Research on security situation assessment model of video transmission network
Автор: Gao Jian, Yue Ting, Zhu RongChen
Журнал: International Journal of Modern Education and Computer Science @ijmecs
Статья в выпуске: 4 vol.11, 2019 года.
Бесплатный доступ
In this paper, we propose a situation assessment model for video transmission network, which evaluates the security risk of video transmission network information from four aspects: front-end perception layer, transmission layer, application layer and other risks.We divide the video network security evaluation system into three layers, and use AHP to determine the weight of each index.The weights of these four aspects are calculated by analytic hierarchy process.The method proposed in this paper can provide an evaluation system and a calculation method for the safe operation of video transmission network and important systems, and can provide specialized information security services for the construction project of video transmission network.
Video Transmission Network, Analytic Hierarchy Process, Evaluation Model
Короткий адрес: https://sciup.org/15016844
IDR: 15016844 | DOI: 10.5815/ijmecs.2019.04.05
Текст научной статьи Research on security situation assessment model of video transmission network
Published Online April 2019 in MECS DOI: 10.5815/ijmecs.2019.04.05
-
I. Introduction
"China has built the world's largest video surveillance network, with more than 20 million video cameras," CCTV's documentary "Glorious China" reported. But on the other hand, the invasion, hijacking and legal information sales of cameras once constituted an industrial chain, and their impact was not limited to privacy leakage, but is also spreading to criminal cases and even to some areas such as national defense security information, financial trading information, commercial office secrets[1], etc.During the outbreak of blackmail virus in May 2017, more than 120, 000 network cameras around the world were hacked as springboards for virus transmission and attacks[2].On July 26, 2018, the Science, Technology and Information Technology Bureau of the
Ministry of Public Security informed the Ningdu County Public Security Bureau that on July 24, a video private network and a dual network card server in public security network of the Traffic Control Brigade of the Ningdu County Public Security Bureau scanned a large number of servers of the national public security network servers[3].After the initial investigation by Ningdu County Public Security Bureau, it was found that the server was illegally invaded.Someone used hacker technology to invade the computers of public security network and install the Monroe coin mining software[4, 5].
Enea Tsanai[6, 7], propose a cross-layer design that aims to improve the performance of video transmission using TCP Friendly Rate Control .Thomas Kunkelmann[8], give an overview of the security requirements of multimedia conferencing systems and of applicable security functions.For real-time video transmission, it is necessary to selectively encrypt the transmitted data.The existing methods are investigated and their advantages and disadvantages are pointed out.Chuanping Hu[9], focus on the area of public security and build an Intelligent Video and Image Analysis Evaluation Platform for Public Security (IVIAEPPS).They introduces some existing works on building this platform, as well as a video and image challenge based on it.Cha Sungyong[10], proposed a novel security evaluation framework for Military IoT Devices.
In recent years, the Party Central Committee and the State Council have attached great importance to the integration of social video resources, and have successively introduced a series of policy measures: In April 2015, the General Office of the CPC Central
Committee and the General Office of the State Council jointly issued the " Opinions on Strengthening the Construction of Social Security Prevention and Control System ", which is required to improve the technical standards, strengthen the system networking, effectively integrate all kinds of video and image resources at different levels, and gradually expand the application fields[11, 12, 13].In May 2015, the National Development and Reform Commission and the nine ministries and commissions issued a document “Several Opinions on Strengthening the Network Application of
Public Security Video Surveillance Construction”[14, 15].It was suggested that by 2020, the networking rate of video surveillance in key public areas should reach 100%, and the networking rate of video and image resources in key industries and fields involving public areas should reach 100%[16].
The content of this paper is arranged as follows: The second part introduces the overall framework of video transmission network, the third part introduces the security evaluation model and evaluation system, and finally summarizes the paper.
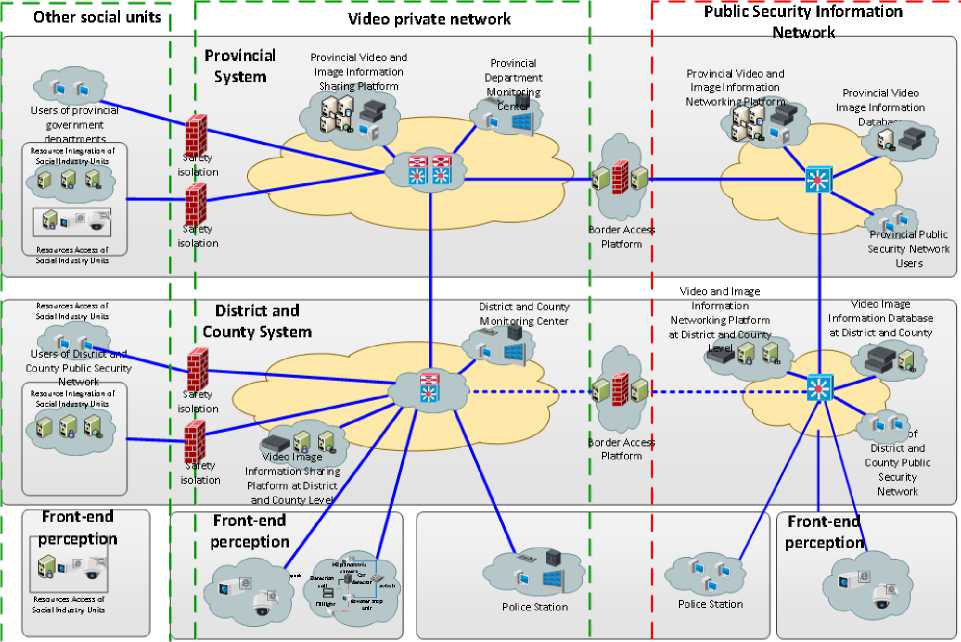
Fig.1. Overall architecture of video transmission network
-
II. Overall Architecture of Video Transmission Network
Problems in the video private network are as follows:
-
1. There is a threat of illegal replacement of cameras.Most of the front-end cameras are outdoors, and they are at risk of being replaced by others. If there is no access control for illegally replaced devices in the network, it is very likely that the lawbreakers can easily enter the video private network through a camera.
-
2. The camera has weak passwords and vulnerabilities.Cameras have a web interface for remote login management.There are many cameras
-
3. The data transmission is not encrypted.Most of the video data and control data transmitted in the video private network are not encrypted, and there is a risk of being sniffed and tampered by the man-in-the-middle.The national standard "Technical Requirements for Information Security of Public Security Video Surveillance Networking" published in 2017 clearly defines the standards and requirements of video encryption.
-
4. There are high-risk vulnerabilities in the application systems.If operating system vulnerabilities, platform vulnerabilities, and system security policies are not fixed or configured, they will pose a risk to the entire network.If an attacker enters the video network, he or she can obtain server
-
5. Other risks include natural disasters (such as earthquakes, fires, etc.) and non-compliance with regulations, such as connecting the intranet computer to the external network through dual network cards or wifi.
permissions through the vulnerabilities to obtain video resources of the entire network.
-
III. Safety Assessment Model
In this paper, AHP (Analytic Hierarchy Process) is used to analyze the information security risk of video transmission network.Based on the hierarchical model of video transmission network, the evaluation index system is established from four aspects: front-end perception layer, transmission layer, application layer and other risks.The perception layer includes illegal replacement, weak password and camera vulnerabilities; the transmission layer includes physical security of transmission lines and data transmission security; the application layer includes server vulnerabilities, platform vulnerabilities and security policies; and other risks include natural disasters and illegal outreach, as shown in the Figure 2.
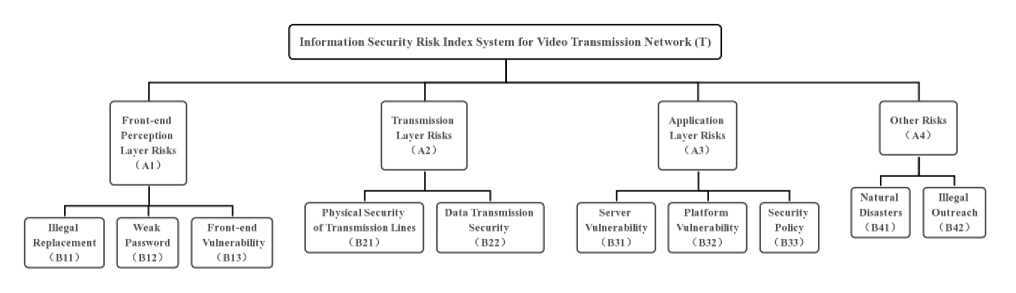
Fig.2. Video transmission network information security risk indicator system (T)
Table 1. Scale Principles of 1-9
|
Scale |
Definition and Explanation of Comparison of Two Elements |
|
1 |
Both have the same importance (or the same strong) |
|
3 |
One element is slightly more important (or slightly stronger) than the other |
|
5 |
One element is more important (or stronger) than the other |
|
7 |
One element is obviously more important (or obviously stronger) than the other |
|
9 |
One element is absolutely more important (or absolutely stronger) than the other |
|
2, 4, 6, 8 |
Scale between the above two standards |
We use analytic hierarchy process to construct discriminant matrix.In the whole index system, the discriminant matrix is constructed by comparing the importance of N indexes in the same layer with those in the upper layer.In this paper, the expert scoring method is used, and the discriminant matrix is obtained by comparing each index in pairs according to the scale principles of 1-9.
Firstly, we used the AHP to analyze the impact of each principle’s various types of risks on the IoT information security system.According to Table 1, the principle layers are compared in pairs, and we can obtain six ratios of A i A1.
A i[ A1,A i /A2,A i /A3,A i! A4 ( i =1,2,3,4 ) , constitutes a discriminant matrix P of 4 rows and 4 columns that judges the importance of four factors.
|
" A1/A1 |
A1 A2 |
A1 A3 |
A1/A4" |
|
|
A2/A1 |
A2 A2 |
A2 A3 |
A2 A4 |
(1) |
|
A3/A1 |
A3 A2 |
A3 A3 |
A3 A4 |
|
|
A4/A1 |
A4 A2 |
A4 A3 |
A4/A4 |
Suppose the vector consisting of sub-factors is:
Q = ( A1 A2 A3 A4 ) T (2)
|
’ A1/A1 A1/A2 A1/A3 A^A4" |
" A1" |
||
|
P * Q = Q |
A2/A1 A2/A2 A2/A3 A2/A4 |
A2 |
(3) |
|
A3/A1 A3/A2 A3/A3 A3/A4 |
A3 |
||
|
A4/A1 A4/A2 A4/A3 A4/A4 |
[A4J |
|
P |
°" = a21 ° 31 _ a 4i " A1/A1 A2/A1 A3/A1 _ A4/A1 |
a 12 a 13 a 22 a 23 a 32 a 33 a 42 a 43 A1 A2 A2 A2 A3 A2 A4 A2 |
a14 a24 a 34 a 44 _ A1 A3 A2 A3 A3 A3 A4 A3 |
AVA4 " A2 A4 A3 A4 A4/A4 _ |
(4) |
|
" A1/A1 |
A1 A2 |
A1 A3 |
AVA4" |
||
|
A2 A1 |
A2 A2 |
A2 A3 |
A2/A4 |
||
|
A3 A1 _ A4/A1 |
A3 A2 A4 A2 |
A3 A3 A4 A3 |
A3/A4 A4/A4 _ |
The element ау ^ 0, (i, j = 1,2,3,4) satisfies the following conditions:
-
(1) ai = i .
-
(2) a.. =--- , the matrix is reciprocal.
a ji
Table 2. Value-added Risks
|
Front-end Perception Layer Risks |
Transmission Layer Risks |
Application Layer Risks |
Other Risks |
|
|
Front-end Perception Layer Risks |
1 |
7 |
3 |
5 |
|
Transmission Layer Risks |
1/7 |
1 |
1/5 |
1/3 |
|
Application Layer Risks |
1/3 |
5 |
1 |
4 |
|
Other Risks |
1/5 |
3 |
1/4 |
1 |
According to the eigenvectors and eigenvalues calculated by the reciprocal matrix, we used Matlab to calculate the weights corresponding to the various types of risks, as shown in the Table 3.
The eigenvector corresponding to the maximum eigenvalue of the judgment matrix is normalized (so that the sum of the elements in the vector is equal to 1) and then written down as W. The elements of W are ranking weights of the relative importance of the same level factor to the upper level factor. This process is called hierarchical single ranking. Confirmation of hierarchical single ranking requires consistency testing, which means determining the allowable range of inconsistencies for A. The unique non-zero eigenvalue of the n-order uniform matrix is n; the maximum eigenvalue of the n-order positive and reciprocal matrix A, if and only then, is a uniform matrix.
Because of the continuous dependence of λ, the greater the ratio of λ to n, the more serious the inconsistency of A. The smaller the CI is, the greater the consistency is. When the eigenvector corresponding to the maximum eigenvalue is used as the weight vector of the influence degree of the comparative factor on the upper factor, the greater the degree of inconsistency, the greater the judgment error. Therefore, the inconsistency of A can be measured by the value of λ-n.
Table 3. Weights of Principal Layer Risks
|
Principa l Layer |
Front-end Perception Layer Risks ( A1 ) |
Transmiss ion Layer Risks ( A2 ) |
Applicatio n Layer Risks ( A3 ) |
Other Risks ( A4 ) |
|
Weights |
0.5565 |
0.0542 |
0.2809 |
0.1085 |
Verifying the consistency of P: C.I=0.0574 C.R=0.0645, we can know that the consistency of the matrix is acceptable.
Similarly, we used AHP to determine the weights of other risk indicators of video transmission network information security.
In the front-end perception layer risks, the weights of illegal replacement, weak password, and front-end vulnerability are as shown in the Table 4
Table 4. Weights of Front-end Perception Layer Risks
|
Front-end Perception Layer Risks |
Illegal Replacement ( B11 ) |
Weak Password ( B12 ) |
Front-end Vulnerability ( B13 ) |
|
Weights |
0.6483 |
0.2297 |
0.1220 |
In the transmission layer risks, the weights of physical security of transmission lines and data transmission security are as shown in the Table 5.
Table 5. Weights of Transmission Layer Risks
|
Transmission Layer Risks |
Physical Security of Transmission Lines ( B21 ) |
Data Transmission Security ( B22 ) |
|
Weights |
0.7500 |
0.2500 |
In application layer risks, the weights of server vulnerability, platform vulnerability, and security policy are as shown in the Table 6.
Among other risks, the weights of natural disasters and illegal outreach are as shown in the Table 7.
Table 7. Weights of Other Risks
|
Other Risks |
Natural Disasters ( B41 ) |
Illegal Outreach ( B42 ) |
|
Weights |
0.7500 |
0.2500 |
Finally, we determined the weight of each indicator in the information security risk indicator system of the video transmission network, as shown in the following Figure 3.
Table 6. Weights of Application Layer Risks
|
Application Layer Risks |
Server Vulnerability ( B31 ) |
Platform Vulnerability ( B32 ) |
Security Policy ( B33 ) |
|
Weights |
0.2583 |
0.6370 |
0.1047 |
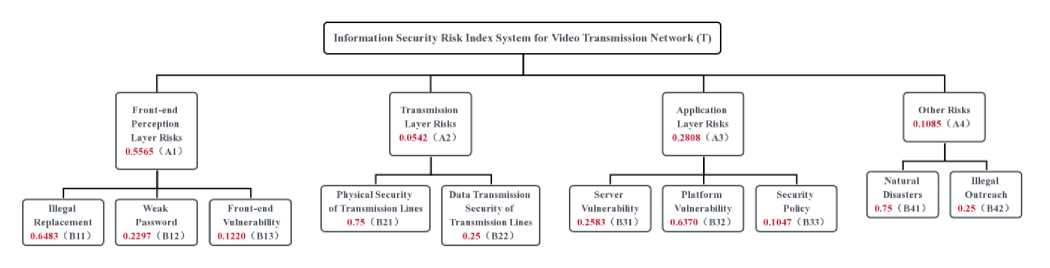
Fig.3. Video transmission network information security risk indicator system (T) and their weights
When assessing the information security risks of video networks, the third-level indicators can be scored by the percentage system, that is, the scores of the overall evaluation are calculated through the indicator system framework proposed in this paper.
-
IV. Conclusions
The method proposed in this paper can provide an evaluation system and calculation method for the safe operation of video transmission network and important systems, provide specialized information security services for the construction project of China’s video transmission network , promote the development of security assessment and risk assessment technologies of China’s video transmission network, and enhance the research and development level of information security technology of China’s video transmission network, and ultimately provide an effective means to achieve video transmission network information security leap-forward development[17].
Well-known network security enterprises and institutions have built a threat information sharing and exchange platform, and related sharing and exchange standards and technologies have accelerated the process of threat information sharing and utilization. However, threat intelligence sharing in dynamic, open and diversified video surveillance network space has the characteristics of massive data, low value information density and ambiguous quality[18] .A large number of deceptive, misleading or confused false information and counter-intelligence make it difficult to find the real correct and valuable information for security analysis and decision-making. In the security defense and early warning emergency system centered on threat intelligence, how to create reliable and fidelity information from shared intelligence and maintain low false alarm rate is very important for network security defense, detection and traceability applications[19].
The model can be further improved on the evaluation criteria and testing methods to improve service capabilities and service processes, which is of great significance for promoting the construction and development of China's video transmission network.
Acknowledgment
This paper is supported by the project (2017 GABJC38) and project(2019 JKF221).
Список литературы Research on security situation assessment model of video transmission network
- Houtgast T, Steeneken H J M .Evaluation of speech transmission channels by using artificial signals[J].Acta Acustica United with Acustica, 1971, 25(25):355-367.
- Wong T, Findlay J, Mcmurtrie A .An On-Line Method for Transmission Ampacity Evaluation [J].IEEE Transactions on Power Apparatus & Systems, 1982, PAS-101(2):309-315.
- Kim H .Evaluation of power system security and development of transmission pricing method[J].Dissertation Abstracts International, Volume: 65-07, Section: B, page: 3606.;Chair: Chanan Singh. 2003.
- Xie L , Yang Z , Zhang C , et al.Security evaluation and auxiliary decision-making method for integrated generation and transmission outage schedule[J].Automation of Electric Power Systems, 2012, 36(15):116-119.
- Gupta R, Goel L .Security constrained well-being evaluation of a sub-transmission system[C]// International Conference on Electrical & Electronics Engineering. IEEE, 2005.
- FarrukhEhtisham, Panaousis E A, Politis C .Performance Evaluation of Secure Video Transmission over WIMAX[J].International Journal of Computer Networks & Communications, 2011, 3(6):28-38.
- Tsanai E , Bouras C , Kioumourtzis G , et al.Evaluation of Video Transmission in Emergency Response Ad Hoc Networks[C]// 4th International Conference on Data Communication Networking - DCNET.IEEE, 2013.
- Kunkelmann T, Reinema R, Steinmetz R , et al.Evaluation of Different Video Encryption Methods for a Secure Multimedia Conferencing Gateway[J].From Multimedia Services to Network Services, 1997, 1356:75-89.
- Hu C, Xue G, Mei L , et al.Building an intelligent video and image analysis evaluation platform for public security[C]// IEEE International Conference on Advanced Video & Signal Based Surveillance.IEEE, 2017.
- Sungyong C, Seungsoo B, Sooyoung K, et al.Security Evaluation Framework for Military IoT Devices[J].Security and Communication Networks, 2018, 2018:1-12.
- Jiarun S , Ziqiang X U, Fuzheng Y .Parametric-planning model combining the transmission characteristics of network video service[J].Journal of Xidian University, 2016.
- Hörsch, Jonas, Hofmann F, Schlachtberger D, et al.PyPSA-Eur: An open optimisation model of the European transmission system[J].Energy Strategy Reviews, 2018, 22:207-215.
- Wang P , Zhang G , Ni C, et al.A Two Time-Scales Network Bandwidth Measurement for Video Transmission[C]// 2016 International Conference on Network and Information Systems for Computers (ICNISC).IEEE, 2016.
- Nagashino H, Kinouchi Y .Oscillatory modes in a neuronal network model with transmission latency[J].Social Science Electronic Publishing, 2018, 52(02):843-848.
- Fu Y, Zhu J, Gao S .CPS Information Security Risk Evaluation System Based on Petri Net[C]// IEEE Second International Conference on Data Science in Cyberspace.IEEE, 2017.
- Rizvi S, Ryoo J, Kissell J, et al.A security evaluation framework for cloud security auditing[J].The Journal of Supercomputing, 2017.
- Lee J H, Kim S J .Analysis and Security Evaluation of Security Threat on Broadcasting Service[J].Wireless Personal Communications, 2017.
- Gulve S P, Khoje S A, Pardeshi P. Implementation of IoT-Based Smart Video Surveillance System[J]. 2017.
- Hasan R, Mohammed S K, Khan A , et al. A color frame reproduction technique for IoT-based video surveillance application[C]// IEEE International Symposium on Circuits & Systems. IEEE, 2017.


