Modeling and Analysis on a DTN Based Wireless Sensor Network Topology Control
Автор: Luqun Li
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 1 vol.1, 2009 года.
Бесплатный доступ
Wireless sensor networks (WSNs) have unlimited and extensive potential application in different areas. Due to WSNs’ work environments and nodes behavior, intermitted network connection may occur frequently, which lead packets delay and lose in the process of data transmission. Most related works on WSNs, seldom consider how to address the issue of intermitted network connection in WSNs. To the best of our knowledge, few papers did related work on how to utilize intermitted network connection to control the topology of WSNs and save the battery of nodes in WSNs. Although intermitted network connection in WSNs is not a good phenomenon, when it occurs, it indeed can keep some nodes in power saving mode. If we can intelligently control WSNs network topology and get intermitted network connection during the intervals of transmission, we will find another way to save the nodes energy to the maximum extent. Based on these ideas, we import the idea of Delay Tolerant Network (DTN) protocol to address the issue. In this paper, first we give the modeling and analysis on node behaviors in DTN WSNs, then we present the end to end performance analysis in DTN WSNs to get the parameters of optimistic hops, maximum hops and each node’s neighbor number, after that we give some basic rules on DTN parameters selection for DTN based WSNs topology control. Finally, we do a related simulation by our DTN based WSNs topology control approach and HER routing algorithm; simulation results show that our approach and algorithm gained better performance in WSN life span, nodes energy equilibrium consumption than DADC.
DTN, Wireless sensor networks, Topology control, M/G/1/K queue, Little’s Law
Короткий адрес: https://sciup.org/15010974
IDR: 15010974
Текст научной статьи Modeling and Analysis on a DTN Based Wireless Sensor Network Topology Control
Published Online October 2009 in MECS
Wireless sensor networks (WSNs) serve as a significant role to bridge the gap between the physical and logical worlds [1]. Nodes in WSNs are tiny embedded devices which only own limited computing ability, data storage space, constrained battery energy and narrow wireless network band width. Among the most critical issues of WSNs is nodes’ energy consumption in general. So, usually, in a WSNs application, to save the battery energy in each node, node can be in power saving model, or in sleeping mode which may lead intermitted network connection and long time delay of transmission
Manuscript received January 20, 2009; revised June 20, 2009; accepted July 20, 2009.
This paper is partly supported by Shanghai Normal University SK200709, DZL805, CL200652 and PL531.
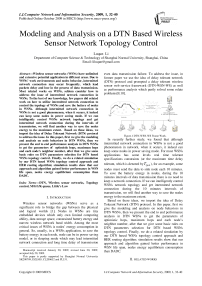
even data transmission failure. To address the issue, in former paper we use the idea of delay tolerant network (DTN) protocol and prompted a delay tolerant wireless sensor web service framework (DTN-WSN-WS) as well as performance analysis which partly solved some relate problems[9,10].
Figure.1 DTN-WSN-WS Frame Work.
In recently further study, we found that although intermitted network connection in WSNs is not a good phenomenon in network, when it occurs, it indeed can keep some nodes in power saving mode. For most WSNs applications has some levels real time tolerant specifications constraints (or the maximum time delay tolerant, which is denoted by T QoS ), for an example, some nodes must send the data to sink node each 10 minutes. To save the battery energy in nodes, during the 10 minutes intervals of data transmission there is no need to keep a network connection. If we can intelligently control WSNs network topology and get intermitted network connection during the 10 minutes intervals of transmission, we will find another way to save the nodes energy to the maximum extent.
Based on these ideas, we import the idea of Delay Tolerant Network (DTN) protocol. In this paper, first we give the modeling and analysis on node behaviors in DTN WSNs, then we present the end to end performance analysis in DTN WSNs to get the parameters of optimistic hops, maximum hops and each node’s neighbor number, after that we give some basic rules on DTN parameters selection for DTN based WSNs topology control. Finally, we do a related simulation by our DTN based WSNs topology control approach and HER routing algorithm; simulation results show that our approach and algorithm gained better performance in WSN life span, nodes energy equilibrium consumption than DADC.
-
II. RELATED WORKS
Topology Control (TC) is one of the most important techniques used in wireless ad hoc and sensor networks to reduce energy consumption and radio interference. [1] gave a whole survey of topology control for WSN. [2] proposed a distributed k-connected (KC) energy saving topology control algorithm for wireless sensor networks. In the algorithm, each node constructs a local k-connected sub-network independently based on the neighbor topology information, and adjusts its transmission power using a Max-Min method to save energy. [3] proposed the event-to-sink reliable transport (ESRT) protocol, which is a novel transport solution developed to achieve reliable event detection in WSN with minimum energy expenditure. [4] gave a topology control method for multi-path wireless sensor networks.[5] gave a topology control for delay sensitive applications in wireless sensor networks,[6] presented a energy-aware topology control for wireless sensor networks using mimetic algorithms, [7] put forward a energy-efficient localized topology control algorithms in IEEE 802.15.4-based sensor networks,[8] gave a algorithms for fault-tolerant topology in heterogeneous wireless sensor networks.[9] put a topology control and geographic routing in realistic wireless networks.
These papers share the common goal of this technique, which is to control the topology of the graph representing the communication links between network nodes with the purpose of maintaining some global graph property (e.g., connectivity), while reducing energy consumption and/or interference. Intermitted network connection should be avoided in topology control.
For the core current communication theory and protocols in WSNs are inherited from traditional wired or wireless network, and the preconditions of related research works are supposed to have at least one route existing from data transmitting source to destination and small delay of transmission. Intermitted network connection does not meet the preconditions of research; there is no doubt to see that most related protocols will run into fatal problems. When intermitted network connection phenomena occurs in WSNs, if traditional communication protocols are taken, nodes in WSNs may mistakenly treat intermitted network connection phenomena as network congestion or packets lose in transmission, to make matter worse, they may deal with these issues by adjusting the size of data sending window or resending packets which will lead much network traffic, lower network performance and much nodes battery energy consumption. So how to cope with intermitted network connection problem is becoming a new and challenge issue in WSNs. To the best of our knowledge, we think that these papers do not yet do related study on how to use Intermitted network connection phenomenon to control the topology of WSNs and save each node’s energy.
-
III. P ROBLEM D EFINATION
A wireless sensor network is denoted with Nwsn , Nwsn = {n1, n2 K niK}, ni is a node in Nwsn , ni is with a specific geographic location, battery power and 2 < i < N , the total number of nodes in WSN is denoted with Nwsn [9,10].
ni ’s next hop nodes (or neighbor node) set is denoted with N c , N c = { nj ,K, n k } , | N T| is the total number nodes of ni 's neighbor node. Note that Nic may be controlled by dynamic regulating the signal power of each node, for example, by controlling each node’s sensing or transmitting power (or keeping some node in power saving mode), we can get different number of Nic for ni . Set Nic is one problem of topological control for WSN. It is the initial parameters to calculate the routing, and very important for routing selection.
In traditional wired or wireless network, it supposed to have at least one route existing from data transmitting source to destination and small delay of transmission. At a given instant time ti , a route can be denoted with R , ( t\t = t i ) ,and R , ( t\t = t i ) = { n s , L , n d }, where ns is the source node, and nd is the destination node, and s Ф d . h i (t|t = t i ) denotes the total hops of the route. We use R ( t|t = t i ) to denote the set of all routes from n s to n d . R ( t\t = t,) = { R ( t , ) , , R ( t,) 2 K R ( t,) , K R ( t,) c }. (see Figure.2)
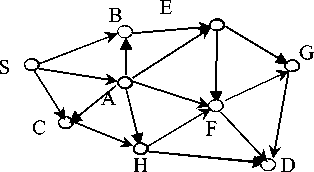
Figure.2 A Typical Traditional Wireless Sensor Network
For most WSNs applications has some levels real time delay tolerant specifications constraints ( TQoS ) which means the maximum delay time from end to end TQoS is given. In a DTN WSNs, data are handled by “store and forward” approach, intermitted network connection phenomena may occur at any time.
Different from traditional route description above, a route in DTN can be denoted with R i ( t E [0, T qoS ]) , and R , ( t e [0, TQoS ]) = { n s , L , nd } . where ns is the source node, and n d is the destination node, and s ^ d h i (t E [0, T qoS ]) denotes the total hops of the route.(see Figure.3)
E

H
F
Figure.3 A Typical DTN Wireless Sensor Network
By modeling and analysis the nodes behavior, we can get the delay time in each node in a route Ri (t E [0,TQoS]) , then we can deduce the total delay time from ns to nd Ti . To meet the requirement of within delay time of TQoS for data transmitting, Ti < TqoS , then we can get the maximum total hops hmax(t E [0, TQos ]) in Ri(t E[0, TQos]) from ns to nd . h.^t E [0, IQS ]) is a key parameters in DTN WSNs topology.
In summary, the fundamentally science issues behind DTN topology control for given specific nodes collection in a specific geography space are:
-
(1) . How to model and analysis the node behavior (for example, node in power saving state or service time of node) in a DTN WSNs, and get the total delay time Ti for data transmitting?
-
(2) . For a specific TQoS , how to find the maximum total hoPs h max ( t E [0, TQoS ]) in a route?
-
(3) . How to control each node ni ’s next hop nodes set Nic to get an optimistic WSN topology;
In this paper, instead of giving a specific DTN topology control algorithm, we mainly address these three key issues above.
-
IV. M ODELING ON N ODE BEHAVIOR
A. Queueing Model for WSNs Node
For a given specific WSNs, node can offer data collecting service, we denoted it with S c . S c is composited of two type of services, or S c = S n + S c,
S n is called data service;
S c is called cache service . n
Data in each node may have different privilege levels to be transmitted. For example, if some data is beyond normal distribution region, it may imply some dangerous things happened, and the data should have high privilege to be transmitted. Besides, the user of Sn may be a common user (or other WSNs node) or a administrator, the administrator sends control packet to Sn regulate the work states of Sn , while the common user only request for the data from Sn [9,10].
So S n service can be classified into different privilege levels, to make the problem simple, the users are classified into two classes, or administrators and common users.
Besides, to enhance the throughput of the system and save the battery energy ofSn,we also introduce a cache service system Sc to reduce unnecessary repeated n request from Sc . To analysis the performance of node behavior in DTN we build the following queueing mode
(See Figure.4)
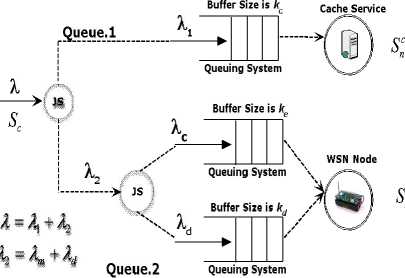
Figure.4 Queue Model for the Framework
Queue.1 The first queue is forSc , Sc is only for WSNs nn cache data packet, WSNs cache system is usually a data search operation, and we use M/D/1/K for this queueing model. The total service request rate is Я , Sc messages come to Sc queue at the rate of Я, PA is probability of n 11
getting data from Sc . So we can arrive at Я 1 = A g p 1 . As for this queue is rather easy, we will not go any further Queue.2 This queue is for S n . This queue is work for both WSNs control and data packet request, as for the service time of S n is usually with general distribution and it may be in the state of energy saving (node service in vacations states), we use M/G/1/K non-preemptive priority with vacations for this queueing model. Note that the real service is hosted in a WSN node, while the buffer is hosted in S n . All S c messages are firstly sent to a job scheduling system ( JS ). JS will check the message type and the time stamp to determine which queue the request should be forward to process.
In this model, we assume service request message types are classified in to n priority classes. Messages of each priority class i ( i = 1,2, K n ) arrive according to a
Poisson process with rate X i and to be served by Scn with a general service time distribution of mean x i and second moment xi 2 . To make the problem simple, we assume there are two priority classes in our model, the first one is control message, which is usually the control message sent by the administrators or some urgent message request, it comes with the rate of Xc ; the second one is data message, it comes with the rate of X d . The arrival Xc and X d are assumed to be independent of each other and service process. All messages comes at the rate of X 2 = Xc + X d . Xc is to be served by S n with a general service time distribution of mean xc and second moment X 2 . Pc is its traffic intensity or utilization factor. ^c is the service rate . Xd is to be served by S n with a general service time distribution of mean xd and second moment x d . p d is its traffic intensity or utilization factor. ^ d is the service rate. Then we can deduce the relationship among these parameters above in the followings:
X = X 1 + X 2, X = XgP 1, X 2 = Xc + X d
Pc = Xc gXc , Pd = Xd CXd , Pl = Л/Pl = Pc + Pd - X - X — ^ X^ x^ x=vgXc+ -fgXd, x2 = -gxgx2+ -d-gx2
X 2 X 2 X 2 X 2
Another import thing to be noted is S n may be in energy saving state in a DTN WSNs. In this state S n does not process any requests. Assume that V 1 , V 2 , K are the residual of S n ’s successive vacation time. The mean of vacation time V 1 , V 2 , K is V , and the second moment is V 2
R v
= lim
t ^ ” 2
For each M/G/1/K, given can the buffer size Ki [3]:
K i =
a
^^^^^e
m ( t )
Z V2
k = 1_______
C m ( t )
Z vk
v i 2
2 g vi
k = 1
block probability of Pk , we
a g b
2 g ln ( P i )
where i = c , d ,
a=- ln (PkK1- Pi+Pk gPi))+ln (Pi)
andS 2 is squared coefficient of variation of the service i process. Note that Ki can be hosted on Sn . The mean
residual service time Rs for all jobs in the queue [12] can be arrived:
n 2 n
Rs = ZPi ^ = 2ZXX i=1 ^ xi ^
So, the total residual service time ° [1] is i = Rv + Rs(2)
The waiting time of a job in class i is:
_______________i (3)
1 - Z Pk 11) 1 - zZ p .
k = 1 ) V
According the Little’s law, the average number of jobs in each class waiting queue is Nqi , and
M i = ХЙУ =--------XlC°
Nq XigfV i Z i-1 \ Z i\
| 1 - Z P k |c^ 1 - Z P k l
V k=1 7 V k=1
The total time that a job spent is Ti , and
B. Performance Analysis on Queue.2
Queue.2. is composed of two queues, one is for control (or urgent) message and the other one is for data message, both queues are M/G/1/K queueing system. Each node may be in power saving sate in DTN WSNs, the residual service time Rv in this state can be get by[1]:
Ti = Wi + Xi = -z------1----^-----i ----т + Xi (5
| 1 - Z P . 1 j1 - Z P k\ V k = 1 7 V k = 1 7
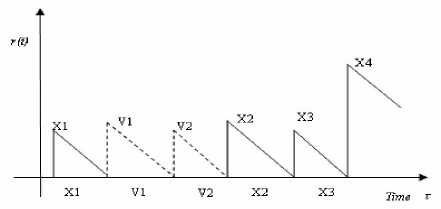
Figure.4 Residual Service Time for All Messages
K i , N q i , T i are very important initial parameters in node behavior in Fig.1. Let Tti denotes the maximum tolerant delay time, pki denotes the blocking probability. To guarantee Tti and pki constrained QoS, the following prerequisites must exist:
N i < K & T < T (6) qt
Then we can determine the initial parameters in Fig.1, P i , X i , ^ i etc.. Moreover, for a given specific framework, we can give its performance evaluation by our model as well.
C. Numeral Results and Analysis
To analysis the results that we have deduced above, we give the following initial parameters in the framework: x, = 0.01 , ст2 = 0.02 , x 2 = ( x ,) + ст, 2 ; x = 0.001 , d d d d dc
ст2 = 0.01 , x2 = ( x ) + ст2 ; V = 0.04 , ст2 = 0.01 , c cc c v
V = ( V ) + ст ^ ^ = 0.1 X 2 ,we get P k " P —Buffer Size
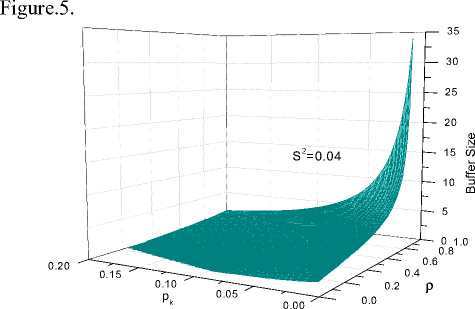
Fig.6 shows that with the increasing of p , Wc will also increase, but the wait time will be below than 1.4 second; while Wd will increase very fast, and the wait time will below 84 second. Given a specific ki and Tti , we can roughly get the range of p i , for the service time ^ .usually is known, then we can regulate S c ’s rate X to get the QoS guaranteed service.
V . E ND TO E ND P ERFORMANCE F LOW ANALYSIS
In a DTN WSNs, data is stored and forwarded by nodes along a path from source to destination.
S1 F’ A B E
F REQ
S2 F’’
F
O-
Figure.8 Data Transmitting in A DTN WSNs
RRPL
D
Figure.5 p k - p -Buffer Size Relationship
According to the equation (2)(3)(4)(5), by increase the value of X ,we will also get increased traffic intensity of the system p ,the we can get the queue size and wait time of each message with different priority, see Figure.6 and Figure.7
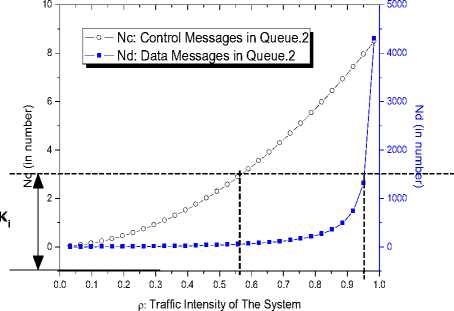
Figure.6 Nc and Nд with p
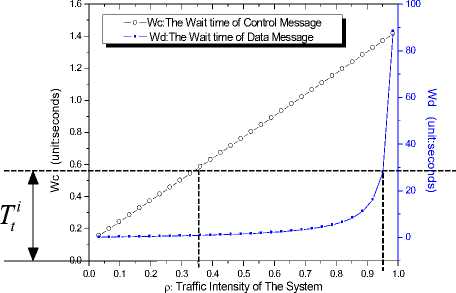
Figure.7 Wc and W j with p
To guarantee bounded delay end to end with zero packet loss, we use Stop-and-GO queueing as deterministic bounds (See Fig.). Stop-and-GO queueing was prompted by Golestani, S.J [13].
The Stop-and-GO queueing rules in our model are stated as follows:
-
(1) . Packet in incoming “Bundles” F ' and F '' are stored at node A, and cannot be forwarded until the beginning of the outgoing “Bundles” F following completion of “Bundles” F ' and F '' respectively.
-
(2) . A node should not stay idle or in pore is any eligible “Bundles” in the queue.
The total delay Dp end-to-end, for any packet by Stop-and-GO queueing is bounded by[13]:
(m - 1)T + T < dp < (ggm+1)T + T (7)
Where, m is the hops of the route, g = 2 , T . in equation(5) is the total time that a job spent in a node, T is propagation delay which is determined by the transmitting technology that use in WSNs. For example, T k in a Zigbee WSNs is great then that in a Wi-Fi WSNs.
To meet a specific TQoS , the up bound in equation (7)
must small than TQoS ,i.e.
(g gm+1)T + Tk < tqos
Then we get the hops in the transmitting route is bounded by:
m <
T
TQoS
- T - T.
ggTi
The lower bound of m is denoted by I m I , and the
maximum total hops h max ( t E [0, T qoS ]) in a route must meet:
hmax (t E [0, TqoS ]) = Lm J =
T qoS -T k -T g g T i
Equation (9) mean for any route Ri from source node ns to nd ’ hiE [1, hmax (t E[0, TQoS ])L is:
Etx (k, d ) = Etx - elec (k) + Etx - amp (k, d ) k gEelec + k £fx gd 2, d < d0 = ^
, k gE elec + k g^ mp gd 4 , d ^ d 0
Where, Eelec is the electronics energy, it depends on factors such as the digital coding, modulation, filtering, and spreading of the signal, as for the amplifier energy, £ fx gd 2 or £mp gd 4 , it depends on the distance to the receiver and the acceptable bit-error rate.
For the data receiving nodes in WSN, to receive this message, the energy consumption model is:
Maximum Hops
Erx (k) = Erx - elec (k) = kEec
л h (t e [0, Tn J) = m I = max ’ QoS L J
T qoS - T - T g g T i
0 10 20 30 40 50 60 70 80 90 100 110
Ti ( time of unit)
Figure.9 Data Transmitting in A DTN WSNs
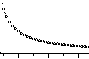
To evaluate equation (9), we give the following initial parameters T qoS = 1000 time unit, T k = 1 time unit; we get the relationship of h max against Ti in Figure. Fig shows that with Ti increasing h max drops rapidly.
-
B. The Determination of Optimistic Hops h *
From a global view, each node’s neighbor nodes should be determined by hops from source node to sink node and the distance of each hop.
Список литературы Modeling and Analysis on a DTN Based Wireless Sensor Network Topology Control
- .Santi, P., Topology control in wireless ad hoc and sensor networks. Acm Computing Surveys, 2005. 37(2): p. 164-194.
- .Zhang, L., X.H. Wang, and W.H. Dou, A K-connected energysaving topology control algorithm for wireless sensor networks. Distributed Computing - Iwdc 2004, Proceedings, 2004. 3326: p. 520-525.
- .Akan, O.B. and I.F. Akyildiz, Event-to-sink reliable transport in wireless sensor networks. Ieee-Acm Transactions on Networking, 2005. 13(5): p. 1003-1016.
- .Wu, Z.D., S.P. Li, and J. Xu, A topology control method for multi-path wireless sensor networks. Embedded Software and Systems, Proceedings, 2005. 3820: p. 210-219.
- .Ahdi, F., V. Srinivasan, and K.C. Chua, Topology control for delay sensitive applications in wireless sensor networks. Mobile Networks & Applications, 2007. 12(5-6): p. 406-421.
- .Konstantinidis, A., et al., Energy-aware topology control for wireless sensor networks using memetic algorithms. Computer Communications, 2007. 30(14-15): p. 2753-2764.
- .Ma, J., et al., Energy-efficient localized topology control algorithms in IEEE 802.15.4-based sensor networks. Ieee Transactions on Parallel and Distributed Systems, 2007. 18(5): p. 711-720.
- .Cardei, M., S.H. Yang, and J. Wu, Algorithms for fault-tolerant topology in heterogeneous wireless sensor networks. Ieee Transactions on Parallel and Distributed Systems, 2008. 19(4): p. 545-558.
- .Lillis, K.M., S.V. Pemmaraju, and I.A. Pirwani, Topology Control and Geographic Routing in Realistic Wireless Networks. Ad Hoc & Sensor Wireless Networks, 2008. 6(3-4): p. 265-297.
- .Luqun Li. and MinLe. Zuo. A Dynamic Adaptive Routing Protocol for Heterogeneous Wireless Sensor Networks. International Conference on Networks Security, Wireless Communications and Trusted Computing (NSWCTC 2009). Published by IEEE CS. 2009.04.
- .Luqun Li. and Jian Sun. Modeling and Performance Analysis on A Delay Tolerant Differentiated Wireless Sensor Web Service Framework. International Conference on Networks Security, Wireless Communications and Trusted Computing (NSWCTC 2009). Published by IEEE CS. 2009.04.
- .Smith, J. MacGregor.M/G/c/K blocking probability models and system performance. Performance Evaluation, v 52, n 4, May, 2003, p 237-267
- .Golestani, S.J., A stop-and-go queueing framework for congestion management. SIGCOMM Comput. Commun. Rev., 1990. 20(4): p. 8-18.
- .QING Li, ZHU Qing-Xin,WANG Ming-Wen Zhao Cheng A Distributed Energy-Efficient Clustering Algorithm for Heterogeneous Wireless Sensor Networks. Journal of Software.2006.3.
- .M.P., Wendi B. Heinzelman, “General Network Lifetime and Cost Models for Evaluating Sensor Network Deployment Strategies,” IEEE Transactions on Mobile Computing, Vol. 7, pp. 484-497,April .2008.
- .Rami Mochaourab, Waltenegus Dargie, “A fair and energyefficient topology control protocol for wireless sensor networks,” Proceedings of the 2nd ACM international conference on Context-awareness for self-managing systems, pp. 6 15, May. 2008.
- .M. Bhardwaj, T. Garnett, and A. Chandrakasan, Upper bounds on the lifetime of sensor networks, Communications, 2001. ICC 2001. IEEE International Conference on, 3:785–790 vol.3, 2001
- .Wei Cheng, Kai Xing, Xiuzhen Cheng, Xicheng Lu, Zexin Lu, Jinshu Su, Baosheng Wang, Yujun Liu, “Route Recovery in Vertex-Disjoint Multipath Routing for Many-To-One Sensor Network,” Proceedings of the 9th ACM international symposium on Mobile ad hoc networking and computing, pp. 209 – 220, May. 2008 .
- .N. Israr, I. Awan, “Coverage based inter cluster communication for load balancing in heterogeneous wireless sensor network,” Springer, pp.121-132, April .2008.
- .Li, L. A dynamic adaptive and robust routing protocol for wireless sensor networks. 2008. Piscataway, NJ 08855 1331, United States: Institute of Electrical and Electronics Engineers Computer Society.
- .Li, L. and M. Li, The Study on Mobile Web Service Computing for Data Collecting. 2004 International Conference on Communications, Circuits and Systems IEEE., 2004. Volume II: p. P1497~1501.
- .Yu, Y., L. J, and Rittle, Supporting Concurrent Applications in Wireless Sensor Networks. SenSys’06, November 1 3, 2006, Boulder, Colorado, USA., 2006: p. P139-152.
- .Whitehouse, K., F. Zhao, and J. Liu, Semantic streams: A framework for compostable semantic interpretation of sensor data. Proc. European Workshop on Wireless Sensor Networks (EWSN?6), Zurich, Switzerland (Feb. 2006).
- .Zhu, F., M.W. Mutka, and L.M. Ni, Service discovery in pervasive computing environments. Pervasive Computing, IEEE, 2005. 4(4): p. 81-90.
- .Delicato, F.C., et al., A flexible web service based architecture for wireless sensor networks. Distributed Computing Systems