Prolong the Lifetime of WSN by Determining a Correlation Nodes in the Same Zone and Searching for the "Best" not the "Closest" C.H.
Автор: Mishall H. Awaad, Wid A. Jebbar
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 11 vol.6, 2014 года.
Бесплатный доступ
There were a lot of methods that introduced in the information search field; one of those methods is the wireless sensor networks; and one of the most famous protocols in WSNs is LEACH protocol. And because of that protocol suffering from some defects like sometimes the node attaching to C.H. near from it, but that C.H. far from the B.S. even the node itself near to the B.S. than its C.H.; to solve that problem a new method will introduce in this research which basing on: Allocation of 5 meters (0-5) and prevent the election of any C.H. on it. Division of the Network area into four parts (near, mid, far, and very far) according to the node`s distance from B.S. Restriction of the attachment between the nodes and the C.Hs. in the same part. If a particular part is empty from the C.H. so the nodes will attach to C.H. from the upper parts, But with a condition (the distance between the C.H. and the node <= the distance between node and B.S. /2) Through these improvements, good results were gotten in the simulation, which showed that the improved LEACH was more efficient than the original LEACH.
WSN, routing, cluster, CH, BS, network lifetime, reduce power, LEACH, improved LEACH, remaining nodes
Короткий адрес: https://sciup.org/15014703
IDR: 15014703
Текст научной статьи Prolong the Lifetime of WSN by Determining a Correlation Nodes in the Same Zone and Searching for the "Best" not the "Closest" C.H.
Published Online November 2014 in MECS DOI: 10.5815/ijmecs.2014.11.04
The WSN`s became a very important method to collect the information [1]; this is because of the huge applications scale of those networks such as security, military systems and the environment adaptation. The WSN`s consist of so many sensor nodes, which their main task is to collect the data from the area that those sensors exist in and then make a computation process on those data and communicate with the other sensors in this network. in fact, those sensors are restricted in a limited power battery; so it is impossible to recharge those batteries after deployment [2], so the main problem with those networks is their dependence on a limit power battery [3][4], so the routing protocol and data fusion are effective methods to reduce the computation power and prolong the lifetime of WSN, the cluster routing protocols reduce the communication distance between the nodes to transmit their data.
On the other hand, data fusion reduces the data redundancies in a huge way [2] ; so because of the importance of the routing protocols in reducing the wasted power so there were a lot of protocols have been proposed in this purpose and those protocols can be classified according to the network topology to "plane routing protocols, and level routing protocols" the protocols of the first class are: DD, SAR, SPIN, Romor Routing and etc.; where the protocols of the second class are: LEACH, LEACH-C, PAGASIS, TEEN and etc. [5]
Between all of those protocols the most important one is (LEACH: Low Energy Adaptive Clustering Hierarchy) because of his huge role in reducing the power; but despite that it is still has some defects like the C.H. in this protocol selecting randomly and the nodes usually connected to the nearest C.H not to the closest one to the node and to the B.S , so in this research we will propose a new method to recover LEACH protocol from those problems which will help prolong the lifetime of the WSN and help in collecting as much as possible from information.
-
II. Similar Studies
As said previously that the power issue is a very sensitive issue in the WSNs so there are so many researches have been introduced to decreasing the consumption of it as follow:
Jun, Xin and et al, introduced improved protocol based on enhancing the transmission distance in the clustering routing protocol which is LEACH-SC (LEACH-Selective
Cluster); in this protocol a new method has been used to choose the C.H; where a specific node will choose the closest C.H to the center point to the distance between the node and the BS; anyway that protocol did not handled the problem of there is more than one C.H. achieve that center point condition; also did not handled the problem of the node which is close to the B.S more than its C.H. [6] where; most of those problems have been handled in our research. Xiaoping, Hong and et al. have been present enhanced protocol basing on LEACH protocol, which is included C.H selection and multi-hop routing, in this protocol there is a huge reduction of the power attrition rate which prolong the lifetime of the WSN [7] .
Wang, Zhang and et al, have been proposed a new protocol, LEACH-ECD to reduce the power, in this protocol has been taken in the view the remainder power for the nodes during the C.H. selection and has been chosen an assistant node in the cluster, the purpose of that is to balance the communication load from the cluster during the transmission of the data between the nodes, in this protocol the C.H has its own power guided factor by which it deciding the transmission mode. By combining the single hop and multi-hop communication modes, the wasted power has been reduced in this protocol so this is helping to prolong the lifetime of the WSN [8].
In this research there is a new method will be introduced to enhance the work of LEACH protocol and helping in recovering it from the problems that suffering from and decreasing the power consumption.
-
III. Leach Description
-
3.1 The Work of LEACH Protocol
LEACH (Low-Energy Adaptive Clustering Hierarchy) is a protocol organizing himself by himself, adaptive hierarchy which uses the randomization to distribute the power equally between nodes in the network [9] and [10].
In this protocol the nodes organizing themselves in a local cluster with one node serve as local B.S or C.H, if that C.H has been selected stable and at a prior time in the overall system just like most of the clustering algorithms, so it is so easy to believe that the unlucky sensor nodes if they chose to be C.H then they will die quickly and ends all the nodes in their own cluster. So LEACH supply a random rotation for the low power C.H locations, the purpose of that is to not put the load on one node; also LEACH protocol supply local data fusion to compress the data to send them from the C.H to the B.S [11] this will lead to reduce the wasted power and prolong the lifetime of the network.
The nodes chose themselves to be a C.H in any time with a specific probability, those C.H will announce their status to the other nodes in the network to give the nodes the opportunity to choose which C.H wants to belong to according to the lowest communication power C.H, when all that`s done then the C.H will create a schedule to the nodes in its own cluster this is allowed for those not C.H nodes to turn their own radio off except when they transmitting their data this is will lead to minimizing the wasted power by each individual node, after the C.Hs receiving the data from their own nodes in their own cluster they will aggregate them and then sending them to the B.S. [10].
The operation of LEACH is broken up into rounds as in Fig. 1, where each round begins with a set-up phase, when the clusters are organized, followed by a steadystate phase, when data transfers to the base station [12].
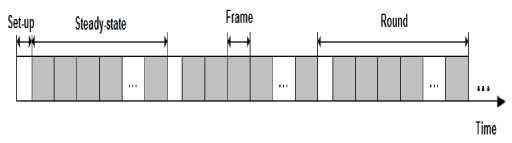
Fig. 1: Time line showing operation of LEACH
-
• Set-up phase
In the set-up phase when the clusters are organized, the LEACH sets a threshold value T(n) first, and then sensor node i generates a random number between 0 and 1 automatically by distributed computing. If the random number < T(n), the node will become the cluster-head of the current round r, and common nodes join in the nearest cluster. After a period of data transmission, the network starts cluster reconstruction of the new round [13] .
-
• Steady-state phase
The steady-state phase duration is usually much longer than the set-up phase duration. However, the first phase is more important, in which sensor nodes are allowed to elect themselves as cluster-heads randomly, and then divided into clusters. Each node that becomes the cluster head (CH) will create a TDMA (Time division multiple access) schedule for the sensor nodes within the cluster. That allows the radio components of each non-CH node to be turned off all times except during their transmit time [13] .
Threshold T (n) is determined by the following [11] :
T ( n ) =
P
,n G
1 - P x [ rmod ( 1/p ) ]
0,
otherwise
Where n=given number of nodes.
p=the priori probability (e.g. =0.05) of a node being elected as a cluster-head.
r=a random number between 0 and 1 that is selected by a sensor node. If this random number is less than the threshold value T(n), then the respective node becomes the cluster-head.
G=the set of nodes that were not accepted as cluster head in the last “1/p” events.
Elected cluster head node broadcasts a message about the first node cluster to the entire network [14]. The rest nodes of the network decide to join which cluster according to signal strength of receiving information, and notify the corresponding cluster head node, completing the establishment of the cluster [15]. The cluster heads combine and compress the data and forward it to the base station, therefore it extends the lifetime of major nodes.
-
3.2 LEACH'S Problems
As everything in this life LEACH protocol is not perfect; although it has a lot of advantages in reducing power, but at the same time it has problems that cause in a way or another power consumption, these problems are as follows:
The first one is the "triple distance problem"; maybe someone will ask what the triple distance is? The triple distance problem means the distance between (the node, the C.H. and the B.S.) LEACH protocol does not suppose a balance between those triple distances. In other words, sometimes the node and its C.H. are close from each other, but at the same time only one of them is close to the B.S. while the other is far; that is for sure will waste the power as we can see in Fig. 2:
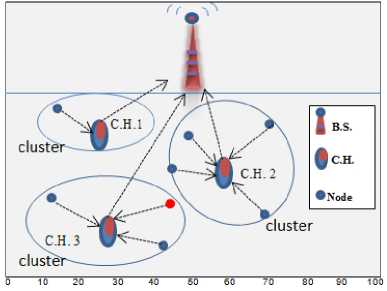
Fig. 2: the problem of distance in LEACH
If a look has been taken to Fig. 2 specifically to the red node and its C.H. will see that the distance between that node and the C.H3. is good (close) but let's take a different look; let's look to the distance between that C.H and the base station as we can see that it is not the better one for that node to attaching to, because it is so far from the B.S. and better for that node to attaching to C.H.2 which is close to it and to the B.S. Another problem with LEACH protocol is when there is a specific node close to the B.S. from all C.H. exist in the network area in this case how is this node will find its perfect C.H.?, the previous problems made LEACH protocol suffering from the power wasting and decrease the lifetime of the overall WSN, So to recover LEACH protocol from those problems will be introduced in the next section our solution which will enhance the LEACH protocol and prolonging the lifetime of the WSN.
-
IV. Leach- (Ar, Ac With Bsc)
-
4.1 How does LEACH- (AR, AC with BSC) Work?
Low Energy Adaptive Clustering Hierarchy – ( A ttachment R estriction and A ttachment C ontrolling; with the B est S election of the C .H.)
The principle of the methods that have been added to enhance LEACH protocol will be clear in the next section.
The things that have been added to the original protocol for enhancing it were as follows:
-
• The whole network area has been divided into four parts; Near, Mid, Far and Very far…
Where:
The node is pointed to be (Near, Mid, Far or Very Far) according to its distance from the B.S. and also 5 meters from (0-5) has been allocated for the whole area and prevented the selection of a C.H. in that area because it is so far from the B.S. and Fig. 3 will clarify that:
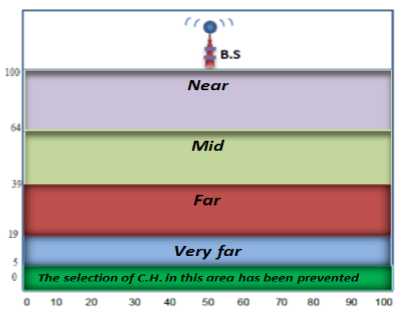
Fig. 3: the division of the whole network area
Then the number of the nodes and the number of C.H. has been counted in each part.
-
• That division in the previous step was as a preparing step to what will happen in this step; the restriction of the attachment step; The restriction of the attachment process means every node must attach to a C.H. from its part; in other words, if the node belong to the 'Near' part then the C.H. that will attach to must be from that part too; from the 'Near' part.
This restriction has been proposed as a solution to the problem of the far distance between the node and the C.H.
-
• Controlling on the attachment in each part; this is determined by the following conditions
- sometimes at the same part for a particular node there is more than one C.H. close to that node, the distance between those C.Hs and each other is so close; at this case the distance between all those C.Hs and the B.S. has been computed and made that node attaching to the closest C.H. for it and for the B.S. in another word this is a searching for the best C.H. not the closest at the same part
-because of the election of the C.H. in the original protocol and even in this protocol depending on a random value; so maybe after so many round one of those parts
will be empty from the C.H. then we allowed to the nodes at that part attaching to a C.H. from the upper parts; but with conditions to keep searching the best not the closest; and those conditions as follows.
That C.H. must achieve the condition (the distance between that node and the C.H. (distance1) must be <= the distance between that node and the B.S. (distance2) /2); this is mean that the distance between that node and the C.H. must be less or equal to the 'middle' distance between that node and the B.S.; this condition is to searching for the best C.H. not for the closest because it is take into a count the distance between the C.H and node and comparing it with the distance of the node and the B.S. But when there is more than one C.H. achieve this condition; then in this case the attachment will be to the closest C.H. to the node which at the same time achieving that previous condition. And Fig. 4 A, B and C will make that clear.
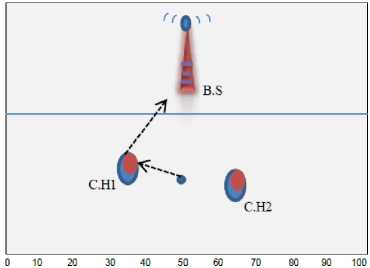
Fig. 4 A: The case that more than one C.H. closes from the node
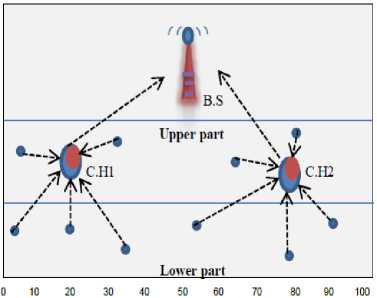
Fig. 4 B: The case of no C.H. in a particular part
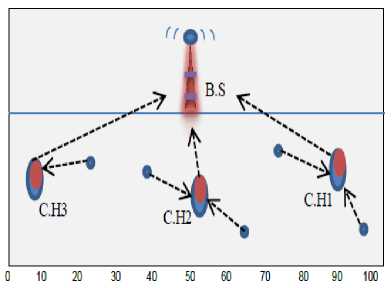
Fig. 4 C: the case of more than one C.H in one part but far from each other
As we can see from Fig. 4:A that both of the C.H.s are so close to the node so in this case the node will attach to the C.H which closest to the B.S, so the node will attach to C.H.1 the nearest to the B.S. While in B. we see the lower part with no C.H. so in this case we broke the rule and made the nodes attaching to the closest C.H. to them which achieving the condition (the distance between the node and the C.H. <= the distance between the node and the B.S. /2) from the upper parts. In C the distances between the nodes and the C.H.s are not so close to each other at that part; so in this case every node will attach to closest C.H. to it. The process of the attachment will be clear in Fig. 5:
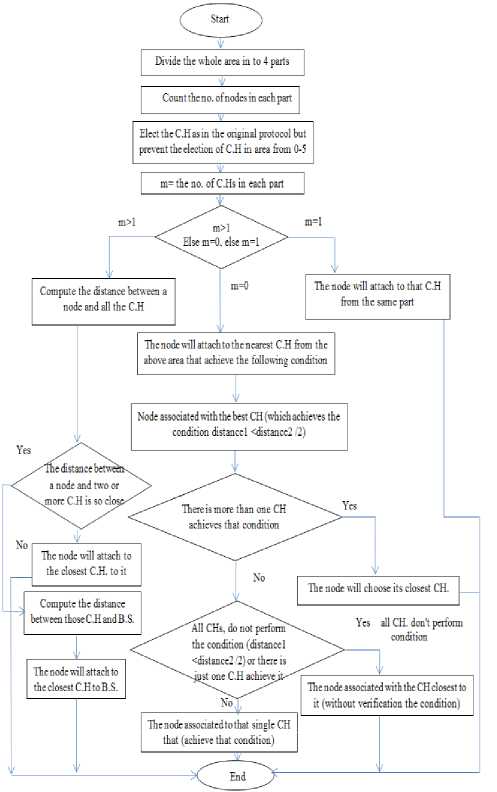
Fig.5: the flowchart of the attachment process in the improved protocol
The application of the previous algorithm in the improved LEACH protocol led to an increase in network lifetime and reduces power consumption, and therefore that the improved protocol is more efficient than the original protocol. In the next section the simulation results of the two protocols will be explained in detail.
-
V. Results And Their Analysis
In this section, the simulation will be used to analyze and evaluate the efficiency of the improved LEACH protocol algorithm. Where it was compared to the results of the original LEACH protocol and improved LEACH protocol to show the efficiency of the network lifetime and reduce the power consumption, the number of dead nodes and the remaining nodes in each round and thus illustrate the efficiency of the improved LEACH protocol. Usually, the nodes of WSN are distributed randomly by helicopter for different reasons; one of those reasons is the use of these networks in the military area. Suppose also that all nodes are consumed equal power and the base station (BS) is static and positioned distant from the sensors. Table1 shows the parameters used in the original LEACH protocol and the improved LEACH protocol simulations:
Table 1: Simulation parameters
|
Parameter |
Values |
|
Nodes |
100 |
|
Simulation area |
100x100 m 2 |
|
Base station location |
(50,170) |
|
Node energy |
0.5J |
|
Rounds |
800 |
|
Size of Packet |
6400 byte |
|
Meta-data |
200 byte |
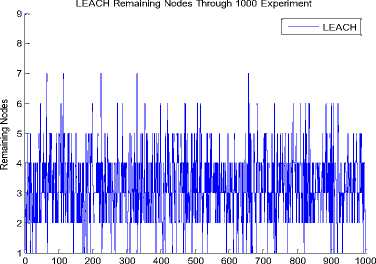
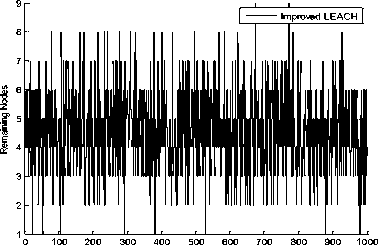
After the implementation of the program by using the previous parameters we got the result that the remaining nodes in the improved protocol more than the original protocol as in Fig. 6(A, B).
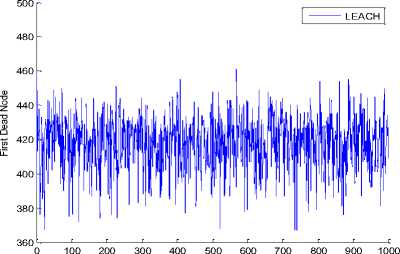
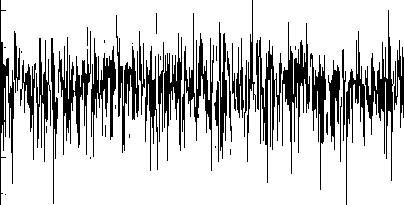
While the first dead node through rounds in the improved protocol has been founded less than the original protocol as we can see in the Fig. 7(A, B) below:
LEACH First Dead Node Through Rounds in 1000 Experiment
1000Experiment
Fig. 7 A: First dead node through rounds in original LEACH protocol
Improved LEACH First Dead Node Through Rounds in 1000 Experiment
Improved LEACH
0 100 200 300 400 500 600 700 800 900 1000
1000 Experiment
1000 Experiment
Fig. 6 A: Remaining nodes in original LEACH through 1000 experiment
Fig. 7 B: First dead node through rounds in improved LEACH protocol
Also dead nodes in rounds (500 and 700) in both protocols are shown in the Fig. (8 and 9), which shows that the improved protocol is better than the original protocol, and thus live more nodes in the improved protocol and thus will get more information. After the implementation of both protocols for 1000 experiment we got the results in Table 2 (as shown in Fig. 10)which shows the efficiency of the improved protocol in the remaining nodes, first dead, and the dead node in round 500, and the dead node in round 700. All of those results show that the improved protocol prolong the lifetime of the WSN and help in getting more information.
Improved LEACH Remaining Nodes Through 1000 Experiment
1000 Experiment
Fig. 6 B: Remaining nodes in improved LEACH through 1000 experiment
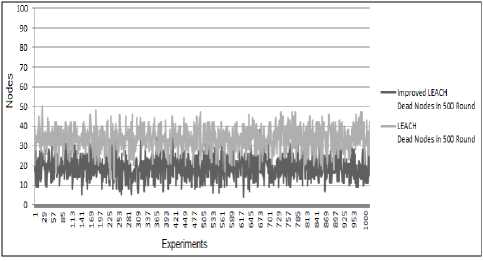
Fig. 8: dead nodes in 500 rounds in both protocols for 1000 experiment
Fig. 9: dead nodes in 700 rounds in both protocols for 1000 experiment
Table 2: The summary results for both protocols after 1000 experiment
|
Original LEACH |
Improved LEACH |
|
|
No. of results for remaining nodes |
168 |
832 |
|
No. of results for first dead nodes |
179 |
821 |
|
No. of results for the dead nodes in 500 round |
45 |
955 |
|
No. of results for the dead Nodes in 700 round |
60 |
940 |
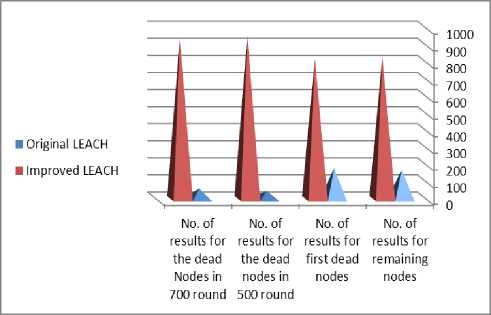
Fig. 10: summary of results comparison between original and improved protocols
-
VI. Conclusions
After all researches that have been introduced under the subject of enhancing the performance of LEACH protocol but it still suffering from some problems that cause in a way or another to wasting the power which is very important issue in the WSNs field; so in this research there was a new method that has been introduced to enhancing LEACH protocol and helping in recovering it from those problems; after we analyze that improved protocol we got a good results related to the number of dead nodes, the first dead node, the number of dead nodes in the 500 round and the number of dead nodes in the 700 rounds. But have been noticed that in the results of some experiments that the original LEACH better than improved LEACH in terms of the first dead node; and the reason that the attachment process restricted in the same part; so sometimes there is C.H. from another part so close to the node more than any other C.H. in its part so that may cause that node die in the improved protocol faster than the original protocol; also another reason that it does not elect any CHs within the area farthest from the BS; so sometimes be the death of the first node in improved LEACH faster than the original LEACH. These cases do not happen as much; as shown in Fig. 10.
So after all; the words that can be used to describe the improved protocol, which introduced in this research is 'so much better' than the original protocol in the things pointed above; and more efficient to extend the lifetime of the network and thus reducing the power consumption in sensor networks.
Acknowledgment
We would like to thank our families for their support which without it this research will never be possible, also we would like to thank the reviewers for their valuable comments and suggestions.
Список литературы Prolong the Lifetime of WSN by Determining a Correlation Nodes in the Same Zone and Searching for the "Best" not the "Closest" C.H.
- S. mittal, A. aggarwal and S.L. maskara, "Contemporary Developments in Wireless Sensor Networks", IJMECS Vol. 4, No. 3. 2012 MECS.
- W. Chen and B. Hu, "A Data Fusion Algorithm in LEACH Protocol Using Gauss Membership Function", School of Electronic and Information Engineering South China University of Technology Guangzhou, China, (2010) IEEE
- I. Amdouni, P. Minet, and C. Adjih, "Adaptivity of a Coloring Algorithm to Unreliable Communications for Data Gathering in Wireless Sensor Networks", International Journal of Digital Information and Wireless Communications (IJDIWC) 3(1): 61-74 (2013).
- R. K. Singh and A. Bhadoria, "Lifetime of Sensor Network by Exploiting Heterogeneity –A Survey", IJMECS Vol. 6, No. 7. MECS 2014.
- W. Wang, Q. Wang, and W. Luo, Sheng, M., Wu, W., Hao, L., "LEACH-H: An Improved Routing Protocol for Collaborative Sensing Networks", Department of Computer Science and Technology China University of Mining and Technology Xuzhou, China, (2009) IEEE.
- W. Jun and Z. Xin, "A Distance-based Clustering Routing Protocol in Wireless Sensor Networks", Journal: IEEE 12th International Conference on Communication Technology, (2010).
- W. Xiaoping, L. Hong and L. Gang, "An Improved Routing Algorithm Based On LEACH Protocol", Journal: International Symposium on Distributed Computing and Applications to Business, Engineering and Science, (2010) IEEE.
- Q. Wang, F. Zhang, L. Hao, H. Liao, M. Xiong and Y. Cheng, "LEACH-ECD: Routing Protocol Based on Energy Consumption", Journal: IEEE 2nd Symposium on Web Society, (2010) IEEE.
- W. Heinzelman, A. Chandrakasan and H. Balakrishnan, "an application-specific protocol architecture for wireless micro-sensor networks", IEEE Transactions on Wireless Communications, 1(4):660~670 (2002).
- W. Heinzelman, A. Chandrakasan and H. Balakrishnan, "Energy-Efficient Communication Protocol for Wireless Micro-sensor Networks", Massachusetts Institute of Technology Cambridge, MA02139, January 4-7, (2000) IEEE.
- W. Xinhua and W. Sheng, "Performance Comparison of LEACH and LEACH-C Protocols by NS2", IEEE Computer Society, International Symposium on Distributed Computing an Application to Business, Engineering and Science (2010).
- T. Madhav and V. Sarma, , "Maximizing Network Lifetime through Varying Transmission Radii with Energy Efficient Cluster Routing Algorithm in Wireless Sensor Networks", International Journal of Information and Electronics Engineering, National Institute of Technology Warangal Deemed University, Warangal, India Vol. 2, No. 2 (2012).
- L. J. Villalba, A. L. Orozco, A. T. Cabrera, C. J. B. Abbas, "Routing Protocols in Wireless Sensor Networks", Received: 14 September 2009; in revised form: 28 September 2009 / Accepted: 10 October 2009 / Published: 26 (2009), ISSN 1424-8220.
- F. Xiangning and S. Yulin, "Improvement on LEACH Protocol of Wireless Sensor Network ", 2007 IEEE.
- Z. Peng and X. Li, "The Improvement and Simulation of LEACH Protocol for WSNs ",2010 IEEE.


