Reliable Communication in Delay Tolerant Network by Utilizing the Concept of Acknowledgement based Hop by Hop Retransmission
Автор: S. Dheenathayalan
Журнал: International Journal of Computer Network and Information Security @ijcnis
Статья в выпуске: 6 vol.17, 2025 года.
Бесплатный доступ
A delay-tolerant network is one that may temporarily hold packets at intermediate nodes while waiting for an end-to-end route to be rebuilt or restored. Due to the difficulty of establishing reliable routing in such a network, we use the Wavelength Routing Algorithm-based idea of hop-by-hop retransmission acknowledgement. It calculates the blocking probability for each connection request and decides whether the connection proceeds or not. This helps to reduce power consumption and the available resources. During retransmission, the intermediate nodes may have some duplicate messages; we utilize the concept of Cuckoo search to omit the duplicate messages. Our proposed mechanism is implemented in the ONE simulator, which states the performance of our reliable communication in comparison with other existing algorithms.
Wavelength Routing Algorithm, Cuckoo Search, Reliable Communication, Hop by Hop Retransmission
Короткий адрес: https://sciup.org/15020111
IDR: 15020111 | DOI: 10.5815/ijcnis.2025.06.02
Текст научной статьи Reliable Communication in Delay Tolerant Network by Utilizing the Concept of Acknowledgement based Hop by Hop Retransmission
In general, a computer network is a collection of computers that are linked together for the purposes of resource sharing, file sharing, and communication. There are two different kinds of network connections: wired and wireless [1]. A heterogeneous wireless network is a wireless LAN with multiple access technologies that can continue service when switching to a cellular network [2]. These heterogeneous networks are preferred due to its dynamic topologies and resource constraints such as buffer space, energy utilization, and bandwidth restrictions. A type of challenging network known as a delay-tolerant network supports collaboration between different wireless local area networks [3]. Due to inconsistent connectivity, DTN cannot offer reliable delivery. Congestion is a result of the restricted network resources that are present. These networks were lack in terms of end-to-end connections between the nodes because of node mobility and constrained power sources [4]. To get around the patch connectivity, DTN nodes store and carry the data packets until the nodes are in the communication range. The nodes distributed many copies of the same packet around the network to increase the likelihood of delivery. Numerous routing protocols, including Spary and Wait, PROPHET, and Epidemic, have been created recently with DTNs in mind [5]. The information used by these protocols to direct the packets to their destinations and the number of copies they propagate vary. Because they depend on constant end-to-end connectivity between sources and destinations, conventional routing techniques for wired and wireless networks cannot function in this situation. Simple DTN routing systems have no selection criteria and forward packet copies to any node they come into touch with [6]. They range from partial flooding to full network inundation.
Due to these difficulties, data handling is done with the best effort feasible, and the goal is to transmit data as reliably as possible. To increase the delivery ratio and guarantee message delivery in such a situation, the suggested routing strategies use several copies of each message [7]. The bulk of these routing techniques select the nodes that will take part in the message routing without taking their remaining energy into account or taking into account the past of the relays that have already gotten a copy of the message [8]. Delay Tolerant Networks (DTNs) are a new type of network distinct from traditional TCP/IP networks. It is suitable for challenging circumstances where establishing a reliable end-to-end communication connection is impossible. When network nodes come together, they copy information to relay messages via the replication-based DTN routing algorithm [9]. As a result, there will be a lot of message replicas in the network during the delivery process, which will obviously use up a lot of network resources [10]. The network is sparse and broad, and there is no assertion of end-to-end communication between the network's nodes, making message delivery difficult [11, 12].
To guarantee the dependability of message transmission, Wavelength Routing Technique includes a retransmission acknowledgement protocol hop-by-hop. To maintain the buffer capacity, the blocking probability for each connection request is determined. The network nodes may contain some duplicate messages when using the retransmission idea. We provide the idea of the Cuckoo search method to get rid of duplicate communications. Our main goal was to suggest a routing algorithm for a dependable and effective data transfer that relies on acknowledgement based hop-by-hop retransmission mechanism and enables nodes to convert effortlessly to delay-tolerant transmission.
The paper is structured as follows. Literature reviews are comprehended in chapter 2. A detailed explanation of the proposed networking algorithm is given in chapter 3. The results are discussed in chapter 4. Chapter 5 gives the conclusion about the proposed work.
2. Related Works
Han and Chung [13] used the epidemic protocol to hasten the adoption of the Probability Routing Protocol utilizing the History of Encounters and Transitivity (PRoPHET) if the forwarding nodes and hop node values were less than or equal to the threshold values. The performance measures, such as overhead ratio, average time, and delivery probability were evaluated. The PRoPHET Protocol can improve its delivery likelihood, average delay, and overhead ratio by carefully selecting the threshold value for the forwarding counter and hop counter. The performance can be improved further by an adaptive selection of threshold values for the forwarding counter and threshold hop counter.
Yu et al. [14] proposed a novel routing protocol based on message delivery probability and message redundant to decrease communication overhead. Based on the effects of both frequency and contact time, this method calculates the likelihood that a message will be delivered. The maximum number of message copies is also specified by the source node, and relay nodes are charged with transmitting message copies in accordance with a binary tree's pattern. This allows for the implementation of multi-path parallel transmission for message forwarding.
A strategy to choose a node's neighbours in order to build a high-quality social network is suggested by Song et al. [15]. Utilizing the created social graph, a hybrid popularity metric may be used to gauge a node's influence on the network. In addition to implying a node's ability to connect its neighbours, node popularity also provides an estimate of the message's potential reach following two-hop relays. Then, in order to save network resources and boost message delivery rates, two routing algorithms depending on node popularity were presented. In order to enhance the performance of the DTN, it is intended to focus on recognizing other social ties, such as social community.
A Trust based Intelligent Routing Algorithm was proposed by Singh et al. [16]. Artificial neural networks have the ability to compute, learn, and develop common values of trust. This approach reduces the demand for nodes' resources, such as energy use, processing time, and space overheads. The suggested algorithm improves the routing efficiency of delay tolerant networks. In most cases, earlier work that makes efficiency claims ends up using network resources. On the other hand, the suggested algorithm comes with built-in security without any more work. Future studies may examine how well the TBIR in DTN applies to real-world situations.
Liu et al. [17] proposed a novel model for the maximum throughput routing problem. In their work, a set of k splittable multi-commodity flows with equal demands were given. Then, the subset of flow with n – node network was choosen and the routing process was initialized. The main contribution of the work was the development of the first k-and n-independent constant throughput approximation method for an NP-hard problem with a sublinear edge capacity violation ratio of O (k).
3. Proposed Methodology
The primary objective is to transmit as many messages as possible to their intended recipients without any loss by using an acknowledgement based hop-by-hop retransmission mechanism for dependable and effective data transport. The majority of the time in DTN, the whole path from source to target does not exist, making it challenging to route packets in such a situation. For this, the messages will be transmitted to other intermittent nodes in the DTN by taking into account the transmission range, each node's storage space and message size by gathering evidence about other nodes in the network. The transition probabilities between encountered nodes and the message destination and the transition probabilities between encountered nodes and nodes that have previously received a message copy are the two key pieces of information that the nodes use when exchanging messages. With the use of this technique, nodes are able to cease transmitting messages to relays that have already taken a copy of the message before it reaches its intended destination. Wavelength Routing Technique includes a retransmission acknowledgement protocol hop-by-hop is used in this proposed approach to guarantee the dependability of message transmission. To maintain the buffer capacity, the blocking probability for each connection request is determined. The network nodes may contain some duplicate messages when using the retransmission idea. We provide the idea of the Cuckoo search method to get rid of duplicate communications.
Network Characteristics
Considerations for network environment:
-
• There is no direct path from source to target; the nodes can only communicate with one another when they are physically close to one another and cannot predict in advance if contacts will be available in the future.
-
• Limited storage space and power availability.
-
• There could be repeated connectivity failures.
Collecting information
During this phase, network nodes gather data from other nodes and store it in their routing tables. To avoid power consumption, unnecessary route updates, and other issues, the routing table is updated reactively. Proactive table updates will increase resource and power consumption since DTN is characterized by scarce power sources, constrained data storage, network links that are prone to failure, and a lack of connectivity. The nodes exchange information on a variety of topics, including buffer space, energy level, and the number of nodes that are typically encountered while travelling to a specific area. The communication between the two nodes is shown in Figure 1. The acquired information will be used in the routing procedure to search for relay nodes that have a higher probability of delivering the message to its destination.
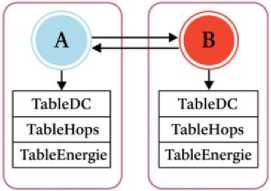
Fig.1. The communication of information between nodes A and B
The information transmission between nodes A and B is shown in Figure 1 above. All nodes in the network gather data about one another to ensure the dependable delivery of packets. These tables are used to implement routing.
Using the Hop-by-hop retransmission acknowledgement technique for DTN routing
Data packets are moved from their source to their destination through the routing procedure. The lack of connectivity between nodes, lack of buffer space, lack of energy, dependability, and other factors make routing in the DTN challenging. Therefore, the first problem to be resolved is reliable data transport. We must suggest a solution that can address the aforementioned problems to improve the DTN's ability to communicate reliably. Here, using the Wavelength Assignment (RWA) algorithm as the hop-by-hop retransmission acknowledgement mechanism, we present an effective routing method. The link state i,0 < i < К — 1at time t, for example, can be stated as a column vector represented in eqn. 1 if there are K links with W wavelengths.
°tm = (ot(\0),ot(\1),....,ot(\W—1^^^^ 1 (1)
Eqn. 1 above, the network connectivity between the nodes is represented by the column vector. If a connection between the nodes at time t uses the wavelength Л у , the column vector will be written as in equation 2:
Ot = (ot(0),....,Ot(*-1)) (2)
Our routing algorithm looks for P = (i 1 , i2,...., i i ) an at time t if a connection request comes in from any source to a certain destination node, such that Ot!lk)(j) = 0 for every k=1, 2,..., l and some j. The routing table is used for path discovery in a network to provide a dependable connection while taking buffer space, energy level, and other factors into account. At time t, a random connection request is received from any source node, and connections that are already established will end after a random amount of time. Here, we use a network status matrix to visualize the connection connectivity. A single path is assigned by a fixed column in the network state matrix format if routing is fixed for each pair. A single path Psd is assigned by a fixed column in the network state matrix at if routing is fixed for each pair (s, d). It chooses a row with no items in any of the columns for simplicity's sake. Since we display the wavelengths as a row vector, the wavelength item becomes 0 if the routing is fixed means (from eqn2.). For instance, it begins with A0and continues until an appropriate wavelength is found. The degree to which the pathfinding is adjusted dynamically depends on the state of the network ot. Our proposed routing algorithm selects the best path based on the network status ot at the time of connection formation. A search over the network state matrix's rows and columns can be compared to the process of finding a route and a wavelength assignment.
Traffic analysis and Buffer management
The connection demand (s,d) is established with duration t to reach the destination. In this process, each row displays the topology with the corresponding feasible wavelength. The proposed method sequentially involves scanning across wavelength sets until the open path is found. To find a path on effective topology, a standard shortest path algorithm is used. The connection request is terminated to conserve resources if there is no path after exhausting all of the set's wavelengths.
After some time, let's find that there is no method to establish communication between any source and destination nodes, regardless of our efforts. It will impact the processing time and the resources that are available. By initially blocking the impossible transmission, the available buffer space is controlled. Any set of nodes' connection requests will be treated as Poisson distributions with an assumed average arrival rate p r for the rth s — dpair. The period of time between the request and the creation of the connection follows a mean 1/^ Let ar — Pr/ir exponential distribution. Let К represent the number of network links and R represent the number of network pairs s — d . S is the link-path incidence matrix К x RL, which is defined as
' — (,
1, if _link_i_is_utilized_on_path_j
0, other-wise
The value of S will be "1" if the link is used on a specific path and "0" otherwise. This incidence matrix assists in locating the established network path that will lessen traffic or congestion. For the first pair, we represent the determined path as well as the alternative paths (if any connection fails due to a network fault) as a column "L" to examine the traffic through the network. Running indices are r, l, I w, and z for the s — dpair, physical alternate paths, logical path (a mix of physical path and wavelength), wavelength, and connections, respectively. The ith logical path's provided traffic with rth s — d pair be A^. Let azWthe traffic from the rth stream on the Ith alternating path be the traffic given to wavelength w on link z, and let azw the traffic from all traffic streams, i.e., azw
— T^i^ a zW
If
x
represents a quantity of offered traffic, then let use
X
to represent the same quantity of transported traffic. Let's define
F[
as the likelihood that a call from the
rth
traffic stream roverflows to the ith logical path,
Bzw
as the likelihood that a wavelength wwill be used on the connection z, and
RI'
as the jamming probability on the ith logical path of the traffic stream. Each link's state zis represented by a Wcomponent binary vector j(z), where wavelength I on a link's ith entry
Computation of Blocking probability
The entries in the state vector are supposed to be independent statistically. Moreover, the entries are not evenly distributed because of the asymmetry offered by the fixed-order wavelength search. After making an assumption that the link-blocking events are separate, the wavelength continuity restriction for determining the offered traffic for the links is not considered. These assumptions are typical in the circuit-switched network blocking analysis. We first set A ' = ar and F Q — 1 then compute the blocking probability. Next, s — d for each pair, we scan the route trees and carry out the following process for each logical path (i = 0,1,..., LW — 1).
Calculate the carried load for the ith logical path's rth stream using this formula
r
At = A ' (1 — P[) = A ' Пкк -1 (1 — Bk , imoa w )Sk ,(r-i) L+l _i/w_! (5)
For all streams r = 1,2, ..., R. This phrase presupposed independence between the link-blocking occurrences.
Utilize the fact that traffic on a connection on a logical path carried by a stream r is identical to the traffic on that logical path carried by the rth stream to acquire rl _ azl,imodW _ ^TnE-Xl—^k.ijnoirw^^
z,
imo
Regarding every link z on the l th alternate path of the traffic stream r.
Then, given traffic stream r, determine the likelihood of overflow and the offered traffic to the (i + 1)h logical path as
К +1 —№
r _ rrPr
Ai+1 — AiPi
Until all logical pathways of all pairs s — d have been examined, this process is repeated. The total provided load azw for each z and w is presented at the end of the procedure as a function of the link-blocking probabilities Bzw.
The Erlang loss formula then roughly approximates the link-blocking probability as
E(A,N) = AN/N!/X fL0 Ai/i!as
у R yL nrl yr=iLi=i^w
Dz,w C(azw, 1) -ij-vR vL „rl
1+ L r=i L i=i a Zw
In order to find Bzw for all z and all w, a set of nonlinear equations defined by equations (8) and (10) must be solved.
The blocking probability of the rth stream is determined once the Bzw values are acquired as P ^ = F [ w, and the average blocking probability is provided by
x R^i F r^
P av £R =i a r
Observe that the nonlinear equation system has the following form. Bzw = azw(B)/1 + azw(B), where B = (B 00 ,...., BK-10,..., B0w-1,...., BK-1w-1). An iterative procedure described by
Bzw (n+1') =
H zw (B(n))
1+a Zw (B(n))
The iterations continue until B(n + 1) and they fall under the set tolerance.
Hop-by-hop retransmission acknowledgement
In the above phase, the Blocking probability for any communication request is calculated, which helps to determine the unavailable paths for the reduction of resource consumption and unwanted processing. We determine the optimized path for any communication by utilizing the network state matrix and the incidence matrix. For the optimized paths, the connection between the source and destination are established and the packet gets transmitted over the established path. But we didn't have any acknowledgement about the delivery and loss of packets in the network. Our main focus is to provide a reliable delivery in DTN. For that, the efficient mechanism is to provide an acknowledgement about the delivery of packets, and for the packet loss, a retransmission mechanism should be used. In particular, the acknowledgement based Hop by Hop Retransmission Acknowledgement Mechanism is used to ensure dependable network connection.
If the transmission takes place, then the data stream is initially sent from the source node to the next hop. As soon as a packet is determined to be accurate, the intermediate nodes in the network issue a request for retransmission with negative acknowledgement. After receiving the correct packet without any loss, it sends a positive acknowledgement to the sender to indicate the successful reception of the data packet. Likewise, all the intermediate nodes in the network receive the packet and send the positive or negative acknowledgement based on the reception of packets to ensure reliable communication in DTN. Acknowledgement based hop by hop retransmission is depicted in figure 2. In the figure S is the source node, D is the destination node, while A and B are the network's intermediary hops. When a data packet is successfully sent from S to A and returned, a positive ACK is sent to S. Then A transmits this unsuccessful packet to B, along with a retransmission request and a NACK. The packet is successfully sent to D after being successfully retransmitted by A to B, and the trustworthy delivery is verified by the hop-by-hop retransmission acknowledgement process.
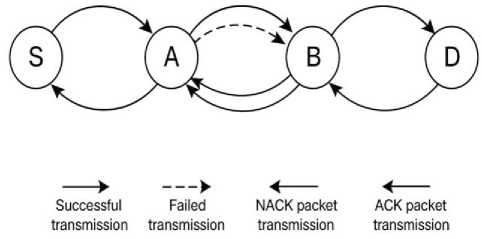
Fig.2. Hop-by-hop retransmission acknowledgement
Figure 2 shows the packets from source to destination are transmitted successfully, but the intermediate nodes may have duplicate copies of the same messages, which will overutilize the available buffer space. To eliminate duplicate messages, we utilize the concept of the Cuckoo search algorithm, which is explained in the following sections.
Elimination of Duplicate Messages
To reduce buffer utilization and ensure reliable communication, duplicate messages in the network hosts must be found and removed. To do that, we must use a unique search algorithm. We make use of the cuckoo search idea. A host bird will either discard the alien eggs or simply depart its nest and create a new nest somewhere to enhance its reproductive capacity if it realizes the eggs are not its own. In a manner similar to that, duplicate messages in network hosts are found and removed. Duplicate messages will be removed from a node, and the buffer space will be reserved for the subsequent packets. Below is a description of how the Cuckoo search algorithm operating.
Algorithm
Start objective function f(x) where x = (x1,..., xd)T;
Initialize a collection of
n
packets
(xi)
with i=1, 2,..., n; while (t
Grab a packet at random. Let's say i
Determine whether or not it is a duplicate; Fi
Pick a packet at random from n (let's say j); if (Fi > Fj)
replace j with the new packet; end
Throw away a duplicate packet (Pa)
Keep the original packet that was delivered appropriately; finalize while visualizing the outcomes;
finalize
4. Results and Discussion
The framework for Reliable and efficient data transfer is implemented in the DTN by utilizing the concept of acknowledgement based hop-by-hop retransmission mechanism. With this concept, there may exist some duplicate messages. To remove the unwanted duplicate messages, we utilize the concept of cuckoo search in the network to reduce resource usage and power consumption for the reliable delivery of messages.
t able 1 . s tatistical test
|
Performance |
100 nodes |
200 nodes |
300 nodes |
400 nodes |
|
Sum of squares |
225.653923 |
2476.289429 |
373.655283 |
654.042928 |
|
Degree of freedom |
2.0 |
2.0 |
2.0 |
2.0 |
|
F-value |
26.728684 |
28.200983 |
36.666125 |
69.365753 |
|
P-value |
5.955749e-11 |
6.957516e-13 |
7.244053e-Z0 |
5.299287e-33 |
Table 1 shows the statistical analysis test for the proposed approach. Sum of squares, degree of freedom, F-value and P-value are the statistical tests taken for this proposed approach by changing the node count from 100 to 400.
Simulation environment
With a set of 25 nodes, each with a storage capacity of 250 MB, we deploy our suggested framework in the ONE simulator (Opportunistic Network Environment Simulator) platform in order to assess its performance. Here, we contrast our suggested framework with the current routing protocols, including ProPHET, Spray and Wait, and Epidemic (the same platform with the same configurations and parameters). Figure 3 below depicts the simulation of our suggested framework's dependable and effective routing.
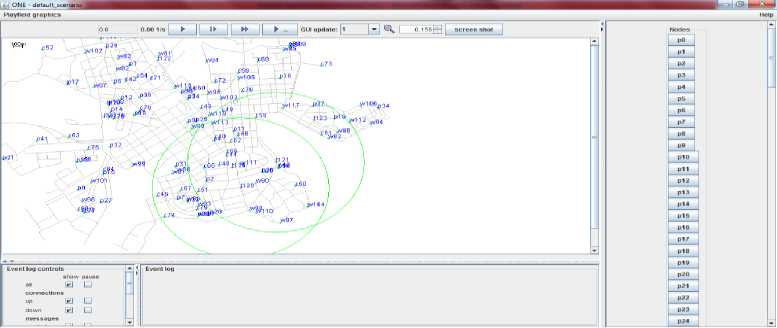
Fig.3. Network setup and the communication range
The above figure illustrates the environmental setup of our proposed implementation. Table 2 below shows the simulation area, transmission rate, number of nodes, transmission range, movement model, storage space of each node, simulation duration, speed, waiting time, message size, and the amount of time needed to transmit a message in our implementation.
Table 2. Simulation parameters of our proposed framework
|
Area of simulation |
100m X 100m |
|
Transmission Rate |
120 ms |
|
Groups of nodes |
25 |
|
Transmission range |
10 m |
|
Movement model |
Mobility model |
|
Each nodes Storage Space |
250 MB |
|
Simulation time |
17 sec |
|
Speed Range |
12 Gbps |
|
Range of Wait Time |
0.342 ns |
|
Message size |
25 kb |
|
Generation time of Messages |
0.5334 ns |
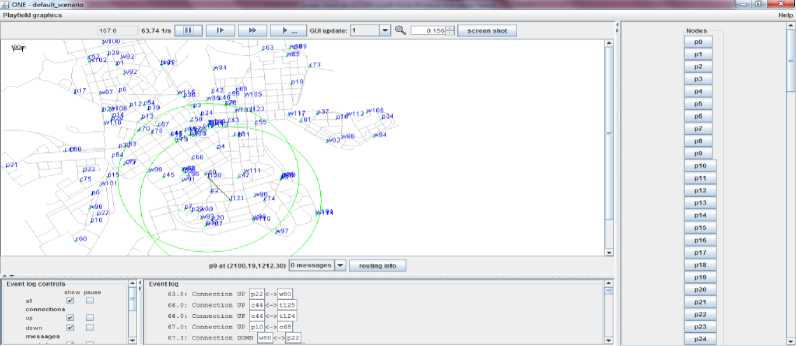
Fig.4. Determining the best path for routing
The above figure 4 represents the best path finding of our proposed methodology. By using our proposed concept, we determine the optimal best path by considering the battery level, buffer space available in each node and so on. This consideration will be very effective for the reliable delivery of messages over the heterogeneous network. If we forward a message to the node with low battery power, then the message will be lost in the network within a short period, i.e., before reaching the destination node. The blocking probability was also calculated for each connection request.
Fig.5. Packet transmission over the determined path
Figure 5 demonstrates the packet transmission over the determined path by our proposed methodology. By forwarding the messages over the determined path, the packet delivery rate will be effectively high.
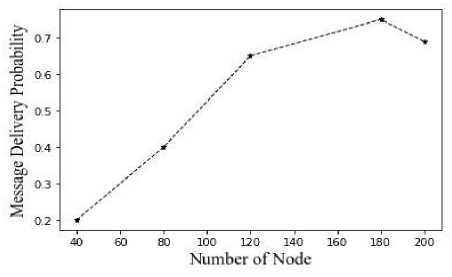
Fig.6. Average message delivery probability vs number of nodes
Figure 6 shows the average message delivery probability of the proposed system with the number of nodes in the delay-tolerant network. The more nodes, the greater the chance that a message will be delivered. As the number of nodes rises, the message delivery is also increased. This indicates that a system with more nodes could still operate efficiently using our suggestion.
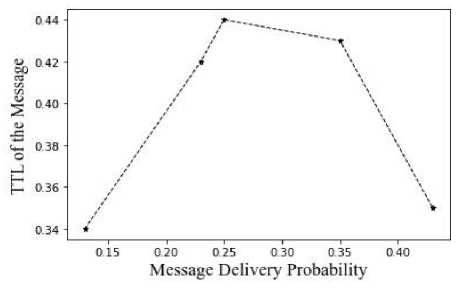
Fig.7. Average message delivery probability vs time to live of the messages
The probability of a message being delivered in relation to its time to live is shown in the above graph figure 7. The delivery probability increases if the TTL is larger. Even when the fastest way to send a specific packet is time-consuming, the packet can still be sent reliably. The greatest period of time that a message can be flooded into the network is called the time to live.
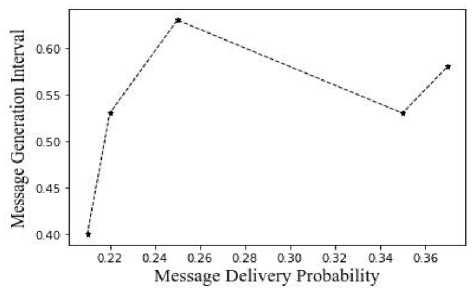
Fig.8. Average message delivery probability vs message generation interval
The illustration of figure 8 demonstrates how the message generating interval affects the message delivery likelihood. The system's performance can be assessed based on how frequently messages are generated. This will enable us to forecast the network's traffic volume and update the incidence matrix.
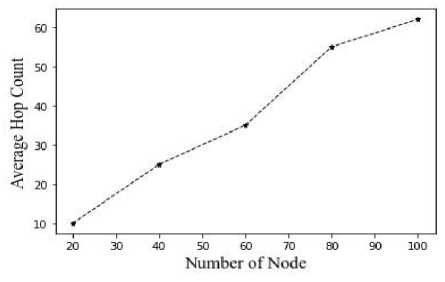
-
Fig.9. Average hop count vs number of nodes
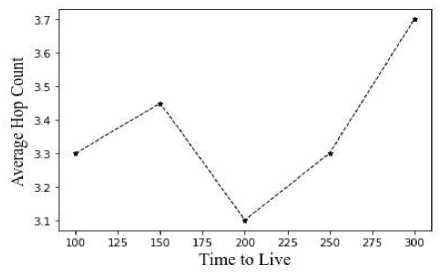
-
Fig.10. Average hop count vs time to live
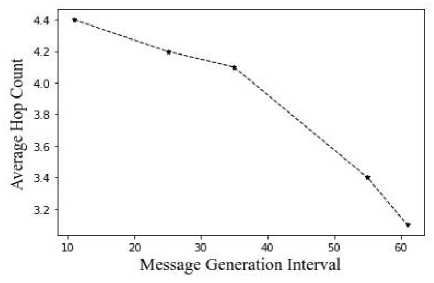
-
Fig.11. Average hop count vs message generation interval
From figures 9, 10, and 11, the average hop count is contrasted with the number of nodes, time to live, and message generation interval. The hop count increases with the number of nodes.
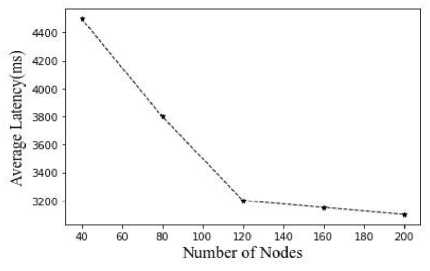
-
Fig.12. Average latency vs number of nodes
-
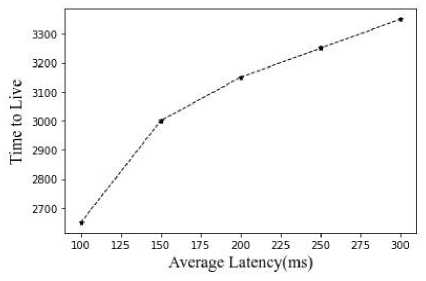
Fig.13. Average latency vs TTL
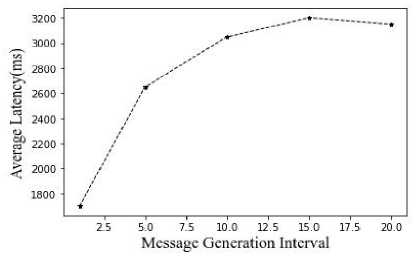
Fig.14. Average latency vs message generation interval
Analysis of the latency of the suggested methodology in relation to node count, Time To Live, and message production interval is shown in Figures 12, 13, and 14 above. With regard to an increase of nodes, latency decreases.
Performance analysis in comparison with the existing methodologies
Proposed Spray and Wait PROPHET Epidemic
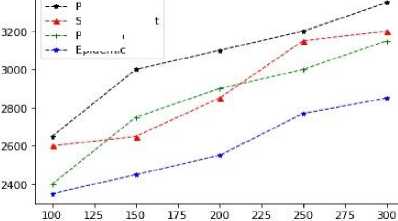
Average Latency(ms)
-
Fig.15. Average latency vs TTL
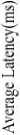
3600 -
3400 -
4400 -
40 60 80 100 120 140 160 180 200
Number of Nodes
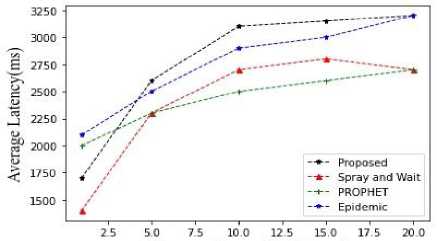
-
Fig.16. Average latency vs number of nodes
Message Generation Interval
Fig.17. Average hop count vs message generation interval
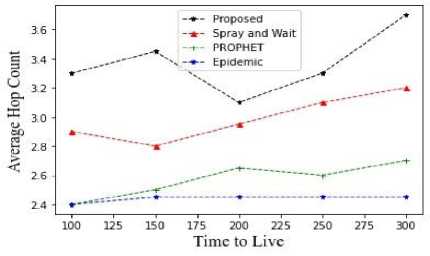
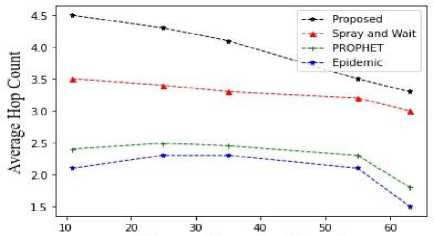
Fig.18. Average hop count vs TTL
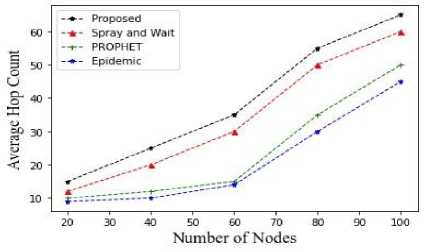
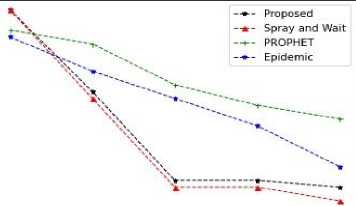
Fig.19. Average hop count vs number of nodes
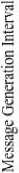
0 60
0 55
0 40
0 30
0.25
Proposed
Spray and Wait PROPHET Epidemic
022 024 026 028 030 032 034 036
Message Delivery Probability
Fig.20. Average message delivery probability vs message generation interval
0 45
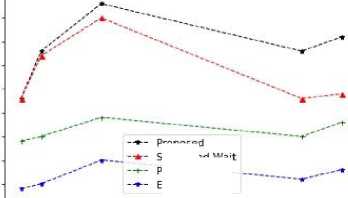
Fig.21. Average message delivery probability vs TTL of messages
Proposed
Spray and Wait PROPHET Epidemic
Proposed Spray and Wait PROPHET Epidemic
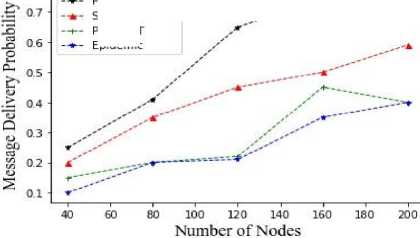
Fig.22. Average message delivery probability vs number of nodes
Message Generation Interval
Fig.23. Average latency vs message generation interval
From the figures 15,16,17,18,19,20,21,22,23 it is clear that the proposed methodology provides a better performance result in comparison with the existing algorithms. The time to live of each message in the network is efficiently high, and the latency is relatively low.
Discussion
An effective network can function even in situations with protracted delays, numerous interruptions, or sporadic connectivity when it is built as a delay-tolerant network (DTN). In contrast to conventional networks, which presume a constant path for data transfer among the source and the destination, DTNs are designed to manage situations in which connectivity is irregular or unpredictable. DTNs are frequently utilized, meanwhile, in situations where data can encounter appreciable delays due to long delay pathways or sporadic connectivity. Time-sensitive applications may be impacted by this. So, Wavelength Routing Technique includes a retransmission acknowledgement protocol hop-by-hop is used in this proposed approach to guarantee the dependability of message transmission. The efficiency of the proposed approach for DTN is analyzed it with some existing approaches. Existing algorithms can provide transmission of messages in DTN, which are not capable of providing reliable communication because of its frequent link failure, node heterogeneity, limited resources and so on. Our proposed mechanism overcomes the above issues and provides the efficient and reliable delivery of messages in DTN.
5. Conclusions
In this paper, the suggested acknowledgement based hop-by-hop retransmission technique to show reliable communication in a delay-tolerant network is proposed. Here, we use the reactive routing table for the best-optimized pathfinding since DTN suffers from the lack of limited resources, continuous link failure and so on. We calculate the blocking probability of each connection request to ensure the reliability of the connection using WRA, which is also useful for the buffer management policy. To ensure the reliable delivery of messages, we implement the concept of hop-by-hop retransmission acknowledgement. During this, the intermediate nodes may have some duplicate messages. To eliminate duplicate messages, we use the efficient Cuckoo search algorithm. Finally, the implementation results show that our proposed mechanism provides efficient and reliable communication in comparison with the existing algorithms. This mechanism is suitable for short communication ranges. In the future, new techniques for integrating DTNs with conventional networks like satellite or cellular systems will be developed in order to improve connection and dependability.


