i = j = 4 (Phase 5) experts determine the value rk ... rk by filling the Table 11 O1O1 OO determining the most critical of ITS components. Table 10. Determination of the Most Critical ITS Components ITS components ITS components O1 O2 Oi Score, “weight” of criteria Place of criteria in the ranking O1 k rO1O1 k rO2O1 k rOiO1 WC RC O2 rOk1O2 k rO2O2 k rOiO2 WC RC O…j k rO1Oj k rO2Oj k rOO WC m R…Cn Table 11. Determination of the most Critical Of ITS Components ITS components ITS components SV NC NH WS Score, “weight” of criteria Place of criteria in the ranking SV > > > 3 1 NC < > > 5 2 NH < < > 8 3 WS < < < 9 4 Thus, we have score of the criterion according to which determining place of criteria in the ranking. Most critical in this case is ITS Server, and the least critical is WorkStation. Phase 8 – Cyberincidents degrees of danger ranking. The input data of this phase is the assessment of the criticality of ITS components (Phase 7, Table 10) and assessments the impact of cyberincidents on ITS components (Phase 6 (23)). Determining the comparative importance of possible damage, to which cyberincident can lead according to the values of each criterion (26) and their “weights” (Table 10). It is important for dispatching strategies and operational impacts. The assessment of comparative importance can be calculated using the formula: Qj = У aixij,j=1,j, (26) i=1 where x – value of i -th criteria j -th cyberincident type in Table 9; a – “weight” of i -th criteria in Table 11. When using the criteria values from the Table 11, the smaller the value Q , the more danger makes cyberincident. The calculation of standardized assessments (Table 12) of cyberincidents implements by the formula: Q j j IQ Table 12. Evaluation the Danger of Cyberincident (27) The level of danger Cyberincident Standardized assessment 1 I1 IL1 2 I2 IL n I…n IL… j In case of occurrence multiple parallel cyberincidents (probability of this is very high due to shown in Fig. 3 statistics and research), and by having a hazard assessment levels of cyberincidents, it is possible to hold the prioritization of cyberincidents in order to adequate responding to them. Output data on this phase is the assessment of risk level (criticality) of cyberincidents that arise in result of implemented attack category. For example, using the values from the Table 9 and Table 11 by the expression (26) calculate the assessment of the danger level of cyberincident (Table 13). For cyberincident MW we get: Q = 3x 2 + 5 x 3 + 8 x 3 + 9 xi = 54, UA: Q = 3x2 + 5x4 + 8x3 + 9xi = 59, BN: Q = 3x1 + 5x2 + 8x3 + 9xi = 46. Standardized assessments of cyberincidents types calculated by (27): IL = 0.34, IL2= 0.37, IL3= 0.29, is recording in the Table 13: Table 13. Evaluation the danger of Cyberincident The level of danger Cyberincident Standardized assessment 1 BN 0,29 2 MW 0,34 3 UA 0,37 Thus, we can conclude that when implementing buffer_overflow cyberattack the most danger (most critical) is Botnet cyberincident, then Malware, and at last Unauthorized Access. Thus, in this paper the method for cyberincidents network-centric monitoring was developed which by classifying of cyberattacks and comparing their parameters with standard, forming the set of basic rules and establishing of dependencies between cyberattacks subclass and cyberincidents category based on their statistical processing, identification objects of protection and expert assessment of cyberincidents impact on them, coordination of experts opinions and ranking danger degrees of cyberincidents, which allows to determine the most important objects of protection (components of ITS or cyberspace), and also to predict the categories of cyberincidents that arising because of cyberattack implementation, and their level of risk (criticality). This method and means which were formed on its basis will be useful for cyberincidents response teams of type CERT / CSIRT for efficient processing of cyberincidents (in particular dispatching) and adequate respond to them, and for units that are assigned to protect both within the ITS enterprise and within the state. This scientific work was supported by RAMECS, CCNU16A02015 and Young Scientists Association of National Aviation University (Kyiv, Ukraine). [3] Gnatyuk V., Volyanska V. Gizun A., «Review of intrusion detection systems based on honeypot technology» Ukrainian Scientific Journal of Information Security, 2012, vol. 18, issue 2, pp. 75-79. [4] Gizun A., Korchenko A., Skvortsov S., «Analysis of modern crisis management systems», Ukrainian Scientific Journal of Information Security, 2015, vol. 21, issue 1, pp. 86-99. [5] Sinyavskiy V., «Influence of the content and principles of "network-centric warfare" in the command and control processes», Science and Military Security, 2010, vol. 4, pp. 36-45. [6] The paradigm of network-centric management and its impact on the command and control processes [Electronic resource]. – Access to resources: [7] Network-centric warfare and wireless communications: [Electronic resource]. — Access to resources: http://www.meshdynamics.com/military-mesh-networks.html [8] Zatuliveter Y., «Computer basis of network-centric management, Proceedings of Russian Conference with international participation "Hardware and software in the control system, the control and measurement"», Moscow pp. 17-37, 18-20 October 2010. [9] Shershakov V., Trahtenherts E., Kamaev D., «Computer support network-centric management practices emergencies», Moscow: Lenand, 2015, p.160. [10] Gnatyuk S., Hohlachova Y., Ohrimenko A., Grebenkova A., «The theoretical basis of construction and operation of information security incident management», Ukrainian Information Security Research Journal, 2012, vol. 54, issue 1, pp. 121-126. [11] Gnatyuk S. «Cyberterrorism: development history, current trends & countermeasures», Ukrainian Scientific Journal of Information Security, 2013, vol. 19, issue 2, pp. 118129. [15] CERT-UA. Basic course of Information Security [Electronic resource]. — Access to resources: http://cert.gov.ua [16] The Law of Ukraine «Information security in telecommunication systems»: № 80/94-BP July 5, 1994, Parliament of Ukraine, vol. 31, p. 286. [17] Karpinski M., Korchenko А., Akhmetova S., «The method of developmentof basic detection rules for intrusion detection systems», Ukrainian Information Security Research Journal, 2015, vol. 17, issue 4, pp. 312324. [18] Gizun A., Gnatyuk V., Suprun О., «Formalized model of construction heuristic rules to detect incidents», Journal of Engineering Academy of Ukraine, 2015. vol. 1, pp. 110115. [19] Korchenko А., Gizun A., Volyanska V., Gavrylenko О., «Heuristic rules based on logical & linguistic connection to detect and identify information security intruders», Ukrainian Information Security Research Journal, 2013, vol. 60, issue 3, pp. 251-257. [20] Gizun A., Gnatyuk V., Balyk N., Falat P., «Approaches to Improve the Activity of Computer Incident Response Teams», Proceedings of the 2015 IEEE 8th International Conference on «Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications», (IDAACS’2015), Warsaw, Poland, September 24-26, 2015, vol. 1, pp. 442-447. [25] Gornitska D., Volyanska V., Korchenko А. «Determining factors of importance for expert evaluation in the field of information security», Ukrainian Information Security Research Journal, 2012, vol.54, issue 1, pp. 108-121. Authors’ Profiles Zhengbing Hu: PhD, Associate Professor of School of Educational Information Technology, Central China Normal University, M.Sc. (2002), Ph.D. (2006) from the National Technical University of Ukraine «Igor Sikorsky Kyiv Polytechnic Institute». Postdoc (2008), Huazhong University of Science and Technology, China. Honorary Associate Researcher (2012), Hong Kong University, Hong Kong. Major research interests: Computer Science and Technology Applications, Artificial Intelligence, Network Security, Communications, Data Processing, Cloud Computing, Education Technology. Viktor Gnatyuk: PhD Student (20122015), Assistant Teacher (from 2013). In 2012 he received MSc degree in Economic Cybernetic from Khmelnitsky National University (Khmelnitsky, Ukraine). He is currently working at NAU in Telecommunication Systems Academic Department. Research interests: Computer Viktoriia Sydorenko: PhD Student (2013-2016), Assistant Teacher (from Information Infrastructure Protection. Technology. Roman Odarchenko: PhD, Associate Professor of Telecommunication systems academic department in NAU. M.Sc. (2010), Ph.D. (2013) from the NAU, teacher in Kyiv College of Communication. Major research interests: Network Security, Communications, Data Processing, Sensor networks, Computer networks, Education Sergiy Gnatyuk: PhD, Associate Professor. In 2007 he received MSc degree in information security from National Aviation University (NAU, Kyiv, Ukraine). He received PhD in Eng degree in information security (quantum cryptography) from NAU in 2011. He is currently working at NAU in Academic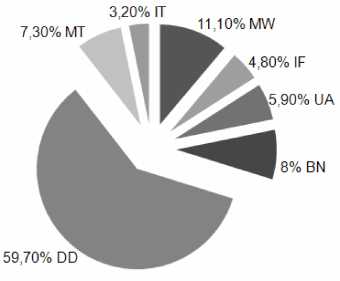
U=
UO1I1
UO2I1
UO1I2
UO2I2
UO1In
UO2In
(23)
U
OmI1
U
OmI2
U
mn
for example, if m=4 (phase 5), n = 7 (phase 3) experts fill the Table 9 establishing the connection between ITS component and category of cyberincident.
V. Conclusions





Список литературы Method for Cyberincidents Network-Centric Monitoring in Critical Information Infrastructure
- Gnatyuk V., «Analysis of "incident" definitions and its interpretation in cyberspace» Ukrainian Scientific Journal of Information Security, 2013, vol. 19, issue 3, pp. 175-180.
- ISO/IEC 27035:2011 — Information technology — Security techniques — Information security incident management, 2011., p. 69.
- Gnatyuk V., Volyanska V. Gizun A., «Review of intrusion detection systems based on honeypot technology» Ukrainian Scientific Journal of Information Security, 2012, vol. 18, issue 2, pp. 75-79.
- Gizun A., Korchenko A., Skvortsov S., «Analysis of modern crisis management systems», Ukrainian Scientific Journal of Information Security, 2015, vol. 21, issue 1, pp. 86-99.
- Sinyavskiy V., «Influence of the content and principles of "network-centric warfare" in the command and control processes», Science and Military Security, 2010, vol. 4, pp. 36-45.
- The paradigm of network-centric management and its impact on the command and control processes [Electronic resource]. – Access to resources: http://agat.by/pres/statia%20nayka-3.pdf.
- Network-centric warfare and wireless communications: [Electronic resource]. — Access to resources: http://www.meshdynamics.com/military-mesh-networks.html
- Zatuliveter Y., «Computer basis of network-centric management, Proceedings of Russian Conference with international participation "Hardware and software in the control system, the control and measurement"», Moscow pp. 17-37, 18-20 October 2010.
- Shershakov V., Trahtenherts E., Kamaev D., «Computer support network-centric management practices emergencies», Moscow: Lenand, 2015, p.160.
- Gnatyuk S., Hohlachova Y., Ohrimenko A., Grebenkova A., «The theoretical basis of construction and operation of information security incident management», Ukrainian Information Security Research Journal, 2012, vol. 54, issue 1, pp. 121-126.
- Gnatyuk S. «Cyberterrorism: development history, current trends & countermeasures», Ukrainian Scientific Journal of Information Security, 2013, vol. 19, issue 2, pp. 118-129.
- Grischuk R., Okhrimchuk V., Akhtyrtseva V., «The sources of primary data for the development potentially dangerous patterns of cyber-attacks», Ukrainian Information Security Research Journal, 2016. vol. 18, issue 1, pp. 21-29.
- KDD CUP99 [Electronic resource]. — Access to resources: https://kdd.ics.uci.edu/databases/kddcup99/task.html
- Official site Common Attack Pattern Enumeration and Classification [Electronic resource]. — Access to resources: https://capec.mitre.org
- CERT-UA. Basic course of Information Security [Electronic resource]. — Access to resources: http://cert.gov.ua
- The Law of Ukraine «Information security in telecommunication systems»: № 80/94-BP July 5, 1994, Parliament of Ukraine, vol. 31, p. 286.
- Karpinski M., Korchenko А., Akhmetova S., «The method of developmentof basic detection rules for intrusion detection systems», Ukrainian Information Security Research Journal, 2015, vol. 17, issue 4, pp. 312-324.
- Gizun A., Gnatyuk V., Suprun О., «Formalized model of construction heuristic rules to detect incidents», Journal of Engineering Academy of Ukraine, 2015. vol. 1, pp. 110-115.
- Korchenko А., Gizun A., Volyanska V., Gavrylenko О., «Heuristic rules based on logical & linguistic connection to detect and identify information security intruders», Ukrainian Information Security Research Journal, 2013, vol. 60, issue 3, pp. 251-257.
- Gizun A., Gnatyuk V., Balyk N., Falat P., «Approaches to Improve the Activity of Computer Incident Response Teams», Proceedings of the 2015 IEEE 8th International Conference on «Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications», (IDAACS'2015), Warsaw, Poland, September 24-26, 2015, vol. 1, pp. 442-447.
- Zhengbing Hu, Vadym Mukhin, Heorhii Loutskii, Yaroslav Kornaga "Stochastic RA-Network for the Nodes Functioning Analysis in the Distributed Computer Systems". International Journal of Computer Network and Information Security(IJCNIS), Vol. 8, No. 6, June 2016, PP.1-8, DOI: 10.5815/ijcnis.2016.06.01
- Rasmi M., Al-Qerem A. PNFE: «A proposal approach for proactive network forensics evidence analysis to resolve cyber crimes». International Journal of Computer Network and Information Security (IJCNIS), Vol. 7, No. 2, January 2015, PP.25-32. DOI: 10.5815/ijcnis.2015.02.03.
- Karuppanchetty C., Edmonds W., Kim S.-il, Nwanze N. Artificially augmented training for anomaly-based network intrusion detection systems. International Journal of Computer Network and Information Security (IJCNIS), Vol. 7, No. 10, September 2015, PP. 1-14. DOI: 10.5815/ijcnis.2015.10.01
- Govindarajan M. Hybrid Intrusion Detection Using Ensemble of Classification Methods. International Journal of Computer Network and Information Security (IJCNIS), Vol. 6, No. 2, January 2014, PP.45-53, DOI: 10.5815/ijcnis.2014.02.07
- Gornitska D., Volyanska V., Korchenko А. «Determining factors of importance for expert evaluation in the field of information security», Ukrainian Information Security Research Journal, 2012, vol.54, issue 1, pp. 108-121.


