Performance Analysis of Route Discovery by Cross Layer Routing Protocol- RDCLRP
Автор: Mehajabeen Fatima, Roopam Gupta, T.K.Bandhopadhyay
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 8 vol.5, 2013 года.
Бесплатный доступ
Wired and wireless network is based on the TCP / IP architecture but it is not sufficient to cope with the dynamics of the MANET. Cross layer design can be an alternative architecture for MANET. Frequent route break is one of the major problems of mobile adhoc network (MANET). Path breaks due to less available battery power and mobility of nodes. Most of the battery power is consumed in flooding of control packets. A key challenge in the design of efficient routing protocol is to reduce link breakage and flooding of control packets. Route breakage can be reduced if the possibility of route breakage is predicted and a handoff is done without drop of data packets. If route breakage is reduced, the more battery power will be available with nodes. In turn it reduces the possibility of route breakage and the possibility of flooding. This is a cumulative effect. So a novel preemptive route repair algorithm is proposed named as RDCLRP- Route discovery by cross layer routing protocol to reduce frequency of control packet flooding and route breakage. Three variants of RDCLRP and their results are illustrated. In this paper, the impact of the number of nodes on performance of RDCLRP are investigated and analyzed. The results show 55.6% reduction in link breakage, 14.7% improvement in residual battery power and an average of 6.7% increase in throughput compared to basic AODV.
MANET, AODV, Cross layer design, route repair, HELLO, ANH, FUZZY
Короткий адрес: https://sciup.org/15011218
IDR: 15011218
Текст научной статьи Performance Analysis of Route Discovery by Cross Layer Routing Protocol- RDCLRP
Published Online June 2013 in MECS
The wired and wireless network is based on the TCP / IP architecture and it is successful worldwide. TCP/IP was originally designed for wired links, characterized by high bandwidth, low delay, low probability of packet loss, high reliability, static routing and no mobility [1]. But in the wireless links, performance and resources are limited by the time-varying channel, the limited availability of the transmission spectrum, the employed modulation type and the limited transmission power [2, 3]. TCP/IP is a hierarchical model in which each layer of the protocol stack operates independently and exchanges information with adjacent layers only. But a strict layered design is insufficient to cope with the dynamics of adhoc networks. So instead of using TCP/IP, cross layer architecture can be a more promising architecture for adhoc networks. Cross-layer design (CLD) breaks the traditional network design, in which information is exchanged among all layers without following any hierarchy of protocol stack [4, 5]. The performance is optimized by adapting each layer. Cross-layering breaks the boundaries between information abstractions to improve performance of the network. The careful exploitation of cross-layer protocol interactions can lead to more efficient performance of the protocol stack [6, 7]. All layers depend on each other and any change on any layer will propagate to all layers. Thus cross layer design can be an alternative but unbridled design may lead to negative results [8]. CLD is used to combine the resources available at the different layers. This creates a highly adaptive network by sharing information among different layers in the system.
In MANET, links between nodes are frequently created and broken due to mobility of nodes. This node mobility affects the source, destination and intermediate nodes due to the networks multihop nature. Many links break after a short time period but their short lifetime is propagated through the network and degrades the performance [9]. The route establishment has been already expensive in MANETs. The short lifetime of the route and rapid routing changes are challenges of the network. The link stability is a tough job when constructing a path, or designing a routing protocol. The high node degree creates a multitude of routing options [9].
In section II review is given, section III discussed problem statement, section IV discussed about proposed algorithm, section V, VI and VII have given variants of the proposed algorithm, section VIII talk about results and analysis. The final conclusion is given in part IX.
II REVIEW
There are many cross-layer design proposals in the literature. A brief survey of different cross layer architectures is given in Table1.
In this paper, the basic concept of cross layer approach is used for implementation of the proposed routing protocol. With the emerging technologies and the popularity of wireless communication, users are increasing day by day. This induces more traffic and data in adhoc network. However, the limited performance of routing protocol becomes the principal factor that restrains large and continuous flow of traffic. Traditional routing protocol selects a route with the smallest hop count. This implies a large distance for each hop results in low link data rate. So the throughput for the route can be low. [12] Xiaoxin Wu et. al. said that the link data rate can be increased if the route has hops of very short link distance. They studied the link distance impact on network throughput in Multirate multihop wireless networks. They built mathematical models for analyzing the throughput in different network scenarios. They concluded that by changing the link distance to an optimum value, the highest throughput can be achieved. It was also observed that a link distance optimum value highly depends on network load density. When the network load density is low, the optimum link distance should be short. Otherwise, the optimum link distance should be longer.
Whatever changes are proposed in the network affects application layer parameters like throughput, end to end delay etc. [13] Chi Pan Chan et.al. investigates the many-to-one throughput capacity of IEEE 802.11 multihop networks, in which many sources send data to a sink. They considered that the source node is just one hop from the sink, the system throughput can approach to Ls, where Ls is the throughput capacity of an isolated link consisting of one transmitter and one receiver. They approached the problem by the partitioning. Allocate some link capacity lies at the sink in the one-hop source nodes and then determine the throughput for the source nodes that are two or more hops away based on the remaining capacity L = (1 — a)La . The throughput of the one-hop nodes will be around Ls. This paper investigated the extent to which the remaining capacity L can be used efficiently by the source traffic for two or more hops away. Investigation of different canonical networks is given in the paper. By proper selection of routes near the gateway, the throughput can be improved to a very large value. They also concluded that deactivating some of the relay nodes near the sink in a dense network can lead to a higher throughput.
Table 1 Brief survey on cross layer architectures
|
Author Name |
Issues discussed |
Basic principle |
Pros |
Cons |
|
Vineet Shrivastava, Mehul motani [6] |
A survey of different proposed cross layer design in literature is given |
How TCP/IP architecture violation can be possible. |
The very good survey is provided |
Only survey is given, the implementation is not discussed |
|
Vijay T. Raisingahani and Sridhar Iyer [10] |
An ÉCLAIR local-view-based cross layer architecture is proposed |
Legacy protocol stack consists of two main components: an optimizing subsystem and tuning layers. The cross layer engine contains many protocol optimizers. Different tuning layers are included in the TCP / IP architecture. These tuning layers are new interfaces. New interfaces are included at different layers. |
Tuning layers provide the necessary APIs to the protocol optimizers. Protocol optimizer interacts with various layers and manipulates the protocol data structures. |
This architecture requires new interfaces. |
|
Marco Conti, Gaia Maselli, Giovanni Turi and Silvia Giordano [11] |
A mobile Man architecture is proposed |
This architecture works on energy management, security and cooperation. A network status is provided to communicate with all layers. All layers can communicate with network status. Network status is like a repository. |
Whenever a protocol in the stack collects information, it will publish this to the repository and thus making it available for every other protocol. |
The Mobile Man reference architecture is just a proposal so far, no performance analysis exists to back up their claims. |
After the establishment of path, the path may break due to node mobility and scarce battery power. So route has to be repaired for further transmission of data. A number of schemes are proposed to handle this problem. [14]Luca Mottola et. al. present COMAN protocol to organize the nodes of a MANET in a treeshaped network able to self-repair. This tolerates the frequent topological reconfigurations of MANETs. This minimizes the changes that impact the CBR layer through repair strategies.
If path breaks then it is repaired with the help of control packets. It is fine to repair the route after the path break. But this hampers continuity of flow of data. So this type of protocol cannot be used for real time communication. So it is required to design the protocol that can be used for both real time and non real time communication. When a node goes out of transmission range, handoff is more promising alternate. [15] Han-Chieh Chao et.al proposed a hand off enhanced extension to the IETF MIPv6 scheme that reduces packet loss at a high-speed handoff rate.
They also considered security in the proposed mechanism. The handoff mechanism is helpful for the real-time traffic in MIPv6. The basic idea is to promote performance when handoffs take place at high speeds. This overcomes the large delay of binding scheme using the proposed prebinding scheme. The new access address NAA can help the mobile node undergoing a handoff to overcome the bad communication environment and to produce successful handoff. A number of assumptions have been taken in this paper so it does not give a proper solution for handoff.
If a route discovery uses a large number of control packets then the performance of protocol cannot be good. This may also result in path disconnection. Many researchers have tried to reduce control packets. [16] Song Guo et.al. proposed a novel on-demand routing protocol called Backup Source Routing (BSR) to establish and maintain backup routes that can be utilized after the primary path breaks. The key advantage of BSR is the reduction of the frequency of route discovery flooding. They define a new routing metric called the route reliability. They use it to provide the basis for the backup path selection. A heuristic cost function is used to develop an analytical model and an approximation method to measure metric. Various algorithms for BSR protocol in the route discovery phase and route maintenance phase have been proposed based on a cost function. The simulations demonstrated that BSR can improve the performance in lower mobility as well as in high mobility.
Energy is one of the scarcest resources in MANET. The conservation of energy is very important. According to Subir Halder et.al., the energy can be conserved by avoiding the problem of occurrence of energy holes [17]. It ensures prolonged network lifetime. It is investigated that the problem of uniform node distribution is incapable to deal with the energy hole problem. They derived the principle of nonuniform node distribution that ensures energy balancing. They have also developed a non-uniform, location wise predetermined node deployment strategy to increase the network lifetime.
-
III PROBLEM STATEMENT
Because of movement of nodes, topology changes frequently. If speed is more and node moves out of transmission range then route will break soon. So route breakage depends on the speed and direction of a node. The dynamic nature of MANET results in unpredictable and considerable changes in the network. This adds the difficulty in searching and maintenance of the route. Thus, establishing communication among mobile nodes is a big task. The challenge in designing a routing protocol is to adapt to the conditions of adhoc network. The On-demand routing protocol uses the flooding method to find a route to the destination [18,19]. RREQ packet is broadcasted for searching of the path. After the establishment of route, path is maintained by broadcast of control packet. When a node goes out of reach, route breaks and route is again searched with the help of the flooding of the RREQ [20]. Consider the situation where mobile nodes broadcast a RREQ message to neighboring nodes. The neighbors may rebroadcast this RREQ message to their respective neighbors. Packet collisions may occur over the wireless medium, resulting in congestion and possible loss of routing control packets. The source node may attempt to recover from loss of routing control packets by initiating another route discovery process. This increases traffic, overhead and reduces battery power in the network which results in route breakage. This is a cumulative effect. In order to maintain a high throughput over a MANET, it is important to reduce the route breakage. In this paper, a novel extension of the AODV routing protocol for mobile ad hoc network is proposed.
RDCLRP- Route discovery using cross layer routing protocol is proposed. AODV is taken as the base routing protocol and it is modified. RDCLRP is a preemptive route repair reactive routing protocol. The RDCLRP works on the prediction of the route breakage. The old route is replaced by new route before route breakage.
-
IV PROPOSED ALGORITHM
The route is searched through flooding of RREQ. If a node has route or is destination itself then it sends RREP. Then the route is established. The established path is called as active path and nodes participating in data communication are called active nodes. All active nodes call speed, RSS, consumed battery power value at the network layer. If speed or RSS value or battery power consumption crosses its threshold then that active node is said to be critical node. Now the critical node does not send periodic HM, rather HM is broadcasted as a Hello warning message (HWM). HWM is sent only when a node touches the threshold. Direction of a node can be predicted by RSS present at MAC layer which is called at the network layer. The position of a node depends on the speed of a node and the speed is called at the network layer. The residual battery power is parameter of hardware, this hardware parameter is called at the network layer, and this is the cross layer approach.
The critical node sends a Hello warning message (HWM) to warn the nodes that the link is going to break after some time. This HWM is broadcasted so that neighbor node can hear it [21]. HWM consists of addresses of its both active neighbors (precursor and next active node) which are participating in the transmission of packets. Precursor active node is renamed as a previous active node. Neighbor nodes hear the warning message and they will see the address of active neighbor nodes of critical node in its routing table. If neighbor node is having the addresses of both active neighbors then it will reply to critical node by sending Hello reply message (HRM). The node which replies first will participate in new route. Then critical node sends service replicate message (SRM) to the active previous and next nodes and new node from whom HWR arrived. The SRM consist of new node id and active neighbor node id. Now the old route will be replaced by new route before link breakage. So a new route is discovered through HWM. Critical node searches the route locally and tries to do preemptive route repair before link breakage. So instead of sending RERR, RREQ and RREP messages, only a warning message is sent as HWM. This message is sent only once whenever it is required. Because of this link breakage reduces, power will be less consumed, the delay will be less and overhead reduces, ultimately an improvement in throughput.
In this work, RDCLRP and variants are proposed for reduction of route breakage, which are discussed in further sections.
RDCLRP variants
-
1. RDCLRP with HELLO or HELLO
-
2. RDCLRP with active nodes HELLO or ANH
-
3. RDCLRP with active nodes HELLO and FUZZY Logic or FUZZY
V ROUTE DISCOVERY BY CROSS LAYER ROUTING PROTOCOL WITH HELLO (RDCLRP-H) OR HELLO
Route discovery by cross layer routing protocol with HELLO (RDCLRP-H) is abbreviated as HELLO. In this protocol, a route is discovered by RREQ and RREP. As soon as RREQ is broadcasted, nodes hear it and start transmitting periodic HM. The neighbor nodes hear HM and do the entry of an IP address of neighbor nodes in its routing table. After path establishment, nodes start transmitting data. If a node becomes critical, the new node can be searched through above explained method. And route is repaired before path breaks.
VI ROUTE DISCOVERY USING CROSS LAYER ROUTING PROTOCOL WITH ACTIVE NODES HELLO (RDCLRP-ANH) OR ANH
Route discovery by a cross layer routing protocol with active nodes HELLO (RDCLRP-ANH) is abbreviated as ANH. HM is sent after every one second, it increases overhead and traffic in turn increases the possibility of congestion, consumes bandwidth unnecessary and most important consumes scarce battery power. Actually the nodes which are not participating in transmission of data, they are not required to tell about themselves. Thus it is not essential for most of the nodes to send HM. So in this proposed algorithm only active nodes are sending HM.
Because of this, power consumption of inactive nodes reduces. When these nodes will become active nodes later, they can utilize unused battery power and possibility of route breakage is reduced. This is the aim of ANH. In HELLO, most of the node sends HM but in ANH, only active nodes send HM.
Overhead reduces as less number of HM are broadcasted and less number of RREQ, RREP. Because of less number of link breakage, delay reduces, throughput increases. For justification of concept results are attached.
VII ROUTE DISCOVERY USING CROSS LAYER ROUTING PROTOCOL WITH ACTIVE NODES HELLO AND FUZZY LOGIC (RDCLRP-FUZZY)
OR FUZZY
Route discovery by cross layer routing protocol with active nodes HELLO and FUZZY Logic (RDCLRP-FUZZY) is abbreviated as FUZZY. Path is established through RREQ and RREP. Only active nodes send HM. If speed(S) varies then a node will go out of transmission range at different times. The life of a node depends on residual battery power. The increasing or decreasing value of received signal strength (RSS) gives information about the direction of node. If the node is in critical condition then HWM is generated but this HWM is not generated instantaneously. HWM generation depends on the value of RSS, Bp and S. So it is required to send HWM at different time i.e. HWM generation should be adaptive. Therefore HWM interval (HI) is made adaptive.
So it is decided to send HWM as per HI. This interval is decided on the basis of fuzzy logic. Fuzzy logic is a tool for mapping the input features to the output based on data in the form of “IF – Then” rules controller [22]. Here three input features are taken, namely RSS, Bp and S. Fuzzified input data trigger one or several rules in the fuzzy model to calculate the result. In this paper 27 rules are mapped. The rule table for calculation of HI is given in Table2. In the next section, we analyze the impact of node density in a fixed terrain on network performance parameters.
Table 2 Rule Table [22]
VIII RESULTS AND ANALYSIS
In this section, we analyze the impact of node density in a fixed terrain on RDCLRP variants. Simulations are done on Network Simulator- Qualnet 5.0. Following are scenario parameters:Simulation Time: 500sec, Number of Nodes:25- 100 Terrain: 1500m x 1500m, Seed=1, Packet interval:1 packet per Sec, Packet Size: 512byte, Link Capacity:2Mbps, Mobility Model: Random Way Point, Channel: Two Ray Propagation Model, Energy Model: Micaz, Battery model: Linear, Noise factor: 10db, MAC Protocol: 802.11, Speed: 20mps, Pause Time: 50s, Work frequency:2.4 GHz, Wavelength: 0.125m,
Transmission power: 15dbm, Receiver sensitivity: -91 dbm, antenna Gain: 0db.
In this paper, terrain and number of sources are kept constant and number of nodes is varying. As node density increases in a terrain, more nodes are available in coverage area and establishment of route will be fast. Thus more data can be received in a fixed simulation time and it increases throughput as shown in Fig. 1. When the node density increases, more nodes are transmitting periodic HM and neighbor nodes hear this HM. Maximum battery power gets consumed due to transmission and reception of packets. So possibility of route breakage increases with the increase in the number of nodes. If route breaks then source reestablish the route, this increases delay of packets to reach to the destination as shown in Figure 2. So less number of packets is received at destination at fixed simulation time resulting in less throughput. When traffic increases the throughput will be less and when node density increases, the throughput can be increased. Thus either node density dominates or traffic dominates the network. Thus throughput oscillates as shown in Fig 1. Throughput is maximum in FUZZY due to adaptive preemptive route repair. Average throughput is highest in FUZZY and minimum in AODV (refer table 3).
Table 3 Throughput Vs number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
Throughput |
||||
|
o.of node |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
9187 |
9231 |
10186.9 |
9410.8 |
|
40 |
11299.9 |
11312 |
10186.9 |
9410.8 |
|
60 |
8648.4 |
8649 |
8538 |
7747 |
|
80 |
7728 |
8248.7 |
8248.7 |
7002 |
|
100 |
9347.6 |
9385 |
10073.9 |
7974.8 |
|
S |
B p Low(L) |
B p Medium(M) |
B p High(H) |
||||||
|
RSS |
RSS |
RSS |
|||||||
|
L |
M |
H |
L |
M |
H |
L |
M |
H |
|
|
L |
L |
L |
L |
H |
M |
H |
H |
H |
H |
|
M |
L |
L |
L |
M |
M |
H |
M |
M |
H |
|
H |
L |
L |
L |
L |
L |
M |
L |
L |
M |
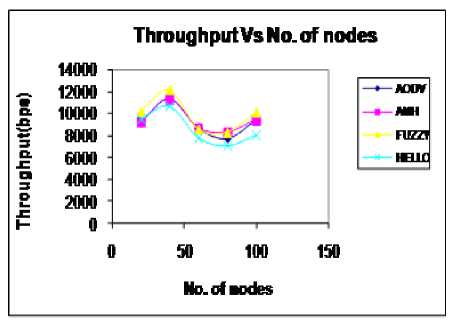
Figure.1 Throughput Vs no. of nodes
Jitter means time taken by packets to reach to the next hop. With the increase in the number of nodes, more packets have to transmit between two hops, so more processing or computing is required to do. Thus it takes more time to transmit packets between two nodes. Thus jitter increases with the increase in the number of nodes. For AODV jitter varies from 63msec to 116msec. For ANH it varies from 80msec. to 690msec. For HELLO it varies from 60msec to 108msec. In FUZZY, jitter varies from 50 msec to 108msec as seen in table 4. Jitter is least in FUZZY as shown in Fig.3.
With the increase of the number of nodes, number of control packet increases in the network and it increases the possibility of congestion, so packets will take more time to reach to the destination. Thus delay will be more as shown in Fig.2. But if link breaks, this hampers the continuity of data transfer and increases delay. But the route will reestablish in less time due to availability of nodes in coverage area, this decreases delay comparative to the less node density. This is shown in Fig.2. The average delay for basic AODV is 205.4msec, 194msec for ANH, 190.8msec for HELLO and 135msec for FUZZY. The delay is minimum in FUZZY. So FUZZY is good among the protocols.
Table 4 Delay Vs number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
DELAY(sec) |
||||
|
o.of nodes |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
0.185 |
0.199 |
0.148 |
0.163 |
|
40 |
0.148 |
0.14 |
0.137 |
0.141 |
|
60 |
0.215 |
0.231 |
0.19 |
0.25 |
|
80 |
0.279 |
0.2 |
0.1 |
0.2 |
|
100 |
0.2 |
0.2 |
0.1 |
0.2 |
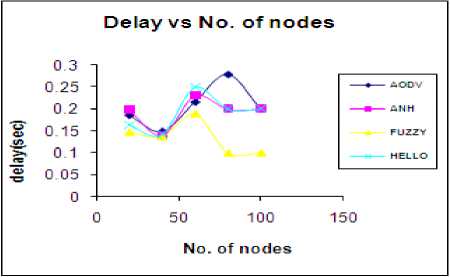
Figure.2 Delay Vs no. of nodes
Table 5 Jitter Vs number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
JITTER(sec) |
||||
|
o.of nodes |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
0.063 |
0.08 |
0.05 |
0.061 |
|
40 |
0.068 |
0.069 |
0.06 |
0.06 |
|
60 |
0.098 |
0.08 |
0.08 |
0.09 |
|
80 |
0.116 |
0.108 |
0.108 |
0.108 |
|
100 |
0.08 |
0.08 |
0.08 |
0.105 |
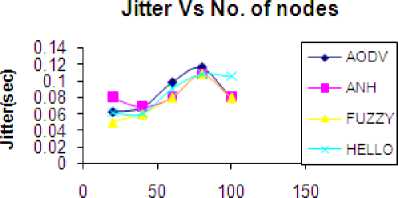
No. of nodes
Figure.3 Jitter Vs no. of nodes
Links on which data packets are transmitted and received are kept constant. With the increase in the number of nodes, control packets can be more, makes network prone to congestion. If route breaks, it can be repaired immediately because of availability of nodes in coverage area. This increases reception of packets as shown in Fig. 4. Sometimes immediate route repair is not possible due to congestion in route. This decreases reception of packets at a fixed simulation time. With the increase in the number of nodes received data packets can be reduced as shown in Fig. 4.
In proposed algorithm, the old route is immediately switch to new route before link breakage occurs. So the possibility of route breakage is less, in turn more packets are received at the destination. That’s why in
FUZZY, more number of packets is received. Fuzzy shows a 6.2% improvement compared to AODV as g iven in table 8.
Table 6 total number of packets received Vs number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
Total no.of pkts received |
||||
|
o.of nodes |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
1100 |
1001.1 |
1215.4 |
1129.7 |
|
40 |
1369.25 |
1371 |
1467.2 |
1286.7 |
|
60 |
1049.25 |
1101.1 |
1037.2 |
939.7 |
|
80 |
937.625 |
1001.6 |
1001.6 |
845.6 |
|
100 |
1136.57 |
1201.6 |
1220.6 |
967.3 |
|
No 2000 -1 * 1500 -f 1000 ■ | 500 - |
of received packets Vs No. of nodes |
|
|
—i— AODV —■—ANH FUZZY HELLO |
||
|
d |
100 200 No. of nodes |
|
Figure. 4 total number of packets received Vs no. of nodes
With the increase in the number of nodes ,load is distributed among all the nodes. So less load is available at the nodes. Thus node will do less transmission and reception and of course less processing. Therefore residual battery power (RBP) increases with an increase in the number of nodes. But in FUZZY, HELLO and ANH less number of control packets propagate in an area. Less power is consumed, thus frequency of route breakage reduces as shown in Fig. 5 and Fig. 6.
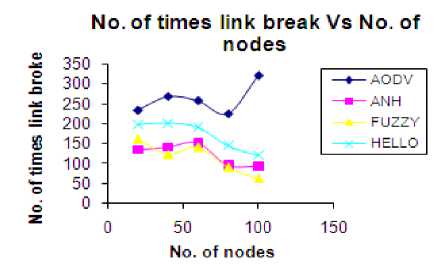
Figure. 5 No. of times link break Vs no. of nodes
But AODV is a protocol which does not take care of route break reduction. Route breakage is 55.6% less in FUZZY, 53.2% less in ANH and 34.5% less in HELLO as compare to AODV. This is shown in the table 8.
Table 8 Residual battery power Vs Number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
Residual battery power(%) |
||||
|
No.of nodes |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
2.3 |
2.84 |
2.45 |
1.4 |
|
40 |
2.4 |
2.9 |
2.95 |
2.7 |
|
60 |
2.5 |
2.69 |
2.9 |
1.9 |
|
80 |
4.8 |
5.1 |
5.4 |
3.98 |
|
100 |
6.3 |
6.9 |
7.3 |
4.84 |
Residual battery power Vs No. of nodes
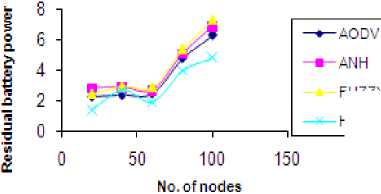
FUZZY
HELLO
Table 7 Number of times link break Vs Number of nodes
|
LINK=20, PAUSE=50s,Speed=20mps, ST=500s, 1500x1500m2 |
||||
|
no.of times link break |
||||
|
No.of nodes |
aodv |
anh |
fuzzy |
hello |
|
AODV |
ANH |
FUZZY |
HELLO |
|
|
20 |
231.85 |
132.8 |
161.4 |
196.1 |
|
40 |
266.8 |
139.2 |
122.3 |
199.4 |
|
60 |
256.1 |
150.6 |
140.7 |
189.5 |
|
80 |
222.9 |
93.3 |
90.3 |
144.2 |
|
100 |
319.4 |
90.5 |
61.2 |
119.7 |
Figure. 6 Residual battery power Vs no. of nodes
Percentage improvement for HELLO, ANH and FUZZY over basic AODV is shown in Table 9. HELLO does not show good performance with respect to increase in number of nodes in a fixed terrain, ANH performs average but FUZZY performs well. All performance parameters are improved in
Table 9. improvement for change in number of nodes
|
Change in number of nodes |
%improvement |
||||||
|
AOD V |
AN H |
FUZZ Y |
HELL O |
AN H |
FUZZ Y |
HELL O |
|
|
through put |
9242.1 8 |
9365. 14 |
9838. 82 |
8550. 12 |
1.3 |
6.7 |
- 7.4 |
|
delay |
0.2054 |
0.194 |
0.135 |
0.190 8 |
5.6 |
34. 3 |
7.1 |
|
jitter |
0.085 |
0.083 4 |
0.075 6 |
0.084 8 |
1.8 |
11 |
2 |
|
Data packets received |
1118.5 39 |
1135. 28 |
1188. 4 |
1033. 8 |
1.5 |
6.2 |
- 7.5 |
|
Residua l battery power |
3.66 |
4.086 |
4.2 |
2.964 |
11. 6 |
14. 7 |
- 19. 6 |
|
No.of times link breaka |
256.41 |
121.2 8 |
115.1 8 |
169.7 8 |
53. 2 |
55. 6 |
34. 5 |
IX CONCLUSION
RDCLRP and its variants ANH, HELLO and FUZZY are proposed for route discovery using cross layer approach. The route is discovered and old route is switched to a new route before route breakage using HWM. Comparative analysis of the proposed algorithms is done with respect to AODV for change in node density. Results illustrate that the FUZZY provides best performance regarding all performance parameters. Route breakage reduces to 55.6%, and throughput increases by an average of 6.7% for FUZZY compared to basic AODV. It is because of preemptive route repair of FUZZY algorithm. Future work will focus on the calculation of overhead enabling the algorithm to be used for non real time communication. FUZZY. Among all the proposed algorithm, FUZZY shows best performance.
Список литературы Performance Analysis of Route Discovery by Cross Layer Routing Protocol- RDCLRP
- Marco Fotino and Floriano De. Energy Issues and Energy aware Routing in Wireless Ad-hoc Networks. Rango, s.l. : International Journal of Communication System, Mobile Ad-Hoc Networks: Protocol Design, 2010, pp. 281-296.
- Amir Esmailpour, Nidal Nasser and Jehad Al Efficient routing for wireless mesh networks using a backup path, s.l. : International Journal of Communication System, May 2012.
- Brian Russel, Michael L. Littman and Wade Trappe, Integrating machine learning in ad hoc routing: A wireless adaptive routing protocol, 2011.
- Wen-Hsin Yang, You Chiun Wang, Yu-Chee Tseng and Bao-Shuh P. Lin, Energy-Efficient Network Selection with Mobility Pattern Awareness in an Integrated WiMAX and WiFi Network.. s.l. : International journal of communication system, 2000.
- Dzmitry Kliazovich, Simone Redana, Fabrizio Granelli.Cross-layer error recovery in wireless access networks: The ARQ proxy approach s.l. : International Journal of Communication System , 2011.
- Vineet Srivastava, Mehul Motani, Cross-Layer Design: A Survey and the Road Ahead. s.l. : IEEE Communications Magazine , December 2005.
- Liang Qin and Thomas Kunz, Survey on Mobile Ad Hoc Network Routing Protocols and Cross-Layer Design. S.I. :, Carleton University, Systems and Computer Engineering, Technical Report SCE-04-14, August 2004
- Vikas kawadia, p. R. Kumar, A cautionary perspective on cross-layer design.. s.l. : IEEE Wireless Communications, February 2005.
- Brent Ishibashi, Raouf Boutaba., Topology and mobility considerations in mobile ad hoc networks, journal of Ad Hoc Networks, 200,5 762–776.
- V. T. Raisinghani and Iyer. Sridhar ECLAIR: AnEfficient Cross Layer Architecture for Wireless Protocol Stacks. ,. s.l. : WWC, 2004.
- Marco Conti, Gaia Maselli, Giovanni Turi, SylviaGiordano, Cross layering in mobile Ad Hoc Network Design. s.l. : IEEE Computer Society, February 2004, pp. 48-51.
- Xiaoxin Wu, Gang Ding, and Wenwu Zhu, Load-Based Route Discovery Through Searching Range Adaptation for MANET Throughput, IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 58, NO. 4, MAY 2009, 2055.
- Chi Pan Chan, Soung Chang Liew, and An Chan, Many-to-One Throughput Capacity of IEEE 802.11 Multihop Wireless Networks 514 IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 8, NO. 4, APRIL 2009
- Luca Mottola, Gianpaolo Cugola, and Gian Pietro Picco, A Self-Repairing Tree Topology Enabling Content-Based Routing in Mobile Ad Hoc Networks, pp: 946-960, IEEE TRANSACTIONS ON MOBILE COMPUTING, VOL. 7, NO. 8, AUGUST 2008.
- Han-Chieh Chao and Ching-Yang Huang, Micro-Mobility Mechanism for Smooth Handoffs in an Integrated Ad-Hoc and Cellular IPv6 Network Under High-Speed Movement, , IEEE TRANSACTIONS ON VEHICULAR TECHNOLOGY, VOL. 52, NO. 6, NOVEMBER 2003.
- Song Guo, Oliver Yang and Yantai Shu, Improving Source Routing Reliability in Mobile Ad Hoc Networks 362 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 16, NO. 4, APRIL 2005
- Subir Halder, Amrita Ghosal, , Sipra Das Bit, 'A pre-determined node deployment strategy to prolong network lifetime in wireless sensor network, journal of Computer Communications, Eisevier, 34, pp:1294–1306, 2011
- Ian D. Chakeres, Elizabeth M. Belding-Royer,The Utility of HELLO Messages for determining Link Connectivity,. International Symposium on Wireless Personal Multimedia Communications - WPMC , vol. 2, pp. 504-508 vol.2, 2002.
- Charles E Perkins and Elizabeth M Royer Adhoc On Demand Distance Vector Routing,
- C. Perkins, E. Belding-Royer and S. Das, Ad hoc On-Demand Distance Vector (AODV) Routing, Request for Comments: 3561, July 2003.
- Mehajabeen Fatima, Roopam Gupta, T.K. Bandhopadhyay RDCLRP-Route Discovery by Cross Layer Routing Protocol for Performance Improvement, Kanyakumari, India : International Conference on Network and Computer Science, April 2011, Vols. V5-306.
- Mehajabeen Fatima, Roopam Gupta, and T.K. Bandhopadhyay Route Discovery by Cross Layer Approach for MANET , s.l. : International Journal of Computer Applications, January 2012, Vols. Volume 37– No.7, pp. 0975 – 8887.


