Протокол безопасности локализации беспроводных сенсорных сетей: анализ и производительность
Автор: Омар Фарук, Фариха Ахмад Чоудхури , Абу Саззад Мд Парвез, Нараян Чандра Нат , Преанка Кабирадж
Журнал: Современные инновации, системы и технологии.
Рубрика: Управление, вычислительная техника и информатика
Статья в выпуске: 5 (1), 2025 года.
Бесплатный доступ
Беспроводные сенсорные сети (WSN) требуют обеспечения безопасности для защиты данных в условиях ограниченных ресурсов и неблагоприятных сред. В статье представлен новый механизм безопасности, основанный на использовании MAC (Message Authentication Code) для аутентификации, который защищает передачу данных на базовую станцию от атак вредоносных узлов.
Сенсорные сети, атаки, протоколы безопасности, сенсорные узлы, проблемы безопасности
Короткий адрес: https://sciup.org/14133008
IDR: 14133008 | УДК: 004.056.5 | DOI: 10.47813/2782-2818-2025-5-1-1048-1059
Текст статьи Протокол безопасности локализации беспроводных сенсорных сетей: анализ и производительность
DOI:
Advancements in Microelectronics, Micromechanics, and wireless communication technologies have enabled the production of micro sensors, which are embedded systems that collect and transmit environmental data independently. These micro sensors are considered one of the ten emerging technologies that are transforming our way of life and work [1]. Computer networks are sets of equipment interconnected for information exchange, with nodes at the end of connections. Wireless networks, on the other hand, are computer or digital networks that connect different positions or systems using radio waves. The IEEE802.11 standard, also known as WiFi, is the most widely used standard for wireless networks [2]. Short-range wireless networks (WPAN) are used to connect peripherals like printers, portable telephones, and domestic appliances. Bluetooth Technology, also known as IEEE 802.15.1, offers a theoretical speed of 1 Mbps and a maximum scope of 30 meters [3]. ZigBee Technology, also known as IEEE 802.15.4, offers low prices and low wireless energy consumption, making it suitable for small electronic devices. Infrared Links allow for wireless links from a few meters with speeds up to a few megabits per second, widely used in home automation [4]. Wireless networks cover a range of approximately 100 meters and allow interconnection of terminals. There are two competing technologies: Wi-Fi (Wireless-Fidelity) networks, which come from the IEEE 802.11 standard, and High-Performance LAN 2.0 networks, which have a theoretical throughput of 54 Mbps on an area of one hundred meters in the frequency range of 5150 and 5300 MHz [5]. Loop local radio (BLR) allows the transmission of voice and broadband data by hertz for internet access and telephone. WiMAX networks, originating from the IEEE 802.16 standard, are designed for telecommunications operation and offer a useful flow of 1 to 10Mbits/s in the 10-66 GHz band for a range of 4 to 10km. Mobile cellular networks, known as GSM, GPRS, and UMTS, are the most widespread of all [6], connecting all mobile phones to a wireless wide area network. Wireless sensor networks extend the scope of sensors, allowing them to detect phenomena in similar environments, quantify them, and transmit data to other elements of the system [7, 8].
Wireless sensor networks (WSNs) differ from traditional sensors in several ways. The first is the term "wireless," as motes are more wired and communicate with other elements via a wireless communication module [9-12]. They can also receive data and serve as relays for collected data and information critical to network maintenance. This transmission is made possible through a transceiver, which communicates in three modes: lasers, infrared, or radio frequency [13]. The second distinction is due to a decrease in production costs and miniaturization of components. This allows for the deployment of a larger number of sensors, creating a denser network with greater reliability [14]. The third differentiation is at the energy source level, as motes have an embedded power supply, which limits battery capacity and makes it difficult to replace them when they are discharged [15].
The last difference lies between the data acquisitions phase and the phase of communication. Motes integrate essential energy saving policies in WSNs, reducing the size of messages passed on to other network elements and reducing the time of use of the transceiver. To achieve this, the sensor should have a necessary storage unit for the establishment and implementation of a software program. Additional memory options include Flash type or EPROM memories, Magneto resistive RandomAccess Memory (MRAM), which is fast, nonvolatile, consumes low energy, can be erased and rewritten unlimited times, has a low manufacturing cost, and does not undergo radiation influence [16, 17]. TinyOS is an open-source operating system designed for wireless sensor networks. It consists of a combination of components, reducing the code size required for implementation. The library of TinyOS is complete, including network protocols, sensor drivers, and data acquisition tools, which can be adapted to specific applications. Developed and supported by Berkeley, TinyOS is event-driven, managing tasks based on high-priority events. It is programmed in NesC language and operates in realtime, managing priorities to meet deadlines [18]. TinyOS is designed to minimize energy consumption of sensors, automatically going into standby when no task is active. The architecture of TinyOS includes a mote, processor, RAM, and Flash, radio and antenna, LED, interface, sensor, and battery [19]. Wireless Sensor Networks (WSNs) have unique characteristics, such as reduced energy consumption, scalability, and routing, which necessitate the development of new protocols for access, routing, security, transport, or application.
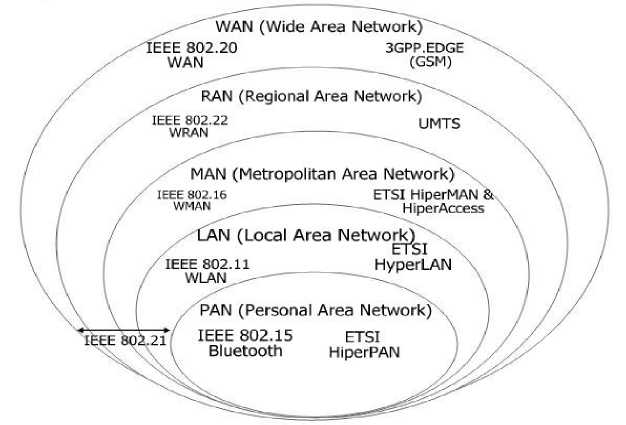
Figure 1. Wireless categories.
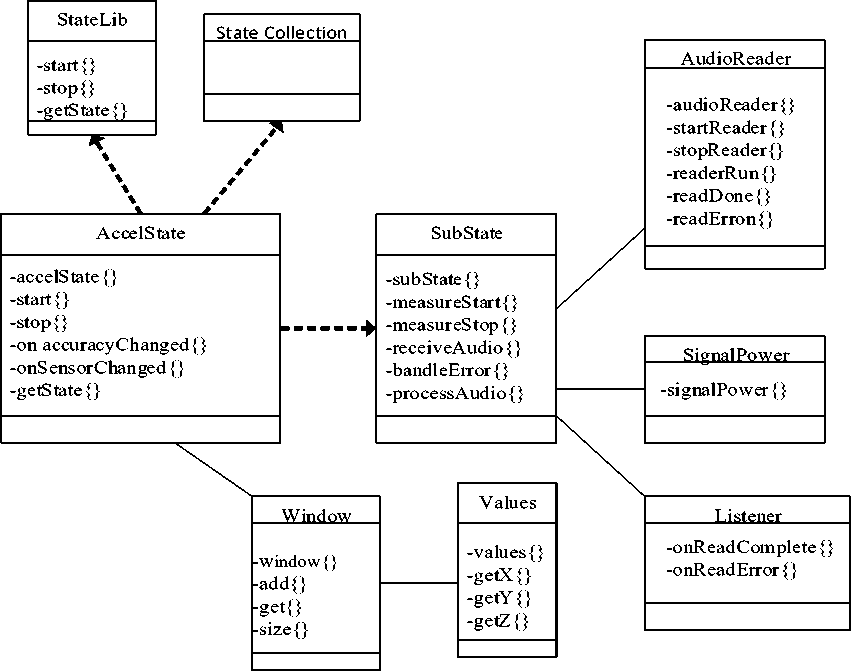
Figure 2. Schematic of a component of a network of sensors, inspired by [10].
REVIEW OF LITERATURE
Since 1992, the use of system and information networks has significantly advanced, requiring increased attention to security. Modern digital technologies, such as infrastructure telecommunications, wireless networks, and computer applications, present vulnerabilities such as security flaws, design defects, and cybercriminal attacks. Sensor networks pose unique safety conditions, including data confidentiality, integrity, data freshness, self-organization, location, and authentication [20, 21]. These factors are crucial for secure data transfer, bi-part communication, and administrative tasks. Wireless Sensor Networks
(WSNs) face security challenges due to limited resources, energy constraints, wireless multihop communications, and tight coupling with the environment [22, 23]. Cryptography, the study of mathematical techniques for security, is used to convert clear information into encrypted information and return the original information. Encryption is a key-based cryptographic system that ensures confidentiality using keys [24]. There are two classes of primitives: symmetrical and asymmetric. Symmetric encryption uses the same key between two communicating nodes, while string encryption is done bit by bit without waiting for data reception. Block ciphers split data into blocks of fixed size, and encryption is performed once each block reaches a proposed size [25]. Symmetric encryption algorithms, such as RC4, are fast and effective but require significant energy dissipation during encryption and decryption phases [26]. Asymmetric encryption involves two different keys generated by the receiver, a public key broadcasted to all nodes for data encryption and a private key kept secret at the receiver for data decryption. Rivest Shamir Adleman (RSA) is the best-known asymmetric encryption algorithm. The routing layer in Wireless Sensor Networks (WSN) is responsible for correctly routing data from one point to another. However, WSN routing protocols are vulnerable to attacks, which can be classified into active and passive categories. Solutions to attacks on data routing in WSN include prevention against active attacks using cryptography, detection of suspicious behavior, and tolerance. INSENS is an intrusion-tolerant routing protocol designed for wireless sensor networks that aims to provide secure routing for each sensor table, even in the presence of intruders [27-29]. The protocol is divided into phases, including Authenticated initiation of the tree construction, construction of the tree by forwarding the request, and route feedback. SecRoute protocol is a secure hierarchical routing protocol that uses a two-tier architecture to organize the network into clusters, each with a leader. Data relay in a Wireless Sensor Network (WSN) involves two stages: member nodes emit data to the leader, who then sends the summary to the collector [26]. The leader aggregates data from members after verifying the MAC from each package, and then emits the summary to the collector. If no route to the collector is known, the process of discovery of paths must be performed. SAWN (Secure Aggregation for Wireless Networks) ensures secure data aggregation in wireless networks using two jumps to verify the aggregation of data [30]. The SAWN protocol aims to authenticate all readings in the aggregate value without receiving all readings.
METHODOLOGY
The proposed security mechanism for Wireless Sensor Networks (WSN) aims to protect data transfer from intruder attacks using a message from control MAC (Message Authentication Code). The protocol consists of an intruder detection system for wireless sensor networks, which can be distributed, centralized, or hybrid. The base station maintains a table of trust for each node in the network, based on their degree of confidence in a suspicious routing path. During communication, the base station uses a control based on the MAC message to ensure the integrity of the sent message and verify the identity of the transmitter.
A MAC is therefore an algorithm that takes as input a message m, a key K and which produces a digest, a tag:
tag = MACK(m)
The verification algorithm for the receiver checks if the received message has not changed during the transmission. In a network of sensors, the end-to-end MAC (MAC) is checked between the base station and each node sending a message. Each node sends a MAC at random times, and when two messages arrive at the base station, the contents are compared. If the content is identical, the path is secured, otherwise, it is reported as insecure. The base station then initiates a process to detect any modifications or tampering in the message [31]. If intruder nodes are detected, routing paths are reconfigured separately.
The proposed security mechanism consists of several algorithms, each dedicated to a specific application. The HEEP routing protocol organizes nodes within a cluster to improve energy dissipation and reduce the load on the cluster head. This reduces data exchange between nodes and their cluster head, preserving energy reserves. The HEEP protocol reduces the number of nodes communicating with the CH, resulting in better energy savings and extended CH lifespan [32]. It uses random rotation and PEGASIS to regulate energy dissipation, preventing nodes far from CHs from depleting their energy reserve. Media access is similar to LEACH, with CHs establishing a transmission plan (TDMA schedule) at each node, ensuring accurate data transmission [33].
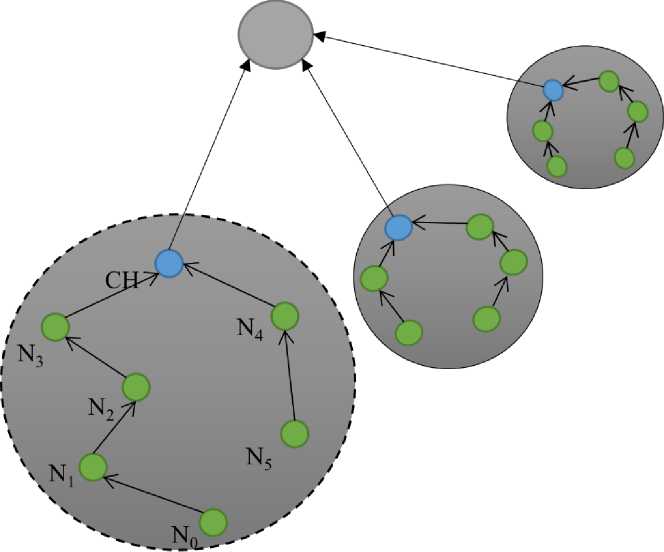
Figure 3. Organization of the node in the network.
ANALYSIS OF SECURITY
In this section we assess the performance of our security protocol over the following safety conditions:
A system for wireless sensor networks that is resistant to intrusions is called INSENS. The goal of the protocol is to make it possible for the BS to create an accurate network map that will provide the routing information for each sensor table. The impacted nodes will get these tables in a safe way later on. The protocol aims to accomplish two things.
At regular intervals, the BS will initiate a request to rebuild the sensor routing tables. Here is the format of the message:
Type|ows|size|path|MACR
For query I, the value of the hash string is indicated by the ows (one-way sequence number) field, which is set to ni. The most recent value received from ows, denoted by owsfresh, is stored locally by every node. Upon receiving a query, node x verifies its validity and timeliness using the following relationship.
Determine j such that ows=hj(owsfresh) and j> 0.
A receiving node x updates the path field with its own identification and computes the MACRx field based on the prior request message:
MACRx is equal to MAC(kx|size|path|ows|type)*.
The node waits for a while after the query is issued before sending feedback to the BS. During this time, it may safely gather data about its immediate vicinity, which will help the BS build a picture of the network. Here is the information included in one feedback message: This is the output of the MACRupstream function called MACFx.
type|ows|path_info|nbr_info|MACRupstream|MAC Fx.
In the 'path_info' field, you may find the MACR, the list of nodes that go from node x to the BS, and x's identity.
IDx|size|path|MACRx
The “nbr_info” field contains a list of identifiers of the neighbors as well as their MACR:
Size|Ida|MACRa|IDb|MACRb|…
MACFx field is calculated as follows:
MACFx=MAC (kx, path_info|nbr_info|ows|type)
The next step is to find an alternate path in the subgraph that does not include any nodes, neighbors, or neighbors' neighbors from the first path. Assuming it doesn't work, we try adding all of the neighbors' neighbors again. If that doesn't work either, we try adding all of the neighbors. Each route is recorded by the BS's relay table, which is computed for each sensor [30]. This table is described by the following statement:
Type|ows|size|routingTable|MAC
Where the MAC is calculated as follows:
MAC= MAC (kx, type|ows|size|table)
Data confidentiality and Authentication
OF PACKETS
In order to guarantee the confidentiality and authentication of message we use a secret key session, when an intruder is detected, the base station reconfigures the network with a new secret key, which does not give hackers the time to explore the secret key, the secure key distribution method does not take charge in our approach, so it is assumed that there is a secure secret key distribution mechanism for each session.
Data Integrity
In our security protocol we focus on the detection of intruders that affects the integrity of the data, the MAC (message authentication mechanism code) mechanism was used for this. For our protocol, the MAC is used as a control message to detect attackers who falsify data or inject packets. When an attacker transfers control messages that are received by the base station, it detects that there is a non-secure way that automatically contains one or more intruders, in this case the base station runs the algorithm to search for intruders [34, 35].
Implementation
In order to implement our protocol, we reused the implementation code of HEEP protocol, and made some changes at several levels. These changes consist of injecting new pieces of code such as for example the procedure of sending of data, procedure of receipt of packages by the base station, procedure of creation of TDMA schedule for chains nodes, etc [36].
Proposed Protocol Implementation
After our implementation environment, begins the protocol implementation step which is to modify the implementation code of HEEP protocol so that it matches the architecture of operation of our protocol. To do this, we added various functions and procedures such as how to send a data, data reception procedure, for creation of TDMA schedule for chains of nodes, etc. Indeed, the implementation code proposed is composed of multiple TCL files each playing a specific role [37]. Thus, we reuse it and we had to analyze and understand the role of each of these files. Because a TCL file is presented as a class that contains several subclasses, the proposed protocol is seen as a set of classes that communicate to achieve a common task. The proposed protocol is a specific application of security protocols to the routing level of data. It is implemented as class-to-class Applications of the NS2 Simulator. In this work we have implemented a new security mechanism dedicated to the routing for the WSN protocols. This mechanism is to protect the process of data transfer based on a special intruder node discover node discovery algorithm. The simulations conducted with our protocol demonstrate the performance of the latter. In perspective, there are plans to try out other security protocol mechanisms of routing in order to refine the performance of our algorithm.
The security mechanism was simulated using the Network Simulator (NS2), a free open-source software developed within the VINT project. The HEEP Protocol, a routing protocol based on clustering of chains, was chosen for testing the security mechanism. The HEEP Protocol reduces transmission distance by creating data paths as strings of adjacent nodes in each cell. NS2 is a C++ and OTCL simulator that supports wireless and wired networks with various protocols. It is the most used simulator in research for testing new protocols. The experimentation model is based on 100 randomly scattered nodes on a 100 m square surface, with a fixed position for all nodes during the simulation period. The simulation duration is 60s, and the number of intruder nodes is 10. Hackers change all packages they retransmit. The simulation settings are summarized in a table.
T able 1: S imulation parameters .
|
Parameters |
Value |
|
Location of the BS |
20,175 |
|
The Number of Nodes |
100 |
|
The Number of clusters |
5 |
|
Muzzle energy |
2J |
|
The packet size |
512 bytes |
|
Control package size |
8 bytes |
The effectiveness of our security solution in terms of its resistance to attacks, data manipulation, and fabrication is evaluated by the driving simulation. Each 10-second interval makes up a portion of the total simulation time.
T able 2. R esults of simulation .
|
Criteria |
0-10s |
10-20s |
20-30s |
30-40s |
40-50s |
50-60s |
|
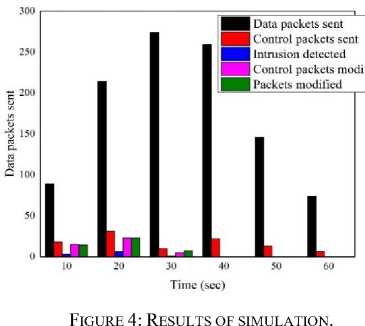
No. of packets from sent data |
89 |
214 |
274 |
259 |
146 |
74 |
|
No. of packets from sent data |
18 |
31 |
10 |
22 |
13 |
6 |
|
No. of packets from modified data |
14 |
23 |
7 |
0 |
0 |
0 |
|
No. of packets from modified control |
15 |
23 |
5 |
0 |
0 |
0 |
|
No. of intruders detected |
3 |
6 |
I |
0 |
0 |
0 |
We measured the amount of data and control packets transmitted to the base station throughout each time period, taking note of changes in both the packet quantity and the number of recognized intruder nodes. The simulation results are included in Table 2 and 3. The simulation output graphs are included in Figures 4, 5 and 6.
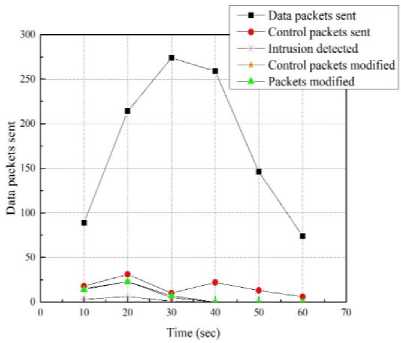
Figure 5. Result of simulation comparison of our approach with HEPP and LEACH-C.
T able 3. P ercentage of number of lively nodes .
|
0s -10s |
10s - 20s |
20s- 30s |
30s - 40s |
40s - 50s |
50s - 60s |
|
|
Percentage of Number of lively nodes |
||||||
|
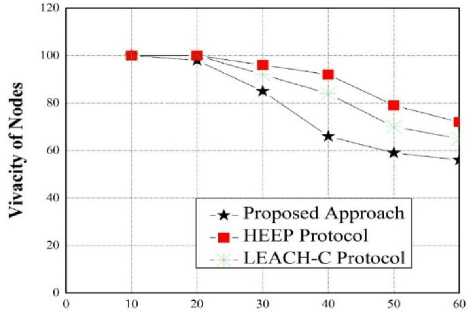
The HEEP protocol |
100 |
100 |
96 |
92 |
79 |
72 |
|
The LEACH-C protocol |
100 |
100 |
92 |
84 |
70 |
65 |
|
Approach proposed |
100 |
98 |
85 |
66 |
59 |
56 |
Time (sec)
Figure 6. Comparison of vivacity of the nodes between the HEEP protocols, LEACH-C and out approach.
Simulation results demonstrated our approach to security ensured a secured communication after two or three cycles of reconfiguration of the cluster, however HEEP and LEACH-C protocols present vulnerability throughout the period of simulation. Energy is a very important factor for any approach to security proposed in WSN, for this, we measured and compared the energy consumption of our approach with the HEEP and LEACH-C protocols. The energy consumed to send messages from controls and reconfiguration of cluster, because the mortality deference of nodes of our approach with the other two HEEP and LEACH-C protocols, but this deference is accepted to ensure a secure communication [38].
The driving simulation evaluates the performance of a security mechanism in terms of resistance against attacks, modification, and falsification of data. The simulation time is divided into several intervals of 10 seconds, and the results are summarized in table 3, figures 4-6. The simulation results demonstrate that our approach ensures secure communication after two or three cycles of reconfiguration of the cluster [34]. However, HEEP and LEACH-C protocols present vulnerability throughout the period of simulation. Energy consumption is a crucial factor for any approach to security proposed in Wireless Sensor Networks (WSN) [39]. The study also measures and compares the energy consumption of our approach with the HEEP and LEACH-C protocols.
The simulation results demonstrate the capability of our algorithm to secure the process of data transfer. The detection of intruder nodes increases as new sensor nodes are involved in data transfer, reducing the percentage of mortality of nodes when intruders are detected. This indicates high reliability of our approach when the time of simulation is increased. This study discusses the essential characteristics of wireless network sensors and the needs and challenges of security in these systems. Key management schemes proposed for WSNs are based on symmetric key cryptography and pre-release of key method to establish keys between communicating entities in the network. The future target of this research is to develop a new authentication protocol or approach that incorporates all the best features of existing security mechanisms and optimizes implementation in wireless sensor networks.
Recent Advantages and Challenges
Smart textiles are revolutionizing the global textile industry, with the potential to revolutionize personal healthcare, sportswear, and other end-use industries. The global market for smart textiles, which began in the late 1980s, has expanded to include temperatureregulating suits, shape-memory and environment-responsive fabrics, and self-cleaning carpets. These textiles are used in sports, protective gear, casual wear, geotextiles, biomedical textiles, and apparel, particularly for winter wear. The Gore Company created Gore-Tex in 1978, the first intelligent fabric, which is windproof, waterproof, and breathable. The market is projected to grow at a 25% CAGR between 2021 and 2031, reaching a valuation of US$23.82 by the end of that year. Recent advancements in smart textile performance include space transportation systems, sportswear, ultrasonic assembly, and space travel fabric. The application field is broad, including automotive, medical, and healthcare sectors. The growth rate is driven by the pursuit of lightweight and comfortable materials for sports and fitness applications [40]. However, compatibility issues between fabrics and electronic systems limit the use of certain smart textiles. The market is expected to exhibit profitable development prospects and applications across various end-use industries.
CONCLUSION
The simulation results demonstrate the capability of our algorithm to secure the process of data transfer. The detection of intruder nodes increases as the new sensor nodes are involved in data transfer so the percentage of mortality of nodes is decreased when intruders are detected. It can be inferred that the reliability of our approach is high when the time of simulation is increased. In this study we put forth the essential characteristics of wireless network sensors, and the needs and the challenges of security in the latter. We studied also some key management schemes that offer the service of basic security for any system based on communication. The whole of the key management protocols proposed for the WSNs are based mainly on the symmetric key cryptography and prerelease of key method to complete the establishment of keys between communicating entities in the network. The future target of this research is to develop a new authentication protocol or approach that should incorporate all the best features of existing security mechanisms and should be optimized for implementation in wireless sensor networks.


