Named Data Networking: Investigate of New Infrastructure for Future of Internet
Автор: Hadis Rezaei, Asad Vakili
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 1 vol.9, 2017 года.
Бесплатный доступ
The Internet main goals are largely achieved, majority of using Internet, are data retrieval and access to services. Whereas host-to-host architecture is designed for applications. According to this problem that existing Internet is like a tree of physical equipment which is established to outflow in packets from each leaf to another leaf, despite having effective communication it has problems in scalability. Also the content-centric network can recognize large amount of information that is produced for first time and used after saving it. The change is using of host-to-host-centric to completely new architecture, that its design represents our understanding of strengths and limitations of architecture of the existing Internet. In NDN applications based data and Content-centric networks, packets are retrieved according to their names instead of their source and destination addresses. This performance is for scalability, security and ease access to data. This paper discussed methods of Internet architecture based data including TDRID, DONA, Netinf, CCN, and NDN.
Content-centric networking, the future Internet architecture, NDN, Data plan, scalability
Короткий адрес: https://sciup.org/15011740
IDR: 15011740
Текст научной статьи Named Data Networking: Investigate of New Infrastructure for Future of Internet
Published Online January 2017 in MECS
-
I. Introduction
Humans are associated with several networks of people, objects and thoughts. Infrastructure of the internet was founded as one of the most comprehensive and the most popular networks in late 1960s and early 1970s, and today we observe it is intertwined with human life. This network which is based on IP uses the host - to- host communications and aims at sending each packet to destination from shortest path. Internet design is inspired by types of communication in that time, such as mail, telephone and telegram. The popularity and wide acceptance in the world of internet, causing rapid and unexpected growth in this network, so that we have seen popularity among billions of users. The Internet has evolved to be concentrated on content distribution. Especially in recent years, with the rapid development of access network bandwidth, most of the content on the Internet exist as information-intensive form like video or audio [1]. That changed the role of Internet. In fact communications from host-to-host mode was changed to Few-to-Many communication, meaning that a lot of member’s uses multi produced limited content. Film
distribution shared networks (such as YouTube), online television, real-time contents and press conferences and many types of this application are good evidence for this change. Nowadays the information is known as a highest reason of existing internet but not the location of information. In fact, users are looking for shortest possible time to earn their content no matter where and from whom. With the emergence of the World Wide Web, the primary use of the Internet is content distribution, primarily in the form of web pages, but increasingly audio and video streams as well. Some measurements indicate that 70 to 80 percent of wide-area Internet trac is HTTP trac. Much of the remainder consists of RealAudio streams and DNS [2, 3].
Nowadays the volume of hardware devices that are connected to the internet as well as applications and media which have been observed in this network are developed and spread. So that media such as photo and sound form very large mass of users' requests. However, all these developments about the utilization of the Internet, there is not enough attention to find appropriate solutions responding to these requirements. Howbeit this structure belongs to several years ago. Internet structure is similar to clothing store in which if someone visit a branch of it in his city and couldn’t find his favorite wear, he should refer to central office or central branch where is too far from his city for finding his favorite clothes. The same scenario for all customers is much more important than this. Clearly this structure faces serious problems to answer content distribution system (CDN) because the focus is on communication instead of content. Thus, requirement to a new and different attitude to the current structure and protocols is completely felt till these kinds of weaknesses to be removed. Despite some efforts to respond these requirements such as CDN, or technologies based on p2p we need to change foundations of the network. Philosophy of network's birth based on information or briefly ICN is the same. The recently proposed Named Data Networking (NDN) architecture[4.5.6].
In fact the goal of networks like this is highlighting the role of content and making retrieve of information easy with less overload and higher speed. NDN architecture used levels network aims to providing direct support for software, data-oriented network and storage opportunities in the, client-centered communication model. And a combination of building blocks that includes encryption and signature in order to improve security in the outgoing data packets.NDN prominent features like the ability to caching data, transmittal data and rapid cause has been popularity of these networks.
In this paper, in section 2, it's explored the various internet architecture, and then in section 3 an overview of the NDN will be scanned. In Section 4 the NDN architecture principles will be studied. In Section 5, IP and NDN will be compared. And at the conclusion, the development of based-content network and structure of the NDN network is investigated.
-
II. An Overview of Different Architectures of the Internet
This section is a summary of some current approaches in future architecture of the Internet, including TARID, NetInf, DONA and CCN.
-
A. CCN architecture
The original design of CCN was offered in 2009. Concept of CCNA includes the consumer's request that sends to receive information. Some special nodes route in the network and each node includes a cache memory that has a copy of the requested information, and in particular occasions uses this information to find the main applicant of data.The main concept behind CCN is that the request is generated by the consumer for the Information object (IO) which is then routed in the direction of that location in a network where that IO is been available. There are certain nodes that are traversed on the path which leads towards the producer [7].
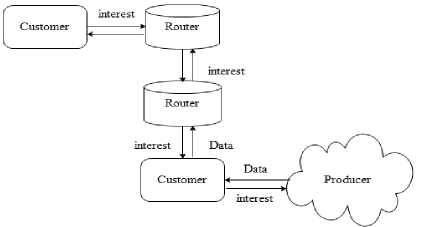
Fig.1. Content-Centric Networking [8]
-
B. TRAID architecture
One of the first efforts to achieve data-centric networks is related to the project TRAID that was started in 1999 by the Stanford University . The main incentive of creators of TRAID, was paying attention to traffic volume of HTTP in that time (Which was around 70 to 80 percent of Internet traffic) and also obviating the needs of IPV6 and deal with the lack of address space. In order to reach this goal they tried to bring the requests of HTTP to the nearest source by starting an overlay network based on IPV4 so the answer would be achieved in the shortest possible time. main purpose was notify routers about its content using header of exchanged packet content , So that they effect on the routing.
The other possibility, most notably used in TRIAD is to route-by-name to the closest copy.[9]. Because of intensive effect of IP routing and TCP operation this method practically was not useful. Researchers who proposed the idea claim that necessity for using IPV6 will be removed by using IPV4 and NAT and also proper implementing of TARID. TRIAD too advocates use of DNS names as global identifiers to uniquely identify each end host from any context[10].
-
C. DONA architecture
In 2006 the DONA project appeared at University of California, Berkeley with an architecture based on content which allowed to customer to order via name of data instead of address. DONA is built on name-based routing as is advocated in TRIAD which was arguably the first to explore the benefits of diverging from the classic lookup-oriented Internet [9].
Architecture the names in DONA are organized based on particular principles [9]. This project started with the problem of services and access to data and it considers how to achieve sustainability, availability and authentication of identification. In this network the purpose was routing to be done based on name of content so each request would be delivered to the nearest person who has its content and the main purpose was to eliminate the necessity of searching DNS for every request. After finding the content, a one-to-one TCP connection will be establish between the applicant and the data source so the data is transferred between the two nodes however this plan failed too.
-
D. PSIRP architecture
Project PSIRP, the result of several academic institution that was introduced in 2008. PSIRP architecture is composed of three major parts: the architecture of protocols, network architectures, and service model [11], which are subject to principles such as [12] the nature of the return on the semantics of information and the information domain as a concept accessible.
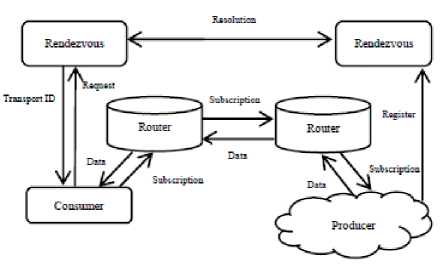
Fig.2. Public Subscribe Internet Routing Paradigm [8]
-
E. Netinf architecture
Information-centric networking (ICN) is a promising approach to networking that has the potential to provide better – more natural and more efficient – solutions for many of today’s important communication applications including but not limited to large-scale content distribution [13].
The project was presented as another data-centric network in research projects in 2008 at the Portland State University . The main objectives of this project include data modeling, naming the content and searching by content rather than routing. For this purpose, with utilizing distributed hash table (DHT) method and search algorithm called Chimera it was tried to speed the operation of searching name. In NetInf the data are broadcasted and numbered within the network and ask help from name resolution service (NSR) and Net locator. When a consumer asks to retrieve a data this request will be classified by NSR and rest of the process is based on locators because they retrieve via bigger sources after using a version of them for requested data.
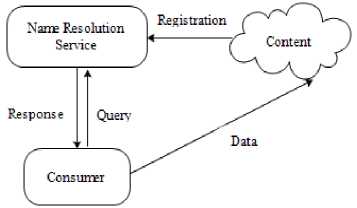
Fig.3. Network of Information [8]
-
III. An Overview of Data Structure of NDN
NDN is a receiver-driven, network-layer communication protocol. This section gives a concise overview of the NDN architecture. A more detailed description can be found elsewhere [14,5]. NDN architecture is similar to IP except a thin waist hourglass that fundamental changes have happened in this architecture via replacing name with address. Whole communication in NDN is done by two types of packets(Figure 4), interest packet and data packet, which carry a name that is Individual identifier of a data that carried by data packet. In addition to its name each Interest Packet has an Option Selector that will be a specific description about transmitted data, and Nonce field is a random number which is produced by consumer to prevent produced loop. In addition to its name a Data packet has a signature that has been made by producer. The signature will make consumer certain about authenticity of sent data.
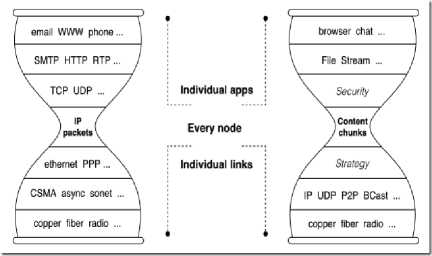
Fig.4. IP and NDN Hourglass Architecture, reused from [6]
Similar to delivery of IP packet, the NDN network has the best effort in retrieve of data. Unlike the approach of IP to deliver data which is based on address, carrying of data in NDN packet is based on name which cause two main differences. First the location of storing data considers mid router rather than just destination address in IP packet. Secondly Interest Packet carries both name and address to identify consumer which can be used by Data packet while returning to applicant. NDN router has registered this information via name of requested data in the entrance interface of PIT table.
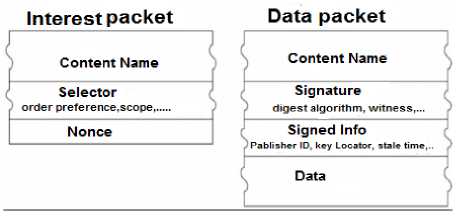
Fig.5. NDN Packets from [15]
-
A. Components of NDN router
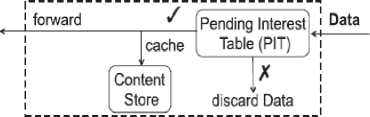
NDN is a receiver-driven, data-centric communication architecture, where all communications in NDN are performed using two distinct types of packets: Interest and Data.[15]. To implement the Interest and Data forwarding functions, each NDN router maintains three major data structures: a Forwarding Information Base (FIB), a Pending Interest Table (PIT), and a Content Store (CS) [16].
FIB in NDN router is similar to FIB router in IP except that NDN used the prefix name to search but in IP prefix of address is considered. PIT table kept all interest packets that have not been answered yet. Each PIT entrance includes the name and interface of incoming and out coming too which handles the registration time of sending forwarded interest. CS provides temporary network storage for incoming data. NDN router is equipped with FIB module that determines how and when forwarding and storing data should be performed.
Figure (6) describes forwarding process in NDN. Hence first the consumer sends an Interest packet with a name that has explanation of considered data [1]. When router receives Interest packet first it examines content of cache memory or CS then if there is requested data in CS, the data will be forwarded to consumer otherwise the PIT table will be examined and if there is a name according to requested data in the entrance of PIT it means that data is asked by that consumer or another consumer so a new interface will be added to entrance of PIT [13]. If forwarding process was successful in NDN router then data packet will be forwarded to consumer. Each interest carries a random Nonce with itself that is produced by consumer to recognize and prevent loop and not to receive repeated interest.
In addition to the name, Data packet uses a signature which contains bonding name. Names in NDN architecture are hierarchical and have variable length. NDN routers to forward the interest packet use scheduler RTT. If in RTT time the consumer doesn’t receive data the interest will be retransmitted. the name carried into Interest packet is similar to IP address, But a copy of it stored in the middle router or data repository so when data is returned to the consumer it can be used. Interest Packet hasn’t the consumer's name and address that is why NDN router in its incoming interface of every Interest packet records information of each packet for matching with consumer.
Interest
Content Store
Data ^
x X
Pending Interest
" Table (PIT) П
FIB
/ forward
X
drop or NACK
add incoming interface
Downstream Upstream
X lookup miss / lookup hit
Fig.6. Interest and Data processing in NDN [14]
-
IV. Ndn Architecture
NDN architecture-based request, which means that all communication starts by the applicant and not begin any connection from the server, In other words, NDN is a receiver-driven architecture with a focus on the name associated data. In this section have an overview of the NDN architecture with a focus on design modalities directed at NDN.
-
A. Principles of architecture in NDN
The new internet design is made sophisticated and powerful by “hourglass architecture” because it hubs on a universal network layer (IP) applying the marginal functionality which is compulsory for worldwide interconnectivity [8].
NDN networks are new and popular model’s that use naming data instead of IP-based communication. Changing in the usage of host-centric to data-centric applications (NDN) is a completely new architecture that its design indicates our perception of the strengths and the limits of existing Internet architecture.
-
B. Names
NDN names are opaque to the network, i.e., routers do not understand the meaning of the names [16]. Moreover these names in NDN are hierarchical. For example, the thesis is written in this format edu/esfhan/cs/chengyi/ thesis.pdf. where ’/’ indicates a boundary between name components. This hierarchical structure has two advantages. First applications can put the content and the relationship between pieces of data in to the name. For example, Section 1 of version 2 of this thesis cannot be named as edu/esfehan/cs/chengyi/dissertation.pdf/2/1/. Secondly aggregation of name in scalability of system in routing id necessary. For example University of esfehan independent in NDN can be with prefix name /EDU / esfehan/ through routing protocols in a distributed way similar to the distribution of IP prefixes in the internet.
-
C. Routing and Forwarding
Named Data Networking (NDN) [4], [6] is an Internet Architecture proposed that modify communication model network of point-to-point retrieval data packet, in which the benefits, consumers sent interest to fetch data[17]. NDN architecture naturally from consumer mobility through stateful forwarding design. Packets in NDN are routed and transmitted by name. Thus unlike IP architecture, NDN has not problems related to address. Because first of all the problem of space exhaustion of IP address is not exist anymore by using unlimited space in NDN. Secondly, in the required routing system there isn't problem of NAT mensuration in public and private addresses. Common routing algorithms such as Link -State or Path-Vector in the NDN can be used. Instead of prefix IP, NDN router announces name prefixes that are willing to serve the routing protocols. And the other routers find their FIB according to routing information. Routing traditional IP protocols like OSPF can be easily adopted via name prefix [14]. Considering hierarchical names with obscure components, router can do the longest prefix match for interest name against FIB.
-
D. Datagram State
NDN router has entry in the PIT table for each pending interest packet, thus say that routing have "state datagram". This will lead to flow the packet, in two symmetrical path. There is a link between a balance of each packet in a data packet is interest only, unless the packet lost or there is no matching data.
It is noteworthy that the datagram NDN fundamental difference with the virtual circuit to the ATM or MPLS. in a virtual circuit is created first, a single route between a pair of input-output routing. When connection disappears It must be repeated again for the entire route, Second, if the virtual circuit link with traffic overhead due to be closed in the same virtual circuit due to the mismatch cannot be delivered But in the case of NDN datagram routers at each step to direct the decision favorites. When routing or link failure. This failure is only the effect on the interest in the specific location and the previous step can quickly detect failures at the site.
-
E. Caching
NDN routers use packet buffers that already exist in IP routers as caches; a cache hit means reduction in bandwidth usage. With a reasonable caching policy, we expect NDN networks to perform better than IP for static data, and no worse than IP for dynamic data, in reducing both bandwidth demand and original server load. We discuss how we will address four caching issues. First, we will investigate cache replacement policies for NDN routers. While prior work on this subject suggested that a least-recently-used (LRU) or least-frequently-used (LFU) policy would be desirable, we hypothesize that a far simpler random replacement policy would perform nearly as well. We plan to study this issue both analytically and experimentally we will base any more advanced schemes on a rich set of literature on caching [18].
Storing with the name of data may increase privacy protection concerns in IP. In fact, the packet of destination address can be found by exploring the header. NDN prevents network to be frankly displayed of network to see requested data by explicit naming of data and it solved this problem approximately.
-
F. Network Security NDN
The proposed architecture must be inherently secure. IP-based network poses security at entirely foreign additions and data structure is not safe. NDN using signature Thin waist hourglass, as inherent to secure all communications and exchanged the packets.
-
G. Create a competitive environment
The proposed structure should facilitate competition and choice for users one of the common behaviors that can be seen on the Internet competition among the various groups and parties rival. So find an organization dominated by the passage of time and more resources from the Internet, increase competitive advantage and accounts greater share of network, So we can say that the Internet is not neutral structure. NDN has its best efforts to respond to this problem in order to power users and between them creation of competitive atmosphere .
-
H. The development of architecture NDN
NDN protocol features to industry-standard formats needs to data and interests packets. The standard format for describing network layer functions that are essential to support them. Build operating networks NDN, requires software libraries to the name, transmit and effective routing, reliable support strategy and management. These libraries as part of IP support (allocation, Address, protocols, routing and DNS) are not part of the core architecture. But naturally support it. This explains the format of the application based on this architecture can be improved and be designed with them.
-
V. Comparing IP and NDN
With the advent of new applications such as ecommerce, digital media, social networks and smart phones, Internet connections are becoming increasingly oriented to content. Current Internet with the limitations facing these problems include: Requires DNS system to convert addresses to names, Lack of cache, Lack of support for of multicast IP that caused the delay and IP is secure against malicious attacks. Although many efforts have been devoted to securing the communication channel, but is still significant security breach. As a result, Jacobson et offered data centric network for Addressing constraints and better communication patterns. In this section we discuss the most important internet failure to reach the motivation and the main reason of introducing data-centric networks for replace with the data-centric networks. And determine the advantages of NDN networks by comparison with IP.
-
• Scalability: Scalability means that system whose performance improves after adding hardware, proportionally to the capacity added, is said to be a scalable system. The shortage and finishing address space of IPV4 and the routing and forwarding issues considering high speed growth of connectors and information, as well one dimensional looking at the nodes and lack of attention to the potential for cooperation between them has challenged the scalability of the internet.
-
• Security : Internet Protocol Security is a protocol series for secure Internet Protocol (IP) communications that works by authenticating and encrypting each IP packet of a communication session. Internet Protocol Security includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to be used in the session.in the routing, the security of routing, BGP security and identity authentication between ordinary users (such as usage of VoIP) are open problems that no universal solution has presented yet.
-
• Cooperation: One of the greatest Internet
shortcomings is the lack of using potential for cooperation between the nodes in the network (for example, distributing a specific content or issues such as congestion control and load sharing). In fact in the network-based IP no matter our neighbors are able to return the content that we're looking for. The only usage of them is sending requests and responding.
And the only use made of them, and that is the sender requests and responses. This attitude cause ignoring a potential source, to reduce network traffic and improve response time.
-
• Mobility: In the current Internet and IP-based networks in general we cannot move a server from one place to another place without manual reconfiguration.
-
• Redundancy: why the neighbors of node should pass the Same way when the node can earn its content from another point using time and network source.
-
• Multicast: IP based internet couldn’t implement multicast by itself. In all above problems in relation with IP-based networks; NDN network could partly remove some of these problems using some policies which some of mentioned issues are shown in the following table by comparing.
Table 1. Comparison between IP and NDN
|
Property |
NDN |
IP |
|
ID |
Content Name |
IP Address |
|
Type of packets |
Data Packet/Interest Packet |
Several packages |
|
Loop |
Essentially without loops using nonce |
Not guarantee |
|
Hop count |
Can predict several steps |
The only predicts a next hop |
|
Forwarding Strategy |
YES |
NO |
|
Separating routing and forwarding |
YES |
NO |
|
Control traffic |
There is In architecture there hourglass |
There isn't In architecture there hourglass |
|
State |
Stateful |
Stateless |
|
Fault detection |
YES |
NO |
|
Convergence Time |
Little |
Much |
|
Load Balancing |
YES |
NO |
|
Security |
Using signature packet is secure |
Using extensions like Spec |
-
VI. Challenges Related to the Issue
Today, computer networks are constitute part of the needs of individuals and organizations. And due to rapid growth of applications and lack accountability of the traditional way to design a scalable network that can more quickly and better service quality to satisfy the needs of users of computer networks is a major challenge.
In this regard, efforts in progress to provide the technologies, protocols and procedures are different. Introduced a new network NDN method
That can increase the power of response in addition to references in large networks also work.
NDN designs are many indicate a new architectural designs and unique opportunities and challenges. NDN networks despite having immense benefits to network IP, are faced with many challenges. Design architecture in this network its infancy. Since internet architecture has been built it is changed significantly. So that these changes were associated with its original application. Generalization of the Internet architecture with a focus on content rather than focusing on the end point address is considered as a major advance. But this new architecture proposed with a focus on "name data" on the basis of simple changes. Hence recognizing a set of research problems to develop and validate is necessary. It's an intellectual challenge including routing scalability to search name, fast transmission of packets based on hierarchical name with variable length, and drawing reliable and usable model for data security, privacy protection.
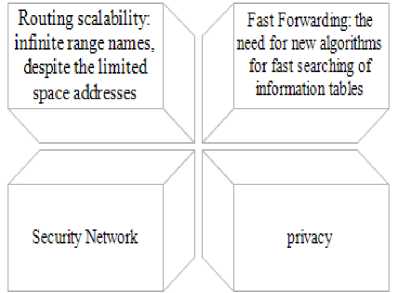
Fig.7. Challenges in NDN
-
VII. Related Work
In fact, we can track many basic ideas on NDN architecture in the design and testing different ways over the past 20 years and before then.This effort early in the design IP multicast routing, design scalable and reliable multicast, Implementation of web storage and TRIAD project is named for the content. In recent years, many attempts to design data-centric network architecture, there has been richer and literature. This is includes data-oriented network architecture, and publishing, Internet sharing, routing paradigm PSIRP. 4WARD project is also developing a data-driven architecture, but with a focus on higher level issues of modeling and abstraction. Now with using DONA style for data and publish / subscribe style provides API. The attempts is designed to secure Internet architecture, and enhance network architecture to support network bearable [19,20,21,22].
-
VIII. Conclusions
Nowadays according to various usage of internet it can be claimed progress in this area has unique value and can significantly affect the whole world. Considering the position of this issue on global level internet architecture is an important challenge, so with a suitable design users can share with each other in a safe environment far away from the stress. Hence designing a new architecture can significantly solve architecture problem using a simple design and easy solution only focusing on the "what" (content) instead of "Where" (address end point), and this architecture is able to reach a great success in this area by presenting solution. In this paper a summary of new Internet architecture is presented which called "named data networking” which was based on a very simple change. Also overview of some of the current Internet architecture methods is proposed. Recognizing and outlining research problems concerning the NDN, can be useful in developing and validating of this new architecture. The main challenges include fast transportation, scalability (routing on the name), signature, trust model (for data-centric security), privacy and content protection, network security, So considering offered communication theories by selecting appropriate solutions in search of name and rapidly sending packet would help better results in the growth and having dynamic network.
Список литературы Named Data Networking: Investigate of New Infrastructure for Future of Internet
- C.Forecast, et al, Cisco visual networking index: Global mobile data traffic forecast update 2009-2014. Cisco Public Information, February, 2010.
- C. Kimberly, G. Miller, and K. Thompson. "The nature of the beast: Recent traffic measurements from an Internet backbone." Proceedings of INET. Vol. 98. 1998.
- S. McCreary, & K. C. Claffy,. Trends in wide area IP traffic patterns. (2000).
- V.Jacobson, Smetters, D. K., Thornton, J. D., Plass, M. F., Briggs, N. H., & Braynard, R. L. (2009, December). Networking named content. In Proceedings of the 5th international conference on Emerging networking experiments and technologies (pp. 1-12). ACM.
- L. Zhang, Deborah Estrin, Jeffrey Burke, Van Jacobson, James D. Thornton, Diana K. Smetters, Beichuan Zhang et al. "Named data networking (ndn) project." Relatório Técnico NDN-0001, Xerox Palo Alto Research Center-PARC (2010).
- ME. Mosko, JJ. Garcia-Luna-Aceves, inventors; Palo Alto Research Center Incorporated, assignee. Multi-publisher routing protocol for named data networks. United States patent US 9,363,179. 2016 Jun 7.
- A. Carzaniga, P. Michele, and L. Alexander. Wolf. "Content-based publish/subscribe networking and information-centric networking." In Proceedings of the ACM SIGCOMM workshop on Information-centric networking, pp. 56-61. ACM, 2011.
- Z. Ahmad, & M. Tahir,. Named Data Networking (NDN), (2013). new approach to future Internet architecture design: A survey. International Journal of Informatics and Communication Technology (IJ-ICT), 2(3), 155-165.
- D. R. Cheriton., & M. Gritter,. TRIAD: A new next-generation Internet architecture. (2000).
- S.Paul, J. Pan, & R. Jain. A survey of naming systems: classification and analysis of the current schemes using a new naming reference model. (2009). WUSTL Technical Report, available at http://www. cse. wustl. edu/~ jain/papers/naming. htm.0001, Xerox Palo Alto Research Center-PARC
- L.Wang, et al., OSPFN: An OSPF based routing protocol for Named Data Networking. University of Memphis and University of Arizona, Tech. Rep, 2012.
- M. Ain, et al., Conceptual architecture of PSIRP including subcomponent descriptions. PSIRP project, Deliverable D, 2008. 2: p. 2.
- C. Dannewitz, D. Kutscher, B. Ohlman, S. Farrell, B. , Ahlgren,., & H. Karl,. Network of Information (NetInf)–An information-centric networking architecture. (2013). Computer Communications, 36(7), 721-735.
- V. Jacobson, D. K .Smetters, J. D. Thornton., M. F. Plass, N. H. Briggs, & R. L. Braynard,. Networking named content. (2009, December). In Proceedings of the 5th international conference on Emerging networking experiments and technologies (pp. 1-12). ACM.
- C. Yi, A. Afanasyev, I. Moiseenko, L. Wang, B .Zhang, &, L. Zhang,. A case for stateful forwarding plane. (2013). Computer Communications, 36(7), 779-791.
- C. Yi, A. Afanasyev, L. Wang, B. Zhang, & L. Zhang,. Adaptive forwarding in named data networking. (2012). ACM SIGCOMM computer communication review, 42(3), 62-67.
- Y. Zhang, A. Afanasyev, J. Burke, & L. Zhang, A Survey of Mobility Support in Named Data Networking. In Proceedings of the third Workshop on Name-Oriented Mobility: Architecture, Algorithms and Applications (NOM'2016).
- J. Wang,. A survey of web caching schemes for the internet. (1999). ACM SIGCOMM Computer Communication Review, 29(5), 36-46.
- The psirp project. http//www.prisp.org/publication
- S. Deering and D. Cheriton. Muticast routing in internetworks and extended LANS. In Proceedings of SIGCOMM 1998.
- L.Zhang, S.Deering, D. Estrin, S. Shenker and D. Zappala. Rvsp: A new resource reservation protocol. In IEEE Network, September, 1993.
- L. Zhang, , D. Estrin, J. Burke, V. Jacobson, J. D. Thornton, D. K., Smetters, & T. Abdelzaher, Named data networking (ndn) project. (2010). Relatório Técnico NDN.
- A. MAJIDI, H. MIRVAZIRI. BDCC: Backpressure routing and dynamic prioritization for congestion control in WMSNs. I.J. Computer Network and Information Security; 2014, 5, 29-34.


