Minimization of Power Consumption in Mobile Adhoc Networks
Автор: B.Ruxanayasmin, B.Ananda Krishna, T.Subhashini
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 2 vol.6, 2014 года.
Бесплатный доступ
An ad hoc network is a mobile wireless network that has no fixed access point or centralized infrastructure. Each node in the network functions as a mobile router of data packets for other nodes and should maintain the network routes for long standing which is not possible due to limited battery source. Also, due to node mobility, link failures in such networks are very frequent and render certain standard protocols inefficient resulting in wastage of power and loss in throughput. The power consumption is an important issue with the goal to maintain the network lives for long by consuming less power. The power consumption can be achieved by modifying algorithms such as cryptographic algorithms,Routing algorithms, Multicast Algorithms, Energy Efficient Algorithms and Power Consumption Techniques in High Performance Computing, Compression and decompression algorithms, minimizing link failure algorithms, and by power control algorithms. In this work, we have proposed a new algorithm for minimization of power consumption in Ad hoc networks. The performance of the proposed model is analyzed and it is observed that, information could be sent with security consuminglesscomputational power, thereby increasing the battery life.
MANET, Power consumption, Security, Compression, Decompression
Короткий адрес: https://sciup.org/15011276
IDR: 15011276
Текст научной статьи Minimization of Power Consumption in Mobile Adhoc Networks
Published Online January 2014 in MECS
An ad hoc network , or MANET (Mobile Ad hoc Network), is a network composed only of nodes, with no Access Point. Messages are exchanged and relayed between nodes. In fact, an ad hoc network has the capability of making communications possible even between two nodes that are not in direct transmission range with each other: packets to be exchanged between these two nodes are forwarded by intermediate nodes, using a routing algorithm. Hence, a MANET may spread over a larger distance, provided that its ends are interconnected by a chain of links between nodes (also called routers in this architecture). These devices are usually deployed in large number and have limited resources in terms of battery energy, bandwidth, memory, and computational power [1].
A secure communication among nodes is necessary to allow the integrity of the delivered packets. Nodes must be able to identify themselves to each other. A node must give their identification and associated credentials to another node to allow authentication. This information sent across the network must be well protected to ensure the integrity of delivered information. Each node must be able to validate the information received so as to verify if the sender is the one it claimed to be. If the identity of a node is revealed to an attacker, the attacker can use it to impersonate a legitimate node or can launch a denial of service attacks by keeping a node busy by sending a lot of dumb messages to that node, yields to increase in overhead which consumes more power. Therefore, limited battery life and security are main constraints and lot of research on security issues and power consumption has been carrying out. Many authors have proposed different solutions to minimize power consumption and some are listed below.
-
A. Minimizing power by reducing link failures B. Specially designed power control techniques
-
C. By modifying cryptographic algorithms
-
D. Data compression techniques
Among many techniques, the authors Ruxanayasmin, et al, proposed LZW compression technique to minimize the power consumption [2]. Lempel-Ziv-Welch (LZW) compression algorithm is fast, simple to apply and works best for files containing lots of repetitive data. LZW algorithm is efficient because the output resembles numerical data and also it doesn’t need to pass the string table to the decompression code. Due to compression, the number of bits can be reduced to maximum extend so that the need of memory and bandwidth are very less. Also, the compressed text resembles a scramble message and an attacker in middle cannot able to understand. Therefore, the data compression not only reduces the size of the original text, but also gives data security. The work [2] is extended by including security techniques along with compression.
Section-II describes the related work on power consumption techniques proposed by different authors and Analysis of existing algorithms is discussed in section-III.Section-IV describes the Problem statement withoverview of proposed algorithm. Implementation and simulation results are observed in section-Vandsection-VI concludes the work with future enhancement.
-
II. RELATED WORK
The authors Subirkumar, et al, [1] proposed the advantages and disadvantages of MANETS and recent developments with applications in ad hoc networks.
The authors Ravindra.E, etal, [3] proposed the mechanism of link failure prediction. This performs local route repair if the signal strength is below the threshold value. The drawback is route rebuilding time. The future work is to develop an algorithm to reduce the route rebuilding time so that real time voice and data can be transmitted in MANET.
The authors Mr.S.A.Jain, et al, [4] proposed different mechanisms for the link failure detection by using alternate route finding from the nearer of the faulty node resulting into improvement in throughput, and end to end delay parameters. Thus performance of MANET will be significantly increased, along with TCP throughput.
The authors DiaaSalama, et al, [5] proposed energy consumption of different common symmetric key encryptions on handheld devices. It is found that after only 600 encryptions of a 5 MB file using Triple-DES the remaining battery power is 45% and subsequent encryptions are not possible as the battery dies rapidly.
The authors Guoliang Xing,et al, [6] proposednew algorithm based on minimum Steiner tree (ISTH). In this, they explained the nodes and transmission power at ideal and sleep nodes. And discussed the comparison of energy in MPCP (Minimum Power Configuration Protocol) and min-power routing. Future work is to maximize system life time, reduce network contention, and estimate data rates.
The author AbdellahIdrissi, et al, [7] proposed an optimization method under constraints for minimizing the power batteries consumption when sending messages from a source device to a destination device. The method presented is based on the adaptation of the Dijkstra’s algorithm. Its approach is to assist users to control and regulate batteries capacities in order to minimize the consumption.
The authors P.Balakumar, et al, [8] proposed an efficient routing protocol called Power efficient Preferred Link-based algorithm (PPL). It shows better than other algorithms in energy-efficient and connection maintenance.
-
III. ANALYSIS OF EXISTING ALGORITHMS
-
A. Dijkstra’s algorithm
MANET assists the users to efficiently use their devices in order to minimize the battery power consumption. The communication between two devices is not necessarily symmetric, i.e., given two devices ‘i’ and ‘j’. The device ‘i’ can send a message to device ‘j’, but device ‘j’ cannot necessarily send any message to device ‘i’. Since ‘i’ and ‘j’ don’t necessarily have the same energy. A fixed amount of data must be sent from a source device to a destination device to determine power. A new algorithm named as Dijkstra’s algorithm proposed by AbdellahIdrissi etal,for energy management in mobile ad hoc network is designed to rectify this problem [7]. It finds the minimum of energy to consume when sending a message from the device ‘s’ to the device ‘d’ in the mobile ad hoc network. The algorithm finds all shortest paths from the source to all destinations. Initially all devices are untreated, and the algorithm ends once a device is treated at destination, and moved from the untreated set to the treated set.
-
B. Power control algorithm
The wireless channel is characterized by signal strength attenuating with distance from the transmitter [10]. The commonly used power-attenuation model for decay of the signal is represented by the non-linear formula
P r (d) = P t / da (1)
Where, P T is the transmitted signal strength.
dα is the distance from the transmitter.
P R (d) is the amplitude of the received signal at the distance‘d’.
In ‘dα ‘ α is the path loss factor whose value typically between 2 and 6.
Nodes can correctly receive a packet if the strength of the packet at that node is above a certain threshold called Receive threshold. If the distance between the transmitter and receiver is such that the signal strength is above this threshold, the receiver is said to be within the transmission range of the sender. There is a lower threshold called carrier sense threshold, up to which the received signal strength is enough for the receiver to detect the packet sent, but the receiver is unable to receive it correctly. All received signals that fall between these thresholds cause the channel to be sensed busy and contribute to the interference at the receiver.
Energy is a source and non-renewable in wireless ad hoc network, energy- efficient protocol design is a key concern. The design and performance analysis of such protocols require proper modeling for the measurement of energy consumption. The authors presented some results measuring energy consumption of various network interferences. The four possible energy consumption states are identified as: transmit, receive, idle and sleep. The first two states are when the node is transmitting and receiving the packets respectively, the idle state is when node is waiting for any packet transfers, and the sleep state is a very low power state where the node can neither receive nor transmit.
The cost associated with each packet at a node is represented as the total of incremental cost ‘m’ proportional to the packet size and a fixed cost ‘b’ associated with channel acquisition.
Cost= m× size +b (2)
Thus, the cost of a broadcast packet will be of the form
Cost broadcast = m send
× size +b
send+∑п∈s (m recv × size +brecv)
Where S= set of nodes with in transmission range of transmitting nodes msend, b send = incremental and fixed cost for sending the broadcast packet mrecev, b recev= incremental and fixed cost for received the broadcast packet.
Similarly the cost of point-to-point traffic at the sender and receiver while considering presence of RTS / CTS control messages in IEEE 802.11 based networks can be respectively represented by the following equation:
D. Multicast routing algorithm
In MANET especially the problem will occur in terms of connection maintenance mechanism and power consumption. Here P.Balakumar, et al, proposed an efficient routing protocol called Power-efficient Preferred Link-based algorithm (PPL) [8]. The performance metric used to evaluate is energy-efficient and connection maintenance. The multicast support to establish communication from one or more source nodes to multiple receiving nodes. Current multicast routing protocols for mobile ad hoc networks can be classified into two categories, tree-based protocol and mesh-based protocol as shown in table1.
Cost unicast –sender = b sendctl + b recvctl + m
send
size +b sen d + b recvct l
Cost
unicast – receiver
= b
recvctl + b sendctl + m recev
TABLE I. COMPARISON OF MULTICAST ROUTING ALGORITHM
|
Categories |
Delivery ratio |
Control overhead |
Energy consumption |
Nodes |
|
Tree-based protocol |
Low |
Low |
Low |
Fixed |
|
Meshbased protocol |
High |
High |
High |
Changed |
size + b recev + b sen d ct l
Where b sendctl = fixed cost for sending a control packet b recvctl = fixed cost for receiving a control packet
Beside this model for energy costs, it also shown that the energy consumed by an idle network interface dominates the total energy consumption (about a magnitude more than sleep mode).The energy spend at each node due to a flow can be calculated in a simple way.
-
C. Minimizing power consumption by the link failure algorithm
In MANEThigh speed of mobility or continuously changing network topology causes link breakage and invalidation of end-to-end route. The link failure will indicated by the absence of hello message. To reduce the link failure the messages are retransmitted. By retransmitting the messages the routes or system consume more energy and its system life time will be less. Therefore radio power consumption must be minimized to extend system lifetime. Under radio power cost the IEEE802.11 network card has the radio power cost of T X =1400, Rx=1000, idle=830, sleeping=120. Transmission consumes more power than receiver and sleep consumes much less power than idle. The idle power of non-communicating nodes is reduced by sending it into the sleep mode [6]. To save the power there are three types:
-
• Topology control reduces node transmission power.
-
• Minimum power routing reduces packet transmission power.
-
• Sleep management reduces idle power through duty cycle.
None of above scheme minimizes both idle and transmission power.
In multicast routing algorithm the authors proposed an efficient routing protocol called power-efficient preferred link-based algorithm (PPL). The performance metric used to evaluate is energy-efficient and connection maintenance and also discuss the issues of multicast routing protocols in MANET is shown in table 2. In this PPL, the authors compared the Bandwidth Efficient Multicast Routing Protocol (BEMRP) and Multicast Incremental Power algorithm (MIP) and PPL. The BEMRP didn’t focus on power efficiency, but for MIP and PPL when the group size is 10, PPL is less power-efficient than MIP.
TABLE II. ISSUES OF MULTICAST ROUTING PROTOCOLS IN MANET
|
Robustness |
High packet delivery ratio |
|
Power management |
Having limited battery by minimizing the number of packet transmissions |
|
Efficiency |
Total number of data packets received by the receivers and the total number of (data and control) packets transmitted in the network |
|
Control overhead |
It keeps minimum overheads |
-
IV. PROBLEM STATEMENT AND OVERVIEW OF PROPOSED ALGORITHM
The main objective of this work is to implement a novel scheme to eliminate the redundant hardware as well as the redundant transformed data which reduces system complexity, memory, bandwidth and power. Also, a secure communication among nodes is necessary to allow the integrity of the delivered packets. To achieve this, we proposed a novel technique which is simple and easy to implement is shown in the Fig.1.
Key 128
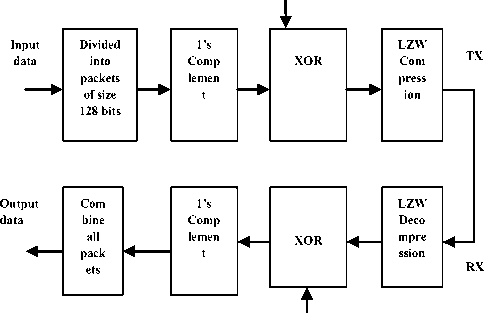
Figure1: Block Diagram Key 128 work
The proposed work is the combination of cryptography and compression algorithms. In the first stage, the incoming bit stream is divided into packets of size 128 bits each, and performs one’s complement on the bits. The one’s complemented data is XORed with secret key of 128 bit size. The encrypted text is compressed using LZW algorithm and transmitted. At receiver, the reverse operation is performed to get back the original data. By implementing this algorithm, we can
-
• Protect the information from attackers
-
• Reduce the memory usage and transmission bandwidth
-
• Transmitting less number of bits consumes less power
The Fig.2 shows the flowchart of the proposed work, in which simple cryptographic algorithms are combined with LZW algorithm [11] [12] and named as Modified LZW (MLZW) algorithm. Our intention is to achieve security by using simple algorithms that involve small inherent delays rather than resorting to complex algorithms, which occupy considerable memory and delays.
A quick examination of the algorithm shows that LZW is always trying to output codes for strings that are already known. And each time a new code is output, anew string is added to the string table.
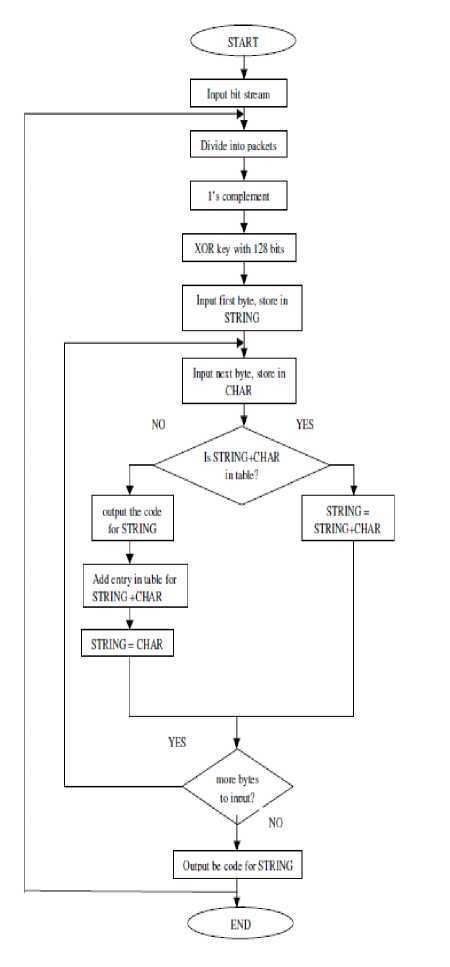
Figure 2: Compression Flowchart
The decompression algorithm [11] [12] needs to be able to take the stream of codes output from the compression algorithm, and use them to exactly recreate the input stream as shown in Fig.3. One reason for the efficiency of the LZW algorithm is that it does not need to pass the string table to the decompression code. The table can be built exactly as it was during compression, using the input stream as data. This is possible because the compression algorithm always outputs the STRING and CHARACTER components of a code before it uses it in the output stream. This means that the compressed data is not burdened with carrying a large string translation table. After decompression, the data is decrypted with secret key and perform one’s complement yields the original data.
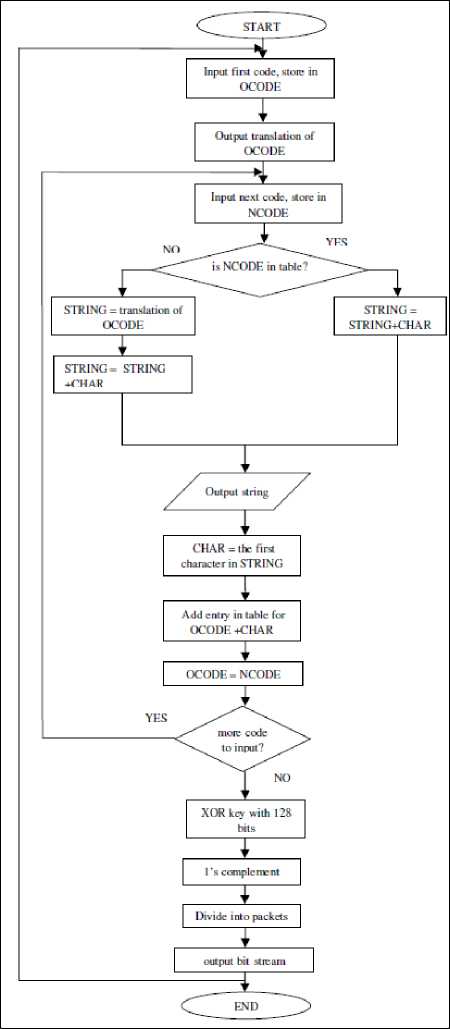
Figure 3: Decompression Flowchart
-
V .IMPLEMENTATION AND SIMULATIONRESULTS
In order to evaluate the network performance of the proposed work, the Ad hoc Network is simulated using Global Mobile Information System Simulation (GloMoSim). It is a scalable simulation environment for large wireless network systems are uses a parallel discrete_ event simulation capability provided by C-based Parallel Simulation Environment for Complex System (PARSEC). The proposed method was simulated considering the following parameters as shown in table 3.
TABLE III. SIMULATION PARAMETERS
|
Parameter |
Value |
|
Simulation area |
2000 X 2000 |
|
Number of Nodes |
30 |
|
MAC Protocol |
802.11 |
|
Transport layer |
UDP and TCP |
|
Traffic Generator |
CBR |
|
Mobility |
Random way point |
|
Node placement |
Random |
|
Routing Protocol |
AODV |
|
Simulation time |
500s |
|
Bandwidth |
2 Mbps |
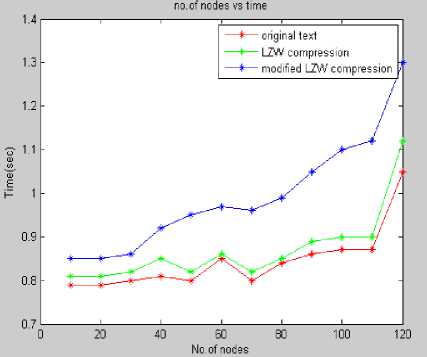
Figure 4: Numbers of Nodes vs. Time
Fig.4shows, the numbers of nodes through which the text is sent is plotted in the x- axis, where as time taken (‘seconds’) to transmit the specified data from the source node to destination node is plotted in the y-axis. It is observed that as the number of nodes increases, the time taken to transmit data packets is high in the case when the compression technique is not used. With the implementation of LZW compression algorithm, it is observed that the time taken to transmit data packets is much less.The MLZW algorithm requires little bit more time compared to LZW algorithm. This is because of encryption-decryption process which is done before compression. Therefore the Fig.4 concludes that by using the LZW and MLZW compression algorithms, the transmission delay can be minimized.
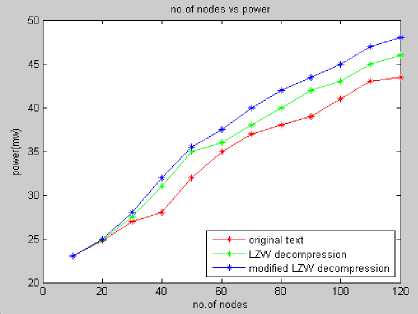
Figure 5: Number of Nodes vs. power
Fig.5shows, the number of nodes through which the text data is transmitted is plotted in the x-axis, where as power consumed (in ‘MilliWatts’) in transmitting the specified data is plotted in the y-axis. Different data packets, of different sizes are sent through the different nodes in the network. The power consumed for transmitting the data from the source to destination is noted down. It is observed that when the original data bits are transmitted without any compression, it requires more power. By using LZW and MLZW algorithms, the power required to transmit the data is less.
It is observed from the result analysis, after implementing the LZW and MLZW compression, data could be sent with reduced power consumption without any loss of data. This in turn helps in reducing the battery consumption, thereby increasing battery life along with information security.
-
VI . CONCLUSION AND FUTURE WORK
In this paper, MLZW data compression algorithm which is an efficient algorithm for compression with data security implemented successfullyusing GLOMOSIM a simulator for wireless networks. Using this compression technique, any text or document file can be compressed to a maximum of one-third of its original size without any loss of data and the performance of the algorithm is analyzed before and after compression. In this, we had considered the data compression to improve the battery life by transmitting compressed data to consume low power. In future, other attributes in this limited battery life can be addressed, so that the Quality of service in Mobile Ad hoc Networks can be improved. In the future, low power image and video compression techniques are need to be design aiming to increase the battery life and strong cryptographic algorithms need to be implement.
Список литературы Minimization of Power Consumption in Mobile Adhoc Networks
- Subirkumarsharkar, T.G.Basavaraju, C.Puttamadappa, “Ad hoc mobile wireless networks, Principles, protocols and applications”, Auerbach PublicationsBoston, MA, USA?2007.
- B.Ruxanayasmin, B.Ananda Krishna and T.Subhashini, “Implementation of Data Compression Techniques in Mobile Ad hoc Networks”, International Journal of Computer Applications, Volume 80, No. 08, Oct.2013.
- Ravindra .E, VinayaDatt V Kohir and V. D Mytri, “A Local Route Repair Algorithm Based On Link Failure Prediction In Mobile Ad Hoc Network”, World Journal of Science and Technology 2011.
- Mr.S.A.Jain and MsAruna.A, Kadam, “A Study of Congestion Control Mechanism Using Link Failure Detection in MANET”, International Journal of Engineering Research and Applications.
- DiaaSalama, HatemAbdual Kader, and MohiyHadhoud, “Studying the effects of Most Common Encryption Algorithms”, International Arab Journal of e-Technology, Vol. 2, No. 1, January 2011.
- Guoliang Xing,Chenyang Lu, Ying Zhang, Qingfeng Huang, Robert Pless, “Minimum Power Configuration in Wireless Sensor Networks”, Washington University in St. Louis Palo Alto Research Center (PARC).
- AbdellahIdrissi, “How to minimize the energy consumption in Mobile Ad hoc Networks”, International Journal of Artificial Intelligence & Applications (IJAIA), Vol.3, No.2, March 2012.
- P.Balakumar, Dr.M.Rajani, “Multicast Algorithm for Mobile Ad Hoc Network Increasing Power-Efficient”, International Journal of Advanced Research in Computer Science and Software Engineering Volume 2, Issue 2, February 2012.
- B.Ruxanayasmin, Dr. B.Ananda Krishna, “Minimization of power consumption in MANETs”, International journal of engineering research and technology (IJERT), PP.31-35, 2013.
- Geraud Allard, Pascale Minet, Dang-Quan Nguyen, and NirishaShrestha, “Evaluation of the Energy Consumption in MANET”, Institute national de recherché en informatique et en automatique, N 5851, FEBRUARY 2006.
- Steven W. Smith, “The Scientist and Engineer’s Guide to Digital Signal Processing”, Chapter 27 – Data Compression.
- Ziv J. and Lempel A., "A Universal Algorithm for Sequential Data Compression", IEEE Transactions on Information Theory, May 1977.


