Robust Dual Watermarking Scheme for Video Derived from Strategy Fusion
Автор: Neeta Deshpande, Archana Rajurkar, R.R.Mathalkar
Журнал: International Journal of Image, Graphics and Signal Processing(IJIGSP) @ijigsp
Статья в выпуске: 5 vol.6, 2014 года.
Бесплатный доступ
Current paper proposes a novel robust dual watermarking scheme that entrench a decipherable sample in the spatial domain and an invisible watermark in frequency domain of a color video. Visible watermark facilitate in the protection of publicly accessible data thus providing an imperative contribution for avoiding illegal duplication of data. The adaptive visible watermarking algorithm exploits various histogram features and not only embeds a visible watermark in the spatial domain but also facilitates its extraction and removal thus endowing with the facet of reconstruction of the video. For enhancing the robustness of the scheme and increasing the degree of protection of the watermark, invisible watermark is scrambled in parts and embedded in various frames of the video in DCT domain. These dual watermarks are embedded in host video. The robustness of the scheme is verified with various signal processing attacks, geometric attacks and video watermarking attacks like frame averaging. Reconstruction of the video helps the authorized subscribers to refurbish the original video.
Watermarking, video, algorithm, Embedding watermark, extraction techniques
Короткий адрес: https://sciup.org/15013292
IDR: 15013292
Текст научной статьи Robust Dual Watermarking Scheme for Video Derived from Strategy Fusion
Published Online April 2014 in MECS DOI: 10.5815/ijigsp.2014.05.03
The obligation of secure communication and multimedia data transmission has potentially augmented with the advances of multimedia schemes. Information consistency is not secure in image transfer [1]. Digital watermarking [2] is a technique used for protection of Intellectual Property rights and copyright protection. The copyright data may be in the form of text [3 [4], image [5]-[8], audio [9], video [10-11]. Watermarking may be visible or invisible. Invisible watermarking [12] implies that the presence of the watermark is barely discernible when the watermarked signal is displayed. The media embedded with visible watermarks [13-16] contain recognizable but unobtrusive copyright pattern that conveys an immediate claim of the ownership of the media. When using a conventional visible watermarking technique, a user must keep both the original image and the watermarked one. Removable visible watermarking is proposed in this paper facilitating the reconstruction of the video. Few dual watermarking algorithms are proposed in literature [17-22]. Most of the algorithms have been experimented and studied for the gray scale images. Shih and Wu [17] proposed a combinational method that embeds distinct watermark parts into the host gray scale image. This scheme embedded two invisible watermarks, and was capable of resisting the cropping attack. In [18], the author embedded a visible logo into the host image, and an invisible authentication code into the most significant bit (MSB) of the processed image. For the verification of the tampered data, the algorithm can retrieve the invisible authentication code once the visible watermark suffers an attack. However, the ownership of the watermarked image cannot be claimed from the extracted authentication code. Hu et al. [19] prevailed over [20] by embedding an invisible watermark into the frequency of visibly watermarked image via the discrete wavelet transform (DWT). The ownership of the protected image can be verified with the invisible extracted watermark when the visual watermark was attacked. This scheme can resist the JPEG compression and partially resist in painting attacks. In [20], the author designed a dual watermarking algorithm that was capable of resisting the in painting attack. The algorithm was able to restore the unmarked image. Without any attacks, the former embedded logo is seriously distorted in [17-19] because the embedded dual logos are overlapped in the watermarked image, and embedding the second logo modifies the pixel values of the previous. Design of a dual watermarking scheme that can resist malicious attacks without causing logo overlap is still under investigation [20]. The schemes in [17, 19, and 20] were basically designed for gray scale images. In [21], the author offers an algorithm for embedding dual watermarks in gray videos. Two invisible watermarks were embedded using two spread sequences exploiting the DWT technique. This algorithm was robust to attacks like low pass filtering, frame dropping and MPEG coding. Also in the algorithm presented in [22], the author embedded two invisible watermarks in the video by means of the DWT technique and it was robust to geometric attacks like rotation, cropping and contrast altercation.
To assure the protection of the publicly available data with a visible watermark and to ensure copyright protection with robust invisible watermark, we offered a dual watermarking scheme that embeds a visible watermark using an adaptive embedding algorithm and invisible watermark exploiting the DCT technique. The visible watermark of the proposed scheme can visibly specify the rights of the protected video while the invisible one can avoid the watermarked video from malicious attacks. Consequently the experimental results of the designed algorithm allow the authorized users to recover the watermarked video. The invisible watermark is scrambled into parts to enhance the robustness of the scheme thus enhancing the degree of protection. The valuable feature offered in the algorithm is the reconstruction of the video after removal of the visible watermark.
The paper is organized in four main sections. Subsequent section explicates the robust dual watermarking scheme offering the four algorithms for embedding and extraction of visible and invisible watermarks as its subsections. Section III is devoted to experimental results and discussions about the proposed robust dual watermarking scheme including the comparative results of the proposed scheme by means of various histogram features for embedding dual watermarks with the techniques available in the literature.
Section IV focuses on the conclusion examined out with the proposed scheme.
-
II. PROPOSED DUAL WATERMARKING SCHEME
The proposed algorithm embeds dual watermarks, an adaptive visible and a scrambled invisible watermark in the video sequence. The visible watermarking is based on four histogram features standard deviation, skewness, entropy and energy.
Four versions of visible watermarking algorithms are designed in combination of an invisible watermarking algorithm to embed the dual watermarks in the video sequence. The invisible watermarking algorithm exploits the DCT concept and the concept of watermark casting in combination with the zigzag scanning to embed the scrambled watermark in the video sequence. So every video frame will consist of two watermarks, an adaptive visible watermark embedded by using any one of the histogram feature and an invisible watermark embedded using watermark casting. Fig 1 shows the proposed algorithm for embedding dual watermarks in the video sequence.
-
A. Visible Watermarking and Schemes of Evaluation
The offered scheme is an adaption and extension of the watermarking algorithm from [23] that embeds an adaptive watermark in the video frame in spatial domain by exploiting the sensitivity of human eyes. The algorithm is extended for video and refurbished with various histogram features to exploit the sensitivity of human eyes. Visible watermarking is one of the ways to prevent illegal use from the unauthorized users by observing the visible logo by human eyes.
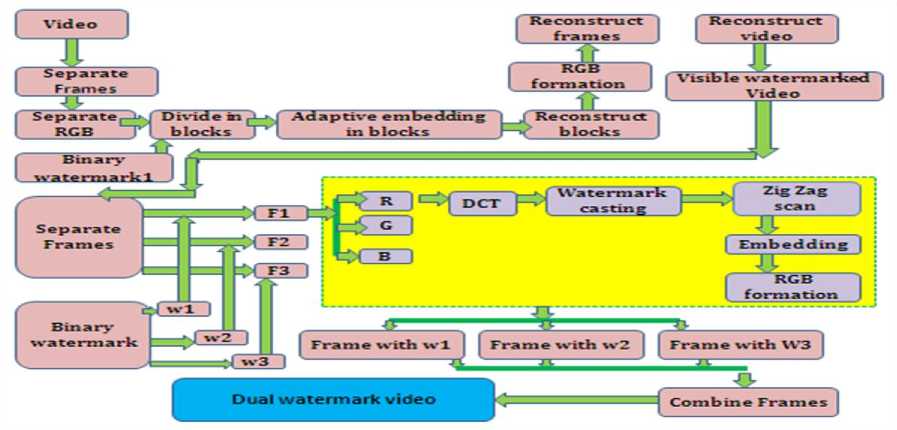
Figure 1 Proposed Algorithm for Embedding Dual Watermark
Visible watermarking is one of the ways to prevent illegal use from the unauthorized users by observing the visible logo by human eyes. The embedded watermark must be visible to human eyes and robust to most image processing operations. To meet these requirements, the visible watermark bits are embedded in the block of the host image depending on the intensity pixels of the block. In [23], the author has embedded an adaptive watermark by modifying the intensities of some of the pixels in the blocks. The intensities of the pixel in the block were altered depending on the contrast of the pixels in the block. The same concept was exploited with an extension by modifying the pixels in the blocks with various histogram features.
-
a) Visible Watermarking with Standard Deviation
Standard deviation is a measure to describe the magnitude of noise. This noise may degrade the quality of the image. Standard deviation calculates the distinctive dissimilarity that a pixel will have from its accurate value. We explored this parameter of an image to embed the visible watermark in the video frames. In general the parameters of first order histogram probability [24] are defined as
Р (9) = N (д )/М (1)
Wher e P (g) = probability of gray level g in the image, N (g) = number of pixel with gray level g in the image, M =total number of pixels in the image.
The experimentation of the watermarking scheme is carried out with Mean and Standard deviation defined as
L—l height—1 width-1
Мест = д=^д Kg= Z Z ^МТ g=0 r=0 c=0
Standard Deviation ag = Z
(д-д )2 P(g )
The same algorithm is extended for pixel modification depending on the entropy, skewness and energy of the pixels that is used in combination with the invisible watermarking algorithm and functioned to frames of the video. Selection of the visible algorithm for the frame is done randomly. The embedded watermark is successfully extracted and also removal of the visible watermark is possible from the video frames and the video reconstructed.
-
b) Visible Watermarking with Skewness
The skewness measures the asymmetry or the unbalance about the mean in the gray level distribution [24]. This feature is exploited and the visible watermarking algorithm is extended by comparing the intensities of the block of the video frame with the skewness value and modifying the pixel intensities accordingly to embed the visible watermark. Skewness can be defined as [24]
skew = -^ XLg=o(g - д )3 P(g)(4)
-
c) Visible Watermarking with Entropy and Energy
The quality of the image can be described by the statistical measure Entropy [24] defined as
Entropy = -T^log2 [PCs)](5)
Energy is defined as
Energ у = Z^^Cg)]2
The Visible watermarking algorithm has four separate algorithms exploiting standard deviation, entropy, skewness and energy of the pixels for embedding the visible watermark.
A.1 Visible watermark embedding algorithm (energy version)
Step 1: Preprocessing
-
1. Load the video and separate frames in RGB components. For a frame, I , with the size of M × N , the binary watermark wm, is embedded into its R G B components, W is the watermarked frame and wm is a binary watermark wm(x, y) ε {0, 1}, x = 1……M, y = 1……N.
-
2. Select an arbitrary threshold value for alpha that determines the relative brightness difference in the image.
Step2: Block processing
-
1. Divide the frame in infrequent blocks of 4*4
-
2. Calculate the energy for every block Mblk, by using (Entropy, std deviation and skewness in various versions) as in equation 5.
Step 3: Adaptive Watermark Embedding
-
1. Find pixels having values < energy for every block
-
2. Find their average Navg
-
3. For Embedding, validate the values of all pixels in the block
Navg=sum [Mblk]/no of values
-
a) If the watermark bit is 1
-
i) Compare values of the block with the average of the pixels Navg
-
ii) If a pixel > Navg value is found replace it with the maximum intensity pixel in the block.
-
iii) If a pixel with value > Navg but < energy of block is found, replace it with the value of energy.
-
iv) For other pixels increase the relative brightness by adding the threshold.
Mblk(s) = Mblk(s) + alpha
-
b) If the watermark bit=0
-
i) Compare values of the block with the average of the pixels (Navg) whose values are less than energy of the block.
-
ii) If a pixel < Navg replace it with the minimum intensity pixel in the block.
-
iii) If a pixel > Navg and < than energy of the block is found, replace it with the value of energy.
-
iv) For other pixels decrease the relative brightness by subtracting the threshold.
Mblk(s) =Mblk(s)-alpha
Step 4:-Reconstruction of the image and watermarked video.
-
1. Reconstruct the block Mblk with modified values in the entire blocks
-
2. Reconstruct the frames from RGB
-
3. Reconstruct the frames to form a watermarked video
-
A.2 Visible watermark extraction and removal
The extraction of the visible watermark is a non blind retrieval requiring the original frame during the execution.
-
1. The process for extraction of the visible watermark follows similar lines of the embedding procedure in reverse order.
-
2. Divide the original and watermarked frames in same number of blocks Xo and Xw respectively.
-
3. Figure out the pixel intensities of each block PXo and PXw respectively and evaluate their sum.
-
4. If sum of block of original frame is greater than watermarked frame
-
• Set watermark bit = 1
-
• Set reference out = PXo
Else if sum of block of original frame is less than or equal to watermarked frame
-
• Set watermark bit to 0
-
5. Reconstruct the watermark from the extracted bits, and reconstruct the frame from blocks of PXo.
-
B. Invisible Watermarking
The basic watermarking casting concept is adapted from [26] and is exploited for embedding the scrambled watermark in the video sequence. In the proposed algorithm a binary watermark is scrambled in three components and each component is embedded using the zigzag scanning of the DCT coefficient in different frames of the video. This is done exploring the watermark casting concept on the frame where a visible watermark is already placed. The following algorithm results in robust embedding of the invisible watermark on the video sequence .
-
B.1 Invisible Watermark Embedding Algorithm
Step 1: Preprocessing
-
1. Load the visible watermarked video obtained in step 1 and separates the frames. Let I(x, y) is a frame of the video of size X*Y.
-
2. Select a binary image wm of size P*Q to conceal as an watermark
-
3. Scramble wm in three parts wm1, wm2 and wm3 depending on the size of the watermark such that wmi=P*Qi where Qi=Q/3.
-
4. Define random threshold value for alpha α
-
5. Generate a key for embedding. Same key would be needed for the extraction of the watermark
Step 2 Embedding
-
1. One Scrambled watermark is embedded in each frame of the video. Translate the scrambled image Wmi(x,y) of size m*n to a vector and reorder into one dimensional zigzag sequence.
-
2. Separate the frame I in R, G, and B components and find the discrete cosine transform of the every component.
-
3. Embedding is done by casting the watermark in the coefficients of the mid band frequency of DCT spectrum by the following equation
-
4. The high energy pixels of the watermark are stored in the selected DCT coefficients with low energy and added with original frame to get the watermarked frame.
R(x,y)=zigzag(wmi)*scaling factor.
Step 3 Watermarked Video Construction
-
1. Reverse zigzag scan is performed along with the inverse DCT to get the original Component of the frame.
-
2. A dual watermarked video is obtained by reconstructing the video RGB components
-
B.2 Invisible Watermark Extraction Algorithm
-
1. Load the watermarked video and the original video and separate them in frames W’(x,y) and I(x,y) respectively
-
2. Select arbitrary threshold alpha and key that is same as was in the embedding procedure.
-
3. Read in the scrambled watermark image Wi (x,y) of size m*n that was embedded as an invisible watermark.
-
4. Separate watermarked frame and original frame R, G, B components and find the DCT of the every component of original and watermarked frame to get the difference.
-
5. Stock it up in a vector manner by storing in the zigzag scan order. Watermark casting is again done
-
6. Generate a random matrix R(x,y) of the size of the watermark wmi and compute
-
7. The scrambled binary watermark Wm’(x,y ) is formed by extracting the 0’s and ones from the Wm’(x,y).
to extract the DC components from the difference and store in Temp.
Wm’(x,y)=Temp/R(x,y)
-
III. RESULTS AND DISCUSSIONS
The proposed algorithm has been implemented and tested on a various videos and the experimentation testing was carried out on various avi video files in mat lab. Dual watermarks, a visible in the spatial domain exploiting the histogram features and an invisible watermark in the frequency domain exploiting DCT concept were successfully embedded and extracted by the proposed embedding and extraction algorithms. A successful removal of the visible watermark was achieved with disturbing the perceptual quality of the video. This section offers the Pictorial and graphical results of experimentation. The testing was carried out with
Visimark1_0 [27], a tool for evaluating the robustness of the video watermarking algorithms.
-
A. Embedding and Extraction of Dual Watermarks
The binary image watermark was successfully embedded and extracted from the video sequence. In the dual embedding procedure all four versions of the visible watermarking are applied sequentially on frames of video and the scrambled invisible watermark is embedded in different frames of video. Fig 2 illustrates the results of entire dual watermarking process for a video whose frame is watermarked with the energy version of visible and the scrambled parts of the invisible watermark in each frame sequentially. Fig2a 2b and 2c shows the original video frame, binary invisible and binary visible watermark respectively. In the process of watermarking the invisible watermark is scrambled in three parts shown in Fig b1, b2 and b3 respectively. Fig 2d illustrated the frame of the dual watermarked video. In the extraction process, foremost the invisible scrambled watermarks are obtained as shown in Fig 2f that are merged together to obtain the extracted invisible watermark of Fig 2g. Finally the visible watermark is extracted as shown in Fig 2f.

a) Original Video frame



b1

b2
d ) Scrambled invisible watermarks

b3
e) Dual watermarked frame
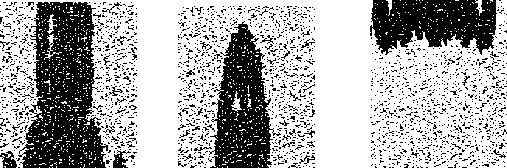
f) Extracted Scrambled watermarks

g) Combined Invisible

h) Extracted Visible
Figure 2 Results of Dual watermark embedding procedure with Visible and Invisible Watermarks
PSNR
MSAD
Averaging Filter attacked
Blurring attacked
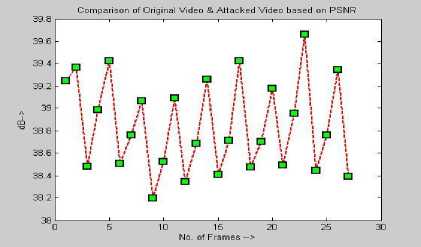
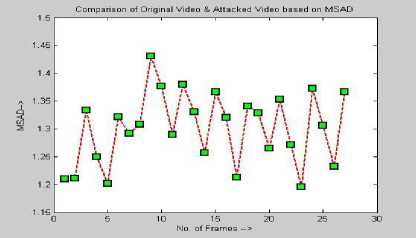
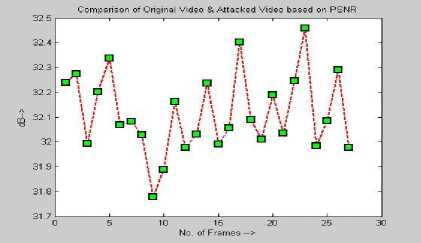
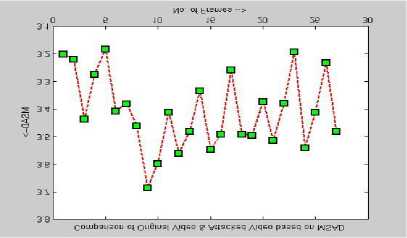
Figure 3 PSNR and MSAD between original and attacked videos
-
B. Verification of Quality of Original and Watermarked Video
The measures adopted by researchers for the evaluation of watermarking algorithms are followed in the proposed work. The quality of embedding was tested with parameters like peak signal to noise ratio PSNR is calculated from Mean Square error (MSE) between two images and DELTA is the mean difference of the color components in the corresponding points of the image.
PSNR = 10 1 о g 1 0 [^ ] (7)
DEL TA = I^h — (8)
, V—1 mn
The results of PSNR and MSAD of the averaging filter and the blurring attacked videos and original videos are illustrated in Fig 3. The Quality of Robustness is evaluated by the Normalized cross correlation [25] given as
Where Wji , j )) and W'ji , j) are the original and the watermarked images.
-
C. Verification Of Robustness For Extracted Dual Watermarks
After Successful embedding and extraction of the dual watermarks, the dual watermarked video was tested to assortment of attacks. Successful testing on various attacks like filtering, noising, scaling, frame dropping etc was carried out. Fig 4 illustrates the frames of the attacked videos and the extracted visible and invisible watermarks after the attacks were applied. To verify the robustness of the scheme of the watermarking scheme, the normalized correlation coefficient was calculated for the extracted visible and invisible watermark and the results are elaborated in Figure 5. The proposed algorithm is able to extract both the invisible and visible watermark with an accuracy of above 90 percent, yielding the NC value above 0.9. The proposed algorithm allowed the removal of the visible watermark even after the application of various attacks.
NC
=ZM T2 (i ^')w' ( i')
Z—ii=iZ—ij=i
Ml М2
Ml М2
/ VZ Z w( ^ j )2 ^ZZ w' (u')2
1=17=1
1=1 7 = 1

a)Blurring attacked Extracted Visible

Extracted Invisible

Visibl e removed after blurring attack

b)Gaussianfilter(GF)attacked Extracted Visible

Extracted Invisible

Visible removed after GF attack

c) Sharpening(S) attacked

Extracted Visible

Extracted Invisible

Visible removed after S attack

d) Averaging Filter (AF)

Extracted Visible

Extracted Invisible

Visible removed after AF attack

e) Scaling attacked

Extracted Visible

Extracted Invisible

Visible removed after scaling attack
Figure 4 Attacked frames extracted watermarks and visible removed frames after attacks
-
D. Comparison with Existing Techniques in the Literature
The proposed dual watermarking algorithm is compared with the dual watermarking algorithms available in the literature. The proposed algorithm is successfully implemented to embed robust dual watermarks in video. The main feature of dual watermarking is that if one watermark is unable to resist a particular attack then the other still persists to fulfill the aim of watermarking. Table 1 elaborates the comparison with the techniques available in the literature. In the proposed scheme, the dual watermark was embedded in the color host video. To enhance the security, the invisible watermark was scrambled into parts and was embedded in the successive frames. Successful extraction of both visible and invisible watermarks further strengthened the algorithm. Reconstruction of the video after the removal of the visible watermark was yet another focusing feature of the proposed scheme.
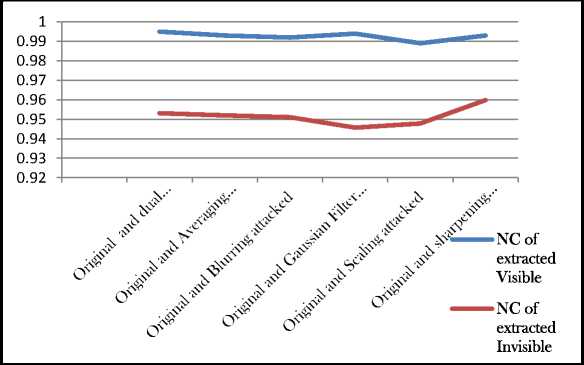
Figure 5 Normalized Correlation Coefficient of Original and Extracted Visible and Invisible Watermarks
TABLE I. Comparison of Techniques in Literature
|
[17] |
[18] |
[19] |
[20] |
[21] |
[22] |
Ours |
|
|
Base for Embedding |
Gray Image |
Gray image/color |
Gray |
Image |
Video |
color Video |
Color Video |
|
Dual Watermark |
Invisible + Invisible |
Visible + Invisible |
Visible + Invisible |
Visible + Invisible |
Invisible+ invisible |
Invisible + Invisible |
Visible + Invisible |
|
Technique |
Spatial + DCT |
Spatial + Spatial |
DWT + DWT |
Spatial + DCT |
DWT+ DWT |
DWT+DWT |
Spatial+DC T |
|
Extraction/Detection |
Extraction |
Detection |
Extraction |
Extraction |
Extraction |
Extraction |
Extraction |
|
Scramble Watermark |
Yes |
No |
No |
No |
No |
No |
Yes |
|
Image/Video reconstruction |
- |
- |
- |
Yes |
- |
- |
Yes |
|
PSNRof reconstructed |
- |
- |
- |
db |
- |
- |
db |
|
DELTAof reconstructed |
- |
- |
- |
- |
- |
- |
Yes |
|
Normalized Cross corelation |
- |
- |
- |
yes |
Yes |
-
IV. CONCLUSIONS
The proposed scheme of dual watermarking for video that embedded a readable sample i.e. a binary image in the spatial domain and an invisible binary watermark in frequency domain was successfully implemented. Illegal duplication of data can be avoided due to visible watermark. The robustness of the scheme and the extent of protection of the watermark are enhanced by embedding scrambled invisible watermark in various frames of the video in DCT domain. Evaluation of robustness of the scheme is verified with various signal processing attacks, geometric attacks and video watermarking attacks like frame averaging. Reconstruction of the video is an added feature that helps the valid users to renovate the original video.
Список литературы Robust Dual Watermarking Scheme for Video Derived from Strategy Fusion
- F. Deguillaume, S. Voloshynovskiy, and T. Pun. Hybrid robust watermarking resistant against copy attack. In EUSIPCO'02, Toulouse, France, 2002.
- I. G. Langelaar and R.Lagendijk, “Watermarking digital image and video data: A state-of-the-art overview,” IEEE Signal Processing Magazine, vol. 17, pp. 20–46, 2000.
- J. Brassil, S. Low, N. Maxemchuk, and L. O’Gorman “Electronicmarking and identification techniques to discourage document copying,” IEEE J. Select. Areas Commun., vol. 13, pp. 1495–1504, Oct. 1995.
- S. Low, N. Maxemchuk, J. Brassil, and L. O’Gorman, “Document marking and identification using both line and word shifting,” in Proc. Infocom ’95, Boston, MA, Apr. 1995
- Y. Yorozu, M. Hirano, K. Oka, and Y. Tagawa, “Electron spectroscopy studies on magneto-optical media and plastic substrate interfaces(Translation Journals style),” IEEE Transl. J. Magn.Jpn., vol. 2, Aug. 1987, pp. 740–741 [Dig. 9th Annu. Conf. Magnetics Japan, 1982, p. 301].
- F. M. Boland, J. J. K. ó Ruanaidh, and W. J. Dowling, “Watermarking digital images for copyright protection,” in Proc. Int. Conf. Image Processing and Its Applications,
- F. M. Boland, J. J. K. ó Ruanaidh, and W. J. Dowling, “Watermarking digital images for copyright protection,” in Proc. Int. Conf. Image Processing and Its Applications, vol. 410, Edinburgh, U.K., July 1995.
- M. S. Kankanhalli, Rajmohan, and K. R. Ramakrishnan, “Contentbased watermarking of images,” in Proc. ACM Multimedia ’98, Bristol, U.K., Sept. 1998
- L. Boney, A. H. Tewfik, and K. H. Hamdy, “Digital watermarks for audio signals,” in Proc. EUSIPCO 1996, Trieste, Italy, Sept. 1996.
- F. Hartung and B. Girod, “Digital watermarking of raw and compressed video,” in Proc. SPIE Digital Compression Technologies and Systems for Video Commun., vol. 2952, Oct. 1996, pp. 205–213.
- F. Jordan, M. Kutter, and T. Ebrahimi, “Proposal of a watermarking technique for hiding/retrieving data in compressed and decompressed video,” ISO/IEC Doc. JTC1/SC29/WG11 MPEG97/M2281, July 1997.
- S. D. Lin and C. F. Chen, “A Robust DCT-Based Watermarking for copyright Protection,” IEEE Trans. on Consumer Electronics, Vol. 46, No. 3, pp. 415?421, Aug 2000.
- Mohan S. Kankanhalli, Rajmohan, and K. R. Ramakrishnan, “Adaptive visible watermarking of images.” Proc. 1999 IEEE Int. Conf. on Multimedia Computing and Systems, Vol. 1, pp. 568 –573, 1999.
- Saraju P. Mohanty, K.R. Ramakrishnan, and Mohan S. Kankanhalli, “A DCT domain visible watermarking technique for images.” Proc. 2000 IEEE Int. Conf. on Multimedia and Expo, Vol. 2, pp.1029 –1032, 2000.
- Pei-Min Chen, “A visible watermarking mechanism using a statistic approach,” Proc. 5th Int. Conf. on Signal Processing, Vol. 2, pp. 910 –913, 2000.
- Yongjian Hu and Sam Kwong, “Wavelet domain adaptive visible watermarking,” Electronics Letters, Vol. 37, pp. 1219 –1220, Sept. 2001.
- Y. Shih and Y. T. Wu, “Combinational image watermarking in the spatial and frequency domains,” Pattern Recognition, vol. 36, no. 4, pp. 969–975, Apr. 2003.
- S. P. Mohanty, K. R. Ramakrishnan, and M. S. Kanakanhalli, “A dual watermarking technique for images,” in Proc. 7th ACM Int. Multimedia Conf. (ACMMM), vol. 2. FL, Oct.–Nov. 1999, pp. 49–51.
- Y. Hu, S. Kwong, and J. Huang, “Using invisible watermarks to protect visibly watermarked images,” in Proc. 2004 Int. Symp. Circuits Syst., vol. 5. pp. 584–587.
- Pei-Yu Lin, Jung-San Lee, and Chin-Chen Chang, Fellow, IEEE “ Dual digital watermarking for Internet media based on hybrid strategies” IEEE trans on circuits and systems for video technology pp 1169-1177 Aug 2009
- Seung-Jin Kim1, Suk-Hwan Lee1, Kwang-Seok Moon2, Woo-Hyun Cho2, In-Taek Lim3, Ki-Ryong Kwon3, and kuhn-Il Lee1 “A New Digital Video Watermarking Using the Dual Watermark Images and 3D DWT” ieee tencon south korea pp291-294 , 2004
- Gandhe,S.T.; Potdar, U.; Talele, K.T.; S.P.I.T., Mumbai, India , Dual Watermarking in Video Using Discrete Wavelet Transform machine Vision pp 216-219 , 2009
- C.H.Lee and Y.K.Lee, “ An adaptive image watermarking technique for copyright protection”, IEEE transactions on consumer electronics, Vol 45, No 4, November 1999 pp.1005-1015
- http://metalab.uniten.edu.my//....Chapter%202_5%20-%20feature.
- Fabien A. P. Petitcolas, Ross J. Anderson and Markus G. Kuhn, Information Hiding|A Survey”, Proceedings of the IEEE, special issue on protection of multimedia content, 87(7):1062{1078}, July 1999
- Fabing Duana and Derek Abbot ,” The application of nonlinear bistable detectors to DCT-domain watermarking schemes, proc of SPIE vol 6802,680215(2008)
- Mrs Neeta Deshpande, Mr Mahesh Sanghavi , Dr. Archana Rajurkar , Dr R.R. Manthalkar , “Visimark1_0 :- An Assistant tool for evaluating the robustness of video watermarking Algorithms, I.J. Information Technology and Computer Science, 2013, 05, 10-21 Published Online April 2013 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijitcs.2013.05.02 pp 10-21.


