Performance Evaluation of Routing Protocol with Selfish Users in Realistic Environment
Автор: Mansi Dua, Shailender Gupta, Bharat Bhushan, C. K. Nagpal
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 6 vol.5, 2013 года.
Бесплатный доступ
Mobile Ad hoc Network (MANET) consists of wireless mobile nodes that can be set up any time at any place without the requirement of pre-requisite infrastructure. The nodes in these networks have several constraints such as battery power, processing capability and bandwidth. Moreover each node in MANET has to act as a relay node for others for the successful network operations. In an ideal environment in spite of above mentioned limitations, the node performs this community task faithfully but as in real world there exists nodes with selfish attitude also. Therefore, this paper is an effort to evaluate the efficacy of network with nodes having such behavior prevailing in realistic environment. Various researchers have evaluated the network performance in idealistic conditions but none has made an effort to evaluate it in practical condition such as in presence of obstacles. To make the scenario realistic different number, type and shape of obstacles were taken. The work was accomplished by designing a simulator in MATLAB-11.
Ad-hoc network, Routing, Obstacles
Короткий адрес: https://sciup.org/15014559
IDR: 15014559
Текст научной статьи Performance Evaluation of Routing Protocol with Selfish Users in Realistic Environment
Published Online July 2013 in MECS DOI: 10.5815/ijmecs.2013.06.07
MANET [1-4] is a collection of wireless nodes that can dynamically be setup anywhere and anytime without using any pre-existing network infrastructure. Each node in MANET is free to move randomly and often act as routers, transmitter and receiver at the same time. Due to absence of centralized access points and infrastructure less, the communication in MANET is multi-hop in nature wherein each node relays data packets of other nodes thereby spending its resources such as battery power, CPU time and memory. In an ideal environment, each node in MANET is supposed to perform this community service truthfully. However this is not the case and existence of selfish nodes [5-9] is a very common feature in MANETs. The selfish nodes are the ones that use others for their own profit. The behavior of selfish nodes can be characterized [6, 10] as follows:
-
• Do not participate in routing process
-
• Do not reply or send hello messages
-
• Intentionally delay the RREQ packet
-
• Dropping of data packets
The major reason behind selfishness may be low residual battery power [7, 8, 11] or rogue intentions [5, 6] of a node. Various researchers have evaluated the network performance in presence of selfish nodes. This paper evaluates the performance of selfish users in realistic environments. A realistic environment [1, 12-17] is one that contains obstacles of different number, types and shapes.
The rest of the paper has been organized as follows: Section 2 provides the problem identification. The details of simulation setup and parameters are discussed in section 3. Section 4 provides the impact of realistic scenario on MANET performance. Section 5 provides the conclusion followed by references.
-
II. MOTIVATION AND PROBLEM IDENTIFICATION
The problem of selfish node is very common in ad hoc network. If this type of behavior prevails in the network among large number of the nodes, it may eventually lead to disruption of network. Various researchers have tried to find the impact of selfish nodes on MANET performance as follows:
The work done by Shailender Gupta et. al.[5] shows that as the concentration of selfish nodes increases the performance metrics such as packet delivery ratio and probability of reachability decreases significantly but never falls to zero since at 100% concentration of selfish
Performance Evaluation of Routing Protocol with Selfish Users in Realistic Environment nodes the communication still prevails among neighboring nodes.
The work done by Li feng et. al. [18] showed that a threshold limit exists for nodes cooperation above which there is no effect on network connectivity and path delay but when this limit is crossed, the path delay increases linearly and network connectivity breaks frequently.
To overcome this selfish attitude various strategies in literature have been proposed such as reputation based [5, 9, 11, 19-21] and motivational based [5, 8, 9, 11, 1921] approaches. The reputation based mechanisms develops reputation index periodically and if a node has reputation index above a predetermined threshold then it is added to trust worthy list otherwise it is treated as selfish or malicious. On the other hand motivational based approaches tries to motivate a particular node to participate in the routing and data forwarding process by using virtual currencies such as nuglets etc.
All these strategies developed have been simulated in idealistic conditions but to have a realistic output they should be tested in practical conditions. We are of the opinion that if we want to find impact of selfish nodes on MANET performance then it should be done in realistic environment i.e. in presence of obstacles. Thus the results that obtained would be quite practical. The next section give details of the various simulations set up parameters used to make the scenario more practical.
-
III. EXPERIMENTAL SET UP PARAMETERS
In order to evaluate the network performance in realistic environment under the presence of selfish nodes we have evaluated the impact of selfish user with varying number, type and shape of the obstacle (see Fig. 1). The path marked with blue color shows the shortest path between a given pair of source and destination having no selfish node. While the path marked with red color shows the path formation in presence of selfish nodes.
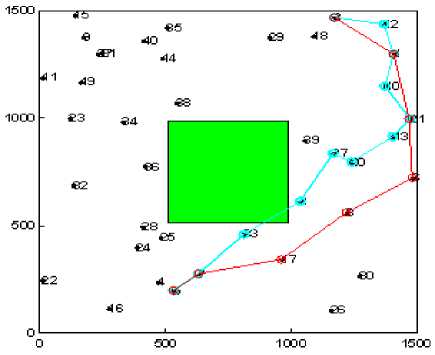
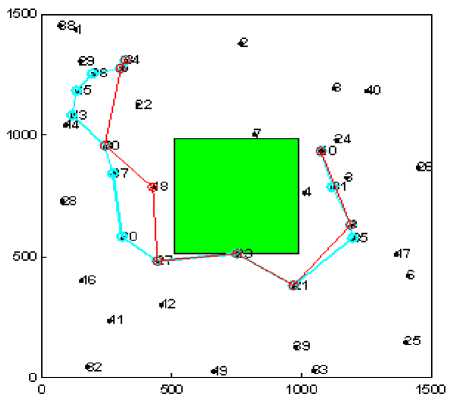
Figure1 (b) Experimental snapshot for moutain type obstacle
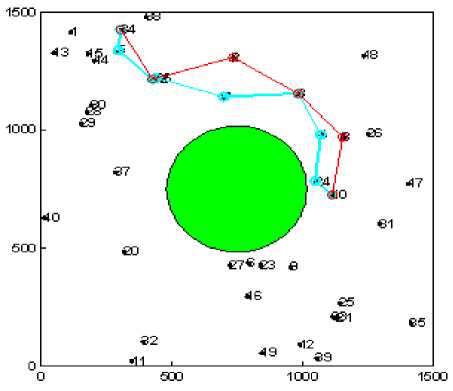
Figure1 (c). Experimental snapshot for Circular Obstacle
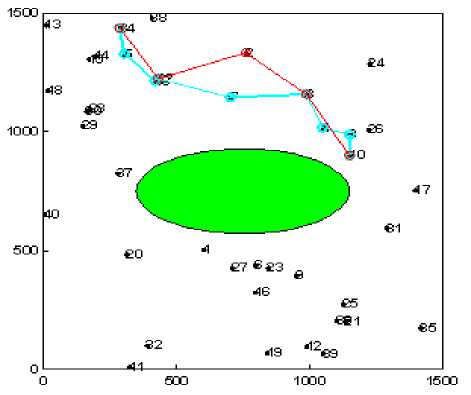
Figure1 (a). Experimental snapshot for river type obstacle
Figure1 (d). Experimental snapshot forEliptical Obstacle
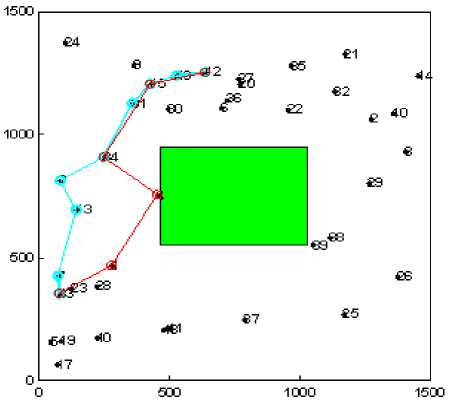
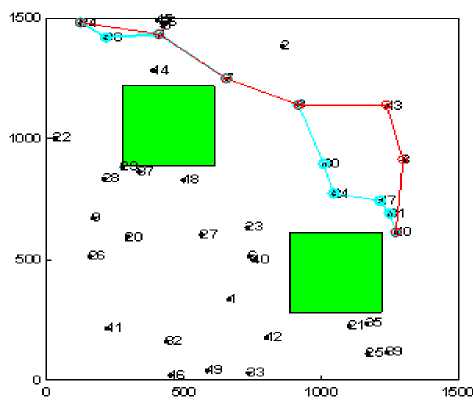
Figure1 (h). Experimental snapshot for Two Obstacle
Figure1 (e). Experimental snapshot for Rectangular Obstacle
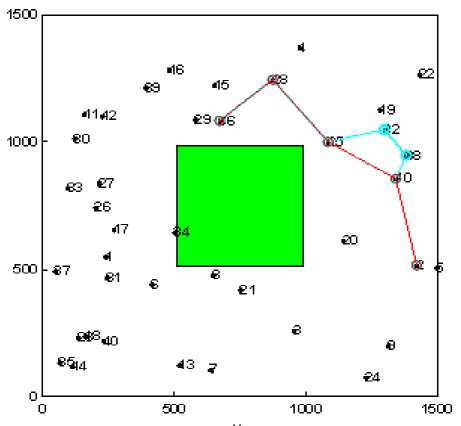
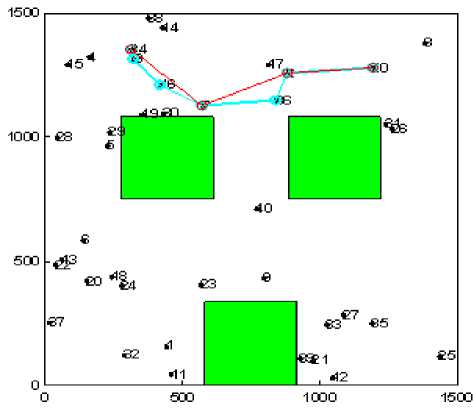
Figure1 (f) Experimental snapshot for Square obstacle
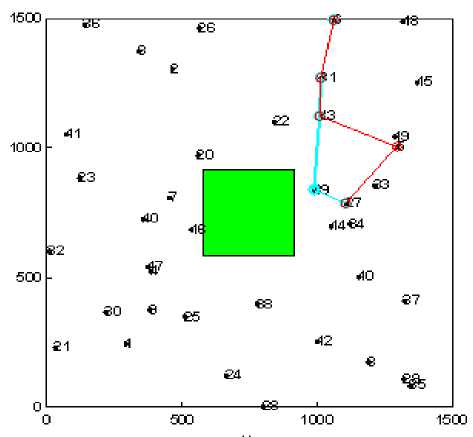
Figure1 (g). Experimental snapshot for One Obstacle
Figure1 (i). Experimental snapshot for Three Obstacle
Figure1. Experimental snapshots
-
A. Performance Metrics used
-
• Hop Count: Defined as the number of intermediate nodes from source to destination for a successful communication.
-
• Path Optimality: Defined as the ratio of total distance traversed in an environment with no selfish nodes to selfish nodes.
-
• Reachability: Defined as the ratio of successful routes formed to the total number of route request generated.
To calculate the above mentioned results the algorithm used is as follows.
-
B. Algorithm
The algorithm shown below calculates the various performance metrics mentioned above. It takes 40 nodes (N = 40) and define K% of nodes as selfish ones. To calculate the value of reachability a variable count is used. It is initialized to zero value and is incremented each time by one when a path exists between a randomly (using rand function) chosen pair of source and destination. The process is repeated thirty times and at last reachability is calculated using the equation
Reachability =count/40;
To calculate path optimality and hop count we calculate the total distance and intermediate hops between a successful pair of source and destination using cum_path_length( ) and cum_hop_count( ). This process is repeated as mentioned above is repeated and at last average of all these values is taken as also given in the algorithm.
Algorithm
Total Nodes N = 40;
count =0
Cum_Hop_count = 0;
for i=1 to 30
S= rand(N)
D= rand(N)
If path(S,D) exists
Cum_path_length=Cum_path_length+path_length(S,D) Cum_hop_count = Cum_hop_count + Hop_Count(S,D); Count++ end end path_lengtht = Cum_path_length / count; reachability =count/30 ;
Hop count = Cum_Hop_Count/40;
-
C. Set up parameters
The various simulation set up parameters for this experiment are as follows:
TABLE 1: Set up parameters
|
Size of region |
2250000 sq. units |
|
Shape of region |
Square : 1500 (Length) |
|
Mobility Model Used |
Random walk (RW) |
|
Number of Nodes Deployed |
40 |
|
Transmission Range |
250 |
|
Routing Algorithm Used |
Dijkstra’s shortest Path Routing Algorithm |
|
Placement of Nodes |
Random |
|
Number of iterations |
30 |
|
Obstacle Type |
Mountain, River |
|
Obstacle Number |
1-3 |
|
Obstacle Shapes |
Circular, Elliptical, Square, Rectangular |
IV. RESULT OF TYPE OF OBSTACLE
-
A. Impact on Hop count:
In the real world obstacle can be of type mountain, river etc. These obstacles cause significant impact on the network performance in different ways.
Following inference can be made from the Fig. 2:
-
• In both the cases i.e. in presence and absence of selfish nodes, river type obstacle has highest hop count in comparison to mountain type obstacle.
-
• In presence of obstacles at 50% concentration of selfish nodes, the value of average hop count for the river and the mountain is almost same.
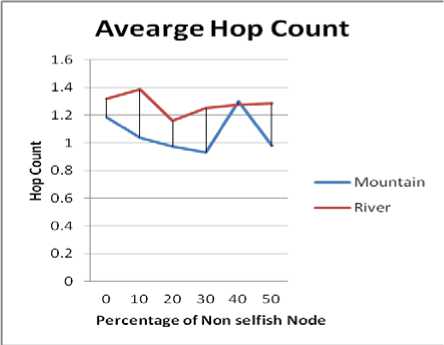
Figure2(a) Impact under Non Selfish Node
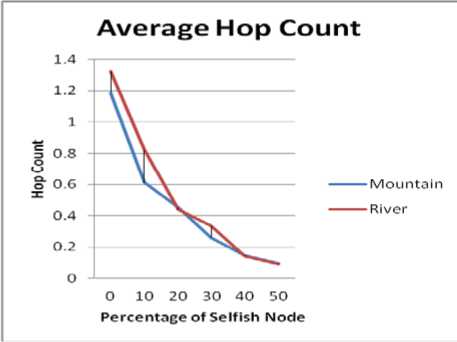
Figure2.(b) Impact under Selfish Node
Figure 2 Experimental Impact of Obstacle Type on Hop Count
-
B. Impact on Reachability:
The mountain affects both the node movement and the effective transmission range of the nodes. While the river type obstacle affect the node movement only. Therefore as expected the reachability value in case of mountain is lower in and absence of selfish nodes as also shown in Fig. 3.
Average Reachability
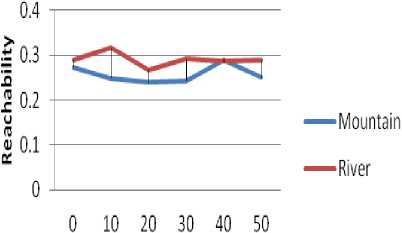
Percentage of Non Selfish Node
Figure3(a) Impact under Non Selfish Node
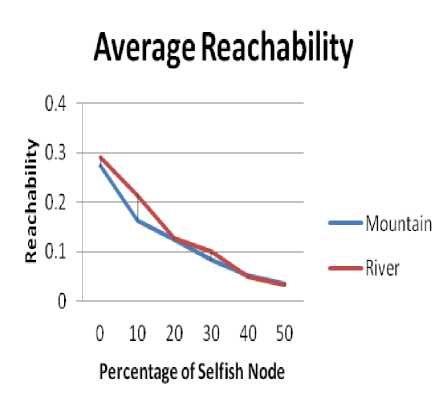
Figure3(b) Impact under Selfish Node
Figure 3. Experimental Impact of Obstacle Type on Reachability.
V. RESULT OF NUMBER OF OBSTACLE
-
A. Impact on Hop count:
Fig. 4 shows the impact of number of obstacles in both the environment having selfish and non selfish nodes. The following inference can be drawn:
-
• As the number of obstacles increases the value of hop count decreases since the path having higher hop count values now becomes less reliable.
-
• In an environment having no obstacle and no selfish nodes the value of hop count is almost same. This shows that idealistic situations are quite different from real ones.
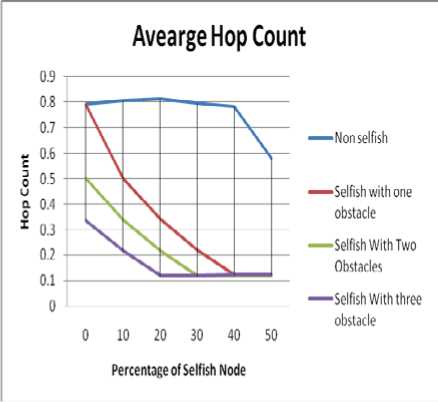
Figure 4. Impact of varying number of obstacle
-
B. Impact on Reachability:
Number of obstacle causes significant impact on the connectivity between the communicating nodes in the network thus affecting the reachability value as shown in Fig. 5. The following inference can be drawn:
-
• As the number of obstacles increases the value of reachability decreases that is also evident from our graphs.
-
• The results of both the environment i.e. nonselfish and selfish are quite different.
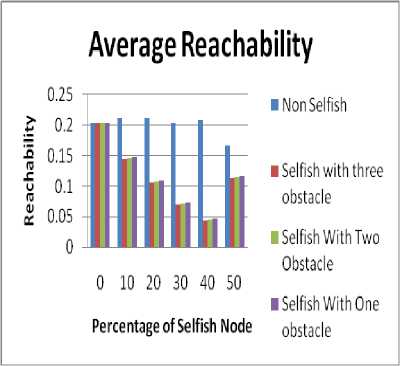
Figure5. Experimental Impact of different number of obstacles on Reachability
VI. RESULT OF SHAPE OF OBSTACLE
-
A. Impact on Hop count:
Fig.6 shows the impact of hop count for different shapes of the obstacle. The following inference can be drawn:
-
• The average hop count at lower concentration of selfish nodes is highest for circular shape. While it is least for elliptical shape.
-
• At higher concentration of selfish nodes the hop count value does not follow any pattern. It is also verified from our results of reachability.
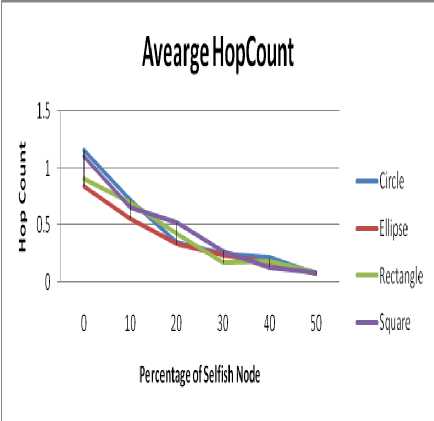
Figure 6. Experimental Impact of different shape of obstacles on Hop Count
-
B. Impact on Reachability:
Fig. 7 shows the impact of reachability for different shapes of the obstacle. The result of reachability does not follow any trend at higher concentration of selfish nodes.
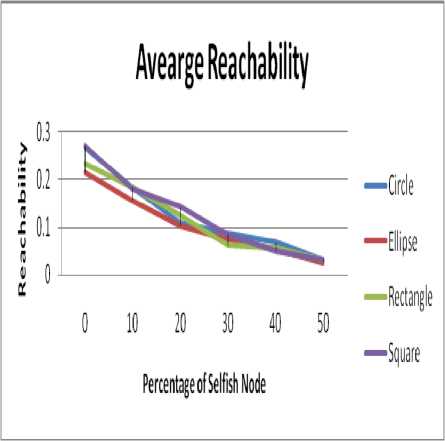
Figure 7. Experimental Impact of different shape of obstacles on Reachability
VII. CONCLUSIONS
TABLE: 2 Overall Comparisons
|
Obstacle Type ^ |
Type |
Number |
Shape |
||||||
|
Performa nce Paramete r |
Mou ntai n |
R iv er |
1 |
2 |
3 |
Cir cle |
Ell ipti cal |
Sq uar e |
R ec ta n gl e |
|
Hop Count |
L |
H |
L |
M |
H |
Does Not Follow any Trend |
|||
|
Reachabi lity |
L |
H |
L |
M |
H |
||||
Where, L= Low, M = Medium, H= High
In this paper an effort has been made to evaluate the efficacy of routing protocols in presence of selfish user in realistic environment. The following inference can be drawn from the Table 2 as follows:
-
1. The mountain type obstacle obstructs both node movement as well as effective transmission range of the nodes hence the reachability and hop count values are quite low.
-
2. As the number of obstacles increases the hop count value and reachability values decreases
-
3. The idealistic environment results are quite different from real ones.
These results can be very fruitful for researchers working in this direction.
Список литературы Performance Evaluation of Routing Protocol with Selfish Users in Realistic Environment
- Shailender Gupta ,Chirag Kumar ,C. K. Nagpal ,Bharat Bhushan ,” Performance Evaluation of MANET in Realistic Environment “,I.J.Modern Education and Computer Science, July 2012 in MECS.
- Joseph Macker and Scott Corson,”Mobile ad-hoc networks (MANET)”, http://www.ieft.org/procedings/01dec/183.htm,December 2001.
- Charles E.Perkins,”Mobile Ad-hoc Networks,” Addison – Wesley (2000).
- Giorgos Papastergiou, Ioannis Psaras , Vassilis Tsaoussidis," Deep-Space Transport Protocol: A Novel Transport Scheme for Space DTNs", Computer Communications Volume 32, Issue 16, 15 October 2009, Pages 1757–1767 , Elsevier.
- Shailender Gupta , C. K. Nagpal and Charu Singla ” IMPACT OF SELFISH NODE CONCENTRATION IN MANET S”, IJWMN Vol. 3, No. 2, April 2011.
- S. Marti, T. J. Giuli, K. Lai, M. Baker, “Mitigating Routing Misbehavior in Mobile Ad Hoc Networks,” Proc. of MobiCom 2000, Boston, August 2000.
- L. Blazevic, L. Buttyan, S. Capkun, S. Giordano, J. P. Hubaux, J. Y. Le Boudec, “Self- Organization in Mobile Ad-Hoc Networks: the Approach of Terminodes,” IEEE Communications Magazine, Vol. 39, No. 6, June 2001.
- L. Buttyán, J.-P. Hubaux, “Nuglets: a Virtual Currency to Stimulate Cooperation in Self- Organized Mobile Ad Hoc Networks,” Technical report No. DSC/2001/001, Swiss Federal Institution of Technology, Lausanne, January 2001. http://icawww.epfl.ch/hubaux/.
- Levente Butty′an and Jean-Pierre Hubaux. Nuglets: a Virtual Currency to Stimulate Cooperation in Self-Organized Mobile Ad Hoc Networks. Technical Report DSC/2001/001, EPFL-DI-ICA, January 2001.
- Shailendra Gupta,C.K.Nagpal,Charu Singla,” Impact of Selfish Node Concentration in MANETs”, IJWMN,Vol. 3,No.2,April 2011.
- Levente Butty′an and Jean-Pierre Hubaux. Stimulating Cooperation in Self-Organizing Mobile Ad Hoc Networks. ACM/Kluwer Mobile Networks and Applications, 8(5), October 2003.
- Michael Feeley, Norman Hutchinson, and Suprio Ray,"Realistic Mobility for Mobile Ad Hoc Network Simulation",I. Nikolaidis et al. (Eds.): ADHOC-NOW 2004, LNCS 3158, pp. 324–329, 2004.
- Cedric Gael AboueNze, Frederic Guinand and Yoann Pign,"Impact of Obstacles on the Degree of Mobile Ad Hoc Connection Graphs",arXiv:0911.0141v1 [cs.NI] 1 Nov 2009.
- Amit Jardosh, E. M. Belding-Royer, K. C. Almeroth, and S. Suri, "Real world Environment Models for Mobile Ad hoc Networks," IEEE Journal on Special Areas in Communications - Special Issue on Wireless Ad hoc Networks, vol. 23, pp. 622-632, 2005.
- P. Venkateswaran, Rahul Ghosh, Aritra Das, S.K. Sanyal, R. Nandi,"An Obstacle Based Realistic Ad-Hoc Mobility Model for Social Networks",JOURNAL OF NETWORKS, VOL. 1, NO. 2, JUNE 2006.
- P. Venkateswaran, Rahul Ghosh, Aritra Das, S.K. Sanyal, R. Nandi,"An Obstacle Based Realistic Ad-Hoc Mobility Model for Social Networks",JOURNAL OF NETWORKS, VOL. 1, NO. 2, JUNE 2006.
- Chirag Kumar, C.K. Nagpal, Bharat Bhushan, Shailender Gupta,"Reachability Analysis of Mobility Models under Idealistic and Realistic Environments", published in prceedings by springer,wimoa-2012,page no. 519.
- Li Feng,Qinghai Yang,Fenglin Fu,Kyung Sup Kwak,”Impact of node selfishness on the connectivity and path delay of Ad-hoc networks”,ICT Convergence(ICTC),2012,International Conference.
- Yongguang Zhang, Wenke Lee, and Yi-An Huang. Intrusion Detection Techniques for Mobile Wireless Networks. to appear in ACM Wireless Networks (WINET), 9, 2003. also available as http://www.wins.hrl.com/people/ygz/papers/winet03. pdf.
- Sheng Zhong, Jiang Chen, and Yang Richard Yang. Sprite: A simple, cheat-proof, credit-based system for mobile ad-hoc networks. In Proceedings of IEEE Infocom ’03, San Francisco, CA,April 2003.
- Yongguang Zhang and Wenke Lee. Intrusion detection in wireless ad-hoc networks. In Mobile Computing and Networking, pages 275–283, 2000.


