Risk Reduction Activities Identification in Software Component Integration for Component Based Software Development (CBSD)
Автор: Fariha Fatima, Saqib Ali, Muhammad Usman Ashraf
Журнал: International Journal of Modern Education and Computer Science (IJMECS) @ijmecs
Статья в выпуске: 4 vol.9, 2017 года.
Бесплатный доступ
In the modern era, the ideas related to software developments are totally replaced the old traditional software development to CBSD. CBSD is the approach that can provide reusability of components to develop new software under minimum chances of risks. Beyond the CBSD features, there are still some significant risks overall the development phase. Generally, the quality of a developed software is depending upon the component integration phase. Nevertheless, component integration phase plays a tremendous role in the success of CBSD that leads to develop new risk free software. The objective of this research was to identify all the risks in CBSD and applied risk reduction activities to mitigate these risks. On the basis of the literature survey, categorized the risks into different categories. For this, an online questionnaire was performed to identify the risks and the risk reduction activities. 85% results point out that CBSD approach is the best approach as compared to the traditional approach. 80% results show that it performs the risk reduction activities, then the quality of the product improves. However, it is a step towards the mitigation of the vulnerabilities and reducing the cost of maintenance.
Integration, CBSD, Risk Reduction Activities, Risk Mitigation
Короткий адрес: https://sciup.org/15014959
IDR: 15014959
Текст научной статьи Risk Reduction Activities Identification in Software Component Integration for Component Based Software Development (CBSD)
Published Online April 2017 in MECS DOI: 10.5815/ijmecs.2017.04.03
Component Based Software Development is an emerging approach that arises to change the software development. CBSD is an emerging and improving approach in software engineering. Once the requirement phase is completed, generally the projects are developed from scratch, which leads towards the increase of time and cost. However, instead of using the concept of building from scratch, software component development and reusability is a better approach. This concept leads towards the quality of a product that is time saving under less budget. [1]
The new system can be developed from the preexisting components that are available in the component repository, but there are many risks and challenges which are facing by CBSD. The organizations that are using CBSD are facing many significant problems due to adopting this technology. In the success of CBSD, component integration plays a vital role. But in order to use existing components, there are many issues related to integration. There are many reasons for this, such as sometimes a component that is generally developed does not full fill the requirements, similarly a component has many features which are not required by the software. For developing a CBSD, there is a need of components with the specific architecture. Each component has its specific name, semantics, interface and the body as well where component name describes the identity, semantics is short description, and interface is an interaction layer for input/output and component body for implementation respectively.
In CBSD, the main working is the integration of components. In CBSD, for developing large, complex software by the already developed components, integration plays an important role to integrate all the components in an efficient way. Therefore, in the CBSD life cycle, component integration plays an important role. These significant problems are sometimes very serious for the small organization to move them towards the failure. These significant problems are arising due to the risk factors involved in the different phases of CBSD. These risks are rising due to five development activities such as component integration, development, component evaluation, and system evolution and system implementation. The risks are categorized into five main categories such as selection, integration, development, implementation and evolution risks [2]
Risk identification is used to determine threat, vulnerability and risk impact on the software project. It is a process which is usually used for gathering information and then determines a specific risk or group of risks related to the project. It is a process that is used to firstly identify all the possible risks that are involved in a process. CBSD was a process which was a mechanism with low risks and is a development of a system.
Mostly risks may not be identified in the first phase, so these risks can be transferred to the next phase. This may cause many problems in CBSD. So for this a proper risk management process can be used to identify and mitigate all the risks that are involved in the phases of CBSD. Risk reduction activity is such an activity that is used now days to less the specific risks or the group of risks. In each and every phase of CBSD, risks is involved. So it is necessary to take proper actions to mitigate these risks involved in each phase. It is an important step to mitigate those risks which can be identified in the phases of CBSD to give software without any error. [3]
The main objective of the paper is to give a prominent solution to overcome the problems regarding to the large size of software. Component Based Software Development is such an approach that can develop a better quality software with lowest price. But CBSD is such an approach that develops a new system from the existing components, but due to the use of existing components, there are many risks arises in the development phase of CBSD. The main purpose of the paper is to develop a software by identification of risks and categorization of risks. The rest of the paper is organized as follows: Section I is the introduction. Section II reviews related literature. In Section III, we define the research methodology. Section IV describes the statistical analysis of the questionnaire. Section V describes the validation using questionnaires. Finally, section VI describes the conclusion of the paper.
-
II. Related work
CBSD develops software quickly by using fewer resources. The systematic literature survey was used for integration testing techniques of CBSD. By this survey, study the behavior of reused components. It also investigates the automation of testing in CBSD. Sometimes the reused components became a big problem so testing was performed to overcome this problem. [4] In CBSD, there are a large number of risks are involved. There are a lot of risks arises in each phase of CBSD because not a proper risk identification strategy is used. Risk identification approach is used to identify the risks at each phase of CBSD and perform the activities to reduce the identified risks. Due to non-proper risk accessing strategy, a number of risks could be found in the phases of CBSD. By the risk identification method, it is easy to find the risks at each phase. In the future there is a need of the mitigation strategy methods.[5] Mahmood [6] stated that it is important to integrate each and every individual component for the success of a CBS. For the information management system, he also proposed an integration testing framework. In it, integration testing was based on complexity metrics. In complexity metrics, try to provide the components without any fault. In it, there are to consider two main key issues which are interaction between components and the testing of components. For prioritizing integration testing, complexity measures can be used. Complexity measures can also be used to select the test criteria. Further this approach will be shifted to large scale applications. Gupta and Raghav [7] explained the risks in COTS based projects and in RUP phase. RUP is best for CBSD. In CBSD risk identification is the main step to identify the risk which is involved in each phase of CBSD and after this; many activities related to it can be performed. In the RUP phases, a survey for risk identification was performed and also it was evaluated by different formulas. In [8] explained that the differences between CBSD and traditional software processes by mentioning different CBSD life cycle models and their phases. It explains that system development is different from component development. It also explained the reusability concept without any changes as many times as required. CBSD has advantages as well as the disadvantages related to it. The disadvantages of CBSE can be reduced by merging of CBSE with traditional software engineering. They explained that reuse concept is different from the traditional approach. In the traditional approach there are no concept of reuse and the risks which are involved in it. In the traditional approach, there is a difference between the system and component development. Mandal and Pal [9] explained that CBSD is a process that uses the concept of reusing of components. During risk analysis, firstly identified the risks, then analyzed these risks and finally documented these risks. Mostly the risks are analyzed at component level. This approach is used by industries for large projects by the reusing of usable components. The reuse concept changes the industry into a new direction with the concept of reducing the cost of developing the software. Component technique is used to develop software quickly in an efficient manner. The concept of software reuse is to make the system that is according to user requirements and is related to the construction phase of software also. There are two aspects related to computer reuse. One is the assembling of components without any change according to user’s requirements. Second is the changing of the developed component. Mainly in it, they describe the advantages, disadvantages and issues related to CBSE [10].
There is a need of identifying, classifying and comparing of risks in development and acquisition. For this purpose they used a systematic mapping study. They surveyed, these risks in Indonesian background. On the basis of this study, they classified risks into 17 types. Mostly in both risks are same and similar. This study provides a framework in which past risks which could not be avoided would also study in this study. This study has not a use of hypothesis. They also performed an online questionnaire survey of the risk occurrence. This mapping study identifies the risks a give a checklist of the risks. There are 11 risks which are related to the
COTS study [11]. COTS integration [12] is a process which plays a vital role. During integration, it is necessary to respond to the mismatches which can be occurred during combining these pieces together. CBSD concept is not related to scratch; it is mainly related to developing the new components by reusing the existing components in a manageable way. In the component integration, integrate all the components of the reuse concept and check it’s in the environment. During integration, the main problem is the combination of different components from different developers. In [13] [14] risk management plays an important role in software projects and project management. Some studies are related to this issue. There is positive as well as negative view about the risk management. In search and practice point of view, the development of risk is a very slow process. There is need of study between risks, risks, strategies and project performance. By the past research it is reviewed that there is a close relationship between risk management in the project success. He can explain the six risk management activities. There is knowledge about risk management activities, but not proper practices of it. There is not knowledge about risk mitigation activities that are also cost and time effective. Culture also plays an important role in the direction of identifying the risks and the risk reduction strategies. In its first of the three relate to the present practices related to risk management while for the out coming approaches last three are proposed. In the multi projects companies, there are a use of multiple practices and their comparison to change into a single approach. Mahmood [15] performed an empirical study of CBS integration process activities. These process activities are related to the success of CBS. The key integration process activities of CBS are component functional specification, structural compatibility analysis, architectural model development and early glue code specification. For the development of CBS this study describes the importance of the integration process activities. Pande [16] stated that CBSD approach is attracting the software companies towards its benefits. It also increases the quality. The best challenge is to select the components on the basis of the functions that it provides. Sometimes, during the selection of components, there is a situation that increases the cost of the components. So there are some guidelines to know about the best components. The main objective of CBSD is the reduced development cost and time to provide a best fitted components.
CBSE is that approach which is attracted by all researchers in the field of software engineering. It is described in a systematic mapping study to explain the working related to CBSE in the period 1984-2012. The main contribution of CBSE that was found in this time period is related to cost, time and productivity. In it, different models, techniques were explained to show the gaps which were occurring due to CBSE. In it, there are three types of research questions are discussed which are related to research topics, types of research, and types of contributions which are involved in it. This research is basically introducing the gaps between the researchers and discuss about those areas where an investigation is required. It deeply explains all the activities related to CBSE with mentioning each and very thing related to it [17]
The literature survey describes that CBSD is a new technique in the era and is a better approach than the traditional approach. The risk management strategy is a process that is describing the risks and the risk reduction strategies that are involved in CBSD for the identification of risks. Classification of risks is based on that stage where a new risk can be identified. Risk can be serious and difficult to mitigate when it occurs in later stages. CBSD is a new technique in the modern era of IT that is mainly based on the reusing concepts of components.
-
III. Research Methodology
Firstly, it is necessary to identify all the risks which are involved in the phases of CBSD. There are many chances of getting risks due to components from different vendors. Then the risks are classified into three main areas such as Operational Requirements (due to the functionality and performance of the system), Technical Approach (related to technical characteristics) and business strategies (due to involvement of vendors).
The data can be evaluated by using survey strategies that is carried out from the software houses. The study was conducted in following phases:
-
1. Questionnaire Design
-
2. Data Gathering
-
3. Data Analysis and Results
The research is done by sending an online questionnaire to the different software houses. The questionnaire is designed on the literature on CBSD and the risks involved in the different phases of CBSD. The main tool of the research is the questionnaire that has involved 24 questions about the risk and risk reduction strategies in CBSD. The main objective of the
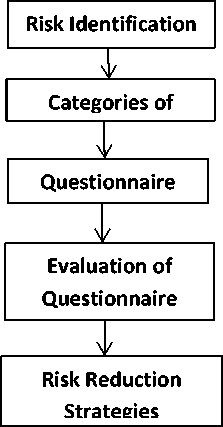
Fig.1. Research Methodology questionnaire to know about the risks and risk reduction activities in CBSD. The respondents to the questionnaires are the managers, software engineers and risk managers.
An online questionnaire is sent to different software houses. The data are gathered by different responses from the software houses. Then the data are coded and is entered in SPSS 17 for analysis. Percentage method is used to analyze the gathered data. [ ]
When the risks are identified, then different risk reduction strategies are used to minimize the risks at each and every phase of CBSD. By different risk reduction strategies, minimize all the risks.
-
IV. Statistical Analysis of Questionnaires
The gathered data related to the questionnaire are collected by sending the questionnaire to the different companies by online. The questionnaire had been sent to 150 companies. There had an aggregate of 101 respondents who filled the structures and sent back. The results are analyzed by using SPSS tool and the results are represented by frequency tables and bar charts that are the best representation of the best analysis of the data.
-
V. Validation USING Questionnaire
We are describing the validation of results on the basis of our results that are shown by the frequency table (Appenix II) and graphs.
Employee Size
"о
Than 50
than 200
Fig.2. Employee Size
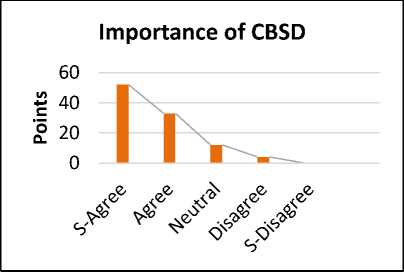
Fig.3. Importance of CBSD in Organization
The reply shows that 52% are strongly agreed, 33% are agreed. Whereas 12% are neutral for the proposed solution. While 4 % are disagreeing. The survey results indicate that CBSD is such an approach that is playing an important role in the organization nowadays. CBSD is the concept that is on the rise because it can reduce cost and time and develop a new software within a short time. The quality of a system is mostly related to the quality of the components that are involved. But some companies have some confusion related to CBSD approach [18]
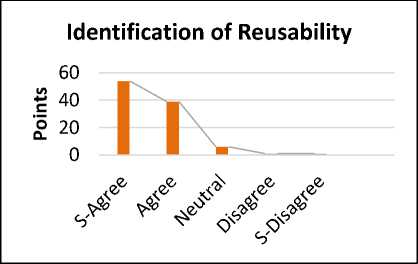
Fig.4. Identification of Reusability by CBSD
The reply shows that 54% are strongly agreed, 39% are agreed. Whereas 6% are neutral for the proposed solution. While 1 % are strongly disagreed and 1% is also disagreed. CBSD is promoting the use of specialists that are dealing with the reusable components on the basis of the knowledge. Reusability is the most important factor in the success of components. CBSD has a repository that has reusable and tested components. Due to the reusing components, CBSD plays an important role in the software industry now-a-days.
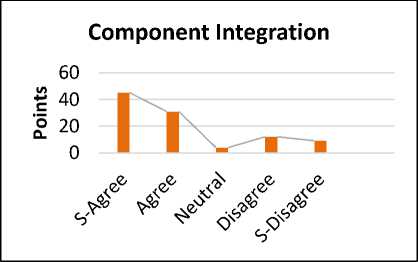
Fig.5. Component Integration without Error
The reply shows that 45% are strongly agreed, 31% are agreed. Whereas 4% are neutral for the proposed solution. While 12 % are disagreeing and 9 % are strongly disagreed. The survey results describe that it is not too much easier to integrate the components. Because during component integration, when parts of the components are combined together, then sometimes there is a mismatch between the parts. So the error occurs. So it is necessary to integrate the components without error.
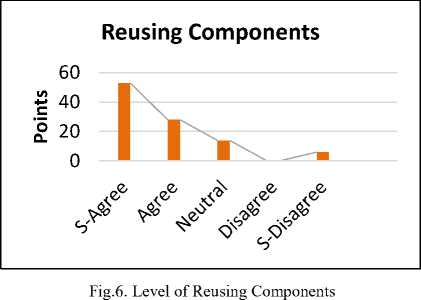
The reply shows that 53% are strongly agreed, 28% are agreed. Whereas 14% are neutral for the proposed solution. While 6 % are strongly disagree. The survey results revealed that CBSD approach is preferable as compared to the traditional approaches. Mostly the companies are moving towards CBSD approaches due to the reusing concept. CBSD is an approach that makes it possible to identify and define the reusable components. The survey results pointed out that the reuse level in the different organizations is high.
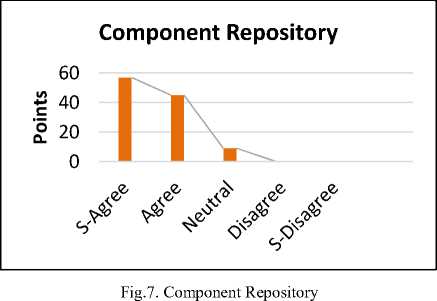
The reply shows that 57% are strongly agreed, 45% are agreed. Whereas 9% are neutral for the proposed solution. CBSD has a component repository that has reusable and tested components. Due to the reusing components, CBSD plays an important role in the software industry now-a-days. The survey shows that for developing a new software, there is necessary to have a component repository to develop an error free new software. Based on the survey results, the component repository is used to store the existing and new components in it. So the results revealed that if the component repository is available, then it is easy to store the information about the components.
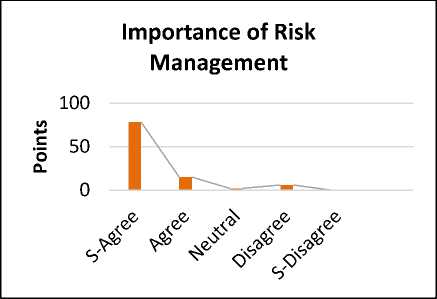
Fig.8. Importance of Risk Management in Success of Organization
The reply shows that 78% are strongly agreed, 15% are agreed. Whereas 2% are neutral for the proposed solution. While 6 % are disagree. Based on the results, risk management strategy is used to identify the risks and the mitigation strategies to mitigate these risks. Some risks are avoidable while some are non-avoidable. For avoiding the risks which are changing into mature problems, applying the risk reduction activities. When the risks can be changed into mature problem, then contingency plans can be taken place. A mitigation strategy is a better approach as compared to the contingency plans because it is an easier and cheaper way to recover these risks. That’s why mostly the organization gives the importance to the risk management. Mostly the companies have the risk management process. [19]
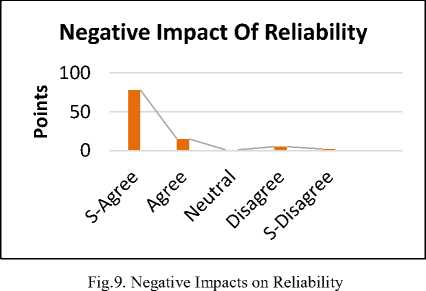
The reply shows that 78% are strongly agreed, 15% are agreed. Whereas 1% are neutral for the proposed solution. While 5 % are strongly disagree and 2% are disagreed. On the basis of component integration, there is a negative impact on the reliability. Because if the components are not according to the user’s requirements, then it affects the reliability. Reliability is such a factor that is used to improve the quality of a product according to the users requirements.
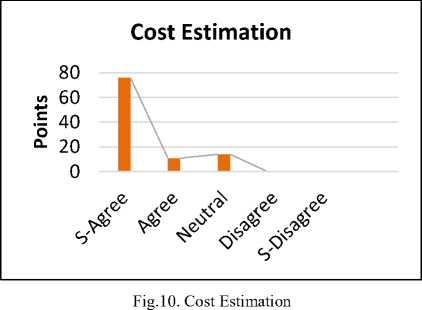
The reply shows that 76% are strongly agreed, 11% are agreed. Whereas 14% are neutral for the proposed solution. The survey results demonstrated that if the information about the component is not available them the cost estimation schedule is high. So it is necessary to get the reliable information from the users to provide error free components with low cost. This new component is according to the user requirements.
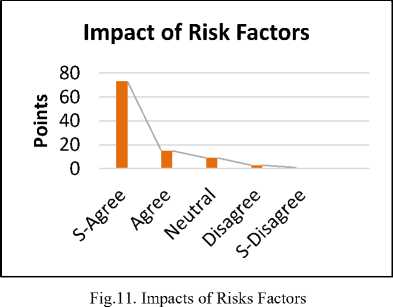
The reply shows that 73% are strongly agreed, 15% are agreed. Whereas 9% are neutral for the proposed solution. While 3 % are strongly disagreeing and 1 % is disagreed. The survey results demonstrated that in CBSD many risks are involved which are affecting the standards of Software development. There are many risks in the different phases of CBSD that is affecting the standards of reused components.
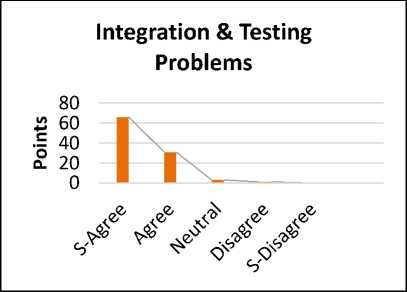
Fig.12. Integration and Testing Problems
The reply shows that 66% are strongly agreed, 31% are agreed. Where as 3% are neutral for the proposed solution. While 1 % are disagree. Based on the results, there is a main focus on the integration and testing problems. So in CBSD, it is necessary to integrate the components and avoid the testing problems. Integrate the components is a basic focusing point to resolve the problems related to a newly components.
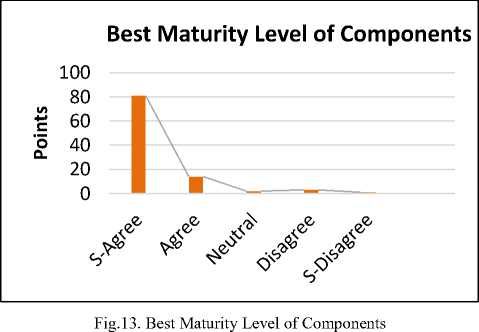
The reply shows that 81% are strongly agreed, 14% are agreed. Whereas 2% are neutral for the proposed solution. While 3 % are strongly disagree and 1% are disagreed. The survey results point out that the main focus is on the selection of components on the basis of market level. For avoiding the chances of risks, those components are selected which has best maturity levels in the market and those are according to the user requirements. So it can be easy to get a new components according to the new standards.
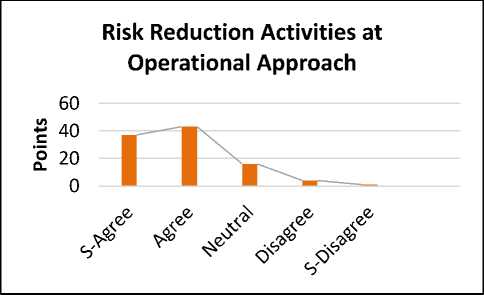
Fig.14. Risk Reduction Activities at Operational Approach
The reply shows that 37% are strongly agreed, 43% are agreed. Whereas 16% are neutral for the proposed solution. While 4 % are strongly disagree and 1% are disagreed. Based on the survey results, it is demonstrated that there is a need of user’s communication for the evaluation of requirements at the operational approach to perform its functionality in a better manner.
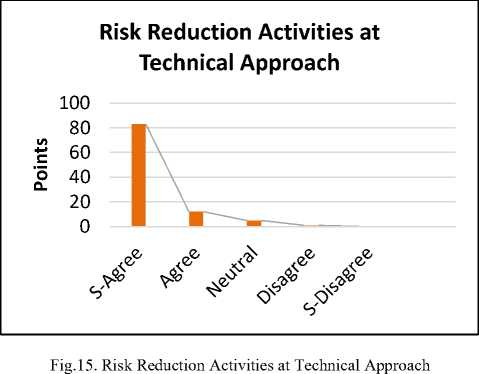
The reply shows that 83% are strongly agreed, 12% are agreed. Whereas 5% are neutral for the proposed solution. While 1 % are disagree. The survey results revealed that before the final selection of a component, it is necessary to perform prototyping. So the standard component is selected.
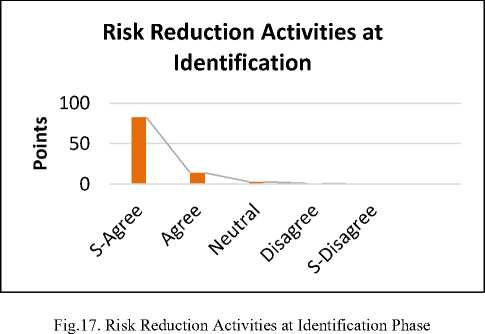
The reply shows that 86% are strongly agreed, 12% are agreed. Whereas 2% are neutral for the proposed solution. While 1 % are disagree. On the basis of results, the risks at the identification phase should be mitigated if a fresh component is used in developing a new software and a proper documentation is required and in this phase component repository is the main factor to provide the suitable components.
Risk Reduction Activities at Integration Phase
о
Fig.18. Risk Reduction Activities at Integration Phase
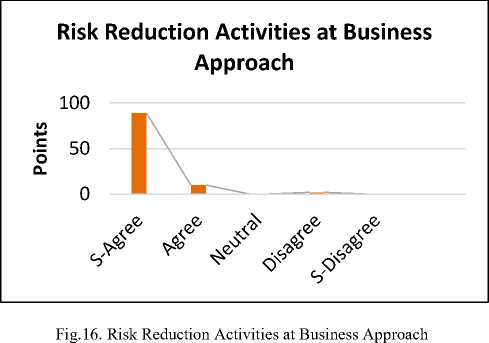
The reply shows that 89% are strongly agreed, 10% are agreed. While 2 % are disagree. The survey results point out that if better time is selected, then risks at the business approach can easily be mitigated. Because if the statement is not according to the user requirements than many risks can be involved in this approach. So it is necessary to the use of the frequent prototyping according to market standards.
The reply shows that 83% are strongly agreed, 8% are agreed. Whereas 5% are neutral for the proposed solution. While 2% are disagreed and 3 % are strongly disagreed. The survey shows that if the component is selected on the basis of user’s requirements, then it is easy to integrate the components and develop a new components with consistency and according to user specifications
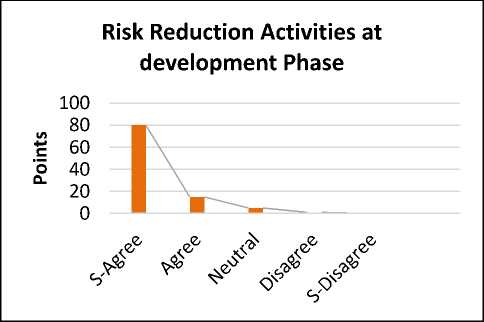
Fig.19. Risk Reduction Activities at Development Phase
The reply shows that 80% are strongly agreed, 15% are agreed. Whereas 5% are neutral for the proposed solution. While 1 % are disagree. The survey points out that if proper resource management is used that provides the resources on time and proper resource management for the availability of resources during the development of software, then it is easy to mitigate the risks at the development phase.
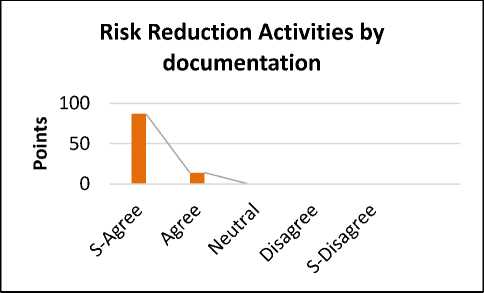
Fig.20. Risk Reduction Activities by Documentation
The reply shows that 87% are strongly agreed, 14% are agreed. On the basis of survey results, documentation for the development of new software by CBSD approach is a very main point to mitigate all the risks that are occurring during the development phase. Documentation is the written agreement between the clients and vendors.
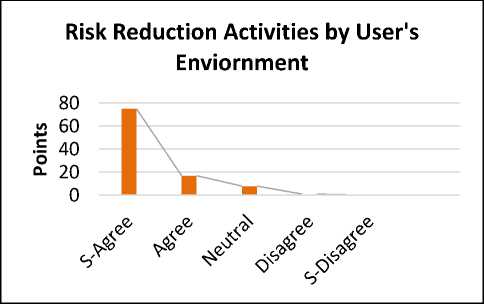
Fig.21. Risk Reduction Activities by User’s Environment
The reply shows that 75% are strongly agreed, 17% are agreed. Whereas 8% are neutral for the proposed solution. While 1 % are disagree. The survey results show that the environment also plays an important role because if the environment is not according to the requirements then it is difficult to operate it.
Risk Reduction Activities by Modification of Components
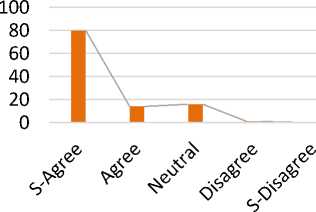
Fig.22. Graphical Representation of Risk Reduction by Modification of Components
The reply shows that 80% are strongly agreed, 14% are agreed. Whereas 6% are neutral for the proposed solution. While 1 % are strongly disagree. Based on the survey results, if the component is not according to the requirements then it are easily modified by the availability of proper resources. Mostly survey results show that modification of components plays an important role in the development of software that fulfills the users requirements.
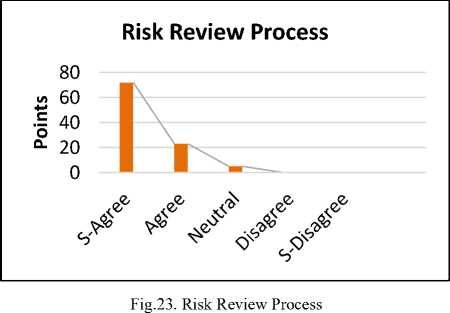
The reply shows that 73% are strongly agreed, 23% are agreed. Whereas 5% are neutral for the proposed solution. When the risk reduction activities can be identified, then it is necessary to have a risk review process to implement the mitigation measures to reduce the risks that are involved in CBSD. So by the survey, it is revealed that many companies have a risk review process. So they can easily manage and identify the risks and mitigate these risks by applying different risk reduction activities.
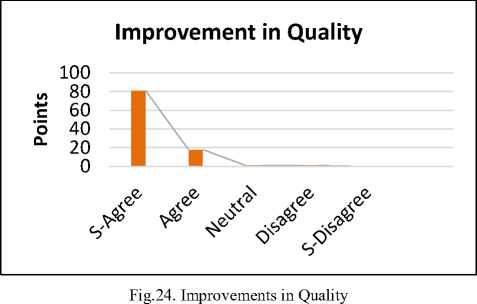
The reply shows that 81% are strongly agreed, 18% are agreed. Whereas 1% are neutral for the proposed solution. While 1 % disagree. The survey results confirmed that by applying the risk reduction activities on the identified risks, the quality of a component is improving daily. So it is a step towards the mitigation of the vulnerabilities and reducing the cost of maintenance. The software product is a quality product if it is according to the user’s requirements and it has minimum risks which can be easily to identify and mitigate.
Table 2. Risk Reduction Strategies
|
Approach |
Risk ID |
Parameter |
Risk Reduction Activity |
|
Operational |
RO1 |
Non Availability of COTS Product |
Conduction of market research per standards of the market and meets the user’s requirements. |
|
RO2 |
Functionality and Performance Risks |
Evaluate the product by prototyping and compare the same requirements with the other users to know about their experiences |
|
|
RO3 |
Requirement Gap |
Requirement of the operational documents to know about the user’s requirements |
|
|
Technical |
RT1 |
Non acceptance of COTs products |
Identification of a product that can meet the standards and the requirements |
|
RT2 |
No Experience Technical Operator |
Specification of contractor criteria on the basis of selection, integration and testing of the products |
|
|
RT3 |
Poor quality Requirements |
Prototyping before final selection and use the market trends for the selection of a component |
|
|
RT4 |
Portability Risks |
Selection of components that can easily be adjusted on any platform without any error or complication |
|
|
RT5 |
Evolution Risks |
Coordination of hardware and software platforms with the selected components |
|
|
RT6 |
No access to source Code |
Use the alternative ways to find the faults in the products due to poor integration and testing |
|
|
Business |
RB1 |
Acquisition Alternative Risks |
On the basis of requirements and utilization, choose such licensing terms that are according to the requirements |
|
RB2 |
Vendor Reliability Risks |
Know about the history of vendors such as financial status, behavior with the products |
|
|
RB3 |
Business Skills |
Establishment of contractor’s relationship with the vendors and licensing party |
|
|
RB4 |
Statement of Work not according to COTs Products |
Maintenance of integration lab, use of early and frequent prototyping and updating about the market standards. |
|
|
Identificatio n Phase |
RId1 |
Unclear Requirements |
Proper documentation of requirements according to the user’s requirements and the requirements should be feasible. |
|
RId2 |
Shortage of Resources |
Component Repository is used to identify the components and gives importance to the latest techniques |
|
|
Selection Phase |
RS1 |
Incomplete System’s Requirements |
Elicit, analyze and record the requirements by proper requirements analysis to know about the user’s requirements |
|
RS2 |
Poor Description of requirements according to architecture |
For the selection of components COTS Aware Requirements Engineering and Software Architecture (CARE/SA) framework should be used |
|
|
RS3 |
Lack of methods for the selection of components |
PORE (Procurement Oriented Requirement Engineering) method should be followed for the selection of components according to user’s requirements |
|
|
Integration Phase |
RInt1 |
Lack of Interpretability Standards |
Use of open standard technologies for providing consistency among the components. |
|
RInt2 |
Format Variation |
For the automation of components, component wrappers can be used for the treatment of component composition |
|
|
RInt3 |
Glue Code |
Exact matching of components according to user’s requirements to minimize the glue code in the integration phase |
|
|
Developmen t Phase |
RD1 |
Unsuitable process for CBSD |
For the reduction of critical risks, use the process models to identify and reduce the risks |
|
RD2 |
Lack of resources |
There is a need of proper resource management for the availability of resources |
|
|
Implementat ion Phase |
RIMP1 |
Reduction of quality of testing due to unclear design assumptions |
Four testing methods such as Integrated system, nonfunctional testing, prior to deployment, regression testing, |
|
RIMP2 |
Security Risks |
Documentation and certification for the reliable components is required |
|
|
RIMP3 |
Vulnerability Risks |
The security policy should be used for the procurement of products |
|
|
Evolution Phase |
RE1 |
System Updating Risks |
Changes in components are occurring so for this a proper updated management should be required to manage these changes |
|
RE2 |
Replacement Risks |
Impact analysis should be performed for the replacement of products |
|
|
RE3 |
Modification Risks |
For the modification of components, configuration management should be performed |
|
|
RE4 |
Technical Risks |
Analyze the costs related to each component when it can be needed. |
-
VI. Conclusion
In the modern era of information technology, the old traditional approach is replacing by CBSD due to reusing concept. In order to develop new software’s, CBSD approach is one of the best being used due to reusable components. The main quality of any developed software is depending upon the component integration phase. In the development of any software, risk identification is playing a vital role. Risk identification is a process that is used to identify the risks. CBSD is such an approach that is increasing the productivity of the organizations. For the success of CBS, component integration is playing a vital role. During the integration phase, there are many challenges and issues which are facing by the developer due to the use of preexisting components. Risk Identification is a process that is used to identify all the possible risks in all the phases of CBSD. Firstly, identify and locate the risks which are involved in the phases of CBSD. Then indicates those risks which are more critical and other all risks which are not important are avoided. Risk reduction activity is such an activity that is used to mitigate all the risks in the phases of CBSD. In it, categorize the risks, and then mitigate those risks by applying different risk reduction activities. The risk identification and risk reduction activities are used to develop a software by reusable components in the early stages with a little bit complications. The main tool that is involved during the research is an online questionnaire survey that is consisting of 25 questions that are related to risk identification and risk reduction activities in an organization. By the online questionnaire, it is proved that CBSD is playing a vast role nowadays as compared to the traditional approach. 90% results show that if the risks are properly identified and mitigated, then the quality of the product is improving day by day. By applying the risk reduction activities in the phases of CBSD, the quality of the products that are developed by CBSD is increasing on a daily basis. By this the time and cost of the product is minimized easily. Mostly risks are not identified in the first phase, so these risks overlap to the next phase. So for avoiding this, the proper risk management strategy is used to minimize the possible risk.
Список литературы Risk Reduction Activities Identification in Software Component Integration for Component Based Software Development (CBSD)
- Basha, N. M. J. and Dr. S. A. Moiz. 2012. Component Based Software Development: A State of Art. ICAESM., pp. 599-604.
- Qureshi, M. R. J. and E. Sandhu. 2009. A validation of proposed Component Based Devlopment process. Sci. Int., 21(2): 131-135.
- Kaur, A. and S. Goel. 2011. Designing RIMCOTS Model for Risk Identification and Mitigation for COTS –based Software Development. pp. 24- 26.
- Shashank, P. S., P. Chakka and D. V. Kumar. 2010. A Systematic Literature Survey of Integration Testing in Component Based Software Engineering. ICCCT., pp. 562-568.
- Johar, K. A. and S. Goel. 2011. COTS Components usage Risks in Component Based Software Development. International Journal of Information Technology and Knowledge Management, 4(2): 573-575.
- Mahmood, S. 2011. Towards Component Based System Integration Testing Framework. Engineering, pp. 4-8.
- Gupta, R. and S. Raghav. 2012. Risk Assessment Techniques and Survey Method for COTS Components. IJJSEA., 3(1): 181-195.
- Khan, A., N. Qayyum and U. A. Khan. 2012. An Improved Model for Component Based Software Development. Software Engineering, 2(4): 138-146.
- Mandal, A. and S. C. Pal. 2012. Emergence of Component Based Software Engineering. IARCSSE., 2(3): 311-315.
- Khan, U. A., I. A. Al-Bidewi and K. Gupta. 2011. Challenges in Component Based Software Engineering as the Technology of Modern Era. IJIC., 1(2): 67-72.
- Kusumo, D. S., M. Staples, L. Zhu, H. Zhang and R. Jeffery. 2012. Risks of Off the Shelf Based Software Acquisition and Development: A Systematic Mapping Study and Survey. IET., pp. 233-242.
- Kaur, M. 2014. Analysis of Component Integration on Component Based Development Paradigm. IJESRT., 3(8): 143-146.
- Bannerman, P. L. 2015. A Reassessmet of Risk Management in Software Projects. Springer, pp. 1119-1134.
- Ray, M. and D. P. Mohaptra. 2013. Risk analysis, a guiding force in the improving of Testing. IET Softw., pp. 29-46.
- Mahmood, S. 2013. Empirical Study of Software Component Integration Process Activities. IET Softw., 7(2): 65-75.
- Pande, J. 2012. On Some Critical Issues in Component Selection in Component based Software Development. International Journal of Computer Application., 46(4): 44-50.
- Vale, T., I. Crnkovic, E. S. D. Almeida, P. A. D. M. S. Neto, Y. C. Cavalcanti and S. R. D. L. Meira. 2016. Twenty Eight years of Component Based Software Engineering. Sci. Dir., 111:128-148.
- Kathan, H., N. A. Bakar and R. Nordin. 2014. Reviewing the Challenges of Security Features in Component Based Software Development Models. IEEE., pp. 230-235.
- Hijazi, H., S. Alqrainy, H. Muaidi and T. Khdour. 2014. Identifying Casualty Relation between Software Projects Risk Factors. IJSEIA., 8(2): 51-58.


