Multicopy energy aware distance and inter-contact delay routing (EDICDR) approach for delay tolerant networks
Автор: Savita, D. K. Lobiyal
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 5 vol.11, 2019 года.
Бесплатный доступ
In this paper, we propose to optimize energy and overheads of a network by reducing the copies of messages in the network. The key idea behind the proposed scheme is to select the distance of encountered node from the destination to decide the relay nodes. This limits the number of relay nodes and thus reduces the communication energy and message overheads by producing lesser number of copies of the messages in the network. Further to maintain delivery of messages, the proposed protocol evaluates delivery probability of relay nodes. The measures of probability are inter-contact delay and variance in delay between the nodes. This probability is used to decide how many copies of a message is transferred to the encountered node. This further reduces the communication energy as well as message overheads. The simulation results show that our proposed strategy reduces message overheads and energy consumption as compared to the previous existing strategy while maintaining comparable delivery probability.
Delay tolerant networks (DTNs), Energy control, Opportunistic networks, Overhead, Routing
Короткий адрес: https://sciup.org/15015688
IDR: 15015688 | DOI: 10.5815/ijcnis.2019.05.05
Текст научной статьи Multicopy energy aware distance and inter-contact delay routing (EDICDR) approach for delay tolerant networks
Published Online May 2019 in MECS
Intermittent connectivity is the main challenge of DTNs. Due to this, the waiting time range may vary from seconds to days. It becomes difficult to establish connection between source and destination in such scenario. Most of the existing protocols depend on the techniques that use previous encounter history of nodes. These techniques produce multiple copies to improve the delivery of messages in DTNs, but introduce high overheads and consume lot of energy in communication. In this work, we aim at reducing energy consumption and message overheads using the inter-contact delay between nodes as well as shortest distance from the destination. Our proposed method considers the history of delay in delivering messages between nodes. This delay and its variance are used to calculate the probability of nodes to determine how many messages a node can deliver to a particular destination. On the basis of probability, we assign the number of copies of a message to the various nodes. We also choose only those nodes as relay nodes that have smaller distance as compared to encountered node from the destination.
Our proposed strategy reduces communication energy and message delivery overheads as it forwards lesser number of copies of a message. The numbers of copies of a message are reduced as it uses only a limited number of relay nodes and forwards more copies of a message to those nodes that have high chance of delivery, i.e. The node with higher delivery probability. An encountered node transfers p * I number of copies of a message to its neighbour node. Here, p represents delivery probability of the neighbour node and I represents existing number of copies at encountered node.
The rest of the paper is organized as follows: Section 2 explains the state-of-the-art techniques in the domain of DTN routing. Our proposed protocol EDICDR is discussed in Section III. We have presented simulation setup and the results in Section IV. Finally, Section V concludes the work presented in the article.
-
II. Related Works
A great body of work has been devoted to the area of DTN routing in the literature [1-17]. DTN has many routing algorithms, but they hardly consider the energy constraint. Most of the routing algorithms consider encounter information as a measure of relay selection. Few of the routing algorithms consider contact time [912]. In this work we focuses on time based and distance protocols. This category represents the protocols which select relay node on the basis of distance and time. Here time means the interval, duration, intermeeting time or inter-contact time etc. In 2013, Uddin et al. [18] proposed
an Inter-contact routing (ICR) protocol. In this protocol, messages are forwarded based on cost assessment of inter-contact delay and delivery probability. Li et al. [10] proposed SEDUM, is a multi-copy algorithm that uses less number of copies according to optimal tree replication.
Spyropoulos et al. [15] proposed seek-and-focus protocol, which depends on latest encounter time. The initial phase of protocol is seek phase. It changes to focus phase, if a better opportunity for destination node is encountered with the latest encounter time. Conan et al. [19] proposed 2-Multi-Hop (2-MH) by extending the Two-Hop-Relay protocol. Fixed point theory based routing uses average of inter-meeting time. This is a loop free recursive approach to minimize delivery delay. In this paper, they incorporate message forwarding time and region id to evaluate delivery probability of messages.
Here we define some distance based, direction based and map based protocols. Movement of vehicle (MOVE) [20] protocol uses the moving direction of nodes to decide the forwarding node delivery utility. This protocol selects the node as a relay node which moves towards the destination node. As the name suggests, Distance aware epidemic routing (DAER) [21] protocol uses the distance from the destination node as utility metric. This protocol also reduces the replication copies if the node is moving away from the destination. Delay Tolerant Link State Routing (DTLSR) [22] is an extension of classic link state routing. Each node maintains current view of the network and uses Dijkstra algorithm for finding the shortest route. As end-to-end path is not available in DTNs, DTLSR does not use hop count metric for shortest path estimation. It uses expected delay (MEED), introduced by Jones, et al. [23]. This is an approximate amount of time that the route may be available after the calculated delay. DTN hierarchical routing (DHR) [24] depends on the recurrent pattern of stationary node and mobile nodes. But in network like DTN which is highly dynamic it is difficult to maintain time variant hierarchical information. Mobility prediction based adaptive data (MPAD) [25] uses intersection of moving direction and transmission range of sink node. It assumes the stationary sink node. S. Dhurandher et al. [26] proposed a history-based prediction routing (HBPR) which observes the behaviour of nodes. It chooses the relay node by observing the moving direction of nodes using Markov predictors. B. Poonguzharselvi et al. [27] presented a mobile-trace based routing protocol using location information. Location information (direction) helps in making decision to select relay node. Each node uses trace file containing history of movements which is used to trace the direction of nodes. It also has a beacon message facility that contains node ID, location and timestamp to inform other nodes of its presence. In our proposed scheme, we take advantage of both types of approaches (i) time based (ii) distance based.
-
III. Proposed Protocol: Distance and InterContact Delay Routing (EDICDR)
In the EDICDR protocol, we proposed to improve upon the energy consumption by decreasing the number of copies of a message in the network. When nodes encounter each other, they calculate their respective distance from the destination. This calculated distance is used for the selection of relay nodes and delivery probability. This calculated information helps in deciding the number of copies to be forwarded to the relay node.
-
A. Incorporation of Distance Information
In the proposed protocol, shortest distance from the destination information is used for selection of relay nodes [28]. Therefore, by selecting the limited number of relay nodes using distance-information reduces energy consumption. The proposed EDICDR method ensures directional forwarding of messages using the concept of shortest distance from the destination.
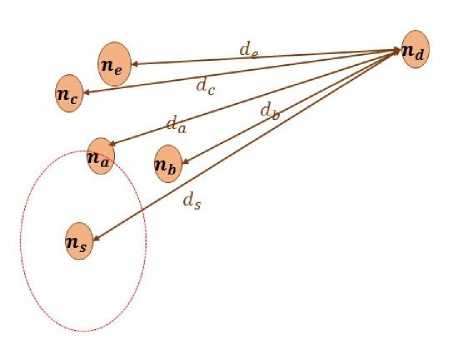
Fig.1. Distance Calculation from Destination Node n d
When a node ns (source node) comes into the range of node na, the protocol evaluates the distance of na from the destination node. If node na having distance smaller than the node ns, is considered as a relay node. It assumes that a node with the smaller distance from destination can be a good forwarder. This ensures that delivery of messages can be carried out by selecting appropriate relay nodes rather than forwarding messages to all encountered nodes. As shown in Figure 1, the distance between nodes is determined using the location information of the destination. The chance of delivery of messages through smaller distance nodes to destination is high. Therefore, only selecting a short distance node as a relay node, results in reduction of the number of copies in the network as well as reduction in the communication energy and overheads.
-
B. Inter-contact Graph
Most of the existing routing protocols use encounter graph in which each vertex represents a node and edge represents an encounter between nodes. Our proposed model also uses inter-contact graph of the network. An inter-contact graph is associated with recurrent pattern. A pattern is recurrent, if nodes encounter frequently within specific period of time. Figure 2 shows the method of relay selection and transfer of copies of a message to relay node. Here da and db shows the distance of node na and nb from the destination respectively.
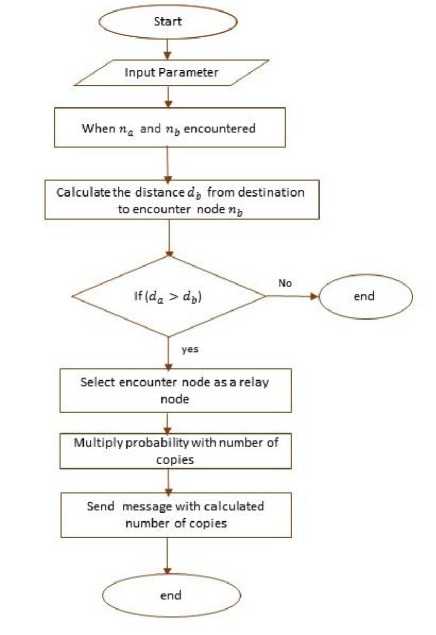
Fig.2. Flow Chart for Relay Selection and Decision of Number of Copies
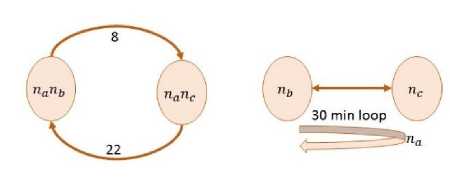
Fig.3. Representation of Inter-contact Graph and Recurrent Scenario
C. Delivery Probability Calculation using ICR
The proposed protocol consists of path delay and its variance for the destination node пд . In Inter-contact routing, these values are reflected as delay distribution parameters. Using these delay distribution parameters, we can measure the cost of a path. This cost estimates the paths using low delay and delay variance.
Message independent path cost is defined as [29]:
cost = d
a
(n
a
Tl
b
| ^ w) +
1.65V
This model uses inter-contact graph which represents intermeeting time between nodes, rather than a common encounter graph. In inter-contact graph vertex signifies the encounter between nodes and edges signifies the delay between two nodes. Each edge, nanb ^ nanc maintained by two values (6(nanb ^ nanc), ( O"2 ^ nanc)), where 6 (nanb ^ nanc) is the average delay incurred between nodes na encounters node nb and then node nc , and, (c2 ^ nanc) represents associated variance in delay. Inter-contact graph path is symbolized as |^. For example (nanb | ^ пд) is a path from node na n b to П д . Path delay is represented as 6 (nan b | ^ П д ) and path variance as o2(nan b | ^ П д ) [29]. For example, consider a team of volunteers which takes round of 30 mins in a city and comes back at same point. It passes two stops П ь and nc approximately in 8 mins distance. According to given scenario, na (volunteers) meets П ь and after 8 mins, it meet nc . When it meets nc after 22 mins it meets to nb again because it’s a 30 mins loop for a city. In inter-contact graph as shown in Figure 3, the direct edge from nan b to nanc reflect 8 mins distance and direct edge from nanc to nan b reflect 23 mins distance. In inter-contact graph, delay depends on previous nodes as well as next nodes.
Each vertex (nanb) concern with both the routing tables of nodes, i.e. node na and node nb for vertex (^ a ^ b ).
When two nodes na and nb encounter each other, they update the routing table for vertex nanb. Let assume that node nb encounters node na . Node nb revaluates the optimal paths for all possible destinations.
For every neighbour l € Sb , mean delay, variance and cost are computed [29] as follows:
delayl = 6(пьпа ^na^ + db(nbl ^ nw)(2)
varl = ff2(nbna^nbl’) + ffb2(nbl^nw^(3)
cost = delay l + 1.65^varl(4)
Where S b represents the group of neighbours of nb.
The estimation of optimal cost is as follows:
l * = arg min i es ,i #na cost i (5)
delay l * and varl * are sent by node nb to node na. This works as a mean delay and variance for destination nwvia nb . Node na updates its routing table with d(nanb ^ пд) = delayl and o2 (nanb ^ пд) = varl . Similarly, node na updates the routing table of node nb . After that delivery probability Pc is evaluated separately for all its neighbours n c as follows:
Pc= P{0 < delay < TTL /delay > 0}
P c =
/ TTL-delayc
-Jv^c
l—V—detayc'
V0(
-
detoyc
) ) У
^""k /
where ф(.) represents the related distribution function of normal distribution. D. Replication decision
We assume that there is some defined number of initial copies of every message. On encounter with intermediate nodes, a node forwards some copies to them according to their delivery probability value. Suppose a node na has a message with
Nc
copies to be transferred to nd, and it comes in contact with
пь
Each encountered node
пь
is allocated
P(b,(T) * Nc
copies and these allotments are deducted from
Nc.
This continues until
Nc
runs out. We consider two possibilities for node
n
,
[30]:
Case 1
:
Nc
finishes out before, we dispense allotment of
n
,
’s.
It refers to the fact that there are satisfactorily superior nodes ahead of
пь
. No copies are forwarded to П
ь
.
Case 2
:
Nc
finishes out, we dispense
n
,
’s allotment. Here,
пь
gets
P
(b, d) *
Nc
copies or remainder of
Nc
if the remainder is lesser than
P(b, d) * Nc
.
IV. Simulation Setup and Results In this work, we have evaluated the performance of EDICDR for different mobility models and also compared its performance with ICR protocol. The simulation parameters considered for comparative analysis are summarized in Table 1. Table 1. Simulation Parameters
Parameters
Values
Number of Copies of a
40
message
Number of Nodes
100
Seconds in Time Unit
60 sec
Initial Energy
300J
Scenario End Time
12000 Time Unit
Scenario Number of Host
1
Group
Bluetooth Interface Type
Simple Broadcast Interface
Transmit Speed
250kBps
Buffer Size
5 M
Waiting Time
0.120 Time Unit
Message Sizes
500 kb – 1 MB
World's Size for Movement
4500, 3400
Models
Message TTL
300 minutes (5 hours)
A. Evaluation of EDICDR Protocol
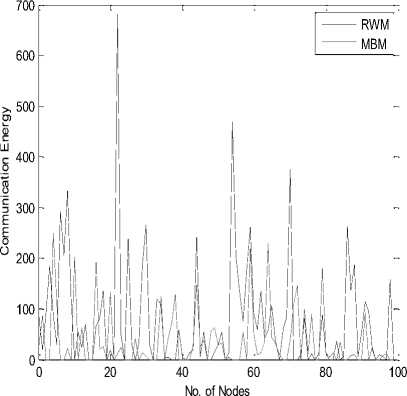
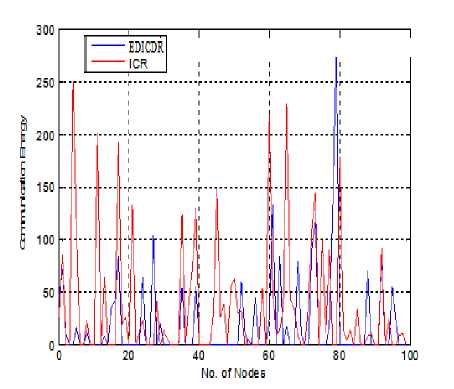
This section illustrates the performance of EDICDR protocol. We have evaluated EDICDR protocol with two different mobility models- Map Based Movement (MBM) model and Random Way Movement (RWM) model to find where EDICDR protocol performs better. Figure 4 shows the performance of EDICDR protocol for both the mobility models. Results show that in RWM most of the nodes consume more energy in comparison of MBM because it does not capture well the recurrence inherent in mobility patterns of nodes. Fig.4. Comparison of RWM and MBM (EDICDR) Fig.5. Communication Energy Comparison of ICR and EDICDR
B. Comparison of EDICDR and ICR
As discussed in previous section, ICR forward the copies of a message to each of its neighbours according to the probability as calculated. Our scheme focuses on the reduction of communication energy and overheads by reducing the number of copies in the network. We give direction the delivery of packets towards the destination.
C. Communication Energy
We evaluate the communication energy of EDICDR for the same simulation parameters as given in Table 1. Figure 5 shows energy consumption by each node in EDICDR. Energy consumption (per byte) is based on the message size that can be calculated as follows: Receiving/transferring message m given as
E
req
=
m. size
* energy per byte (7)
Ereq
shows required energy to transfer the message m.
Energy required by each node is much less for EDICDR as compared to ICR. It shows that the direction based forwarding can give better results in energy constrained environment.
D. Number of Initial Copies
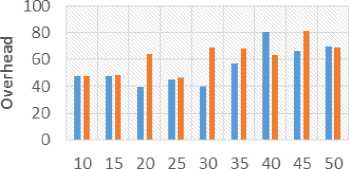
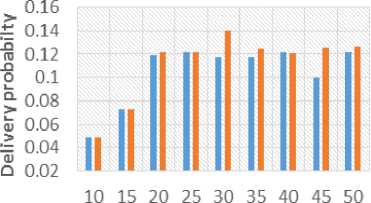
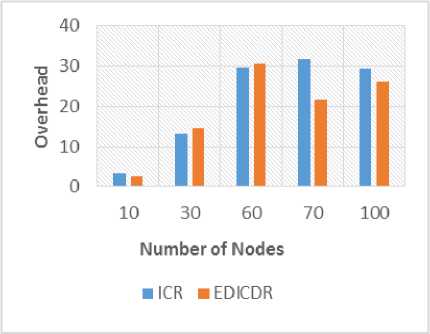
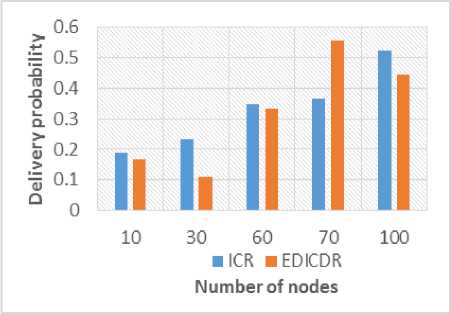
We have also computed overhead ratio and delivery probability with varying number of initial copies of a message as shown in Figure 6 and 7. In most cases (20, 25, 30, 35 and 45 initial copies), there has been considerable reduction in the overheads as shown in Figure 6. This happens due to the smaller number of copies of the messages exist in the network. Lesser number of copies of the messages reduced significant amount of overheads used in communication. Figure 7 shows delivery ratio versus initial number of copies. EDICDR have equal or reduced delivery probability. But it can be concluded that this factor is not much affected as forwarding number of copies of a message depends on the probability of encounter node. It is also observed from Figure 6 that the overhead of EDICDR and ICR increases with the increase in the number of initial copies. In Figure 7 delivery probability of proposed protocol also increases. But after a limited number of copies, it shows the constant delivery probability. This means after a limited number of copies, it only increases overheads in the network and delivery probability of messages does not improve. Therefore, the decision of initial number of copies also demands an attention of researchers. Number of initial copies ■ EDICDR elCR Fig.6. Overhead Vs. Initial Number of Copies Numberof initial copies ■ EDICDR ■ ICR Fig.7. Delivery Probability Vs. Initial Number of Copies First, the performance of ICR and EDICDR is compared in terms of overheads for varying node density. It is observed from the Figure 8 that there is a considerable reduction in the overheads for EDICDR strategies. Fig.8. Overhead Vs. Number of nodes Therefore, it can be concluded that in resource constrained networks, our proposed EDICDR protocol performs better. Figure 9 depicts delivery probability for different number of nodes. It can be observed here that the suggested strategies have maintained delivery probability. It has also been observed that in ICR, overheads increases sharply when number of nodes increases. But EDICDR is able to maintain the overheads except for case four with 70 nodes. It means for dense network there may be a good possibility, if we incorporate distance based approaches. Fig.9. Delivery Probability Vs. Number of nodes
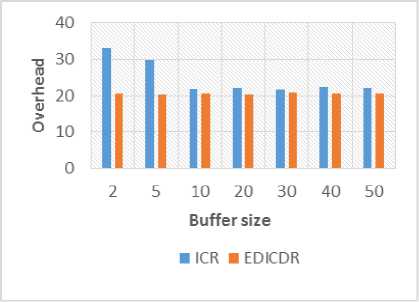
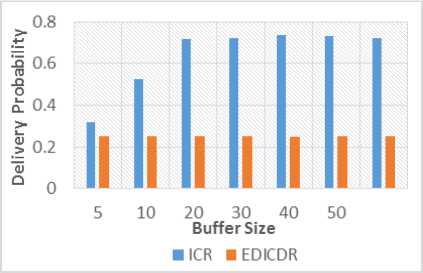
E. Buffer Size
In the case of the fourth simulation, we have compared the overheads for variable buffer size as presented in Figure 10 and Figure 11. Similar to the first observation, Figure 10 also shows note-worthy reduction in the overheads for additional strategies for all the cases. The delivery ratio for varying buffer sizes is shown in Figure 11. In accordance with the above-mentioned reasons, the delivery probability of the proposed protocol is lesser or equal as compared to other protocols. It has also been observed that after a limited buffer size both the protocols show constant results because it is possible to store messages for long lime. This decreases the drop rate. Fig.10. Overhead Vs. Buffer size Fig.11. Delivery Probability Vs. Buffer Size Fig.12. Overhead Vs. Message size Fig.13. Delivery Probability Vs. Message Size
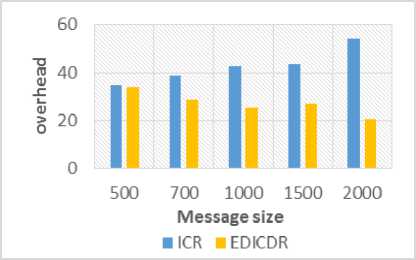
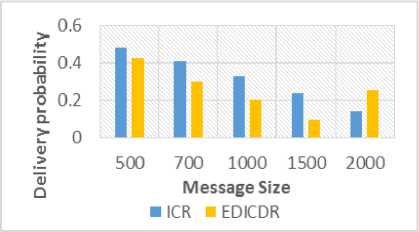
F. Message Size
Figure 12 shows relationship between message overheads and message size. It can be clearly seen from the Figure 12 that EDICDR performs better for the varying message size. Figure 13 shows the relation between delivery probability and message size. Results shows EDICDR performs better as compared to ICR. V. Conclusions Our Simulation results suggest that, smaller number of nodes with higher delivery probability can lead to reduction in the communication energy. Some nodes consume higher energy and receive or transmit lesser number of messages in ICR. This is because these nodes do not use direction towards the destination and thus have lesser chances to deliver the messages. Therefore, in EDICDR, we have sent smaller number of copies of a message to them. This saves the energy used in communication process. Further, in EDICDR overheads are smaller and maintained delivery probability as compared to ICR. But for energy constrained applications like disaster response networks, it should be our primary concern to reduce energy consumption and increase the lifetime of the network. In future, we will attempt to explore other location based schemes which can provide better direction of delivery towards the destination. Further, a better buffer management scheme that improves the delivery of messages can be incorporated in future.
Список литературы Multicopy energy aware distance and inter-contact delay routing (EDICDR) approach for delay tolerant networks
- M. J. Khabbaz, C. M. Assi, and W. F. Fawaz, “Disruption-tolerant networking: A comprehensive survey on recent developments and persisting challenges,” IEEE Commun. Surv. Tutorials, vol. 14, no. 2, pp. 607–640, 2012.
- S. Jain, K. Fall, and R. Patra, “Routing in a delay tolerant network,” ACM SIGCOMM Comput. Commun. Rev., vol. 34, no. 4, p. 145, 2004.
- A. E. Al Fagih and H. S. Hassanein, “Routing Schemes for Delay - Tolerant Networks - An Applications Perspective Technical Report 2012-588,” no. December 2010, 2012
- P.R. Makawana, & R.H. Jhaveri, “Encounter record trust-based scheme against flooding attack in delay tolerant networks”, Vol. 9, no. 4, pp 399–409, 2017.
- “Time Evolving DTN.” [Online]. Available: http://www.engr.uconn.edu/~tehrani/teaching/CE_Seminar/Farahmand.pdf.
- Y. S. Uddin, N. G. Ave, D. M. Nicol, and R. H. Kravets, “A Post-Disaster Mobility Model for Delay Tolerant Networking,” pp. 2785–2796, 2009.
- Z. and D. S. Zhang, “Routing in Intermittently Connected Mobile Adhoc Networks and Delay Tolerant Networks: Overview and Challenges,” pp. 24–37, 2006.
- P. Puri, “A Survey Paper on Routing in Delay-tolerant Networks,” pp. 215–220, 2013.
- H.;Weihua Z. Samuel, “‘Unauthorized Messages in DTN Based Mobile Ad Hoc Networks’,,” in IEEE Procedding of Global Telecommunications Conference, GLOBECOM, 2009.
- Li Z, Shen H (2013) SEDUM: Exploiting social networks in utility-based distributed routing for DTNs. IEEE Transactions on Computers 62(1): pp.83-97..
- J. Shen, S. Moh, and I. Chung, “Routing Protocols in Delay Tolerant Networks: A Comparative Survey,” pp. 1577–1580, 2008.
- W. Zhao, M. Ammar, E. Zegura, and C. Computing, “A Message Ferrying Approach for Data Delivery in Sparse Mobile Ad Hoc Networks Categories and Subject Descriptors,” pp. 187–198.
- S. Merugu, M. H. Ammar, and E. W. Zegura, “Routing in Space and Time in Networks with Predictable Mobility,” Time, no. iii, pp. 1–13, 2004.
- A. Vahdat and D. Becker, “Epidemic Routing for Partially-Connected Ad Hoc Networks.”
- T. Spyropoulos, K. Psounis, and C. S. Raghavendra, “Spray and Wait: An Efficient Routing Scheme for,” Direct, pp. 252–259, 2005.
- A. Lindgren, A. Doria, and O. Schelén, “Probabilistic routing in intermittently connected networks,” ACM SIGMOBILE Mob. Comput. Commun. Rev., vol. 7, no. 3, p. 19, 2003.
- C. Becker and G. Schiele, “New mechanisms for routing in ad hoc networks through world models,” pp. 1–4.
- M. Y. S. Uddin, H. Ahmadi, T. Abdelzaher, and R. Kravets, “Intercontact routing for energy constrained disaster response networks,” IEEE Trans. Mob. Comput., vol. 12, no. 10, pp. 1986–1998, 2013.
- V. Conan, J. Leguay, T. Friedman, “Fixed Point Opportunistic Routing in Delay Tolerant Networks,” IEEE J. Selected Areas Comm., vol. 26, no. 5, pp. 773-782, 2008.
- J. LeBrun, C.N. Chuah, D. Ghosal, and M. Zhang, “Knowledge-based opportunistic forwarding in vehicular wireless ad hoc networks,” in IEEE VTC ’05-Spring, Stockholm, Sweden, 2005.
- H. Huang, W. Shu, M. Li, and M.-Y. Wu, “A mobility prediction-based adaptive data gathering protocol for delay tolerant mobile sensor network,” in IEEE GLOBECOM ’08, New Orleans, Louisiana, USA, 2008.
- M. Demmer, and K. Fall, “DTLSR: delay tolerant routing for developing regions,” in ACM NSDR ’07, Kyoto, Japan, 2007.
- EPC Jones, L. Li, JK Schmidtke, PAS Ward Practical Routing in Delay-Tolerant Networks. IEEE Transactions on Mobile Computing 6(8):943-959, 2007.
- C. Liu and J. Wu, “Scalable routing in delay tolerant networks,” in Proc.ACM MobiHoc, 2007.
- J. Zhu, J. Cao, M. Liu, Y. Zheng, H. Gong, and G. Chen, “A mobility prediction-based adaptive data gathering protocol for delay tolerant mobile sensor network,” in IEEE GLOBECOM ’08, New Orleans, Louisiana, USA, 2008.
- S. Dhurandher, D. Sharma, I. Woungang, and S. Bhati, “HBPR: History based prediction for routing in infrastructure-less opportunistic networks,” in 2013 IEEE 27th Int. Conf. Adv. Inf. Networking and Applications (AINA), Barcelona, pp. 931–936.
- B. Poonguzharselvi, and V. Vetriselvi, “Data forwarding in opportunistic network using mobile traces,” CS and IT-CSCP, pp. 425-430, 2012.
- Y. Ko and N. H. Vaidya, “Location-Aided Routing ( LAR ) in mobile ad hoc networks ∗,” vol. 6, pp. 307–321, 2000.
- M. Y. S. Uddin, H. Ahmadi, T. Abdelzaher, and R. Kravets, “A Low-energy, Multi-copy Inter-contact Routing Protocol for Disaster Response Networks,” 2009 6th Annu. IEEE Commun. Soc. Conf. Sensor, Mesh Ad Hoc Commun. Networks, pp. 1–9, Jun. 2009.
- Savita and Lobiyal, D.K. (2015) ‘Location information in inter-contact based routing approach in delay tolerant network’, Proceedings of the 3rd International Conference on Recent Trends in Computing, IRCTC Procedia Computer Science, Vol. 57, No. 1, pp.1367-1375.
- A. Keränen, T. Kärkkäinen, and J. Ott, “Simulating Mobility and DTNs with the ONE (Invited Paper),” J. Commun., vol. 5, no. 2, pp. 92–105, Feb. 2010.
- A. Keränen, J. Ott, and T. Kärkkäinen, “The ONE simulator for DTN protocol evaluation,” Proc. Second Int. ICST Conf. Simul. Tools Tech., 2009.
- X. Liu and Y. Chen, “Report of A DTN Simulator - THE ONE,” no. January 2011, pp. 1–8, 2013.


