Mitigating Technical Challenges via Redesigning Campus Network for Greater Efficiency, Scalability and Robustness: A Logical View
Автор: A.A. Ojugo, A.O. Eboka
Журнал: International Journal of Modern Education and Computer Science @ijmecs
Статья в выпуске: 6 vol.12, 2020 года.
Бесплатный доступ
Data transfer over the Internet comes with its range of challenges and associated prospects as a major milestone in the convergence of information and communication technology (ICT). Campus network implemented on IP-telephony defines a range of convergence technologies and applications that refers to a multi-service network that allows integration of data, audio, voice, and video solutions onto a converged infrastructure so that data can be transported via the use of open-source applications, protocols, hardware, and software. The study adopts the Federal College of Education Technical Asaba. It is observed that some issues in its implementation include packet loss, jitters, and latency. Jitters and packet loss can be curbed via an increased bandwidth allocation; while latency is minimized via constant upgrade in network infrastructure to increase speed. Overall, the proposed network seeks to provide its users with mobility, resilience, economy, flexibility, and productivity. Its results recommends that organizations wishing to harness its potentials should join forums and user-groups that will constantly update their knowledge in a bid to help them improve the efficiency and effectiveness of their infrastructure implementation.
Telephony, security, jitters, packet loss, resilience, redundancy
Короткий адрес: https://sciup.org/15017609
IDR: 15017609 | DOI: 10.5815/ijmecs.2020.06.03
Текст научной статьи Mitigating Technical Challenges via Redesigning Campus Network for Greater Efficiency, Scalability and Robustness: A Logical View
The advent of the Internet has continued to advance trends in the field of informatics and communication systems as adversaries have continued to seek breaches to nullify efforts made towards secure data sharing, improved network security, non-repudiation amongst others features. These feats have since become imperative goals as well as accompanying tools in data communications. The benefits of the information and communication technology in our society today, is quite tremendous; And, has arguably, become the largest engineered system [1, 2]. Its benefits cannot be over-estimated and over-emphasized, ranging from the great ease in effective communication systems to improved transactions at ever-increasing unprecedented speed, accuracy, portability, reliability, manageability, mobility and versatility [3, 4, 5, 6].
Graphs have since become the dominant life-form of many tasks and events in today’s society. Graphs seeks to advance the study of connectionist systems, its corresponding applications and measurement of features and parameters that have made it stood out alongside having been successfully applied to many disciplines [7, 8, 9]. In analyzing graphs (or networks), we seek feats that depending on the nature of the task in hand, raises new questions such as: (a) what feats are required for a performance threshold that yields great perturbations in the network, (b) what and which behaviors are likely to change and with such change, can impact on both local feats for a node with resultant global pattern or may likely emerge as a global paths, and (c) are there somewhat boundaries that should or must be set for such feats to occur [10, 11, 12, 13].
Networks have today been seen in our society, to effectively and efficiently aid communication (systems). They have since become a critical key factor to aid individual and organizational successes irrespective of their area of interest. Networks have proven successful in lieu of the impression they seek to create [14]. A network is a collection of autonomous computing devices connected together irrespective of the medium for the purpose of sharing resources that may include files, audio, voice, video, software/hardware resources [15, 16, 17, 18, 19, 20, 21].
Networks differ in forms and sizes from a unit or department within an organization – to cities and even different parts of the world. These forms of networks have proven to be very helpful, giving the organizations that effectively utilize them a strategic advantage in the competitive environment they find themselves. It is hoped that with a proper articulation of the needs of the various stakeholders, an efficient and cost-effective, intelligent, scalable and robust network will be the result of this study. This will in turn yield as its secondary deliverable, solutions to other concerns and issues that will be raised therein.
-
A. Internetworking: Panacea for Effective Communication
The birth of 3G-telecommunications has brought about use of interactive services, originally made possible via PSTN (public switched telephone network) so that transfer is now expansive (over long distances) without video interactions. The advent of IP reinvents communications via new technologies, allowing users to exchange data via telephony that has fast gained wide acceptance as open-source solutions to users. It also opens new functionalities for markets that previously required expensive PBXs [46]. Organizations that adopt network services are positioned for resource sharing. A robust network helps advance and automate the daily operational activities of such an organization. Thus, networks are designed to meet specific user needs [2, 20, 21].
-
B. Converged Network and Internet
The foundations of a converged network is in its capabilities and tools that allows for user flexibility, cost effectiveness and secure data transfer services (in combination of data, voice and video) packets across the same transmission links via the same switching, routing and gateway platforms. Thus, the converged-network is more secure, more fault tolerable, flexible, scalable, resilient and with easy manageability of resources [22, 23, 24, 25, 26]. For its applications, it employs an intelligent network within that ensures data transfer service quality, availability, reliability and security [27]. With the proliferation of electronic systems on every frontier, access becomes increasingly bothersome to have users tethered with wires. Thus, the need for wireless devices whose merits include: low-cost deployment, broadcast the same data to many locations simultaneously, deployment ease in hostile environ, and mobile communication. However, its demerits include lesser data rates, lesser reusable frequencies, and they are more susceptibility to interference [27]. IP telephony is the process that uses signal technology built on Open IP-standards to provide users with end-to-end communication / data transfer (file, data, voice and video) – to aid data transfer services for public carrier networks and Internet users in general with an inter-operable networks [28].
-
[29] IP telephony involves large family of communication standards to deliver voice and video services via open packet network and uses the H.323 protocol to setup, control and manage sessions. The many benefits of IP-network as easily deployed services over legacy PSTN includes: (a) It allows call services to be located anywhere on network and use packet networks rather than TDM, (b) allows service delivery so that dual cabling and network equipment for PBX or IP-PBX connections is not required, (c) carry traffic across various areas and various vendors across various countries – interfacing a variety of Internet and Telephone technologies more flexibly, with greater benefits at reduced cost of implementation and operation. Thus, a converged network helps extend capabilities of such an intelligent IP network over or into a PSTN network (when built to use underlying network) protocols and are based on server or network appliance [30, 31].
-
C. Benefits of the Converged Network
The benefits of converged intelligent network are derived from its fundamental capabilities to provide these advantages:
-
1. Economy – The advent of the Internet has birthed effective data sharing. It has mitigated challenges experienced with the traditional public switched telephone network (PSTN), which employed expensive legacy systems as connecting elements, apps and technologies like DS1/DS0 line cards, trunk cards and digital signalling technologies. Conversely, the advent of the Internet has and continues to advance the use of IP networks allow users to build data services via Ethernet economics and Moor’s law for rapid advances in computing performance. A merit of IP-network is its cost in connecting enterprise PBX system to PSTN via ports, cards and circuits. Thus, cost is lesser to provide connections to other sites and to other apps [24].
-
2. Flexibility – PSTN element/app(s) are mostly proprietary, monolithic and restrictive. Whereas IP network connections are made from virtual reach with resources distributed on demand to anywhere needed, and economies are gained via centralized gateway and server resources. Use of many types of media and applications to be brought together to facilitate communication. It supports broadband voice, front and back office integration and apps, outsourcing operation, mobility, centralised management, telecommuting, desktop integration, moves/adds/changes, automation and enterprise directories. It takes advantage of a plethora of emerging web services such as instant messaging, presence and mobility [26].
-
3. Security – Achieving a higher degree of security for secure data transfer that is vastly superior over legacy technologies; while deploying and integrating wireless LAN apps, video surveillance, IP video on demand, streaming and rich media conferencing applications [24, 25].
-
4. Resilience - With business continuity and disaster recovery high, resiliency of connectivity and abilities provided by IP network keeps an organization connected make it an ideal candidate for survivable services. Its redundancy is built into intelligent layer technologies and apps. Clustering and hot standby technologies, fault tolerant storage technologies like RAID, dual power supply are now common. IP offers superior failover, self-healing and redundant abilities that are easy to deploy, open-standards based, and supports an organization's communication needs via feats of reliability, availability and superior alternatives than PSTN [25, 26].
-
5. Productivity – Its focus, shifts from cost savings to enabling users become more productive with apps to help accomplish higher quality communications more quickly and easily, has yielded a network of phone apps that uses any existing web or enterprise database on an IP network. Thus, end-users can take advantage of web innovations, enterprise directories, e-mails, voice mail, fax, and general tools for programming communication rules. Voice recognition and soft-phone support via user desktops are added to IP-communications environment. While, some of these feats exist in legacy PSTN, they are more expensive, less scalable, and more difficult to deploy [32].
-
D. Rationale of The Study
The study seeks connectivity of systems to aid effective and efficient resource sharing. The advent of computer networks have ushered in better and unlimited opportunities for resource sharing and collaboration amongst individuals, professionals in different fields and organizations both locally and globally – spanning across industrial processes to academic research. This study seeks to design an intelligent, scalable and robust network model that will ultimately improve communication and record management abilities for the management, staff and students of Federal College of Education (Technical), Asaba. It hopes to achieve with the following objectives:
1. Identify the requirement needs of all stakeholders therein.
2. Analyze the existing network with a view to identifying the initial condition of the network.
3. Determine the physical architecture of the existing network
4. Determine its inherent limitations, bottlenecks and demerits
5. Generate a requirements document and application list as needs list for a proposed network.
6. Estimate the expected data flow for the proposed network.
7. Recommend appropriate security measures for the safety of devices and the infrastructure.
8. Run simulations of both the existing and proposed network systems making use of OPNET IT Guru, Academic Edition.
2. Materials and Methods
-
A. Federal College of Education Technical Asaba
Educational institutions thrive on the quality of its products, data management and sharing mechanisms, and communication processes. The Federal College of Education Technical Asaba was set up by Decree No. 4 of Extraordinary Official Gazette No. 16, Vol.73 of the Federal Republic of Nigeria. Its mission is to train teachers in different fields of endeavor – making them agents of change in the lives of others, their communities, the nations and the world at large. As a staff of the organization in question, the quality of technological education (with respect to teaching and learning) and the quality of technology education (with respect to integration of technology as alternative delivery means) were lacking as opposed to international best practices. In furtherance, communication processes and record keeping abilities presently utilized, were observed also to be inefficient. A resultant effect in the absence of a systemic approach to efficient communication mechanism and an effective method for storing vital records in such an institution. These and others, are what this paper seeks to address. An intelligent, scalable, robust and properly designed network infrastructure will take into account, the requirement needs of the stakeholders and in turn, boost the communication amongst its users, improve the research capabilities of users within the institution as well as improve overall organizational efficiency.
Currently, most part of the students’ records such as semester and section results are computed and stored manually. This has led to the misplacement of some students’ academic record at the time of final computation of results. Also, management to staff communication, staff to staff communication management to student and staff to student communication is grossly inefficient. This makes it an occasional occurrence for some members of staff to miss important meetings with management because memos were manually disseminated and some members of staff might be out on one academic exercise or another and as such might not be privileged to come to the school environment before the scheduled meeting date [33, 34].
In the institution in question, a network was set to enhance communication and research capabilities of staff; But, network collapsed only few weeks afterwards. The researcher opines that the principles of network design and management were not effectively used. Thus, resulting in a collapse of the network system. In addition, management, staff and students find it difficult to establish an effective communication mechanism to inform each other of changes in scheduled meetings, lectures and examinations. Furthermore, access to online materials for students preparing for examinations, undertaking their research or dissertation is quite a daunting task and as such poor examination performance and poor quality research are produced on a regular basis. This necessitated the researchers’ need to propose a robust network system that will tackle the issues raised above while offering the stakeholders a better quality of service, an improved mechanism for conducting its daily activities and a greater channel for reaching out to a larger number of potential student population both locally and globally. This research attempts to analyse the existing network with a view to identifying the devices, applications and technologies that can be reused in the upgraded model.
-
B. Data Gathering
Study seeks to modify an existing network infrastructure at Federal College of Education (Technical), Asaba. A breakdown of the community population size is listed in the Table 1.
Table 1. Dataset Fact-Sheets for User Population
|
No |
Population |
Number |
Expertise |
Training Required |
|
1 |
Management Staff |
12 |
Little-None |
Yes |
|
2 |
Academic Staff |
348 |
Little-None |
Yes |
|
3 |
Non-Academic Staff |
775 |
Little-None |
Yes |
|
4 |
Student(s) |
2364 |
Little-None |
Yes |
|
5 |
Technical ICT Team |
14 |
Little-None |
Yes |
-
C. Breakdown of Existing Network Components
Table 2. Dataset Fact-Sheets for User Population
|
No |
Population |
Status |
|
1 |
Internet services provider: Cyberspace Nigeria Limited |
Wide coverage with 3Mbps speed or higher broadband is ideal. |
|
2 |
10Base-T Connectivity between network devices |
Upgrade Required |
|
3 |
100Base-Tx Ethernet Tech Connectivity between servers |
Upgrade Required |
|
4 |
Category six cabling |
Still useful |
|
5 |
3-CISCO ME 3640 24CX Series Ethernet Access Switches |
Still useful |
|
6 |
1-CISCO 7000 Series Router, reached end-of-life |
Still useful for backup purposes |
|
7 |
1-CISCO Aironet Wireless 1800 Access Points in ICT Unit |
More Required |
Table 3. Fact-Sheets of Available Server and Devices
|
No |
Hardware |
Status |
|
1 |
HP Pro-Liant DL560 Gen8 Servers with Server, two 750 GB HDD Working on RAID |
More Server machines required |
|
2 |
Workstation (50 pieces) |
Additional Required |
|
3 |
Network Printers Available (4) |
More Required |
Table 4. Fact-Sheets of Available Application Software
|
No |
Software |
Status |
|
1 |
MS Secured Safe Server |
Upgrade Required. Microsoft Visual Studio Team System Server Recommended |
|
2 |
MS SQL Server 2008 |
Upgrade Required to SQL Server 2012 |
|
3 |
Active Directory |
Still Useful |
|
4 |
MS Exchange Server 2010 |
Still useful |
|
5 |
Web Server (Microsoft IIS/8.5) |
Still useful |
|
6 |
MS SQL Server 2008 R2 RTM |
Still useful |
|
7 |
MS Virtual Machine Server 2008 R2 |
Still useful |
|
8 |
DHCP Server |
Still useful |
Tables 2, 3 and 4 respectively show the available hardware and software applications present in the existing network.
-
D. Limitations of Existing Network
The following limitations and bottlenecks were observed:
1. Single Router poses the risk of a single point failure, in the event of a malfunctioning router. This will crash the entire network. An ideal situation is to introduce some resilience via use of a backup router using the appropriate technology to recover in the event of a failure in the main router.
2. Absence of Backup Servers is also a drawback.
3. Network Topology does not support efficient scalability and will obviously not be able to integrate the ever-growing user and application requirements.
4. Single Internet Service Provider is an issue to availability and has been so, subject to the budgetary provisions.
5. Absence of Redundancy with use of a single main Switch is not healthy. In event of an upgrade, redundancy would have to be introduced to ensure resilience in the network.
6. Apps Location: Office and antimalware apps are located on individual user systems in the ICT unit. This is an expensive both to the network and the applications. Each application would require upgrades and patches individually. This would cumulatively lead to an increase in network traffic.
3. Experimental/Proposed Network Design
After the identification of the applications and devices in the existing network, a proposal was drawn by the researcher to reflect network requirement in terms of application, devices and user requirements. This is to ensure that the proposed network withstands the challenges expected by its potential users. Tables 5 and 6 respectively are breakdown of these various requirement specifications.
-
A. Layout Architecture of Existing Network
The network topologies used in a design is quite essential in the analysis of a system. [35] opined that it greatly influences and is responsible in determining the overall performance of the network. [36] There are two types of topologies: physical and logical. Physical topology consists of the device and their cabling layout. The logical topology deals with the pathways data signals undertake as routes in the network from one point to another. The logical is usually an offshoot of the physical topology. Thus, we seek to analyse the physical topologies of existing network [37].
The logical architecture for the existing network employed a flat network topology – from simplicity of network operation and functionality. Basic operations allow for online integration as alternative delivery and result storage system. Thus, course registration forms were accessed from the Web server; while, completed forms are stored back into the database server. The traffic generated in the network was periodic. Thus, the network has few challenges at peak periods. This can no longer be the case in the event of the incorporation of new applications and user groups.
Table 5. Fact-Sheets of Proposed Network Specifications
|
No |
Date |
Type |
Description |
Gathered At |
Location |
Status |
Priority |
|
1 |
NA |
Device |
Cisco ASR1002-X Chassis Router (1) |
Initial Condition |
ICT unit |
Core |
High |
|
2 |
NA |
Device |
Cisco Aironet 3600 Series (9) |
Initial Condition |
See Map |
Core |
High |
|
3 |
NA |
Device |
New HDD for VM Server |
Management |
ICT unit |
Core |
High |
|
4 |
NA |
Device |
HP Pro Liant DL560 Gen8 Servers with 1.5TB each to add to existing server (4) |
Initial Condition |
ICT unit |
Core |
High |
|
5 |
NA |
Device |
Cisco Catalyst 6500 Series Switches for the distribution layer (2) |
Initial Condition |
ICT unit |
Core |
Critical |
|
6 |
NA |
Device |
CCTV to enhance physical security in ICT unit |
Management |
See Map |
Core |
Critical |
|
7 |
NA |
Device |
Swipe cards for authentication |
Management |
ICT unit |
Core |
High |
|
8 |
NA |
Network |
10GB Category five-e cables for patch panels |
Management |
See Map |
Core |
High |
|
9 |
NA |
Network |
10GB Category Six cables for host to Servers |
Management |
See Map |
Core |
High |
|
10 |
NA |
Network |
1GB multimode fibre server/network backbone |
Management |
See Map |
Core |
High |
|
11 |
NA |
Network |
Cisco ASA 5550 Adaptive Security Appliance |
Management |
Server Room |
Core |
Critical |
|
12 |
NA |
Users |
Training of various categories of staff |
Management |
TBD |
Core |
Critical |
|
13 |
NA |
Business |
Minimal Budget (btw £300,000 - £400,000) |
Management |
Info |
Core |
High |
|
14 |
NA |
Business |
Minimal disruption of organizational activities |
Management |
Info |
Core |
High |
Table 6. Fact-Sheets of Proposed Application Services for Proposed Network
|
No |
Date |
Type |
Description |
Gathered from |
Location |
Status |
Priority |
|
1 |
NA |
Application |
Active Directory and Domain Controller is installed on main and backup servers |
Management |
Server Machine |
Core |
Critical |
|
2 |
NA |
Application |
Microsoft SQL Server 2012 to link to the Database Server |
Management |
Server Machine |
Core |
Critical |
|
3 |
NA |
Application |
MOSS SharePoint 2008 for data and protocol centralization |
Management |
Server Machine |
Core |
Critical |
|
4 |
NA |
Application |
MS Office 2013 |
Management |
Server |
Core |
High |
|
5 |
NA |
Application |
NovaBack16: Disaster Recovery Backup |
Management |
Server Machine |
Core |
Medium |
|
6 |
NA |
Application |
Antivirus Software |
Management |
Server |
Core |
Critical |
|
7 |
NA |
Application |
Payroll Software |
Management |
Dedicated Machines |
Core |
High |
|
8 |
NA |
Application |
Microsoft Virtual Server 2012 |
Management |
Server |
Core |
Medium |
|
9 |
NA |
Application |
DNS Server |
Initial Condition |
Server |
Core |
Critical |
|
10 |
NA |
Application |
DHCP Server / Solar Wind Suite |
Initial Condition |
Server |
Core |
Critical |
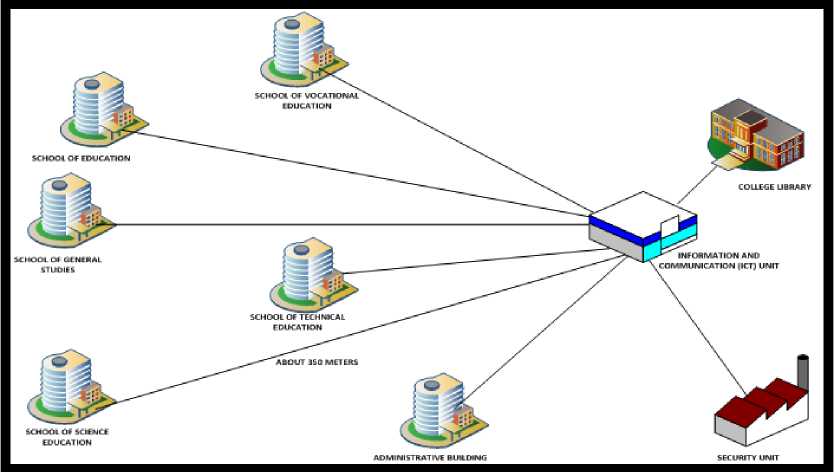
Fig. 1. Site map of Recommended Buildings to Implement the Proposed Network
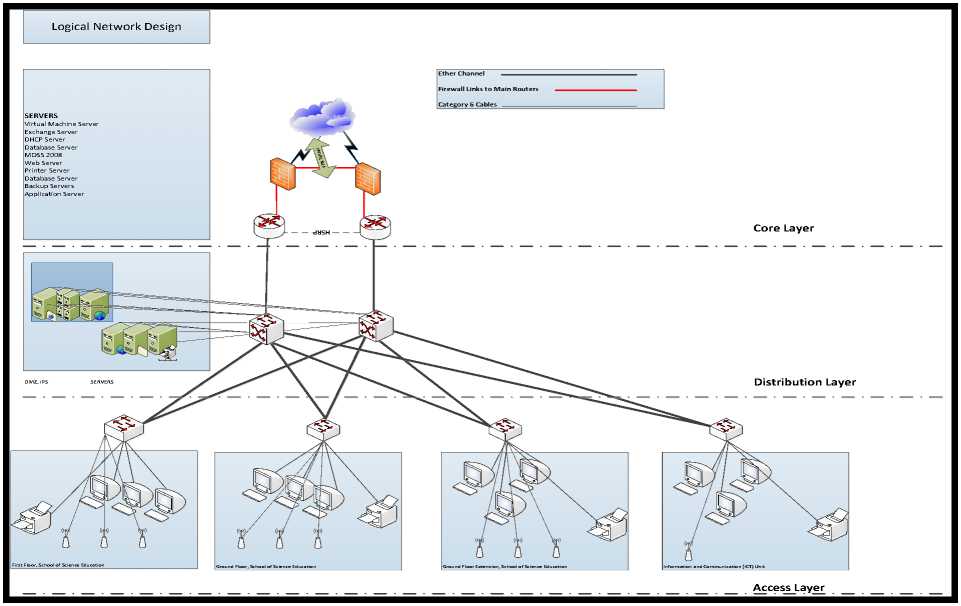
Fig.2. Logical Architecture of Proposed Network
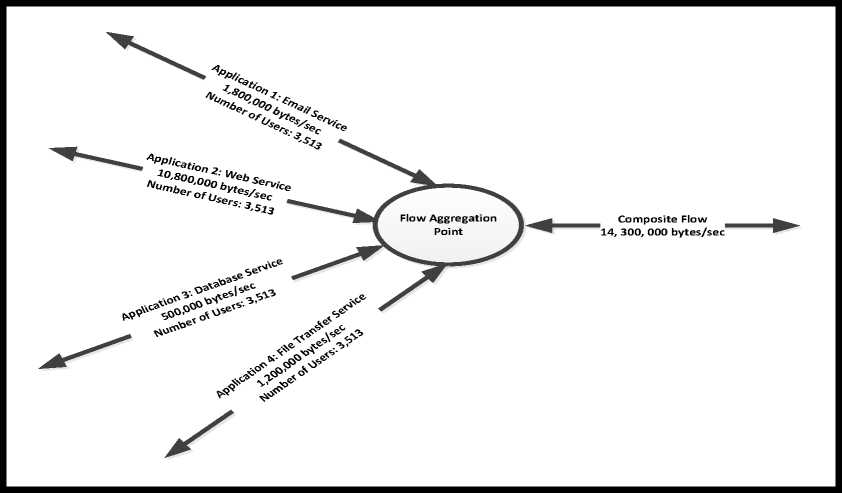
Fig. 3. Composite flow of critical applications in the Proposed Network
-
B. Design Approach Implemented
There are different network design strategies around today. Common ones include top-down (hierarchical design) and the bottom-up design. The hierarchical model structures a network based on the users need, segmenting the network into layers for easy design, management and troubleshooting. This design has been adopted as most suited for the following feats [36, 38, 39, 40, 41, 42, 43, 44, 45, 46]:
-
1. Incorporation of organizational needs in Network Design achieved via network segmentation into layers giving each layer a unique functionality.
-
2. Improved Manageability as it offers the choice for network policies to be applied at different layers as the need arises.
-
3. Improved Troubleshooting as fault diagnosis and repair becomes less tasking without disrupting normal operations.
-
4. Improved ease of manageability yields improved security strategies and policies, which properly handled will further increase speed and other quality of service parameters.
-
5. Improved Scalability via network agility allows for addition of applications, users and devices without necessarily reducing network performance to an intolerable state.
With the benefits of the hierarchical network design, it is quite obvious why it was preferred over the bottom up approach. This is because it has the ability of meeting organizational goals by capturing the requirements from user’s perspective.
-
C. Physical Architecture of Proposed Network
Cabling is usually not given the consideration it deserves as certain factors play critical roles in cabling plan of a network. These include the structure of the building, location of network devices, underlying technologies of the cables and requirements of redundancy and performance. The centralized cabling type is highly recommended as it is cost effective and easily managed. Its major drawback is scalability. For the different buildings in the campus, distributed cabling topology is recommended due to ease of troubleshooting and fault isolation [47, 48, 49].
Telecommunication
________г
First Floor Extension, FCE(T), Asaba
Telecommunication
Telecom
Ground Floor Extension, FCE(T), Asaba
Ground Floor FCE(T), Asaba
ICT Unit, FCE(T), Asaba
Fig.4. Centralized Cabling System for Proposed Network
-
D. Logical Design of Proposed Network
With an analysis of the logical architecture of the existing system, some lapses were observed ranging from a poor network design that would have issues with scalability to single point failures on the main router, the main switch and possibly the network provider. Absence of DMZ, Intrusion Prevention System, firewall, virtual LANs were also observed to pose both security and management challenges. Proposed system hopes to address these constrains via different strategies as stated below.
-
1. Improved Security: Introduction of a firewall and Intrusion Prevention System was achieved via Cisco ASA 5550. Also, implementing a virtual LANs on the main switches, virtual private network (VPN) at the core and a Demilitarized Zone (DMZ) at distribution layer will improve the security.
-
2. Improved Resilience: To improve network redundancy, additional routers were placed at the core support the main linking them with the Hot Standby Router Protocol. Also, redundancy was introduced in the distribution layer to add resilience to the network. Finally, backup servers were introduced to aid network data recovery in case of crash.
-
3. Improved Performance and Availability: Use of multimode fibre for upload/download at distribution layer. Also, three wireless access points will be placed at strategies locations in each of the floors and extensions of the
various buildings – to boost network access apart from cablings in building. To improve availability, Cisco Express Forwarding (CEF), Low Latency Queuing (LLQ) and Committed Access Rate (CAR) will also be used to boost the network performance.
-
E. Naming and Addressing Plan for Proposed Network
An addressing plan involves a framework for allocating IP addresses to authorized devices in the network. This involves proper care, as an addressing plan has a huge impact on the optimization, management and troubleshooting of a network.
Table 7. Users and devices that requires an IP address.
|
Network Entity |
Addresses |
|
|
1 |
Employees |
1,149 |
|
2 |
Students |
2,364 |
|
3 |
Main Routers |
2 |
|
4 |
Network Printers (For Now) |
4 |
|
5 |
Core Layer Switches |
2 |
|
6 |
Distribution Layer Switches |
2 |
|
7 |
Access Layer Switches for Management Staff |
1 |
|
8 |
Access Layer Switches for Academics |
2 |
|
9 |
Access Layer Switches for Non Academics |
3 |
|
10 |
Access Layer Switches for Students |
5 |
|
11 |
Server Machines |
5 |
|
12 |
Wireless Access Points |
9 |
|
13 |
Firewalls |
2 |
|
Total Number of Required IP Addresses |
3,547 |
Table 8. Subnet Table for Different User Groups
|
Networ k Host |
Subnet ID |
1st Usable |
Last Usable |
Broadcast ID |
CI DR |
|
Devices |
172.16.0.0 |
172.16.0.1 |
172.16.0.254 |
172.16.0.255 |
20 |
|
Manage ment |
172.16.1.0 |
172.16.1.1 |
172.16.1.254 |
172.16.1.255 |
20 |
|
Academ ics |
172.16.2.0 |
172.16.2.1 |
172.16.3.254 |
172.16.3.255 |
20 |
|
Other Staff |
172.16.4.0 |
172.16.4.1 |
172.16.6.254 |
172.16.6.255 |
20 |
|
Students |
172.16.7.0 |
172.16.7.1 |
172.16.16.254 |
172.16.16.255 |
20 |
|
Support |
172.16.17.0 |
172.16.17.1 |
172.16.17.254 |
172.16.17.255 |
20 |
|
Unused |
172.16.18.0 |
172.16.18.1 |
172.16.255.254 |
172.16.255.255 |
20 |
Route aggregation was also considered in determining the class of network to be chosen and the range of IP addresses to be used in other to reduce bandwidth consumption. Also private range of IP addresses will be used, to provide security and reduce the cost acquiring multiple public IP addresses which are very experience. The NAT (Network Addressing Table) will be used in the conversion of private IP addresses to public addresses when communicating with devices external to the network. After due consultation of the number of IP addresses required for the expected amount of devices on the network, a class “B” network was chosen the following range of IP addresses. The non-variable length method (Non-VLSM) was applied for easy management of the network. The addressing plan is as in table 8. [50] in Digital project Advisory Group [51] views a naming convention as a set of regulations that can be used in the naming and identification of digital or electronic documents. They actually help in the easily location of documents and devices in a particular scenario. [52] enumerated guidelines to include the avoidance of names that will create redundancy, the use of names with clear and concise meanings, use of names that link to the devices they represent and so on.
Table 9. Sample Implementation of naming Convention
|
S/No |
Component / Location / Departments |
Naming |
|
1 |
Router |
_rt |
|
2 |
Switch |
/sw |
|
3 |
Access Point |
/ap |
|
4 |
Server |
/ser |
|
5 |
Workstation |
/wrk |
|
6 |
Laptop |
/lap |
|
7 |
Core Layer |
/cl |
|
8 |
Distribution Layer |
/dl |
|
9 |
Access Layer |
/al |
|
10 |
Department of Computer Education |
/dcom |
|
11 |
Department of Physics Education |
/dphy |
|
12 |
Department of Chemistry Education |
/dchem |
|
13 |
Department of Biology Education |
/dbio |
|
14 |
Department of Mathematics Education |
/dmath |
|
15 |
Department of Integrated Science Edu. |
/dintSc |
|
16 |
Deans Office |
/deof |
|
17 |
Information and Communication Unit |
/ict |
|
18 |
Ground Floor |
/gf |
|
19 |
First Floor |
/ff |
|
20 |
Second Floor |
/Sf |
|
21 |
Extension |
/ex |
|
22 |
School of Science Education |
/sse |
An application of the naming convention is seen in table 10 with the format chosen as thus: school* /department*/office*/ floor* / layer* / device /make /model / device number. The names marked with asterisks (*) sign are the optional.
Table 10. Sample Implementation of naming Convention
|
Device |
Naming |
|
|
1 |
Router |
Ict/cl/rt/cisco/4451/00001 |
|
2 |
Distribution Layer Switch |
Ict/dl/sw/cisco/4948/00002 |
|
3 |
Access Point |
Sse/ff/ap/cisco/1200/00006 |
|
4 |
Server Machine |
Ict/ser/hp/ dl560 gen8/00003 |
|
5 |
Workstation |
Sse/dphy/ex/wrk/hp/corei7/00013 |
F. Flow Analysis on the Logical View
4. Result Findings and Discussion
In [42], flow analysis is the process of characterizing traffic flows through a network – considering the likely areas of convergence and performance levels required in those areas. A proper understanding of the flow of traffic in a network is quite pertinent. The flow analysis helps network designers to characterize traffic (individual, composite and critical flows), flow models and identify data sources and sinks. To analyse this, we considered various requirements, locations and behaviors of user, applications and protocol overheads (which cannot be actually computed). Critical applications are bi-directional moving from client workstations to servers, and back. The estimated flow on the network is computed for the various bandwidths required to accommodate these flows. It involves determining available network capacity and average network utilization of specific applications that are critical to a network. The application utilization is captured via a network analyzer (in this case, the Riverbed) with values listed in table 11. The proposed network utilizes a 10Gbps multimode fibre which can support can a bandwidth of about one billion bytes (1,000,000,000 bytes/sec). Adding protocol overhead and other applications, the proposed network will work optimally. We compute average network utilization of specific applications, achieved via the use of a network analyzer and comparing it with bandwidth of the cable used in transporting the traffic. The cable bandwidth can be computed by determining the amount of available network bandwidth and computing the average utilization required by the specific applications.
Table 11. Capacity of Major Applications (in bytes/secs)
|
No |
Type of Application |
Bandwidth in Bytes/secs |
Estimated Users |
|
1 |
Email Service |
1,200,000 |
3153 |
|
2 |
Web Utilization |
1,800,000 |
3153 |
|
3 |
File Transfer |
10,800,000 |
3153 |
|
4 |
Database Query |
500,000 |
3153 |
|
Total Bandwidth Utilization |
14,300,000 |
3153 |
|
For an effective conduction of this test, test scripts were designed. The Riverbed Modeller, Academic Edition 17.5 was used for the first sets of test. To effectively run the simulation, we properly configured the software with required applications and user population – via use of the application configuration and profile configuration options.
-
A. Application Response Time
This test is a performance metric to determine time interval between a user’s request and the actual time a response is fed back. To achieve response time from a Database Query, a HTTP Page, file downloads from FTP and Email Server was tracked as in figures 6 and 7 respectively using two scenarios.
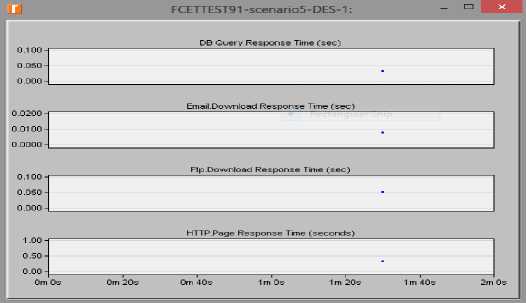
Fig.5. Response time for scenario 1 (actual population)
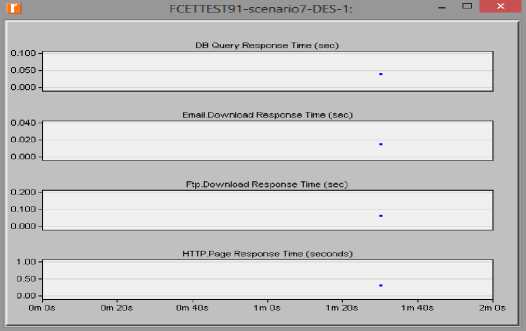
Fig.6. Response time for scenario 2 (doubled population)
In scenario 1, the response times for Database queries was about 0.38 seconds, 0.008seconds for Email download, 0.052 seconds for file download and 0.32 seconds for HTTP page retrieval; While, for scenario 2, there was a longer response time as it took about 0.40 seconds for Database Queries, 0.015 seconds for Email download, 0.060 seconds for file download and 0.35 seconds for HTTP page retrieval. There was no significant difference in the response time for the various applications in both scenarios. With the results as above, we can conclude that the response time even with a doubled population is still very fast and the system is highly scalable. Table 12 paints a vivid picture of the simulation results.
|
Items |
Scenario 1 |
Scenario 2 |
Scenario 1 |
Scenario 2 |
|
Time Secs |
Population |
Time Secs |
Population |
|
|
DB Query |
0.38 |
0.40 |
3512 |
7230 |
|
|
0.008 |
0.015 |
3512 |
7230 |
|
FTP |
0.052 |
0.060 |
3512 |
7230 |
|
HTTP |
0.32 |
0.35 |
3512 |
7230 |
-
B. Throughput Testing
In [14], throughput is defined as the actual transfer rate of data in a medium over given a period of time. Being another performance metric test, throughput test is essential because the capacity of a network can be affected by interference and errors, thus making the stated capacity quite different from the actual capacity. For throughput, the data transfer rate of the four LAN segments was analyzed as in Figure 8 and 9 respectively.
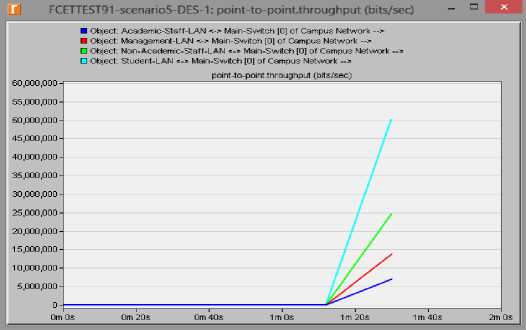
Fig.7. Throughput test for scenario 1
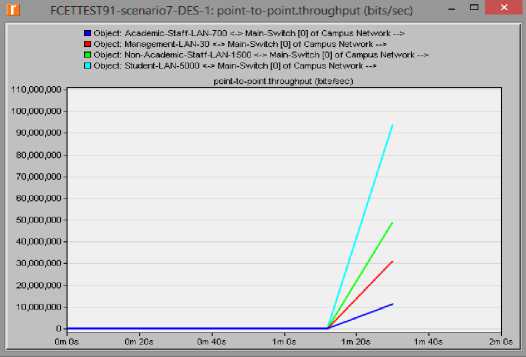
Fig.8. Throughput test for scenario 2
In scenario 1, the highest data transfer rate or throughput was about 50,000,000 bps (i.e. about 47.68mbps) – coming from the student LAN; while, lowest came from the management LAN with about 7,000,000 bps (i.e. about 6.68 mbps) as in figure 8; For scenario 2, the highest throughput came from the student LAN with about 94,000,000 bps (i.e. 89.65 mbps), and lowest still came from the management LAN with about 12,000,000 bps (i.e. about 11.44 mbps) as shown in table 7. This is expected because the traffic was doubled in scenario seven.
Our cabling from the various LAn to the main switch uses the multimode fibre optic cabling with a bandwidth capacity of 9.92Gps. As such, the effect of the highest throughput has no negative consequence on the network. With our LAN cabling capacity, optimal performance is expected.
-
C. Availability Test
The ping command is used to reach the different nodes on the network. It sends Internet Control Message Protocol to different devices across the network. Figure 10 shows its execution.
From the diagram, we can clearly see that different nodes were sent echo request, and an eighty per cent (80%) response rate was gotten. This was solely because it was the first time. Subsequent echo request had a success rate of a hundred per cent. This clearly shows that the different nodes were reachable.
-
D. Network Security
To conduct the security test for the proposed network, the Riverbed OPNET was employed once again. It was used to test the effectiveness of the system’s firewall. The test consisted of two scenarios; the first scenario allowed external users to have unrestricted access to the network resources, while the second scenario restricted the external users from having access the networks’ web and database servers.
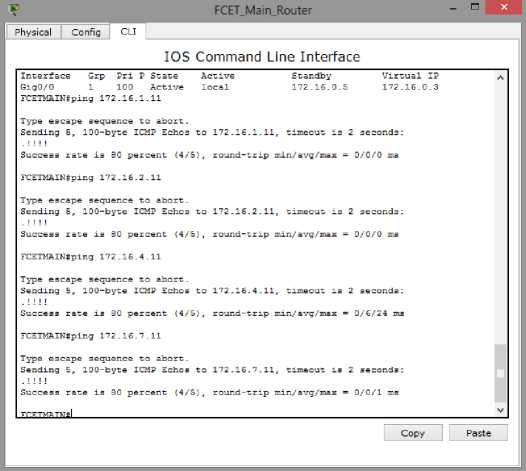
Fig.9. Reachability Test for Proposed Network
Fig.10. Security with Firewall for Proposed Network
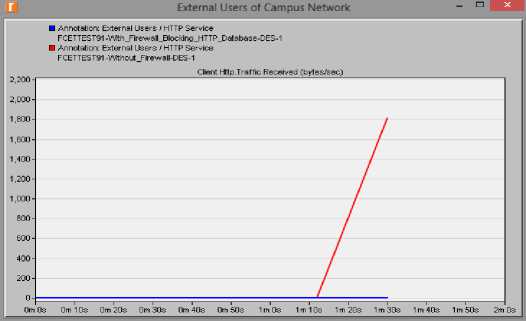
Fig.11. Firewall implementation of HTTP Service
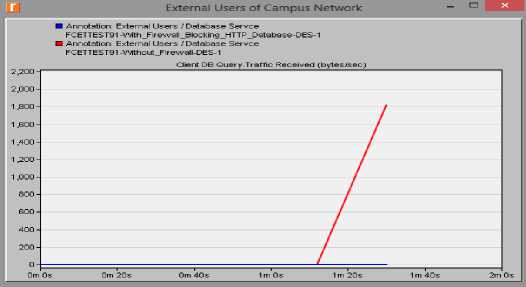
Fig.12. Firewall implementation of Database Service
Figure 12 shows the results from the two for web traffic to the external users. The first scenario indicated by the red line shows the amount of data received per second by the external users; while the second scenario (indicated by the blue line) shows that no access was granted to the external users for having access to the web server. The result was also reflected in the database server as shown in figure 13. For the other applications that granted access to the external users, but the traffic was still filtered. This can be seen in figures 14 showing data traffic flow from the file server to the external users.
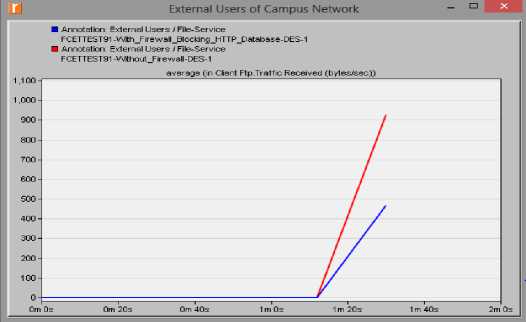
Fig.13. Firewall implementation filtering traffic from FTP
5. Conclusion
The study explored standardized approaches to network analysis, design, architecture, modelling, testing and optimization to deliver a network that met the requirements of the stakeholders of the client organization. To ensure that users’ requirements were met, hierarchical design was employed. It ensures that the requirements of the various stakeholders formed the basis for which diverse network topologies, applications, devices and protocols were chosen. The constraints of resources, time and energy made it impractical to explore many more opportunities from a technical viewpoint. Study though implements four applications on the designed networks namely centralized data storage, file transfers, web services and e-mail services. We recommend the possibility of implementing voice over internet protocol (VoIP) and campus-cloud for internal communication and external data storage respectively. VoIP will guarantee an optimal utilization of the network infrastructure; while, campus cloud in its variations will provide a reliable platform for data recovery and network agility required by organizations in today’s competitive world. In a nutshell and from the various test carried out on the network, the basic functions of the proposed network were working as stipulated and in tandem with the project objectives. We opine that the deployment of this network as stipulated will meet the needs of the various stakeholders.
Список литературы Mitigating Technical Challenges via Redesigning Campus Network for Greater Efficiency, Scalability and Robustness: A Logical View
- Kurose, J. and Ross, K. (2013) Computer Networking: A Top-Down Approach. 6th edn. ed. by Hirsch, M. and Snider, E. Boston: Pearson Education Limited
- Ojugo, A.A., R.E. Yoro., A. Eboka., M. Yerokun and I. Iyawa., (2012). Implementation issues of VoIP to enhance rural telephony in Nigeria, Journal of Emerging Trends in Computing & Information Systems, 4(2): pp113-120, [web]: cisjournal.org/journalofcomputing/Archive_Feb_2013.aspx
- Ojugo, A.A., Eboka, A.O., (2014). Social engineering detection model for mobile smartphone clients, African J. of Computing & ICT, 7(3): pp91–100. [web]: www.africanjournalofcomputingict1.files.wordpress.com/2017/08/vol-7-no-3-september-2014.pdf
- Ojugo, A.A., A.O. Eboka., (2019). Inventory prediction and management in Nigeria using market basket analysis associative rule mining: memetic algorithm approach, Int. Journal of Information and Communication Technology, 8(3): pp128-138, doi: 10.11591/ijict.v8i3, [web]: www.ijict.iaescore.com/index.php/IJICT/issue/view/554
- Ojugo, A.A., A.O. Eboka., (2020). Memetic algorithm for short messaging service spam filter text normalization and semantic approach, Int. Journal of Information and Communication Technology, 9(1): pp13 – 27, doi: 10.11591/ijict.v9i1, [web]: www.ijict.iaescore.com/index.php/IJICT/issue/view/555
- D.A. Oyemade., J. Akpojaro., A.A. Ojugo., R. Ureigho., F. Imouokhome., E. Omoregbee., (2016). A three tier learning model for universities in Nigeria, Journal of Technologies in Society, 12(2): pp9-20, [web]: https://jts.cgpublisher.com
- Ojugo, A.A., O.D. Otakore., (2018a). Mitigating social engineering menace in Nigerian Universities, J. of Comp. Sci. & Application, 6(2): pp64–68, doi: 10.12691/jcsa-6-2-2, [web]: www.sciepub.com/jcsa/content/6/2
- Ojugo, A.A., D.O. Otakore., (2018b). Redesigning academic website for better visibility and footprint: a case of Federal University of Petroleum Resources Effurun website, Network & Communication Technologies, 3(1): pp33 –44, https://doi.org/10.5539/nct.v3n1p33, [web]: www.ccsenet.org/journal/index.php/nct/
- Ojugo, A.A., A.O. Eboka., (2018). Assessing user satisfaction and experience on academic websites: a case of selected Nigerian Universities websites, Int. J. Tech & Comp. Sci., 10(7): pp53-61, doi: 10.5815/ijitcs.2018.10.07, [web]: www.mecs-press.net/ijitcs
- Ojugo, A.A., I.P. Okobah., (2018). Prevalence rate of hepatitis-B virus infection in Niger Delta region of Nigeria using graph-based diffusion heuristic model, IJCAOnline International Journal of Computer Application, 179(39): pp27 –33, [web]: www.ijcaonline.org/archives/volume179/number39/
- R.E. Yoro., Ojugo, A.A., (2019a). An intelligent model to predict the relationship of weather conditions for fish farming production yield in Nigeria, American Journal of Modeling and Optimization, 4(3): pp79-90
- R.E. Yoro., Ojugo, A.A., (2019b). Quest for prevalence rate of Hepatitis-B Virus infection in Nigeria: comparative study of supervised versus unsupervised model, American J. of Modeling & Optimization, 4(3): pp79-90
- R.E. Yoro., Ojugo, A.A., (2019c). An intelligent client-trusted and dependable security framework to ease smartphone portability on community cloud computing, J. of Network and Communication, 4(3): pp79-90
- Dye, M., McDonald, R., and Rufi, A. (2008) Network Fundamentals: CCNA Exploration Companion Guide. 1st edn. ed. by Ray, M. Indianapolis, Indiana, USA: Cisco Press
- White, C. (2011) Data Communications and Computer Networks: A Business User’s Approach. Boston, USA: Course Technology Publications
- Derfler, F.J. (2000) Practical Networking. Indiana: Que
- Comer, D. (2008) Computer Networks and Internets. 5th edn. London: Addison-Wesley
- Beasley, J. (2008) Networking. 2nd edn. USA: Prentice Hall
- Tanenbaum, A. and Wetherall, D. (2010) Computer Networks. 5th edn. USA: Prentice Hall
- Ojugo, A.A., Yoro, R., Oyemade, D.A., Eboka, A.O., Ugboh, E., Aghware, F., (2013a). Robust cellular network rural telephony in Southern Nigeria, American J. of Net. Comm. 2(5): 125-132 www.article.sciencepublishinggroup.com/html/10.11648.j.ajnc.20130205.12.html
- Ojugo, A.A., Abere, R., Orhionkpaiyo, B., Yoro, R., Eboka, A., (2013b). Technical issues for IP-based telephony in Nigeria, Int. J. Wireless Comm. & Mobile Comp., 1(2): 58-67, [web]: www.article.sciencepublishinggroup.com/html/10.11648.j.ajnc.20130102.14.html
- Eung-Ha, K., Cho, K.S and Ryu, W., “Amendment to MSF whitepaper on personalized converged services: network-to-network”, [online]: www.msforum.org/techninfo/reports.shtml, last accessed March 2013.
- Schwartz, R., “Wireless communications in developing nations: cellular and satellite net systems”, 1997, Artech house. MA: Boston.
- Stallings, W and Van Slyke, R., “Business data communications”, 6th Ed., 2010, Prentice Hall Int. Ed., ISBN – 1-13-761230-3, pp316-340.
- Williams, M., Ewan, S and Reza, T., “Convergence, IP telephony and regulations: issues and opportunities for network development in India”, 2005, Technical University of Denmark Center for ICT, Denmark: Lyngby.
- Conte, R., “Rural telephony: new approach via mobile satellite communication”, Proceedings of Pacific telemmunication conf., 1994, Hawai: Honolulu
- Garg, V., Smolik, K and Wilkes, J., “CDMA application in wireless communications”, 1997, Prentice Hall publications, New Jersey: Upper Saddle River.
- Helgert, H., “Integrated services digital net: Architecture, protocols and standards”, 1991, Readings: MA: Addison-Wesley.
- Brennen, R and Dipak, G., “Secure IP telephony via multi-layered protection”, 2009, Technical University of Denmark report, Centre for ICT, Denmark: Lyngby
- Martins, J.A.H., “Telecommunications and the computer”, 1990, Prentice Hall publications, New Jersey: Upper Saddle River
- Rosa, J., “Rural telecommunications via satellite”, Journal of Telecommunications, 2005, 3(2), pp 75 – 81.
- Hafner, K and Lyon, M., “Where wizards stay up late”, 1996, Simon and Schuster, New York.
- Ojugo, A.A., F. Aghware., R. Yoro., M. Yerokun., A. Eboka., C. Anujeonye., F. Efozia., (2015a). Dependable community-cloud framework for smartphones, American J. of Networks and Communications, 4(4): pp95-103, [web]: article.sciencepublishinggroup.com/html/10.11648.j.ajnc.20150404.13.html
- Ojugo, A.A., D. Oyemade., D. Allenotor., R.E. Yoro., C.N. Anujeonye., (2015b). Immunization problem for Ebola virus in rural Sierra-Leone, African J. of Comp. & ICT., 8(1): pp1 –10: [web]: www.afrjcict.net/
- Subramoni, H., Kandalla, K., Vienne, J., Sur, S., Barth, B., Tomko, K., Mclay, R., Schulz, K., and Panda, D.K. (2011) “Design and Evaluation of Network Topology-/Speed- Aware Broadcast Algorithms for InfiniBand Clusters”. 2011 IEEE International Conference on Cluster Computing [online] 317–325. available from http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=6061150 [8 June 2014]
- Kumar, H. (2013). Physical vs. logical topologies [online] available from http://egyaan.in/2013/04/22/physical-vs-logical-topologies/
- Sun, X. and Xie, G.G. (2013) “Minimizing Network Complexity through Integrated Top-down Design”. Proceedings of the ninth ACM conference on Emerging networking experiments and technologies - CoNEXT ’13 [online] 259–270. available from http://dl.acm.org/citation.cfm?doid=2535372.2535376
- DiNicolo, D. (2007) Advantages and Disadvantages of Different Network Design Approaches [online] available from http://www.2000trainers.com/ccda-study-guide/comparing-network-design-approaches/ [2 June 2014]
- Huynh, M., Goose, S., and Mohapatra, P. (2010) “Resilience Technologies in Ethernet”. Computer Networks [online] 54 (1), 57–78. available from http://linkinghub.elsevier.com/retrieve/pii/S1389128609002692[1 June 2014]
- Iqbal, R. and Xingang, W. (2014) Network Planning and Management [online] Coventry. available from http://cumoodle.coventry.ac.uk/course/view.php?id=10062
- Lanxiaopu, M. (2012) An Investigation and Comparison on Network Performance Analysis [online] UNIVERSITY OF OSLO. available from https://www.duo.uio.no/bitstream/handle/10852/9087/MxMT.pdf?sequence=1
- McCabe, J. (2008) Network Analysis, Architecture and Design. 3rd edn. London: Morgan Kaufmann
- Rouse, M. (2006) Definition: Scalability [online] http://searchdatacenter.techtarget.com/definition/scalability [23 June 2014]
- Rouse, M. (2010) Network Topology [online] available from http://whatis.techtarget.com/definition/network-topology [23 May 2014]
- Duboc, L., Letier, E., and Rosenblum, D.S. (2013) “Systematic Elaboration of Scalability Requirements through Goal-Obstacle Analysis”. IEEE Transactions on Software Engineering [online] 39 (1), 119–140. available from http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=6152130
- Oppenheimer, P. (2011) Top-Down Network Design. 3rd edn. Indianapolis: Cisco Systems Inc.
- Derbel, H., Agoulmine, N., and Salaün, M. (2009) “ANEMA: Autonomic Network Management Architecture to Support Self-Configuration and Self-Optimization in IP Networks”. Computer Networks [online] 53 (3), 418–430. available from http://linkinghub.elsevier.com/retrieve/pii/S138912860800354X[13 June 2014]
- Jang, W.S. and Healy, W.M. (2010) “Wireless Sensor Network Performance Metrics for Building Applications”. Energy and Buildings [online] 42 (6), 862–868. available from http://linkinghub.elsevier.com/retrieve/pii/S0378778809003314[23 May 2014]
- Trivedi, K.S., Kim, D.S., and Ghosh, R. (2009) “Resilience in Computer Systems and Networks”. Proceedings of the 2009 International Conference on Computer-Aided Design - ICCAD ’09 [online] 74. available from http://portal.acm.org/citation.cfm?doid=1687399.1687415
- Sterbenz, J.P.G., Hutchison, D., Çetinkaya, E.K., Jabbar, A., Rohrer, J.P., Schöller, M., and Smith, P. (2010) “Resilience and Survivability in Communication Networks: Strategies, Principles, and Survey of Disciplines”. Computer Networks [online] 54 (8), 1245–1265. available from http://linkinghub.elsevier.com/retrieve/pii/S1389128610000824[30 May 2014]
- Digital Project Advisory Group (2008) Guidelines on File Naming Conventions for Digital Collections [online] available from http://ucblibraries.colorado.edu/systems/digitalinitiatives/docs/filenameguidelines.pdf
- Robinson, M. (2007) Record Management Guidance [online] United Kingdom. available from http://www.st-andrews.ac.uk/media/business-improvements/recordsmanagement/documents/NamingConventionsV01.pdf
- Ergu, D., Kou, G., Shi, Y., and Shi, Y. (2014) “Analytic Network Process in Risk Assessment and Decision Analysis”. Computers & Operations Research [online] 42, 58–74. available from http://linkinghub.elsevier.com/retrieve/pii/S0305054811000785[11 June 2014]
- Cárdenas, A.A., Amin, S., and Lin, Z. (2011) “Attacks Against Process Control Systems : Risk Assessment , Detection , and Response Categories and Subject Descriptors”. in Proceedings of the 6th ACM Symposium on Information, Computer and Communications Security [online] held 2011. available from http://delivery.acm.org/10.1145/1970000/1966959/p355-cardenas.pdf?ip=194.66.32.1&id=1966959&acc=ACTIVESERVICE&key=BF07A2EE685417C5%2E7D2D40990 E9ACC88%2E390D382F189BE0B3%2E4D4702B0C3E3 8B35&CFID=475734200&CFTOKEN=24026082 &__acm__=1402505101_fcc3872ecbd6835d17a0b00d66bd540f
- Kizza, J.M., (2013) Computer Communication and Networks: A Guide to Computer Network Security. 2nd edn. London: Springer
- Roy, S., Ellis, C., Shiva, S., Dasgupta, D., Shandilya, V., and Wu, Q. (2010) “A Survey of Game Theory as Applied to Network Security”. 2010 43rd Hawaii International Conference on System Sciences [online] 1–10. available from http://ieeexplore.ieee.org/lpdocs/epic03/wrapper.htm?arnumber=5428673
- Miaji, Y. and Ph, D. (2014) “Novel Performance Enhancement of University ’ S Network Exploiting Cisco Network Design Model : Study Case on IUKL Network”. in International Conference on Computer Security and Digital Investigation [online] held 2014 at Malaysia. 36–41. available from http://sdiwc.net/digital-library/novel-performance-enhancement-of-universitys-network-exploiting-cisco-network-design-model-study-case-on-iukl-network


