Reviewing Existing Forensic Models to Propose a Cyber Forensic Investigation Process Model for Higher Educational Institutes
Автор: Rabail S. Satti, Fakeeha Jafari
Журнал: International Journal of Computer Network and Information Security(IJCNIS) @ijcnis
Статья в выпуске: 5 vol.7, 2015 года.
Бесплатный доступ
Digital Forensics can be defined as a field of study involving the usage of technical and proved procedures for collecting, preserving, validating, analyzing, interpreting and presenting the Evidences extracted from the digital sources for presenting those in the court of law. Different process models have been proposed by the researchers for cyber crimes' investigation process, each having its own suitability to environments where they are applicable and other pros and cons. The paper includes the tailoring of existing process models to the particular domain of higher education institutes. With the growing access of computing resources and internet to the students, employees and overall citizens, it is the need of time that organizations should establish and maintain their cyber forensics analysis policy along with whole process to be followed in case of any cyber crime scene reporting.
Cyber forensics investigation, Cyber forensics investigation process models, Domain Specific, Comparative analysis, Law compliance
Короткий адрес: https://sciup.org/15011409
IDR: 15011409
Текст научной статьи Reviewing Existing Forensic Models to Propose a Cyber Forensic Investigation Process Model for Higher Educational Institutes
Published Online April 2015 in MECS
Digital forensics investigation is not a new field but still based on new practices and new threats encountered; it is an evolving one. Forensics investigation is the vital phase for Cyber forensic analysis because the analysis totally depends upon the quality, fine granularity, effectiveness, systematic and legal investigation process being carried out by the computer forensics experts. The most critical part in forensic investigations is to dig out and relate the “relevant” information for a forensic case by the investigators. So, for that purpose the investigations should be systematic, expert, customized and sound enough making it a process been done in less time and therefore causing more relevant information to be collected and subsequently being investigated. Among so many forensic investigation processes being proposed, there are few phases which are common to all of them; consisting of some pre-process tasks which may consist of formal permissions and legal issues before starting the actual investigations proceeded by the evidences acquired and preserved from the crime scene. The analysis is performed on the acquired evidences, the results are documented and presented (in courts etc) and finally some post processing is performed in which evidences are again preserved for any future reference and records are maintained.
-
II. Literature Review
Many process models have been proposed for digital investigation procedures and researchers have mainly focused on the nature and number of steps involved in the investigations process of cyber crimes. For the literature review, many proposed digital forensics investigation processes have been reviewed and the main focus would be on discussing the salient features of those models and comparing those features for their implementation in other models.
-
A. Kruse and Heiser Model
The earliest known methodical approach employed to computer forensics. It was based on three fundamental phases. The first phase involves acquiring the data evidence. It is recommended that the data integrity should be ensured. The second step is to check the validity of the collected data by authentication process. The third phase is the analysis of data keeping intact the data integrity and validity. A generalized view of the framework is given in figure below.
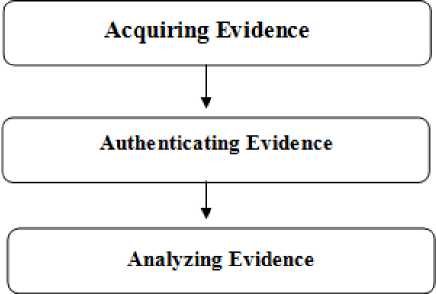
Fig. 1. Kruse and Heiser Model [1]
Advantages and disadvantages
The Kruse and Heiser model is the simplest of above all and hence prone to many limitations and shortcomings. This model puts main emphasis on the integrity of data during investigation. It lacks a key step of investigatory practice though i.e. reporting or presenting the evidence before law.
forensic investigation at that point in time. It outlined the process of digital investigation into seven action classes or steps namely; identification, preservation, collection, examination, analysis, presentation and decision. The framework is represented in the form of a table which includes columns for each activity class whereas each row represents the candidate techniques that could be employed (Table 1). These techniques are variable and could be performed in context of goal to be achieved through that action class [4].
Advantages
It provides a consistent and standardized framework for further enhancement of digital forensic investigatory models.
This model also proposes the mechanism for application of same framework to upcoming digital technologies. The model is generalized to accommodate usage by non-technical observers like judiciary and prosecution. It also identifies a tentative set of tools to be used, taking help from a similar scenario from previous experience.
B. US department of Justice (USDOJ) Model [2]
This model is primarily based on the standard crime scene investigation protocol and comprises of four steps, the collection, examination, analysis and reporting. The collection stage involves looking out for various kinds of evidence and collecting it. The examination stage is related to data mining in order to reveal substantial evidence of meaningful nature. The analysis stage deals with interpreting the data in relation to the questions under investigation to reach a plausible conclusion. The fourth step is reporting or presenting of evidence in the court of law [3]. The simplest schematic workflow is shown in figure 2.

Fig. 2. The US Department of Justice Model
Table 1. Basic matrix of a DFRWS Framework [5]

Preservation
Preservation
Documentation
Event/Crime Detection Resolve Signture Profile Detection Anomalous Detection
Management Imaging Technologies Chain of Custody
Time Synch.
Preservation
Approved
Methods
Approved
Software
Approved
Hardware
Complaints System
Monitoring
Audit Analysis





Sampling
Legal Authority Lossless Compression


Data Reduction
Recovery Techniques
Traceability Validation Techniques Filtering Techniques Pattern Matching Hidden Data Discovery Hidden Data Extraction
Traceability
Statistical
Protocols
Data Mining
Timeline

Expert Testimony
Clarification
Mission Impact Statement
Recommended Countermeasure Statistical Interpretation


Spacial




Advantages and disadvantages
Disadvantages
This model represents an adaptation of Kruse and Weiser model for use in judicial environment. The stages of evidence collection, its examination and analysis are almost parallel with those proposed in the earlier model. However the vital component of reporting of evidence, which was missing in Kruse model, was incorporated in department of Justice Framework. But still this model lacks the depth to address the needs of an ever evolving landscape of cyber forensics investigations.
-
C. Digital Forensic Research Workshops (DFRWS) Model
The first DFRW in 2001 was an initiative of academia that largely served to bring together the wide spectrum of communities involved in digital forensic research; from academics to practitioners, from civilian as well as military institutions. The consensus paper of these proceedings drew the first images of the state of digital
The categories definition could be too general to be practical. It is not easy to be tested through available comparative tools. The number of sub-categories added to the matrix further complicates it.
The DFRWS model appears to be bit rigid, but serves well when different steps of investigative activity are well-known to the investigator.
-
D. Abstract Digital Forensics Model (ADFM) [2]
The researchers at US Air Force proposed an abstract forensic investigation model in 2002. Although it incorporated many of the common processes from existing models but, assumed to be largely inspired by the DFRW framework, rather an extension of it. It adds three more phases to the process resulting in nine stages namely: identification; preparation, approach, strategy, preservation, collection, examination, analysis, presentation, and returning of the evidence (figure 3).
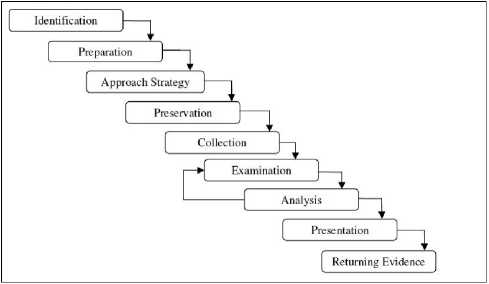
Fig. 3. Abstract Digital Forensic Model [6]
Advantages
The key features of this model are comprehensive pre-and post-investigation procedures in addition to the actual investigatory exercise. These three stages are preparation, approach strategy and returning evidence. The first stage defines the preparation of tools, techniques and securing management support. The approach strategy deals with means to acquire maximum amount of meaningful and genuine evidence and the return evidence stage is introduced for safe storage of evidence for subsequent retrieval.
Disadvantages
Although this model combines the features of most prevalent models of the time yet is not applicable to many real-time situations and serves only to provide a guideline for future digital investigatory model designing.
-
E. Integrated Digital Forensic Investigation Process (IDIP) Model [7]
In 2003, Brian D. Carrier and Eugene H. Spafford integrated the digital investigation to physical forensic investigation process. They introduced a concept of digital crime scene in a virtual environment created with the help of soft and hardware. This model organizes the investigatory process to five groups and 17 phases (figure 4).
and collection of physical evidence. The digital crime scene investigation also follows the same stages but in a digital context. Lastly in review phase the evidence is reconstructed and presented before the court.
The comparison of IDIP with some already existing forensic investigation process models is given in Table 2:
Table 2. Phases in IDIP and the Existing Models
|
PHASES |
|||
|
IDIP |
Incident response model |
DOJ model |
Abstract model |
|
Operation readiness |
Pre incident preparation |
Preparation |
Identificati on |
|
Infrastructure readiness |
Detection of incident |
Collection |
Preparatio n |
|
Detection and notification |
Initial response |
Examination |
Approach strategy |
|
Confirmation and authorization |
Response strategy formulation |
Analysis |
Preservatio n |
|
Preservation (physical1) |
Duplication |
Reporting |
Collection |
|
Survey (physical) |
Investigation |
Examinatio n |
|
|
Documentation (physical) |
Secure investigation |
Analysis |
|
|
Search and collection (physical) |
Network monitoring |
Presentatio n |
|
|
Reconstruction (physical) |
Recovery |
Return evidence |
|
|
Presentation (physical ) |
Reporting |
||
|
Preservation (digital2) |
Follow up |
||
|
Survey (digital ) |
|||
|
Documentation (digital) |
|||
|
Search and collection (digital) |
|||
|
Reconstruction (digital) |
|||
|
Presentation (digital) |
|||
|
Review |
|||
Readiness Phases
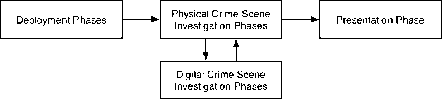
Fig. 4. Graphical Representation of IDIP Model [7]
The readiness phase emphasizes on the inclination of the operational and infrastructural support. The deployment phase provides mechanism to detect and confirm an incident or event. It can be split into detection/notification phase and a confirmation/ authorization phase. The collection of physical evidence is done in physical crime scene investigation under subphases of preservation, survey, documentation, search
Table 3. Comparison of IDIP Model and EIDIP Model
|
Phases in IDIP Model |
Phases in EIDIP Model |
|
Readiness Phase |
x |
|
Deployment phases |
x |
|
Physical crime scene investigation phases |
x |
|
Digital crime scene investigation phases |
x |
|
Trace back phases |
|
|
Dynamite phases |
|
|
Review phase |
x |
Another model termed “Enhanced Integrated Digital Investigation Process Model (EIDIP)” was proposed by Baryamureeba Venansius and Tushabe Florence. The model is the integration of two model i.e. forensic process model and abstract process model. Basically it is the enhanced version of the IDIP. The extra phase that is included in the proposed model is the “trace back” phase which is not present in the previous models. Table 3 shows the comparison of IDIP and EIDIP models:
Advantages
This model outlines principles for digital investigations based on those practiced for physical crime scene investigations. It defines computer and the digital activity as a separate crime scene and not as an object of mere physical evidence. It also points towards methods to be devised for establishing an interaction between the digital and physical investigation. This model contains many of the same ideas as the DFRWS and ADFM models presented in different categories e.g. the DFRWS does not differentiate between preservation and preservation phases. Similarly the boundaries between examination and analysis phases are neither vivid nor the need for event reconstruction has been highlighted.
Disadvantages
This proposed model was though comprehensive, yet too abstract to be applied successfully into two different scenarios (physical and digital). The means of interactions suggested to link both tiers of investigations may not necessarily be applicable to many situations as such. A further enhanced model adds further complexity by introducing a trace back option to each process.
-
F. Systemic Digital Forensic Investigation (SRDIFM) Model [5]
Agarwal and colleagues in 2011 proposed a systemic approach to digital forensic investigation. There are 11 phases in this model named Preparation, securing the scene, survey and recognition, documentation of scene, communication shielding, evidence (both volatile and non-volatile) collection, preservation, examination, analysis, presentation, result and review (Figure 5).
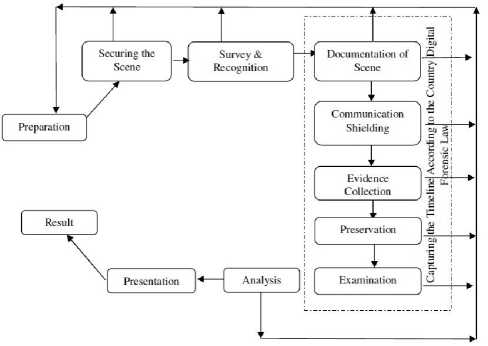
Fig. 5. A Systemic Digital Forensic Investigation Model [5]
Advantages
This model is the most comprehensive in terms of flexibility and practicality. The model is divided into 11
phases with each step looping back to add more flexibility. It incorporates the key practices in investigatory process and simultaneously realizes the properties of reliability and testability during analysis of digital crime. This might serve as a generalized solution to the increasingly complex needs of an ever-evolving digital technology world.
Disadvantages
The incorporation of additional phases adds to the complexity and timeline of investigatory process, which in certain cases is the rate –limiting step in combating cyber crimes.
-
G. Cyber Forensics Field Triage Process Model (CFFTPM)
This model was proposed by Rogers et al. in 2006 to provide an on-site field approach for identification, analysis and interpretation of digital data (evidence) bypassing the immediate need for bringing it back to lab. The model consists of 6 primary phases which can be further divided into 6 sub-classes. The process is claimed to be in compliance with the widely practiced forensic principles. This model emphasizes on the need to collect maximum informative evidence from the site at the earliest possible time, without support of digital forensic lab.
Advantages
The computer forensics field triage process model proposed for the first time an on-site investigation process in the field, which reduces much of time loss and logistics hurdles. Besides it does not preclude the possibility to transfer/transport evidence and system or storage media back to the lab for a thorough investigation. There is also an emphasis on the specificities of the case.
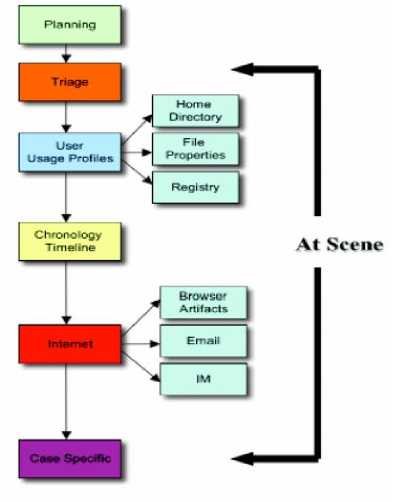
Fig. 6. Cyber Forensics Field Triage Process Model (CFFTPM) [8]
Disadvantages
Despite its utility in the field, this model fails to entertain a diverse array of scenarios and cases. Moreover it resembles more to a computer-based digital forensic model and prone to ignore physical evidence which limits its utility.
-
H. Digital Forensic Model based on Malaysian Investigation Process (DFMMIP) [9]
Sundresan Perumal, in 2009, proposed a digital forensic investigation model which was the digital investigation practices in Malaysia. This model consists of 7 phases named; planning, identification, reconnaissance, transport and storage, analysis, proof and defense and archive storage. One of the salient features of this model is reconnaissance phase which deals with investigation being carried on active devices in order to increase the possibility of acquiring fragile data in a live scenario.
Advantages
This model being implemented by law enforcing agencies in Malaysia, is more apt to the needs of the chain of custody and authorization to handle fragile digital data. Furthermore it emphasizes more on acquisition of both live and static digital data.
Disadvantages
As this framework is designed to augment the capacity of law enforcing agencies to investigate cyber crimes, therefore its target is more towards traditional crime scene investigation than a scientific inquisition. It adds legal documentations like search warrants and reconnaissance.
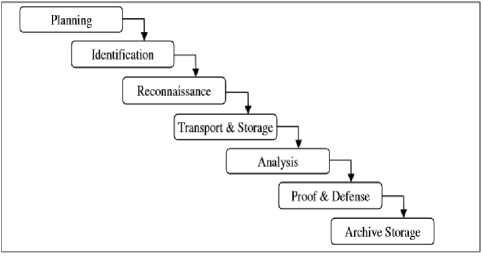
Fig. 7. Digital Forensic Model based on Malaysian Investigation Process [6]
-
I. Generic Computer Investigation Model (GCFIM)
Recently Yunus Yusoff and his colleagues came up with a review of digital investigation models from 1985 till 2011. They examined the pre-existing models for sorting of common phases and then proposed a generic computer investigation model, consisting of 5 generic phases shown in figure 8. Each of these generic phases represent the main phases present in most of the digital investigation models [10].
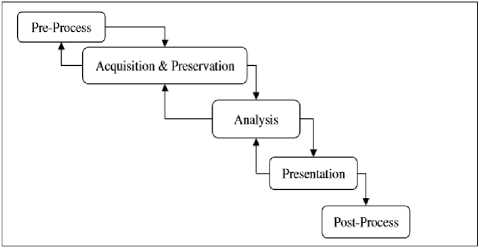
Fig. 8. Generic Computer Forensic Investigation Model (GCFIM) [6]
Advantages
The model emphasizes on the hardcore essentials of a forensic investigation process and provides a basis for investigating a wide variety of cases in the ever-evolving field of information technology. The simplicity of the model offers a flexibility to adapt to different scenarios.
Disadvantages
Owing to its extreme simplicity this model is rated as more of a guideline framework rather than a model as the phases presented in the model are too general to be implemented in a real-life investigation scenario.
The comparison (on the basis of steps involved) of National Institute of Justice (NIJ) model, DOJ model, DRFWS model, IDIP model, EIDIP model, Abstract model and SRDFIM model is given below (Table 4):
Table 4. Comparative Analysis of Digital Forensic Process Models
|
Steps |
NIJ |
DOJ |
DRF WS |
Abstra ct |
IDIP |
EIDI P |
SRDF IM |
|
Collection |
х |
х |
х |
х |
х |
х |
х |
|
Examinati on |
х |
х |
х |
х |
х |
||
|
Analysis |
х |
х |
х |
х |
х |
||
|
Reporting |
х |
х |
х |
||||
|
Preparatio n |
х |
х |
х |
||||
|
Approach Strategy |
х |
||||||
|
Preservati on |
х |
х |
х |
х |
х |
||
|
Presentatio n |
х |
х |
х |
х |
х |
||
|
Identificati on |
х |
х |
х |
||||
|
Return Evidence |
х |
||||||
|
Decision |
х |
||||||
|
Review |
х |
х |
х |
||||
|
Reconstruc tion |
х |
х |
|||||
|
Document ation |
х |
х |
х |
||||
|
Authorizat ion |
х |
х |
х |
||||
|
Survey |
х |
х |
|||||
|
Trace back |
х |
||||||
|
Dynamite |
х |
||||||
|
Communic ation |
х |
||||||
|
Explorator y Testing |
х |
On the basis of steps or phases involved in these process models; SRDFIM model can be considered as extensive model among all the others based on the following reasons:
-
• SRDFIM model provide complete and concrete steps in order to perform digital investigation.
-
• NIJ model and DOJ model have very limited steps; therefore they are not appropriate in order to perform digital investigation thoroughly. The analysis phase of NIJ is improperly define and ambiguous.
-
• Communication shielding is the step which is very important in order to secure the evidence from unauthorized access by blocking all the devices such as WIFI, USB, cables etc after the digital crime has happened. And only SRDFIM model is the only model that is providing that step among all these process models.
-
• Though IDIP model has seventeen and EIDIP model has nineteen steps but there are repetitions of steps in these process models that will make these models extensive and time consuming with respect to the investigation. They both focus on physical as well as digital investigation and physical investigation is not a concern of this research.
-
• In abstract model the third phase (Approach strategy) is the duplication of its second phase (Preparation).
On the basis of advantages and disadvantages some of the characteristics of these process models have also been mapped. The comparison is given in the form of Table 5.
Table 5: Comparative Analysis of Forensic Models w.r.t Different Attributes
|
Attributes |
NIJ |
DOJ |
DRFW S |
Abstra ct |
IDIP |
EIDI P |
SR DF IM |
|
Iterative Model |
x |
x |
|||||
|
Linear Model |
x |
x |
x |
x |
x |
||
|
Explorato ry Testing |
x |
||||||
|
Chain of Custody |
x |
x |
x |
x |
|||
|
Applicable for Law Enforcem ent |
x |
x |
x |
x |
x |
x |
x |
|
Applicable for Corporate Sector |
x |
x |
x |
-
III. Domain Specific Cyber Forensic Investigation Process Model (DSCFIPM)
After reviewing multiple existing models, important phases of cyber investigation process have been identified and some other phases which are specific to the domain, are also been added in the proposed model. Domain
Specific Cyber Forensics Investigation Model has been proposed as a starting step towards establishing a policy and process flow of the forensics investigation in case of cyber crime scene reporting. In the university domain, hundred percent students have access to internet in university labs and on their laptops etc. Also, correspondents from different positions have also confidentially revealed that they have been sent bogus emails, threats, and unethical content through their emails etc. So cyber crimes are present but there is no reporting cell inside the university where they can get help from. So this model is being presented to address the particular domain of university which operates under the judicial, government laws and university charter, so during all phases of cyber investigations, the restrictions and limitations enforced by these laws, regulations and SOPs would be considered.
The proposed model is being shown below in figure 9.
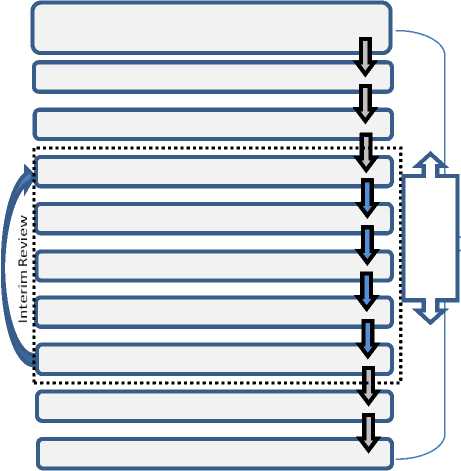
Compliance with govt., judicial laws, university charter and cyber forensic practices
Fig. 9. Domain Specific Cyber Forensics Investigation Process Model
First phase of DSCFIPM is the establishment of Cyber forensics investigations SOPs for university domain. It has been confirmed by university officials that there are no such SOPs in place up till now, so the first and most important step is to formulate a policy regarding the cyber crimes handling at institute level and disseminating that information to the students and employees. Once a cyber crime has been reported, then the strategic level planning is done to handle the situation; and the scope of cyber investigations is determined. University management will take services of expert cyber forensics analysts who will investigate the case in consultation with the university management and relevant officials who will guide them for university SOPs and other legalities applicable in the scenarios. The crime scene will be sealed for avoiding the tampering of evidences present in that area. Then possible evidences will be collected and preserved by Cyber Forensics Investigators (CFIs). Relevant evidences will be extracted and analyzed using their expert judgments and cyber forensics investigations tools like Encase, Autopsy, and Access data FTK etc. The analysis results and findings will be presented to university officials and afterwards in the court of law (if required). The interim review can be done on any phase starting from evidence collection up till presentation of results e.g. if the presented results need more elaboration (if required by university officials) and evidences need more correlation to be specified, then cyber forensics expert can review his work and rework on any intermediate phase as and when required. In the selected domain, it is up to the expertise of CFI, to correlate the digital and non digital evidences; which can reasonably help in investigations process and reaching the exact initiator of the cyber crime. Necessary documentation will be done on every phase of the process. The case history will be maintained for archiving and future reference purposes. Digital evidences can also be preserved again or can be returned to authorize people as and when required. In the post-case review phase, the updates in security policy and cyber forensics investigation policy are being done, as and when required.
The awareness is being given about the changes e.g. if some firewall security policy has been tightened and as a result internet browsing speed slowed down; so people should be given awareness about the need and importance of changes in firewall policy/settings.
During the whole process of cyber forensics investigations, the judicial and government laws should be kept in consideration so that the investigation process can not be objected and its results are admissible to courts (if required). University charter should be known to investigators so that they do not go beyond jurisdictions while investigation process. SOPs should be followed and at least one senior level university official should be designated to facilitate the CFIs understand and comply with university SOPs. Standard processes and practices of Cyber forensic analysis should be followed to avoid any misunderstandings or objections.
-
IV. Comparative Analysis of DSCFIPM with
EXISTING MODELS
Table 6. Digital Forensic Investigation Phases in Different Models
|
Kruse and Heiser |
Department of Justice |
DFRWS |
ADFM |
IDIP |
SRDIFM |
DSCFIPM (Domain Specific Cyber Forensics Investigation Process Model) |
|
2001 |
2001 |
2001 |
2002 |
2003 |
2011 |
2014 |
|
3 phases |
4 phases |
6 phases |
9 phases |
5 phases |
11 phases |
10 phases |
|
Acquiring Evidence |
Collection |
Identification |
Identification |
Readiness |
Preparation |
Establishment of institutional cyber forensics investigations SOPs |
|
Authenticating Evidence |
Examination |
Preservation |
Preparation |
Deployment |
securing scene |
Strategic planning & scope definition |
|
Analyzing Evidence |
Analysis |
Collection |
Approach strategy |
Physical CSI |
Survey and recognition |
Crime Scene Sealing |
|
Reporting |
Examination |
Preservation |
Digital CSI |
documentation of scene |
Evidence Collection (by Investigating Authorities) |
|
|
Analysis |
Collection |
Presentation |
communication shielding |
Evidence Preservation |
||
|
Presentation |
Examination |
Evidence collection |
Extraction of Relevant Evidences |
|||
|
Analysis |
Preservation |
Evidence Analysis |
||||
|
Presentation |
Examination |
Presentation of analysis and findings |
||||
|
Returning Evidence |
Analysis |
Archiving of Case History Records |
||||
|
Presentation |
Post-case review |
|||||
|
Result and review |
The comparison of different forensics investigation models shown in Table 6 depicts that different researchers defined their digital forensic process models consisting of multiple steps. Some just limited the number of steps to a few number while others presented quite elaborative process models, like SRDIFM consisted of 11 phases whereas Kruse and Heiser’s model consisted of only 3 main steps, but detailed insight shows that even in those concise 3 steps, they had to follow almost all phases presented in SRDIFM model. So we can generalize the digital forensics investigation model to must have the evidence acquisition, Evidence analysis and result presentation phases.
The proposed model also consists of major phases used in most of the process models, and a few specific phases tailored according to the domain requirements.
The opted digital forensic investigation process model should suit the nature and requirements of the domain and moreover the particular case undertaken for investigations. The investigating organization or team can also tailor the existing process models according to their desired investigation flow. Or they can even add some new phases if they find those to fit in the flow and are significant for their investigations. That is why, the proposed DSCFIPM is elaborative and best suits the particular investigation flow to be carried out in the university domain. A further comparison of DSCFIPM with selected digital forensic investigation models is given below in Table 3.
The comparisons helped identifying the advantages and shortcomings of each of the above mentioned models. Elaboration has been done in the previous section, so investigators should know the pros and cons of using each of these models. The comparative analysis shown above also showed that number of phases gradually increased as years advanced and more research was undertaken in the field of digital forensics.
So we may predict that in future we can see even more elaborative models for digital investigations which at one side will help the investigators have a predefined elaborative roadmap in their hands before starting their investigations, but on the other side it may add to the complexities with the addition of every new phase. Thus the investigators would have to have better knowledge and command on the details of digital forensics, and subsequently they will have to make people understand the need and purpose of the prolonged investigation process.
The proposed model has been developed using the major phases of existing models and tailoring them to suit the process flow of our selected domain. Its comparison with existing models is given in Table 7.
Table 7. Comparison of DSCFIPM with Selected Digital Forensic Investigation Models
|
DSCFIPM |
Kruse and Heiser |
Deptt. of Justice |
DFRWS |
ADFM |
IDIP |
CFFTP M |
DFMM IP |
GCFIM |
SRDIFM |
|
Establishment of institutional cyber forensics investigation SOPs |
|||||||||
|
Strategic planning & scope definition |
x |
x |
x |
x |
x |
||||
|
Crime Scene Sealing |
x |
x |
x |
||||||
|
Identification of Relevant Evidences |
x |
x |
x |
x |
x |
x |
x |
||
|
Evidence Collection by Investigating Authorities |
x |
x |
x |
x |
x |
x |
x |
x |
x |
|
Evidence Preservation |
x |
x |
x |
x |
x |
x |
|||
|
Extraction of Relevant Evidences |
x |
x |
x |
x |
x |
x |
x |
||
|
Evidence Analysis |
x |
x |
x |
x |
x |
x |
x |
x |
x |
|
Presentation of analysis and findings |
x |
x |
x |
x |
x |
x |
x |
x |
|
|
Archiving of Case History Records |
x |
x |
|||||||
|
Post-case review |
x |
x |
-
V. Conclusion
Complexity of the nature of digital forensic investigation is indicated by the high number of forensic investigation models that have been proposed and the great degree of variability among them. Emphasis has been put on a particular aspect of investigation by the different models or they are confined to address a limited number of scenarios. But over the last decade, a strong foundation to digital forensic research has been provided by the growing census in order to meet the growing challenges by offering sufficient diversity and flexibility with standardization in practices that will enhance the outcome’s reproducibility and reliability.
On the basis of the attributes discussed in Table 5, SRDIFM can be considered valuable and generic model to be used for cyber forensic investigations because:
-
• This is the only model that is providing exploratory testing which means that the researchers have their own methods for testing.
-
• SRDFIM is the iterative model and divided the investigation into four tiers. EIDIP is also an iterative process but it has not divided the investigation into different tiers.
-
• Allocable for both law enforcement as well as the corporate sector where as the models i.e; NIJ, DOJ, DFRWS and abstract models are only applicable for the law enforcement.
The model (DSCFIPM) is also proposed based on major and critical phases being discussed in most of the above mentioned Cyber investigation process models. It can serve the purpose of laying foundation for providing secure and monitored computing environment for university students and employees.
Список литературы Reviewing Existing Forensic Models to Propose a Cyber Forensic Investigation Process Model for Higher Educational Institutes
- W. G. Kruse and J. G. Heiser, "Computer Forensics: Incident Response Essentials" 1st edition, Addison Wesley, 2002.
- M. Reith, C. Carr, G. Gunsch, "An Examination of Digital Forensic Models" IJDE, vol. 1, issue 3, 2002.
- Technical working group electronic crime scene investigation, "A Guide for First Responders", USDOJ, July 2001.
- G. L. Palmer, Technical report DTR-T0010-01 "A Roadmap for Digital Forensic Research," DFRWS, Utica, New York 2001.
- A. Agarwal, M. Gupta, S. Gupta and S.C. Gupta, "Systematic Digital Forensic Investigation Model," IJCSS, vol. 5, issue 1, pp.118-131, 2011.
- B. Yunus, Y, Roslan I & Zainuddin, H, "Common Phases of Computer Forensics Investigation Models", International Journal of Computer Science & Information Technology (IJCSIT), Vol. 3, No 3, June 2011
- M.D. Kohn, M.M. Eloff, J.H.P. Eloff, "Integrated digital forensic process model", Computers & Security, vol. 38, pp. 103-115, October 2013.
- K.Rogers, M., Goldman, J., Mislan, R., Wedge, T., & Debrota, S., "Computer Forensics Field Triage Process Model", Journal of Digital Forensics, Security and Law, Vol. 1 (2), 2006.
- P. Sundresan, "Digital Forensic Model based on Malaysian Investigation Process", International Journal of Computer Science and Network Security, Vol. 9, No. 8, 2009
- V. Baryamureeba, F. Tushabe, "The Enhanced Digital Investigation Process Model", Asian Journal of Information Technology, Volume 5, Issue 7, 2006.
- E. Casey, G. Katz, and J. Lewthwaite, "Honing digital forensic processes", Digital Investigation, 2013, pp.138-147.
- G. Ruibin, C. H. K. Yun, Tony, M. Gaertner, "Case-Relevance Information Investigation: Binding Computer Intelligence to the Current Computer Forensic Framework", IJDE, vol. 4, issue 1, 2005.
- S. R. Selamat, R. Yusof, and S. Sahib, "Mapping Process of Digital Forensic Investigation Framework", IJCSNS, vol. 8, issue 10, pp. 163-169, October 2008.


