Requirement elicitation methods for cloud providers in IT industry
Автор: Muhammad Imran Manzoor, Momina Shaheen, Hudaibia Khalid, Aimen Anum, Nisar Hussain, M. Rehan Faheem
Журнал: International Journal of Modern Education and Computer Science @ijmecs
Статья в выпуске: 10 vol.10, 2018 года.
Бесплатный доступ
In cloud computing, requirements engineering is a greatly under-researched topic. Requirement elicitation is a key activity that helps in assemble the requirements of a system from different users, customers and stakeholders. Cloud services providers need methods to correctly elicit requirements from consumers, as the consumers of cloud services are more diverse and there occur some conflictions in the non-functional requirement of some kinds of consumers. Sometimes eliciting security requirements is an important task, because the cloud services are acquired by potential cloud consumers are secure for them to use. Both literature and market surveys are performed on different elicitation approaches that are followed by CSPs to fetch consumer requirements, recommendations and data from cloud service providers and from consumers of cloud computing services. This study aims to discuss the elicitation methods being used by cloud providers in Pakistan IT industry, and the resulting feedback of the consumers by these methods. This would lead to determine current elicitation methods are sufficient or there is a need to design a new elicitation method that can sufficiently provide with more customer satisfaction. We have used semi-structured interviews and questionnaires to gather information about the elicitation techniques that are used by cloud providers to elicit consumer requirements. This study is conducted in Pakistan IT industry. Somehow, this research enlightens the trend and scope of cloud computing in Pakistan. This study would be beneficial for cloud providers adequately gather their consumer requirements and enhance the knowledge of elicitation techniques that are used by cloud providers.
Cloud computing, requirement engineering, requirement elicitation methods, Pakistan IT industry
Короткий адрес: https://sciup.org/15016801
IDR: 15016801 | DOI: 10.5815/ijmecs.2018.10.05
Текст научной статьи Requirement elicitation methods for cloud providers in IT industry
Published Online October 2018 in MECS DOI: 10.5815/ijmecs.2018.10.05
Cloud computing, the trendiest focus of information computing, is still on the wish list of many organizations and one of the most significant current research area [1]. Cloud Computing is a term to keep your data in the remote server rather than to keep in-house. People can get their information from laptop, mobile or from tablet through an internet connection from any location in the world [2,3]. No internet, no cloud computing. It allows workers to work remotely [4]. Amazon Web Services, OneDrive, DropBox are some cloud service provider. People login their cloud drive from pc or mobile, get or upload their data from any location. Customer-centricity, custom-tailored, scalability and malleable pricing are some key features of cloud computing [5]. Cloud providers main task is to ensure quality, data security, privacy and optimization of requirement [6]. These are the characteristics that cloud computing generally has: a) Cloud computing resources are provided to users without requiring human interaction, almost done through a webbased self-service portal, c) Cloud computing allows their consumers to enter and use their data of business at any time with low cost and from any place [7], The cloud adapts to our immediate business needs flexibly.
In contrast to traditional software/hardware components, cloud computing provides asset-free resources to meet customer requirements in terms of space, cost, support, and maintenance[6]. Instead of the advantages of cloud computing, still many organizations are reluctant to adopt cloud computing because this young domain is facing a lot of challenges and uncertainties. Moreover, there is a high cost of switching to cloud.
The US National Institute of Standards and Technology [8] categorized cloud computing service models as, Infrastructure-as-Service (IaaS)[9], Platform-as-Service (PaaS)[10], and Software-as-Service (SaaS)[11] and cloud computing deployment models as private, community, public, hybrid[12].
Table 1 shows the different technologies used in different cloud computing service types. [10].
As the technology advances in the last two decades, it brought ICT for modern progress in technology[13]. This gave birth to Cloud computing and business service providing to the customers. These days the Cloud providers are not only limited to some providers or data centers. Cloud computing and its infrastructures have been evolved now, using decentralized computing[14]. Providing clear, comprehensive, and accurate requirements is a challenging and tough task in the requirements engineering[15,12].
Table I. Technologies used in cloud computing service
|
Service Type |
IaaS |
PaaS |
SaaS |
|
Service category |
Online Storage |
Online Operating Environment, Online Database |
Application Software Rental |
|
Service Security |
Storage Encryption and location |
Data Isolation Operating Environment Isolation |
Data Isolation Operating environment Isolation |
|
Service monitoring |
Physical Resource Monitoring |
Logic resource Monitoring |
Application Monitoring |
|
Service customizatio n |
Server Template |
Logic Resource Template |
Application Template |
Using these elicitation techniques do not fit to gather all requirements of the project and RE cost will also increase and make project fails[16]. Hence, there are many ways of eliciting consumers requirement for a given project [16].
We are concerned in the study to recognize which existing elicitation techniques support cloud services providers. Cloud Providers have need of new methods to elicit requirements correctly from variety cloud consumers. Also, those methods must be suitable and according to their needs. There is need of a method that is fit for both cloud service consumers and provider’s needs for better communication of requirements [17].
-
II. Problem Statement
Requirement elicitation is a vast field which has many approaches and methods of eliciting requirements from the stakeholders. In the context of Cloud Computing, Requirement Elicitation have been a lesser area of focus in the developing countries such as Pakistan. The area of concern is to know how Cloud service providers elicit requirements from the customer in Pakistan. Examine if the prevailing methods are sufficient for cloud providers, or they entail designed techniques, precisely custom-made rendering to their essentials.
In a cloud computing context, examine existing requirements elicitation techniques, regarding their applicability which will help CSPs to choose their suitable elicitation techniques in a particular condition.
-
III. Significance
This research on the identification of the methods which have been used by cloud providers to elicit customer requirements and to look at if the existing methods are sufficient for cloud service providers, or they call for dedicated approaches, particularly according to their needs. This study would be beneficial to companies who have moved to the cloud and using cloud so that cloud providers correctly gather their consumer requirements and enhance the knowledge of elicitation techniques that are used by cloud providers. Furthermore, this study would provide the necessary information on the different existing elicitation methods meet cloud providers needs or not.
-
IV. Research Objectives
This study aims:
-
• To identify elicitation methods are being used by the cloud providers in Pakistan IT industry.
-
• To determine which Requirement Elicitation method provides more satisfaction to the customers.
-
• To determine if the current elicitation methods are sufficient.
This study would be beneficial to companies who have moved to cloud and using cloud so that cloud providers correctly gather their consumer requirements and enhance the knowledge of elicitation techniques, which are being used by cloud providers.
A. Research Questions:
In order to reach these objectives, two questions were used to gather the data:
RQ1- Which of the popular Cloud Service Provider is being followed by other organization in Pakistan?
RQ2- What functionalities are mostly demanded by customers from the cloud providers?
RQ3- What methods used by cloud providers elicit consumer requirements?
RQ4- Do the existing elicitation methods meet the requirements of cloud providers and their customers or not?
-
V. Literature Review
A comprehensive literature review has been done to obtain background knowledge on the topic. The literature review is also beneficial as it discloses some methods that correctly identify the needs of cloud stakeholders. A detailed review of the literature has been done to obtain background knowledge in this research area but the selected readings are included. Following are the selected readings have been carried out to be more focusing towards the topic.
Vijayashree et al, wrote about requirements elicitation techniques helps in eliciting or identifying stakeholder and consumer requirements in developing a software or system [18]. From Literature there is no relevant ETM-Elicitation Topic Map for a specific system. There no Standard approach to elicit requirement of cloud consumers. They developed a framework to elicit consumer requirement for cloud providers. Elicitation Topic Map (ETM) is presented for cloud platform. Issues and challenges reduced using this framework; video recording technique can be used to gather requirement.
Irina Todoran, et al, discussed that cloud services has grown rapidly. Cloud consumer demands new techniques to choose suitable cloud services according to their requirements, while cloud providers need a dedicated approach to elicit requirement correctly from a variety of consumers. They developed the StakeCloud community platform [17]. This platform serves as a cloud resource for the open market, letting consumers enter requirements and deliver them with corresponding cloud services. Thus result will facilitate resource identification at ease and their communication of requirements in cloud systems, hence assist cloud consumers and providers correspondingly. Additionally, examine information retrieval methods from cloud service providers. A very few companies user traditional method to elicit consumer requirement all other rely on Ad-hoc process [16]. A very few current elicitation techniques (surveys, questionnaires, document analysis and prototyping) used by cloud providers to elicit requirement successfully, further investigate new methods and ways of supporting cloud providers.
Kristian Beckers, et al. described in their research paper Cloud computing offer an alternative to traditional IT systems because it provides economic flexible environment [19]. Eliciting security requirements is a complicated task, due to the number of stakeholders and technical components. They propose an organized pattern-based technique supporting eliciting of security requirements and selecting security measures.
Nuno Ferreira, et al. analyze the benefits of cloud systems. When cloud service providers want to elicit requirement from the consumer, if they are not fully satisfied then a process-level perspective is used as an alternative [20]. They developed a real industrial case where the technique was applied and evaluated. In the construction of a legalized architectural model and in the discovery of veiled requirements for the envisioned cloud design is the outcome of the technical application. In contrast, the manual implementation of the method tends to errors and time-consuming.
Xin Zhou, Li Yi, Wei Zhang et al. discussed Software as a Service (SaaS) offers a model to connect many clients with signal application instance through webbased software [11].
The main problem faced with this application development (SaaS) is how to elicit requirements of multiple clients. They present a collaborative requirement elicitation technique (CRETE) that keeps every customer of SaaS application attentive what type of requirements other client raised. To keep on an eye on all the requirements stored in one repository that is helpful to develop a SaaS application.
Boulila, et al, wrote that current requirements elicitation methods have demonstrated that inadequate to record complete, consistent, and precise requirements [23]. Studies conducted have shown that 40% of faults in software development projects are because of incorrectly recorded requirements. In this paper, they report on an experiment involving twenty-five domain experts from various industrial companies to collect requirements using a Storytelling technique. In particular, they argue that Storytelling is a more effective tool than brainstorming for eliciting requirements and including the tacit knowledge as part of the elicitation process. Traditional brainstorming sessions do not lead necessarily to better quality requirements or to discover more requirements than in using Storytelling.
Irina Todoran et al, stated that due to the growing trend of cloud, the figure of cloud service providers is continuously increasing and consumers’ needs are becoming more sophisticated [24]. They claimed consumers need new traditions to find the cloud services which fulfill their needs. They present a StakeCloud platform that works as a cloud marketplace, providing consumers to input their needs and giving them their required cloud services [17].
They examined that elicitation of the requirement is a necessary step in the direction of making effective systems. The theme of requirements elicitation process for the cloud-based systems still reside uncovered. They presented a novel approach to fuzzy Galois lattices for gathering requirements by examining search queries [25]. These lattices can make it easier for cloud providers for the examination on the collection of theories to satisfy large populations with a minimum of implemented requirements, and to indicate new classes of services needed on the market. They plan to release a tool that supports the cloud providers can benefit from the automatic features.
Beckers, et al, examine legal and legislative aspects throughout software designing and development is a perplexing problem, due to the requirement of crossdisciplinary expertise [26]. Because of the large quantity of data and international distribution, and a great amount of stakeholders who process this data. They presented a combined method for requirement elicitation. They planned to develop a tool that supports their approach.
The literature review discussed above provide information about the elicitation techniques that are followed by the cloud service providers to elicit requirements from consumers. As well as they also described the elicitation of security requirements. Many different approaches, framework, and others methods are used for recognizing the consumer requirements. Somehow, some elicitation processes that are used by cloud providers to elicit consumer requirements but these are not meeting their needs.
-
VI. Methodology
This research is qualitative as the opinions of Cloud providers about their method of elicitation requirements and the satisfaction of their customers are to be taken. Some methods that are supported by the literature are taken to identify what are the questions that should be asked by cloud providers. Then in an evaluation phase, the attempt chosen was to collect the answers to those questions. We choose both qualitative and quantitative research approaches.
The research proceeded in two phases.
-
• During the first phase, we sent questionnaires to some employees of different firms of Pakistan to gather information of cloud providers that which elicitation methods they are used to elicit consumer requirement and also examine if the current elicitation methods are sufficient for cloud providers or not.
-
• During the second phase, we conducted in-depth interviews with some employees from different firms of Pakistan. The interview instrument consists of two portions. The first question focuses on the description of the company. The other question on cloud provider’s methods [16] for identifying consumer requirements. This data enabled us to find out what methods are mostly applied by the cloud providers and if those methods satisfying their needs or not.
-
A. Analysis
The analysis is conducted to reach some results on the basis of the data gathered through questionnaires and interviews. These interviews were taken with the intention to answer all the questions of this research. In this section, all the results of the research question are included. So that these can provide a better understanding of Requirement elicitation process used by the Cloud providers in Pakistan.
The first question of this research was about the popularity of platforms among cloud providers. Most of the cloud service provider’s use Google cloud platform to facilitate the cloud consumers,
Figure 1. shows 80% companies provide Google cloud platform, 40% use Microsoft Azure services,23% Amazon Web services. Few companies have their own cloud platform. There are certain reasons behind the popularity of the Google Cloud Platform (GCP) among all other services. One of them is storage Cost GCP is economical than Amazon Web Services (AWS). Google cloud platform have a PAY-PAR-USE concept, which is better than PAY-PAR-SEC concept of Amazon Web services.
Microsoft Azure is better than AWS in terms of security and privacy as it is most trusted cloud for Pakistan Government organizations as similar to the US Government.
The second question of this research was about the functionalities that are required by customers as shown in figure 2.
■ Amazon Web Services ■ Microsoft Azure I Google Cloud Platform ■other
100% -
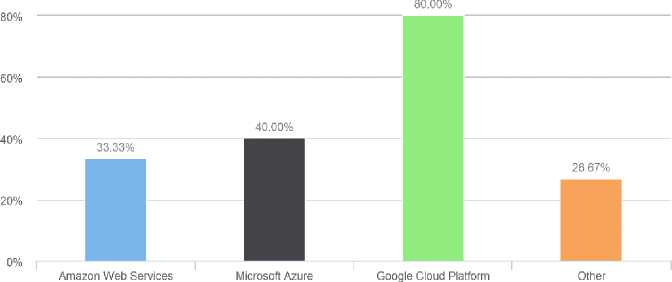
Fig.1. Popularity of platform among cloud providers
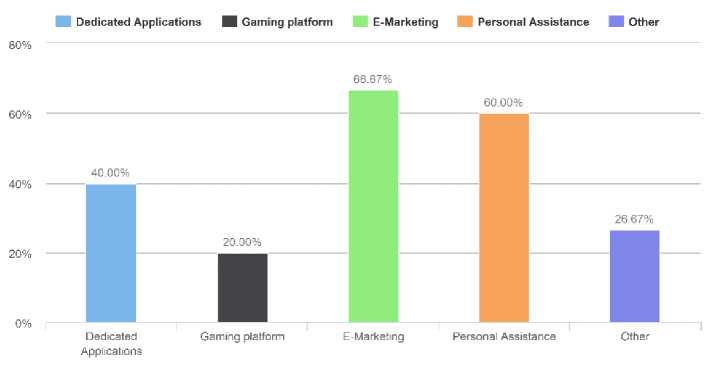
Fig.2. Functionalities required by cloud providers
Internet marketing is growing rapidly, it states the decision of purchasing customer’s product, as studied an increasing number of social media users they can make the final decision before purchasing the final product. Companies that provide dedicated applications, EMarketing, Personal Assistance, and gaming platform are focused on this survey. Internet marketing (e-marketing) facilitates you to develop your own business around the clock without worrying about store opening or payable staff at a little cost. Survey analysis shows that several customers use community platform for E-marketing solutions. Figure 2. shows that about 67% customers are interested in E-marking services. Along with this, the functionality of Personal Assistance ratio is also required by 60% of the market.
The Third question was about what methods used by cloud providers elicit consumer requirements
And which method is widely followed by the cloud providers.
Most of the cloud providers use the traditional requirement elicitation methods, which are getting used software product such as:
-
• Survey/questionnaire, ad-hoc – meeting individuals,
-
• Prototyping – a rough sketch of project requirement,
-
• observation – watch people in natural
environment,
-
• Brainstorming – sit with stakeholders, document analysis – analyze existing related documents, Focus group – together in one room approach,
-
• interface analysis – human interaction with the interface,
And some use other techniques like emailing, storytelling, through Skype or any other social interaction techniques.
Most of the CSP’s use more than one requirement elicitation method according to the nature of the consumer requirements. Not a single method is best in all scenarios, through this study almost all companies checked more than one requirement election methods, they were currently using. Survey analysis shows that most of the companies follow ad-hoc elicitation process, yet the term “trust cloud” is not mature enough, many potential customers have issues regarding the privacy and security in the cloud. In that sense, several companies preferred Ad-hoc Elicitation to elicit consumer requirement.
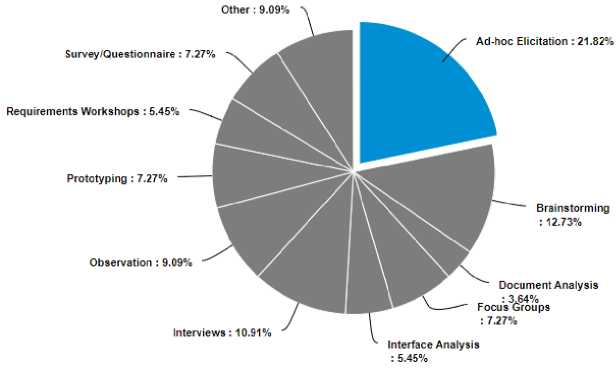
Fig.3. Methods used by cloud providers elicit consumer requirements
The Last finding was about the level of satisfaction of the customers and this is shown in the figure below. Through interview and questionnaires, used in this study, it can be evaluated that if the recipients are happy while choosing the current requirement elicitation process. Through questions we provide a scale ranges from 1 to 5, in correspondence to “highly satisfied” to “highly dissatisfied”, moreover, we provide another scale to compare their companies with other companies. Among all organizations, 40% of the companies are highly dissatisfied, thus, we can evaluate that requirement elicitation techniques are not sufficient and can easily lead to the dissatisfaction of the customers. On the basis of above stated reason, that companies are not satisfied while providing consumers requirements.
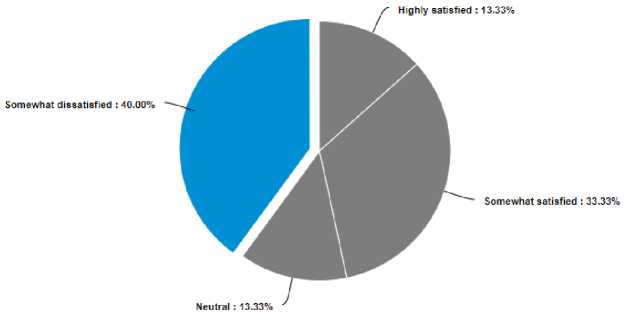
Fig.4. Level of satisfaction
It can be drawn that the requirement elicitation methods are not adequate to provide maximum level of customer satisfaction. And the first three findings can be related with the customer satisfaction as shown in the table below.
-
VII. Results
This research is based on the level of satisfaction of the cloud providers, which shows the existing requirement elicitation approaches provide moderate to low customer’s satisfaction. Only Ad-hoc elicitation process is highly satisfactory. The most The Last finding was about the level of satisfaction of the customers and this is shown in the figure below. Through interview and questionnaires, used in this study, it can be evaluated that if the recipients are happy while choosing the current requirement elicitation process. Through questions we provide a scale ranges from 1 to 5, in correspondence to “highly satisfied” to “highly dissatisfied”, moreover, we provide another scale to compare their companies with other companies. Among all organizations, 40% of the companies are highly dissatisfied, thus, we can evaluate that requirement elicitation techniques are not sufficient and can easily lead to the dissatisfaction of the customers. On the basis of above stated reason, that companies are not satisfied while providing consumers requirements satisfied elicitation process is Ad-hoc elicitation process in CSP’s because of the customer’s trust as it provides more customer satisfaction upon their data integrity.
Brainstorming and Interviews are slightly satisfactory elicitation technique used by CSP’s to elicit consumer requirement. However, those Cloud provider companies which use the interface analysis technique and it is proven to be an unsatisfactory technique for requirement elicitation. With Document analysis, CSP’s cloud
Table II. Key Findings
|
Ad-hoc Elicitation |
Brainstor ming |
Document Analysis |
Focus Group |
Interface Analysis |
Interv iews |
Observ ation |
Prototy pes |
Requirements Workshops |
Survey/ Queatiooaire |
|
|
Highly Satisfied |
v |
|||||||||
|
Somewhat Satisfied |
V |
V |
||||||||
|
Neutral |
V |
V |
V |
V |
||||||
|
Somewhat Dissatisfied |
V |
V |
||||||||
|
Highly Dissatisfied |
V |
companies are highly dissatisfied. We have observed that there is no single process that fit to elicit all of the requirement for all of the software product as according to product nature, requirement changes and requirement elicitation techniques also changes. Some companies also use Focus group process, when the client is mature enough to know about the product, but it happens in Pakistan IT industry that there are only a few clients know about the product requirements. Study conclude that Focus groups, Requirement Workshops, Survey/Questionnaire, observation and prototyping are those techniques which are impartial.
-
VIII. Conclusion and Future Work
This paper mainly focuses on the benefits of requirements elicitation that, which elicitation techniques cloud providers used. Our study includes different companies from Pakistan IT industry. The main contribution is to analyze elicitation techniques which are immensely used by CSPs, their constraints and challenges faced to elicit requirement from the consumer. Moreover, we find out the satisfaction of CSP’s to which extent they are satisfied when they elicit requirements from the cloud consumers. Our effort shows some potential headings for future work and indicates new zones which should be investigated what the elicitation method is fit for requirement elicitation of cloud consumer. In the future, we will develop a new framework for requirement elicitation method to overcome the challenges that cloud providers are currently facing.
Список литературы Requirement elicitation methods for cloud providers in IT industry
- R. Colomo-Palacios, E. Fernandes, M. Sabbagh, and A. de A. Seco, “Human and intellectual capital management in the cloud: Software vendor perspective,” J. Univers. Comput. Sci., vol. 18, no. 11, pp. 1544–1557, 2012.
- V. Inukollu, S. Arsi, and S. Ravuri, “Security Issues Associated With Big Data in Cloud Computing,” Int. J. Netw. Secur. Its Appl., vol. 6, no. 3, pp. 45–56, 2014.
- S. M. Parikh, N. M. Patel, and H. B. Prajapati, “Resource Management in Cloud Computing: Classification and Taxonomy,” 2017.
- M. Sookhak, A. Gani, M. K. Khan, and R. Buyya, “Dynamic remote data auditing for securing big data storage in cloud computing,” Inf. Sci. (Ny)., vol. 380, pp. 101–116, 2017.
- L. Ren, L. Zhang, L. Wang, F. Tao, and X. Chai, “Cloud manufacturing: key characteristics and applications,” Int. J. Comput. Integr. Manuf., vol. 30, no. 6, pp. 501–515, 2017.
- I. Zikra, “Model-based requirements for integrating cloud services,” CEUR Workshop Proc., vol. 1612, pp. 65–72, 2016.
- S. Marston, Z. Li, S. Bandyopadhyay, J. Zhang, and A. Ghalsasi, “Cloud computing - The business perspective,” Decis. Support Syst., vol. 51, no. 1, pp. 176–189, 2011.
- P. Mell, T. Grance, and T. Grance, “The NIST Definition of Cloud Computing Recommendations of the National Institute of Standards and Technology.”
- D. Wentzlaff et al., “An operating system for multicore and clouds,” Proc. 1st ACM Symp. Cloud Comput. - SoCC ’10, p. 3, 2010.
- S. Jones, Z. Irani, U. Sivarajah, and P. E. D. Love, “Risks and rewards of cloud computing in the UK public sector: A reflection on three Organisational case studies,” Inf. Syst. Front., pp. 1–24, 2017.
- S. Applications, “IBM Research Report A Collaborative Requirement Elicitation Technique for SaaS Applications A Collaborative Requirement Elicitation Technique for,” vol. 25081, 2010.
- H. M. Sabi, F. M. E. Uzoka, K. Langmia, F. N. Njeh, and C. K. Tsuma, “A cross-country model of contextual factors impacting cloud computing adoption at universities in sub-Saharan Africa,” Inf. Syst. Front., pp. 1–24, 2017.
- B. T. Bresnahan and P. L. Yin, “Adoption of New Information and Communications Technologies in the Workplace Today,” Innov. Policy Econ., vol. 17, no. 1, pp. 95–124, 2017.
- B. Varghese and R. Buyya, “Next generation cloud computing: New trends and research directions,” Futur. Gener. Comput. Syst., 2017.
- M. Kassab, “The changing landscape of requirements engineering practices over the past decade,” 2015 IEEE Fifth Int. Work. Empir. Requir. Eng., no. January, pp. 1–8, 2015.
- I. Todoran, N. Seyff, and M. Glinz, “How Do Cloud Providers Elicit Consumer Requirements ?,” p. 2014.
- I. Todoran and M. Glinz, “Towards bridging the communication gap between consumers and providers in the cloud,” Proc. WICSA/ECSA 2012 Companion Vol. - WICSA/ECSA ’12, p. 78, 2012.
- J. Vijayashree, P. U. Ivy, and J. Jayashree, “Requirements Elicitation Framework for Cloud Applications,” vol. 3, no. 1, pp. 729–733, 2015.
- K. Beckers, I. Côté, L. Goeke, S. Güler, and M. Heisel, “A Structured Method for Security Requirements Elicitation concerning the Cloud Computing Domain,” Int. J. Secur. Softw. Eng., vol. 5, no. 2, pp. 20–43, 2014.
- N. Ferreira, N. Santos, R. J. Machado, and D. Gaševi, “Derivation of Process-Oriented Logical Architectures : An Elicitation Approach for Cloud Design *,” pp. 44–58, 2012.
- “Cloud Computing Consumer Protocol ACS Cloud Discussion Paper July 2013,” 2013.
- S. Zardari and R. Bahsoon, “Cloud adoption: A goal-oriented requirements engineering approach,” Proc. - Int. Conf. Softw. Eng., pp. 29–35, 2011.
- N. Boulila, A. Hoffmann, and A. Herrmann, “Using Storytelling to Record Require ments: Elements for an Effective Requirements Elicitation Approach,” pp. 9–16, 2011.
- I. T. Koitz and M. Glinz, “StakeCloud Tool: From cloud consumers’ search queries to new service requirements,” 2015 IEEE 23rd Int. Requir. Eng. Conf. RE 2015 - Proc., pp. 286–287, 2015.
- I. Todoran and M. Glinz, “Quest for Requirements: Scrutinizing Advanced Search Queries for Cloud Services with Fuzzy Galois Lattices,” 2014 IEEE World Congr. Serv., no. iii, pp. 234–241, 2014.
- K. Beckers, S. Faßbender, and H. Schmidt, “An integrated method for pattern-based elicitation of legal requirements applied to a cloud computing example,” Proc. - 2012 7th Int. Conf. Availability, Reliab. Secur. ARES 2012, no. August, pp. 463–472, 2012.


